8.0 Introduction
8.0.1 Welcome
8.0.1.1 Chapter 8: Implementing Virtual Private Networks
Designing, implementing and managing an effective IP addressing plan ensures that networks can operate effectively and efficiently. This is especially true as the number of host connections to a network increases. Understanding the hierarchical structure of the IP address and how to modify that hierarchy in order to more efficiently meet routing requirements is an important part of planning an IP addressing scheme.
In the original IPv4 address, there are two levels of hierarchy: a network and a host. These two levels of addressing allow for basic network groupings that facilitate in routing packets to a destination network. A router forwards packets based on the network portion of an IP address. When the network is located, the host portion of the address allows for identification of the destination device.
However, as networks grow, with many organizations adding hundreds, and even thousands of hosts to their network, the two-level hierarchy is insufficient.
Subdividing a network adds a level to the network hierarchy, creating, in essence, three levels: a network, a subnetwork, and a host. Introducing an additional level to the hierarchy creates additional sub-groups within an IP network that facilitates faster packet delivery and added filtration, by helping to minimize ‘local’ traffic.
This chapter examines, in detail, the creation and assignment of IP network and subnetwork addresses through the use of the subnet mask.
8.1 VPNs
8.1.1 VPN Overview
8.1.1.1 Introducing VPNs
Broadcast Domains
In an Ethernet LAN, devices use broadcasts to locate:
- Other devices – A device uses Address Resolution Protocol (ARP) which sends Layer 2 broadcasts to a known IPv4 address on the local network to discover the associated MAC address.
- Services – A host typically acquires its IPv4 address configuration using the Dynamic Host Configuration Protocol (DHCP) which sends broadcasts on the local network to locate a DHCP server.
Switches propagate broadcasts out all interfaces except the interface on which it was received. For example, if a switch in the figure were to receive a broadcast, it would forward it to the other switches and other users connected in the network.
Routers do not propagate broadcasts. When a router receives a broadcast, it does not forward it out other interfaces. For instance, when R1 receives a broadcast on its Gigabit Ethernet 0/0 interface, it does not forward out another interface.
Therefore, each router interface connects a broadcast domain and broadcasts are only propagated within its specific broadcast domain.
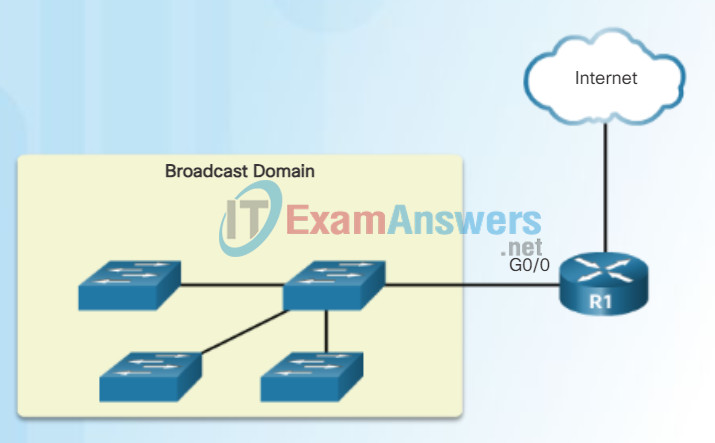
An Interface Connects a Broadcast Domain
8.1.1.2 Layer 3 IPsec VPNs
Problems with Large Broadcast Domains
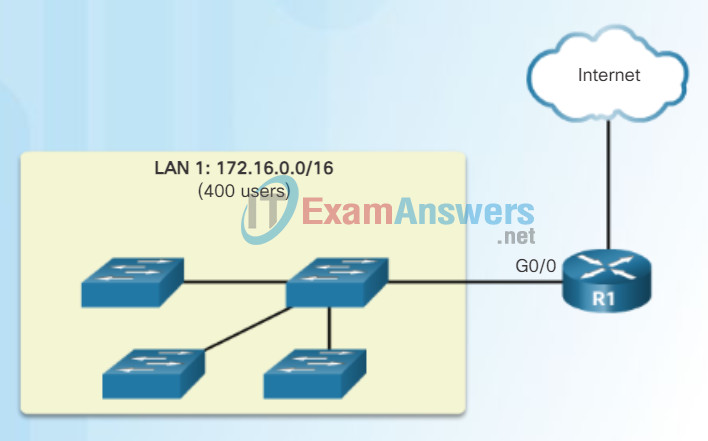
A Large Broadcast Domain
A large broadcast domain is a network that connects many hosts. A problem with a large broadcast domain is that these hosts can generate excessive broadcasts and negatively affect the network. In Figure 1, LAN 1 connects 400 users that could generate broadcast traffic resulting in:
- Slow network operations due to the significant amount of traffic it can cause
- Slow device operations because a device must accept and process each broadcast packet
The solution is to reduce the size of the network to create smaller broadcast domains in a process called subnetting. These smaller network spaces are called subnets.
In Figure 2 for example, the 400 users in LAN 1 with network address 172.16.0.0 /16 have been divided into two subnets of 200 users each; 172.16.0.0 /24 and 172.16.1.0 /24. Broadcasts are only propagated within the smaller broadcast domains. Therefore a broadcast in LAN 1 would not propagate to LAN 2.
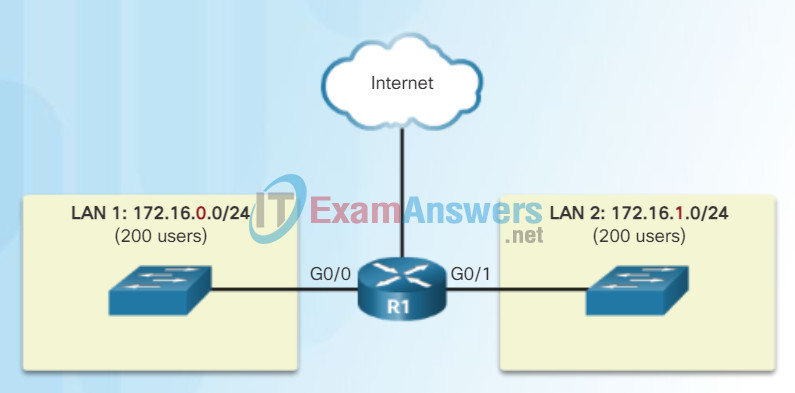
Communicating between Networks
Notice how the prefix length has changed from a /16 to a /24. This is the basis of subnetting; using host bits to create additional subnets.
Note: The terms subnet and network are often used interchangeably. Most networks are a subnet of some larger address block.
8.1.2 VPN Topologies
8.1.2.1 Two Types of VPNs
Octet Boundaries
Every interface on a router is connected to a network. The IPv4 address and subnet mask configured on the router interface are used to identify the specific broadcast domain. Recall that the prefix length and the subnet mask are different ways of identifying the network portion of an address.
IPv4 subnets are created by using one or more of the host bits as network bits. This is done by extending the subnet mask to borrow some of the bits from the host portion of the address to create additional network bits. The more host bits that are borrowed, the more subnets that can be defined.
