CCNA Security 2.0 Study Material – Chapter 4: Implementing Firewall Technologies
4.0 Introduction
4.0.1 Welcome
4.0.1.1 Chapter 4: Implementing Firewall Technologies
Chapter 4: Network Access
To support our communication, the OSI model divides the functions of a data network into layers. Each layer works with the layers above and below to transmit data. Two layers of the OSI model are so closely tied, that according to the TCP/IP model they are in essence one layer. Those two layers are the data link layer and the physical layer.
On the sending device, it is the role of the data link layer to prepare data for transmission and control how that data accesses the physical media. However, the physical layer controls how the data is transmitted onto the physical media by encoding the binary digits that represent data into signals.
On the receiving end, the physical layer receives signals across the connecting media. After decoding the signal back into data, the physical layer passes the frame to the data link layer for acceptance and processing.
This chapter begins with the general functions of the physical layer and the standards and protocols that manage the transmission of data across local media. It also introduces the functions of the data link layer and the protocols associated with it.
4.1 Access Control Lists
4.1.1 Configuring Standard and Extended IPv4 ACLs with CLI
4.1.1.1 Introduction to Access Control Lists
Types of Connections
Whether connecting to a local printer in the home or a web site in another country, before any network communications can occur, a physical connection to a local network must be established. A physical connection can be a wired connection using a cable or a wireless connection using radio waves.
The type of physical connection used is dependent upon the setup of the network. For example, in many corporate offices employees have desktop or laptop computers that are physically connected, via cable, to a shared switch. This type of setup is a wired network. Data is transmitted through a physical cable.
In addition to wired connections, many businesses also offer wireless connections for laptops, tablets, and smartphones. With wireless devices, data is transmitted using radio waves. The use of wireless connectivity is common as individuals, and businesses alike, discover the advantages of offering this type of service. To offer wireless capability, devices on a wireless network must be connected to a wireless access point (AP).
Switch devices and wireless access points are often two separate dedicated devices within a network implementation. However, there are also devices that offer both wired and wireless connectivity. In many homes, for example, individuals are implementing home integrated service routers (ISRs), as shown in Figure 1. ISRs offer a switching component with multiple ports, allowing multiple devices to be connected to the local area network (LAN) using cables, as shown in Figure 2. Additionally, many ISRs also include an AP, which allows wireless devices to connect as well.

Home Router

Connecting to the Wired LAN
4.1.1.2 Configuring Numbered and Named ACLs
Network Interface Cards
Network Interface Cards (NICs) connect a device to the network. Ethernet NICs are used for a wired connection, as shown in Figure 1, whereas WLAN (Wireless Local Area Network) NICs are used for wireless. An end-user device may include one or both types of NICs. A network printer, for example, may only have an Ethernet NIC, and therefore, must connect to the network using an Ethernet cable. Other devices, such as tablets and smartphones, might only contain a WLAN NIC and must use a wireless connection.
Not all physical connections are equal, in terms of the performance level, when connecting to a network.
For example, a wireless device will experience degradation in performance based on its distance from a wireless access point. The further the device is from the access point, the weaker the wireless signal it receives. This can mean less bandwidth or no wireless connection at all. Figure 2 shows that a wireless range extender can be used to regenerate the wireless signal to other parts of the house that are too far from the wireless access point. Alternatively, a wired connection will not degrade in performance.
All wireless devices must share access to the airwaves connecting to the wireless access point. This means slower network performance may occur as more wireless devices access the network simultaneously. A wired device does not need to share its access to the network with other devices. Each wired device has a separate communications channel over its Ethernet cable. This is important when considering some applications, such as online gaming, streaming video, and video conferencing, which require more dedicated bandwidth than other applications.
Over the next couple of topics, you will learn more about the physical layer connections that occur and how those connections affect the transportation of data.

Wired Connection using an Ethernet NIC
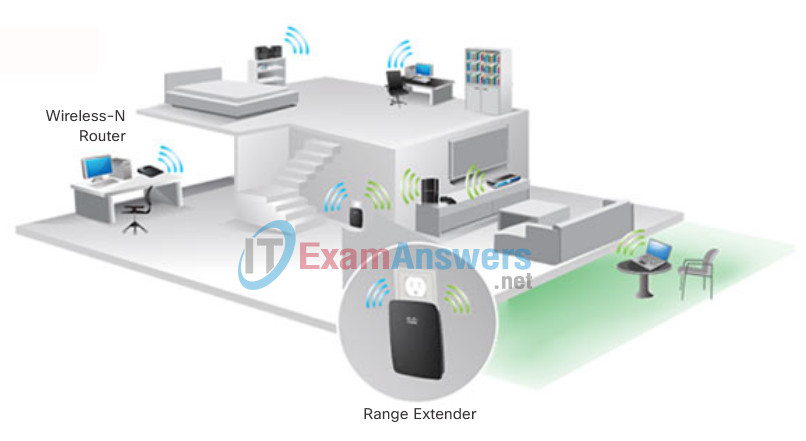
Connecting to the Wireless LAN with a Range Extender
4.1.1.3 Applying an ACL
Syntax – Apply an ACL to an interface

Syntax – Apply an ACL to the VTY lines

Example – Named Standard ACL
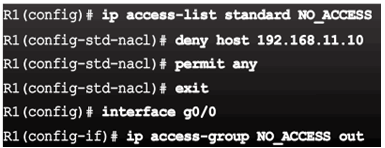
Example – Named Extended ACL
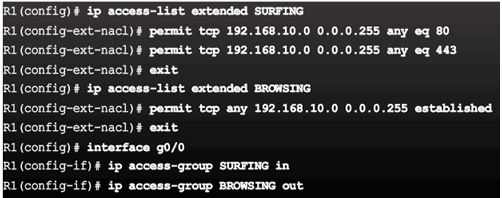
Syntax – Apply an ACL to the VTY lines

Example – Named ACL on VTY lines with logging
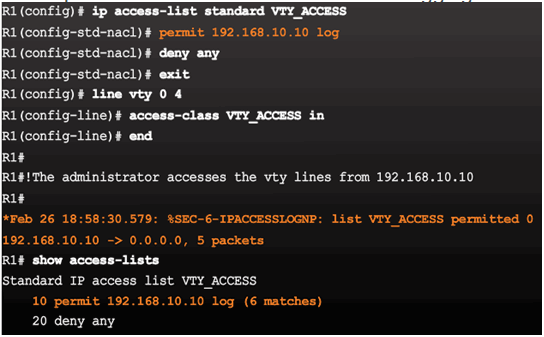
4.1.1.4 ACL Configuration Guidelines
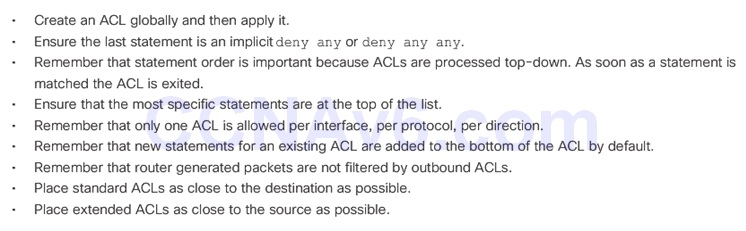
4.1.1.5 Editing Existing ACLs
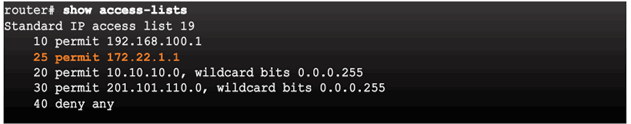
Existing access list has three entries

Access list has been edited, which adds a new ACE and replaces ACE line 20.
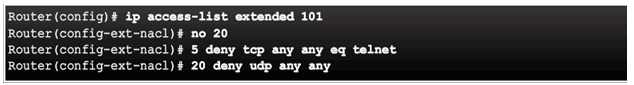
Updated access list has four entries

