Section 1 Tasks:
Today you will learn about the fol lowing:
- Network devi ces and diagrams
- The OSI and TCP model s
- Cables and media
- Connecting to a router
This module maps to the fol lowing ICND1 syl labus requi rements:
- Recognise the purpose and functions of various network devi ces, such as routers, switches, bridges, and hubs
- Select the components required to meet a given network specification
- Identify common applications and their impact on the network
- Describe the purpose and basi coperation of the protocol s in the OSI and TCP/IP models
- Predict the data flow between two hosts across a network
- Identify the appropriate media, cables, ports, and connectors to connect Cisco network devices to other network devices and hosts in a LAN
Network DevicesNetwork Devices
As a network engineer, you will be using a range of network cables and other media. You need to know which cables will work with which devices and interfaces for WAN, LAN, and management ports. Much of the information will serve as a review if you have studied the CompTIA Network+ before the CCNA (which I recommend).
Common Network Devices
Network Switches
Only a few years ago, networks were still pretty small. This meant that you could simply plug all devices into a hub or a number of hubs. The hub’s job was to boost the signal on the network cable, if required, and then pass out the data on the wire to every other device plugged in. The problem with this, of course, is that the message was intended for only one network host, but it would be sent to tens or hundreds of other hosts connected to other hubs on the network. (Hubs and switching technology will be covered in more detail in the next module.)
Network switches are a more intelligent version of hubs. Switches use Content Addressable Memory (CAM) and therefore have the ability to remember which device is plugged into which port. Cisco manufactures switch models which are designed to work in small offices and all the way up to large enterprise networks consisting of thousands of devices. We will explore this in more detail later, but, basically, switches operate by using the device’s MAC addresses (known as Layer 2) and IP addresses (known as Layer 3), or they can perform more complex tasks, such as processing lists of permit/deny traffic or protocols and port numbers (known as Layer 4), or a combination of all these layers and more. We will cover what comprises these layers and their functions later in this module.
Early versions of switches were referred to as network bridges. Bridges examined the source ports and MAC addresses of frames in order to build a table and make forwarding decisions. The tables were typically accessed via software, whereas switches used hardware (i.e., Application Specific Integreated Chips, or ASICs) to access a CAM table (more on this later). Therefore, a switch can be thought of as a multiport bridge.
Using a switch (see Figure 1.1) allows you to divide your network into smaller, more manageable sections (known as segments). This in turn allows the teams who work inside your company, such as human resources, finance, legal, etc., to work on the same section of the network at the same time, which is useful because the devices will spend most of their time communicating with each other.

Figure 1.1 - Cisco 2960 Switch
Each device will connect to an interface on the switch, which is referred to as a port. Common network port speeds are 100Mbps and 1000Mbps (usually referred to as 1Gbps). There are often fibre ports you can use to connect a switch to another switch. Each switch features management ports, which you can connect to in order to perform an initial configuration and gain general access for maintenance over the network.
Figure 1.2 below shows a close-up of a Cisco 2960 switch. Several models of the 2960 are available to meet the needs of a small- to medium-sized business.
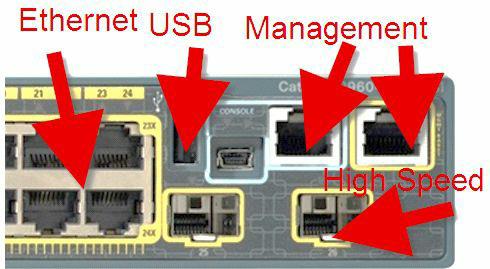
Figure 1.2 - Switch Interface Types
You can also use IP telephones with the switches and, even better, the switch ports can provide power to these telephones (using power over Ethernet (PoE) interfaces). The basic network switch will be used to:
- Connect network devices such as printers and PCs
- Give access to network servers and routers
- Segment the network with VLANs
VLANs are virtual Local Area Networks. We will cover these in detail in Section 2.
Routers
As a Cisco engineer, you will spend a lot of time installing, configuring, and troubleshooting routers. For this reason, over half of the CCNA syllabus is dedicated to learning all about router configuration.
A router (see Figure 1.3) is a device used for networking. While network switches involve devices on the same network communicating with each other, the router communicates with devices on different networks. Older models of routers only had ports, which were physically built into them and attached to the motherboard. This is still sometimes the case, but modern networks now require a router to perform functions for IP telephony, switching, and security, and to connect to several types of telecoms companies. For this reason, routers are also modular, which means you have the router chassis and empty slots into which you can connect a variety of routing or switching modules.

Figure 1.3 - Modular Cisco Router with a Blank Slot to the Right
The Cisco website has a lot of advice and information available to explain which router model will suit your business needs. There are also tools which will help you select the correct model and operating system. It’s well worth your time learning how to navigate the support and configuration pages and bookmarking them for quick reference.
How Networks Are Represented in Diagrams
All network engineers need a common method to communicate, despite which vendor and telecoms provider they are using. If I had to describe my network topology to you for design or security recommendations, it would work much better if it were in an agreed format as opposed to something I had drawn by hand from memory. The Cisco Certified Design Associate (CCDA) exam is where you will learn about network topologies in far more detail. As for the CCNA exam, you will need a basic understanding of these topologies because the exam may present network issues and ask where you think the problem lies.
Here are the common symbols for network devices you will encounter in your work as a network engineer. You can download these icons from the Cisco website if you type “Cisco icons” in your browser’s search engine. We use either plain blue or color (for the Kindle version). I’ve used a mix of the most common router and switch symbols throughout the book so get used to the types you will see in network diagrams in the real world.
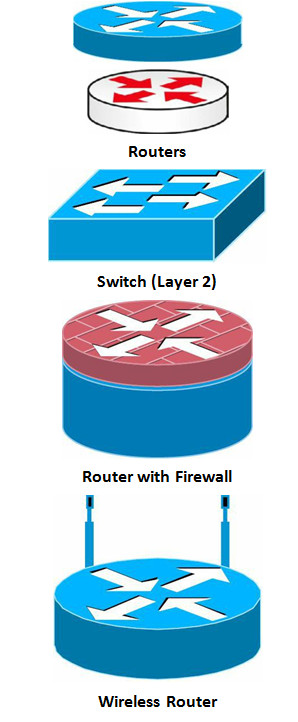
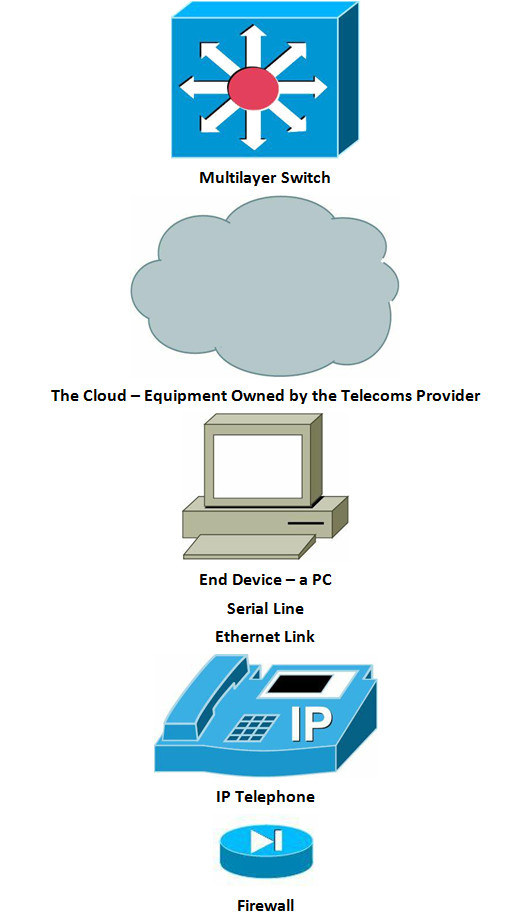
LAN and WAN Topologies
Topology refers to how network equipment is arranged in order to communicate. How this is done could be limited by the communication protocols the equipment uses, cost, geography, or other factors, such as the need for redundancy should the main link fail.
You should also note that there is often a difference between physical and logical topology. Physical topology is how the network appears when you look at it, whereas logical topology is how the network sees itself. The most common topologies are described in the following sections.
Point-to-Point
This topology is used mainly for WAN links. A point-to-point link is simply one in which one device has one connection to another device. You could add a secondary link connecting each device but if the device itself fails, then you lose all connectivity.