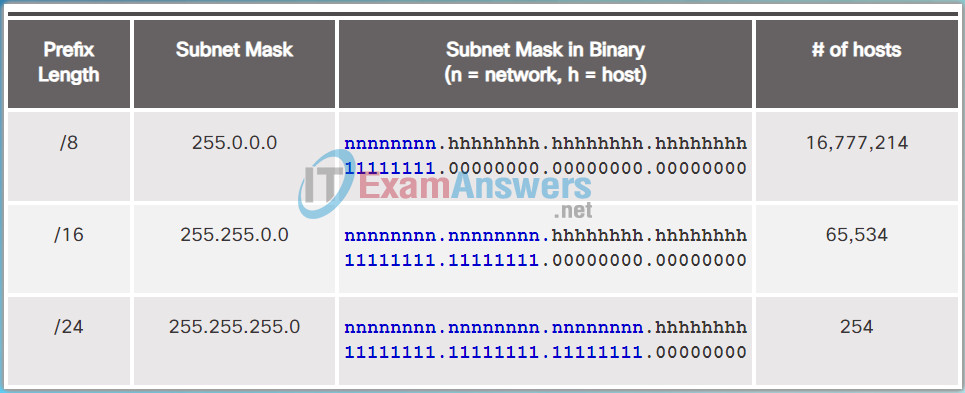
Subnetting Networks on the Octet Boundary
Networks are most easily subnetted at the octet boundary of /8, /16, and /24. The table in the figure identifies these prefix lengths, equivalent subnet masks, the network and host bits, and the number of hosts each subnet can connect. Notice that using longer prefix lengths decreases the number of hosts per subnet.
8.1.2.2 Components of Remote-Access VPNs
Subnetting on the Octet Boundary
To understand how subnetting on the octet boundary can be useful, consider the following example. Assume an enterprise has chosen the private address 10.0.0.0/8 as its internal network address. That network address can connect 16,777,214 hosts in one broadcast domain. Obviously, this is not ideal.
The enterprise could further subnet the 10.0.0.0/8 address at the octet boundary of /16 as shown in Figure 1. This would provide the enterprise the ability to define up to 256 subnets (i.e., 10.0.0.0/16 – 10.255.0.0/16) with each subnet capable of connecting 65,534 hosts. Notice how the first two octets identify the network portion of the address while the last two octets are for host IP addresses.
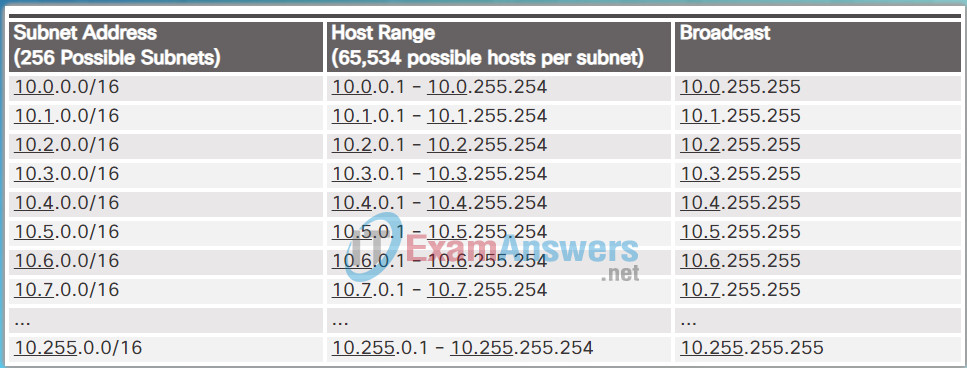
Subnetting Network 10.x.0.0/16
Alternatively, the enterprise could choose to subnet at the /24 octet boundary as shown in Figure 2. This would enable the enterprise to define 65,536 subnets each capable of connecting 254 hosts. The /24 boundary is very popular in subnetting because it accommodates a reasonable number of hosts and conveniently subnets at the octet boundary.
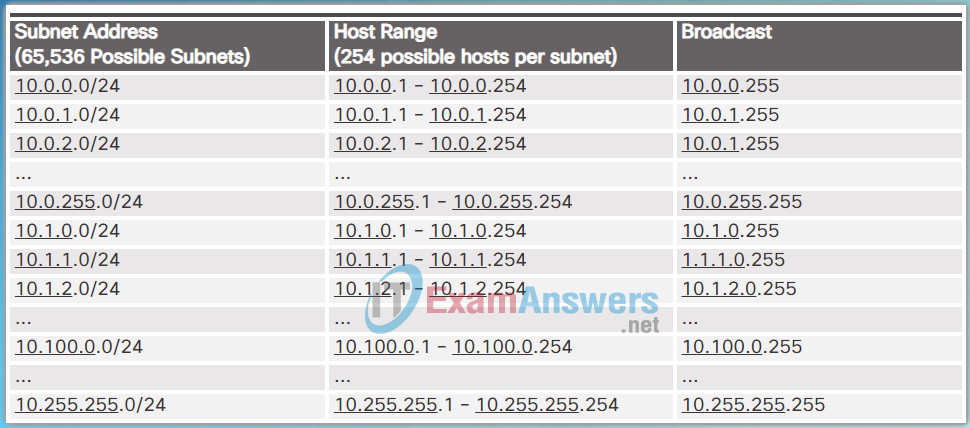
Subnetting Network 10.x.x.0/24
8.1.2.3 Components of Site-to-Site VPNs
The examples seen so far borrowed host bits from the common /8, /16, and /24 network prefixes. However, subnets can borrow bits from any host bit position to create other masks.
For instance, a /24 network address is commonly subnetted using longer prefix lengths by borrowing bits from the fourth octet. This provides the administrator with additional flexibility when assigning network addresses to a smaller number of end devices.
As shown in the figure:
- /25 row – Borrowing 1 bit from the fourth octet creates 2 subnets supporting 126 hosts each.
- /26 row – Borrowing 2 bits creates 4 subnets supporting 62 hosts each.
- /27 row – Borrowing 3 bits creates 8 subnets supporting 30 hosts each.
- /28 row – Borrowing 4 bits creates 16 subnets supporting 14 hosts each.
- /29 row – Borrowing 5 bits creates 32 subnets supporting 6 hosts each.
- /30 row – Borrowing 6 bits creates 64 subnets supporting 2 hosts each.
For each bit borrowed in the fourth octet, the number of subnetworks available is doubled while reducing the number of host addresses per subnet.
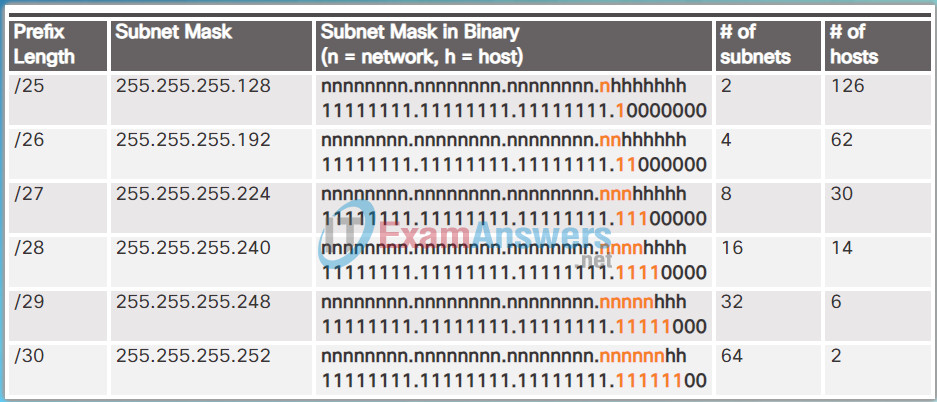
Subnetting a /24 Network
8.1.2.4 Activity – Compare Remote-Access and Site-to-Site VPN
8.1.2.5 Hairpinning and Split Tunneling
8.2 IPsec VPN Components and Operation
8.2.1 Introducing IPsec
8.2.1.1 IPsec Technologies
Network Address Planning
As shown in the figure, the allocation of network layer address space within the corporate network needs to be well designed. Address assignment should not be random.
