Network Defense (NetDef) Module 1 – 3 Group Exam – Checkpoint Exam: Principles, Practices, and Processes of Network Defense
How to find: Press “Ctrl + F” in the browser and fill in whatever wording is in the question to find that question/answer. If the question is not here, find it in Questions Bank.
NOTE: If you have the new question on this test, please comment Question and Multiple-Choice list in form below this article. We will update answers for you in the shortest time. Thank you! We truly value your contribution to the website.
1. Which security management function is concerned with the inventory and control of hardware and software configurations of systems?
- configuration management
- vulnerability management
- risk management
- asset management
Explanation: Security risks can be reduced through secure device configuration. Configuration management addresses the inventory and control of hardware and software configurations of systems.
2. What device would be used as a second line of defense in a defense-in-depth approach?
- edge router
- internal router
- switch
- firewall
Explanation: In a defense-in-depth approach, the edge router would form the first line of defense. The firewall would be the second line of defense followed by the internal router making up the third line of defense.
3. Which security measure is typically found both inside and outside a data center facility?
- biometrics access
- continuous video surveillance
- a gate
- exit sensors
- security traps
Explanation: Continuous video surveillance is a security measure found both inside and outside a data center facility. A gate provides outside perimeter security. Security traps, biometrics access, and exit sensors provide inside perimeter security.
4. What is a characteristic of the security artichoke, defense-in-depth approach?
- Threat actors can easily compromise all layers safeguarding the data or systems.
- Each layer has to be penetrated before the threat actor can reach the target data or system.
- Threat actors no longer have to peel away each layer before reaching the target data or system.
- Threat actors can no longer penetrate any layers safeguarding the data or system.
Explanation: In the security artichoke, defense-in-depth approach not every layer needs to be penetrated by the threat actor in order to get to the data or systems. Each layer provides a layer of protection while simultaneously providing a path to attack.
5. Which two options are security best practices that help mitigate BYOD risks? (Choose two.)
- Only turn on Wi-Fi when using the wireless network.
- Only allow devices that have been approved by the corporate IT team.
- Use paint that reflects wireless signals and glass that prevents the signals from going outside the building.
- Keep the device OS and software updated.
- Decrease the wireless antenna gain level.
- Use wireless MAC address filtering.
Explanation: Many companies now support employees and visitors attaching and using wireless devices that connect to and use the corporate wireless network. This practice is known as a bring-your-own-device policy or BYOD. Commonly, BYOD security practices are included in the security policy. Some best practices that mitigate BYOD risks include the following:
Use unique passwords for each device and account.
Turn off Wi-Fi and Bluetooth connectivity when not being used. Only connect to trusted networks.
Keep the device OS and other software updated.
Backup any data stored on the device.
Subscribe to a device locator service with a remote wipe feature.
Provide antivirus software for approved BYODs.
Use Mobile Device Management (MDM) software that allows IT teams to track the device and implement security settings and software controls.
6. Which type of business policy establishes the rules of conduct and the responsibilities of employees and employers?
- data
- security
- company
- employee
Explanation: Business policies set a baseline of acceptable use. Company policies establish the rules and conduct and the responsibilities of both employees andthe employer. Company policies protect the rights of the workers as well as the business interests of the company.
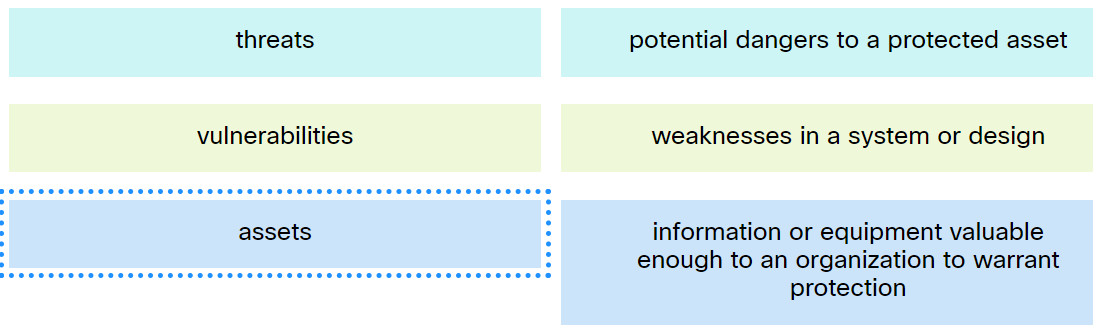
7. Match the term to the description.
Network Defense (NetDef) Module 1 – 3 Group Exam
Explanation: Place the options in the following order:
| assets |
information or equipment valuable enough to an organization to warrant protection |
| threats |
potential dangers to a protected asset |
| vulnerabilities |
weaknesses in a system or design |
8. Which network monitoring tool is in the category of network protocol analyzers?
Explanation: Wireshark is a network protocol analyzer used to capture network traffic. The traffic captured by Wireshark is saved in PCAP files and includes interface information and timestamps.
9. What is a strength of using a hashing function?
- It is a one-way function and not reversible.
- Two different files can be created that have the same output.
- It is not commonly used in security.
- It can take only a fixed length message.
- It has a variable length output.
Explanation: Understanding the properties of a hash function shows its applicability such as one-way function, arbitrary input length, and fixed output.
10. A user has created a new program and wants to distribute it to everyone in the company. The user wants to ensure that when the program is downloaded that the program is not changed while in transit. What can the user do to ensure that the program is not changed when downloaded?