Figure 1.4 - Point-to-Point Topology
Bus
This topology was created with the first Ethernet networks, where all devices had to be connected to a thick cable referred to as the backbone. If the backbone cable fails, then the network goes down. If a cable linking the device to the backbone cable fails, then only that device will lose connection.
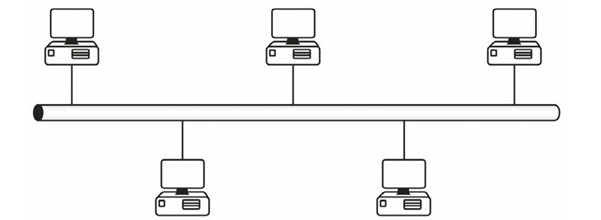
Figure 1.5 - Bus Topology
Star
This is probably the most common topology you will encounter. Each network device is connected to a central hub or switch. If one of the cables to the devices fails, then only that device becomes disconnected.
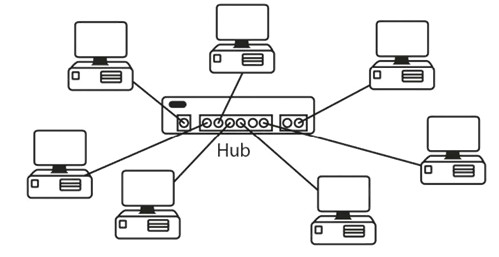
Figure 1.6 - Star Topology
Ring
A ring topology is used by token ring networks and Fiber Distributed Data Interface (FDDI) networks, both of which went out of use several years ago.
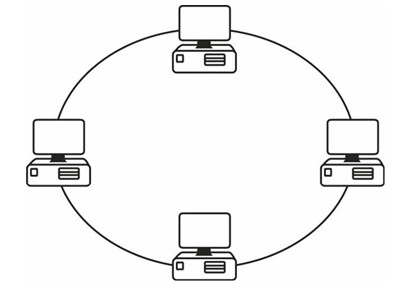
Figure 1.7 - Token Ring Topology
A ring topology that is used with FDDI networks employs a dual-ring connection to provide redundancy should one ring fail.
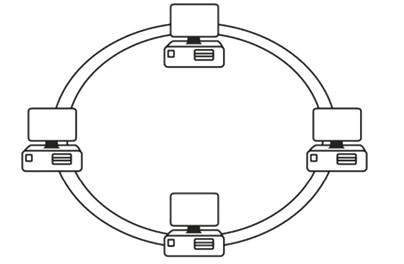
Figure 1.8 - Dual-Ring Topology
Mesh
When downtime is not an option, a mesh topology can be considered. Full-mesh networks provide a connection to each device from every other device. This solution is often used with WAN connections.
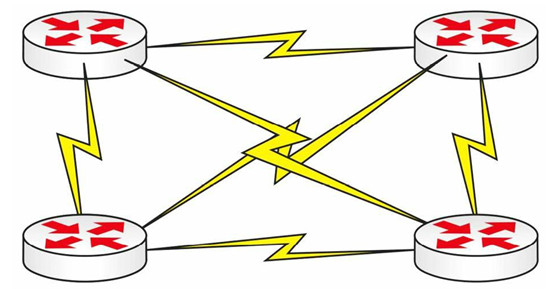
Figure 1.9 - Full-Mesh Topology
Typically, this type of solution will prove very costly. For this reason, partial-mesh topologies can be considered. This means that there may be one or more “hops,” or routers, to get to each device.
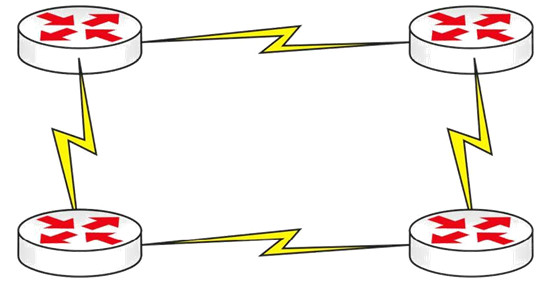
Figure 1.10 - Partial-Mesh Topology
Hub-and-Spoke
Due to the cost of equipment and WAN connections and bandwidth, companies often use a hub-and-spoke design. A powerful router is in the centre (hub), usually at a company’s HQ, while the spokes represent remote offices, which require less powerful routers. There are obviously issues with this type of topology; however, it is still widely used. We will revisit hub-and-spoke topologies again in the Frame Relay section, as it still forms a large part of the CCNA syllabus because of the routing issues it creates.
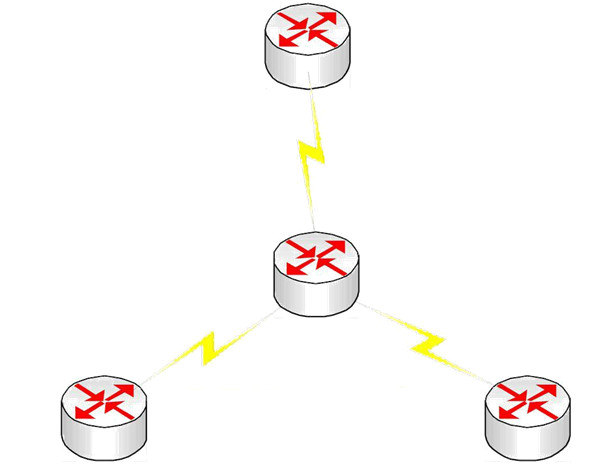
Figure 1.11 - Hub-and-Spoke Topology
Physical versus Logical
When you can see the network equipment, you are looking at the physical topology. This can be misleading because, although the network appears to be wired in a star fashion, it could in fact be working logically as a ring. A classic example of this is a ring network. Although the traffic circulates round the ring in a circular fashion, all of the devices plug into a hub. The ring is actually inside the token ring hub, so you can’t see it from the outside, as illustrated in Figure 1.12 below:
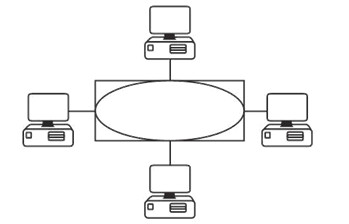
Figure 1.12 - The Ring Is Inside the Hub
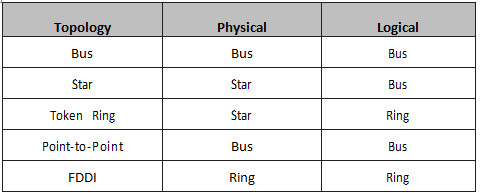
You may be asked to identify the different types of networks, both physically and logically. It is a good idea to remember that the physical topology is what you can see and the logical topology is what the network can see (i.e., how the data flows). This is summarised in Table 1.1 below:
Table 1.1 – Physical versus Logical Topologies
OSI and TCP Models
The OSI Model
Open Standards Interconnection (OSI) was created by the International Organization for Standardization (ISO). With the technology boom came the rise of several giants in the fields of networking devices and software, including Cisco, Microsoft, Novell, IBM, HP, Apple, and others. Each vendor had their own cable types and ports and ran their own communication protocols. This caused major problems if you wanted to buy routers from one company, switches from another, and servers from yet another.
There were workarounds for these problems, such as deploying gateways on the network that could translate between protocols, but such solutions created bottlenecks (i.e., slow portions of the network) and made troubleshooting very difficult and time-consuming. Eventually, vendors had to agree on a common standard which worked for everyone, and the free suite of protocols called Transmission Control Protocol/Internet Protocol (TCP/IP) was ultimately adopted by most. In the end, those vendors who failed to adopt TCP/IP lost market share and went bust.
The ISO created the OSI model to help vendors agree on a set of common standards with which they could all work. This involved dividing network functions into a set of logical levels or layers. Each layer would perform a specific set of functions, so, for example, if your company wanted to focus on network firewalls, they would work with other vendors’ equipment.
The advantage was that each device was designed to perform a specific role well, rather than several roles inadequately. Customers could choose the best device for their solution without being tied to one vendor. Troubleshooting became much easier because certain errors could be traced to a certain OSI layer.
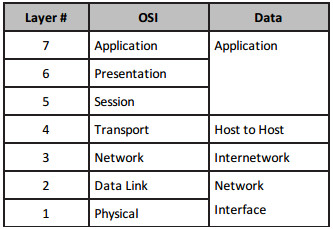
The OSI model divides all network functions into seven distinct layers. The layered model starts at Layer 7 and goes all the way down to Layer 1. The more complex functions, which are closer to the user, are at the top, moving down to network cable specifications at the bottom layer, as illustrated in Table 1.2 below:
Table 1.2 – The OSI Model
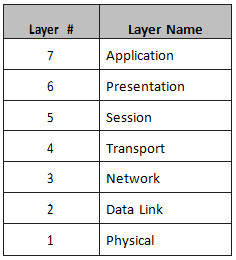
You can easily remember the names of the layers with the mnemonic “All People Seem To Need Data Processing.” I would certainly get used to referring to each layer by its number because this is how real-world network technicians use the OSI.
As data is passed down from the top layers to the bottom for transportation across the physical network media, the data is placed into different types of logical data boxes. Although we often call these data boxes “packets,” they have different names depending upon the OSI layer. The process of data moving down the OSI model is referred to as encapsulation (see Figure 1.13). Moving back up and having these boxes stripped of their data is called de-encapsulation.
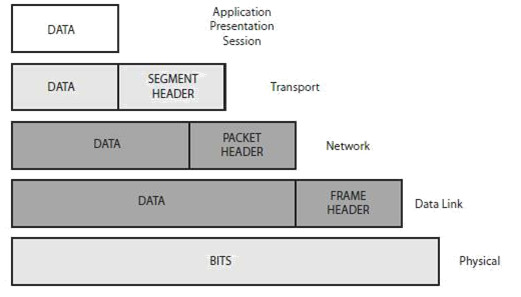
Figure 1.13 - Encapsulation
For the CCNA exam, you will be expected to understand the OSI model and which applications and protocols fit in which layer. You may also have to apply your troubleshooting knowledge using the OSI layered approach. Let’s examine each layer of the OSI, starting with Layer 7.
Layer 7 – Application Layer
This layer is the closest layer to the end-user, you and me. The Application Layer isn’t the operating system of the devices but usually provides services such as e-mail (SNMP and POP3), web browsing (using HTTP), and file transfer services (using FTP). The Application Layer determines resource availability.
Layer 6 – Presentation Layer
The Presentation Layer presents data to the Application Layer. Multimedia works here, so think MP4, JPEG, GIF, etc. Encryption, decryption, and data compression also take place at this layer.
Layer 5 – Session Layer
The role of the Session Layer is to set up, manage, and terminate sessions or dialogues between devices. These take place over logical links, and what is really happening is the joining of two software applications. SQL, RPC, and NFS all work at the Session Layer.
Layer 4 – Transport Layer
The role of the Transport Layer is to break down the data from the higher layers into smaller parts, which are referred to as segments (at this layer). Virtual circuits are set up here, which are required before devices can communicate.
Before the data can be passed across the network, the Transport Layer needs to establish how much data can be sent to the remote device. This will depend upon the speed and reliability of the link from end to end. If you have a high-speed link but the end-user has a low-speed link, then the data will need to be sent in smaller chunks.
The three methods used to control data flow are as follows:
- Flow control
- Windowing
- Acknowledgements
Flow Control
If the receiving system is being sent more information than it can process, it will ask the sending system to stop for a short time. This normally happens when one side uses broadband and the other uses a dial-up modem. The packet sent telling the other device to stop is known as a source quench message.
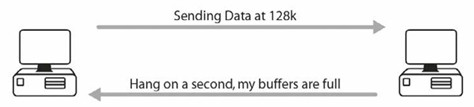
Figure 1.14 - Flow Control
Windowing
With windowing, each system agrees upon how much data is to be sent before an acknowledgment is required. This “window” opens and closes as data moves along in order to maintain a constant flow.

Figure 1.15 - Windowing
Acknowledgements
When a certain amount of segments is received, the fact that they all arrived safely and in the correct order needs to be communicated to the sending system.

Figure 1.16 - Acknowledgements
All of this is agreed upon during a process known as a three-way handshake (see Figure 1.17). This is where you send a packet to establish the session. This first packet is called a synchronise (SYN) packet. Then the remote device responds with a synchronise acknowledgement (SYN-ACK) packet. The session is established in the third phase when an acknowledgement (ACK) packet is sent. This is all done via the TCP service.

