Section 6 Tasks
• Read today’s lesson notes (below)
• Review yesterday’s lesson notes
• Complete today’s labs
• Read the ICND1 cram guide
• Spend 15 minutes on the subnetting.org website
Network Address Translation (NAT) is another strange subject, because Cisco has broken down NAT requirements between the ICND1 and the ICND2 syllabuses.
Today you will learn about the following:
• NAT basics
• Configuring and verifying NAT
• NAT troubleshooting
This module maps to the following ICND1 syllabus requirements:
• Identify the basic operation of NAT
° Purpose
° Pool
° Static
° One-to-one
° Overloading
° Source addressing
° One-way NAT
• Configure and verify NAT for given network requirements
NAT Basics
Imagine for a moment that networks run on colours instead of using IP addresses. There is an unlimited supply of the colours blue and yellow but the other colours are in short supply. Your network is divided into many users using the colours blue and yellow because they are free to use. The blue users need to get out to the web fairly regularly, so you buy a few green tokens which your router can use to swap for the blue users’ tokens when they need to reach hosts on the web. Your router would be doing this:
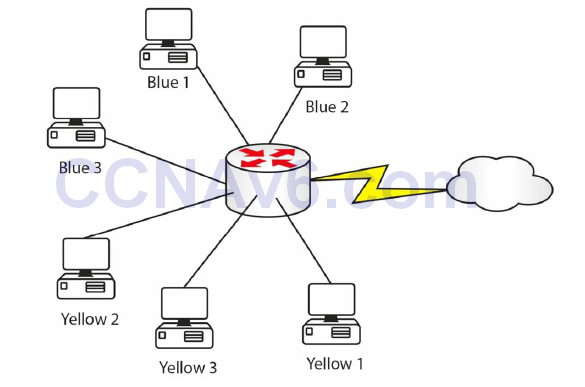
Figure 6.1 – Inside Tokens Swapped for Outside Tokens
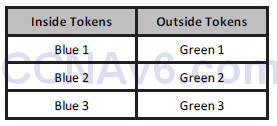
When each of the blue devices has finished with the outside connection, the green token can be released for use by another blue device. The benefits to this are outside devices can’t see your internal token IDs and you are helping conserve the limited amount of green tokens available for use on the Internet.
As you can see, NAT not only protects your network IP addresses but also is another method of address conservation. NAT is performed on routers or firewalls, so, instead of colours, you would see something like this:
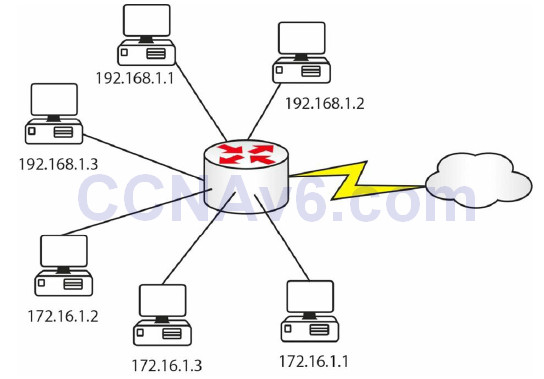
Figure 6.2 – Inside Addresses Swapped for Outside Addresses
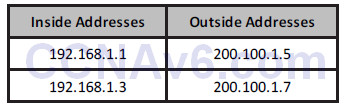
There are three ways to configure NAT on your router, depending upon your particular requirements. You will need to know all three for the CCNA exam.
In order to configure NAT, you need to tell the router which interfaces are on the inside and outside of your NAT network. This is because you could actually swap internal addresses for a pool of NAT addresses, or, at the very least, a single NAT address, and perform NAT between two Ethernet interfaces on your router.
Having said that, for the exam and in the real world, you will usually translate private Internet addresses into routable addresses on the Internet. You will see this on your home broadband router, which will usually give your laptop an IP in the 192.168.1 range but then have a routable address on the interface to the ISP.
