Section 41 Tasks
- Read today’s lesson notes (below)
- Review yesterday’s lesson notes
- Complete the lab(s) of your choice
- Read the ICND2 cram guide
- Spend 15 minutes on the subnetting.org website
Cisco split WAN concepts between the ICND1 and ICND2 exams, with the latter focusing on Frame Relay and PPP protocols. For this reason, we will look at basic WAN concepts, technologies, and protocols.
Today you will learn about the following:
- WAN components
- WAN protocols
- Basic serial line configuration
- Troubleshooting WAN connections
This lesson maps to the following ICND2 syllabus requirements:
- Identify different WAN Technologies
- Metro Ethernet
- VSAT
- T1 / E1
- T3 / E3
- ISDN
- DSL
- Cable
- Cellular 3G / 4G
- VPN
- MPLS
- Configure and verify a basic WAN serial connection
- Implement and troubleshoot PPPoE
WAN Overview
Wide Area Networks (WAN) span across large geographical distances in order to provide connectivity for various parts of the network infrastructure. Unlike the Local Area Network (LAN) environment, not all WAN components are owned by the specific enterprise they serve. Instead, WAN equipment or connectivity can be rented or leased from service providers.
Most service providers are well trained in order to make sure they can properly support not just the traditional data traffic but also voice and video services (which are more delay sensitive) over large geographical distances.
Another interesting thing about WANs is that, unlike LANs, there is typically some initial fixed cost and some periodic recurring fees for the services. With wide area networking, not only do you not own the connection and some of the equipment but you will also have to regularly pay fees to the service providers. This is one of the reasons why you should avoid over-provisioning (i.e., buy only the bandwidth you think you will use). This leads to the need for implementing effective Quality of Service mechanisms to avoid buying additional WAN bandwidth. The high costs are usually associated with the recurring fees that might appear in the case of overprovisioning the bandwidth.
WAN technology design requirements are typically derived from the following:
- Application type
- Application availability
- Application reliability
- Costs associated with a particular WAN technology
- Usage levels for the application
WAN Categories
An essential concept in WAN categorisation is circuit-switched technology, the most relevant example of this technology being the Public Switched Telephone Network (PSTN). One of the technologies that fall into this category is ISDN. The way circuit-switched WAN connections function is by becoming established when needed and terminating when they are no longer required. Another example that reflects this circuit-switching behaviour is the old-fashioned dial-up connection (dial-up modem analog access over the PSTN).
NOTE: Not too long ago, dial-up technology was the only way to access Internet resources, offering an average usable bandwidth of around 40Kbps. Nowadays, this technology is almost extinct.
The opposite of the circuit-switched option is leased-line technology. This is a fully dedicated connection that is permanently up and is owned by the company. Examples of leased lines include Time Division Multiplexing (TDM)-based leased lines. These are usually very expensive because a single customer has full use of the connection.
Another popular category of WAN technology involves packet-switched networks. In a packetswitched infrastructure, shared bandwidth utilises virtual circuits. The customer can create a virtual path (similar to a leased line) through the service provider infrastructure cloud. This virtual circuit has a dedicated bandwidth, even though technically this is not a real leased line.
Frame Relay is an example of this type of technology.
Some legacy WAN technologies include X.25, which is the predecessor of Frame Relay. This technology is still present in some implementations but it is very rare (Frame Relay is also pretty rare nowadays).
Another WAN category you may have heard about is cell-switched technology. This is often included in packet-switched technologies, as they are very similar. A cell-switched technology example is ATM (Asynchronous Transfer Mode, which is also pretty rare nowadays). This operates by using fixed-size cells, instead of using packets (as used in Frame Relay). Cellswitched technologies form a shared bandwidth environment so that the service provider can guarantee customers a certain level of bandwidth through their infrastructure. Broadband is another growing WAN category and this includes technologies such as the following:
- DSL
- Cable
- Wireless
Broadband has the capability of taking a connection, like the old-fashioned coaxial cable that carries TV signals, and figuring out how to use different aspects of that bandwidth. For example, by using multiplexing an additional data signal could be transmitted along with the original TV signal.
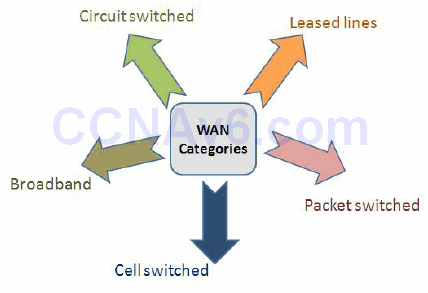
Figure 41.1 – WAN Categories
As detailed in Figure 41.1 above, there are many options when discussing WAN categories and this is just a general introduction to them. All of these technologies can support the needs of modern networks that operate under the 20/80 design rule, meaning 80% of the network traffic uses some kind of WAN technology in order to access remote resources.