Figure 1.17 - Three-Way Handshake
The Transport Layer includes several protocols, and the most widely known are Transmission Control Protocol (TCP) and User Datagram Protocol (UDP), which are part of the TCP/IP suite of protocols. This suite is well known because it is the standard used on the Internet. TCP is known as a reliable connection-oriented protocol. It uses the three-way handshake, windowing, and other techniques to guarantee that the data gets to its destination safely. Many protocols use TCP, including Telnet, HTTPS, and FTP (although it sits at the Application Layer, it does use TCP).
UDP, on the other hand, is known as a connectionless protocol. It numbers each packet and then sends them to their destination. It never checks to see whether they arrived safely and will never set up a connection before sending the packet. Sometimes data is not that important and the application developer decides that the information can always be sent again if it fails to arrive at its destination.
Why is UDP used at all? TCP uses a lot of bandwidth on the network and there is a lot of traffic sent back and forth to set up the connection, even before the data is sent. This all takes up valuable time and network resources. UDP packets are a lot smaller than TCP packets and they are very useful if a really reliable connection is not that necessary. Protocols that use UDP include TFTP.
Layer 3 – Network Layer
The Network Layer takes the segments from the Transport Layer and breaks them down into smaller units called packets. Most network engineers refer to data as packets, no matter what the OSI layer, which is fine; however, just remember that they are technically packets at the Network Layer.
The Network Layer must determine the best path to take from one network to another; for this reason, routers work at this layer. Routers use logical addressing here, and TCP/IP addressing is called IP addressing, which will be covered in detail later.
Layer 2 – Data Link Layer
The Data Link Layer chops down packets into smaller units referred to as frames. Layer 2 switches work at this layer and use hardware or MAC addresses, so they can switch traffic much faster because there is no need to check IP addresses and routing tables. WAN protocols work at Layer 2, including HDLC, ISDN, and PPP. Ethernet also works at Layer 2.
In order to interface with the upper and lower levels, the Data Link Layer is further subdivided into the Logical Link Control (LLC) Sublayer and the Media Access Control (MAC) Sublayer. The LLC Sublayer interfaces with the Network Layer and the MAC Sublayer interfaces with the Physical Layer.
Layer 1 – Physical Layer
At this layer, frames are converted into bits for placing on the wire. These bits consist of electrical pulses, which are read as “on” and “off” bits, or in binary 1s and 0s, respectively. Hubs work at this layer, and here is where you will find cable specifications, such as RJ45.
OSI Troubleshooting
Using a layered approach can be very effective when you’re troubleshooting your network. The only decision from this point onwards is to determine which way you want to use the OSI stack – top-down, bottom-up, or divide-and-conquer method, which involves focusing on sections of the network in turn.
I recommend using the bottom-up method at the beginning so you don’t waste time looking at applications when the cause can often be found at the lower layers, such as loose or broken cables or incorrect IP addressing. As you gain more experience, using the divide-and-conquer method will probably be faster, depending on the symptoms. If you start at the bottom layer and work your way up, you would do something like this:
Layer 1 – Are all the cables inserted into the ports correctly, or have they come loose? Are the cable ends bent or worn out? If cables are the problem, you will usually see an amber light showing on the device when it should be green. Has somebody forgotten to add the correct speed to the interface? Has the speed of the Ethernet port been set correctly? Has the interface been opened for use by the network administrator?
Layer 2 – Has the correct protocol been applied to the interface so it agrees with the other side, such as Ethernet/PPP/HDLC, etc.?
Layer 3 – Is the interface using the correct IP address and subnet mask?
Layer 4 – Is the correct routing protocol being used, and is the correct network being advertised from the router?
You will see how to apply these steps as you complete the labs in this book. Experts may argue that some Layer 4 issues are at Layer 3, some Layer 2 issues are actually at Layer 1, and so on. I prefer to focus on the fact that we are applying a layered troubleshooting method rather than debating about whether the correct issue is at the correct layer.
The TCP/IP, or DoD, Model
The TCP/IP model is another framework and an alternative to the OSI model. The TCP/IP model is a four or five-layered model created by an association known as DARPA. It is also known as the Department of Defense (DoD) model. The four layers from the top down are as follows:
4 – Application [Telnet/FTP/DNS/RIP]
3 – Transport/Host-to-Host [UDP/TCP/ICMP]
2 – Internet or Internetwork [IPSec/IP]
1 – Link/Network Interface [Frame Relay/Ethernet/ATM]
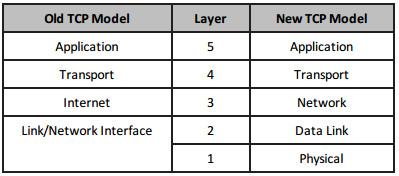
The TCP/IP model has been updated from four to five layers, so you may be asked questions about a five-layered TCP model in the exam. The upper layers are closer to the end-user and the lower layers describe how the technology or protocols interact with other systems. The five-layered TCP model is as follows:
5 – Application [Telnet/FTP/DNS/RIP/HTTP]
4 – Transport/Host-to-Host [UDP/TCP/ICMP]
3 – Network [IPSec/IP]
2 – Data Link [Ethernet/Frame Relay/PPP]
1 – Link/Network Interface/Physical [Bits on the wire]
A five-layered TCP model allows for more granularity and it more accurately represents what actually occurs before data is put onto the wire. For example, at Layer 2 encapsulation of data occurs and addressing takes place (i.e., Data Link addressing). Cisco seem to prefer the five-layered model when it comes to exam questions.
Data is encapsulated as it travels down from the Application Layer to the Physical Layer in exactly the same way as demonstrated in the OSI model, as illustrated in Table 1.3 below:
Table 1.3 – The Five-Layered TCP Model
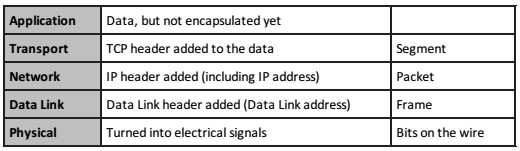
You may be asked how the TCP/IP model maps to the OSI model. This is illustrated below in Table 1.4:
Table 1.4 – Mapping the TCP/IP Model to the OSI Model
Cisco now prefer the (new) TCP model over the OSI model as a network framework, but they still expect you to understand the OSI model and thus have left it in the syllabus for now.
Table 1.5 – Old versus New TCP Model
TCP/IP
TCP/IP is a complete suite of protocols and services which enable communication to take place over networks. Earlier competitors to TCP/IP, such as IPX/SPX, have all but died out due to their lack of adoption and ongoing development.
TCP/IP is a freely available and free to use set of standards maintained by the Internet Engineering Task Force (IETF), and it is used for end-to-end device connectivity. It has been developed and improved upon through submission of Requests for Comments (RFCs), which are documents submitted by engineers to convey new concepts or for peer review. One example is Network Address Translation (NAT) discussed in RFC 2663. IETF adopted some of these RFCs as Internet standards. You can learn more about the IETF and RFCs at the link below:
TCP/IP offers many services but many are outside the scope of the CCNA exam and will not be covered. I will also omit those covered in other sections, such as DNS and DHCP. The following sections outline the basics of TCP/IP. Because the CCNA isn’t a basic networking exam, it is expected that you already have a good grasp of networking concepts such as those learned in the Network+ exam from CompTIA.
Transmission Control Protocol (TCP)
TCP operates at the Transport Layer of the OSI model. It provides a connection-oriented service for reliable transfer of data between network devices. TCP also provides flow control, sequencing, windowing, and error detection. It attaches a 32-bit header to the Application Layer data, which is in turn encapsulated in an IP header. TCP is described in RFC 793. Common TCP ports include the following:
- FTP Data – 20
- FTP Control – 21
- SSH – 22
- Telnet – 23
- SMTP – 25
- DNS – 53 (also uses UDP)
- HTTP – 80
- POP3 – 110
- NNTP – 119
- NTP – 123
- TLS/SSL – 443
Internet Protocol (IP)
IP operates at the Network Layer of the OSI model. It is connectionless and is responsible for transporting data over the network. IP addressing is a function of Internet Protocol. IP examines the Network Layer address of every packet and determines the best path for that packet to take to reach its destination. IP is discussed in detail in RFC 791.
User Datagram Protocol (UDP)
UDP also operates at the Transport Layer of the OSI model. It transports information between network devices but, unlike TCP, no connection is established first. UDP is connectionless, gives best-effort delivery, and gives no guarantee that the data will reach its destination. UDP is much like sending a letter with no return address. You know it was sent, but you never know if the letter got there.
UDP consumes less bandwidth than TCP does and is suitable for applications in which low latency is preferred over reliability or guarantees. Both TCP and UDP are carried over IP. UDP is described in RFC 768. Common UDP port numbers include the following:
- DNS – 53
- TFTP – 69
- SNMP – 161/162
File Transfer Protocol (FTP)
FTP operates at the Application Layer and is responsible for reliably transporting data across a remote link. Because it has to be reliable, FTP uses TCP for data transfer.
You can debug FTP traffic with the debug ip ftp command.
FTP uses ports 20 and 21. Usually, a first connection is made to the FTP server from the client on port 21. A second data connection is then made either leaving the FTP server on port 20 or from a random port on the client to port 20 on the FTP server. You may wish to read more about active versus passive FTP for your own information, but it is unlikely that this will be covered in CCNA-level exams.
Trivial File Transfer Protocol (TFTP)
For less reliable transfer of data, TFTP provides a good alternative. TFTP provides a connectionless transfer by using UDP port 69. TFTP can be difficult to use because you have to specify exactly the directory in which the file is located.
To use TFTP, you need to have a client (the router, in your case) and a TFTP server, which could be a router or a PC, or a server on the network (preferably on the same subnet). You need to have TFTP software on the server so the files can be pulled off it and forwarded on to the client.