NAT enables hosts on private networks to access resources on the Internet or other public networks. NAT is an IETF standard that enables a LAN to use one set of IP addresses for internal traffic, typically private address space as defined in RFC 1918, and another set of addresses for external traffic, typically publicly registered IP address space.
NAT converts the packet headers for incoming and outgoing traffic and keeps track of each session. The key to understanding NAT and, ultimately, troubleshooting NAT problems is having a solid understanding of NAT terminology. You should be familiar with the following NAT terms:
• The NAT inside interface
• Inside local address
• Inside global address
• The NAT outside interface
• Outside local address
• Outside global address
In NAT terminology, the inside interface is the border interface of the administrative domain controlled by the organisation. This does not necessarily have to be the default gateway used by hosts that reside within the internal network.
The inside local address is the IP address of a host residing on the inside network. In most cases, the inside local address is an RFC 1918 address (i.e., non-routable, such as 192.168.x.x or 172.16.x.x). This address is translated to the outside global address, which is typically an IP address from a publically assigned or registered pool. It is important to remember, however, that the inside local address could also be a public address.
The inside global address is the IP address of an internal host as it appears to the outside world. Once the inside IP address has been translated, it will appear as an inside global address to the Internet public or to any other external network or host.
The outside interface is the boundary for the administrative domain that is not controlled by the organisation. In other words, the outside interface is connected to the external network, which may be the Internet or any other external network, such as a partner network, for example. Any hosts residing beyond the outside interface fall outside the local organisation’s administration.
The outside local address is the IP address of an outside, or external, host as it appears to inside hosts. Finally, the outside global address is an address that is legal and can be used on the Internet. Both outside local addresses and outside global addresses are typically allocated from a globally routable address or network space.
To clarify these concepts further, Figure 6.3 below shows the use of the addresses in a session between two hosts. NAT is enabled on the intermediate gateway:
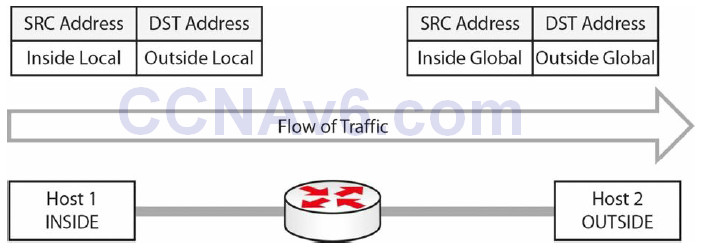
Figure 6.3 – Understanding NAT Inside and Outside Addresses
NAT inside and outside addressing is a classic exam question, so come back to this concept a few times.
Configuring and Verifying NAT
The configuration and verification of Network Address Translation with Cisco IOS software is a straightforward task. When configuring NAT, perform the following:
• Designate one or more interfaces as the internal (inside) interface(s) using the ip nat inside interface configuration command.
• Designate an interface as the external (outside) interface using the ip nat outside interface configuration command.
• Configure an access control list (ACL) that will match all traffic for translation. This can be a standard or an extended named or numbered ACL.
• Optionally, configure a pool of global addresses using the ip nat pool <name> <start-ip> <end-ip> [netmask <mask> | prefix-length <length>] global configuration command. This defines a pool of inside global addresses to which inside local addresses will be translated.
• Configure NAT globally using the ip nat inside source list <ACL> [interface|pool] <name> [overload] global configuration command.
Farai says – “Please also check out the ip nat inside source static command, which you can review for free at www.howtonetwork.net/public/698.cfm.”