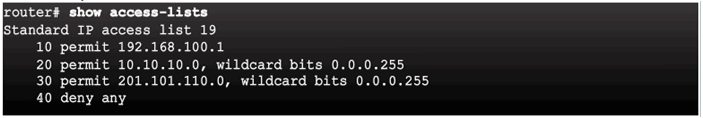
4.1.1.6 Sequence Numbers and Standard ACLs
Existing access list has four entries
Access list has been edited, which adds a new ACE that permits a specific IP address.
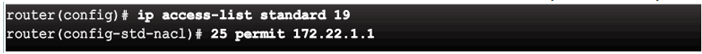
Updated access list places the new ACE before line 20
4.1.1.7 Activity – Configuring Standard ACLs
4.1.1.8 Activity – Creating an Extended ACL Statement
4.1.1.9 Activity – Evaluating Extended ACLs
4.1.1.10 Packet Tracer – Configuring Extended ACLs Scenario 1
4.1.1.10 Packet Tracer – Configuring Extended ACLs Scenario 1
4.1.1.11 Packet Tracer – Configuring Extended ACLs Scenario 2
4.1.1.10 Packet Tracer – Configuring Extended ACLs Scenario 2
4.1.2 Mitigating Attacks with ACLs
4.1.2.1 Antispoofing with ACLs
The Physical Layer
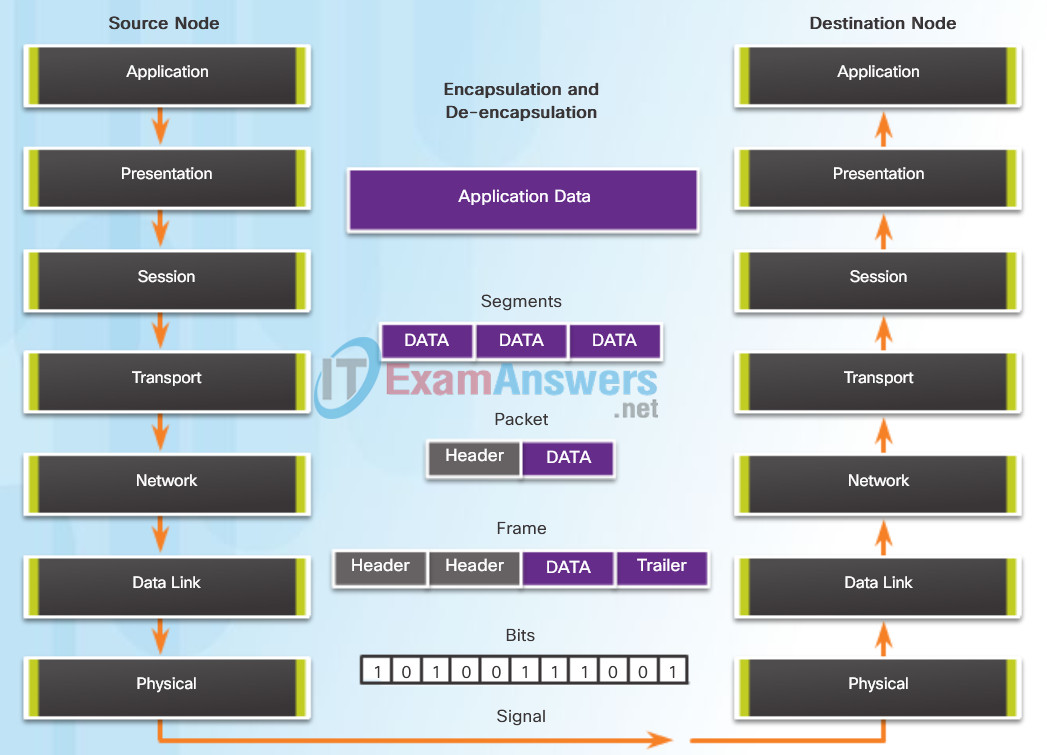
The OSI physical layer provides the means to transport the bits that make up a data link layer frame across the network media. This layer accepts a complete frame from the data link layer and encodes it as a series of signals that are transmitted onto the local media. The encoded bits that comprise a frame are received by either an end device or an intermediate device.
The process that data undergoes from a source node to a destination node is:
- The user data is segmented by the transport layer, placed into packets by the network layer, and further encapsulated into frames by the data link layer.
- The physical layer encodes the frames and creates the electrical, optical, or radio wave signals that represent the bits in each frame.
- These signals are then sent on the media, one at a time.
- The destination node physical layer retrieves these individual signals from the media, restores them to their bit representations, and passes the bits up to the data link layer as a complete frame.
4.1.2.2 Permitting Necessary Traffic through a Firewall
Physical Layer Media
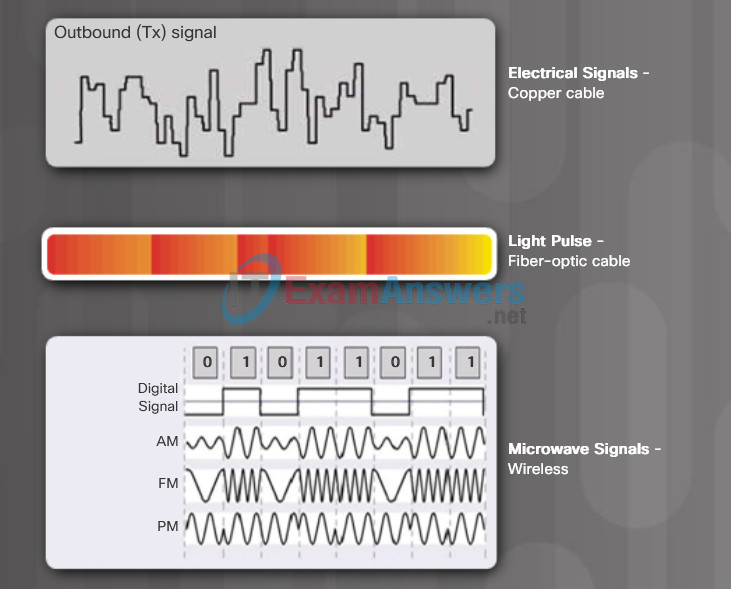
There are three basic forms of network media. The physical layer produces the representation and groupings of bits for each type of media as:
- Copper cable: The signals are patterns of electrical pulses.
- Fiber-optic cable: The signals are patterns of light.
- Wireless: The signals are patterns of microwave transmissions.
The figure displays signaling examples for copper, fiber-optic, and wireless.
To enable physical layer interoperability, all aspects of these functions are governed by standards organizations.
4.1.2.3 Mitigating ICMP Abuse
Physical Layer Standards
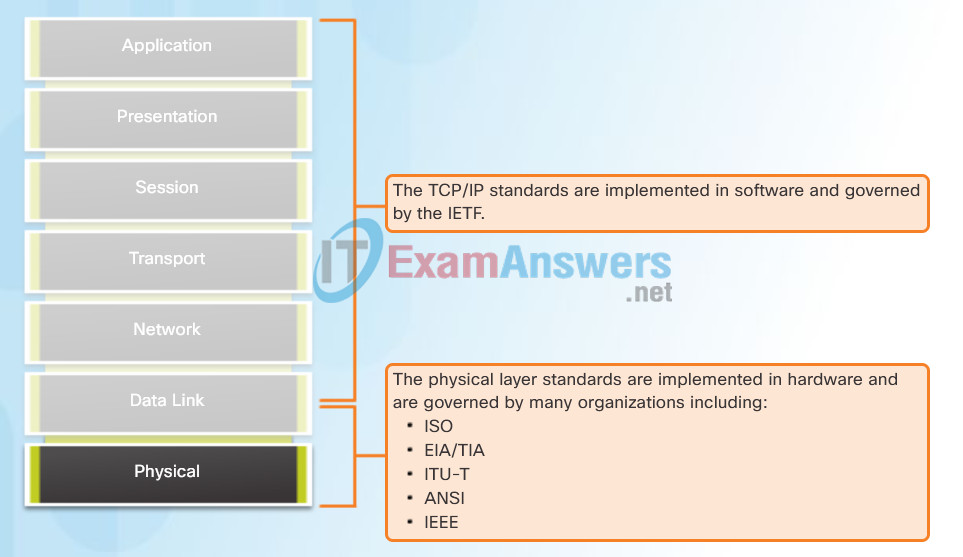
The protocols and operations of the upper OSI layers are performed in software designed by software engineers and computer scientists. The services and protocols in the TCP/IP suite are defined by the Internet Engineering Task Force (IETF).
The physical layer consists of electronic circuitry, media, and connectors developed by engineers. Therefore, it is appropriate that the standards governing this hardware are defined by the relevant electrical and communications engineering organizations.
There are many different international and national organizations, regulatory government organizations, and private companies involved in establishing and maintaining physical layer standards. For instance, the physical layer hardware, media, encoding, and signaling standards are defined and governed by the:
- International Organization for Standardization (ISO)
- Telecommunications Industry Association/Electronic Industries Association (TIA/EIA)
- International Telecommunication Union (ITU)
- American National Standards Institute (ANSI)
- Institute of Electrical and Electronics Engineers (IEEE)
- National telecommunications regulatory authorities including the Federal Communication Commission (FCC) in the USA and the European Telecommunications Standards Institute (ETSI)
In addition to these, there are often regional cabling standards groups such as CSA (Canadian Standards Association), CENELEC (European Committee for Electrotechnical Standardization), and JSA/JIS (Japanese Standards Association), developing local specifications.
4.1.2.4 Mitigating SNMP Exploits
Lab – Identifying Network Devices and Cabling
In this lab, you will complete the following objectives:
- Part 1: Identify Network Devices
- Part 2: Identify Network Media
4.1.2.5 Packet Tracer – Configure IP ACLs to Mitigate Attacks
4.1.2.5 Packet Tracer – Configure IP ACLs to Mitigate Attacks
4.1.3 IPv6 ACLs
4.1.3.1 Introducing IPv6 ACLs
Functions
The physical layer standards address three functional areas:
Physical Components
The physical components are the electronic hardware devices, media, and other connectors that transmit and carry the signals to represent the bits. Hardware components such as NICs, interfaces and connectors, cable materials, and cable designs are all specified in standards associated with the physical layer. The various ports and interfaces on a Cisco 1941 router are also examples of physical components with specific connectors and pinouts resulting from standards.
The transition occurs at the middle of each bit period.
Encoding
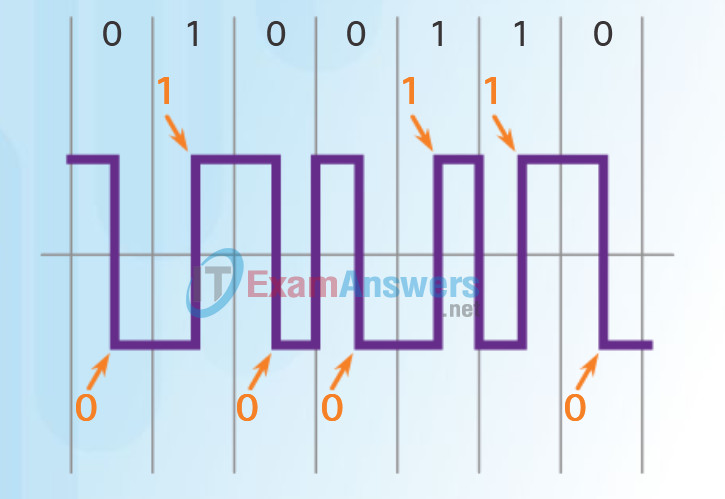
Encoding or line encoding is a method of converting a stream of data bits into a predefined “code”. Codes are groupings of bits used to provide a predictable pattern that can be recognized by both the sender and the receiver. In the case of networking, encoding is a pattern of voltage or current used to represent bits; the 0s and 1s.
For example, Manchester encoding represents a 0 bit by a high to low voltage transition, and a 1 bit is represented as a low to high voltage transition. An example of Manchester encoding is illustrated in Figure 1. The transition occurs at the middle of each bit period. This type of encoding is used in 10 b/s Ethernet. Faster data rates require more complex encoding.
Signaling
The physical layer must generate the electrical, optical, or wireless signals that represent the “1” and “0” on the media. The method of representing the bits is called the signaling method. The physical layer standards must define what type of signal represents a “1” and what type of signal represents a “0”. This can be as simple as a change in the level of an electrical signal or optical pulse. For example, a long pulse might represent a 1 whereas a short pulse represents a 0.
This is similar to how Morse code is used for communication. Morse code is another signaling method that uses a series of on-off tones, lights, or clicks to send text over telephone wires or between ships at sea.
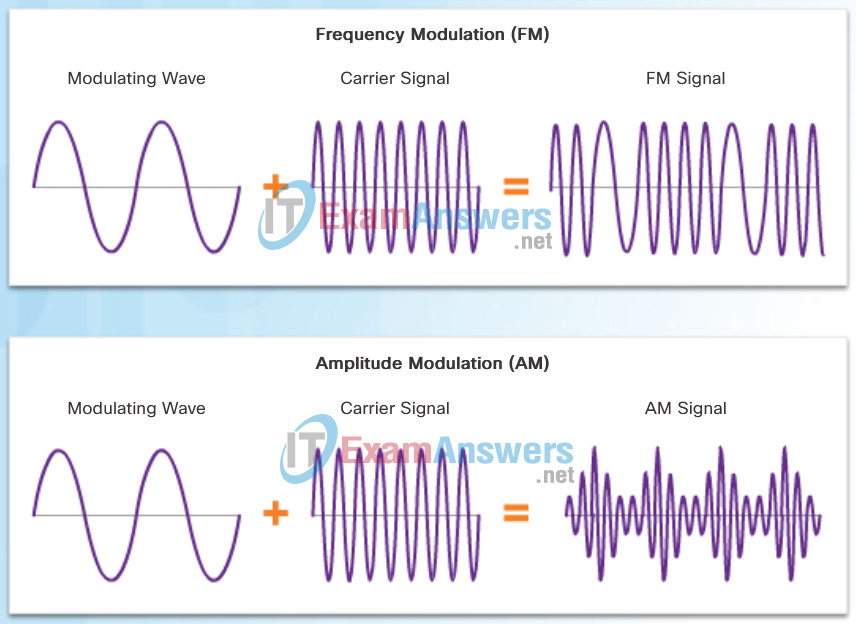
There are many ways to transmit signals. A common method to send data is using modulation techniques. Modulation is the process by which the characteristic of one wave (the signal) modifies another wave (the carrier).
The nature of the actual signals representing the bits on the media will depend on the signaling method in use.
Figure 2 illustrates the how AM and FM techniques are used to send a signal.
4.1.3.2 IPv6 ACL Syntax
Bandwidth
Different physical media support the transfer of bits at different rates. Data transfer is usually discussed in terms of bandwidth and throughput.
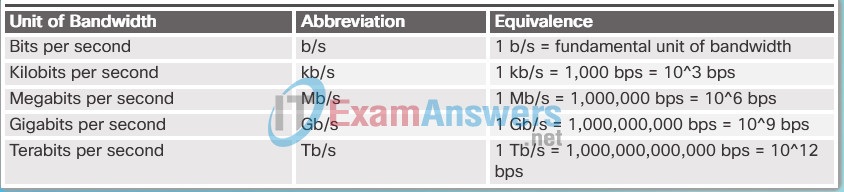
Bandwidth is the capacity of a medium to carry data. Digital bandwidth measures the amount of data that can flow from one place to another in a given amount of time. Bandwidth is typically measured in kilobits per second (kb/s), megabits per second (Mb/s), or gigabits per second (Gb/s). Bandwidth is sometimes thought of as the speed that bits travel, however this is not accurate. For example, in both 10Mb/s and 100Mb/s Ethernet, the bits are sent at the speed of electricity. The difference is the number of bits that are transmitted per second.
