1. Which security measure is typically found both inside and outside a data center facility?
- a gate
- biometrics access
- exit sensors
- security traps
- continuous video surveillance
2. Which statement accurately characterizes the evolution of threats to network security?
- Threats have become less sophisticated while the technical knowledge needed by an attacker has grown.
- Early Internet users often engaged in activities that would harm other users.
- Internal threats can cause even greater damage than external threats.
- Internet architects planned for network security from the beginning.
3. Which security technology is commonly used by a teleworker when accessing resources on the main corporate office network?
- SecureX
- IPS
- VPN
- biometric access
4. A security intern is reviewing the corporate network topology diagrams before participating in a security review. Which network topology would commonly have a large number of wired desktop computers?
- cloud
- CAN
- data center
- SOHO
5. In the video that describes the anatomy of an attack, a threat actor was able to gain access through a network device, download data, and destroy it. Which flaw allowed the threat actor to do this?
- a flat network with no subnets or VLANs
- improper physical security to gain access to the building
- lack of a strong password policy
- open ports on the firewall
6. Which type of network commonly makes use of redundant air conditioning and a security trap?
- cloud
- WAN
- data center
- CAN
7. Which technology is used to secure, monitor, and manage mobile devices?
- VPN
- rootkit
- ASA firewall
- MDM
8. When considering network security, what is the most valuable asset of an organization?
- customers
- financial resources
- personnel
- data
9. What is hyperjacking?
- adding outdated security software to a virtual machine to gain access to a data center server
- using processors from multiple computers to increase data processing power
- overclocking the mesh network which connects the data center servers
- taking over a virtual machine hypervisor as part of a data center attack
10. Which resource is affected due to weak security settings for a device owned by the company, but housed in another location?
- cloud storage device
- hard copy
- removable media
- social networking
11. Refer to the exhibit. An IT security manager is planning security updates on this particular network. Which type of network is displayed in the exhibit and is being considered for updates?
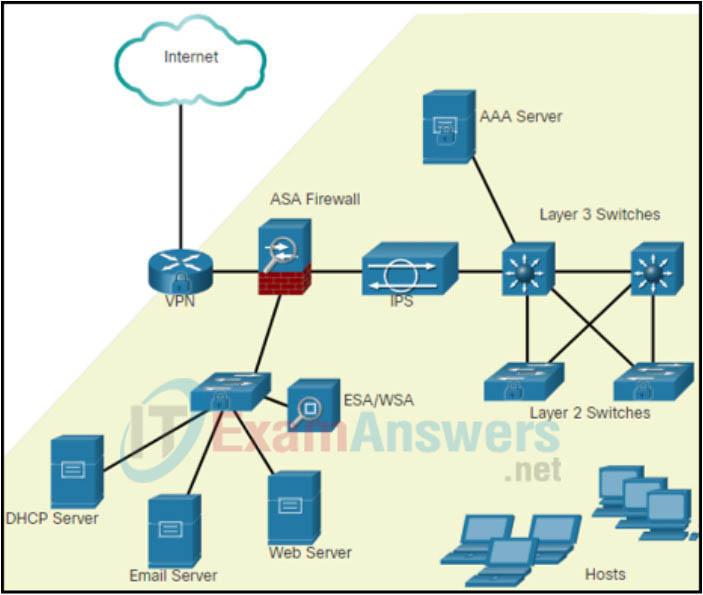
- WAN
- CAN
- data center
- SOHO