The following output shows you one way to configure NAT (dynamic NAT) with Cisco IOS software. You can see that the configuration has used the description and remark features available to help administrators more easily manage and troubleshoot their networks:
R1(config)#interface FastEthernet0/0 R1(config-if)#description ‘Connected To The Internal LAN’ R1(config-if)#ip address 10.5.5.1 255.255.255.248 R1(config-if)#ip nat inside R1(config-if)#exit R1(config)#interface Serial0/0 R1(config-if)#description ‘Connected To The ISP’ R1(config-if)#ip address 150.1.1.1 255.255.255.248 R1(config-if)#ip nat outside R1(config-if)#exit R1(config)#access-list 100 remark ‘Translate Internal Addresses Only’ R1(config)#access-list 100 permit ip 10.5.5.0 0.0.0.7 any R1(config)#ip nat pool INSIDE-POOL 150.1.1.3 150.1.1.6 prefix-length 24 R1(config)#ip nat inside source list 100 pool INSIDE-POOL R1(config)#exit
Following this configuration, the show ip nat translations command can be used to verify that translations are actually taking place on the router, as illustrated below:
R1#show ip nat translations Pro Inside global Inside local Outside local Outside global icmp 150.1.1.4:4 10.5.5.1:4 200.1.1.1:4 200.1.1.1:4 icmp 150.1.1.3:1 10.5.5.2:1 200.1.1.1:1 200.1.1.1:1 tcp 150.1.1.5:159 10.5.5.3:159 200.1.1.1:23 200.1.1.1:23
You actually have three choices when it comes to configuring NAT on your router:
• Swap one internal address for one external address (static NAT)
• Swap many internal addresses for two or more external addresses (dynamic NAT)
• Swap many internal addresses for many external ports (Port Address Translation or oneway
NAT)
Static NAT
You would want to swap one specific address for another address when you have a web server (for example) on the inside of your network. If you keep using dynamic addressing, then there is no way to reach the destination address because it keeps changing.
Farai says – “You would use static NAT (see Figure 6.4 below) for any server that needs to be reachable via the Internet, such as e-mail or FTP.”
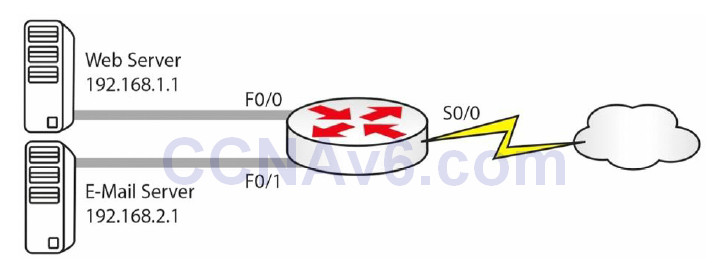
Figure 6.4 – Static NAT in Use
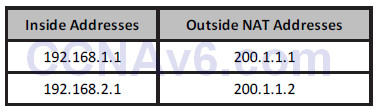
For the network above, your configuration would be as follows:
Router(config)#interface f0/0 Router(config-if)#ip address 192.168.1.1 255.255.255.0 Router(config-if)#ip nat inside Router(config)#interface f0/1 Router(config-if)#ip address 192.168.2.1 255.255.255.0 Router(config-if)#ip nat inside Router(config)#interface s0/0 Router(config-if)#ip nat outside Router(config-if)#exit Router(config)#ip nat inside source static 192.168.1.1 200.1.1.1 Router(config)#ip nat inside source static 192.168.2.1 200.1.1.2
The ip nat inside and ip nat outside commands tell the router which are the inside NAT interfaces and which are the outside NAT interfaces. The ip nat inside source command defines the static translations, of which you could have as many as you wish, so long as you paid for the public IP addresses. The vast majority of configuration mistakes I fixed whilst at Cisco were missing ip nat inside and ip nat outside statements! You might see questions in the exam where you have to spot configuration mistakes.
I strongly recommend that you type the commands above onto a router. You will do many NAT labs in this book, but the more you type whilst you read the theory section, the better the information will stick in your head.
Dynamic NAT or NAT Pool
You will often need to use a group, or pool, of routable addresses. One-to-one NAT mapping has its limitations, of course, expense and extensive lines of configuration on your router to name two. Dynamic NAT allows you to configure one or more groups of addresses to be used by your internal hosts.