A combination of factors determines the practical bandwidth of a network:
The properties of the physical media
- The technologies chosen for signaling and detecting network signals
- Physical media properties, current technologies, and the laws of physics all play a role in determining the available bandwidth.
The table shows the commonly used units of measure for bandwidth.
4.1.3.3 Configure IPv6 ACLs
Throughput
Throughput is the measure of the transfer of bits across the media over a given period of time.
Due to a number of factors, throughput usually does not match the specified bandwidth in physical layer implementations. Many factors influence throughput, including:
- The amount of traffic
- The type of traffic
- The latency created by the number of network devices encountered between source and destination
Latency refers to the amount of time, to include delays, for data to travel from one given point to another.
In an internetwork or network with multiple segments, throughput cannot be faster than the slowest link in the path from source to destination. Even if all or most of the segments have high bandwidth, it will only take one segment in the path with low throughput to create a bottleneck to the throughput of the entire network.
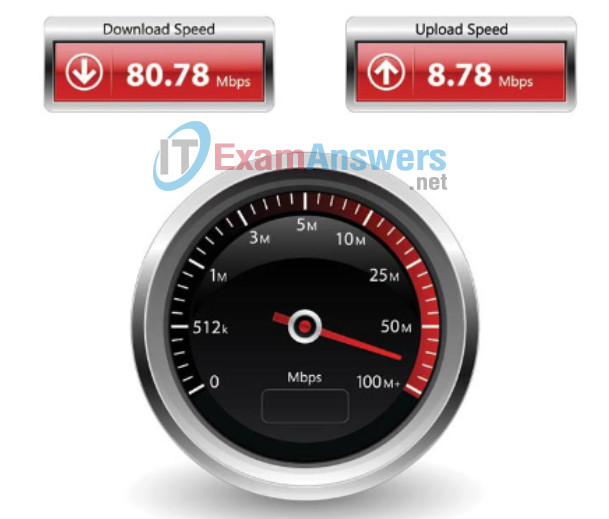
There are many online speed tests that can reveal the throughput of an Internet connection. The figure provides sample results from a speed test.
There is a third measurement to assess the transfer of usable data that is known as goodput. Goodput is the measure of usable data transferred over a given period of time. Goodput is throughput minus traffic overhead for establishing sessions, acknowledgments, and encapsulation.
4.1.3.4 Packet Tracer – Configure IPv6 ACLs
4.1.3.4 Packet Tracer – Configure IPv6 ACLs
Types of Physical Media
The physical layer produces the representation and groupings of bits as voltages, radio frequencies, or light pulses. Various standards organizations have contributed to the definition of the physical, electrical, and mechanical properties of the media available for different data communications. These specifications guarantee that cables and connectors will function as anticipated with different data link layer implementations.
As an example, standards for copper media are defined for the:
- Type of copper cabling used
- Bandwidth of the communication
- Type of connectors used
- Pinout and color codes of connections to the media
- Maximum distance of the media
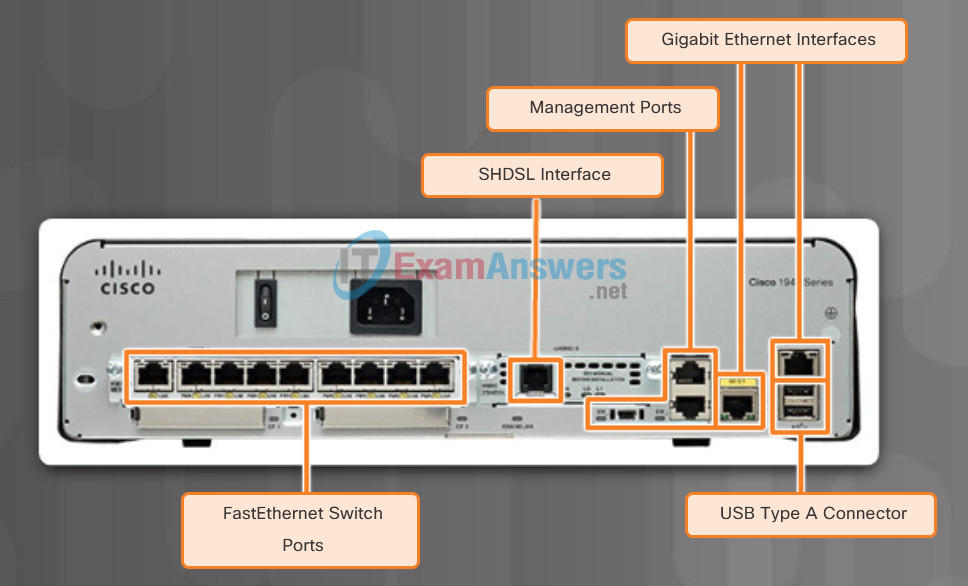
The figure shows different types of interfaces and ports available on a 1941 router.
4.2 Firewall Technologies
4.2.1 Securing Networks with Firewalls
4.2.1.1 Defining Firewalls
Characteristics of Copper Cabling
Networks use copper media because it is inexpensive, easy to install and has low resistance to electrical current. However, copper media is limited by distance and signal interference.
Data is transmitted on copper cables as electrical pulses. A detector in the network interface of a destination device must receive a signal that can be successfully decoded to match the signal sent. However, the longer the signal travels, the more it deteriorates. This is referred to as signal attenuation. For this reason, all copper media must follow strict distance limitations as specified by the guiding standards.
The timing and voltage values of the electrical pulses are also susceptible to interference from two sources:
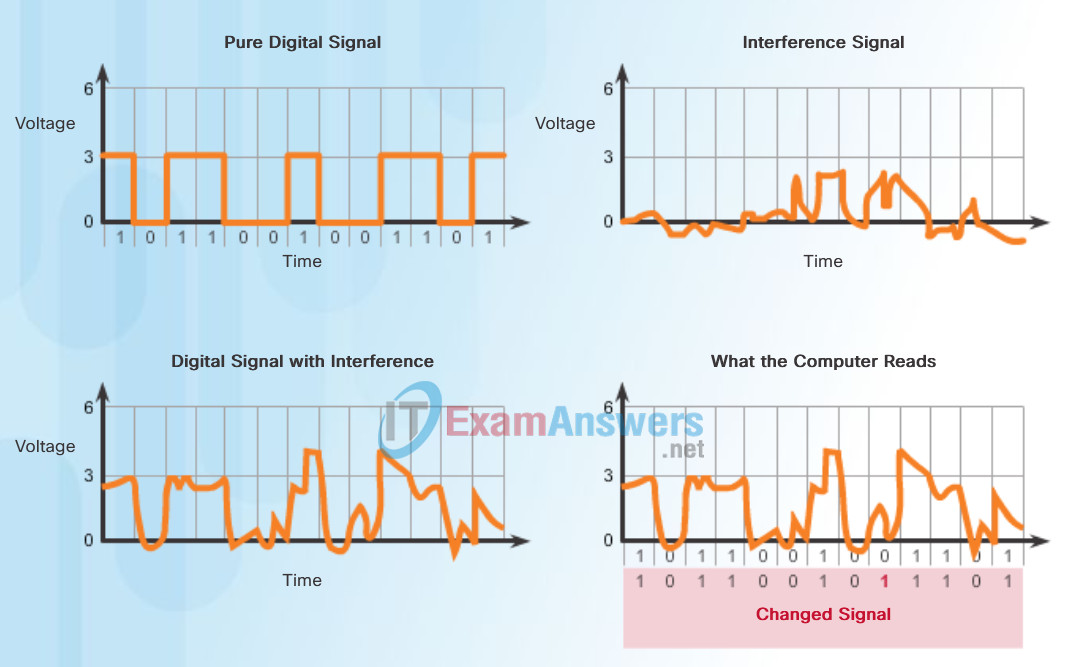
- Electromagnetic interference (EMI) or radio frequency interference (RFI) – EMI and RFI signals can distort and corrupt the data signals being carried by copper media. Potential sources of EMI and RFI include radio waves and electromagnetic devices, such as fluorescent lights or electric motors as shown in the figure.
- Crosstalk – Crosstalk is a disturbance caused by the electric or magnetic fields of a signal on one wire to the signal in an adjacent wire. In telephone circuits, crosstalk can result in hearing part of another voice conversation from an adjacent circuit. Specifically, when an electrical current flows through a wire, it creates a small, circular magnetic field around the wire, which can be picked up by an adjacent wire.
Play the animation in the figure to see how data transmission can be affected by interference.
To counter the negative effects of EMI and RFI, some types of copper cables are wrapped in metallic shielding and require proper grounding connections.
To counter the negative effects of crosstalk, some types of copper cables have opposing circuit wire pairs twisted together, which effectively cancels the crosstalk.
The susceptibility of copper cables to electronic noise can also be limited by:
- Selecting the cable type or category most suited to a given networking environment.
- Designing a cable infrastructure to avoid known and potential sources of interference in the building structure.
- Using cabling techniques that include the proper handling and termination of the cables.
4.2.1.2 Benefits and Limitations of Firewalls
Copper Media
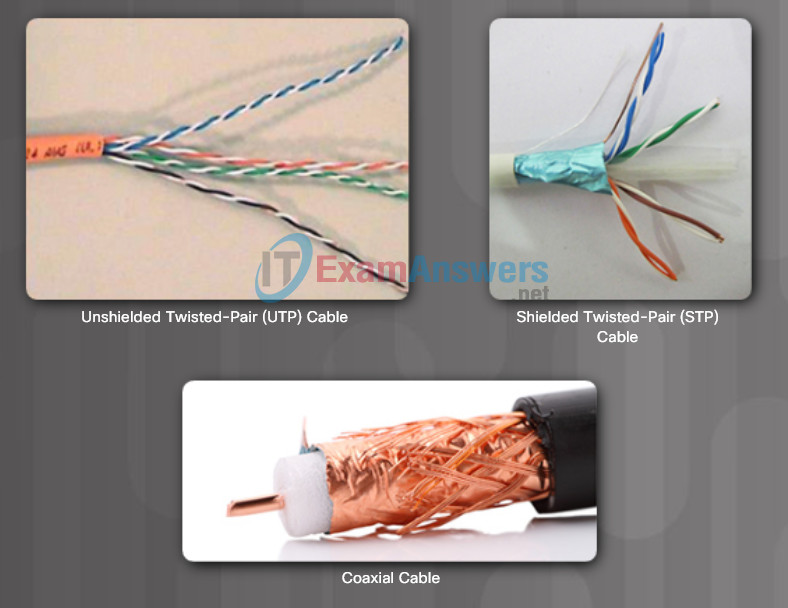
There are three main types of copper media used in networking:
- Unshielded Twisted-Pair (UTP)
- Shielded Twisted-Pair (STP)
- Coaxial
These cables are used to interconnect nodes on a LAN and infrastructure devices such as switches, routers, and wireless access points. Each type of connection and the accompanying devices has cabling requirements stipulated by physical layer standards.
Different physical layer standards specify the use of different connectors. These standards specify the mechanical dimensions of the connectors and the acceptable electrical properties of each type. Networking media use modular jacks and plugs to provide easy connection and disconnection. Also, a single type of physical connector may be used for multiple types of connections. For example, the RJ-45 connector is widely used in LANs with one type of media and in some WANs with another media type.
4.2.2 Types of Firewalls
4.2.2.1 Firewall Type Descriptions
Properties of UTP Cabling
When used as a networking medium, unshielded twisted-pair (UTP) cabling consists of four pairs of color-coded copper wires that have been twisted together and then encased in a flexible plastic sheath. Its small size can be advantageous during installation.
UTP cable does not use shielding to counter the effects of EMI and RFI. Instead, cable designers have discovered that they can limit the negative effect of crosstalk by:
- Cancellation: Designers now pair wires in a circuit. When two wires in an electrical circuit are placed close together, their magnetic fields are the exact opposite of each other. Therefore, the two magnetic fields cancel each other and also cancel out any outside EMI and RFI signals.
- Varying the number of twists per wire pair: To further enhance the cancellation effect of paired circuit wires, designers vary the number of twists of each wire pair in a cable. UTP cable must follow precise specifications governing how many twists or braids are permitted per meter (3.28 feet) of cable. Notice in the figure that the orange/orange white pair is twisted less than the blue/blue white pair. Each colored pair is twisted a different number of times.
UTP cable relies solely on the cancellation effect produced by the twisted wire pairs to limit signal degradation and effectively provide self-shielding for wire pairs within the network media.