Planning network subnets requires examination of both the needs of an organization’s network usage, and how the subnets will be structured. Performing a network requirement study is the starting point. This means looking at the entire network and determining the main sections of the network and how they will be segmented. The address plan includes determining the needs of each subnet in terms of size, how many hosts per subnet, how host addresses will be assigned, which hosts will require static IPv4 addresses, and which hosts can use DHCP for obtaining their addressing information.
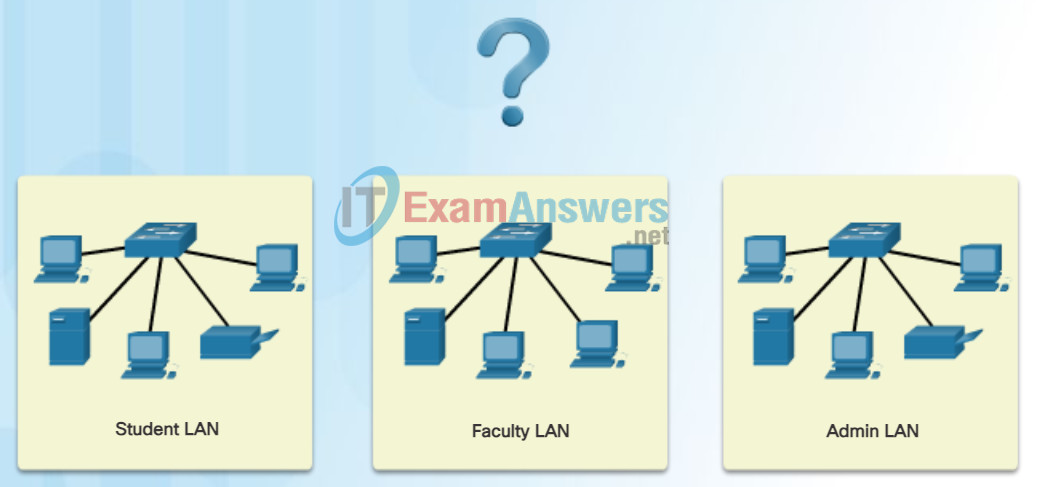
The size of the subnet involves planning the number of hosts that will require IPv4 host addresses in each subnet of the subdivided private network. For example, in a campus network design, you might consider how many hosts are needed in the Administrative LAN, how many in the Faculty LAN, and how many in the Student LAN. In a home network, a consideration might be done by the number of hosts in the Main House LAN and the number of hosts in the Home Office LAN.
As discussed earlier, the private IPv4 address range used on a LAN is the choice of the network administrator and needs careful consideration to be sure that enough host addresses will be available for the currently known hosts and for future expansion. Remember the private IPv4 address ranges are:
- 10.0.0.0 – 10.255.255.255 with a subnet mask of 255.0.0.0 or /8
- 172.16.0.0 – 172.31.255.255 with a subnet mask of 255.240.0.0 or /12
- 192.168.0.0 – 192.168.255.255 with a subnet mask of 255.255.0.0 or /16
Knowing your IPv4 address requirements will determine the range or ranges of host addresses you implement. Subnetting the selected private IPv4 address space will provide the host addresses to cover your network needs.
Public addresses used to connect to the Internet are typically allocated from a service provider. So, while the same principles for subnetting would apply, this is not generally the responsibility of the organization’s network administrator.
Planning IP Address Assignment
Planning requires decisions on each subnet in terms of size, the number of hosts per subnet, and how host addresses will be assigned.
8.2.1.2 Confidentiality
Planning to Address the Network
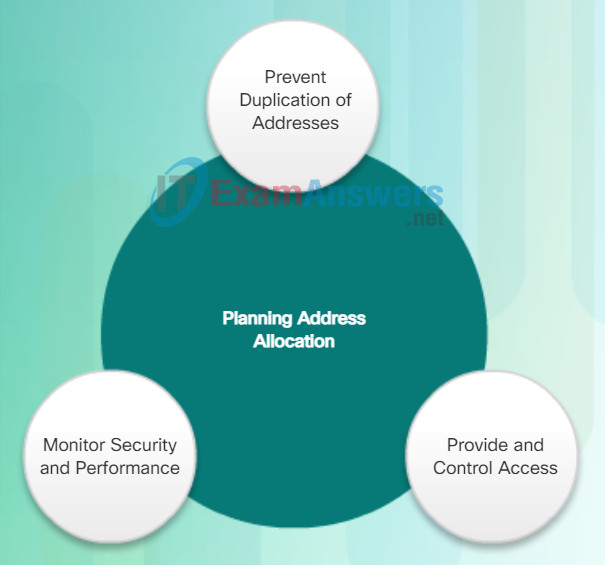
Three primary considerations for planning address allocation are displayed in the figure.
Preventing the duplication of addresses refers to the fact that each host in an internetwork must have a unique address. Without the proper planning and documentation, an address could be assigned to more than one host, resulting in access issues for both hosts.
Providing and controlling access refers to the fact that some hosts, such as servers, provide resources to internal hosts as well as to external hosts. The Layer 3 address assigned to a server can be used to control access to that server. If, however, the address is randomly assigned and not well documented, controlling access is more difficult.
Monitoring security and performance of hosts means network traffic is examined for source IP addresses that are generating or receiving excessive packets. If there is proper planning and documentation of the network addressing, problematic network devices should easily be found.
Primary Considerations when Planning Address Allocations
8.2.1.3 Integrity
Assigning Addresses to Devices
Within a network, there are different types of devices that require addresses, including:
- End user clients – Most networks allocate addresses dynamically using Dynamic Host Configuration Protocol (DHCP). This reduces the burden on network support staff and virtually eliminates entry errors. As well, addresses are only leased for a period of time. Changing the subnetting scheme means that the DHCP server needs to be reconfigured, and the clients must renew their IP addresses. IPv6 clients can obtain address information using DHCPv6 or SLAAC.
- Servers and peripherals – These should have a predictable static IP address. Use a consistent numbering system for these devices.
- Servers that are accessible from the Internet – In many networks, servers must be made available to the remote users. In most cases, these servers are assigned private addresses internally, and the router or firewall at the perimeter of the network must be configured to translate the internal address into a public address.
- Intermediary devices – These devices are assigned addresses for network management, monitoring, and security. Because we must know how to communicate with intermediary devices, they should have predictable, statically assigned addresses.
- Gateway – Routers and firewall devices have an IP address assigned to each interface which serves as the gateway for the hosts in that network. Typically, the router interface uses either the lowest or highest address in the network.
The table in the figure provides a sample of address allocation for a small network.
When developing an IP addressing scheme, it is generally recommended to have a set pattern of how addresses are allocated to each type of device. This benefits administrators when adding and removing devices, filtering traffic based on IP, as well as simplifying documentation.

