Module Group Exam 3: Network Defense (NetDef) Module 9 – 11 Group Exam – Checkpoint Exam: Evaluating Security Alerts
How to find: Press “Ctrl + F” in the browser and fill in whatever wording is in the question to find that question/answer. If the question is not here, find it in Questions Bank.
NOTE: If you have the new question on this test, please comment Question and Multiple-Choice list in form below this article. We will update answers for you in the shortest time. Thank you! We truly value your contribution to the website.
1. Which two technologies are primarily used on peer-to-peer networks? (Choose two.)
- Darknet
- Snort
- BitTorrent
- Bitcoin
- Wireshark
Explanation: Bitcoin is used to share a distributed database or ledger. BitTorrent is used for file sharing.
2. Which technique would a threat actor use to disguise traces of an ongoing exploit?
- Use SSL to encapsulate malware.
- Create an invisible iFrame on a web page.
- Corrupt time information by attacking the NTP infrastructure.
- Encapsulate other protocols within DNS to evade security measures.
Explanation: The Network Time Protocol (NTP) uses a hierarchy of time sources to provide a consistent time clock to network infrastructure devices. Threat actors may attack the NTP infrastructure in order to corrupt time information that is used in network logs.
3. Which type of attack is carried out by threat actors against a network to determine which IP addresses, protocols, and ports are allowed by ACLs?
- reconnaissance
- phishing
- social engineering
- denial of service
Explanation: Packet filtering ACLs use rules to filter incoming and outgoing traffic. These rules are defined by specifying IP addresses, port numbers, and protocols to be matched. Threat actors can use a reconnaissance attack involving port scanning or penetration testing to determine which IP addresses, protocols, and ports are allowed by ACLs.
4. What is the purpose of Tor?
- to allow users to browse the Internet anonymously
- to securely connect to a remote network over an unsecure link such as an Internet connection
- to inspect incoming traffic and look for any that violates a rule or matches the signature of a known exploit
- to donate processor cycles to distributed computational tasks in a processor sharing P2P network
Explanation: Tor is a software platform and network of peer-to-peer (P2P) hosts that function as routers. Users access the Tor network by using a special browserthat allows them to browse anonymously.
5. Which protocol is exploited by cybercriminals who create malicious iFrames?
Explanation: An HTML element known as an inline frame or iFrame allows the browser to load a different web page from another source.
6. After a security monitoring tool identifies a malware attachment entering the network, what is the benefit of performing a retrospective analysis?
- It can determine which network host was first affected.
- It can identify how the malware originally entered the network.
- A retrospective analysis can help in tracking the behavior of the malware from the identification point forward.
- It can calculate the probability of a future incident.
Explanation: General security monitoring can identify when a malware attachment enters a network and which host is first infected. Retrospective analysis takes the next step and is the tracking of the behavior of the malware from that point forward.
7. Which technique is necessary to ensure a private transfer of data using a VPN?
- encryption
- scalability
- authorization
- virtualization
Explanation: Confidential and secure transfers of data with VPNs require data encryption.
8. Which method is used by some malware to transfer files from infected hosts to a threat actor host?
- UDP infiltration
- ICMP tunneling
- iFrame injection
- HTTPS traffic encryption
Explanation: ICMP traffic from inside the company is also a threat. Some varieties of malware use ICMP packets to transfer files from infected hosts to threat actors via ICMP tunneling.