TFTP is used extensively on Cisco routers to back up configurations and upgrade the router. The following command will carry out these functions:
RouterA#copy tftp flash:
You will be prompted to enter the IP address of the other host in which the new flash file is located:
Address or name of remote host []? 10.10.10.1
You will then have to enter the name of the flash image on the other router:
Source filename []? / c2500-js-l.121-17.bin Destination filename [c2500-js-l.121-17.bin]?
If you have an older version of IOS, you may be prompted to erase the flash on your router before copying, and then the file will be transferred. When the router reloads, your new flash image should be available for use.
Other optional commands are copy flash tftp if you want to store a backup copy or copy running config tftp if you want to back up your running configuration file.
You can run a debug on TFTP traffic with the debug tftp command.
Simple Mail Transfer Protocol (SMTP)
SMTP defines how e-mails are sent to the e-mail server from the client. It uses TCP to ensure a reliable connection. SMTP e-mails are pulled off the SMTP server in different ways, and SMTP is used as an e-mail delivery service by most networks. POP3 is another popular way to do this.
POP3 is a protocol that transfers the e-mail from the server to the client. SMTP uses TCP port 25.
Hyper Text Transfer Protocol (HTTP)
HTTP uses TCP (port 80) to send text, graphics, and other multimedia files from a web server to clients. This protocol allows you to view web pages, and it sits at the Application Layer of the OSI model. HTTPS is a secure version of HTTP that uses Secure Sockets Layer (SSL) or Transport Layer Security (TLS) to encrypt the data before it is sent.
You can debug HTTP traffic with the debug ip http command.
Telnet
Telnet uses TCP (port 23) to allow a remote connection to network devices. You will learn more about Telnet in the labs. Telnet is not secure so many administrators are now using Secure Shell (SSH), which uses TCP port 22, as an alternative to ensure a secure connection. Telnet is the only utility that can check all seven layers of the OSI model, so if you Telnet to an address, then all seven layers are working properly. If you can’t Telnet to another device, it doesn’t necessarily indicate a network problem. There could be a firewall or an access control list blocking the connection purposely, or Telnet may not be enabled on the device.
In order to connect remotely to a Cisco router or switch, there must be an authentication method for VTY lines configured on the router. If you are trying to Telnet to another device but cannot connect to it, you can enter Ctrl+Shift+6 and then enter X to quit. To quit an active Telnet session, you can simply type exit or disconnect.
You can debug Telnet with the debug telnet command.
Internet Control Message Protocol (ICMP)
ICMP is a protocol used to report problems or issues with IP packets (or datagrams) on a network. ICMP is a requirement for any vendor who wishes to use IP on their network. When a problem is experienced with an IP packet, the IP packet is destroyed and an ICMP message is generated and sent to the host that originated the packet.
As defined in RFC 792, ICMP delivers messages inside IP packets. The most popular use of ICMP is to send ping packets to test the network connectivity of remote hosts. A ping command issued from a network device generates an echo request packet that is sent to the destination device. Upon receiving the echo request, the destination device generates an echo reply.
Because pings also have a Time to Live (TTL) field, they give a good indication of network latency (delay). The ping output below is from a desktop PC:
C:\>ping cisco.com Pinging cisco.com [198.133.219.25] with 32 bytes of data: Reply from 198.133.219.25: bytes=32 time=460ms TTL=237 Reply from 198.133.219.25: bytes=32 time=160ms TTL=237 Reply from 198.133.219.25: bytes=32 time=160ms TTL=237 Reply from 198.133.219.25: bytes=32 time=180ms TTL=237 Ping statistics for 198.133.219.25: Packets: Sent = 4, Received = 4, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 160ms, Maximum = 460ms, Average = 240ms
In the output above, the ping packet is 32 bytes long, the Time field reports how many milliseconds the response took, and the TTL is the Time to Live field (i.e., how many milliseconds before the packet expires).
The ping command on a Cisco router has a verbose facility that provides more granularity from which you can specify the source you are pinging, how many pings, and what size you are sending, along with other parameters. This feature is very useful for testing and is used several times in the accompanying lab scenarios, as illustrated in the output below:
Router#ping ← press Enter here Protocol [ip]: Target IP address: 172.16.1.5 Repeat count [5]: Datagram size [100]: 1200 Timeout in seconds [2]: Extended commands [n]: yes Source address: ← you can specify a source address or interface here Type of service [0]: Set DF bit in IP header? [no]: yes Data pattern [0xABCD]: Loose, Strict, Record, Timestamp, Verbose[none]: Type escape sequence to abort. Sending 5, 1000-byte ICMP Echos to 131.108.2.27, timeout is 2 seconds: U U U U U Success rate is 0% percent, round-trip min/avg/max = 4/6/12 ms
Several notations represent the response the ping packet receives, as follows:
- ! – One exclamation mark per response
- . – One period for each timeout
- U – Destination unreachable message
- N – Network unreachable message
- P – Protocol unreachable message Q – Source quench message
- M – Could not fragment
- ? – Unknown packet typ
You can terminate a ping session by holding down the Ctrl+Shift+6 keys (all together) and then the X key (on its own).
ICMP packet types are defined in RFC 1700. Learning all the code numbers and names is outside the scope of the CCNA syllabus.
Many junior network engineers misuse the ping facility when it comes to troubleshooting. A failed ping could indicate a network issue or that ICMP traffic is blocked on the network. Because ping attacks are a common way to attack a network, ICMP is often blocked.
Traceroute
Traceroute is a very widely used facility which can test network connectivity and is a handy tool for measurement and management. Traceroute follows the destination IP packets by sending UDP packets with a small maximum TTL field, and then listens for an ICMP time-exceeded response. As the Traceroute packet progresses, the records are displayed hop by hop. Each hop is measured three times. An asterisk [*] indicates that a hop has exceeded its time limit.
Cisco routers use the traceroute command, whereas Windows PCs use tracert, as illustrated in the output below:
C:\Documents and Settings\pc>tracert hello.com Tracing route to hello.com [63.146.123.17] over a maximum of 30 hops: 1 81 ms 70 ms 80 ms imsnet-cl10-hg2-berks.ba.net [213.140.212.45] 2 70 ms 80 ms 70 ms 192.168.254.61 3 70 ms 70 ms 80 ms 172.16.93.29 4 60 ms 81 ms 70 ms 213.120.62.177 5 70 ms 70 ms 80 ms core1-pos4-2.berks.ukore.ba.net [65.6.197.133] 6 70 ms 80 ms 80 ms core1-pos13-0.ealng.core.ba.net [65.6.196.245] 7 70 ms 70 ms 80 ms transit2-pos3-0.eang.ore.ba.net [194.72.17.82] 8 70 ms 80 ms 70 ms t2c2-p8-0.uk-eal.eu.ba.net [165.49.168.33] 9 151 ms 150 ms 150 ms t2c2-p5-0.us-ash.ba.net [165.49.164.22] 10 151 ms 150 ms 150 ms dcp-brdr-01.inet.qwest.net [205.171.1.37] 11 140 ms 140 ms 150 ms 205.171.251.25 12 150 ms 160 ms 150 ms dca-core-02.inet.qwest.net [205.171.8.221] 13 190 ms 191 ms 190 ms atl-core-02.inet.qwest.net [205.171.8.153] 14 191 ms 180 ms 200 ms atl-core-01.inet.net [205.171.21.149] 15 220 ms 230 ms 231 ms iah-core-03.inet.net [205.171.8.145] 16 210 ms 211 ms 210 ms iah-core-02.inet.net [205.171.31.41] 17 261 ms 250 ms 261 ms bur-core-01.inet.net [205.171.205.25] 18 230 ms 231 ms 230 ms bur-core-02.inet.net [205.171.13.2] 19 211 ms 220 ms 220 ms buc-cntr-01.inet.net [205.171.13.158] 20 220 ms 221 ms 220 ms msfc-24.buc.qwest.net [66.77.125.66] 21 221 ms 230 ms 220 ms www.hello.com [63.146.123.17] Trace complete.
The fields in the Traceroute output are as follows:
- ... – Timeout
- U – Port unreachable message
- H – Host unreachable message
- P – Protocol unreachable message
- N – Network unreachable message
- ? – Unknown packet type
- Q – Source quench received
Traceroute is a very useful command when you want to troubleshoot network connectivity issues. Although it is outside the scope of the CCNA syllabus, here is a more detailed explanation of how it operates.
Traceroute works by sequentially incrementing the TTL field of UDP packets (only used in Cisco and Linux; Microsoft Windows tracert command uses ICMP echo request datagrams instead of UDP datagrams as probes) destined for a host and recording the replies received from intermediate routers.
Every packet has a TTL value associated with it and each time the packet reaches a hop, its TTL value is decreased by 1. The first packet is sent to the destination with TTL=1, which reaches Router 1, but because its TTL value has dropped to 0, the router sends an error message (TTL exceeded in transit). Then a second packet is sent with TTL=2. This reaches Router 2, which also sends the same error message that Router 1 sent. This is continued until the destination is reached.
All hops, except for the last one, should return a “TTL exceeded in transit” message, whereas the last hop should return a “destination unreachable/port unreachable” message, indicating that it cannot handle the received traffic (UDP Traceroute packets are typically addressed to a pseudorandom high port on which the end host is not likely to be listening).
Address Resolution Protocol (ARP)
Two types of addressing are used to identify network hosts – the IP (or Layer 3) address and the local (or Data Link Layer) address. The Data Link Layer address is also commonly referred to as the MAC address. Address resolution, as defined in RFC 826, is the process in which the IOS determines the Data Link Layer address from the Network Layer (or IP) address.
ARP resolves a known IP address to a MAC address. When a host needs to transfer data across the network, it needs to know the other host’s MAC address. The host checks its ARP cache and if the MAC address is not there, it sends out an ARP Broadcast message to find the host, as illustrated in Figure 1.18 below:
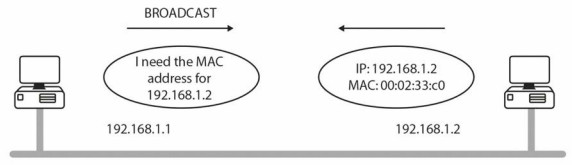
Figure 1.18 - One Host Broadcasts for Another Host’s MAC Address
You can debug ARP with the debug arp command.
An ARP entry is required for communication across the network. You can see that a Broadcast has taken place if there is no ARP entry. It is also important to understand that ARP tables on routers and switches are flushed after a certain amount of time (four hours by default) to conserve resources and prevent inaccurate entries.
On the router below, it has an ARP entry only for its own FastEthernet interface until its neighbour is pinged, so the first of five ping (ICMP) packets fails, as shown by the period followed by four exclamation marks:
Router#show arp Protocol Address Age (min) Hardware Addr Type Interface Internet 192.168.1.1 - 0002.4A4C.6801 ARPA FastEthernet0/0 Router#ping 192.168.1.2 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.1.2, timeout is 2 seconds: .!!!! ← first packet fails due to ARP request Success rate is 80 percent(4/5),round-trip min/avg/max = 31/31/31 ms Router#show arp
| Protocol | Address Age (min) | Hardware Addr | Type | Interface | |
| Internet | 192.168.1.1 | 0002.4A4C.6801 | ARPA | FastEthernet0/0 | |
| Internet | 192.168.1.2 | 0 | 0001.97BC.1601 | ARPA | FastEthernet0/0 |
| Router# | |||||
Proxy ARP
Proxy ARP (see Figure 1.19 below) is defined in RFC 1027. Proxy ARP enables hosts on an Ethernet network to communicate with hosts on other subnets or networks, even though they have no knowledge of routing.
If an ARP Broadcast reaches a router, it will not forward it (by default). Routers do not forward Broadcasts, but if they do know how to find the host (i.e., they have a route to it), they will send their own MAC address to the host. This process is called proxy ARP and it allows the host to send the data thinking it is going straight to the remote host. The router swaps the MAC address and then forwards the packet to the correct next hop.
The ip proxy-arp command is enabled on Cisco routers by default.
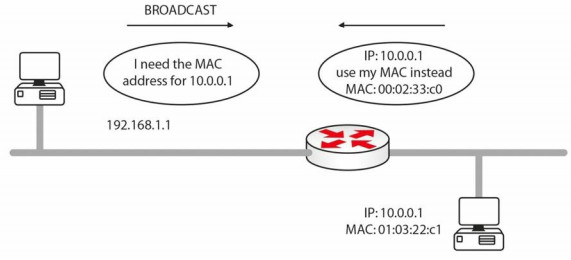
Figure 1.19 - Router Uses Proxy ARP to Allow the Hosts to Connect
Expanding upon the previous point, part of the exam requirements is understanding how addressing changes as packets traverse the network. As the packet traverses the network, there must be a way for each end device to communicate, but also a way for intermediary devices to be able to exchange the next-hop address for the packet to traverse. Proxy ARP provides the answer again. The source and destination IP address never change but in order for the packet to be passed to a next-hop address, the MAC address (in the frame) changes between devices.
In Figure 1.20 below, the frame will leave HOST A with the source IP address 192.168.1.1, the destination IP address 172.16.1.2, the source MAC address AAAA:AAAA:AAAA, and the destination MAC address AAAA: AAAA:BBBB. R1 will retain the IP addresses but change the source address to AAAA:AAAA:CCCC. By the time the packet leaves R2 for HOST B, the IP addresses will not have changed but the source MAC address is now AAAA:AAAA:DDDD and the destination MAC address is AAAA:AAAA:EEEE.
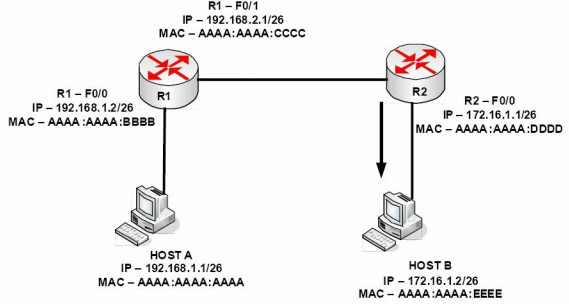
Figure 1.20 - MAC Address Changes as the Packet Traverses Network Devices
Reverse Address Resolution Protocol (RARP)
RARP maps a known MAC address to an IP address. Hosts such as diskless workstations (also known as thin clients) know their MAC address when they boot. They use RARP to discover their IP address from a server on the network
Gratuitous Address Resolution Protocol (GARP)
GARP is a special ARP packet. A normal host will always send out a GARP request after the link goes up or the interface is enabled. Gratuitous in this case means a request/reply that is not normally needed according to the ARP RFC specification but could be used in some cases. A gratuitous ARP request is an ARP request packet where the source MAC, the source IP, and the destination IP addresses are all set to the IP address of the machine issuing the packet, and the destination MAC is the Broadcast address FFFF: FFFF: FFFF. Ordinarily, no reply packet will occur.
A GARP reply is one to which no request has been made (if you see a GARP reply, that means another computer on the network has the same IP address as you have). GARP is used when a change of state happens in FHRP protocols (e.g., HSRP; this will be covered later), with the objective of updating the Layer2 CAM table. We will discuss GARP again in the IPv6 section.
Simple Network Management Protocol (SNMP)
SNMP is used for network management services. An SNMP management system allows network devices to send messages called traps to a management station. This informs the network administrator of any faults on the network (such as faulty interfaces), high CPU utilisation on servers, etc.
You can debug SNMP traffic with the debug snmp command. SNMP uses UDP ports 161 and 162.
Hyper Text Transfer Protocol Secure (HTTPS)
TLS, and the older protocol SSL, is used for secure communication over the Internet, which is carried out by means of cryptography. You will also find these used for e-mail and Voice over IP (VoIP), and when surfing sites which begin with the URL https://. HTTP with TLS/SSL (HTTPS) uses port 443.
IP Configuration Command
This is not actually a Cisco tool but it’s part of your troubleshooting toolkit. The ipconfig command used at a Windows command prompt allows you to use several switches, but perhaps the most commonly used command is ipconfig /all, as shown in the screenshot below:
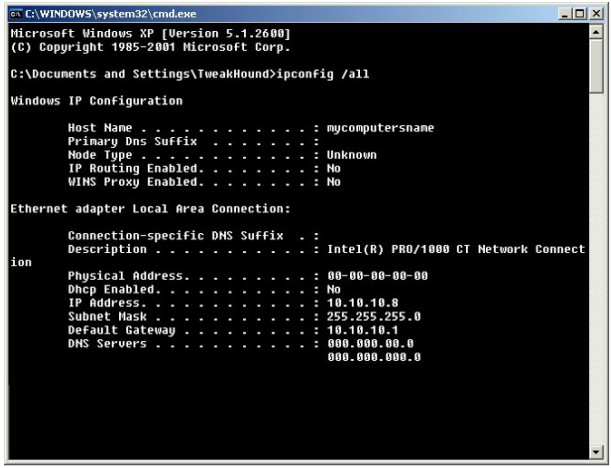
Figure 1.21 - The ipconfig /all Command Output
Other switches you can use with the ipconfig command are as follows:
/? Display this help message /all Display full configuration information /release Release the IP address for the specified adapter /renew Renew the IP address for the specified adapter /flushdns Purges the DNS Resolver cache /registerdns Refreshes all DHCP leases and re-registers DNS names
Cables and Media
Cabling and cable-related issues will become part of your day-to-day routine as a network engineer. You will need to know which cables plug into which devices, the industry limitations, and how to configure equipment for use with the correct cable type.
LAN Cables
Ethernet Cables
Most cable-related network problems will occur on the Local Area Network (LAN) side rather than on the Wide Area Network (WAN) side due to the sheer volume of cables and connectors, and the higher frequency of reseating (unplugging and plugging in) the cables for device moves and testing.
Ethernet cables are used to connect workstations to the switch, switch-to-switch, and switch-to-router. The specifications and speeds have been revised and improved many times in recent years, which means you can soon expect today’s standard speeds to be left behind for new and improved high-speed links right to your desktop. The current standard Ethernet cable still uses eight wires twisted into pairs to prevent electromagnetic interference (EMI), as well as crosstalk, which is a signal from one wire spilling over into a neighbouring cable.
Cable categories, as defined by ANSI/TIA/EIA-568-A, include Categories 3, 5, 5e, and 6. Each one gives standards, specifications, and achievable data throughput rates, which can be achieved if you comply with distance limitations. Category 3 cabling can carry data up to 10Mbps. Category 5 cabling is primarily used for faster Ethernet networks, such as 100BASE-TX and 1000BASE-T.
Category 5e cabling uses 100-MHz-enhanced pairs of wires for running GigabitEthernet (1000Base-T). Finally, with Category 6 cabling, each pair runs 250 MHz for improved 1000Base-T performance. (“1000” refers to the speed of data in Mbps, “Base” stands for baseband, and “T” stands for twisted pair.) Table 1.6 below demonstrates some common Ethernet standards you should be familiar with:
Table 1.6. Common Ethernet Standards
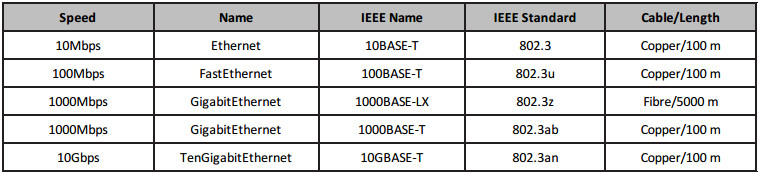
Cisco like to sneak cable specification questions into the exam from time to time, so make sure you memorise the table above.
Duplex
When Ethernet networking was first used, data was able to pass on the wire in only one direction at a time. This is because of the limitations of the cables used at that time. The sending device had to wait until the wire was clear before sending data on it, without a guarantee that there wouldn’t be a collision. This is no longer an issue because a different set of wires is used for sending and receiving signals.
Half duplex means that data can pass in only one direction at a time, while full duplex means that data can pass in both directions on the wire at the same time (see Figure 1.22). This is achieved by using spare wires inside the Ethernet cable. All devices now run at full duplex unless configured otherwise.
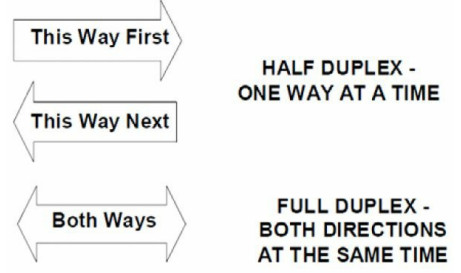
Figure 1.22 - Duplex Topology
You will still be expected to understand and troubleshoot duplex issues in the exam; we will cover troubleshooting Layer 1 and Layer 2 issues later in this guide. You can easily check an interface’s duplex settings with the show interface X command.
Switch#show interface FastEthernet0/1 FastEthernet0/1 is down, line protocol is down (disabled) Hardware is Lance, address is 0030.a388.8401 (bia 0030.a388.8401) BW 100000 Kbit, DLY 1000 usec, reliability 255/255, txload 1/255, rxload 1/255 Encapsulation ARPA, Loopback not set Keepalive set (10 sec) Half-duplex, 100Mb/s
If this interface was connected to a full-duplex device, you would see interface errors immediately and experience slow traffic on the link. You can also issue the show interfaces status command on a live switch, although this command may not work in the exam because a router simulator has limited commands (same for Packet Tracer). You can see possible issues with interface Fast Ethernet 1/0/2 below:
| Switch#show interfaces status | |||||
| Port Name | Status | Vlan | Duplex | Speed | Type |
| Fa1/0/1 | notconnect | 1 | auto | auto | 10/100BaseTX |
| Fa1/0/2 | notconnect | 1 | half | 10 | 10/100BaseTX |
| Fa1/0/3 | notconnect | 1 | auto | auto | 10/100BaseTX |
| Fa1/0/4 | notconnect | 1 | auto | auto | 10/100BaseTX |
| Fa1/0/5 | notconnect | 1 | auto | auto | 10/100BaseTX |
And of course you can fix this issue easily, as shown below:
Switch(config)#int f1/0/2 Switch(config-if)#duplex ? auto Enable AUTO duplex configuration full Force full duplex operation half Force half-duplex operation Switch(config-if)#duplex full
Please do try this and all the other commands on live Cisco equipment, GNS3, or at least Packet Tracer in order to remember them! We will cover the speed setting next.
Speed
You can leave the speed of the Ethernet port on your routers or switches as auto-negotiate, or you can hard set them to 10Mbps, 100Mbps, or 1000Mbps.
To set the speed manually, you would configure the router as follows:
Router#config t Router(config)#interface GigabitEthernet 0/0 Router(config-if)#speed ? 10 Force 10 Mbps operation 100 Force 100 Mbps operation 1000 Force 1000 Mbps operation auto Enable AUTO speed configuration
The following commands would allow you to view the router Ethernet interface settings:
Router#show interface FastEthernet0 FastEthernet0 is up, line protocol is up Hardware is DEC21140AD, address is 00e0.1e3e.c179 (bia 00e0.1e3e.c179) Internet address is 1.17.30.4/16 MTU 1500 bytes, BW 10000 Kbit, DLY 1000 usec, rely 255/255, load 1/255 Encapsulation ARPA, Loopback not set, keepalive set (10 sec) Half-duplex, 10Mb/s, 100BaseTX/FX
Specifications for Ethernet cables by EIA/TIA dictate that the end of the cable presentation should be RJ45 male (see Figure 1.23; Figure 1.24 shows the female end), which will allow you to insert the cable into the Ethernet port on your router/switch/PC.