Your router will keep a list of the internal addresses to external addresses, and eventually the translation in the table will time out. You can alter the timeout values but please do so on the advice of a Cisco TAC engineer.
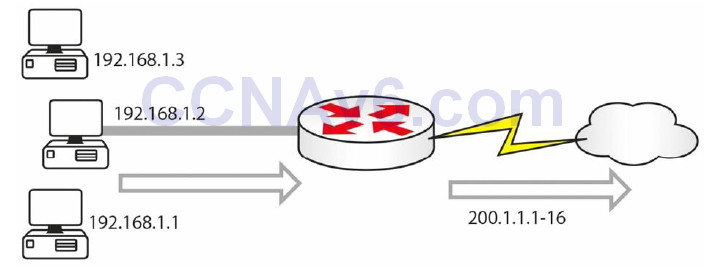
Figure 6.5 – Internal Addresses to a NAT Pool of Routable Addresses
If you issued a show ip nat translations command on the router when the inside hosts have made outside connections, you would see a chart containing something like this:
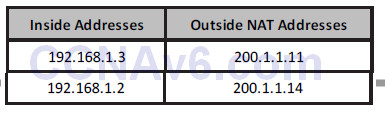
In Figure 6.5 above, you have internal addresses using a pool of addresses from 200.1.1.1 to 200.1.1.16. Here is the configuration file to achieve it. I have left off the router interface addresses for now:
Router(config)#interface f0/0 Router(config-if)#ip nat inside Router(config)#interface s0/1 Router(config-if)#ip nat outside Router(config)#ip nat pool poolname 200.1.1.1 200.1.1.16 netmask 255.255.255.0 Router(config)#ip nat inside source list 1 pool poolname Router(config)#access-list 1 permit 192.168.1.0 0.0.0.255
The ACL is used to tell the router which addresses it can and cannot translate. The subnet mask is actually reversed and is called a wildcard mask, which will be covered later. All NAT pools need a name, and in this example, it is simply called “poolname.” The source list refers to the ACL.
NAT Overload/Port Address Translation/One-Way NAT
IP addresses are in short supply, and if you have hundreds or thousands of addresses which need to be routed, it could cost you a lot of money. In this instance, you can use NAT overload (see Figure 6.6), also referred to as Port Address Translation (PAT) or one-way NAT by Cisco. PAT cleverly allows a port number to be added to the IP address as a way of uniquely identifying it from another translation using the same IP address. There are over 65,000 ports available per IP address.
Although this is beyond the scope of the CCNA exam, it could be useful to know how PAT handles port numbers. Per Cisco documentation, it divides the available ports per global IP address into three ranges: 0–511, 512–1023, and 1024–65535. PAT assigns a unique source port to each UDP or TCP session. It will attempt to assign the same port value of the original request, but if the original source port has already been used, it will start scanning from the beginning of the particular port range to find the first available port and will assign it to the conversation.
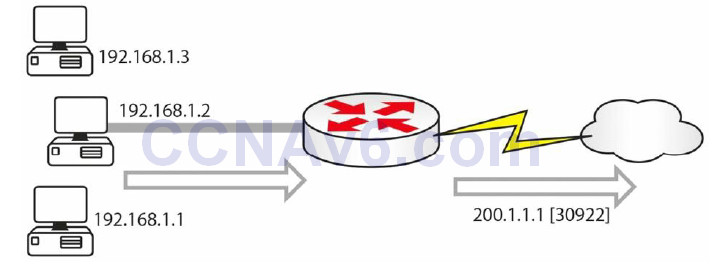
Figure 6.6 – NAT Overload
The show ip nat translations table this time would show the IP addresses and port numbers:
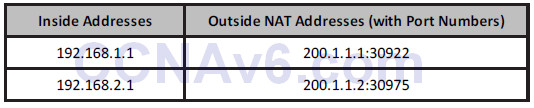
To configure PAT, you would carry out the exact same configuration as for dynamic NAT, but you would add the keyword [overload] to the end of the pool:
Router(config)#interface f0/0 Router(config-if)#ip nat inside Router(config)#interface s0/1 Router(config-if)#ip nat outside Router(config)#ip nat pool poolname 200.1.1.1 200.1.1.1 netmask 255.255.255.0 Router(config)#ip nat inside source list 1 pool poolname overload Router(config)#access-list 1 permit 192.168.1.0 0.0.0.255
This should be pretty easy to remember!
