Chapter 7 – Sections & Objectives
- 7.1 ACL Operation
- Explain how ACLs filter traffic.
- Explain how ACLs use wildcard masks.
- Explain how to create ACLs.
- Explain how to place ACLs.
- 7.2 Standard IPv4 ACLs
- Configure standard IPv4 ACLs to filter traffic to meet networking requirements.
- Use sequence numbers to edit existing standard IPv4 ACLs.
- Configure a standard ACL to secure vty access.
- 7.3 Troubleshoot ACLs
- Explain how a router processes packets when an ACL is applied.
- Troubleshoot common standard IPv4 ACL errors using CLI commands.
7.1 ACL Operation
7.1.1 Purpose of ACLs
What is an ACL?
- By default, a router does not have ACLs configured; therefore, by default a router does not filter traffic.
Packet Filtering
- Packet filtering, sometimes called static packet filtering, controls access to a network by analyzing the incoming and outgoing packets and passing or dropping them based on given criteria, such as the source IP address, destination IP addresses, and the protocol carried within the packet.
- A router acts as a packet filter when it forwards or denies packets according to filtering rules.
- An ACL is a sequential list of permit or deny statements, known as access control entries (ACEs).
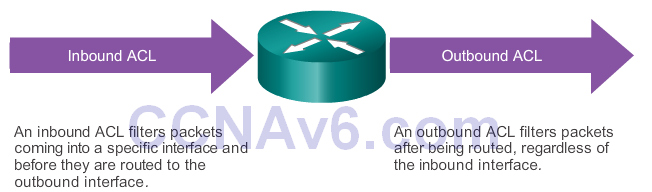
ACL Operation
7.1.2 Wildcard Masks in ACLs
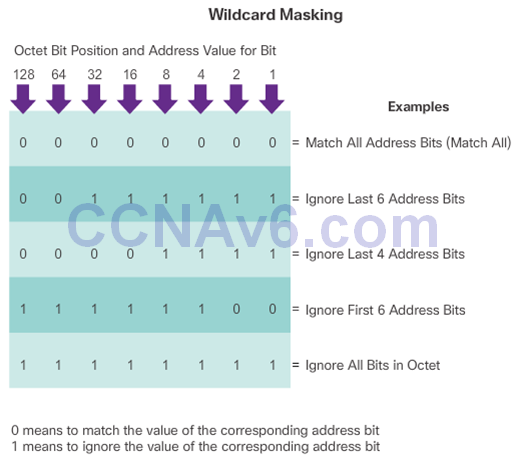
Introducing ACL Wildcard Masking
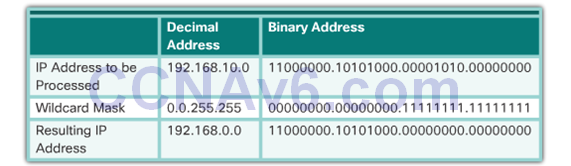
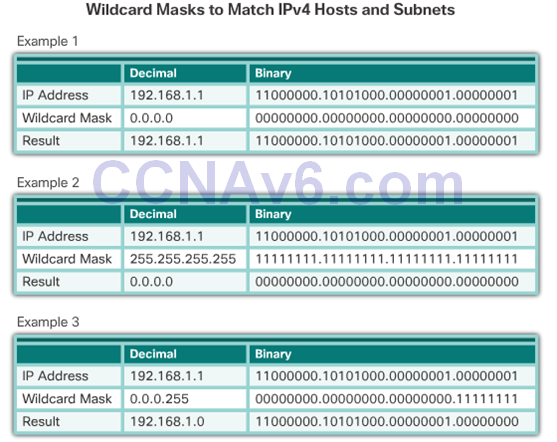
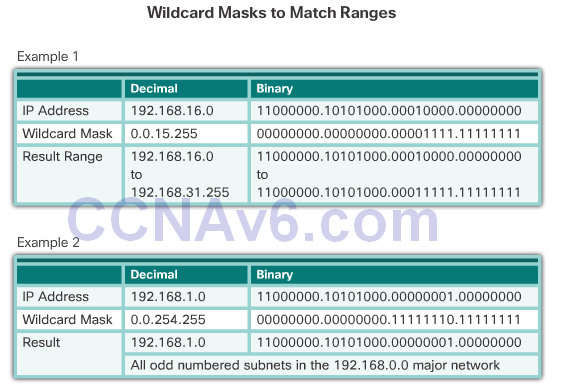
Example
Wildcard Mask Examples
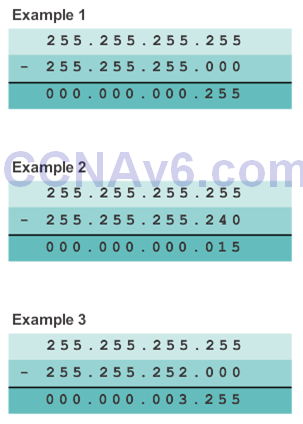
Calculating the Wildcard Mask
- Calculating wildcard masks can be challenging. One shortcut method is to subtract the subnet mask from 255.255.255.255.
