Time limit: 0
Quiz-summary
0 of 30 questions completed
Questions:
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
Information
Good luck!
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading...
You must sign in or sign up to start the quiz.
You have to finish following quiz, to start this quiz:
Results
0 of 30 questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 points, (0)
| Average score |
|
| Your score |
|
Categories
- Not categorized 0%
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- Answered
- Review
-
Question 1 of 30
1. Question
1 pointsWhat are two expected features of modern enterprise networks? (Choose two.)Correct
Incorrect
Hint
All modern enterprise networks are expected to support critical applications, converged network traffic, diverse business needs, and provide centralized administrative control. Users expect enterprise networks to be up 99.999 percent of the time (not 90 percent.). Support for limited growth is not a usual network design criterion. -
Question 2 of 30
2. Question
1 pointsWhich type of information is displayed by the show ip protocols command that is issued from a router command prompt?Correct
Incorrect
Hint
The show ip protocols command displays information about the routing protocols that are configured, the networks the router is advertising, and the default administrative distance. The show interfaces command displays interfaces with line (protocol) status, bandwidth, delay, reliability, encapsulation, duplex, and I/O statistics. The show ip interfaces command displays interface information, including protocol status, the IP address, whether a helper address is configured, and whether an ACL is enabled on the interface. The show protocols command displays information about the routed protocol that is enabled and the protocol status of interfaces. -
Question 3 of 30
3. Question
1 pointsWhich action should be taken when planning for redundancy on a hierarchical network design?Correct
Incorrect
Hint
One method of implementing redundancy is path redundancy, installing alternate physical paths for data to traverse the network. Redundant links in a switched network supports high availability and can be used for load balancing, reducing congestion on the network. -
Question 4 of 30
4. Question
1 pointsRefer to the exhibit. Which devices exist in the failure domain when switch S3 loses power?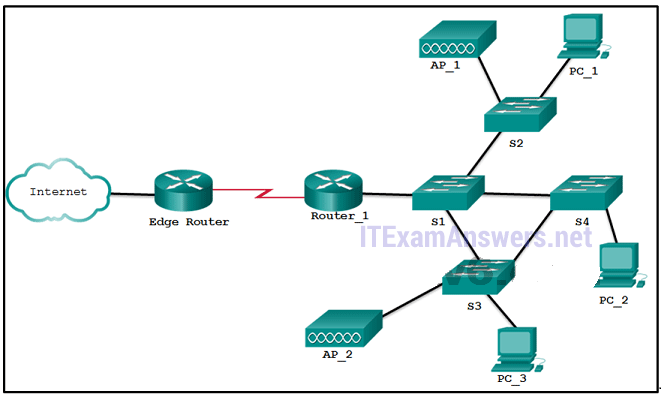 Correct
Correct
Incorrect
Hint
A failure domain is the area of a network that is impacted when a critical device such as switch S3 has a failure or experiences problems. -
Question 5 of 30
5. Question
1 pointsWhich design feature will limit the size of a failure domain in an enterprise network?Correct
Incorrect
Hint
In order to best limit the of a failure domain, routers or multilayer switches can be deployed in pairs. The failure of a single device should not cause the network to go down. Installing redundant power supplies may protect a single device from a power failure, but if that device suffers from another type of problem, a redundant device would have been a better solution. Purchasing enterprise equipment that handles large flows of traffic will not provide extra reliability in times of an outage. If a collapsed core design is used, the core and distribution are collapsed into a single device, increasing the chance of a devastating outage. -
Question 6 of 30
6. Question
1 pointsA network administrator is planning redundant devices and cabling in a switched network to support high availability. Which benefit will implementing the Spanning Tree Protocol provide to this design?Correct
Incorrect
Hint
With the implementation of redundant devices and links, redundant paths will exist in the network. This may cause a Layer 2 loop, and Spanning Tree Protocol (STP) is used to eliminate switching loops while maintaining reliability. STP is not required to combine multiple physical interfaces into a single EtherChannel interface. STP does not provide faster convergence or an expanded network that uses wired or wireless connectivity. -
Question 7 of 30
7. Question
1 pointsWhat are two benefits of extending access layer connectivity to users through a wireless medium? (Choose two.)Correct
Incorrect
Hint
Wireless connectivity at the access layer provides increased flexibility, reduced costs, and the ability to grow and adapt to changing business requirements. Utilizing wireless routers and access points can provide an increase in the number of central points of failure. Wireless routers and access points will not provide an increase in bandwidth availability. -
