OS and Endpoint Security Checkpoint Exam – Endpoint Security (ESec) Module 7 – 10 Group Exam Answers (Module Group Exam 2)
1. What principle prevents the disclosure of information to unauthorized people, resources, and processes?
- confidentiality
- integrity
- accounting
- availability
- nonrepudiation
Explanation: The security principle of confidentiality refers to the prevention of the disclosure of information to unauthorized people, resources, and processes.
2. A user is proposing the purchase of a patch management solution for a company. The user wants to give reasons why the company should spend money on a solution. What benefits does patch management provide? (Choose three.)
- Administrators can approve or deny patches.
- Updates can be forced on systems immediately.
- Patches can be chosen by the user.
- Computers require a connection to the Internet to receive patches.
- Updates cannot be circumvented.
- Patches can be written quickly.
Explanation: A centralized patch management system can speed up deployment of patches and automate the process. Other good reasons to using an automated patch update service include the following:
– Administrators control the update process.
– Reports are generated.
– Updates are provided from a local server.
– Users cannot circumvent the update process.
3. What are two advantages of the NTFS file system compared with FAT32? (Choose two.)
- NTFS allows faster access to external peripherals such as a USB drive.
- NTFS supports larger files.
- NTFS provides more security features.
- NTFS allows faster formatting of drives.
- NTFS is easier to configure.
- NTFS allows the automatic detection of bad sectors.
Explanation: The file system has no control over the speed of access or formatting of drives, and the ease of configuration is not file system-dependent.
4. What are three access control security services? (Choose three.)
- access
- availability
- accounting
- authentication
- repudiation
- authorization
Explanation: This question refers to AAA authentication, authorization, and accountability.
5. What three tasks are accomplished by a comprehensive security policy? (Choose three.)
- is not legally binding
- gives security staff the backing of management
- vagueness
- defines legal consequences of violations
- useful for management
- sets rules for expected behavior
Explanation: The security policy of an organization accomplishes several tasks:
- It demonstrates the commitment to security by an organization.
- It sets the rules for expected behavior.
- It ensures consistency in system operations, and software and hardware acquisition use and maintenance.
- It defines the legal consequences of violations.
- It gives security staff the backing of management.
6. In the Linux shell, which character is used between two commands to instruct the shell to combine and execute these two commands in sequence?
Explanation: In the Linux shell, several commands can be combined to perform a complex task. This technique is known as piping. The piping process is indicated by inserting the character “|” between two consecutive commands.
7. A PC user issues the netstat command without any options. What is displayed as the result of this command?
- a list of all established active TCP connections
- a local routing table
- a historical list of successful pings that have been sent
- a network connection and usage report
Explanation: When used by itself (without any options), the netstat command will display all the active TCP connections that are available.
8. Why would a network administrator choose Linux as an operating system in the Security Operations Center (SOC)?
- More network applications are created for this environment.
- It is easier to use than other operating systems.
- The administrator has more control over the operating system.
- It is more secure than other server operating systems.
Explanation: There are several reasons why Linux is a good choice for the SOC.
Linux is open source.
The command line interface is a very powerful environment.
The user has more control over the operating system.
Linux allows for better network communication control.
9. What are three states of data during which data is vulnerable? (Choose three.)
- data in-transit
- data decrypted
- data in-process
- data encrypted
- purged data
- stored data
Explanation: A cybersecurity specialist must be aware of each of the three states of data to effectively protect data and information. Purged data was stored data. Encrypted and decrypted data can be in any of the three states.
10. Which two options are window managers for Linux? (Choose two.)
- PenTesting
- KDE
- File Explorer
- Kali
- Gnome
Explanation: The X Window System provides the basic framework for a GUI, but the GUI itself varies greatly between different distributions. Two window managers are Gnome and KDE.
11. What term describes a set of software tools designed to increase the privileges of a user or to grant access to the user to portions of the operating system that should not normally be allowed?
- package manager
- rootkit
- penetration testing
- compiler
Explanation: A rootkit is used by an attacker to secure a backdoor to a compromised computer, grant access to portions of the operating system normally not permitted, or increase the privileges of a user.
12. What is the difference between an HIDS and a firewall?
- An HIDS blocks intrusions, whereas a firewall filters them.
- An HIDS monitors operating systems on host computers and processes file system activity. Firewalls allow or deny traffic between the computer and other systems.