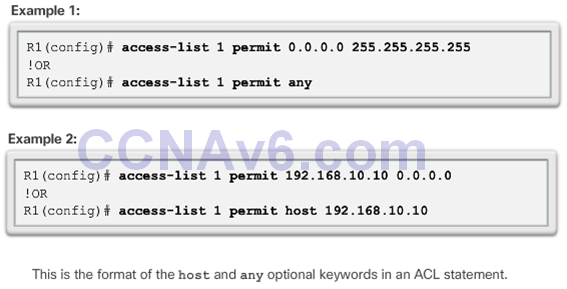
Wildcard Mask Keywords
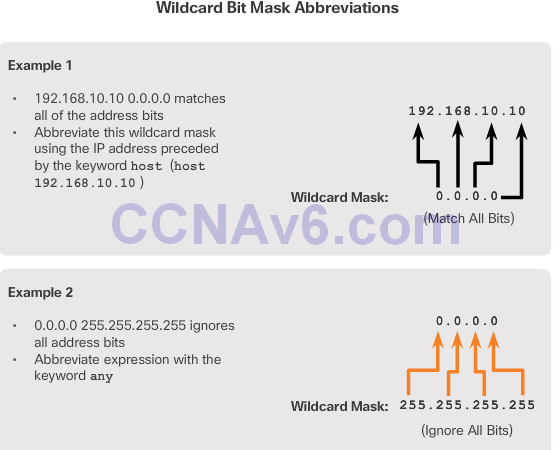
Wildcard Mask Keyword Examples
7.1.3 Guidelines for ACL Creation
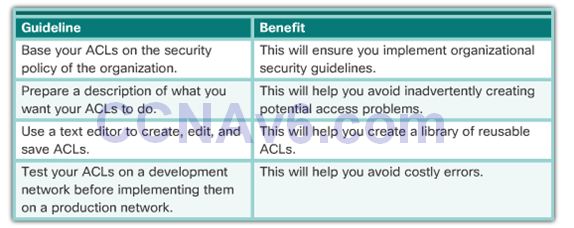
General Guidelines for Creating ACLS
ACL Best Practices
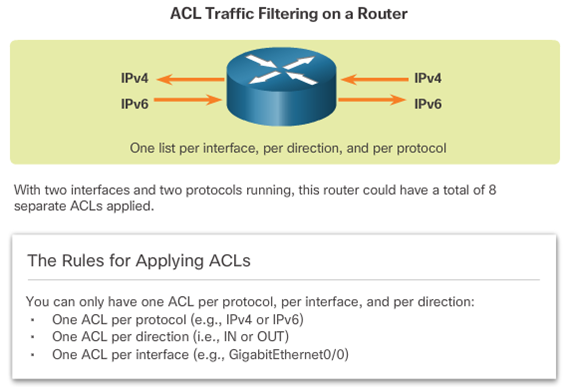
7.1.4 Guidelines for ACL Placement
Where to Place ACLs
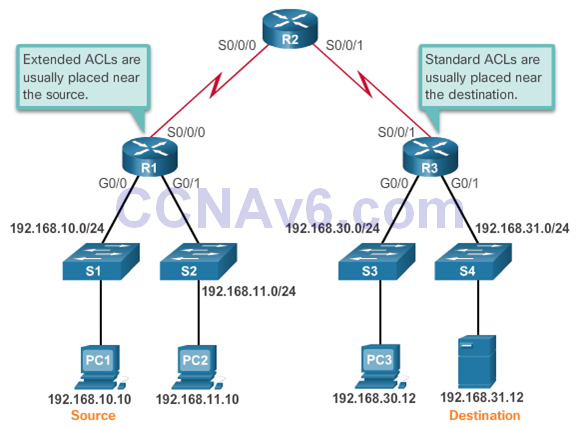
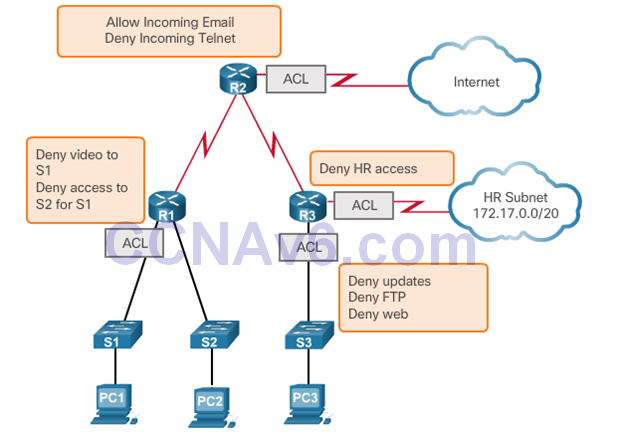
- Every ACL should be placed where it has the greatest impact on efficiency. The basic rules are:
- Extended ACLs – Locate extended ACLs as close as possible to the source of the traffic to be filtered.