Farai says – “Using PAT with more than one IP is a waste of address space because the router will use the first IP and
increment port numbers for each subsequent connection. This is why PAT is typically configured to overload to the
interface.”
Troubleshooting NAT
Nine times out of ten, the router administrator has forgotten to add the ip nat outside or ip nat inside command to the router interfaces. In fact, this is almost always the problem! The next most frequent mistakes include the wrong ACL and a misspelled pool name (it is case sensitive).
You can debug NAT translations on the router by using the debug ip nat [detailed] command, and you can view the NAT pool with the show ip nat translations command.
Section 6 Questions
1. NAT converts the _______ headers for incoming and outgoing traffic and keeps track of
each session.
2. The _______ address is the IP address of an outside, or external, host as it appears to
inside hosts.
3. How do you designate inside and outside NAT interfaces?
4. Which show command displays a list of your NAT table?
5. When would you want to use static NAT?
6. Write the configuration command for NAT 192.168.1.1 to 200.1.1.1.
7. Which command do you add to a NAT pool to enable PAT?
8. NAT most often fails to work because the _______ command is missing.
9. Which debug command shows live NAT translations occurring?
Section 6 Answers
1. Packet.
2. Outside local.
3. With the ip nat inside and ip nat outside commands.
4. The show ip nat translations command.
5. When you have a web server (for example) on the inside of your network.
6. ip nat inside source static 192.168.1.1 200.1.1.1.
7. The overload command.
8. The ip nat inside or ip nat outside command.
9. The debug ip nat [detailed] command.
Section 6 Labs
Static NAT Lab
Topology

Purpose
Learn how to configure static NAT.
Walkthrough
1. Add IP address 192.168.1.1 255.255.255.0 to Router A and change the hostname to Router A. Add IP address 192.168.1.2 255.255.255.0 to Router B. Add a clock rate to the correct side and ping from A to B or from B to A. Check the previous labs if you need a reminder.
2. You need to add an IP address to Router A to simulate a host on the LAN. You can achieve this with a Loopback interface:
RouterA#conf t Enter configuration commands, one per line. End with CNTL/Z. RouterA(config)#interface Loopback0 RouterA(config-if)#ip add 10.1.1.1 255.0.0.0 RouterA(config-if)#
3. For testing, you need to tell Router B to send any traffic to any network back out towards Router A. You will do this with a static route:
RouterB#conf t Enter configuration commands, one per line. End with CNTL/Z. RouterB(config)#ip route 0.0.0.0 0.0.0.0 Serial0/1/0 RouterB(config)#
4. Test to see whether the static route is working by pinging from the Loopback interface on Router A to Router B:
RouterA#ping Protocol [ip]: Target IP address: 192.168.1.2 Repeat count [5]: Datagram size [100]: Timeout in seconds [2]: Extended commands [n]: y Source address or interface: 10.1.1.1 Type of service [0]: Set DF bit in IP header? [no]: Validate reply data? [no]: Data pattern [0xABCD]: Loose, Strict, Record, Timestamp, Verbose[none]: Sweep range of sizes [n]: Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.1.2, timeout is 2 seconds: Packet sent with a source address of 10.1.1.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 31/31/32 ms RouterA#
5. Configure a static NAT entry on Router A. Using NAT, translate the 10.1.1.1 address to 172.16.1.1 when it leaves the router. You also need to tell the router which is the inside and outside NAT interface:
RouterA#conf t Enter configuration commands, one per line. End with CNTL/Z. RouterA(config)#int Loopback0 RouterA(config-if)#ip nat inside RouterA(config-if)#int Serial0/1/0 RouterA(config-if)#ip nat outside RouterA(config-if)# RouterA(config-if)#ip nat inside source static 10.1.1.1 172.16.1.1 RouterA(config)#
6. Turn on NAT debugging so you can see the translations taking place. Then issue another extended ping (from L0) and check the NAT table. Your output may differ from mine due to changes in IOS.