NBMA Technologies
A special technology that appears in wide area networking is Non-Broadcast Multi-Access (NBMA). This presents some challenges that are not present in traditional broadcast networking. The need for NBMA arises when there is no native Broadcast support for a group of systems that want to communicate over the same network. Issues arise when the devices cannot natively send a packet destined for all the devices on the Multi-Access segment. Frame Relay, ATM, and ISDN are examples of technologies that are NBMA by default.
All of these technologies do not have any native ability to support Broadcasts. This prevents them from running routing protocols that use Broadcasts in their operation. Native Multicast support is also missing in Non-Broadcast networks. In the case of a routing protocol, all the nodes that participate must receive Multicast updates. One approach to this using an NBMA network is sending the Multicast or Broadcast packets as replicated Unicast packets. In this way, the Broadcast/Multicast frames are individually sent to every node in the topology. The tricky part in this scenario is that the device has to come up with a way to solve the Layer 3 to Layer 2 resolution. Particular packets have to be addressed for the specific machines that need to receive them.
Methodologies must exist for addressing this Layer 3 to Layer 2 resolution issue. The Layer 3 address is typically the IP address and the Layer 2 address usually varies, based on the technology used. In the case of Frame Relay, this will consist of the Data Link Connection Identifier (DLCI) number, so a way to resolve the DLCI to the IP address must be found.
In the case of Broadcast networks, Layer 3 resolution uses MAC addresses as the Layer 2 address and this has to be resolved to IPv4 addresses. This is accomplished with the Address Resolution Protocol (ARP). In a Broadcast-based network, the devices broadcast the requests by specifying the devices it wants to communicate with (typically learned via DNS) and asking for the MAC addresses specific to those devices. The reply is via Unicast and includes the requested MAC address.
In NBMA environments you still need to bind the Layer 3 address (IP address) to the Layer 2 address (DLCI). This can be done in an automated fashion using Inverse ARP. This is used to resolve the remote Layer 3 address to a Layer 2 address and is only used locally. Inverse ARP can be utilised in Frame Relay environments. The issue with Inverse ARP as the solution for the Layer 3 to Layer 2 resolution in an NBMA environment is that it is limited to directly connected devices. This creates issues in partial-mesh NBMA networks (where not all devices are directly connected).
Two types of NBMA interfaces exist – Mulitipoint and Point-to-Point, as illustrated in Figure 41.2 below . Multipoint interfaces require some kind of Layer 3 to Layer 2 resolution methodology. As its name implies, it can be the termination point of multiple Layer 2 circuits.
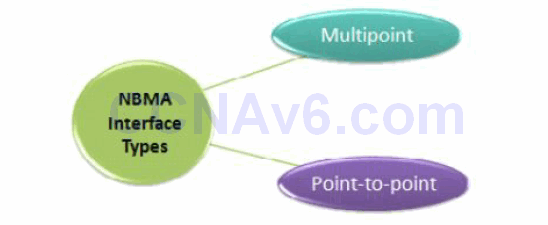
Figure 41.2 – NBMA Interface Types
If Frame Relay is configured on the main physical interface of a device, that interface will be Multipoint by default. If a subinterface is created on a Frame Relay physical interface, the option of creating it as Multipoint exists. Layer 3 to Layer 2 resolution has to be configured for both the physical interfaces and for the subinterfaces. There are two options for doing this in Frame Relay:
- Inverse ARP
- Statically map
Layer 3 to Layer 2 resolution is not always an issue on NBMA interfaces because Point-to-Point WAN interfaces can be created. A Point-to-Point interface can only terminate a single Layer 2 circuit, so if the interface communicates with only one device, Layer 3 to Layer 2 resolution is not necessary. With only one circuit, there is only one Layer 2 address to communicate with. Layer 3 to Layer 2 resolution issues disappear when running a Frame Relay Point-to-Point subinterface type or an ATM Point-to-Point subinterface, for example.
WAN Components
WAN requires a number of physical components to enable a connection. These will differ depending upon the type of connection you are using (e.g., ISDN, ADSL, Frame Relay, leased line, etc.) and other factors, such as back-up connections and the number of incoming networks.
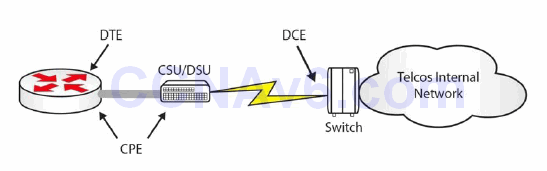
Figure 41.3 – Basic WAN Components
Figure 41.3 above shows a basic serial connection going out to an ISP. As the customer, you are responsible for the Data Terminal Equipment (DTE), which is your router interface accepting the incoming link. You will also be responsible for the cable going to your Channel Service Unit/Data Service Unit (CSU/DSU), which converts your data into a format that your ISP can transport. The CSU/DSU is usually built into your router WAN interface card (WIC). CPE is the Customer Premise Equipment, which is your responsibility.