Question 8 of 30
8. Question
1 pointsWhich two features of enterprise class equipment assists an enterprise network in maintaining 99.999 percent up-time? (Choose two.)Correct
Incorrect
Hint
Enterprise class equipment is designed with features such as redundant power supplies and failover capabilities. A failure domain is an area of a network that is impacted when a critical device fails. A collapsed core is a two-tier hierarchical design where the core and distribution layers are collapsed into a single layer. This reduces cost and complexity but does not provide redundancy and uptime. -
Question 9 of 30
9. Question
1 pointsA network technician needs to connect a PC to a Cisco network device for initial configuration. What is required to perform this device configuration?Correct
Incorrect
Hint
Because the device needs to be initially configured, a network connection is unavailable yet on this device, hence the need for an out-of-band management method. A configuration that uses out-of-band management requires a direct connection to a console or AUX port, and a terminal emulation client. -
Question 10 of 30
10. Question
1 pointsWhat network design would contain the scope of disruptions on a network should a failure occur?Correct
Incorrect
Hint
One way to contain the impact of a failure on the network is to implement redundancy. One way this is accomplished is by deploying redundant distribution layer switches and dividing the access layer switch connections between the redundant distribution layer switches. This creates what is called a switch block. Failures in a switch block are contained to that block and do not bring down the whole network. -
Question 11 of 30
11. Question
1 pointsWhat are three access layer switch features that are considered when designing a network? (Choose three.)Correct
Incorrect
Hint
The port density of a switch (the number of ports available on a single switch), forwarding rate (how much data the switch can process per second), and Power over Ethernet (the ability of the switch to deliver power to a device over the existing Ethernet cabling) are access layer switch features to be considered when designing a network. Failover capability, speed of convergence, and broadcast traffic containment are distribution layer features. -
Question 12 of 30
12. Question
1 pointsWhat are two functions of a router? (Choose two.)Correct
Incorrect
Hint
Routers connect multiple networks in an organization to provide interconnections among them. They perform the task by using the network portion of the destination IP address to determine the best path to send packets to their destination. -
Question 13 of 30
13. Question
1 pointsWhat capability is provided by the use of application-specific integrated circuits in Cisco multilayer switches?Correct
Incorrect
Hint
Application-specific integrated circuits (ASICs) increase the forwarding speed of a switch by allowing packets to bypass the CPU for processing. -
Question 14 of 30
14. Question
1 pointsWhich statement describes a characteristic of Cisco Meraki switches?Correct
Incorrect
Hint
The Cisco Meraki cloud-managed access switches enable virtual stacking of switches. They monitor and configure thousands of switch ports over the web, without the intervention of onsite IT staff. -
Question 15 of 30
15. Question
1 pointsA network engineer is reviewing a network design that uses a fixed configuration enterprise router that supports both LAN and WAN connections. However, the engineer realizes that the router does not have enough interfaces to support growth and network expansion. Which type of device should be used as a replacement?Correct
Incorrect
Hint
Modular routers provide multiple slots that allow a network designer to change or increase the interfaces that exist on the router. A Layer 3 switch may increase the number of ports available on a router, but will not provide WAN connectivity. The PoE capability of a device is not related to the number of ports it has. Using another fixed configuration router will not provide the flexibility to adapt to future growth that using a modular router will provide. -
Question 16 of 30
16. Question
1 pointsIn which situation would a network administrator install a Cisco Nexus Series or Cisco Catalyst 6500 Series switch to promote infrastructure scalability?Correct
Incorrect
Hint