RouterA#debug ip nat IP NAT debugging is on RouterA# RouterA#ping Protocol [ip]: Target IP address: 192.168.1.2 Repeat count [5]: Datagram size [100]: Timeout in seconds [2]: Extended commands [n]: y Source address or interface: 10.1.1.1 Type of service [0]: Set DF bit in IP header? [no]: Validate reply data? [no]: Data pattern [0xABCD]: Loose, Strict, Record, Timestamp, Verbose[none]: Sweep range of sizes [n]: Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.1.2, timeout is 2 seconds: Packet sent with a source address of 10.1.1.1 NAT: s=10.1.1.1->172.16.1.1, d=192.168.1.2 [11] ! NAT*: s=192.168.1.2, d=172.16.1.1->10.1.1.1 [11] NAT: s=10.1.1.1->172.16.1.1, d=192.168.1.2 [12] ! NAT*: s=192.168.1.2, d=172.16.1.1->10.1.1.1 [12] NAT: s=10.1.1.1->172.16.1.1, d=192.168.1.2 [13] ! NAT*: s=192.168.1.2, d=172.16.1.1->10.1.1.1 [13] NAT: s=10.1.1.1->172.16.1.1, d=192.168.1.2 [14] ! NAT*: s=192.168.1.2, d=172.16.1.1->10.1.1.1 [14] NAT: s=10.1.1.1->172.16.1.1, d=192.168.1.2 [15] ! Success rate is 100 percent (5/5), round-trip min/avg/max = 31/46/110 ms RouterA# NAT*: s=192.168.1.2, d=172.16.1.1->10.1.1.1 [15] RouterA#show ip nat translations Pro Inside global Inside local Outside local Outside global icmp 172.16.1.1:10 10.1.1.1:10 192.168.1.2:10 192.168.1.2:10 icmp 172.16.1.1:6 10.1.1.1:6 192.168.1.2:6 192.168.1.2:6 icmp 172.16.1.1:7 10.1.1.1:7 192.168.1.2:7 192.168.1.2:7 icmp 172.16.1.1:8 10.1.1.1:8 192.168.1.2:8 192.168.1.2:8 icmp 172.16.1.1:9 10.1.1.1:9 192.168.1.2:9 192.168.1.2:9 --- 172.16.1.1 10.1.1.1 --- ---RouterA#
7. Bear in mind that the router will clear the NAT translation soon afterwards in order to clear the NAT address(es) for use by other IP addresses:
NAT: expiring 172.16.1.1 (10.1.1.1) icmp 6 (6) NAT: expiring 172.16.1.1 (10.1.1.1) icmp 7 (7)
NAT Pool Lab
Topology
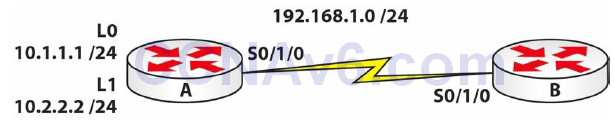
Purpose
Learn how to configure a NAT pool (dynamic NAT).
Walkthrough
1. Add IP address 192.168.1.1 255.255.255.0 to Router A and change the hostname to Router A. Add IP address 192.168.1.2 255.255.255.0 to Router B. Add a clock rate to the correct side and ping from A to B or from B to A. Check the previous lab if you need a reminder.