Networks Support the Way We Communicate
4.2.2.2 Packet Filtering Firewall Benefits and Limitations
UTP Cabling Standards
UTP cabling conforms to the standards established jointly by the TIA/EIA. Specifically, TIA/EIA-568 stipulates the commercial cabling standards for LAN installations and is the standard most commonly used in LAN cabling environments. Some of the elements defined are:
- Cable types
- Cable lengths
- Connectors
- Cable termination
- Methods of testing cable
The electrical characteristics of copper cabling are defined by the Institute of Electrical and Electronics Engineers (IEEE). IEEE rates UTP cabling according to its performance. Cables are placed into categories based on their ability to carry higher bandwidth rates. For example, Category 5 (Cat5) cable is used commonly in 100BASE-TX Fast Ethernet installations. Other categories include Enhanced Category 5 (Cat5e) cable, Category 6 (Cat6), and Category 6a.
Cables in higher categories are designed and constructed to support higher data rates. As new gigabit speed Ethernet technologies are being developed and adopted, Cat5e is now the minimally acceptable cable type, with Cat6 being the recommended type for new building installations.
Click each category of cable in the figure to learn more about their properties.
Some manufacturers are making cables exceeding the TIA/EIA Category 6a specifications and refer to these as Category 7.
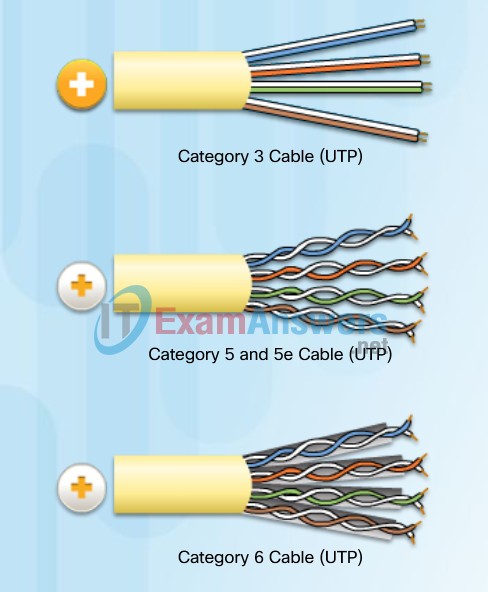
Category 3 Cable (UTP)
- Used for voice communication
- Most often used for phone lines
Category 5 and 5e Cable (UTP)
- Used for data transmission
- Cat5 supports 100 Mb/s and can support 1000 Mb/s, but it is not recommended
- Cat5e supports 1000 Mb/s
Category 6 Cable (UTP)
- Used for data transmission
- An added separator is between each pair of wires allowing it to function at higher speeds
- Supports 1000 Mb/s – 10 Gb/s, though 10 Gb/s is not recommended
4.2.2.3 Stateful Firewalls
UTP Connectors
UTP cable is usually terminated with an RJ-45 connector. This connector is used for a range of physical layer specifications, one of which is Ethernet. The TIA/EIA-568 standard describes the wire color codes to pin assignments (pinouts) for Ethernet cables.
As shown in Figure1, the RJ-45 connector is the male component, crimped at the end of the cable. The socket is the female component of a network device, wall, cubicle partition outlet, or patch panel.
Each time copper cabling is terminated; there is the possibility of signal loss and the introduction of noise into the communication circuit. When terminated improperly, each cable is a potential source of physical layer performance degradation. It is essential that all copper media terminations be of high quality to ensure optimum performance with current and future network technologies.
Figure 2 displays an example of a badly terminated UTP cable and a well terminated UTP cable.
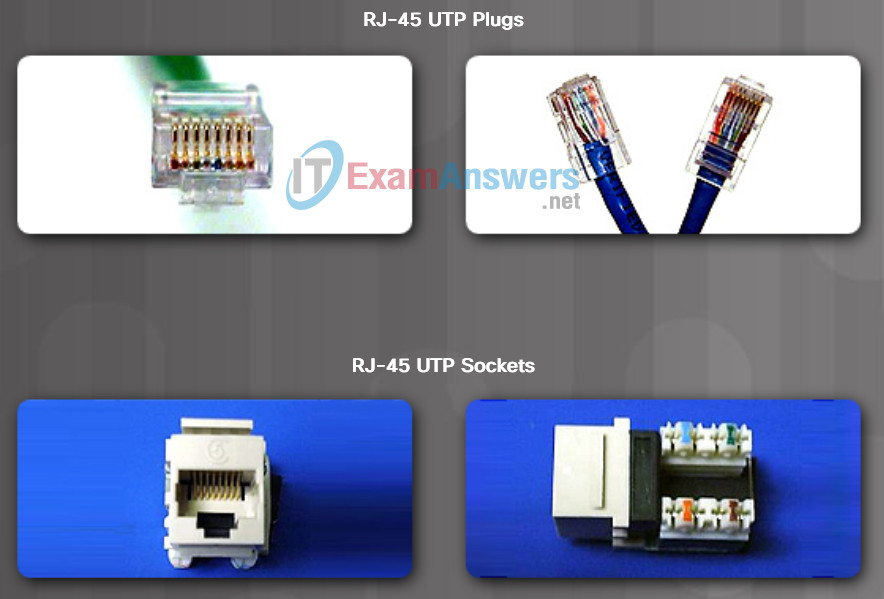

