Category: CCNA Security v2.0 Answers
CCNA Security v2.0 Answers 2015 2016 PDF Download

CCNA Security v2.0 Final Test Online Exam Answers
CCNA Security v2.0 Final Exam Answers 100%
Implementing Network Security (Version 2.0) – CCNAS Final Exam Answers Full 100% Scored 1. Which security implementation will provide control plane protection for a network device? encryption for remote access connections AAA for authenticating management access routing protocol authentication NTP for consistent timestamps on logging messages 2. What …
CCNA Security v2.0 Chapter 11 Exam Answers
1. Which security test is appropriate for detecting system weaknesses such as misconfiguration, default passwords, and potential DoS targets? vulnerability scanning* network scanning integrity checkers penetration testing 2. How does network scanning help assess operations security? It can simulate attacks from malicious sources. It can log abnormal activity. …
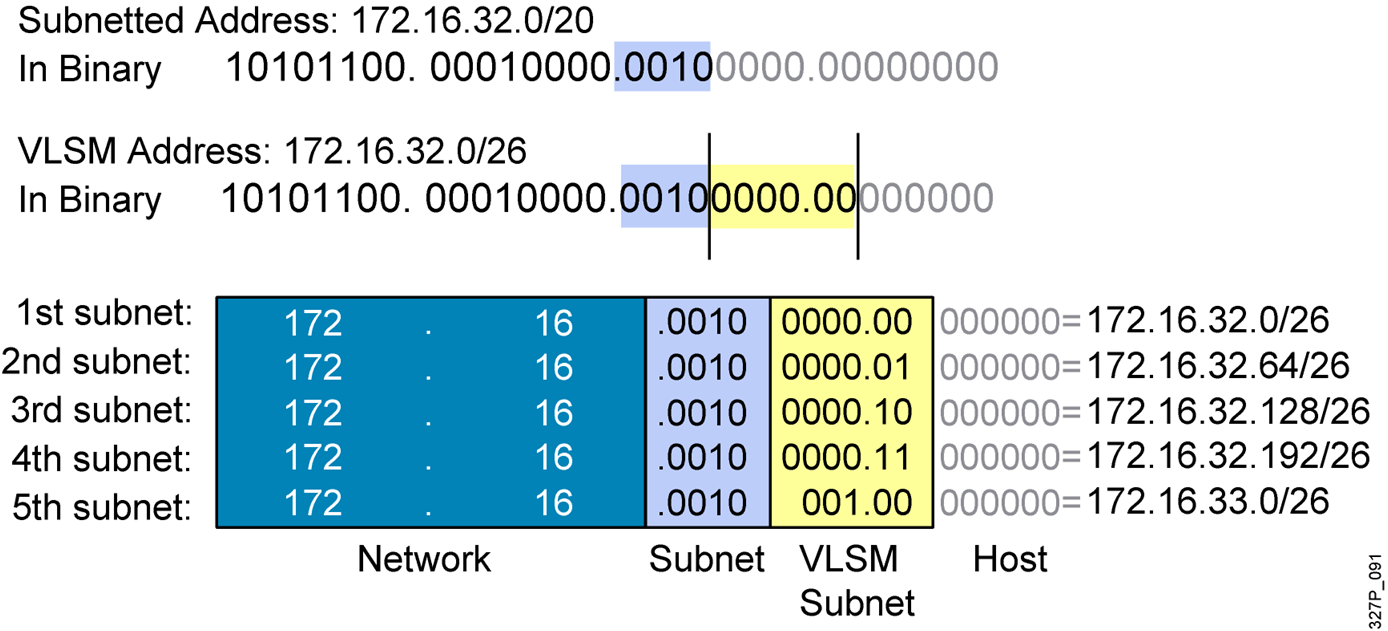
CCNA Security v2.0 Chapter 10 Exam Answers
1. Which ASDM configuration option is used to configure the ASA enable secret password? Device Setup* Monitoring Interfaces Device Management 2. Refer to the exhibit. Which Device Setup ASDM menu option would be used to configure the ASA for an NTP server? Startup Wizard Device Name/Password Routing Interfaces …
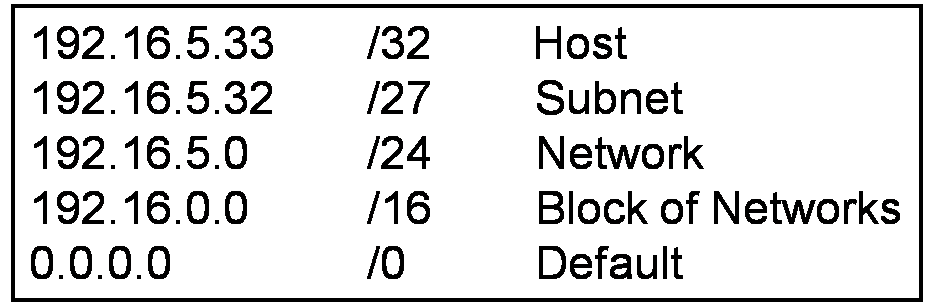
CCNA Security v2.0 Chapter 9 Exam Answers
1. Refer to the exhibit. A network administrator is configuring the security level for the ASA. What is a best practice for assigning the security level on the three interfaces? Outside 40, Inside 100, DMZ 0 Outside 0, Inside 35, DMZ 90 Outside 100, Inside 10, DMZ 40 …