IP Address Ranges
8.2.1.4 Authentication
Packet Tracer – Designing and Implementing a VLSM Addressing Scheme
In this activity, you are given a /24 network address to use to design a VLSM addressing scheme. Based on a set of requirements, you will assign subnets and addressing, configure devices and verify connectivity.
8.2.1.5 Secure Key Exchange
Lab – Designing and Implementing a VLSM Addressing Scheme
In this lab, you will complete the following objectives:
- Part 1: Examine Network Requirements
- Part 2: Design the VLSM Address Scheme
- Part 3: Cable and Configure the IPv4 Network
8.2.1.6 Activity – Identify the Components of the IPsec Framework
8.2.2 IPsec Protocols
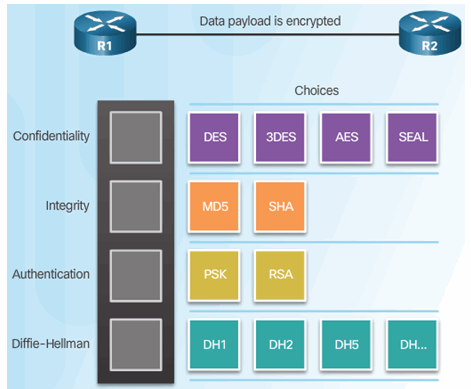
8.2.2.1 IPsec Protocol Overview
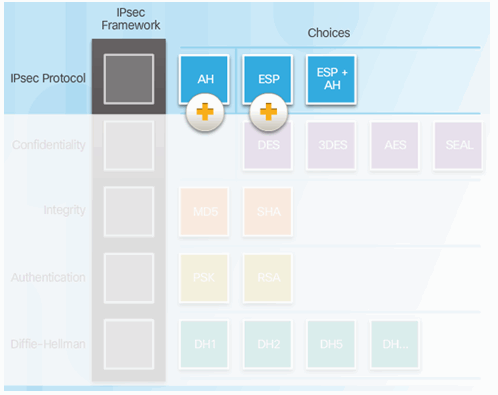
8.2.2.2 Authentication Header
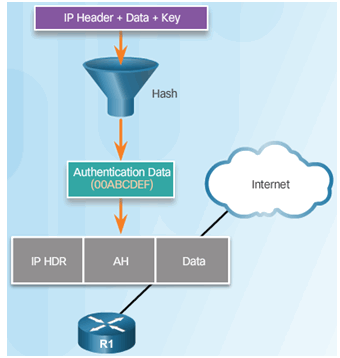
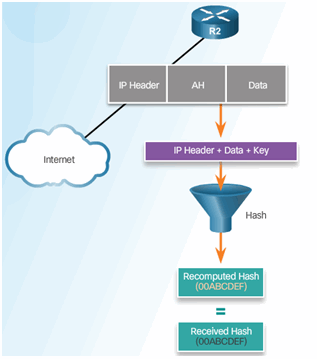
AH Protocols
Router Creates Hash and Transmits to Peer
Peer Router Compares Recomputed Hash to Received Hash
8.2.2.3 ESP
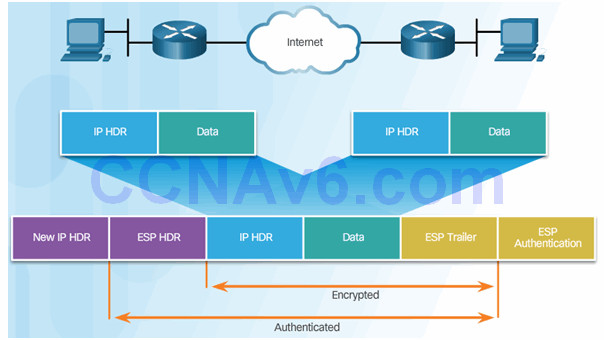
8.2.2.4 ESP Encrypts and Authenticates
8.2.2.5 Transport and Tunnel Modes
Apply ESP and AH in Two Modes
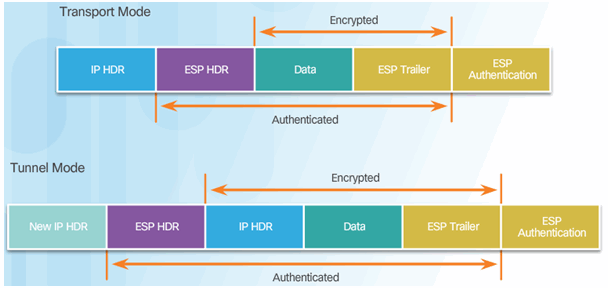
ESP Tunnel Mode
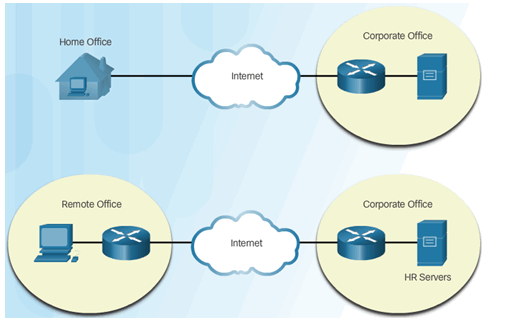
8.2.2.6 Activity – Compare AH and ESP
8.2.3 Internet Key Exchange
8.2.3.1 The IKE Protocol
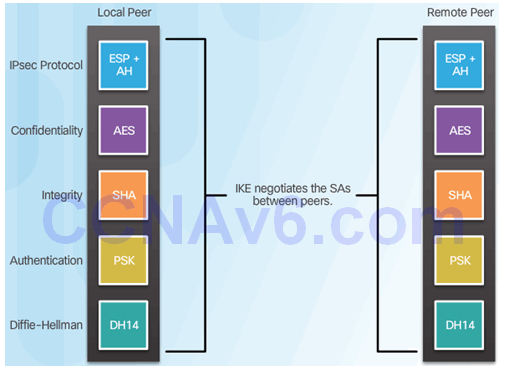
8.2.3.2 Phase 1 and 2 Key Negotiation
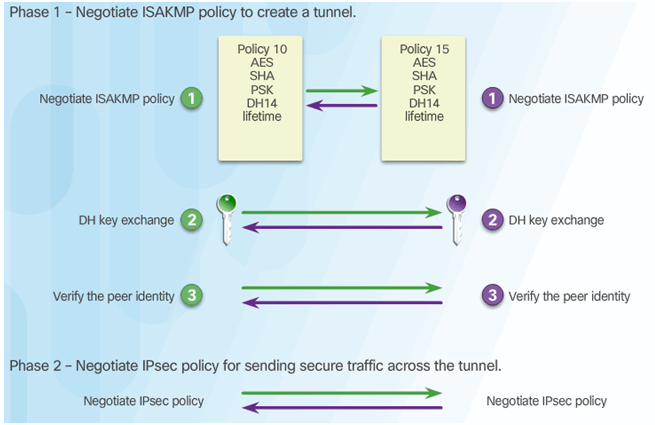
8.2.3.3 Phase 2: Negotiating SAs

8.2.3.4 Video Demonstration – IKE Phase 1 and Phase 2
8.3 Implementing Site-to-Site IPsec VPNs with CLI
8.3.1 Configuring a Site-to-Site IPsec VPN
8.3.1.1 IPsec Negotiation
The IPv6 Global Unicast Address
IPv6 subnetting requires a different approach than IPv4 subnetting. The same reasons for subnetting IPv4 address space in order to manage network traffic also apply to IPv6. However, due to the large number of IPv6 addresses, there is no longer the concern for conserving addresses. The IPv6 address plan can focus on the best hierarchical approach to manage and assign IPv6 subnets. Refer to the figure for a quick review of the structure of an IPv6 global unicast address.