Improper cable termination can impact transmission performance.
4.2.2.4 Stateful Firewall Benefits and Limitations
Types of UTP Cable
Different situations may require UTP cables to be wired according to different wiring conventions. This means that the individual wires in the cable have to be connected in different orders to different sets of pins in the RJ-45 connectors.
The following are the main cable types that are obtained by using specific wiring conventions:
- Ethernet Straight-through: The most common type of networking cable. It is commonly used to interconnect a host to a switch and a switch to a router.
- Ethernet Crossover: A cable used to interconnect similar devices. For example to connect a switch to a switch, a host to a host, or a router to a router.
- Rollover: A Cisco proprietary cable used to connect a workstation to a router or switch console port.
The figure shows the UTP cable type, related standards, and typical application of these cables. It also identifies the individual wire pairs for the TIA-568A and TIA-568B standards.
Using a crossover or straight-through cable incorrectly between devices may not damage the devices, but connectivity and communication between the devices will not take place. This is a common error in the lab and checking that the device connections are correct should be the first troubleshooting action if connectivity is not achieved.
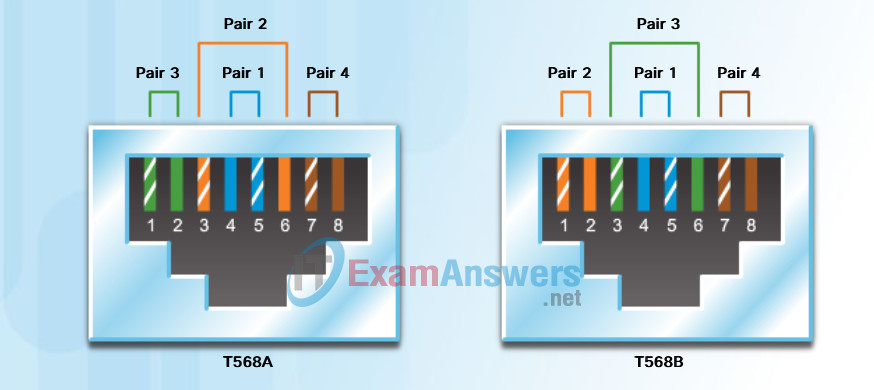
| Cable Type | Standard | Application |
|---|---|---|
| Ethernet Straight-through | Both ends T568A or both ends T568B | Connects a network host to a network device such as a switch or hub. |
| Ethernet Crossover | One end T568A,Other end T568B | Connects two network hosts Connects two network intermediary devices (switch to switch, or router to router) |
| Rollover | Cisco proprietary | Connects a workstation serial port to a router console port, using an adapter. |
4.2.2.5 Next Generation Firewalls
Testing UTP Cables
After installation, a UTP cable tester, like the one shown in the figure, should be used to test for the following parameters:
- Wire map
- Cable length
- Signal loss due to attenuation
- Crosstalk
It is recommended to check thoroughly that all UTP installation requirements have been met.