- Standard ACLs – Because standard ACLs do not specify destination addresses, place them as close to the destination as possible.
- Placement of the ACL, and therefore the type of ACL used, may also depend on: the extent of the network administrator’s control, bandwidth of the networks involved, and ease of configuration.
Standard ACL Placement
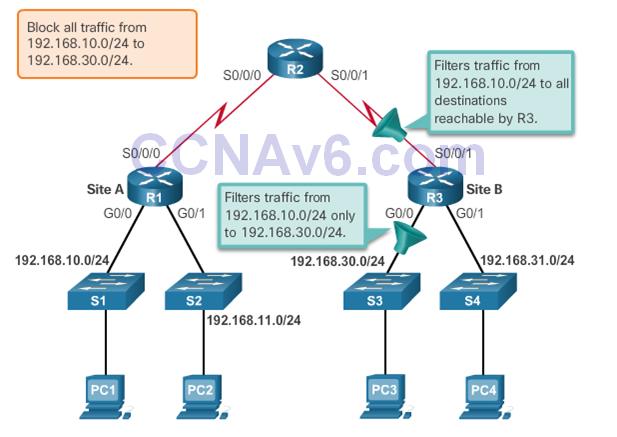
- The administrator wants to prevent traffic originating in the 192.168.10.0/24 network from reaching the 192.168.30.0/24 network.
7.2 Standard IPv4 ACLs
7.2.1 Configure Standard IPv4 ACLs
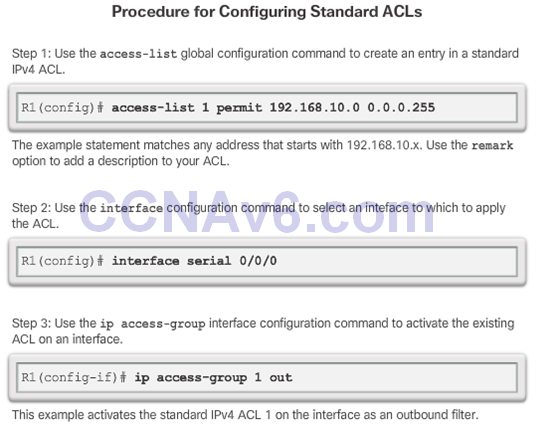