CCNA Security v2.0 Chapter 8 Exam Answers
1. When is a security association (SA) created if an IPsec VPN tunnel is used to connect between two sites? after the tunnel is created, but before traffic is sent only during Phase 2 only during Phase 1 during both Phase 1 and 2* 2. In which situation …
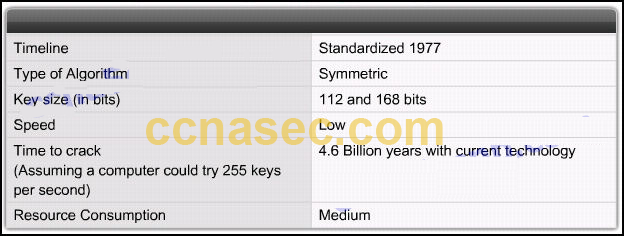
CCNA Security v2.0 Chapter 7 Exam Answers
1. What is the purpose of a nonrepudiation service in secure communications? to ensure that encrypted secure communications cannot be decoded to confirm the identity of the recipient of the communications to provide the highest encryption level possible to ensure that the source of the communications is confirmed* …
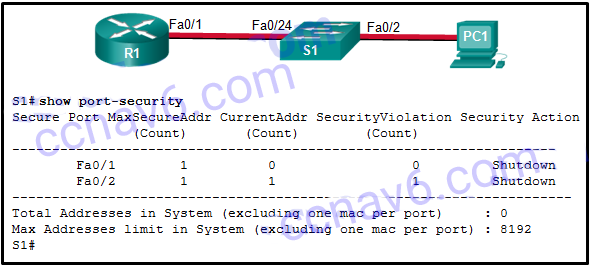
CCNA Security v2.0 Chapter 6 Exam Answers
1. Which type of VLAN-hopping attack may be prevented by designating an unused VLAN as the native VLAN? DTP spoofing DHCP spoofing VLAN double-tagging* DHCP starvation 2. What component of Cisco NAC is responsible for performing deep inspection of device security profiles? Cisco NAC Profiler Cisco NAC Agent* …

CCNA Security v2.0 Chapter 5 Exam Answers
1. In configuring a Cisco router to prepare for IPS and VPN features, a network administrator opens the file realm-cisco.pub.key.txt, and copies and pastes the contents to the router at the global configuration prompt. What is the result after this configuration step? The router is authenticated with the …