From this point on, your ISP or Telco is usually responsible for the connection. They lay the cables and provide switching stations, which transport the data across their network. The ISP owns the Data Communication Equipment (DCE), which is the end that provides the clocking, meaning the rate at which the data can pass on the line.
Common types of WAN connections include the following:
- Leased-line – a dedicated connection available 24/7
- Circuit-switching – set up when required
- Packet-switching – shared link/virtual circuit
The type of link you buy depends on your requirements and budget. If you can afford a dedicated line, you will have exclusive use of the bandwidth and security is less of an issue. A shared connection can mean a slower connection during peak times.
WAN Protocols
Common WAN protocols include PPP, HDLC, and Frame Relay. There are many others, of course, but you need to focus on those included in the CCNA syllabus.
Point-to-Point Protocol (PPP) can be used when you have a Cisco device connecting to a non- Cisco device. PPP also has the advantage of including authentication. It can be used over a number of connection types, including DSL, circuit-switched, and asynchronous/synchronous connections.
Cisco’s High-Level Data Link Control (cHDLC) is its implementation of the open standard version of HDLC. HDLC requires DTE and DCE and is the default encapsulation type on Cisco routers (serial interfaces). Keepalives are sent from the DCE in order to check link status.
As already discussed, Frame Relay is a packet-switching technology which has become less popular in recent years, as DSL has become both more affordable and more readily available. It works at speeds from 56Kbps to 2Mbps and builds virtual circuits every time a connection is required. There is no security built into Frame Relay (but see Farai’s comment below). Frame Relay will be covered in more detail later.
Farai says – “Frame Relay commonly uses Permanent Virtual Circuits (PVCs), which are always present, although it can use Switched Virtual Circuits (SVCs), which are created on demand. A PVC is a type of Virtual Private Network (VPN). However, some people run PPP over Frame Relay (PPPoFR) to allow for PPP security for Frame Relay connections.”
Metro Ethernet
Metro Ethernet technologies involve the use of carrier Ethernet in Metropolitan Area Networks (MANs). Metro Ethernet can connect company LANs and individual end-users to a WAN or to the Internet. Companies often use Metro Ethernet to connect branch offices to an intranet.
A typical Metro Ethernet deployment uses a star or a mesh topology with interconnected network nodes using copper or fibre optic cables. Using the standard and widely deployed Ethernet technology in Metro Ethernet deployments offers a number of advantages, as opposed to using SONET/SDH or MPLS technologies:
- Less expensive
- Easier to implement
- Easier to manage
- Easy to connect customer equipment because it uses the standard Ethernet approach
A typical MAN can be structured under the access/aggregation/core standard design (a Cisco design model), as follows:
- Access Layer – usually at the customer’s premises. This may include an office router or residential gateway
- Aggregation Layer – usually comprises microwave, DSL technologies, or Point-to-Point Ethernet links.
- Core Layer – may use MPLS to interconnect different MANs
Customer traffic separation is usually ensured in a MAN by using Ethernet VLAN tags that allow the differentiation of packets.
VSAT
Very Small Aperture Terminal (VSAT) technology is a telecommunication system based on wireless satellite technology. A VSAT deployment is made up of a small satellite earth station and a typical antenna, as shown in Figure 41.4 below:
Figure 41.4 – Satellite Communication
Typical VSAT components include the following:
- Master earth station
- Remote earth station
- Satellite
The master earth station is the network control centre for the entire VSAT network. This is the place where the configuration, management, and monitoring of the entire network is done.
The remote earth station is the hardware installed at the customer premises and includes the following components:
- ODU (outdoor unit)
- IDU (indoor unit)
- IFL (interfacility link)
The VSAT satellite orbits round the globe and receives and transmits signals from and to the earth stations.
VSAT networks can be configured in one of the following topologies:
- Star topology
- Mesh topology
- Star-mesh combination
Using satellite technology to ensure WAN connectivity is generally more expensive than using a traditional terrestrial network connection. The speeds offered by such connections can reach 5Mbps download and 1Mbps upload, which is usually enough for remote sites.
A significant disadvantage of using satellite connectivity is the increased traffic latency, which can reach up to 250 ms one way (antenna to satellite or satellite to antenna) due to the use of radio signals over a very long distance. This should be carefully analysed when planning to install a satellite WAN connection because the increased latency could prevent sensible applications from functioning, while it has no impact on other applications.