2. You need to add two IP addresses to Router A to simulate a host on the LAN. You can achieve this with two Loopback interfaces. They will be in different subnets but both start with a 10 address:
RouterA#conf t Enter configuration commands, one per line. End with CNTL/Z. RouterA(config)#interface Loopback0 RouterA(config-if)#ip add 10.1.1.1 255.255.255.0 RouterA(config-if)#int l1 ← short for Loopback1 RouterA(config-if)#ip address 10.2.2.2 255.255.255.0 RouterA(config-if)#
3. For testing, you need to tell Router B to send any traffic to any network back out towards Router A. You will do this with a static route:
RouterB#conf t Enter configuration commands, one per line. End with CNTL/Z. RouterB(config)#ip route 0.0.0.0 0.0.0.0 Serial0/1/0 RouterB(config)#
4. Test to see whether the static route is working by pinging from the Loopback interface on Router A to Router B:
RouterA#ping Protocol [ip]: Target IP address: 192.168.1.2 Repeat count [5]: Datagram size [100]: Timeout in seconds [2]: Extended commands [n]: y Source address or interface: 10.1.1.1 Type of service [0]: Set DF bit in IP header? [no]: Validate reply data? [no]: Data pattern [0xABCD]: Loose, Strict, Record, Timestamp, Verbose[none]: Sweep range of sizes [n]: Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.1.2, timeout is 2 seconds: Packet sent with a source address of 10.1.1.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 31/31/32 ms RouterA#
5. Configure a NAT pool on Router A. For this lab, use 172.16.1.1 to 172.16.1.10. Any address starting with 10 will be a NAT. Remember that you MUST specify the inside and outside NAT interfaces or NAT won’t work:
RouterA#conf t Enter configuration commands, one per line. End with CNTL/Z. RouterA(config)#int l0 RouterA(config-if)#ip nat inside RouterA(config)#int l1 RouterA(config-if)#ip nat inside RouterA(config-if)#int Serial0/1/0 RouterA(config-if)#ip nat outside RouterA(config-if)#exit RouterA(config)#ip nat pool 60days 172.16.1.1 172.16.1.10 netmask 255.255.255.0 RouterA(config)#ip nat inside source list 1 pool 60days RouterA(config)#access-list 1 permit 10.1.1.0 0.0.0.255 RouterA(config)#access-list 1 permit 10.2.1.0 0.0.0.255 RouterA(config)#
The ip nat pool command creates the pool of addresses. You need to give the pool a name of your own choosing. The netmask command tells the router which network mask to apply to the pool.
The source list command tells the router which ACL to look at. The ACL tells the router which networks will match the NAT pool.
6. Turn on NAT debugging so you can see the translations taking place. Then issue extended pings (from L0 and L1) and check the NAT table. Your output may differ from mine due to changes in IOS. You should see two addresses from the NAT pool being used.
RouterA#debug ip nat RouterA#ping Protocol [ip]: Target IP address: 192.168.1.2 Repeat count [5]: Datagram size [100]: Timeout in seconds [2]: Extended commands [n]: y Source address or interface: 10.1.1.1 Type of service [0]: Set DF bit in IP header? [no]: Validate reply data? [no]: Data pattern [0xABCD]: Loose, Strict, Record, Timestamp, Verbose[none]: Sweep range of sizes [n]: Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.1.2, timeout is 2 seconds: Packet sent with a source