IPv4 subnetting is not only about limiting broadcast domains but is also about managing address scarcity. Determining the subnet mask and the use of VLSM is done to help conserve IPv4 addresses. IPv6 subnetting is not concerned with conserving address space. The subnet ID includes more than enough subnets. IPv6 subnetting is about building an addressing hierarchy based on the number of subnetworks needed.
Recall that there are two types of assignable IPv6 addresses. An IPv6 link-local address is never subnetted because it exists only on the local link. However, an IPv6 global unicast address can be subnetted.
The IPv6 global unicast address normally consists of a /48 global routing prefix, a 16 bit subnet ID, and a 64 bit interface ID.
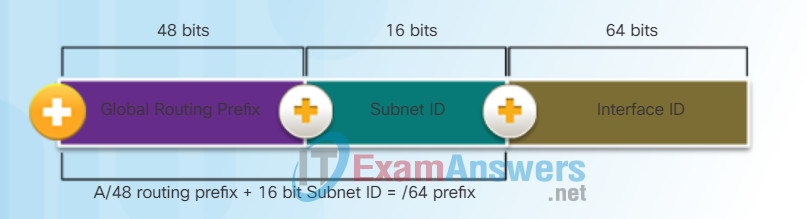
- Global Routing Prefix: This is the prefix, or network, portion of the address that is assigned by the provider. Typically, Regional Internet Registries (RIRs) assign a /48 global routing prefix to ISPs and customers.
- Subnet ID: Used by an organization to identify subnets within its site.
- Interface ID: This is the equivalent to the host portion of an IPv4 address. The term Interface ID is used because a single host may have multiple interfaces, each having one or more IPv6 addresses.
8.3.1.2 Site-to-Site IPsec VPN Topology
Subnetting Using the Subnet ID
The 16 bit subnet ID section of the IPv6 global unicast address can be used by an organization to create internal subnets.
The subnet ID provides more than enough subnets and host support than will ever be needed in one subnet. For instance, the 16 bit section can:
- Create up to 65,536 /64 subnets. This does not include the possibility of borrowing any bits from the interface ID of the address.
- Support up to 18 quintillion host IPv6 addresses per subnet (i.e., 18,000,000,000,000,000,000).
Note: Subnetting into the 64 bit Interface ID (or host portion) is also possible but it is rarely required.
IPv6 subnetting is also easier to implement than IPv4, because there is no conversion to binary required. To determine the next available subnet, just count up in hexadecimal.
For example, assume an organization has been assigned the 2001:0DB8:ACAD::/48 global routing prefix with a 16 bit subnet ID. This would allow the organization to create /64 subnets, as shown in the figure. Notice how the global routing prefix is the same for all subnets. Only the subnet ID hextet is incremented in hexadecimal for each subnet.
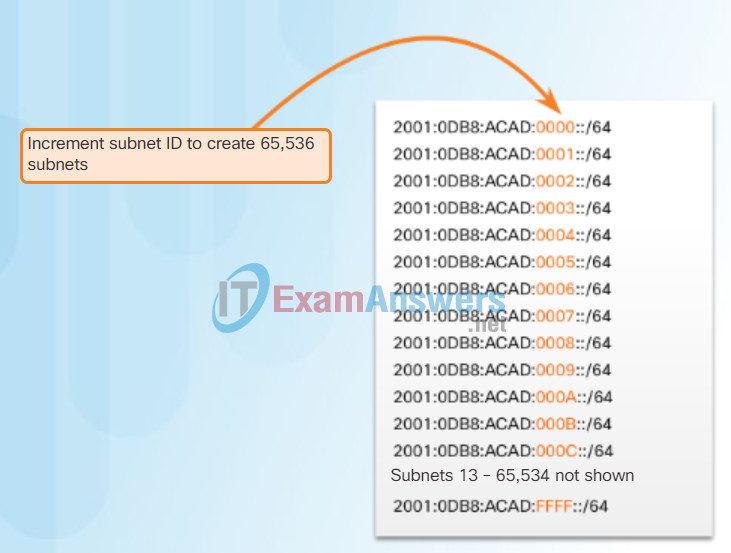
Address Block: 2001:0DB8:ACAD::/48
8.3.1.3 IPsec VPN Configuration Tasks
IPv6 Subnet Allocation
With over 65,000 subnets to choose from, the task of the network administrator becomes one of designing a logical scheme to address the network.
As shown in Figure 1, the example topology will require subnets for each LAN as well as for the WAN link between R1 and R2. Unlike the example for IPv4, with IPv6 the WAN link subnet will not be subnetted further. Although this may “waste” addresses, that is not a concern when using IPv6.
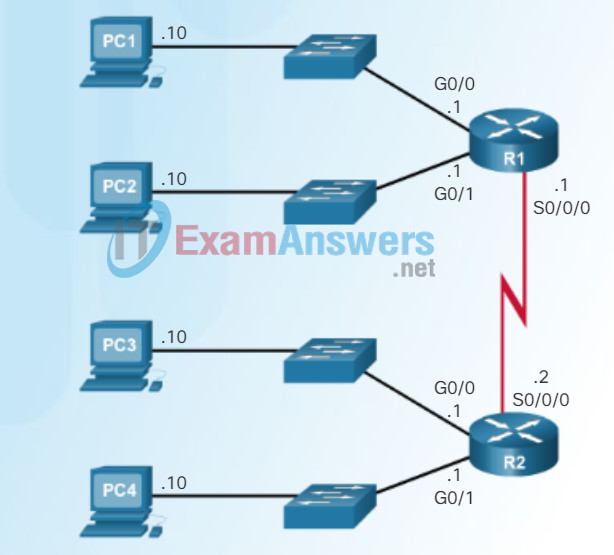
Example Topology
As shown in Figure 2, the allocation of five IPv6 subnets, with the subnet ID field 0001 through 0005 will be used for this example. Each /64 subnet will provide more addresses than will ever be needed.
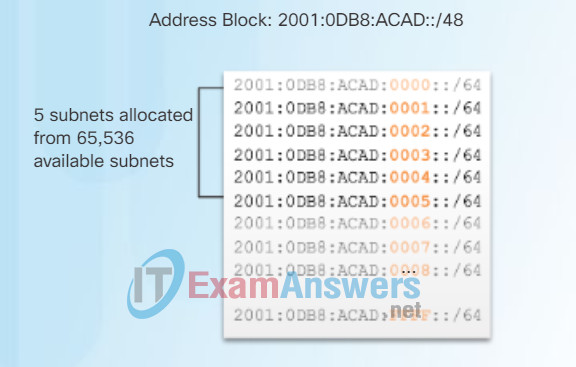
IPv6 Subnetting
As shown in Figure 3, each LAN segment and the WAN link is assigned a /64 subnet.