Another challenge of using satellite connectivity is that the satellite dish has to have line of sight to the satellite. This means that you have to make use of high frequency ranges (2 GHz), and any type of interference (e.g., natural phenomena like rain or storm clouds) may affect the connection throughput and availability.
T1/E1
Standards for T1 and E1 wide area networking have been around for a very long time. T1 stands for T-Carrier Level 1, which is a line that uses Time Division Multiplexing with digital signals associated with different channels based on time. T1 operates using 24 separate channels at a 1.544Mbps line rate, thus allocating 64Kbps per individual channel. You can use the 24 channels any way you want to, and you can even buy just a few channels from the service provider based on your needs. In general terms, consider a T1 connection as a trunk/bundle carrying 24 separate lines. T1 is a standard often used in the following geographical regions:
- North America
- Japan
- South Korea
E1 (E-Carrier Level 1) is a standard similar to T1 but it is used exclusively in Europe. The main difference between E1 and T1 is that E1 uses 32 channels instead of 24, also operating at 64kbps, thus offering a total line rate of 2.048Mbps. E1 functions based on Time Division Multiplexing, just like T1, so all other functionalities are common between the two standards.
T3/E3
T3 and E3 standards offer higher bandwidth than their T1 and E1 predecessors. T3 stands for TCarrier Level 3 and is a type of connection usually based on coaxial cable and a BNC connector. This differs from T1, which is usually offered over twisted-pair media.
T3 connections are often referred to as DS3 connections, which is related to the data carried on the T3 line. T3 offers additional throughput because it uses the equivalent of 28 T1 circuits, meaning 672 T1 channels. This offers a total line rate of 44.736Mbps.
E3 connections are similar to those of T3, with the exception of being equivalent to 16 E1 circuits, meaning 512 E1 channels and a total line rate of 33.368Mbps.
T3/E3 connections are usually used in large data centres because they offer the ability to increase the total amount of throughput when needed.
ISDN
Integrated Services Digital Network (ISDN) is a technology that allows digital communication over a traditional analog phone line, so both voice and data can be digitally transmitted over the PSTN. ISDN never had the popularity that it was expected to have because it came along at a time when other alternative technologies were developed.
There are two flavours of ISDN:
- ISDN BRI (Basic Rate Interface)
- ISDN PRI (Primary Rate Interface)
The ISDN-speaking devices are called terminal emulation equipment and the devices can be categorised into native ISDN and non-native ISDN equipment. The native ISDN equipment is made up of devices that were built to be ISDN-ready and are called TE1 devices (Terminal Equipment 1). Non-native ISDN equipment is made up of TE2 devices. Non-native ISDN equipment can be integrated with native ISDN equipment by using special Terminal Adapters (TAs), meaning only TE2 devices require TA modules.
Moving towards the ISDN provider, you will find Network Termination 2 (NT2) devices and Network Termination 1 (NT1) devices. These are translation devices for media, transforming five-wire connections into two-wire connections (the local loop). The local loop is the user connection line and it is a two-wire link.
An interesting thing about the network termination devices is that in North America the customer is responsible for NT1 devices, while in other parts of the world this is the service provider’s responsibility. Because of this issue, some Cisco routers provide built-in NT1 functionality and they will feature a visible “U” under the port number so that the user can quickly see this capability. The “U” notation comes from the ISDN reference points terminology that describes where you might have a problem in the ISDN infrastructure, as shown in Figure 41.5 below:
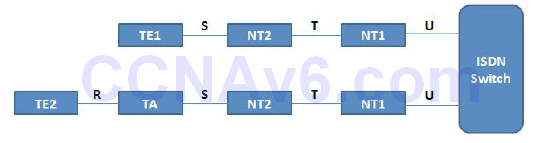
Figure 41.5 – ISDN Reference Points
These reference points are important during the troubleshooting or maintaining process of an ISDN network. The ISDN switch is usually located at the service provider location. The different ISDN reference points are as follows:
- U reference point – between the ISDN switch and the NT1 device
- T reference point – between the NT2 and the NT1 devices
- S reference point – between terminals (TE1 or TA) and NT2 devices
- R reference point – between non-ISDN native devices and TAs
The ISDN Basic Rate Interface (BRI) connectivity contains two B (bearer) channels for carrying data and one D (delta) channel for signaling. The BRI connection is abbreviated as 2B+D to remind you about the number of channels each provides. Each of the bearer channels in ISDN will operate at a speed of 64Kbps. Multilink PPP can be configured on top of these interfaces to allow the user to reach a bandwidth of 128Kbps. This bandwidth is considered to be very low according to modern networks requirements.
The delta (D) channel in BRI ISDN is dedicated to 16Kbps for control traffic. There are also 48Kbps overall for framing control and other overhead in the ISDN environment, meaning the total ISDN bandwidth for BRI is 192Kbps (128Kbps from the B channels + 16Kbps from the D channel + 48Kbps overhead).
