Category: Network Security 1.0
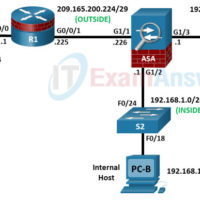
21.9.5 Lab – Configure ASA Basic Settings and Firewall Using ASDM Answers version Addressing Table Device Interface IP Address Subnet Mask Default Gateway Switch Port R1 G0/0/0 172.16.3.1 255.255.255.0 N/A S3 F0/5 G0/0/1 209.165.200.225 255.255.255.248 ASA G1/1 ASA G1/1 (OUTSIDE) 209.165.200.226 255.255.255.248 N/A R1 G0/0/1 G1/2 (INSIDE) 192.168.1.1 …
21.7.6 Optional Lab – Configure ASA Network Services, Routing, and DMZ with ACLs Using CLI Answers version Topology Topology Device Interface IP Address Subnet Mask Default Gateway Switch Port R1 G0/0/0 172.16.3.1 255.255.255.0 N/A S3 F0/5 G0/0/1 209.165.200.225 255.255.255.248 ASA G1/1 ASA G1/1 (OUTSIDE) 209.165.200.226 255.255.255.248 N/A R1 …
21.2.10 Optional Lab – Configure ASA Basic Settings Using the CLI Answers version Topology Addressing Table Device Interface IP Address Subnet Mask Default Gateway Switch Port R1 G0/0/0 172.16.3.1 255.255.255.0 N/A S3 F0/5 G0/0/1 209.165.200.225 255.255.255.248 ASA G1/1 ASA G1/1 (OUTSIDE) 209.165.200.226 255.255.255.248 N/A R1 G0/0/1 G1/2 (INSIDE) …
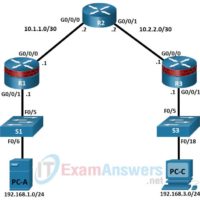
19.5.6 Lab – Configure a Site-to-Site VPN Answers version Addressing Table Device Interface IP Address Subnet Mask Default Gateway Switch Port R1 G0/0/1 192.168.1.1 255.255.255.0 N/A S1 F0/5 G0/0/0 10.1.1.1 255.255.255.252 N/A N/A R2 G0/0/0 10.1.1.2 255.255.255.252 N/A N/A G0/0/1 10.2.2.2 255.255.255.252 N/A N/A R3 G0/0/1 192.168.3.1 255.255.255.0 …
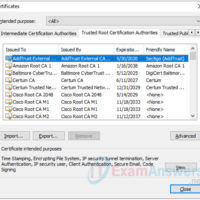
17.2.7 Lab – Certificate Authority Stores Answers version Objectives Part 1: Certificates Trusted by Your Browser Part 2: Checking for Man-In-Middle Background / Scenario As the web evolved, so did the need for security. HTTPS (where the ‘S’ stands for security) along with the concept of a Certificate …
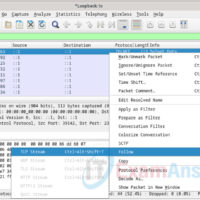
16.3.12 Lab – Examining Telnet and SSH in Wireshark Answers Objectives Part 1: Examine a Telnet Session with Wireshark Part 2: Examine an SSH Session with Wireshark Background / Scenario In this lab, you will configure a router to accept SSH connectivity and use Wireshark to capture and …
16.3.11 Lab – Encrypting and Decrypting Data Using a Hacker Tool Answers version Objectives Part 1: Create and Encrypt Files Part 2: Recover Encrypted Zip File Passwords Background / Scenario What if you work for a large corporation that had a corporate policy regarding removable media? Specifically, it …
16.3.10 Lab – Encrypting and Decrypting Data Using OpenSSL Answers Objectives Part 1: Encrypting Messages with OpenSSL Part 2: Decrypting Messages with OpenSSL Background / Scenario OpenSSL is an open-source project that provides a robust, commercial-grade, and full-featured toolkit for the Transport Layer Security (TLS) and Secure Sockets …
16.1.6 Lab – Hashing Things Out Answers version Objectives Part 1: Hashing a Text File with OpenSSL Part 2: Verifying Hashes Background / Scenario Hash functions are mathematical algorithms designed to take data as input and generate a fixed-size, unique string of characters, also known as the hash. …
15.4.5 Lab – Explore Encryption Methods Answers version Objectives Part 1: Decipher a Pre-Encrypted Message Using the Vigenère Cipher Use an encrypted message, a cipher key, and the Vigenère cipher square to decipher the message. Part 2: Create a Vigenère Cipher Encrypted Message and Decrypt It Work with …