4.2.3 Classic Firewall
4.2.3.1 Introducing Classic Firewal
Properties of Fiber-Optic Cabling
Optical fiber cable transmits data over longer distances and at higher bandwidths than any other networking media. Unlike copper wires, fiber-optic cable can transmit signals with less attenuation and is completely immune to EMI and RFI. Optical fiber is commonly used to interconnect network devices.
Optical fiber is a flexible, but extremely thin, transparent strand of very pure glass, not much bigger than a human hair. Bits are encoded on the fiber as light impulses. The fiber-optic cable acts as a waveguide, or “light pipe,” to transmit light between the two ends with minimal loss of signal.
As an analogy, consider an empty paper towel roll with the inside coated like a mirror. It is a thousand meters in length, and a small laser pointer is used to send Morse code signals at the speed of light. Essentially that is how a fiber-optic cable operates, except that it is smaller in diameter and uses sophisticated light technologies.
Fiber-optic cabling is now being used in four types of industry:
- Enterprise Networks: Used for backbone cabling applications and interconnecting infrastructure devices.
- Fiber-to-the-Home (FTTH): Used to provide always-on broadband services to homes and small businesses.
- Long-Haul Networks: Used by service providers to connect countries and cities.
- Submarine Cable Networks: Used to provide reliable high-speed, high-capacity solutions capable of surviving in harsh undersea environments up to transoceanic distances. Click here to view a telegeography map that depicts the location of submarine cables.
Our focus in this course is the use of fiber within the enterprise.

4.2.3.2 Classic Firewall Operation
Fiber Media Cable Design
Optical fiber is composed of two kinds of glass (core and cladding) and a protective outer shield (jacket). Click each component in the figure to learn more information.
Although the optical fiber is very thin and susceptible to sharp bends, the properties of the core and cladding make it very strong. Optical fiber is durable and is deployed in harsh environmental conditions in networks all around the world.
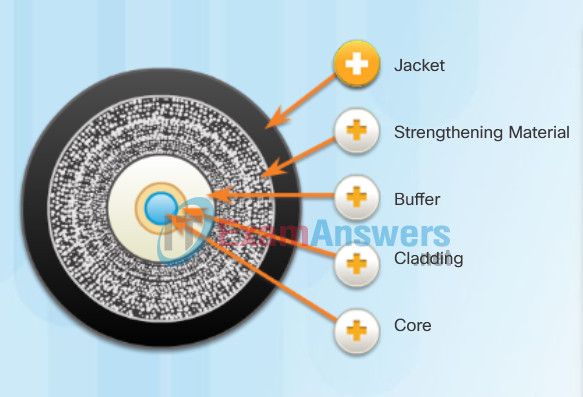
Jacket
Typically a PVC jacket that protects the fiber against abrasion, moisture, and other contaminants. This outer jacket composition can vary depending on the cable usage.

Strengthening Material
Surrounds the buffer, prevents the fiber cable from being stretched when it is being pulled. The material used is often the same material used to produce bulletproof vests.

Buffer
Used to help shield the core and cladding from damage.

Cladding
Made from slightly different chemicals than those used to create the core. It tends to act like a mirror by reflecting light back into the core of the fiber. This keeps light in the core as it travels down the fiber.

Core
The core is actually the light transmission element at the center of the optical fiber. This core is typically silica or glass. Light pulses travel through the fiber core.