Numbered Standard IPv4 ACL Syntax
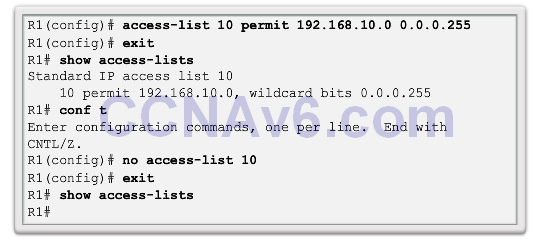
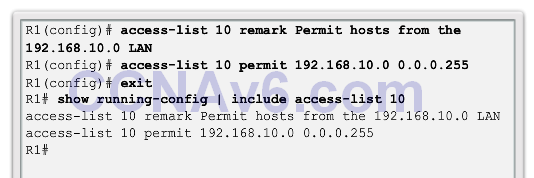
- Router(config)# access-listaccess-list-number { deny| permit | remark } source [ source-wildcard ] [ log ]
Applying Standard IPv4 ACLs to Interfaces
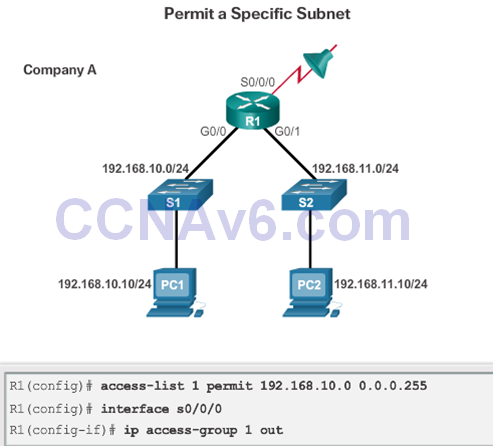
Numbered Standard IPv4 ACL Examples
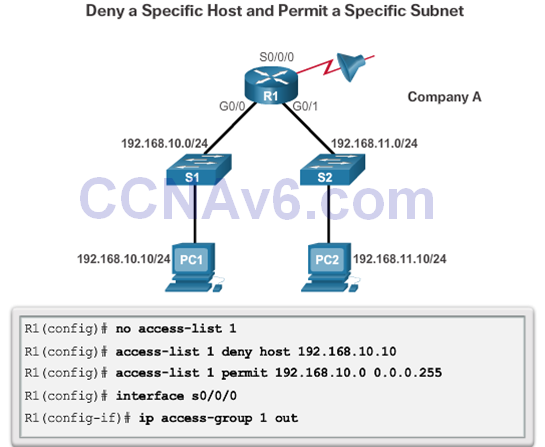
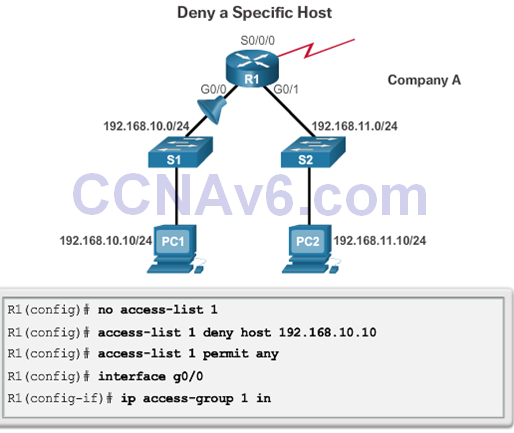
Named Standard IPv4 ACL Syntax
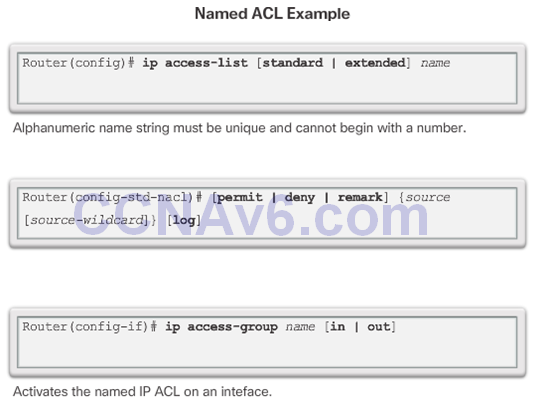
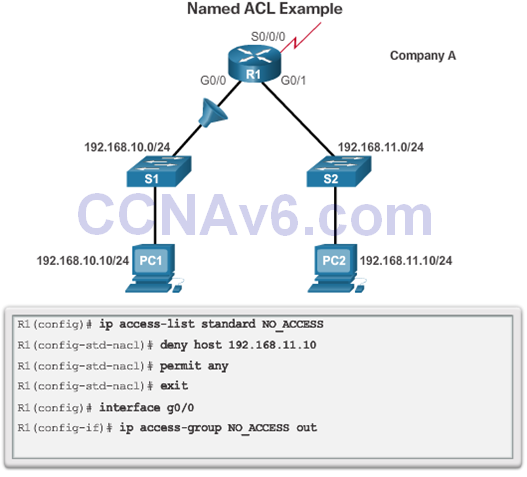
7.2.2 Modify IPv4 ACLs
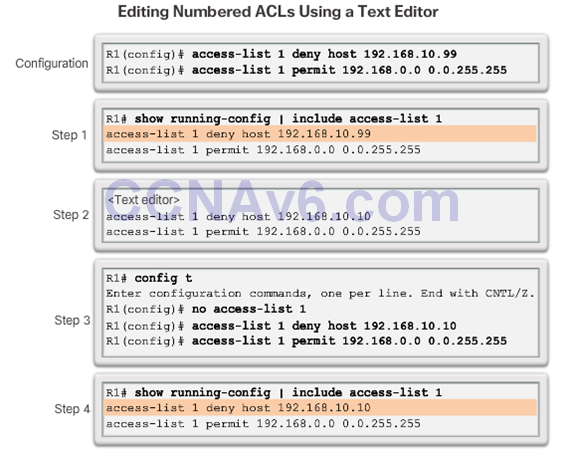