ISDN Primary Rate Interface (PRI) has 23 B channels and one D channel in the US and Japan. The bearer channels and the delta channels all support 64Kbps. If you include the overhead, the total PRI bandwidth is 1.544Mbps. In other parts of the world (i.e., Europe and Australia) the PRI connection contains 30 B channels and one D channel.
ISDN PRI connections are commonly used as connectivity from the PSTN to large phone systems (PBX). Each of the 23 or 30 B channels can be used as a single phone line, so the entire PRI connection can be considered a trunk that carries multiple lines. The main advantage of using a PRI connection instead of multiple individual lines is that it is easier to manage and it offers scalability.
The technologies described above are called Time Division Multiplexing (TDM) technologies. TDM refers to being able to combine multiple channels over a single overall transmission medium and using these different channels for voice, video, and data. Time division refers to splitting the connection into small windows of time for the various communication channels.
In a PSTN, you need to be able to transmit multiple calls along the same transmission medium, so TDM is used to achieve this goal. TDM actually started in the days of the telegraph and later on gained popularity with fax machines and other devices that use TDM technologies.
When you have leased lines (buying dedicated bandwidth), the circuits that are sold are measured in terms of bandwidth. A DS1 or T1 circuit in North America provides 24 time slots of 64Kbps each and a 9Kbps control time slot (for a total of 1.544Mbps, as mentioned earlier). TDM terminology is tightly connected with the leased-line purchasing process.
DSL
Digital Subscriber Line (DSL) is used as an alternative to ISDN for home users. There are a number of types of DSL connections, but the most important ones include the following:
- ADSL
- HDSL
- VDSL
- SDSL
Asymmetric Digital Subscriber Line (ADSL) is the most common form of DSL connection that functions over standard telephone lines. The reason it is called asymmetric is that it offers unequal download and upload throughput, with the download rate being higher than the upload rate. A standard ADSL connection usually offers a maximum of 24Mbps download throughput and a maximum of 3.5Mbps upload throughput over a distance of up to 3 km.
With ADSL the customer connects to a Digital Subscriber Line Access Multiplexer (DSLAM) located at the service provider. DSLAM is a DSL concentrator device that aggregates connections from multiple users.
NOTE: One of the issues with ADSL is the limited distance a subscriber can be from a DSLAM.
High Bitrate DSL (HDSL) and Very High Bitrate DSL (VDSL) are other DSL technologies used on a large scale that offer increased throughput when compared to ADSL. VDSL can operate at rates of up to 100Mbps.
Symmetric DSL (SDSL) offers the same download and upload throughput, but it was never standardised or used on a large scale.
Cable
Digital signals can also be received by home users over standard TV cable connections. Internet access can be provided over cable by using the Data Over Cable Service Interface Specification (DOCSIS) standard. This is usually a low-cost service, as the provider does not need to install a new infrastructure for the data services. The only upgrade to the existing network is the installation of a low-cost cable modem in the customer premises that usually offers RJ45 data connectivity for the user devices.
Data traffic transmission rates over cable technology can go up to 100Mbps, which is more than enough for home users and even small businesses.
NOTE: Besides TV and data signals, cable connection can also carry voice traffic.
Point-to-Point Protocol over Ethernet (PPPoE) is another technology that can be used in conjunction with cable. This can be used between the cable modem and the endpoint devices to add security to the cable modem infrastructure. This allows the user to log on and provide a username and a password that has to be authenticated in order for the cable service to be used. The credentials are carried across the Ethernet connection to the cable modem and beyond by using the PPP running over the Ethernet. We will cover PPPoE shortly.
Cellular Networks
Cellular networks are used in conjunction with mobile devices (e.g., cell phones, tablets, PDAs etc.) to send and receive data traffic with classic voice service. These networks cover large geographical areas by splitting them into cells. Antennas are strategically placed to ensure optimal coverage across these cells and seamless cell roaming for users going from one location to another. The traditional connectivity type is also called 2G and includes the following:
- GSM (Global System for Mobile Communications)
- CDMA (Code Division Multiple Access)
Depending upon the carrier you use and the country you live in, you might use a GSM or CDMA type of communication, although functionally they are often referred to as 2G networks. These networks were designed as analog connections using circuit switching and were not originally designed to send data. Because the data connections use a packet-switching technology, 2G connections offer limited data transmission support.
Newer connection types over cellular networks that allow full-featured packet switching and proper data transmission include the following:
- HSPA+ (High Speed Packet Access)
- LTE (Long Term Evolution)
LTE and HSPA+ are standards created by the 3rd Generation Partnership Project (3GPP), which is a collaboration between a number of telecommunications companies that decided they needed a standardised way to send data on cellular networks.