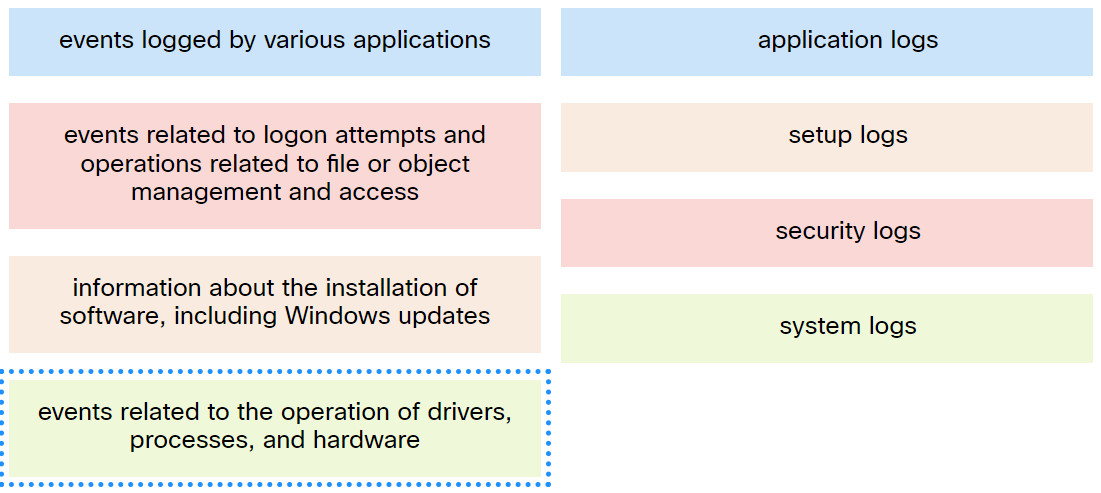
9. Match the Windows host log to the messages contained in it.
Network Defense (NetDef) Module 9 – 11 Group Exam
Explanation: Place the options in the following order:
| Events logged by various applications |
Application logs |
| Events related to the operation of drivers, processes, and hardware |
System logs |
| Information about the installation of software, including Windows updates |
Setup logs |
| Events related to logon attempts and operations related to file or object management and access |
Security logs |
10. What is a key difference between the data captured by NetFlow and data captured by Wireshark?
- NetFlow collects metadata from a network flow whereas Wireshark captures full data packets.
- NetFlow data is analyzed by tcpdump whereas Wireshark data is analyzed by nfdump.
- NetFlow data shows network flow contents whereas Wireshark data shows network flow statistics.
- NetFlow provides transaction data whereas Wireshark provides session data.
Explanation: Wireshark captures the entire contents of a packet. NetFlow does not. Instead, NetFlow collects metadata, or data about the flow.
11. Which type of data is used by Cisco Cognitive Intelligence to find malicious activity that has bypassed security controls, or entered through unmonitored channels, and is operating inside an enterprise network?
- statistical
- session
- alert
- transaction
Explanation: Cisco Cognitive Intelligence utilizes statistical data for statistical analysis in order to find malicious activity that has bypassed security controls, or entered through unmonitored channels (including removable media), and is operating inside the network of an organization.
12. Match the network monitoring data type with the description.
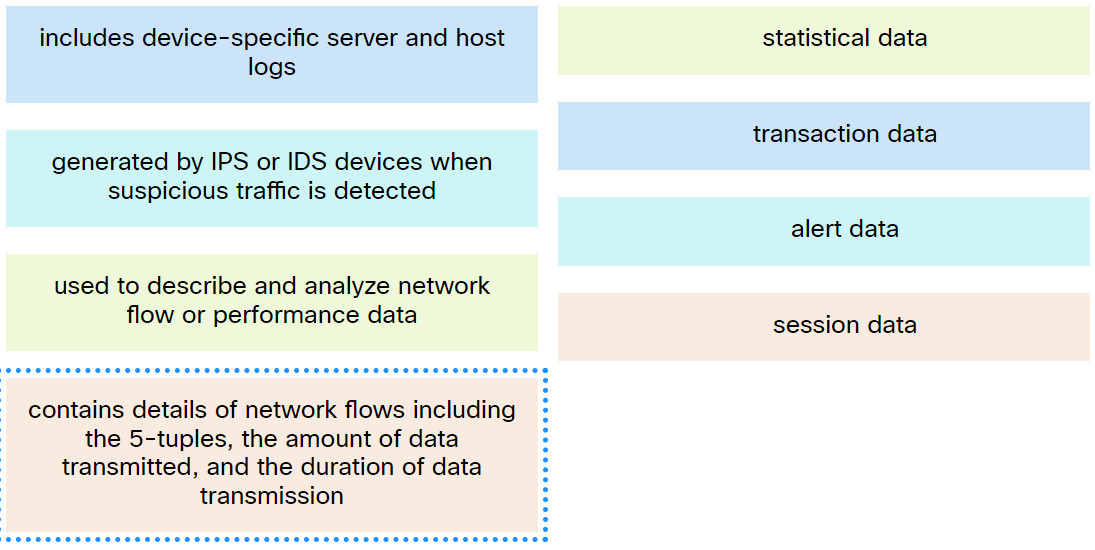
Explanation: Place the options in the following order:
| Includes device-specific server and host logs |
Transaction data |
| Generated by IPS or IDS devices when suspicious traffic is detected |
Alert data |
| Used to describe and analyze network flow or performance data |
Statistical data |
| contains details of network flows including the 5-tuples, the amount of data transmitted, and the duration of data transmission |
Session data |
13. Which Cisco appliance can be used to filter network traffic contents to report and deny traffic based on the web server reputation?
Explanation: The Cisco Web Security Appliance (WSA) acts as a web proxy for an enterprise network. WSA can provide many types of logs related to web traffic security including ACL decision logs, malware scan logs, and web reputation filtering logs. The Cisco Email Security Appliance (ESA) is a tool to monitor most aspects of email delivery, system functioning, antivirus, antispam operations, and blacklist and whitelist decisions. The Cisco ASA is a firewall appliance. The Cisco Application Visibility and Control (AVC) system combines multiple technologies to recognize, analyze, and control over 1000 applications.