- A firewall allows and denies traffic based on rules and an HIDS monitors network traffic.
- A firewall performs packet filtering and therefore is limited in effectiveness, whereas an HIDS blocks intrusions.
- An HIDS works like an IPS, whereas a firewall just monitors traffic.
Explanation: In order to monitor local activity an HIDS should be implemented. Network activity monitors are concerned with traffic and not operating system activity.
13. Consider the result of the ls -l command in the Linux output below. What are the file permissions assigned to the sales user for the analyst.txt file?
ls –l analyst.txt
-rwxrw-r-- sales staff 1028 May 28 15:50 analyst.txt
- read, write, execute
- read only
- read, write
- write only
Explanation: The file permissions are always displayed in the User, Group and Other order. In the example displayed, the file has the following permissions:
The dash (-) means that this is a file. For directories, the first dash would replaced with a “d”.
The first set of characters is for user permission (rwx). The user, sales, who owns the file can read, write and execute the file.
The second set of characters is for group permissions (rw-). The group, staff, who owns the file can read and write to the file.
The third set of characters is for any other user or group permissions (r–). Any other user or group on the computer can only read the file.
14. Match the Linux command to the function. (Not all options are used.)
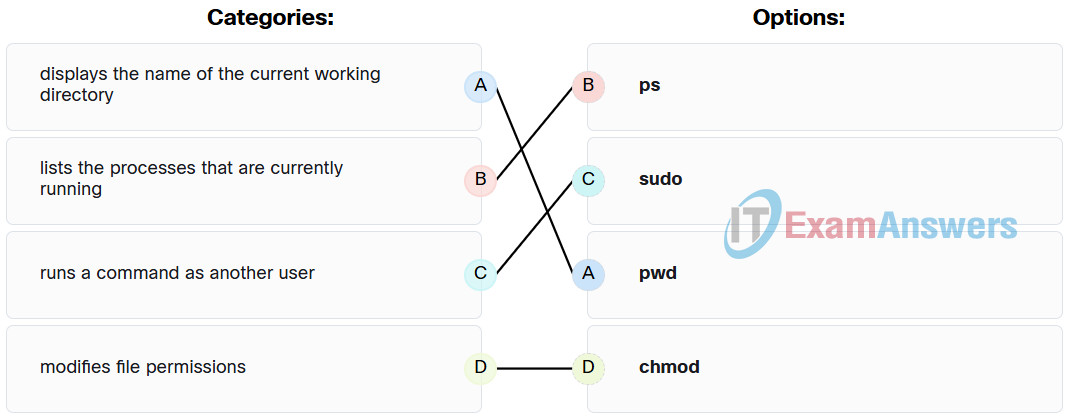
Explanation: Place the options in the following order:
| Displays the name of the current working directory |
pwd |
| Runs a command as another user |
sudo |
| Modifies file permissions |
chmod |
| Shuts down the system |
No answer available |
| Lists the processes that are currently running |
ps |
15. Which statement describes the term iptables?
- It is a file used by a DHCP server to store current active IP addresses.
- It is a DHCP application in Windows.
- It is a rule-based firewall application in Linux.
- It is a DNS daemon in Linux.
Explanation: Iptables is an application that allows Linux system administrators to configure network access rules.
16. On a Windows host, which tool can be used to create and maintain blacklists and whitelists?
- Group Policy Editor
- Local Users and Groups
- Task Manager
- Computer Management
Explanation: In Windows, blacklisting and whitelisting settings can be managed through the Group Policy Editor.