HSPA+ is a standard based on CDMA that offers download rates up to 84Mbps and upload rates of up to 22Mbps. LTE is a standard based on GSM/EDGE that offers download rates up to 300Mbps and upload rates up to 75Mbps.
NOTE: Each of these standards continues to develop, so the throughput rates might increase in the future.
GSM 3G (third generation) is a general term that describes networks with a capability of offering transmission rates of up to several Mbps. This can be achieved by increasing the channels’ allocated bandwidth, along with using packet-switching technology.
GSM 4G (fourth generation) is the latest addition to the GSM portfolio and it is still under implementation in most countries. 4G offers transmission rates that exceed 100Mbps, which are suitable for high-speed broadband Internet access. GSM 4G is based exclusively on IP communication, as the spread spectrum radio technology used in 3G networks is replaced by ODFMA multi-carrier transmission that can assure high transmission rates.
VPN Technologies
VPN is a technology that overlays communications networks and gives them the security and manageability required by businesses. With VPN technology, you can set up secure relationships, automated connections, authorisations, and encryption, while still enjoying the low cost and availability of the Internet.
VPNs protect data while in transit across the Internet, or within a company’s enclave. The VPN has many capabilities, but the primary functions include the following:
- Keep data confidential (encryption)
- Ensure the identities of two parties communicating (authentication)
- Safeguard the identities of communicating parties (tunnelling)
- Ensure data is accurate and in its original form (non-repudiation)
- Guard against packets being sent over and over (replay prevention)
Even though the VPN concept implies security most of the time, unsecured VPNs also exist. Frame Relay is an example of this, as it provides private communications between two locations but it might not have any security features on top of it. Whether you should add security to the VPN connection depends upon the specific requirements for that connection.
VPN troubleshooting is difficult to manage because of the lack of visibility in the service provider infrastructure. The service provider is usually seen as a cloud that aggregates all the network locations’ connections. When performing VPN troubleshooting, you should first make sure that the problem does not reside on your devices and only then should you contact your service provider.
There are many types of VPN technologies, including the following:
- Site-to-Site VPNs, or Intranet VPNs, for example Overlay VPNs (like Frame Relay) or Peer-to- Peer VPNs (like MPLS). You would use these when you want to connect different locations over the public infrastructure. When using a peer-to-peer infrastructure, you can seamlessly communicate between your sites without worrying about IP addressing overlap.
- Remote Access VPNs, for example Virtual Private Dial-up Network (VPDN), which is a dialup approach for the VPN that is usually done with security in mind.
- Extranet VPNs, when you want to connect to business partners or customer networks.
When you use VPNs, you are often tunnelling traffic in order to send it over an infrastructure. One tunnelling methodology for Layer 3 is called Generic Routing Encapsulation (GRE). GRE allows you to tunnel traffic but it does not provide security. In order to tunnel traffic and also provide security, you can use a technology called IP Security (IPSec). This is a mandatory implementation component of IPv6 but it is not a requirement for IPv4. IPSec is also used in conjunction with Authentication, Authorization, and Accounting (AAA) services, which allows tracking of user activity.
The main benefits of VPNs include the following:
- Scalability (you can continuously add more sites to the VPN)
- Flexibility (you can use very flexible technologies like MPLS)
- Cost (you can tunnel traffic through the Internet without much expense)
MPLS
Multiprotocol Label Switching (MPLS) functions by appending a label to any type of packet. The packet is then forwarded through the network infrastructure based on this label value, instead of any Layer 3 information. The labeling of the packet provides very efficient forwarding and allows MPLS to work with a wide range of underlying technologies. By simply adding a label in the packet header, MPLS can be used in many Physical and Data Link Layer WAN implementations.
The MPLS label is positioned between the Layer 2 header and the Layer 3 header. By using MPLS, overhead is added only when the packet enters the service provider cloud. After entering the MPLS network, packet switching is done much faster than in traditional Layer 3 networks because it is based only on swapping the MPLS label, instead of stripping the entire Layer 3 header.
MPLS comes in two different flavours:
- Frame Mode MPLS
- Cell Mode MPLS
Frame Mode MPLS is the most popular MPLS type, and in this scenario the label is placed between the Layer 2 header and Layer 3 header (for this reason MPLS is often considered a Layer 2.5 technology). Cell Mode MPLS is used in ATM networks and uses fields in the ATM header that are used as the label.
MPLS-capable routers are also called Label Switched Routers (LSRs), and these routers come in two flavours:
- Edge LSR (PE routers)
- LSR (P routers)
PE routers are Provider Edge devices that take care of label distribution; they forward packets based on labels and they are responsible for label insertion and removal. P routers are Provider routers and their responsibility consists of label forwarding and efficient packet forwarding based on labels.