4.2.3.3 Classic Firewall Configuration
Types of Fiber Media
Light pulses representing the transmitted data as bits on the media are generated by either:
- Lasers
- Light emitting diodes (LEDs)
Electronic semiconductor devices called photodiodes detect the light pulses and convert them to voltages. The laser light transmitted over fiber-optic cabling can damage the human eye. Care must be taken to avoid looking into the end of an active optical fiber.
Fiber-optic cables are broadly classified into two types:
- Single-mode fiber (SMF): Consists of a very small core and uses expensive laser technology to send a single ray of light, as shown in Figure 1. Popular in long-distance situations spanning hundreds of kilometers, such as those required in long haul telephony and cable TV applications.
- Multimode fiber (MMF): Consists of a larger core and uses LED emitters to send light pulses. Specifically, light from an LED enters the multimode fiber at different angles, as shown in Figure 2. Popular in LANs because they can be powered by low-cost LEDs. It provides bandwidth up to 10 Gb/s over link lengths of up to 550 meters.
One of the highlighted differences between multimode and single-mode fiber is the amount of dispersion. Dispersion refers to the spreading out of a light pulse over time. The more dispersion there is, the greater the loss of signal strength.
Single Mode
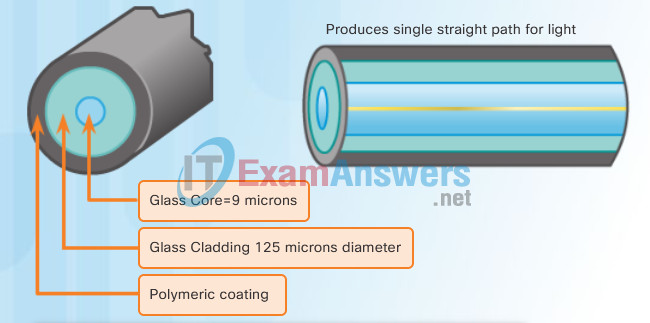
- Small core
- Less dispersion
- Suited for long distance applications
- Uses lasers as the light source
- Commonly used with campus backbones for distances of several thousand meters
Multimode
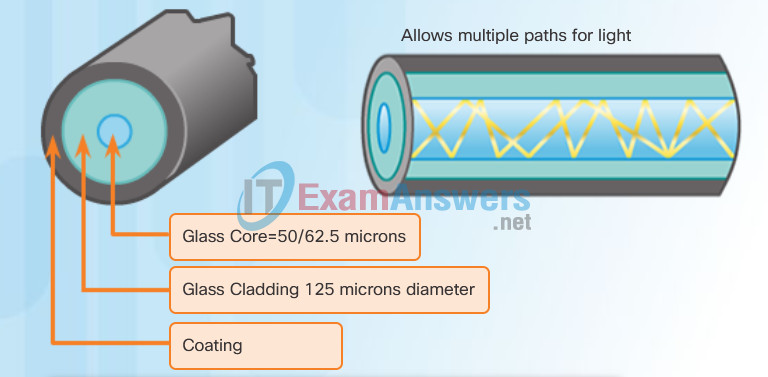
- Larger core than single mode cable
- Allows greater dispersion and therefore, loss of signal
- Suited for long distance applications, but shorter than single mode
- Uses LEDs as the light source
- Commonly used with LANs or distances of a couple hundred meters within a campus network
4.2.4 Firewalls in Network Design
4.2.4.1 Inside and Outside Networks
Properties of Wireless Media
Wireless media carry electromagnetic signals that represent the binary digits of data communications using radio or microwave frequencies.
Wireless media provides the greatest mobility options of all media, and the number of wireless-enabled devices continues to increase. As network bandwidth options increase, wireless is quickly gaining in popularity in enterprise networks.
The figure highlights various wireless-related symbols.
Wireless does have some areas of concern, including:
- Coverage area: Wireless data communication technologies work well in open environments. However, certain construction materials used in buildings and structures, and the local terrain, will limit the effective coverage.
- Interference: Wireless is susceptible to interference and can be disrupted by such common devices as household cordless phones, some types of fluorescent lights, microwave ovens, and other wireless communications.
- Security: Wireless communication coverage requires no access to a physical strand of media. Therefore, devices and users, not authorized for access to the network, can gain access to the transmission. Network security is a major component of wireless network administration.
- Shared medium: WLANs operate in half-duplex, which means only one device can send or receive at a time. The wireless medium is shared amongst all wireless users. The more users needing to access the WLAN simultaneously, results in less bandwidth for each user. Half-duplex is discussed later in this chapter.
Although wireless is increasing in popularity for desktop connectivity, copper and fiber are the most popular physical layer media for network deployments.

4.2.4.2 Demilitarized Zones
Types of Wireless Media
The IEEE and telecommunications industry standards for wireless data communications cover both the data link and physical layers. Click on each standard in the figure for more information.
Note: Other wireless technologies such as cellular and satellite communications can also provide data network connectivity. However, these wireless technologies are out of scope for this chapter.
In each of these standards, physical layer specifications are applied to areas that include:
- Data to radio signal encoding
- Frequency and power of transmission
- Signal reception and decoding requirements
- Antenna design and construction
Wi-Fi is a trademark of the Wi-Fi Alliance. Wi-Fi is used with certified products that belong to WLAN devices that are based on the IEEE 802.11 standards.
Wireless Standards

- Wi-Fi: Standard IEEE 802.11 – Wireless LAN (WLAN) technology, commonly referred to as Wi-Fi. WLAN uses a contention-based protocol known as Carrier Sense Multiple Access/Collision Avoidance (CSMA/CA). The wireless NIC must first listen before transmitting to determine if the radio channel is clear. If another wireless device is transmitting, then the NIC must wait until the channel is clear. CSMA/CA is discussed later in this chapter.
- Standard IEEE 802.15: Bluetooth – Wireless Personal Area Network (WPAN) standard, commonly known as “Bluetooth”, uses a device pairing process to communicate over distances from 1 to 100 meters.
- Standard IEEE 802.16: WiMAX – Commonly known as Worldwide Interoperability for Microwave Access (WiMAX), uses a point-to-multipoint topology to provide wireless broadband access.
4.2.4.3 ZPFs
Wireless LAN
A common wireless data implementation is enabling devices to connect wirelessly via a LAN. In general, a wireless LAN requires the following network devices:
- Wireless Access Point (AP): Concentrates the wireless signals from users and connects to the existing copper-based network infrastructure, such as Ethernet. Home and small business wireless routers integrate the functions of a router, switch, and access point into one device as shown in the figure.
- Wireless NIC adapters: Provide wireless communication capability to each network host.
As the technology has developed, a number of WLAN Ethernet-based standards have emerged. Care needs to be taken in purchasing wireless devices to ensure compatibility and interoperability.
The benefits of wireless data communications technologies are evident, especially the savings on costly premises wiring and the convenience of host mobility. Network administrators need to develop and apply stringent security policies and processes to protect wireless LANs from unauthorized access and damage.

Cisco WRP500 Wireless Broadband Router
4.2.4.4 Layered Defense
Packet Tracer – Connecting a Wired and Wireless LAN
When working in Packet Tracer, a lab environment, or a corporate setting, you should know how to select the appropriate cable and how to properly connect devices. This activity will examine device configurations in Packet Tracer, selecting the proper cable based on the configuration, and connecting the devices. This activity will also explore the physical view of the network in Packet Tracer.

4.3 Zone-Based Policy Firewalls
4.3.1 ZPF Overview
4.3.1.1 Benefits of a ZPF
The Data Link Layer
The data link layer of the OSI model (Layer 2), as shown in Figure 1, is responsible for:
- Allowing the upper layers to access the media
- Accepting Layer 3 packets and packaging them into frames
- Preparing network data for the physical network
- Controlling how data is placed and received on the media
- Exchanging frames between nodes over a physical network media, such as UTP or fiber-optic
- Receiving and directing packets to an upper layer protocol
- Performing error detection
The Layer 2 notation for network devices connected to a common media is called a node. Nodes build and forward frames. As shown in Figure 2, the OSI data link layer is responsible for the exchange of Ethernet frames between source and destination nodes over a physical network media.
The data link layer effectively separates the media transitions that occur as the packet is forwarded from the communication processes of the higher layers. The data link layer receives packets from and directs packets to an upper layer protocol, in this case IPv4 or IPv6. This upper layer protocol does not need to be aware of which media the communication will use.
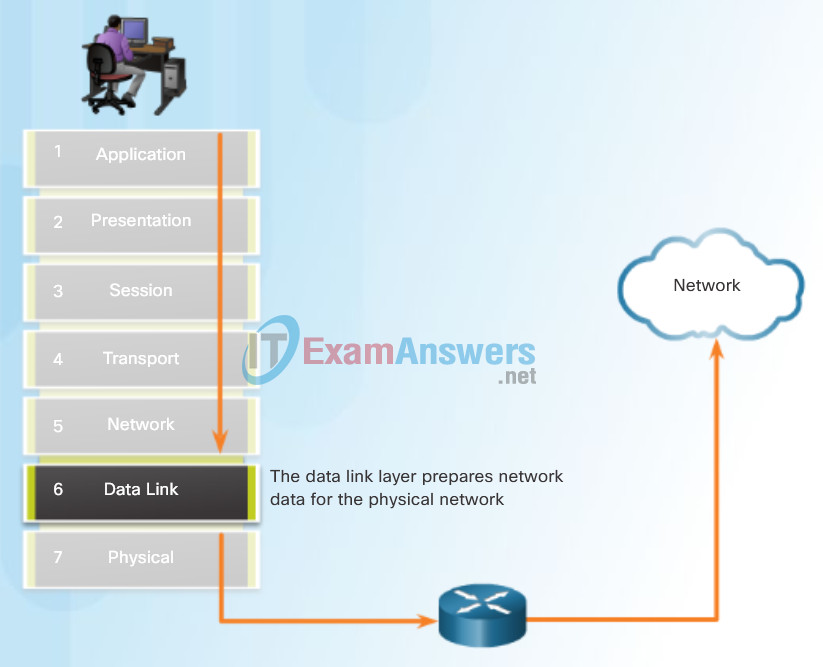
Data Link Layer
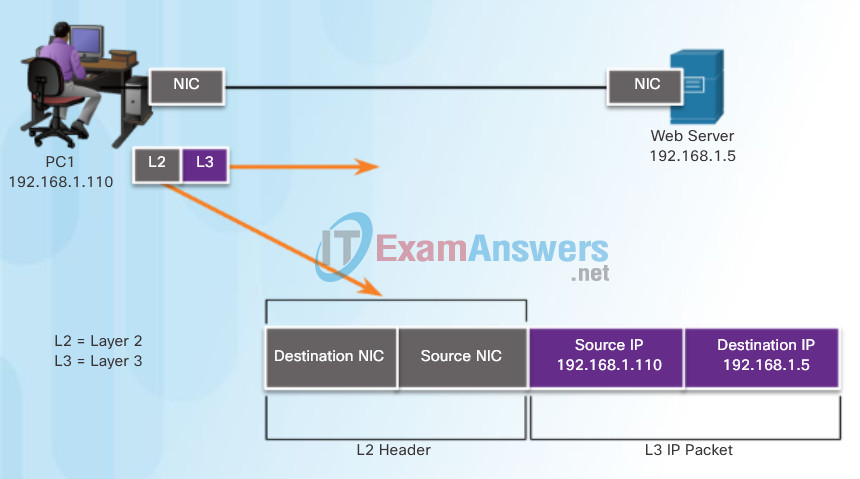
Layer 2 Data Link Addresses
4.3.1.2 ZPF Design
Data Link Sublayers
The data link layer is divided into two sublayers:
- Logical Link Control (LLC) – This upper sublayer communicates with the network layer. It places information in the frame that identifies which network layer protocol is being used for the frame. This information allows multiple Layer 3 protocols, such as IPv4 and IPv6, to utilize the same network interface and media.
- Media Access Control (MAC) – This lower sublayer defines the media access processes performed by the hardware. It provides data link layer addressing and access to various network technologies.
The figure illustrates how the data link layer is separated into the LLC and MAC sublayers. The LLC communicates with the network layer while the MAC sublayer allows various network access technologies. For instance, the MAC sublayer communicates with Ethernet LAN technology to send and receive frames over copper or fiber-optic cable. The MAC sublayer also communicates with wireless technologies such as Wi-Fi and Bluetooth to send and receive frames wirelessly.
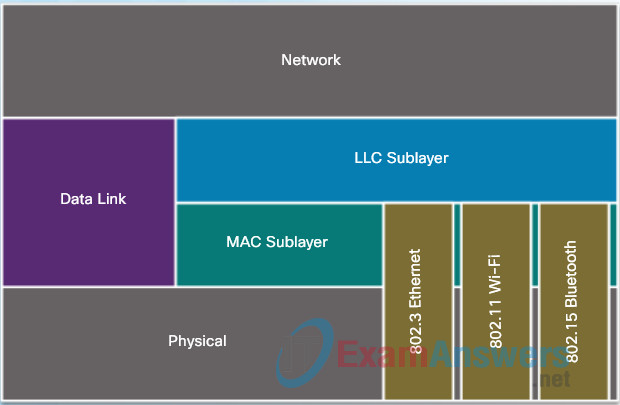
4.3.1.3 Activity – Compare Classic Firewall and ZPF Operation
Media Access Control
Layer 2 protocols specify the encapsulation of a packet into a frame and the techniques for getting the encapsulated packet on and off each medium. The technique used for getting the frame on and off the media is called the media access control method.
As packets travel from the source host to the destination host, they typically traverse over different physical networks. These physical networks can consist of different types of physical media such as copper wires, optical fibers, and wireless consisting of electromagnetic signals, radio and microwave frequencies, and satellite links.
Without the data link layer, network layer protocols such as IP, would have to make provisions for connecting to every type of media that could exist along a delivery path. Moreover, IP would have to adapt every time a new network technology or medium was developed. This process would hamper protocol and network media innovation and development. This is a key reason for using a layered approach to networking.
The animation in the figure provides an example of a PC in Paris connecting to a laptop in Japan. Although the two hosts are communicating using IP exclusively, it is likely that numerous data link layer protocols are being used to transport the IP packets over various types of LANs and WANs. Each transition at a router may require a different data link layer protocol for transport on a new medium.