Figure 1.23 - RJ45 Male End

Figure 1.24 - RJ45 Female End
Straight Cables
Each Ethernet cable contains eight wires and each wire connects to a pin at the end. The position of these wires when they meet the pin determines what the cable can be used for. If each pin on one end matches the other side, then this is known as a straight-through cable. These cables can be used to connect an end device to an Ethernet port on a switch, and a switch to a router. You can easily check whether the wires match by comparing one side of the cable to the other, as shown in Figures 1.25 and 1.26 below:

Figure 1.25 - Comparing Cable Ends
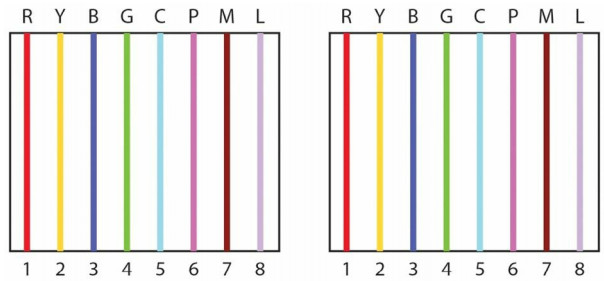
Figure 1.26 - Cable Ends Match
Crossover Cables
By swapping two of the wires on the cable, it can now be used to connect a PC to a PC (without the use of a switch or a hub, although Auto-MDIX ports on newer network interfaces detect whether the connection requires a crossover, and automatically chooses the MDI or MDIX configuration to properly match the other end of the link) or a switch to a switch. The wire on pin 1 on one end needs to connect to pin 3 on the other end, and pin 2 needs to connect to pin 6 on the other end (see Figure 1.27). I have created my own colour scheme for the cables purely to illustrate my point – red, yellow, blue, green, cyan, pink, magenta, and lilac.
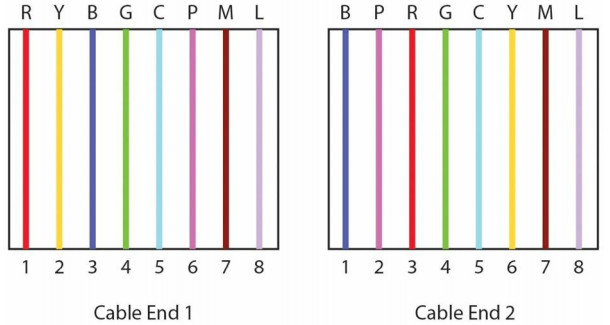
Figure 1.27 - Pin 1 to Pin 3 and Pin 2 to Pin 6
Rollover/Console Cables
All Cisco routers and switches have physical ports to connect to for initial set up and disaster recovery or access. These ports are referred to as console ports and you will regularly use these as a Cisco engineer. In order to connect to this port, you need a special type of cable called a rollover or console cable (see Figure 1.28). It can sometimes be referred to as a flat cable because, as opposed to most round-bodied Ethernet cables, it is often flat along its body.
A rollover cable swaps all pins (see Figure 1.29), so pin 1 on one end goes to pin 8 on the other end, pin 2 goes to pin 7, and so on.

