Network Defense Module 3.5.2 Module 3 – Access Control Quiz Questions Exam Answers
1. Which three processes are examples of logical access controls? (Choose three.)
- swipe cards to allow access to a restricted area
- fences to protect the perimeter of a building
- guards to monitor security screens
- biometrics to validate physical characteristics
- firewalls to monitor traffic
- intrusion detection system (IDS) to watch for suspicious network activity
Explanation: Logical access controls includes but is not limited to the following:
- Encryption
- Smart cards
- Passwords
- Biometrics
- Access Control Lists (ACLs)
- Protocols
- Firewalls
- Intrusion Detection Systems (IDS)
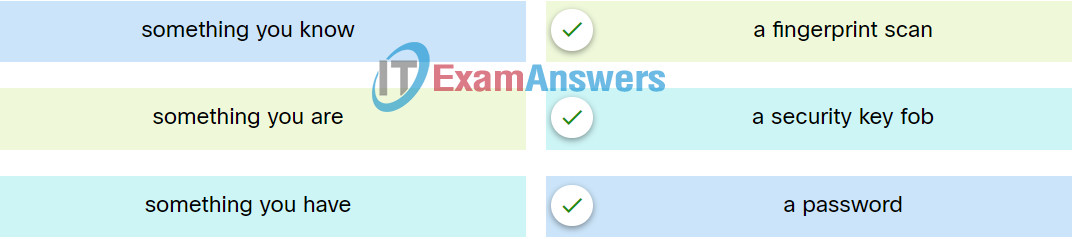
2. Match the type of multifactor authentication with the description.
Explanation: Place the options in the following order:
| something you know |
a password |
| something you have |
a security key fob |
| something you are |
a fingerprint scan |
3. An organization plans to implement security training to educate employees about security policies. What type of access control is the organization trying to implement?
- technological
- logical
- administrative
- physical
Explanation: Access control prevents an unauthorized user from gaining access to sensitive data and networked systems. There are several technologies used to implement effective access control strategies.
4. When a security audit is performed at a company, the auditor reports that new users have access to network resources beyond their normal job roles. Additionally, users who move to different positions retain their prior permissions. What kind of violation is occurring?
- password
- network policy
- least privilege
- audit
Explanation: Users should have access to information on a need to know basis. When a user moves from job role to job role, the same concept applies.
5. Which access control model assigns security privileges based on the position, responsibilities, or job classification of an individual or group within an organization?
- rule-based
- discretionary
- role-based
- mandatory
Explanation: Role-based access control models assign privileges based on position, responsibilities, or job classification. Users and groups with the same responsibilities or job classification share the same assigned privileges. This type of access control is also referred to as nondiscretionary access control.
6. Which type of access control applies the strictest access control and is commonly used in military or mission critical applications?
- discretionary access control (DAC)
- Non-discretionary access control
- mandatory access control (MAC)
- attribute-based access control (ABAC)
Explanation: Access control models are used to define the access controls implemented to protect corporate IT resources. The different types of access control models are as follows:
- Mandatory access control (MAC) – The strictest access control that is typically used in military or mission critical applications.
- Discretionary access control (DAC) – Allows users to control access to their data as owners of that data. Access control lists (ACLs) or other security measures may be used to specify who else may have access to the information.
- Non-discretionary access control – Also known as role-based access control (RBAC). Allows access based on the role and responsibilities of the individual within the organization.
- Attribute-based access control (ABAC) – Allows access based on the attributes of the resource to be accessed, the user accessing the resource, and the environmental factors such as the time of day.
7. Which component is a pillar of the zero trust security approach that focuses on the secure access of devices, such as servers, printers, and other endpoints, including devices attached to IoT?
- workforce
- workplace
- workloads
- workflows
Explanation: The workplace pillar focuses on secure access for any and all devices, including devices on the internet of things (IoT), which connect to enterprise networks, such as user endpoints, physical and virtual servers, printers, cameras, HVAC systems, kiosks, infusion pumps, industrial control systems, and more.
8. A user has been asked to implement IPsec for inbound external connections. The user plans to use SHA-1 as part of the implementation. The user wants to ensure the integrity and authenticity of the connection. What security tool can the user use?
Explanation: HMAC provides the additional feature of a secret key to ensure integrity and authentication.
9. After a security audit for an organization, multiple accounts were found to have privileged access to systems and devices. Which three best practices for securing privileged accounts should be included in the audit report? (Choose three.)
- Secure password storage.
- Reduce the number of privileged accounts.
- Only the CIO should have privileged access.
- No one should have privileged access.
- Enforce the principle of least privilege.
- Only managers should have privileged access.
Explanation: Best practices entail giving the user only what is needed to do the job. Any additional privileges should be tracked and audited.
10. What Windows utility should be used to configure password rules and account lockout policies on a system that is not part of a domain?
- Active Directory Security tool
- Event Viewer security log
- Computer Management
- Local Security Policy tool
Explanation: A cybersecurity specialist must be aware of the technologies and measures that are used as countermeasures to protect the organization from threats and vulnerabilities. Local Security Policy, Event Viewer, and Computer Management are Windows utilities that are all used in the security equation.
11. What is the purpose of the network security accounting function?
- to require users to prove who they are
- to determine which resources a user can access
- to provide challenge and response questions
- to keep track of the actions of a user
Explanation: Authentication, authorization, and accounting are network services collectively known as AAA. Authentication requires users to prove who they are. Authorization determines which resources the user can access. Accounting keeps track of the actions of the user.
12. Because of implemented security controls, a user can only access a server with FTP. Which AAA component accomplishes this?
- auditing
- accessibility
- authorization
- accounting
- authentication
Explanation: One of the components in AAA is authorization. After a user is authenticated through AAA, authorization services determine which resources the user can access and which operations the user is allowed to perform.
13. What is used to scan a BYOD device to verify that it is compliant with company security policies before the device is permitted to access the network?
- ACL
- NAC
- reconnaissance
- proxy server
- IDS
Explanation: One of the goals of NAC is to evaluate device compliance with security policies by user type, device type, and operating system prior to permitting network access. NAC system automation features make network access of BYOD and IoT devices practical.
14. Which AAA component can be established using token cards?
- authentication
- auditing
- authorization
- accounting
Explanation: The authentication component of AAA is established using username and password combinations, challenge and response questions, and token cards. The authorization component of AAA determines which resources the user can access and which operations the user is allowed to perform. The accounting and auditing component of AAA keeps track of how network resources are used.