Method 1 – Use a Text Editor
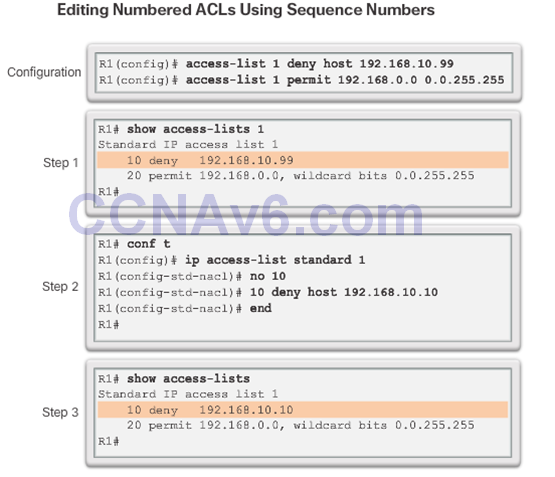
Method 2 – Use Sequence Numbers
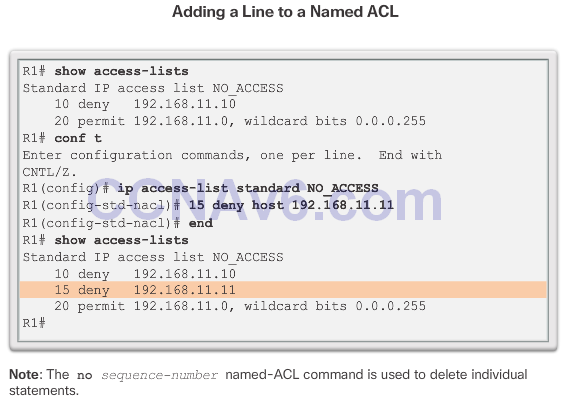
Editing Standard Named ACLs
Verifying ACLs
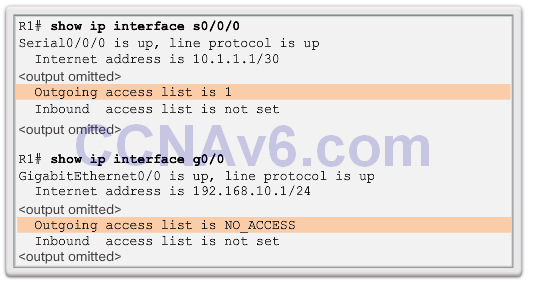
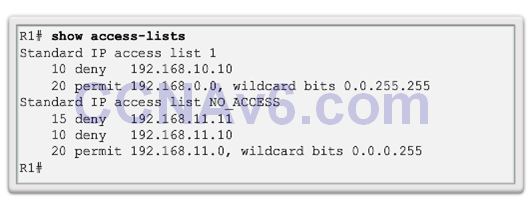
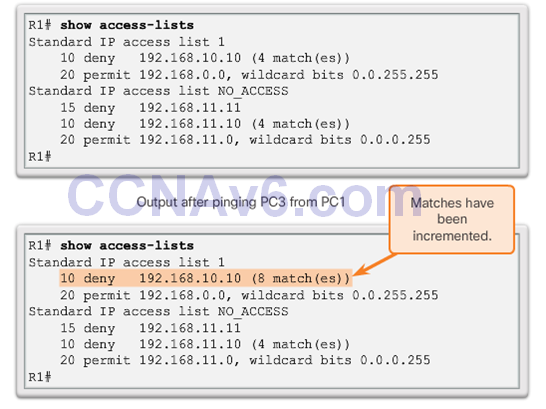
ACL Statistics
7.2.3 Securing VTY Ports with a Standard IPv4 ACL
The access-class Command
- Theaccess-class command configured in line configuration mode restricts incoming and outgoing connections between a particular VTY (into a Cisco device) and the addresses in an access list.