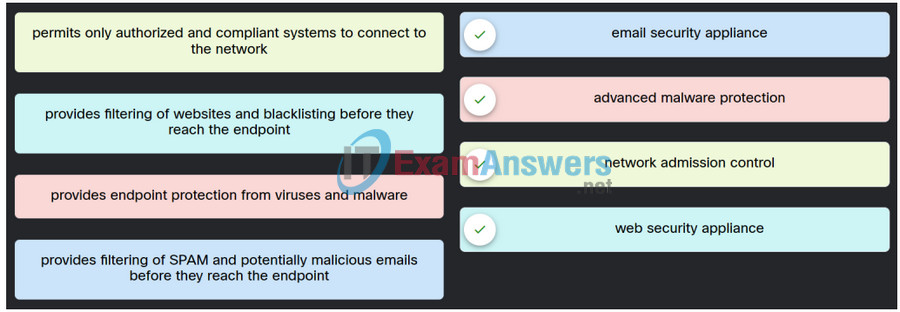
17. Match the network-based anti-malware solution to the function. (Not all options are used.)
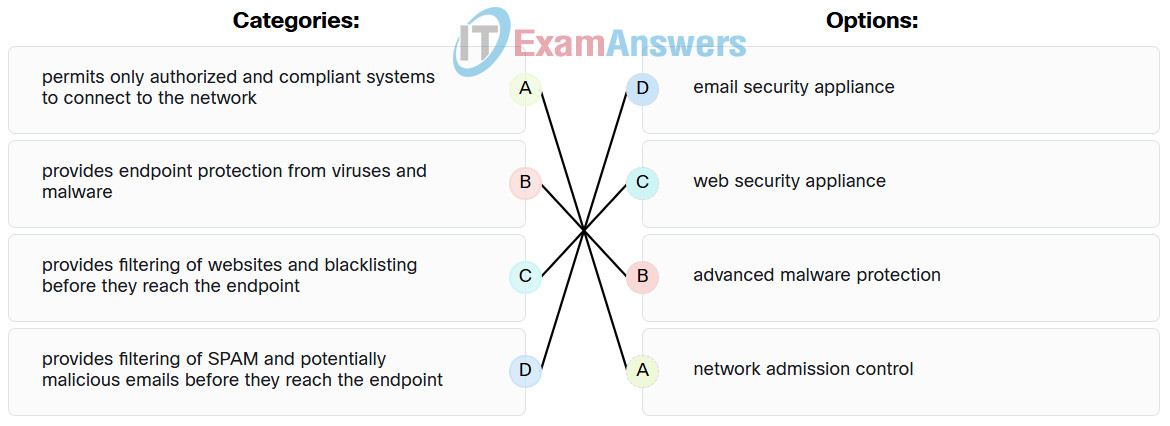
Explanation: Place the options in the following order:
| Provides filtering of SPAM and potentially malicious emails before they reach the endpoint |
Email security appliance |
| Provides filtering of websites and blacklisting before they reach the endpoint |
Web security appliance |
| Permits only authorized and compliant systems to connect to the network |
Network admission control |
| Provides dynamic IP addresses to authenticated endpoints |
No answer available |
| Provides endpoint protection from viruses and malware |
Advanced malware protection |
18. Match typical Linux log files to the function.
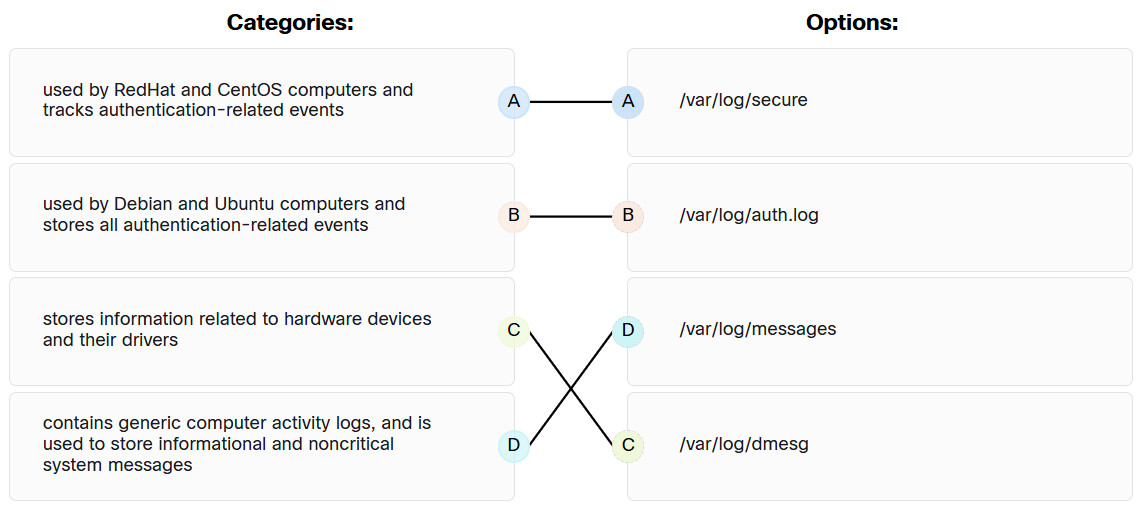
Endpoint Security (ESec) Module 7 – 10 Group Exam 18
Explanation: Place the options in the following order:
| Used by RedHat and CentOS computers and tracks authentication-related events |
/var/log/secure |
| Contains generic computer activity logs, and is used to store informational and noncritical system messages |
/var/log/messages |
| Stores information related to hardware devices and their drivers |
/var/log/dmesg |
| Used by Debian and Ubuntu computers and stores all authentication-related events |
