1.5.3.6 Packet Tracer – Communicating in a Cyber World (Answers) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Addressing Table Device Private IP Address Public IP Address Subnet Mask Site FTP/Web Server 10.44.1.254 209.165.201.3 255.255.255.0 Metropolis Bank HQ Email/DNS …
1.5.3.5 Packet Tracer – Creating a Cyber World (Answers) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Addressing Table Device IP Address Subnet Mask Site FTP/Web Server 10.44.1.254 255.255.255.0 Metropolis Bank HQ Email/DNS Server 10.44.1.253 255.255.255.0 Metropolis Bank HQ …
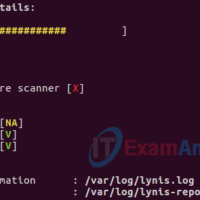
7.1.1.6 Lab – Hardening a Linux System (Answers) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives Demonstrate the use of a security auditing tool to harden a Linux system. Background / Scenario Auditing a system for potential misconfigurations …
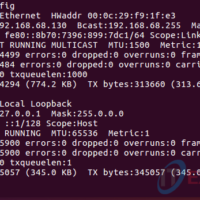
5.4.3.4 Lab – Remote Access (Answers) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives Compare SSH and Telnet for accessing a remote host. Background / Scenario You will use SSH and Telnet to establish remote connections to a …
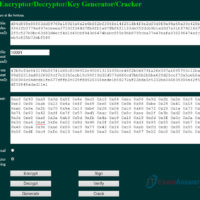
5.2.2.4 Lab – Using Digital Signatures (Answers) Instructor Note: Have students pair up for this lab. Objectives Understand the concepts behind digital signature. Part 1: Demonstrate the use of digital signatures. Part 2: Demonstrate the verification of a digital signature. Background / Scenario A digital signature is a …
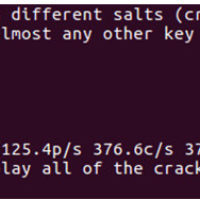
5.1.2.4 Lab – Password Cracking (Answers) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives Use a password cracking tool to recover a user’s password. Background / Scenario There are four user accounts, Alice, Bob, Eve, and Eric, on …
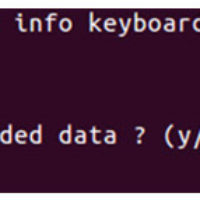
4.3.2.3 Lab – Using Steganography (Answers) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives Use steganography to hide a document within a JPEG file. Background / Scenario Steghide is an open source steganography program that hides data in …
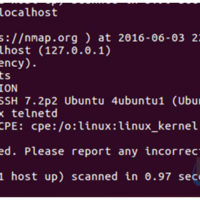
3.3.1.9 Lab – Detecting Threats and Vulnerabilities (Answers) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives Use Nmap, a port scanner and network mapping tool to detect threats and vulnerabilities on a system. Background / Scenario Network Mapper, …
2.5.2.5 Lab – Authentication Authorization Accounting (Answers) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives Given a scenario, select the appropriate authentication, authorization, or access control Install and configure security controls when performing account management, based on best …
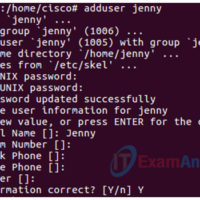
2.5.2.4 Lab – Install a Virtual Machine On A Personal Computer (Answers) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives Part 1: Prepare a Computer for Virtualization Part 2: Import a Virtual Machine into VirtualBox Inventory Background / …