address of 10.1.1.1 NAT: s=10.1.1.1->172.16.1.1, d=192.168.1.2 [26] ! NAT*: s=192.168.1.2, d=172.16.1.1->10.1.1.1 [16] NAT: s=10.1.1.1->172.16.1.1, d=192.168.1.2 [27] ! NAT*: s=192.168.1.2, d=172.16.1.1->10.1.1.1 [17] NAT: s=10.1.1.1->172.16.1.1, d=192.168.1.2 [28] ! NAT*: s=192.168.1.2, d=172.16.1.1->10.1.1.1 [18] NAT: s=10.1.1.1->172.16.1.1, d=192.168.1.2 [29] ! NAT*: s=192.168.1.2, d=172.16.1.1->10.1.1.1 [19] NAT: s=10.1.1.1->172.16.1.1, d=192.168.1.2 [30] ! Success rate is 100 percent (5/5), round-trip min/avg/max = 17/28/32 ms RouterA# NAT*: s=192.168.1.2, d=172.16.1.1->10.1.1.1 [20] RouterA#ping Protocol [ip]: Target IP address: 192.168.1.2 Repeat count [5]: Datagram size [100]: Timeout in seconds [2]: Extended commands [n]: y Source address or interface: 10.2.2.2 Type of service [0]: Set DF bit in IP header? [no]: Validate reply data? [no]: Data pattern [0xABCD]: Loose, Strict, Record, Timestamp, Verbose[none]: Sweep range of sizes [n]: Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.1.2, timeout is 2 seconds: Packet sent with a source address of 10.2.2.2 NAT: s=10.2.2.2->172.16.1.2, d=192.168.1.2 [31] ! NAT*: s=192.168.1.2, d=172.16.1.2->10.2.2.2 [21] NAT: s=10.2.2.2->172.16.1.2, d=192.168.1.2 [32] ! NAT*: s=192.168.1.2, d=172.16.1.2->10.2.2.2 [22] NAT: s=10.2.2.2->172.16.1.2, d=192.168.1.2 [33] ! NAT*: s=192.168.1.2, d=172.16.1.2->10.2.2.2 [23] NAT: s=10.2.2.2->172.16.1.2, d=192.168.1.2 [34] ! NAT*: s=192.168.1.2, d=172.16.1.2->10.2.2.2 [24] NAT: s=10.2.2.2->172.16.1.2, d=192.168.1.2 [35] ! Success rate is 100 percent (5/5), round-trip min/avg/max = 31/31/32 ms RouterA# NAT*: s=192.168.1.2, d=172.16.1.2->10.2.2.2 [25] RouterA#show ip nat trans Pro Inside global Inside local Outside local Outside global icmp 172.16.1.1:16 10.1.1.1:16 192.168.1.2:16 192.168.1.2:16 icmp 172.16.1.1:17 10.1.1.1:17 192.168.1.2:17 192.168.1.2:17 icmp 172.16.1.1:18 10.1.1.1:18 192.168.1.2:18 192.168.1.2:18 icmp 172.16.1.1:19 10.1.1.1:19 192.168.1.2:19 192.168.1.2:19 icmp 172.16.1.1:20 10.1.1.1:20 192.168.1.2:20 192.168.1.2:20 icmp 172.16.1.2:21 10.2.2.2:21 192.168.1.2:21 192.168.1.2:21 icmp 172.16.1.2:22 10.2.2.2:22 192.168.1.2:22 192.168.1.2:22 icmp 172.16.1.2:23 10.2.2.2:23 192.168.1.2:23 192.168.1.2:23 icmp 172.16.1.2:24 10.2.2.2:24 192.168.1.2:24 192.168.1.2:24 icmp 172.16.1.2:25 10.2.2.2:25 192.168.1.2:25 192.168.1.2:25 RouterA#
NAT Overload Lab
Repeat the previous lab. This time, when referring to the pool, add the overload command to the end of the configuration line. This instructs the router to use PAT. Leave off Loopback1. Please note that as Farai says, in the real world, your pool will usually have only one address or you will overload your outside interface.
RouterA(config)#ip nat inside source list 1 pool 60days overload
I’ve done some of the previous labs using Cisco Packet Tracer for convenience, so you will often see different output to mine. Here is a sample output from a PAT lab. You will see that the router is adding a port number to each translation. Unfortunately, you see a similar number at the end of the NAT pool labs, which is an annoyance of PAT.
RouterA#show ip nat tran Inside global Inside local Outside local Outside global 10.0.0.1:8759 172.16.1.129:8759 192.168.1.2:8759 192.168.1.2:8759