Figure 1.28 - A Typical Rollover Cable
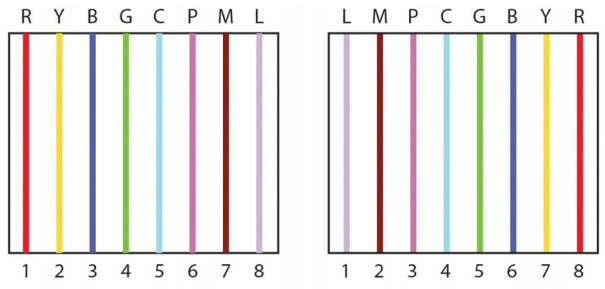
Figure 1.29 - All Pins Swapped
Rollover cables usually have an RJ45 connection on one end and a 9-pin D-shaped connection on the other end, which is designed to connect to the COM port on a PC or laptop. The trouble is that devices no longer come with these ports, as they were so rarely used. You can now buy a DB9-to-USB converter cable (see Figure 1.30) from many electrical stores or online. They come with software drivers which allow you to connect a logical COM port on your PC via a terminal programme, such as PuTTY or HyperTerminal.
Cisco have started to put mini-USB ports (in addition to RJ45 ports) on their devices to allow for console port connectivity using the USB Type A to 5-pin mini-Type B cable. If both console cables are plugged in at the same time, the mini-USB cable takes precedence and becomes active. Figures 1.31 and 1.32 below show the different connection types.

Figure 1.30 - A COM-to-USB Converter Cable

Figure 1.31 - Connecting the Cable to the COM Port
Figure 1.32 - Connecting the Cable to the Router or Switch Console Port
WAN Cables
Used for Wide Area Network connections, serial cables can come in several shapes, sizes, and specifications, depending upon the interface on the router and connection type. ISDN uses different cables than Frame Relay or ADSL do, for example.
One common type of WAN cable you will use, especially if you have a home network to practise on, is a DB60 (see Figure 1.33). For this type of cable, you will have a data terminal equipment (DTE) end, which plugs in to the customer equipment, and a data communication equipment (DCE) end, which determines the speed of the connection from the ISP. Figure 1.34 below shows a DB60 serial interface on a WIC-1T card.

Figure 1.33 - A DB60 Cable

Figure 1.34 - The DB60 Serial Interface on a WIC-1T Card
There is another common presentation type for Cisco WAN Interface Cards (WICs) known as a smart serial cable:

Figure 1.35 - Smart Serial Cable
Of course, you will need the correct interface card in the router if you use this cable type, as shown below in Figure 1.36:

Figure 1.36 WIC-2T Smart Serial Card
The smart serial WIC card gives you two connections for one slot on the router, as opposed to only one connection you would get with a standard WIC-1T card. Each serial connection can use a different encapsulation type, such as PPP for one and Frame Relay for the other.
The most important thing to remember about DCE and DTE cables is that you need to apply a clock rate to the DCE end in order for the line to come up. Normally, your ISP would do this because they own the DCE end, but on a home lab or live rack, you own the DCE end, which makes you the customer on one router and the ISP on the other router. The command you would enter is clock rate 64000 (or whatever speed you like from the available options in bits per second). You can type clock rate ? to see your options.
Please ensure that you understand the following commands before typing them out on a router. Firstly, to establish which router has the DCE cable attached, you need to type the show controllers command, followed by the interface number. This is a very useful command to know for troubleshooting problems in the actual exam (and in the real world). You can see which interfaces you have on your router with the show ip interface brief command.
You can actually shorten most Cisco IOS commands, which is demonstrated in the output below. The shortened versions may not work in the exam, though, because the exam uses a router simulator (i.e., not a live router).
| Router#sh ip int brie | OK? Method Status | |||
| Interface | IP-Address | |||
| Protocol | unassigned | YES unset | administratively down | |
| FastEthernet0/0 | ||||
| down | unassigned | YES unset | administratively down | |
| FastEthernet0/1 | ||||
| down | unassigned | YES unset administratively | ||
| Serial0/1/0 | ||||
| down down | unassigned | YES | ||
| Vlan1 | ||||
unset administratively down down Router#show controllers s0/1/0 Interface Serial0/1/0 Hardware is PowerQUICC MPC860 DCE V.35, no clock Router(config-if)#clock rate ? Speed (bits per second) 1200 2400 4800 9600 19200 38400 56000 64000 ... [Truncated Output]
Connecting to a Router
The first time you connect to a router or a switch, it can seem a little daunting. We have covered console connections above, so once you connect the cable, you will need to use a terminal emulation programme on your PC or laptop. This will allow you to see router output and type in the configuration commands.
HyperTerminal has been the default for many years, and you may need to use this still if you need to perform disaster recovery; however, for now you can stick to PuTTY, which is very widely used. You can download PuTTY from www.putty.org. An old-fashioned connection using the COM port on a PC almost always uses a logical port on it labelled COM1 or COM2. You can see the facility of using this on PuTTY, which actually calls this a serial connection, as shown in Figure 1.37 below:
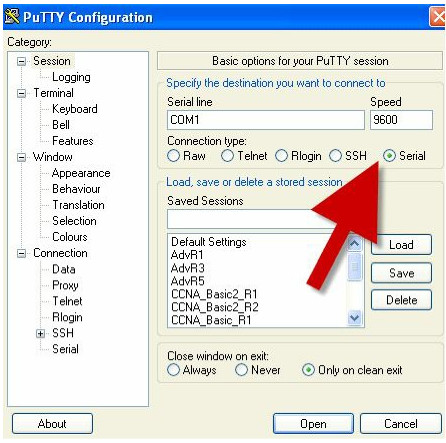
Figure 1.37 – PuTTY Uses COM Ports for Serial Access
If you are using a USB-to-rollover cable, then you will have received a driver CD, which, when run, will give you a COM port number to use. You can find this port number in the Device Manager if you are using Windows, as shown in Figure 1.38 below:
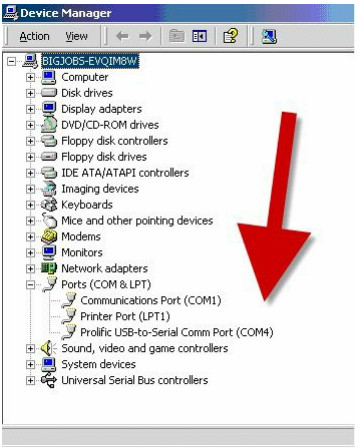
Figure 1.38 – The Driver Has Assigned COM4 for Console Connection
If you are using HyperTerminal, you will also need to select more connection parameters, such as baud rate. You should choose the following, which is illustrated in Figure 1.39:
- Bits per second: 9600
- Data bits: 8 is the default
- Parity: None is the default
- Stop bits: 1 is the default
- Flow control: must be None
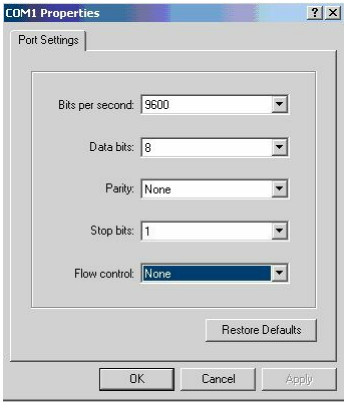
Figure 1.39 – Setting Your HyperTerminal Settings
When you turn on the router, if you have selected the correct COM port AND plugged the rollover cable into the console port (instead of a different port by accident), you should see the router boot-up text (see Figure 1.40). If you can’t see any text, hit the Enter key a few times and then double-check your settings.
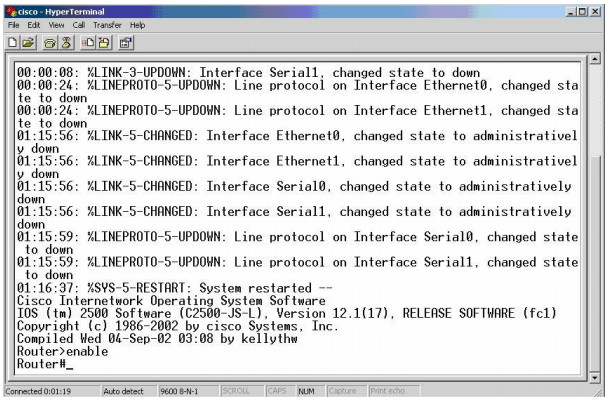
Figure 1.40 – The Router Boot-up Text
The router may ask whether you want to enter Initial Configuration mode. This happens when it can’t find a startup configuration file in NVRAM (covered later) or if the configuration register is set to ignore the startup configuration file (usually 0x2142). Always type “n” or “no” because, otherwise, you will enter setup mode, which you don’t want to do:
Would you like to enter the initial configuration dialog? [yes/no]: % Please answer ‘yes’ or ‘no’. Would you like to enter the initial configuration dialog? [yes/no]: no Press RETURN to get started! Router>
With a different router model, you would see the following output:
Technical Support: www.cisco.com/techsupport Copyright (c) 1986-2007 by Cisco Systems, Inc. Compiled Wed 18-Jul-07 04:52 by pt_team --- System Configuration Dialog ---Continue with configuration dialog? [yes/no]: no Press RETURN to get started! Router>
Router Modes
In order to pass the CCNA exam, you will need to understand which router prompt you should start from to perform various actions. Whatever function you wish to perform, you will have to be in the correct mode (signified by the router prompt). This is the biggest mistake novice students make when they are having problems configuring the router and cannot find the right command to use. Make sure you are in the correct mode!
User Mode
The first mode you will be presented with when the router boots is known as User mode or User Exec mode. User mode has a very limited set of commands that can be used, but it can be useful for looking at basic router elements. The default name of the router is “Router” but this can be changed, as you will see later.
Router>
Privileged Mode
Typing enable at the User prompt takes you into the next mode, known as Privileged mode or Privileged Exec mode. To get back to User mode, you simply type disable. To quit the session altogether, type logout or exit.
Router>enable Router# Router#disable Router>
Privileged mode is very useful for looking at the entire configuration of the router, the statistics about how it is performing, and even which modules you have connected to the router. At this prompt, you would type show commands and troubleshoot with debug commands.
Global Configuration Mode
In order to configure the router, you have to be in Global Configuration mode. To get to Global Configuration mode, you simply type configure terminal, or config t for short, at the Privileged Exec prompt. Alternatively, just type config and the router will ask you which mode you would like to enter. The default is terminal (the default options will be shown inside the square brackets [ ]). If you press Enter, the command inside the brackets will be accepted.
Router#config Configuring from terminal, memory, or network[terminal]? ← press Enter Enter configuration commands, one per line. End with CNTL/Z. Router(config)#
Interface Configuration Mode
Interface Configuration mode allows you to enter commands for individual router interfaces, such as FastEthernet, Serial, etc. On a new router, all of the interfaces will be shut down by default, with no configuration present.
Router>enable Router#config t Enter configuration commands, one per line. End with CNTL/Z. Router(config)#interface Serial0 Router(config-if)#