Cisco Nexus Series switches are employed on data centers to promote infrastructure scalability, operational continuity, and transport flexibility. They also provide secure multitenant services by adding virtualization intelligence technology to the data center network. -
Question 17 of 30
17. Question
1 pointsWhich statement describes a characteristic of Cisco Catalyst 2960 switches?Correct
Incorrect
Hint
Cisco Catalyst 2960 switches support one active switched virtual interface (SVI) with IOS versions prior to 15.x. They are commonly used as access layer switches and they are fixed configuration switches. -
Question 18 of 30
18. Question
1 pointsRefer to the exhibit. Which command was issued on a Cisco switch that resulted in the exhibited output?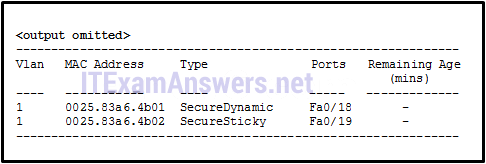 Correct
Correct
Incorrect
Hint
The show port-security address command displays all secure MAC addresses configured on all switch interfaces. The show mac-address-table command displays all MAC addresses that the switch has learned, how those addresses were learned (dynamic/static), the port number, and the VLAN assigned to the port. The show vlan brief command displays the available VLANs and the ports assigned to each VLAN. The show vlan summary command displays the count of all configured VLANs. -
Question 19 of 30
19. Question
1 pointsWhat is a characteristic of in-band device management?Correct
Incorrect
Hint
In-band device management is used to monitor and make configuration changes to a network device over a network connection. Configuration using in-band management requires at least one network interface on the device to be connected and to be operational, and it requires the use of Telnet, SSH, or HTTP to access the device. -
Question 20 of 30
20. Question
1 pointsWhich two requirements must always be met to use in-band management to configure a network device? (Choose two.)Correct
Incorrect
Hint
Direct connections to the console and auxiliary ports allow for out-of-band management. Terminal emulation software is not always required because in-band management can be performed using a browser. -
Question 21 of 30
21. Question
1 pointsWhen a Cisco IOS device is being selected or upgraded, which option indicates the capabilities of the Cisco IOS device?Correct
Incorrect
Hint
The version number and release number refer to the overall device operating system. The platform refers to the specific model of a device. The feature set determines what a particular device is capable of. -
Question 22 of 30
22. Question
1 pointsImmediately after a router completes its boot sequence, the network administrator wants to check the routers configuration. From privileged EXEC mode, which of the following commands can the administrator use for this purpose? (Choose two.)Correct
Incorrect
Hint
The show startup-config command can be used to display the Cisco device configuration stored in NVRAM. The show running-config command can be used to display the currently active configuration that is stored in RAM. The show flash command displays the files (not file content) stored in the flash memory. -
Question 23 of 30
23. Question
1 pointsQuestion as presented: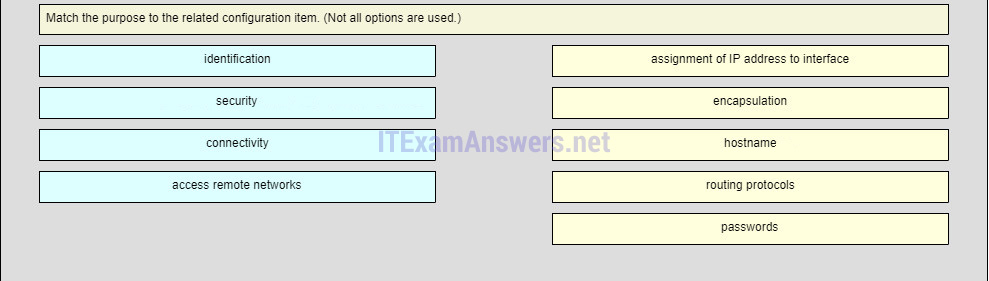
Sort elements
- host name
- passwords
- assignment of IP address to interface
- routing protocol
- encapsulation
-
identification
-
security
-
connectivity
-
access remove networks
Correct
Incorrect
-
Question 24 of 30
24. Question
1 pointsIn the Cisco Enterprise Architecture, which two functional parts of the network are combined to form a collapsed core design? (Choose two.)Correct
Incorrect
-
Question 25 of 30
25. Question
1 pointsWhat are two ways to access a Cisco switch for out-of-band management? (Choose two.)Correct
Incorrect
-
Question 26 of 30
26. Question
1 pointsHow can an enterprise network be designed to optimize bandwidth?Correct
Incorrect
-
Question 27 of 30
27. Question
1 pointsAs the network administrator you have been asked to implement EtherChannel on the corporate network. What does this configuration consist of?Correct
Incorrect
-
Question 28 of 30
28. Question
1 pointsWhat term is used to express the thickness or height of a switch?Correct
Incorrect
-
Question 29 of 30
29. Question
1 pointsWhat is the function of ASICs in a multilayer switch?Correct
Incorrect
-
Question 30 of 30
30. Question
1 pointsWhat is the function of PoE pass-through?Correct
Incorrect

What are two expected features of modern enterprise networks? (Choose two.)
support for converged network traffic* growth
support for critical applications
why is these wrong ? do u can revision ?
thank you, i have edited it.