14. A system administrator runs a file scan utility on a Windows PC and notices a file lsass.exe in the Program Files directory. What should the administrator do?
- Move it to Program Files (x86) because it is a 32bit application.
- Open the Task Manager, right-click on the lsass process and choose End Task.
- Delete the file because it is probably malware.
- Uninstall the lsass application because it is a legacy application and no longer required by Windows.
Explanation: On Windows computers, security logging and security policies enforcement are carried out by the Local Security Authority Subsystem Service (LSASS), running as lsass.exe. It should be running from the Windows\System32 directory. If a file with this name, or a camouflaged name, such as 1sass.exe, is running or running from another directory, it could be malware.
15. How does a web proxy device provide data loss prevention (DLP) for an enterprise?
- by functioning as a firewall
- by inspecting incoming traffic for potential exploits
- by checking the reputation of external web servers
- by scanning and logging outgoing traffic
Explanation: A web proxy device can inspect outgoing traffic as means of data loss prevention (DLP). DLP involves scanning outgoing traffic to detect whether the data that is leaving the enterprise network contains sensitive, confidential, or secret information.
16. Which two services are provided by the NetFlow tool? (Choose two.)
- network monitoring
- log analysis
- access list monitoring
- QoS configuration
- usage-based network billing
Explanation: NetFlow efficiently provides an important set of services for IP applications including network traffic accounting, usage-based network billing, network planning, security, denial of service monitoring capabilities, and network monitoring.
17. What information is contained in the options section of a Snort rule?
- source and destination address
- action to be taken
- text describing the event
- direction of traffic flow
Explanation: Snort rules consist of two sections, the rules header and the rule options. The rule options section of a snort rule consists of the messages text displayed to describe an alert as well as metadata about the alert.
18. Which classification indicates that an alert is verified as an actual security incident?
- true negative
- false negative
- false positive
- true positive
Explanation: Alerts can be classified as follows:
True Positive: The alert has been verified to be an actual security incident.
False Positive: The alert does not indicate an actual security incident. Benign activity that results in a false positive is sometimes referred to as a benign trigger.