- Encrypt the program and require a password after it is downloaded.
- Create a hash of the program file that can be used to verify the integrity of the file after it is downloaded.
- Turn off antivirus on all the computers.
- Install the program on individual computers.
- Distribute the program on a thumb drive.
Explanation: Hashing is a method to ensure integrity and ensures that the data is not changed.
11. What is a purpose of implementing VLANs on a network?
- They eliminate network collisions.
- They prevent Layer 2 loops.
- They can separate user traffic.
- They allow switches to forward Layer 3 packets without a router.
Explanation: VLANs are used on a network to separate user traffic based on factors such as function, project team, or application, without regard for the physical location of the user or device.
12. A user is purchasing a new server for the company data center. The user wants disk striping with parity on three disks. Which RAID level should the user implement?
Explanation: RAID 5 striping with parity would be the best choice.
13. A company is developing an internet store website. Which protocol should be used to transfer credit card information from customers to the company web server?
Explanation: Hypertext Transfer Protocol (HTTP) provides web connectivity and website services. HTTP does not use encryption when transmitting content, leaving the data in transit vulnerable to monitoring and attack. HTTPS uses SSL/TLS to encrypt communication between the client and the server, thus providing confidentiality and preventing eavesdropping and tampering.
14. Why is asset management a critical function of a growing organization against security threats?
- It serves to preserve an audit trail of all new purchases.
- It allows for a build of a comprehensive AUP.
- It identifies the ever increasing attack surface to threats.
- It prevents theft of older assets that are decommissioned.
Explanation: Asset management is a critical component of a growing organization from a security aspect. Asset management consists of inventorying all assets, and then developing and implementing policies and procedures to protect them. As an organization grows, so does the attack surface in terms of security threats. Each of these assets can attract different threat actors who have different skill levels and motivations. Asset management can help mitigate these threats by inventorying the risks as the attack surface grows.
15. What is an example of the implementation of physical security?
- ensuring that all operating system and antivirus software is up to date
- encrypting all sensitive data that is stored on the servers
- requiring employees to use a card key when entering a secure area
- establishing personal firewalls on each computer
Explanation: Encrypting data, keeping software up to date, and the use of personal firewalls are all security precautions, but will not restrict physical access to secure areas by only authorized people.
16. A large retail company uses EAP-based authentication in conjunction with 802.1X. When the client first initiates communication on the wireless network, which type of authentication method is used by the client to associate with the AP?
- WPA3
- Open Authentication
- WPA
- WPA2
Explanation: When 802.1X is used in conjunction with EAP for authentication, a wireless device first uses Open Authentication to associate with the AP. Then, the wireless controller becomes the middleman in the authentication process between the end device and the authentication server. The wireless client cannot pass data onto the wireless network until successful authentication with the authentication server has occurred.
17. What are three examples of administrative access controls? (Choose three.)
- hiring practices
- background checks
- encryption
- guard dogs
- policies and procedures
- intrusion detection system (IDS)
Explanation: Administrative access controls are defined by organizations to implement and enforce all aspects of controlling unauthorized access and include the following:
Policies
Procedures
Hiring practices
Background checks
Data classification
Security training
Reviews
18. Which access control model applies the strictest access control and is often used in military and mission critical applications?
- attribute-based
- nondiscretionary
- mandatory
- discretionary
Explanation: Military and mission critical applications typically use mandatory access control which applies the strictest access control to protect network resources.
19. What is the purpose of the network security authentication function?
- to keep track of the actions of a user
- to require users to prove who they are
- to determine which resources a user can access
- to provide challenge and response questions
Explanation: Authentication, authorization, and accounting are network services collectively known as AAA. Authentication requires users to prove who they are. Authorization determines which resources the user can access. Accounting keeps track of the actions of the user.
20. A network administrator is configuring an AAA server to manage RADIUS authentication. Which two features are included in RADIUS authentication? (Choose two.)
- single process for authentication and authorization
- encryption for only the data
- encryption for all communication
- separate processes for authentication and authorization
- hidden passwords during transmission
Explanation: RADIUS authentication supports the following features:
RADIUS authentication and authorization as one process
Encrypts only the password
Utilizes UDP
Supports remote-access technologies, 802.1X, and Session Initiation Protocol (SIP)
21. Passwords, passphrases, and PINs are examples of which security term?
- access
- authentication
- identification
- authorization
Explanation: Authentication methods are used to strengthen access control systems. It is important to understand the available authentication methods.
22. An intern has started working in the support group. One duty is to set local policy for passwords on the workstations. What tool would be best to use?
- grpol.msc
- password policy
- secpol.msc
- system administration
- account policy
Explanation: Local policies are not group policies and only work on the local machine. Local policies can, however, be overridden if the machine is part of a Windows domain.
23. What is privilege escalation?
- Everyone is given full rights by default to everything and rights are taken away only when someone abuses privileges.
- A security problem occurs when high ranking corporate officials demand rights to systems or files that they should not have.
- Someone is given rights because she or he has received a promotion.
- Vulnerabilities in systems are exploited to grant higher levels of privilege than someone or some process should have.
Explanation: With privilege escalation, vulnerabilities are exploited to grant higher levels of privilege. After the privilege is granted, the threat actor can access sensitive information or take control of the system.
24. Which access control model allows users to control access to data as an owner of that data?
- nondiscretionary access control
- mandatory access control
- attribute-based access control
- discretionary access control
Explanation: In the discretionary access control (DAC) model, users can control access to data as owners of the data.

