9.5.2 Endpoint Protection Quiz Answers
1. Which antimalware software approach can recognize various characteristics of known malware files to detect a threat?
- signature-based
- routing-based
- heuristics-based
- behavior-based
Explanation: Antimalware programs may detect viruses using three different approaches:
- signature-based – by recognizing various characteristics of known malware files
- heuristics-based – by recognizing general features shared by various types of malware
- behavior-based – through analysis of suspicious activities
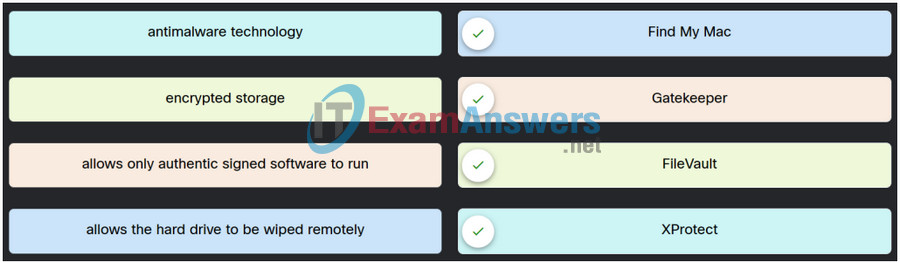
2. Match the Apple system security feature to its purpose.
3. Which device in a LAN infrastructure is susceptible to MAC address-table overflow and spoofing attacks?
- firewall
- workstation
- switch
- server
Explanation: Switches are LAN infrastructure devices interconnecting endpoints. They are susceptible to LAN-related attacks including MAC address-table overflow attacks, spoofing attacks, LAN storm attacks, STP manipulation attacks, and VLAN attacks.
4. In most host-based security suites, which function provides robust logging of security-related events and sends logs to a central location?
- anti-phishing
- safe browsing
- telemetry
- intrusion detection and prevention
Explanation: The telemetry functionality in most host-based security suites provides robust logging functionality and submits logs to a central location for analysis.
5. Which technology might increase the security challenge to the implementation of IoT in an enterprise environment?
- data storage
- CPU processing speed
- cloud computing
- network bandwidth
Explanation: With cloud computing, boundaries of enterprise networks are expanded to include locations on the Internet for which the enterprises are not responsible. Malicious software might access the internal network endpoints to attack internal networks.
6. Which statement describes agentless antivirus protection?
- The antivirus protection is provided by the ISP.
- Host-based antivirus systems provide agentless antivirus protection.
- The antivirus protection is provided by the router that is connected to a cloud service.
- Antivirus scans are performed on hosts from a centralized system.
Explanation: Host-based antivirus protection is also known as agent-based. Agent-based antivirus runs on every protected machine. Agentless antivirus protection performs scans on hosts from a centralized system.
7. Which HIDS is an open-source based product?
- OSSEC
- Tripwire
- Cisco AMP
- AlienVault USM
Explanation: The Open Source HIDS SECurity (OSSEC) software is an open-source HIDS that uses a central manager server and agents that are installed on the hosts that are to be monitored.
8. In Windows Firewall, when is the Domain profile applied?
- when the host is connected to a trusted network such as an internal business network
- when the host is connected to an isolated network from the Internet by another security device
- when the host accesses the Internet
- when the host checks emails from an enterprise email server
Explanation: The Domain profile in Windows Firewall configuration is for connections to a trusted network, such as a business network, that is assumed to have an adequate security infrastructure.
9. What is a host-based intrusion detection system (HIDS)?
- It combines the functionalities of antimalware applications with firewall protection.
- It is an agentless system that scans files on a host for potential malware.
- It identifies potential attacks and sends alerts but does not stop the traffic.
- It detects and stops potential direct attacks but does not scan for malware.
Explanation: A current HIDS is a comprehensive security application that combines the functionalities of antimalware applications with firewall protection. An HIDS not only detects malware but also prevents it from executing. Because the HIDS runs directly on the host, it is considered an agent-based system.
10. As described by the SANS Institute, which attack surface includes the exploitation of vulnerabilities in wired and wireless protocols used by IoT devices?
- software attack surface
- Internet attack surface
- human attack surface
- network attack surface
Explanation: The SANS Institute describes three components of the attack surface:
- Network Attack Surface – exploitation of vulnerabilities in networks
- Software Attack Surface – exploitation of vulnerabilities in web, cloud, or host-based software applications
- Human Attack Surface – exploitation of weaknesses in user behavior
11. Which statement describes the term attack surface?
- It is the group of hosts that experiences the same attack.
- It is the total number of attacks toward an organization within a day.
- It is the network interface where attacks originate.
- It is the total sum of vulnerabilities in a system that is accessible to an attacker.
Explanation: An attack surface is the total sum of the vulnerabilities in a system that is accessible to an attacker. The attack surface can consist of open ports on servers or hosts, software that runs on Internet-facing servers, wireless network protocols, and even users.
12. As described by the SANS Institute, which attack surface includes the use of social engineering?
- network attack surface
- human attack surface
- Internet attack surface
- software attack surface
Explanation: The SANS Institute describes three components of the attack surface:
- Network Attack Surface – exploitation of vulnerabilities in networks
- Software Attack Surface – exploitation of vulnerabilities in web, cloud, or host-based software applications
- Human Attack Surface – exploitation of weaknesses in user behavior
13. Which security endpoint setting would be used by a security analyst to determine if a computer has been configured to prevent a particular application from running?
- services
- whitelisting
- blacklisting
- baselining
Explanation: Blacklisting can be used on a local system or updated on security devices such as a firewall. Blacklists can be manually entered or obtained from a centralized security system. Blacklists are applications that are prevented from executing because they pose a security risk to the individual system and potentially the company.
14. What can you do to ensure that network operating software remains secure? (Choose three.)
- Develop a policy to address application software and operating system updates
- Implement data classification standards
- Install patches and updates regularly
- Conduct software testing prior to launch
Explanation: To secure operating systems against threats, policies that address application system and operating system updates should be implemented so that patches and operating system updates are installed regularly.
15. Which type of technology can prevent malicious software from displaying unwanted popup ads on a device?
- Adware protection
- Antivirus protection
- Spyware protection
Explanation: Adware protection is software that can can be installed on a computer system to prevent popup ads from displaying.
16. What type of lock is recommended to secure an office door?
- Cable lock
- Cipher lock
- Security cage
- Keyed entry lock
Explanation: A cipher lock uses buttons that are pressed in a given sequence to open the door. It can be programmed so that a user’s code may only work during certain days or times. It can also keep a record of when the door opened, and the code used to open it.