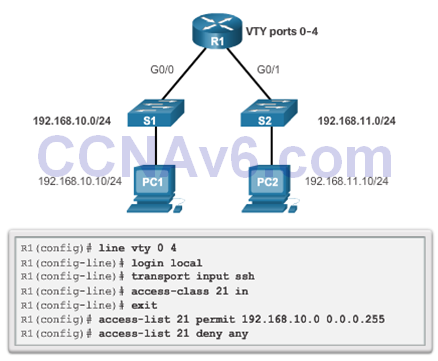
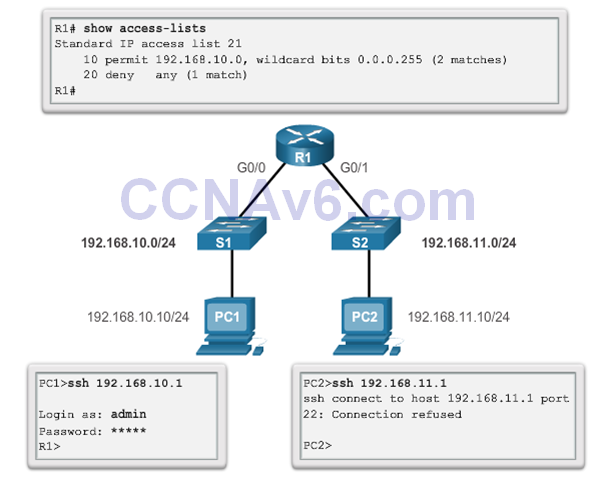
Verifying the VTY Port is Secured
7.3 Troubleshoot ACLs
7.3.1 Processing Packet with ACLs
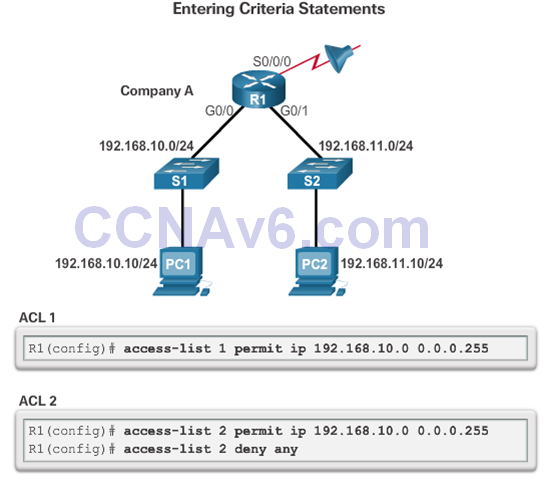
The Implicit Deny Any
- At least one permit ACE must be configured in an ACL or all traffic is blocked.
- For the network in the figure, applying either ACL 1 or ACL 2 to the S0/0/0 interface of R1 in the outbound direction will have the same effect.
The Order of ACEs in an ACL
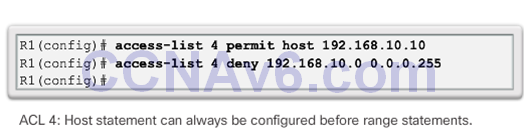
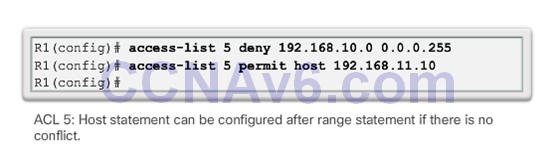
Cisco IOS Reorders Standard ACLs
- Notice that the statements are listed in a different order than they were entered.
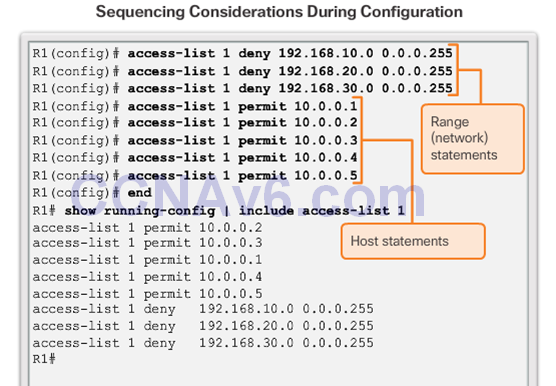
- The order in which the standard ACEs are listed is the sequence used by the IOS to process the list.
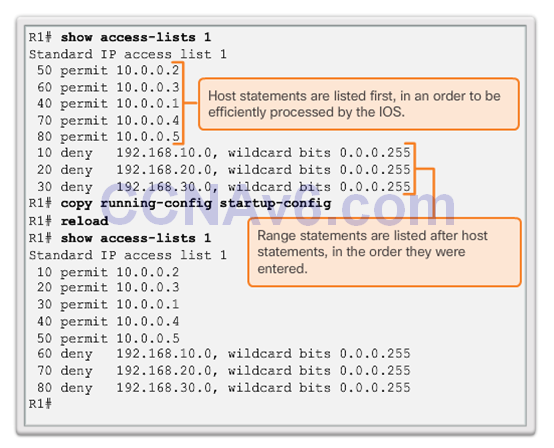
Routing Processes and ACLs
- As a frame enters an interface, the router checks to see whether the destination Layer 2 address matches its interface Layer 2 address, or whether the frame is a broadcast frame.
- If the frame address is accepted, the frame information is stripped off and the router checks for an ACL on the inbound interface.
- If an ACL exists, the packet is tested against the statements in the list.
- If the packet matches a statement, the packet is either permitted or denied.
- If the packet is accepted, it is then checked against routing table entries to determine the destination interface.
- If a routing table entry exists for the destination, the packet is then switched to the outgoing interface, otherwise the packet is dropped.