Basic Serial Line Configuration
If you don’t want to change the default HDLC encapsulation, then, in order to set up your WAN connection, you need only to do the following:
- Add an IP address to your interface
- Bring the interface up (with the no shut command)
- Ensure there is a clock rate on the DCE side
Here is the configuration if you have the DCE cable attached:
Router#config t Router(config)#interface Serial0 Router(config-if)#ip address 192.168.1.1 255.255.255.0 Router(config-if)#clock rate 64000 Router(config-if)#no shutdown Router(config-if)#^Z Router#
PPPoE
Point-to-Point Protocol over Ethernet (PPPoE) is a network protocol used to encapsulate PPP frames inside Ethernet frames.
As customers deploy ADSL, they must support PPP-style authentication and authorisation over a large installed base of legacy bridging customer premises equipment (CPE). PPPoE provides the ability to connect a network of hosts over a simple bridging access device to a remote access concentrator or aggregation concentrator. With this model, each host uses its own PPP stack, thus presenting the user with a familiar user interface. Access control, billing, and type of service can be done on a per-user, rather than a per-site, basis.
As specified in RFC 2516, PPPoE has two distinct stages: a discovery stage and a session stage. When a host initiates a PPPoE session, it must first perform discovery to identify which server can meet the client’s request, and then identify the Ethernet MAC address of the peer and establish a PPPoE session ID. While PPP defines a peer-to-peer relationship, discovery is inherently a client-server relationship.
PPPoE Configuration
The following sections cover server (ISP premises) and client PPPoE configurations. I’ve included them because the CCNA syllabus now mandates that you know how to configure PPPoE!
Server Configuration
The first step in creating the PPPoE server configuration is to define a BBA (broadband aggregation) group which will manage the incoming connections. This BBA group must be associated to a virtual template:
Router(config)#bba-group pppoe GROUP Router(config-bba-group)#virtual-template 1
The next step is to create a virtual template for the customer-facing interface. On the virtual template you need to configure an IP address and a pool of addresses from which clients are assigned a negotiated address:
Router(config)#interface virtual-template 1 Router(config-if)#ip address 10.10.10.1 255.255.255.0 Router(config-if)#peer default ip address pool POOL
The IP pool is defined in global configuration mode. This is similar to a DHCP pool configuration:
Router(config)#ip local pool POOL 10.10.10.2 10.10.10.254
The final step is to enable the PPPoE group on the customer-facing interface:
Router(config)#interface FastEthernet0/0 Router(config-if)#no ip address Router(config-if)#pppoe enable group GROUP Router(config-if)#no shutdown
Client Configuration
On the client side a dialer interface has to be created. This will manage the PPPoE connection. The dialer interface can be assigned a manual IP address or can be instructed to request one from the server ( using the ip address negotiated command):
Router(config)#interface dialer1 Router(config-if)#dialer pool 1 Router(config-if)#encapsulation ppp Router(config-if)#ip address negotiated Router(config)#interface FastEthernet0/0 Router(config-if)#no ip address Router(config-if)#pppoe-client dial-pool-number 1 Router(config-if)#no shutdown
Authentication
In order to secure the PPPoE connection, you can use two methods:
- PAP (Password Authentication Protocol) – insecure, sends the credentials (both username and password) in plain text
- CHAP (Challenge Handshake Authentication Protocol) – secure (clear text username and MD5 hashed password), the preferred method
PAP can be configured as follows:
Server(config)#username Client password Password Server(config)#interface virtual-template 1 Server(config-if)#ppp authentication pap Server(config-if)#ppp pap sent-username Server password Password Client(config)#username Server password Password Client(config)#interface dialer 1 Client(config-if)#ppp authentication pap Client(config-if)#ppp pap sent-username Client password Password
CHAP can be configured as follows:
Server(config)#username Client password Password Server(config)#interface virtual-template 1 Server(config-if)#ppp authentication chap Client(config)#username Server password Password Client(config)#interface dialer 1 Client(config-if)#ppp authentication chap
PPPoE Verification and Troubleshooting
The following message appears on the client console after the PPPoE session has successfully formed:
%DIALER-6-BIND: Interface Vi1 bound to profile Di1 %LINK-3-UPDOWN: Interface Virtual-Access1, changed state to up %LINEPROTO-5-UPDOWN: Line protocol on Interface Virtual-Access1, changed state to up
The following command can be used on the client router to verify the dialer interface obtained (negotiated) and the IP address from the PPPoE server:
Router#show ip interface brief Interface IP-Address OK? Method Status Protocol Virtual-Access1 unassigned YES unset up/up Dialer1 10.10.10.2 YES IPCP up/up
The following command can be used on the client router to show the PPPoE session status:
Router#show pppoe session
1 client session
Uniq ID PPPoE RemMAC Port Source VA State
SID LocMAC VA-st
N/A 16 ca00.4843.0008 Fa0/0 Di1 Vi1 UP
ca01.4843.0008 UP
Useful troubleshooting commands for PPPoE connections are as follows:
Router#debug ppp ? authentication CHAP and PAP authentication bap BAP protocol transactions cbcp Callback Control Protocol negotiation elog PPP ELOGs error Protocol errors and error statistics forwarding PPP layer 2 forwarding mppe MPPE Events multilink Multilink activity negotiation Protocol parameter negotiation packet Low-level PPP packet dump
Troubleshooting WAN Connections
When trying to bring up a WAN connection (forgetting PPP and Frame Relay for the moment), you could use the OSI model:
Layer 1 – Check the cable to ensure that it is attached correctly. Has the no shut command been applied? Is there a clock rate applied to the DCE side?