/var/log/auth.log |
19. Match the antimalware approach to the description.
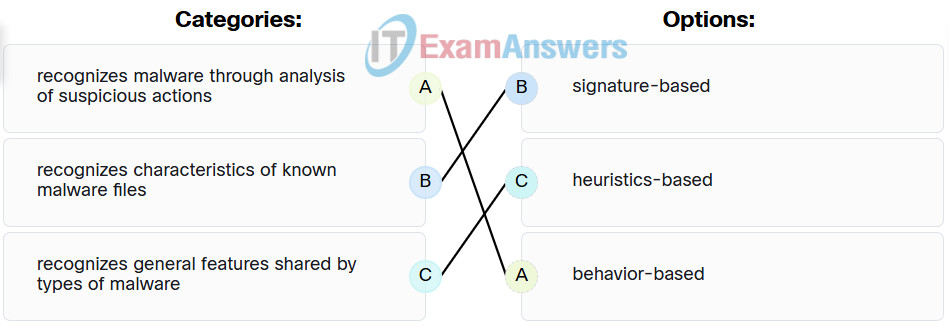
Endpoint Security (ESec) Module 7 – 10 Group Exam 19
Explanation: Place the options in the following order:
| Recognizes characteristics of known malware files |
signature-based |
| Recognizes general features shared by types of malware |
heuristics-based |
| Recognizes malware through analysis of suspicious actions |
behavior-based |
20. A client device has initiated a secure HTTP request to a web browser. Which well-known port address number is associated with the destination address?
Explanation: Port numbers are used in TCP and UDP communications to differentiate between the various services running on a device. The well-known port number used by HTTPs is port 443.
21. Which statement describes the Cisco Threat Grid Glovebox?
- It is a host-based intrusion detection system (HIDS) solution to fight against malware.
- It is a firewall appliance.
- It is a sandbox product for analyzing malware behaviors.
- It is a network-based IDS/IPS.
Explanation: Cisco ThreatGrid Glovebox is a sandbox product for analyzing malware behaviors.
22. Why is Kali Linux a popular choice in testing the network security of an organization?
- It is a network scanning tool that prioritizes security risks.
- It can be used to test weaknesses by using only malicious software.
- It is an open source Linux security distribution containing many penetration tools.
- It can be used to intercept and log network traffic.
Explanation: Kali is an open source Linux security distribution that is commonly used by IT professionals to test the security of networks.
23. Match the Windows system tool with the description. (Not all options are used.)
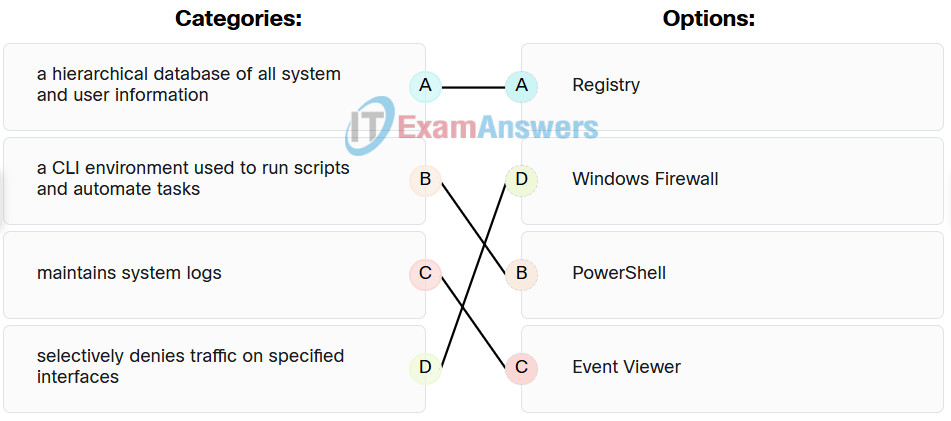
Endpoint Security (ESec) Module 7 – 10 Group Exam 23
Explanation: Place the options in the following order:
| Provides virus and spyware protection |
No answer available |
| A hierarchical database of all system and user information |
Regristry |
| Selectively denies traffic on specified interfaces |
Windows Firewall |
| A CLI environment used to run scripts and automate tasks |
PowerShell |
| Maintains system logs |
Event Viewer |
| Provides information on system resources and processes |
No answer available |
24. What three methods help to ensure system availability? (Choose three.)
- system backups
- system resiliency
- equipment maintenance
- fire extinguishers
- up-to-date operating systems
- integrity checking
Explanation: Methods used to ensure high availability include system redundancy, system backups, increased system resiliency, equipment maintenance, operating system and software updates and patches, and proactive plans for swift recovery from unforeseen disasters.
25. What would be a reason for a computer user to use the Task Manager Performance tab?
- to check the CPU usage of the PC
- to increase the performance of the CPU
- to view the services that are currently running on the PC
- to view the processes that are running and end a process if needed
Explanation: The Performance tab is commonly used to check current computer performance. Two key areas that are shown are memory and CPU usage.
26. What is the function of the kernel of an operating system?
- It provides a user interface that allows users to request a specific task.
- It is an application that allows the initial configuration of a Cisco device.
- The kernel provisions hardware resources to meet software requirements.
- The kernel links the hardware drivers with the underlying electronics of a computer.
Explanation: Operating systems function with a shell, a kernel, and the hardware. The shell interfaces with the users, allowing them to request specific tasks from the device. The kernel provisions resources from the hardware to meet software requirements. The hardware functions by using drivers and their underlying electronics. The hardware represents the physical components of the device.
27. A security specialist is asked for advice on a security measure to prevent unauthorized hosts from accessing the home network of employees. Which measure would be most effective?
- Implement intrusion detection systems.
- Implement a firewall.
- Implement RAID.
- Implement a VLAN.
Explanation: Protecting data confidentiality requires an understanding of the technologies used to protect data in all three data states.
28. Match the Windows command to the description.
29. A user creates a file with .ps1 extension in Windows. What type of file is it?
- PowerShell cmdlet
- PowerShell function
- PowerShell script
- PowerShell documentation
Explanation: The types of commands that PowerShell can execute include the following:
- cmdlets – perform an action and return an output or object to the next command that will be executed
- PowerShell scripts – files with a .ps1 extension that contain PowerShell commands that are executed
- PowerShell functions – pieces of code that can be referenced in a script
30. Match the Windows command to the description.
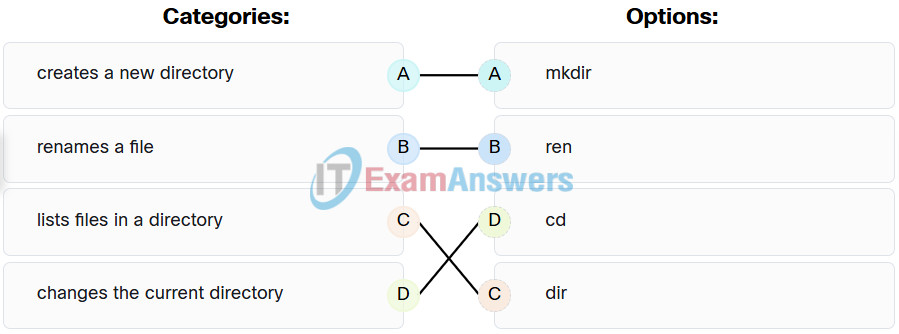
Explanation:
- dir ~~> lists files in a directory
- mkdir ~~> creates a new directory
- cd ~~> changes the current directory
- ren ~~> renames a file
Which statement describes the policy-based intrusion detection approach?
- It compares the signatures of incoming traffic to a known intrusion database.
- It compares the operations of a host against well-defined security rules.
- It compares the antimalware definitions to a central repository for the latest updates.
- It compares the behaviors of a host to an established baseline to identify potential intrusion.
Explanation: With the anomaly-based intrusion detection approach, a set of rules or policies are applied to a host. Violation of these policies is interpreted to be the result of a potential intrusion.








Which statement describes the policy-based intrusion detection approach?
I added. Thank you.