- Next, the router checks whether the outgoing interface has an ACL. If an ACL exists, the packet is tested against the statements in the list. If the packet matches a statement, it is either permitted or denied.
- If there is no ACL or the packet is permitted, the packet is encapsulated in the new Layer 2 protocol and forwarded out the interface to the next device.
7.3.2 Common Standard IPv4 ACL Errors
Troubleshooting Standard IPv4 ACLs – Example 1
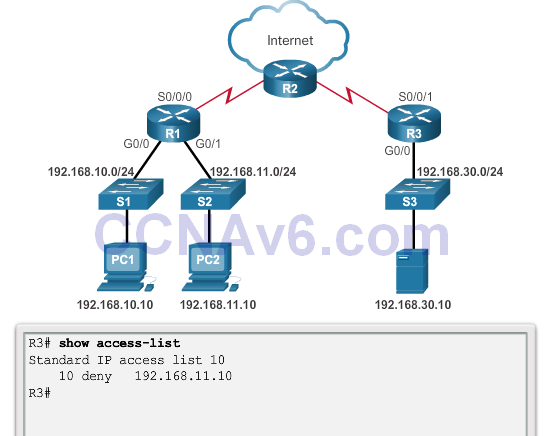
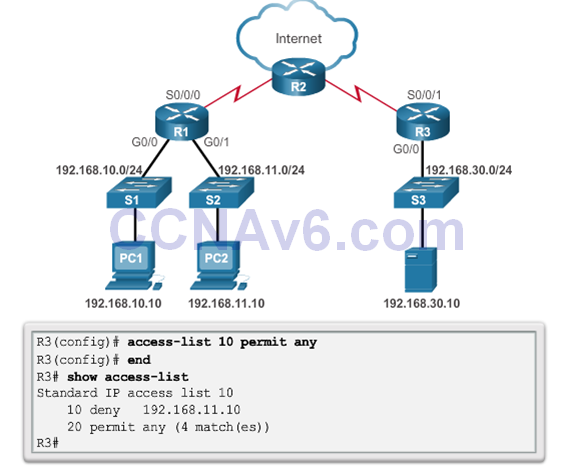
Troubleshooting Standard IPv4 ACLs – Example 2
- Security Policy: The 192.168.11.0/24 network should not be able to access the 192.168.10.0/24 network.
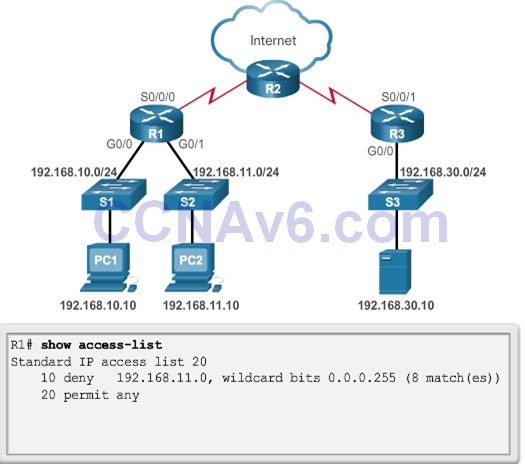
- ACL 20 was applied to the wrong interface and in the wrong direction. All traffic from the 192.168.11.0/24 is denied inbound access through the G0/1 interface.
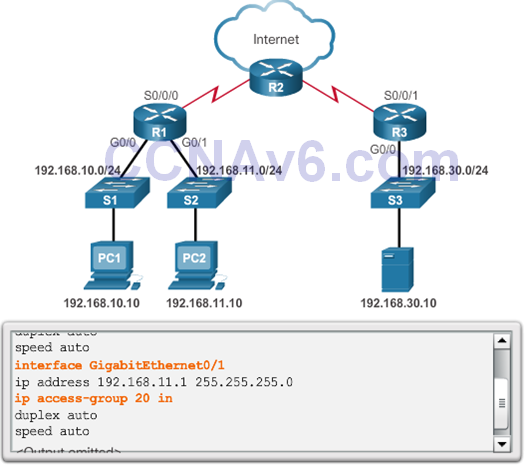
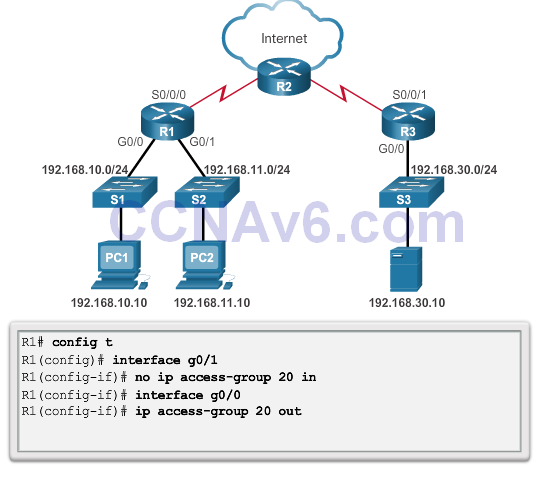
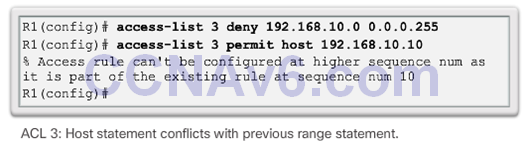
Troubleshooting Standard IPv4 ACLs – Example 3
- Problem
- Security Policy: Only PC1 is allowed SSH remote access to R1.