Line Configuration Mode
Line Configuration mode is used to make any changes to the console, Telnet, or auxiliary ports (if your router has these). You can control who can access the router via these ports, as well as put passwords or a security feature called “access control lists” on them.
Router#config t Enter configuration commands, one per line. End with CNTL/Z. Router(config)#line console 0 Router(config-line)#
You can also configure baud rates, exec levels, and more in Line Configuration mode.
Router Configuration Mode
In order to configure a routing protocol onto the router so it can dynamically build a picture of the network, you will need to be in Router Configuration mode.
Router#config t Enter configuration commands, one per line. End with CNTL/Z. Router(config)#router rip Router(config-router)#
VLAN Configuration Mode
This mode actually only applies to switches but it’s worth mentioning it here while we are discussing modes. You will spend a lot of time in this mode when configuring the switching labs in this book.
Switch#conf t Enter configuration commands, one per line. End with CNTL/Z. Switch(config)#vlan 10 Switch(config-vlan)#
Routers equipped with Ethernet switch cards use VLAN Database Configuration mode (this mode is deprecated on switches), which is similar to VLAN Configuration mode:
Router#vlan database Router(vlan)#vlan 10 VLAN 10 added: Name: VLAN0010 Router(vlan)#exit APPLY completed. Exiting.... Router#
Configuring a Router
There are no menus available on a router, and you cannot use a mouse to navigate between the different modes, as it is all done via the command line interface (CLI). There is, however, some context-sensitive help in the form of the [?] keyword. If you type a question mark at the router prompt, you will be presented with a list of all the available commands.
Please note that you will only see the commands available for your mode. If you want to see interface configuration commands, you must be at the interface prompt.
Router#? Exec commands: access-enable Create a temporary Access-List entry access-profile Apply user-profile to interface access-template Create a temporary Access-List entry alps ALPS exec commands archive manage archive files bfe For manual emergency modes setting cd Change current directory clear Reset functions clock Manage the system clock cns CNS subsystem configure Enter configuration mode connect Open a terminal connection copy Copy from one file to another debug Debugging functions (see also ‘undebug’) delete Delete a file dir List files on a directory disable Turn off privileged commands disconnect Disconnect an existing network connection enable Turn on privileged commands erase Erase a file exit Exit from the EXEC mode help Description of the interactive help system -- More –
If there is too much information to display on the screen, you will see the -- More -- tab. If you want to see the next page, press the space bar. If not, hold down the Ctrl+Z keys together or press “Q” to get back to the router prompt.
In addition, if you have started to type a command but forget what else you need to type in, using the question mark will give you a list of options available. The [?] keyword WILL work in the CCNA exam, but if you are using it, you didn’t follow all my labs!
Router#cl? clear clock
If you begin to type out a command, as long as there is only one possible word or command available with that syntax, you can press the Tab key to have it completed for you.
Router#copy ru ← press the Tab key here Router#copy running-config
The router has several modes from which to choose. This is to ensure that you do not make changes to parts of the router configuration you do not intend to change. You can recognise which mode you are in by looking at the command prompt. For example, if you wanted to make some changes to one of the FastEthernet interfaces, you would need to be in Interface Configuration mode.
First, go into Global Configuration mode:
Router#config t Router(config)#
Next, tell the router which interface you want to configure:
Router(config)#interface FastEthernet0 Router(config-if)#exit Router(config)#
If you are not sure which way to enter the interface number, then use the [?] keyword. Do not worry about all of the choices you will be given. Most people only use the FastEthernet, Serial, and Loopback interfaces.
Router(config)#interface ? Async Async interface BRI ISDN Basic Rate Interface BVI Bridge-Group Virtual Interface CTunnel CTunnel interface Dialer Dialer interface FastEthernet IEEE 802.3u Group-Async Async Group interface Lex Lex interface Loopback Loopback interface Multilink Multilink-group interface Null Null interface Serial Serial interface Tunnel Tunnel interface Vif PGM Multicast Host interface Virtual-Template Virtual Template interface Virtual-TokenRing Virtual TokenRing interface range interface range command Router(config)#interface FastEthernet? <0-0> FastEthernet interface number Router(config)#interface FastEthernet0
Finally, the router drops into Interface Configuration mode:
Router(config-if)#
From here, you can put an IP address on the interface, set the bandwidth, apply an access control list, and do a lot of other things. Please note that your router and switch may well have different interface numbers from mine, so use the ? or show ip interface brief commands to see your options.
If you ever need to exit out of a configuration mode, simply type exit. This takes you back to the next-highest level. To quit any sort of configuration mode, simply press Ctrl+Z together (or type end).
Router(config-if)#exit Router(config)#
Or, if using the Ctrl+Z option:
Router(config-if)#^z Router#
Loopback Interfaces
Loopback interfaces are not normally covered in the CCNA syllabus, but they are very useful in the real world and for practice labs. A Loopback interface is a virtual or logical interface that you configure, but it does not physically exist (so you will never see it on the router panel). The router will let you ping this interface, though, which will save you from having to connect devices to the FastEthernet interfaces in the labs.
An advantage of using Loopback interfaces is that they always remain up, if the router is working, because they are logical, meaning they can never go down. However, you cannot put a network cable into the Loopback interface because it is a virtual interface.
Router#config t Router#(config)#interface Loopback0 Router#(config-if)#ip address 192.168.20.1 255.255.255.0 Router#(config-if)#^z ← press Ctrl+Z Router# Router#show ip interface brief Interface IP-Address OK? Method Status Protocol Loopback0 192.168.20.1 YES manual up up
Your output for this command will show all of the available interfaces on your router.

Loopback interfaces have to be given a valid IP address. You can then use them for routing protocols or for testing your router to see whether it is permitting certain traffic. You will be using these interfaces a lot throughout the course.
Editing Commands
It is possible to navigate your way around a line of configuration you have typed rather than deleting the whole line. The following keystrokes will move the cursor to various places in the line:
Keystroke Meaning
Ctrl+A Moves to the beginning of the command l ine
Ctrl+E Moves to the end of the command l ine
Ctrl+B Moves back one character
Ctrl+F Moves forward one character
Esc+B Moves back one word
Esc+F Moves forward one word
Ctrl+P or up arrow Recal l s the previous command
Ctrl+N or down arrow Recal l s the next command
Ctrl+U Deletes a l ine
Ctrl+W Deletes a word
Tab Fini shes typing a command for you
Show hi story Shows the last 10 commands entered by defaul t
Backspace Deletes a single character
It is fairly common to have a question on the above in the exam.
Configuring a Router Interface
Router interfaces can be of different types, based on the following two factors:
- Underlying technology used (e.g., Ethernet)
- Interface bandwidth
The most common router and switch interfaces used in modern enterprise networks are:
- 100Mbps (commonly named FastEthernet)
- 1Gbps (commonly named GigabitEthernet)
- 10Gbps (commonly named TenGigabitEthernet)
In order to address a specific router interface and to enter Interface Configuration mode to configure specific parameters, you must know the interface notation. This can vary based on the router manufacturer, but the interface notation is usually made up of two parts:
- Interface type (Ethernet, FastEthernet, etc.)
- Interface slot/module and port number
For example, common interface notations include the following:
- Ethernet1/0 (slot 1, port 0)
- FastEthernet0/3 (slot 0, port 3)
- GigabitEthernet0/1/1 (module 0, slot 1, port 1)

In order for a router interface to have basic functionality, you must configure the following parameters:
- Speed
- Duplex
- IP address
You can exemplify these basic configuration settings on a Cisco router, as they are commonly used in modern enterprise networks. To see the available interfaces and their current state, you can issue the following command:
Router#show ip interface brief Interface IP-Address OK? Method Status Protocol FastEthernet0/0 unassigned YES unset administratively down down FastEthernet0/1 unassigned YES unset administratively down down
From the output above, you can see that the router has two FastEthernet (100 Mbps) interfaces on slot 0, both unconfigured (i.e., no IP address) and administratively disabled (i.e., status: administratively down).
Before starting to configure interface parameters, you must enter Router Configuration mode using the configure terminal command on Cisco devices, and then Interface Configuration mode using the interface <interface name> command. The first step in the interface configuration process is enabling the interface. For example, the interface FastEthernet0/0 can be enabled using the no shutdown command:
Router#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Router(config)#interface FastEthernet0/0 Router(config-if)#no shutdown Router(config-if)#no shutdown Router(config-if)# *Mar 1 00:32:05.199: %LINK-3-UPDOWN: Interface FastEthernet0/0, changed state to up *Mar 1 00:32:06.199: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/0, changed state to up
The next configuration step involves setting up speed and duplex settings and we have already covered these.
Configuring an IP Address on an Interface