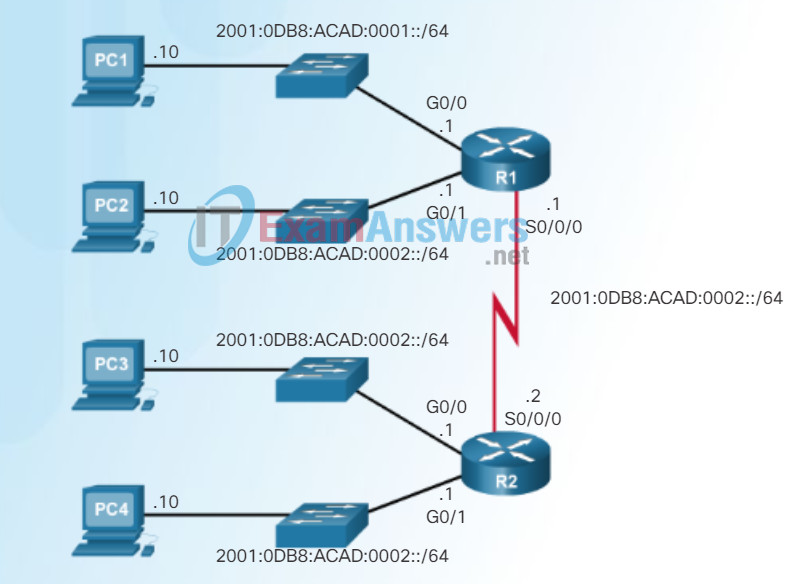
IPv6 Subnet Allocation
Similar to configuring IPv4, Figure 4 shows that each of the router interfaces has been configured to be on a different IPv6 subnet.
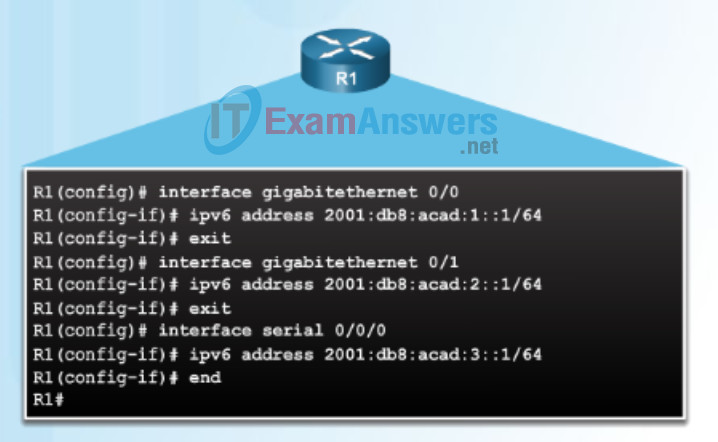
IPv6 Address Configuration
8.3.1.4 Existing ACL Configurations
Packet Tracer – Implementing a Subnetted IPv6 Addressing Scheme
Your network administrator wants you to assign five /64 IPv6 subnets to the network shown in the topology. Your job is to determine the IPv6 subnets, assign IPv6 addresses to the routers and set the PCs to automatically receive IPv6 addressing. Your final step is to verify connectivity between IPv6 hosts.
8.3.1.5 Handling Broadcast and Multicast Traffic
8.3.1.6 Activity – Order the IPsec Negotiation Steps
8.3.2 ISAKMP Policy
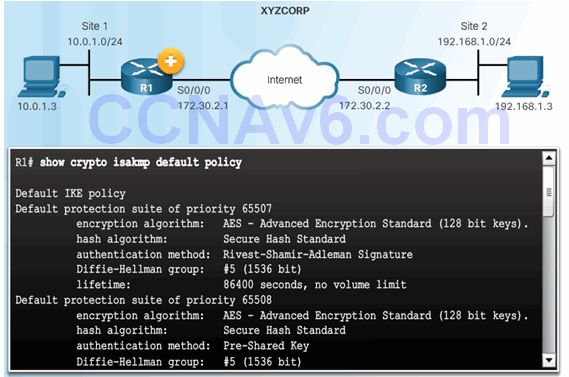
8.3.2.1 The Default ISAKMP Policies
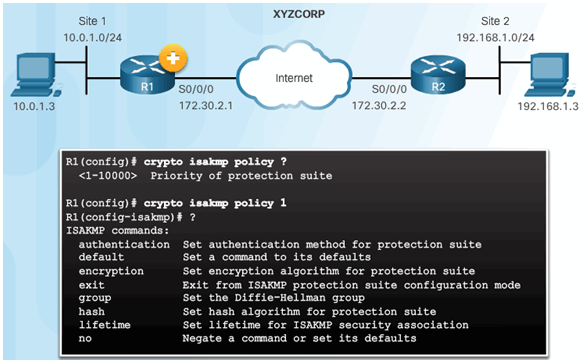
8.3.2.2 Syntax to Configure a New ISAKMP Policy
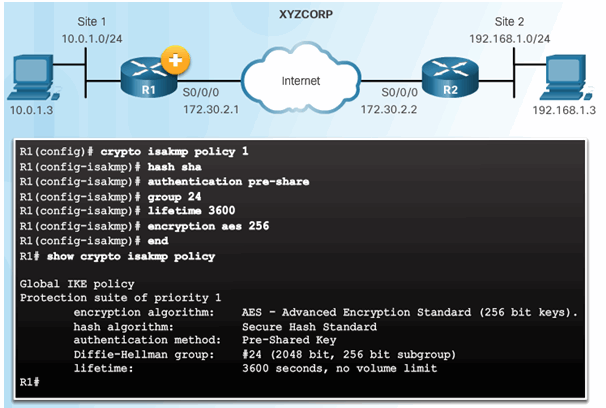
8.3.2.3 XYZCORP ISAKMP Policy Configuration
8.3.2.4 Configuring a Pre-Shared Key
The crypto isakmp key Command

Pre-Shared Key Configuration
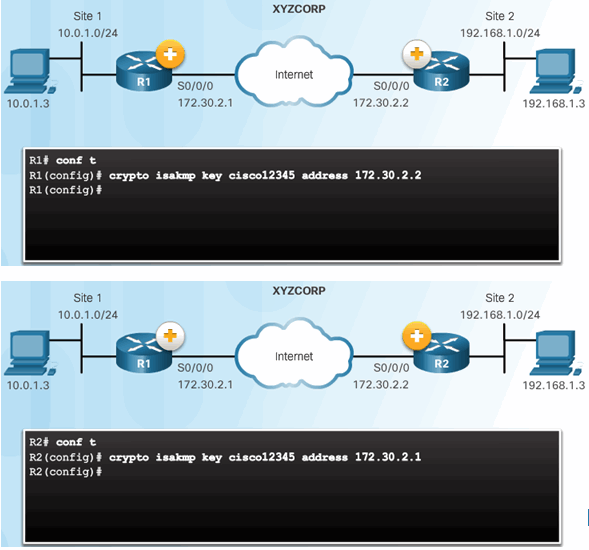

8.3.3 IPsec Policy
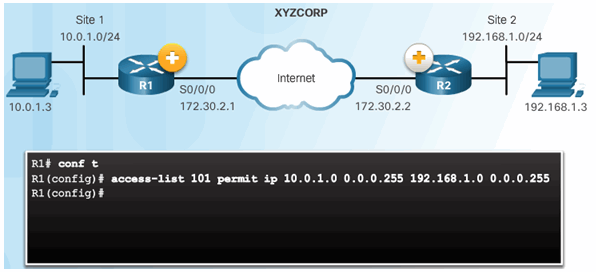
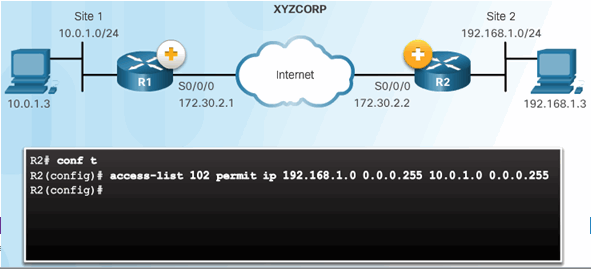
8.3.3.1 Define Interesting Traffic
The IKE Phase 1 Tunnel Does Not Exist Yet
Configure an ACL to Define Interesting Traffic
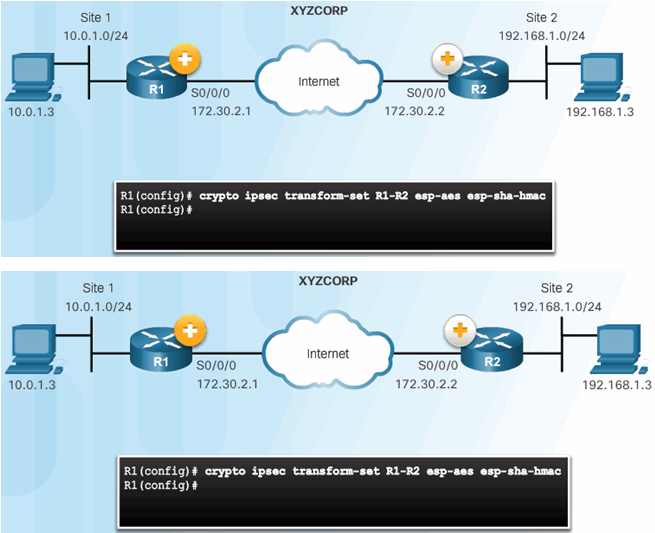
8.3.3.2 Configure IPsec Transform Set
The crypto ipsec transform-set Command
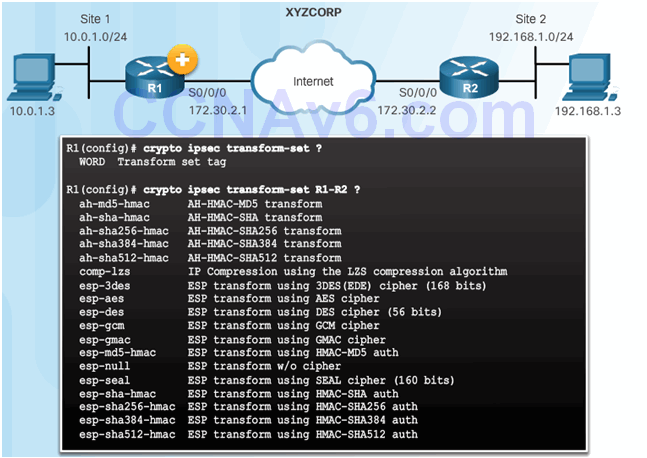
The crypto ipsec transform-set Command
8.3.4 Crypto Map
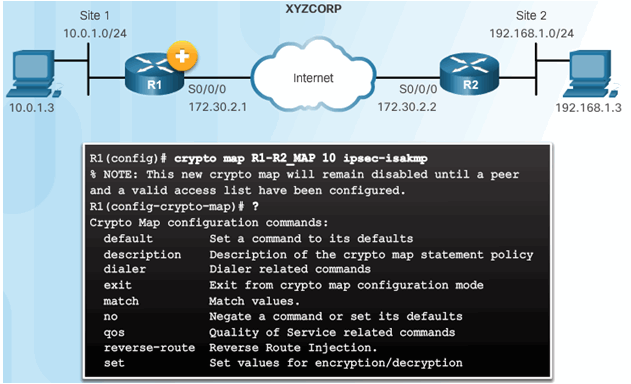
8.3.4.1 Syntax to Configure a Crypto Map
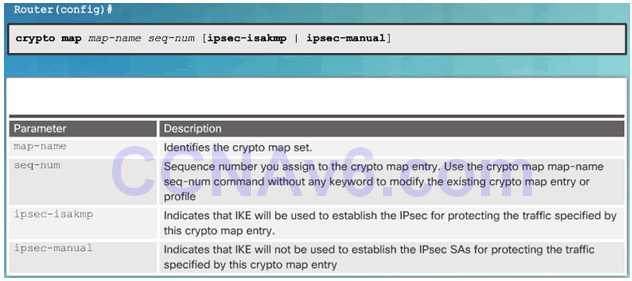
Crypto Map Configuration Commands
8.3.4.2 XYZCORP Crypto Map Configuration
Crypto Map Configuration:
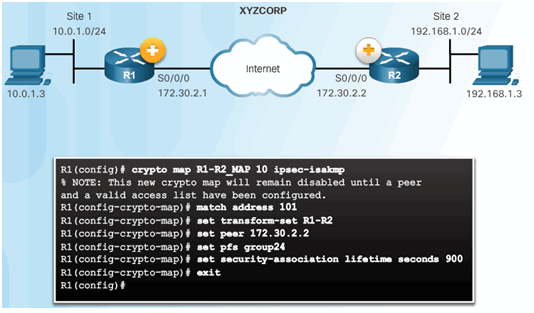
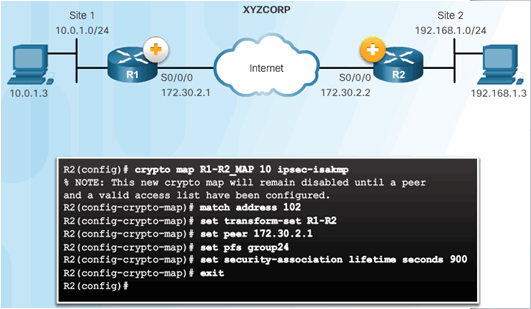
Crypto Map Configuration:
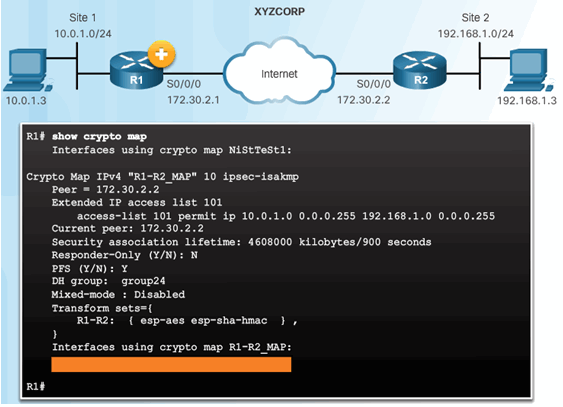
8.3.4.3 Apply the Crypto Map
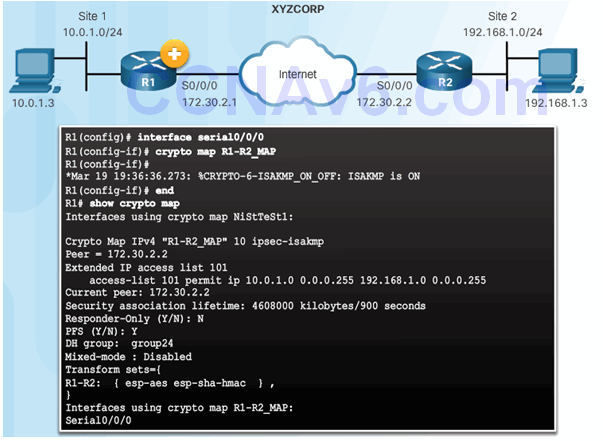
8.3.5 IPsec VPN
8.3.5.1 Send Interesting Traffic
Use Extended Ping to Send Interesting Traffic
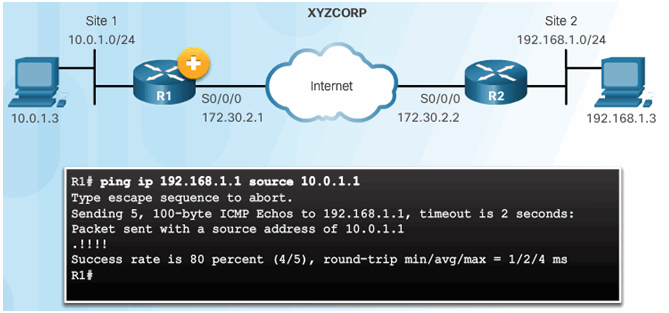
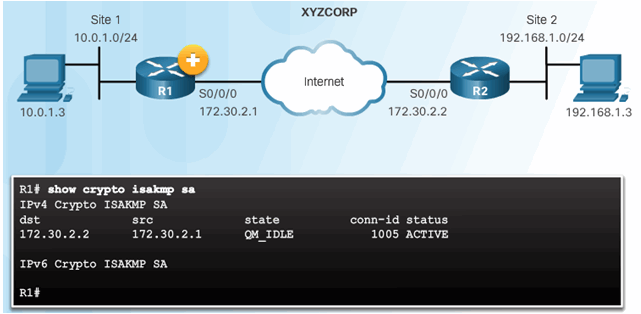
8.3.5.2 Verify the ISAKMP and IPsec Tunnels