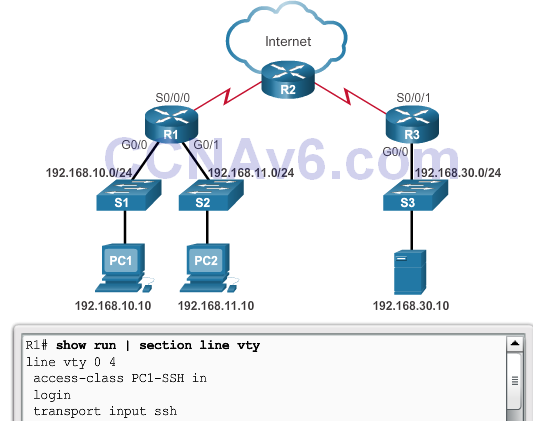

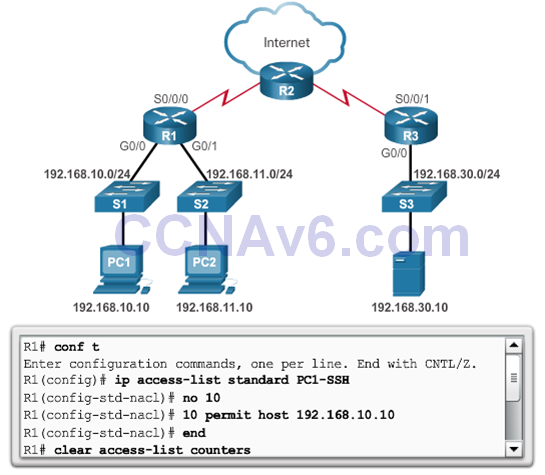
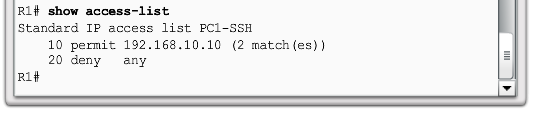
- Solution!
- Security Policy: Only PC1 is allowed SSH remote access to R1.
7.4 Summary
- Explain how ACLs filter traffic.
- Explain how ACLs use wildcard masks.
- Explain how to create ACLs.
- Explain how to place ACLs.
- Configure standard IPv4 ACLs to filter traffic to meet networking requirements.
- Use sequence numbers to edit existing standard IPv4 ACLs.
- Configure a standard ACL to secure vty access.
- Explain how a router processes packets when an ACL is applied.
- Troubleshoot common standard IPv4 ACL errors using CLI commands.
Section 7.1
Terms and Commands
- Access list (ACL)
- Packet filtering
- Access control entries (ACEs)
- Standard ACLs
- Extended ACLs
- Inbound ACLs
- Outbound ACLs
- Wildcard masking
- Wildcard mask bit 0
- Wildcard mask bit 1
- access-list access-list-number permit ip_address wildcard_mask
- host
- any
Section 7.2
Terms and Commands
- access-list access-list-number{ deny | permit | remark }source[ source-wildcard ][ log ]
- show access-lists
- no access-list access-list-number
- ip access-group {access-list-number| access-list-name} { in | out }
- ip access-list standardname
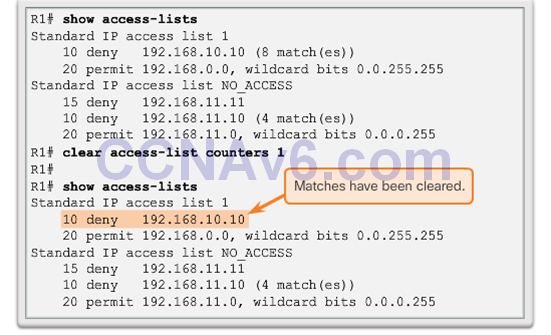
- clear access-list counters
- access-class access-list-number { in |out }
Download Slide PowerPoint (pptx):
