Command
Access-list (Extended)
Use
This command is used to create a list that matches packets on a given criteria. While access-lists are most commonly associated with security, there are numerous uses.
Extended lists match on source addresses and destination addresses as well as protocol information.
Syntax
Router(config)#access-list <100-199 or 2000-2699> <permit or deny> <tcp or udp or ip> <source host address or network or any> <operator> <port><destination host address or network or any> <operator><port>
Options
| <100-199> or <2000-2699> | Defines a standard access-list |
| <permit> | Permits all matches specified in the list. |
| <deny> | Denies all matches specified in the list. |
Network Options
| <host source ip> | Host ip address that sources packets matched by the list. |
| <source network> | IP network that sourced packets matched by the list. Uses Wildcard masks for matching. |
| <host destination ip> | Host ip address that sources packets matched by the list. |
| <destination network> | IP network that packets are destined for are matched by the list. Uses Wildcard masks for matching. |
| <any> | Match anything. |
Protocol Options
| <tcp> | Access-list will match TCP traffic. |
| <udp> | Access-list will match UDP traffic. |
| <ip> | Access-list will match all IP traffic. |
Operator Options
| <eq> | Equals a given port. |
| <gt> | Greater than a given port. |
| <lt> | Less than a given port. |
| <range> | A range between two ports. |
Wildcard Masks
Wildcard masks are how access-lists know what networks apply to the list. They are the inverse of the subnet mask.
For example, network 123.123.123.0 0.0.0.255 would match any ip address in the 123.123.123.0/24 network.
Because a /24 mask is 255.255.255.0, the inverse would be 0.0.0.255. For the network 34.77.108.0/28, the subnet mask would be 255.255.255.248 and the inverse would be 0.0.0.7
Notice how the subnet mask and the inverse add to 255.
Example
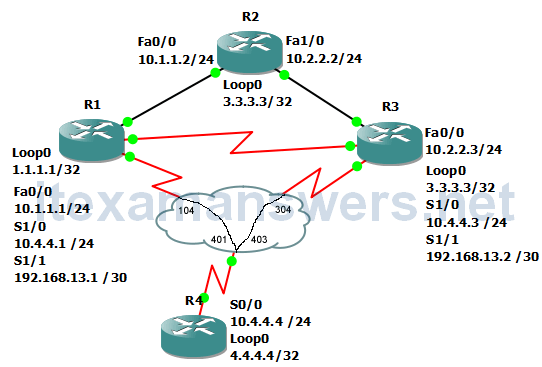
In this example, we will make an access-list that denies packets sourced by the host 1.1.1.1 and apply the list to R2’s Fa0/0.
R1(config)#access-list 101 deny tcp host 10.1.1.254 host 10.2.2.254 eq www R1(config)#access-list 101 permit ip any any R1(config)#int f0/0 R1(config-if)#ip access-group 101 in
In this example, we deny any tcp packet that has a port number 1024 or higher.
R1(config)#access-list 102 deny tcp any any gt 1024 R1(config)#access-list 102 permit ip any any R1(config)#int fa0/0 R1(config-if)#ip access-group 102 in