Verify the ISAKMP Tunnel is Established
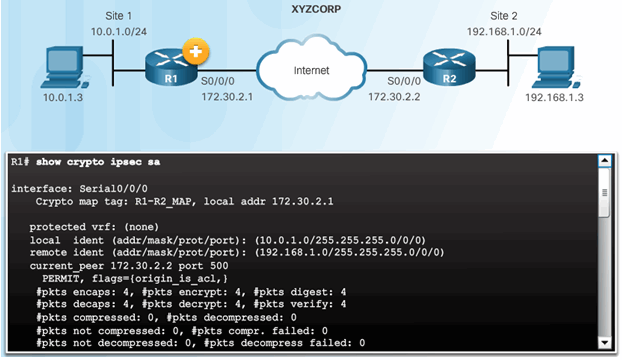
Verify the IPsec Tunnel is Established
8.4 Summary
8.4.1 Conclusion
8.4.1.1 Video Demonstration – Site-to-Site IPsec VPN Configuration
Class Activity – Can you call me now?
Can you call me now?
Note: This activity may be completed individually or in small/large groups using Packet Tracer software.
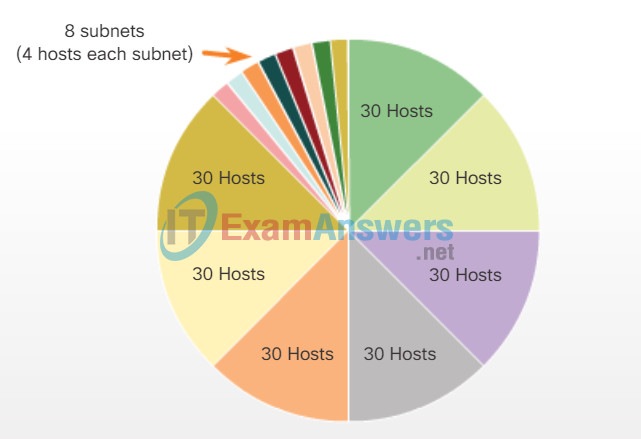
You are setting up a dedicated, computer addressing scheme for patient rooms in a hospital. The switch will be centrally located in the nurses’ station, as each of the five rooms will be wired so that patients can just connect to a RJ-45 port built into the wall of their room. Devise a physical and logical topology for only one of the six floors using the following addressing scheme requirements:
- There are six floors, with five patient rooms on each floor, for a total of thirty connections. Each room needs a network connection.
- Subnetting must be incorporated into your scheme.
- Use one router, one switch, and five host stations for addressing purposes.
- Validate that all PCs can connect to the hospital’s in-house services.
Keep a copy of your scheme to share later with the class or learning community. Be prepared to explain how subnetting, unicasts, multicasts, and broadcasts would be incorporated, and where your addressing scheme could be used.
Careful planning is required to make best use of an IP addressing scheme.
Plan for:
- Size
- Location
- Use
- Access requirements
8.4.1.2 Packet Tracer – Configure and Verify a Site-to-Site IPsec VPN
8.4.1.2 Packet Tracer – Configure and Verify a Site-to-Site IPsec VPN
Packet Tracer – Skills Integration Challenge
As a network technician familiar with IPv4 and IPv6 addressing implementations, you are now ready to take an existing network infrastructure and apply your knowledge and skills to finalize the configuration. The network administrator has already configured some commands on the routers. Do not erase or modify those configurations. Your task is to complete the IPv4 and IPv6 addressing scheme, implement IPv4 and IPv6 addressing, and verify connectivity.
8.4.1.3 Lab – Configuring a Site-to-Site VPN
8.4.1.3 Lab – Configuring a Site-to-Site VPN