RouterA#show controllers serial 0 HD unit 0, idb = 0x1AE828, driver structure at 0x1B4BA0 buffer size 1524 HD unit 0, V.35 DTE cable RouterA#show ip interface brief Interface IP-Address OK? Method Status Protocol Serial0 11.0.0.1 YES unset administratively down down Ethernet0 10.0.0.1 YES unset up up
Layer 2 – Check to ensure that the correct encapsulation is applied to the interface. Ensure that the other side of the link has the same encapsulation type.
RouterB#show interface Serial0 Serial1 is down, line protocol is down Hardware is HD64570 Internet address is 12.0.0.1/24 MTU 1500 bytes, BW 1544 Kbit, DLY 1000 usec, rely 255/255, load 1/255 Encapsulation HDLC, loopback not set, keepalive set (10 sec)
Layer 3 – Is the IP address and subnet mask correct? Does the subnet mask match the other side?
RouterB#show interface Serial0 Serial1 is down, line protocol is down Hardware is HD64570 Internet address is 12.0.0.1/24 MTU 1500 bytes, BW 1544 Kbit, DLY 1000 usec, rely 255/255, load 1/255 Encapsulation HDLC, loopback not set, keepalive set (10 sec)
Section 41 Questions
- Name at least three WAN categories.
- The need for NBMA appears when there is no native _______ support for a group of systems that want to communicate over the same network.
- In NBMA environments you still need to bind the Layer 3 address (IP address) to the Layer 2 address (DLCI). This can be done in an automated fashion, using a technology called Inverse ARP. True or false?
- Name 2 NBMA interface types.
- _______ requires DTE and DCE and is the default encapsulation type on Cisco routers.
- _______ technologies involve the use of carrier Ethernet in Metropolitan Area Networks (MANs).
- T1 is a standard often used in what geographical regions?
- What are the two flavours of ISDN?
- _______ is the most common form of DSL connection that functions over standard telephone lines. It offers unequal download and upload throughput, with the download rate being higher than the upload rate.
- _______ functions by appending a label to any type of packet.
Section 41 Answers
- Circuit-switched, cell-switched, broadband, leased-line, and packet-switched.
- Broadcast.
- True.
- Multipoint and Point-to-Point.
- HDLC.
- Metro Ethernet.
- North America, Japan, and South Korea.
- BRI and PRI.
- ADSL.
- MPLS.
Section 41 Lab
PPPoE Lab
Configure PPPoE with CHAP authentication between two routers as per the information presented in this module:
Server configuration:
Router(config)#bba-group pppoe GROUP Router(config-bba-group)#virtual-template 1 Router(config)#interface virtual-template 1 Router(config-if)#ip address 10.10.10.1 255.255.255.0 Router(config-if)#peer default ip address pool POOL Router(config)#ip local pool POOL 10.10.10.2 10.10.10.254 Router(config)#interface FastEthernet0/0 Router(config-if)#no ip address Router(config-if)#pppoe enable group GROUP Router(config-if)#no shutdown
Client configuration:
Router(config)#interface dialer1 Router(config-if)#dialer pool 1 Router(config-if)#encapsulation ppp Router(config-if)#ip address negotiated Router(config)#interface FastEthernet0/0 Router(config-if)#no ip address Router(config-if)#pppoe-client dial-pool-number 1 Router(config-if)#no shutdown
CHAP Authentication:
Server(config)#username Client password Password Server(config)#interface virtual-template 1 Server(config-if)#ppp authentication chap Client(config)#username Server password Password Client(config)#interface dialer 1 Client(config-if)#ppp authentication chap
Verify the configuration:
Router#show pppoe session
1 client session
Uniq ID PPPoE RemMAC Port Source VA State
SID LocMAC VA-st
N/A 16 ca00.4843.0008 Fa0/0 Di1 Vi1 UP
ca01.4843.0008 UP