4.3.2 ZPF Operation
4.3.2.1 ZPF Actions
- Inspect – Configures Cisco IOS stateful packet inspections.
- Drop – Analogous to a deny statement in an ACL. A log option is available to log the rejected packets.
- Pass – Analogous to a permit statement in an ACL. The pass action does not track the state of connections or sessions within the traffic.
4.3.2.2 Rules for Transit Traffic
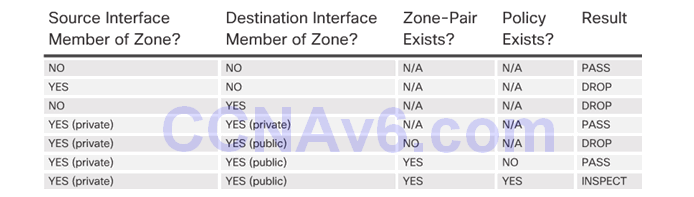
4.3.2.3 Rules for Traffic to the Self Zone
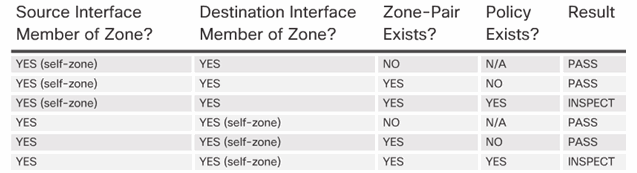
4.3.2.4 Activity – Rules for Transit Traffic
4.3.3 Configuring a ZPF
4.3.3.1 Configure ZPF
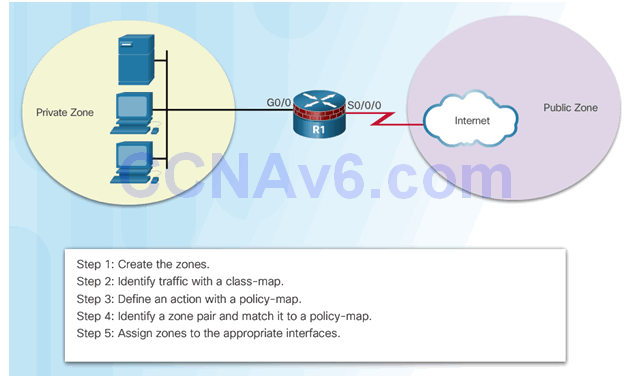
4.3.3.2 Create Zones
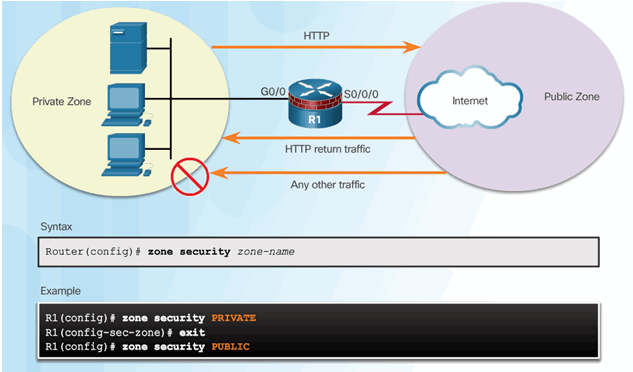
4.3.3.3 Identify Traffic
Command Syntax for class-map
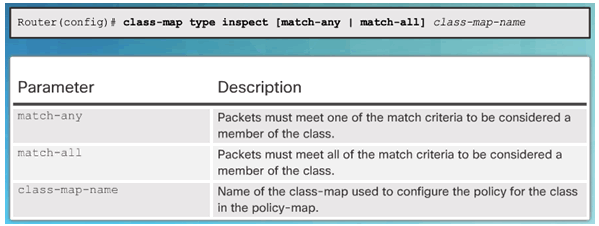
Sub-Configuration Command Syntax for class-map
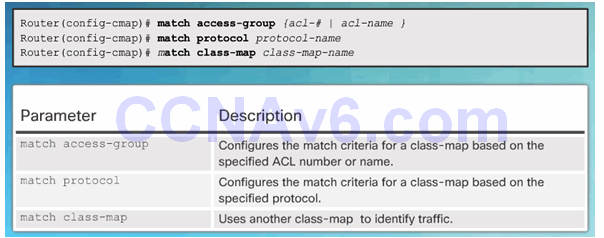
Example class-map Configuration
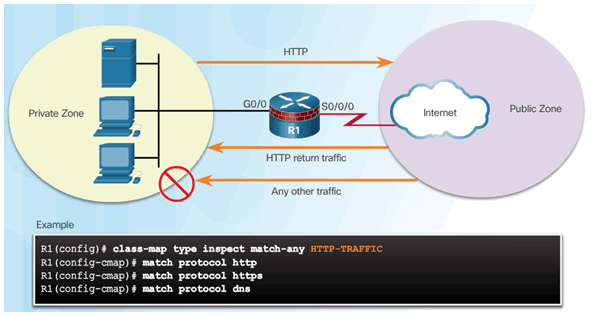
4.3.3.4 Define an Action
Command Syntax for policy-map
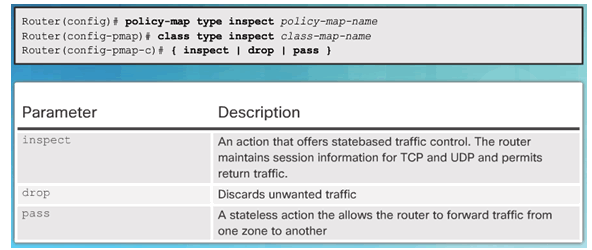
Example policy-map Configuration
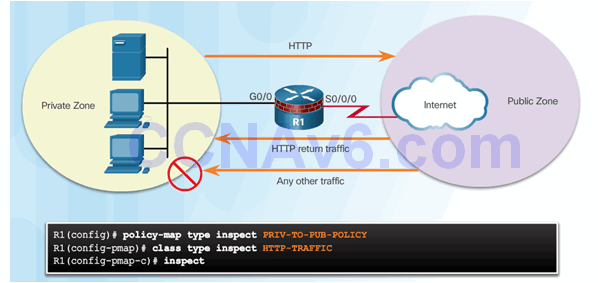
4.3.3.5 Identify a Zone-Pair and Match to a Policy
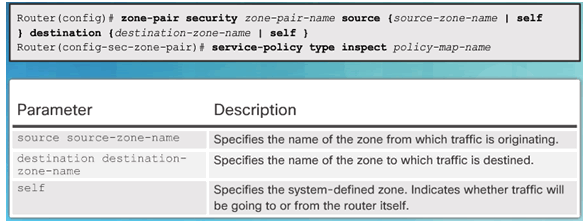
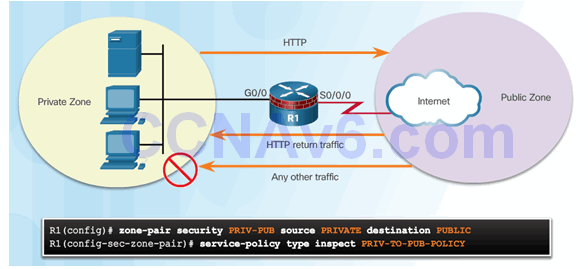
Command Syntax for zone-pair and service-policy
Example service-policy Configuration
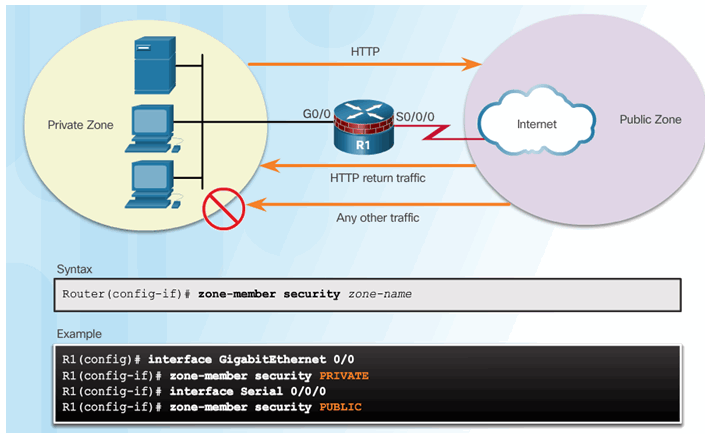
4.3.3.6 Assign Zones to Interfaces
4.3.3.7 Verify a ZPF Configuration
Verification commands:
- show run | begin class-map
- show policy-map type inspect zone-pair sessions
- show class-map type inspect
- show zone security
- show zone-pair security
- show policy-map type inspect
4.3.3.8 ZPF Configuration Considerations
- No filtering is applied for intra-zone traffic
- Only one zone is allowed per interface.
- No Classic Firewall and ZPF configuration on same interface.
- If only one zone member is assigned, all traffic is dropped.
- Only explicitly allowed traffic is forwarded between zones.
- Traffic to the self zone is not filtered.
4.3.3.9 Video Demonstration – ZPFs
4.4 Summary
4.4.1 Conclusion
4.4.1.1 Packet Tracer – Configuring a ZPF
4.4.1.1 Packet Tracer – Configuring a ZPF
Controlling Access to the Media
Regulating the placement of data frames onto the media is controlled by the media access control sublayer.
Media access control is the equivalent of traffic rules that regulate the entrance of motor vehicles onto a roadway. The absence of any media access control would be the equivalent of vehicles ignoring all other traffic and entering the road without regard to the other vehicles. However, not all roads and entrances are the same. Traffic can enter the road by merging, by waiting for its turn at a stop sign, or by obeying signal lights. A driver follows a different set of rules for each type of entrance.
In the same way, there are different methods to regulate placing frames onto the media. The protocols at the data link layer define the rules for access to different media. These media access control techniques define if and how the nodes share the media.
The actual media access control method used depends on:
- Topology – How the connection between the nodes appears to the data link layer.
- Media sharing – How the nodes share the media. The media sharing can be point-to-point, such as in WAN connections, or shared such as in LAN networks.
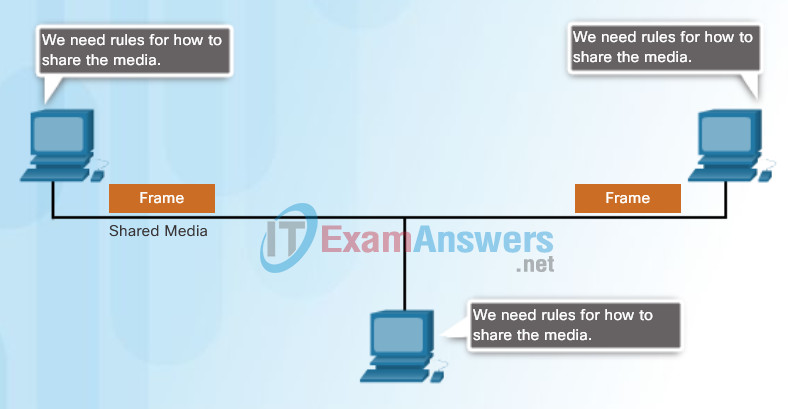
Sharing the Media
4.4.1.2 Lab – Configuring ZPFs
4.4.1.2 Lab – Configuring ZPFs
Physical and Logical Topologies
The topology of a network is the arrangement or relationship of the network devices and the interconnections between them. LAN and WAN topologies can be viewed in two ways:
- Physical topology – Refers to the physical connections and identifies how end devices and infrastructure devices such as routers, switches, and wireless access points are interconnected. Physical topologies are usually point-to-point or star. See Figure 1.
- Logical topology – Refers to the way a network transfers frames from one node to the next. This arrangement consists of virtual connections between the nodes of a network. These logical signal paths are defined by data link layer protocols. The logical topology of point-to-point links is relatively simple while shared media offers different access control methods. See Figure 2.
The data link layer “sees” the logical topology of a network when controlling data access to the media. It is the logical topology that influences the type of network
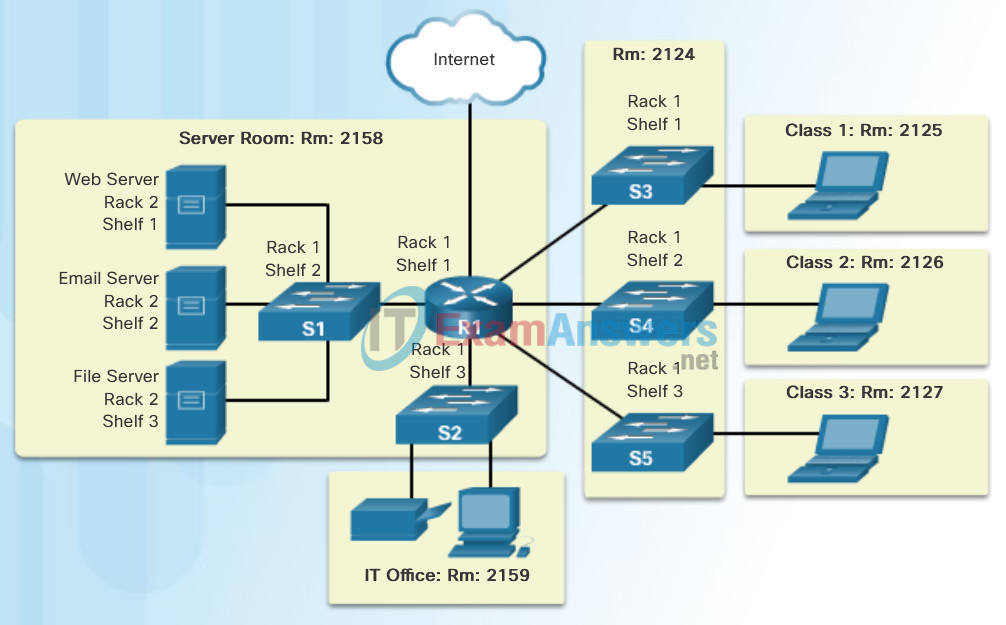
Physical topology
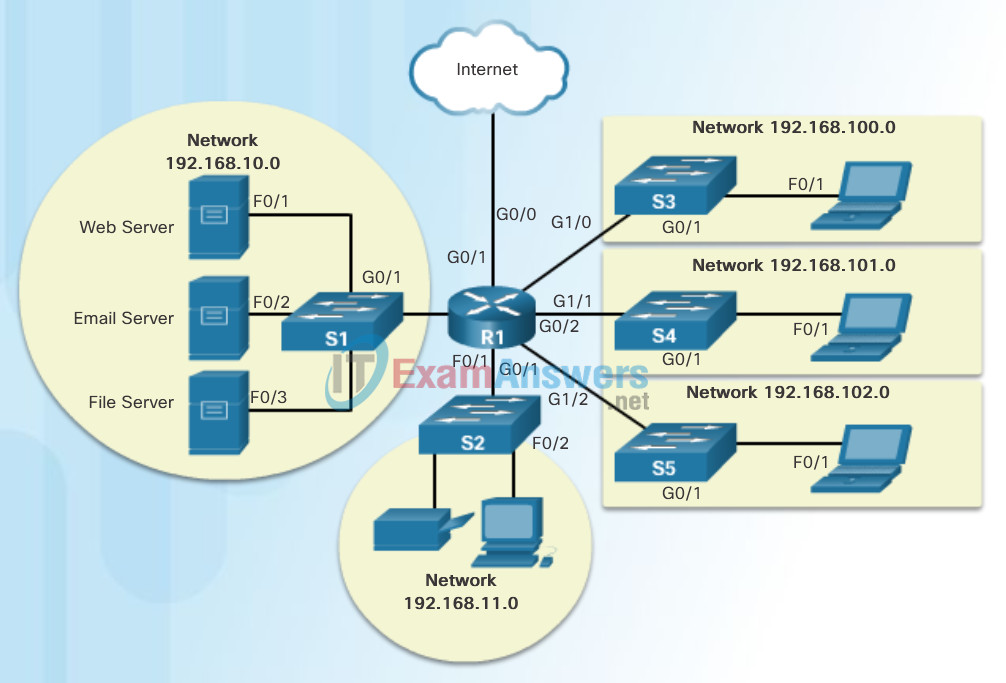
Logical topology