An alternative situation is that an alert was not generated. The absence of an alert can be classified as follows:
True Negative: No security incident has occurred. The activity is benign.
False Negative: An undetected incident has occurred.
19. Match the characteristic to the method of security analysis.
| each event is the inevitable result of antecedent causes |
Deterministic |
| precise method that yields the same result every time by relying on predefined conditions |
Deterministic |
| analysis of applications that conform to application/networking standards |
Deterministic |
| random variables create difficulty in knowing the outcome of any given event with certainty |
Probabilistic |
| preferred method for analyzing applications designed to circumvent firewalls |
Probabilistic |
20. A threat actor has successfully breached the network firewall without being detected by the IDS system. What condition describes the lack of alert?
- false negative
- true positive
- true negative
- false positive
Explanation: A false negative is where no alert exists and exploits are not being detected by the security systems that are in place.
21. What are two scenarios where probabilistic security analysis is best suited? (Choose two.)
- when applications that conform to application/networking standards are analyzed
- when random variables create difficulty in knowing with certainty the outcome of any given event
- when each event is the inevitable result of antecedent causes
- when analyzing applications designed to circumvent firewalls
- when analyzing events with the assumption that they follow predefined steps
Explanation: Probabilistic analysis relies on statistical techniques that are designed to estimate the probability that an event will occur based on the likelihood that prior events will occur.
22. What are the three core functions provided by the Security Onion? (Choose three.)
- security device management
- full packet capture
- alert analysis
- intrusion detection
- business continuity planning
- threat containment
Explanation: Security Onion is an open source suite of Network Security Monitoring (NSM) tools for evaluating cybersecurity alerts. For cybersecurity analysts the Security Onion provides full packet capture, network-based and host-based intrusion detection systems, and alert analysis tools.
23. Refer to the exhibit. Which field in the Sguil event window indicates the number of times an event is detected for the same source and destination IP address?
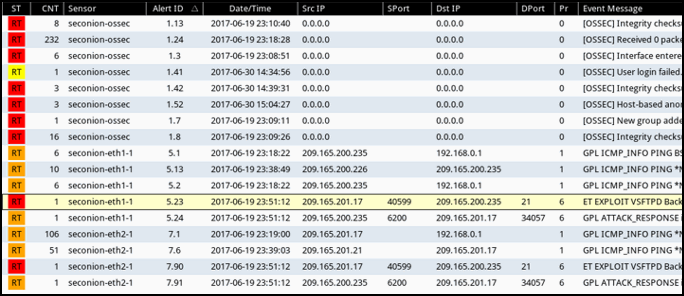
Explanation: The CNT field indicates the number of times an event is detected from the same source and destination IP address. Having a high number of events can indicated a problem with event signatures.
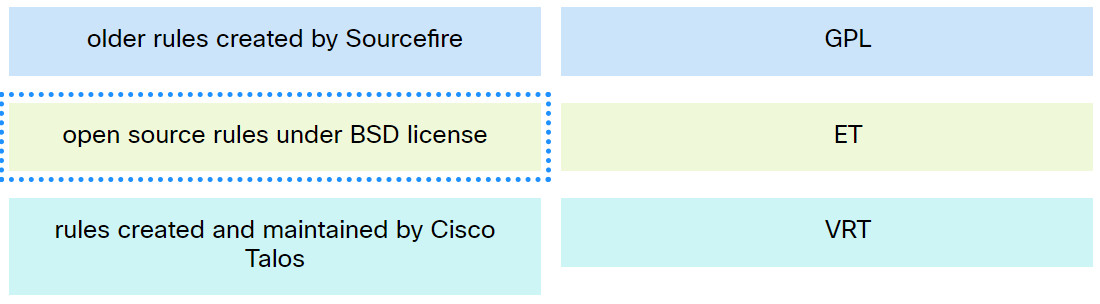
24. Match the Snort rule source to the description.