Don’t worry about where to find the IP address at the moment, as we will look at that later on.
Router>enable ← takes you from User mode to Privileged mode Router#config t ← from Privileged mode to Configuration mode Router(config)#interface Serial0 ← and then into Interface Configuration mode Router(config-if)#ip address 192.168.1.1 255.255.255.0 Router(config-if)#no shutdown ← the interface is opened for traffic Router(config-if)#exit ← you could also hold down the Ctrl+Z keys together to exit Router(config)#exit Router#
A description can also be added to the interface, as shown in the following output:
RouterA(config)#interface Serial0 RouterA(config-if)#description To_Headquarters RouterA(config-if)#^Z ← press Ctrl+Z to exit
After the router interface configuration is complete, you can verify the setting by inspecting the full interface-configured parameters using the commands below on Cisco routers:
RouterA#show interface Serial0 Serial0 is up, line protocol is up Hardware is HD64570 Description: To_Headquarters Internet address is 12.0.0.2/24 MTU 1500 bytes, BW 1544 Kbit, DLY 20000 usec, reliability 255/255, txload 1/255, rxload 1/255 Encapsulation HDLC, loopback not set Keepalive set (10 sec) Last input 00:00:02, output 00:00:03, output hang never [Output restricted...]
Show Commands
You can look at most of the settings on the router simply by using the show x command from
Privileged mode, with x being the next command, as illustrated in the following output:
Router#show ? access-expression List access expression access-lists List access lists accounting Accounting data for active sessions adjacency Adjacent nodes aliases Display alias commands alps Alps information apollo Apollo network information appletalk AppleTalk information arap Show AppleTalk Remote Access statistics arp ARP table async Information on terminal lines used as router interfaces backup Backup status bridge Bridge Forwarding/Filtering Database [verbose] bsc BSC interface information bstun BSTUN interface information buffers Buffer pool statistics cca CCA information cdapi CDAPI information cdp CDP information cef Cisco Express Forwarding class-map Show QoS Class Map clns CLNS network information --More--
Some of the more common show commands and their meanings, along with an example, are listed below:
Show Command Result show running-configuration Shows confi guration in DRAM show startup-configuration Shows confi guration in NVRAM show flash: Shows whi ch IOS i s in flash show ip interface brief Shows brief summary of al l interfaces show interface Serial0 Shows Serial interface stati sti cs show history Shows last 10 commands entered
Router#show ip interface brief Interface Address OK? Method Status Protocol Ethernet0 10.0.0.1 YES manual up up Ethernet1 unassigned YES unset administratively down down Loopback0 172.16.1.1 YES manual up up Serial0 192.168.1.1 YES manual down down Serial1 unassigned YES unset administratively down down
The method tag indicates how the address has been assigned. It can state unset, manual, NVRAM, IPCP, or DHCP.
Routers can recall commands previously entered at the router prompt – the default is 10 commands – which can be recalled by using the up arrow. Using this feature can save a lot of time and effort, as it prevents you from having to re-enter a long line. The show history command shows the buffer of the last 10 commands.
Router#show history show ip interface brief show history show version show flash: conf t show access-lists show process cpu show buffers show logging show memory
You can increase the history buffer with the terminal history size command:
Router#terminal history ? size Set history buffer size <cr> Router#terminal history size ? <0-256> Size of history buffer Router#terminal history size 20
Verifuing Basic Router Configuration and Network Connectivity
The most useful commands that help verify basic router configuration are explained in the following sections.
Show Version
The show version command provides useful information that might represent a starting point in verifying most of the router operations. This information includes the following:
Type of router (another useful command for listing the router hardware is show inventory)
- IOS version
- Memory capacity
- Memory usage
- CPU type
- Flash capacity
- Other hardware parameters
- Reason for last reload
Here is a shortened output of the show version command. Please try it out for yourself.
Router#show version Cisco 1841 (revision 5.0) with 114688K/16384K bytes of memory. Processor board ID FTX0947Z18E M860 processor: part number 0, mask 49 2 FastEthernet/IEEE 802.3 interface(s) 2 Low-speed Serial(sync/async) network interface(s) 191K bytes of NVRAM. 63488K bytes of ATA CompactFlash (Read/Write) Configuration register is 0x2102
Show Running-config
The show running-config command provides full configuration on the router, and it can be used to verify that the device is configured with the proper features. The output for this command is too extensive so it will not be presented here.
Show IP Interface Brief
The show ip interface brief command, as mentioned in a previous section, lists the router interfaces and their state, including:
- Interface name and number
- IP address
- Link status
- Protocol status
Router#show ip interface brief Interface IP-Address OK? Method Status Protocol FastEthernet0/0 unassigned YES unset administratively down down FastEthernet0/1 unassigned YES unset administratively down down Serial0/0/0 unassigned YES unset administratively down down Serial0/1/0 unassigned YES unset administratively down down Vlan1 unassigned YES unset administratively down down Router#
Show IP Route
The show ip route command provides deep information regarding the routing capabilities of the device. It lists all the networks the router can reach and information about the way they can be reached, including:
- Network
- Routing protocol
- Next hop
- Outgoing interface
R1#show ip route Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area, N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2, E1 - OSPF external type 1, E2 - OSPF external type 2, i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area, * - candidate default, U - per-user static route, o – ODR, P - periodic downloaded static route Gateway of last resort is not set R 80.1.1.0/24 [120/1] via 10.1.1.2, 00:00:04, Ethernet0/0.1 D 80.0.0.0/8 [90/281600] via 10.1.1.2, 00:02:02, Ethernet0/0.1 O E2 80.1.0.0/16 [110/20] via 10.1.1.2, 00:00:14, Ethernet0/0.1
In addition to the show commands presented above, other useful methods of verifying router connectivity include using the ping and traceroute commands.
Ping
The ping command provides a basic connectivity test to a specific destination. This way you can test whether the router can reach a network or not. Ping works (using ICMP) by sending echo requests to a machine to verify whether it is up and running. If a specific machine is operating, it will send an ICMP echo reply message back to the source, confirming its availability. A sample ping is presented below:
Router#ping 10.10.10.2 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.10.10.2, timeout is 2 seconds: .!!!! Success rate is 80 percent (4/5), round-trip min/avg/max = 20/40/76 ms
A standard ping command sends five ICMP packets to the destination. When looking at the ping output, a dot (.) represents a failure and an exclamation mark (!) represents a successfully received packet. The ping command output also shows the round-trip time to the destination network (minimum, average, and maximum).
If you need to manipulate ping-related parameters, you can issue an extended ping from a Cisco router. This is done by typing ping and pressing Enter in the console. The router will prompt you with an interactive menu where you can specify the desired parameters, including:
- Number of ICMP packets
- Packet size
- Timeout
- Source interface
- Type of service
Router#ping Protocol [ip]: Target IP address: 10.10.10.2 Repeat count [5]: Datagram size [100]: Timeout in seconds [2]: Extended commands [n]: y Source address or interface: FastEthernet0/0 Type of service [0]: Set DF bit in IP header? [no]: Validate reply data? [no]: Data pattern [0xABCD]: Loose, Strict, Record, Timestamp, Verbose[none]: Sweep range of sizes [n]: Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.10.10.2, timeout is 2 seconds: Packet sent with a source address of 10.10.10.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 20/36/72 ms
Traceroute
The traceroute command is another useful tool that allows you to see the hops a packet passes until it reaches its destination. The output below shows that the packet has to cross a single hop until it reaches its destination:
R2#traceroute 192.168.1.1 Type escape sequence to abort. Tracing the route to 192.168.1.1 1 10.10.10.1 60 msec * 64 msec
Just like with ping, Cisco routers allow you to perform an extended traceroute command that can define a number of associated parameters, most of them similar to the ping-related parameters:
Router#traceroute Protocol [ip]: Target IP address: 192.168.1.1 Source address: 10.10.10.2 Numeric display [n]: Timeout in seconds [3]: Probe count [3]: Minimum Time to Live [1]: Maximum Time to Live [30]: Port Number [33434]: Loose, Strict, Record, Timestamp, Verbose[none]: Type escape sequence to abort. Tracing the route to 192.168.1.1 1 10.10.10.1 76 msec * 56 msec
Section 1 Questions
OSI/TCP Model Questions
- Name each layer of the OSI model, from Layer 7 down to Layer 1.
- The role of the Session Layer is to _______, _______, and _______ sessions or dialogues between devices.
- What are the three methods used to control data flow at Layer 4?
- The Transport Layer includes several protocols, and the most widely known are _______ and _______.
- Why is UDP used at all if TCP/IP offers guaranteed delivery?
- What is data referred to at each OSI layer?
- In order to interface with the upper and lower levels, the Data Link Layer is further subdivided into which two Sublayers?
- What are the five TCP/IP layers from the top down?
- How does the TCP/IP model map to the OSI model?
- Layer 2 addresses are also referred to as _______ addresses.
- Using a switch will allow you to divide your network into smaller, more manageable sections known as ______________.
Cable Questions
- The current standard Ethernet cable still uses eight wires twisted into pairs to prevent_______ _______ and _______.
- _______ is when a signal from one Ethernet wire spills over into a neighbouring cable.
- Which command would set the FastEthernet router interface speed to 10Mbps?
- On a crossover cable, the wire on pin 1 on one end needs to connect to pin _______ on the other end and pin 2 needs to connect to pin _______.
- Which cable would you use to connect a router Ethernet interface to a PC?
- You can see a summary of which interfaces you have on your router with the show_______ _______ _______ command.
- Line Configuration mode lets you configure which ports?
- A Loopback interface is a _______ or _______ interface that you configure.
- The keyboard shortcut Ctrl+A does what?
- The _______ keyboard shortcut moves the cursor back one word.
- By default, the _______ _______ command shows the last 10 commands entered.
Section 1 Answers
OSI/TCP Model Answers
- Application, Presentation, Session, Transport, Network, Data Link, and Physical.
- Set up, manage, and terminate.
- Flow control, windowing, and acknowledgements.
- TCP and UDP.
- TCP uses a lot of bandwidth on the network and there is a lot of traffic sent back and forth to set up the connection, even before the data is sent. This all takes up valuable time and network resources. UDP packets are a lot smaller than TCP packets and they are very useful if a really reliable connection is not that necessary. Protocols that use UDP include DNS and TFTP.
- Bits (Layer 1), Frames (Layer 2), Packets (Layer 3), Segments (Layer 4) and Data (Layers 5-7).
- LLC and MAC.
- Application, Transport, Network, Data Link, and Network.
-
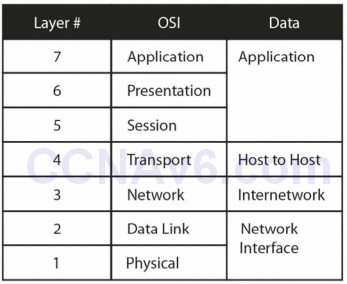
- MAC.
- Collision domains.
Cable Answers
- Electromagnetic interference (EMI) and crosstalk.
- Crosstalk.
- The speed 10 command.
- 3 and 6.
- A crossover cable.
- ip interface brief.
- The console, Telnet, and auxiliary ports.
- Virtual or logical.
- Moves the cursor to the beginning of the command line.
- Esc+B.
- show history.
Section 1 Lab
IOS Command Navigation Lab
Topology
Purpose
Learn how to connect to a router via the console port and try out some commands.
Walkthrough
- Use a console cable, along with PuTTY (free online; search for “PuTTY”), to connect to a router console port.
- From the Router> prompt, enter the commands below, exploring various router modes and commands. If you are asked to enter Setup mode, type “no” and hit Enter. Please bear in mind that you will have a different router model from mine, so some output will differ.
Cisco IOS Software, 1841 Software (C1841-ADVIPSERVICESK9-M), Version 12.4(15)T1, RELEASE SOFTWARE (fc2) Technical Support: www.cisco.com/techsupport Copyright (c) 1986-2007 by Cisco Systems, Inc. Compiled Wed 18-Jul-07 04:52 by pt_team --- System Configuration Dialog ---Continue with configuration dialog? [yes/no]:no Press RETURN to get started! Router>enable Router#show version Cisco 1841 (revision 5.0) with 114688K/16384K bytes of memory. Processor board ID FTX0947Z18E M860 processor: part number 0, mask 49 2 FastEthernet/IEEE 802.3 interface(s) 2 Low-speed Serial(sync/async) network interface(s) 191K bytes of NVRAM. 63488K bytes of ATA CompactFlash (Read/Write) Configuration register is 0x2102 Router#show ip interface brief Interface IP-Address OK? Method Status Protocol FastEthernet0/0 unassigned YES unset administratively down down FastEthernet0/1 unassigned YES unset administratively down down Serial0/0/0 unassigned YES unset administratively down down Serial0/1/0 unassigned YES unset administratively down down Vlan1 unassigned YES unset administratively down down Router# Router#conf t Enter configuration commands, one per line. End with CNTL/Z. Router(config)#interface Serial0/1/0 ← put your serial # here Router(config-if)#ip address 192.168.1.1 255.255.255.0 Router(config-if)#interface Loopback0 Router(config-if)#ip address 10.1.1.1 255.0.0.0 Router(config-if)#^Z ← press Ctrl+Z keys together Router# Router#show ip interface brief Interface IP-Address OK? Method Status Protocol FastEthernet0/0 unassigned YES unset administratively down down FastEthernet0/1 unassigned YES unset administratively down down Serial0/0/0 unassigned YES unset administratively down down Serial0/1/0 192.168.1.1 YES manual administratively down down Loopback0 10.1.1.1 YES manual up up Vlan1 unassigned YES unset administratively down down Router#show history Router(config)#hostname My_Router My_Router(config)#line vty 0 ? <1-15> Last Line number <cr> My_Router(config)#line vty 0 15 ← enter 0 ? to find out how many l ines you have My_Router(config-line)# My_Router(config-line)#exit My_Router(config)#router rip My_Router(config-router)#network 10.0.0.0 My_Router(config-router)#

can you provide notes in hindi.