Chapter 8: Subnetting IP Networks
The process of segmenting a network by dividing it into to multiple smaller network spaces is called subnetting.
Every network address has a valid range of host addresses. All devices attached to the same network will have an IPv4 host address for that network and a common subnet mask or network prefix. Traffic can be forwarded between hosts directly if they are on the same subnet. Traffic cannot be forwarded between subnets without the use of a router. To determine if traffic is local or remote, the router uses the subnet mask. The prefix and the subnet mask are different ways of representing the same thing – the network portion of an address.
IPv4 subnets are created by using one or more of the host bits as network bits. Two very important factors that will lead to the determination of the IP address block with the subnet mask are the number of subnets required, and the maximum number of hosts needed per subnet. There is an inverse relationship between the number of subnets and the number of hosts. The more bits that are borrowed to create subnets, the fewer host bits that are available; therefore, there are fewer hosts per subnet.
The formula 2^n (where n is the number of host bits remaining) is used to calculate how many addresses will be available on each subnet. However, the network address and broadcast address within a range are not useable. Therefore, to calculate the useable number of addresses, the calculation 2^n-2 is required.
Subnetting a subnet, or using Variable Length Subnet Mask (VLSM), was designed to avoid wasting addresses.
IPv6 subnetting requires a different approach than IPv4 subnetting. An IPv6 address space is not subnetted to conserve addresses; rather it is subnetted to support a hierarchical, logical design of the network. So, while IPv4 subnetting is about managing address scarcity, IPv6 subnetting is about building an addressing hierarchy based on the number of routers and the networks they support.
Careful planning is required to make best use of the available address space. Size, location, use, and access requirements are all considerations in the address planning process.
After it is implemented, an IP network needs to be tested to verify its connectivity and operational performance.
