Section 4 Tasks
• Read today’s lesson notes (below)
• Review yesterday’s lesson notes
• Complete today’s lab
• Read the ICND1 cram guide
Switches and routers do not come with any security configuration. You need to add this depending upon your business requirements. The commands and procedures to secure your switch are pretty much the same as those for your router. Now it’s time to move on to the practical steps you can take to secure your router from attempts to log in and reconfigure, either accidentally or maliciously.
My first job at Cisco was on the core team. Our role involved helping customers with access control lists, IOS upgrades, disaster recovery, and related tasks. One of the first things which struck me was how many engineers didn’t lock down their routers with a password. Many of those who did used the password “password” or “cisco” – probably two of the most easily guessed, I would imagine!
In this section of the guide, we will look at the basic steps you should take on every network to protect your routers.
Today you will learn about the following:
• Protecting physical access
• Telnet access
• Protecting Enable mode
• Router logging
• Securing the switch
This module maps to the following CCNA syllabus requirements:
• Configure and verify network device security features, such as:
° Device password security
° Enable secret versus enable
° Transport
° Disable Telnet
° SSH
° VTYs
° Physical security
° Service password
• Describe external authentication methods
• Configure and verify Switch Port Security features, such as:
° Sticky MAC
° MAC address limitation
° Static/dynamic
° Violation modes
° Err disable
° Shutdown
° Protect restrict
° Shut down unused ports
° Err disable recovery
• Assign unused ports to an unused VLAN
• Set native VLAN to something other than VLAN 1
• Configure and verify NTP as a client
Protecting Physical Access
Strange that when you consider the disastrous consequences of losing network access for a business, you often find their router sitting underneath somebody’s desk! Network equipment should be stored in a secure room with keypad access, or at least lock and key access. Cisco routers can be very valuable pieces of equipment, and they are attractive targets to thieves. The larger the network, the more valuable the equipment, and the higher the need to protect the data and router configuration files.
Console Access
The console port is designed to give physical access to the router to permit initial configurations and disaster recovery. Anybody having console access can completely wipe or reconfigure the files, so, for this reason, the console port should be protected with a password by adding either a password or a local username and password, as illustrated below:
• Add a password
Router(config)#line console 0 Router(config-line)#password cisco Router(config-line)#login
• Or add a local username and password
Router(config)#username paul password cisco Router(config)#line console 0 Router(config-line)#login local
You can also create a timeout on the console (and VTY) lines so that it disconnects after a certain period of time. The default is 5 minutes.
Router(config)#line console 0 Router(config-line)#exec-timeout ? <0-35791> Timeout in minutes Router(config-line)#exec-timeout 2 ? <0-2147483> Timeout in seconds <cr> Router(config-line)#exec-timeout 2 30 Router(config-line)#
Telnet Access
You can’t actually Telnet into a router unless somebody adds a password to the Telnet or VTY lines. Again, you can add a password to the VTY lines or tell the router to look for a local username and password (in the configuration file or username and password stored on a RADIUS/TACACS server), as shown below:
Router(config-line)#line vty 0 15 Router(config-line)#password cisco Router(config-line)#login ← or login local
The output below is a Telnet session from one router to another. You can see the hostname change when you get Telnet access. The password will not show as you type it:
Router1#telnet 192.168.1.2 Trying 192.168.1.2 ...Open User Access Verification Username: paul Password: Router2>
If you have a security IOS image, you can configure the router to permit only SSH access rather than Telnet. The benefit of this is that all data is encrypted. If you try to Telnet after SSH has been enabled, the connection will be terminated:
Router1(config)#line vty 0 15 Router1(config-line)#transport input ssh Router2#telnet 192.168.1.2 Trying 192.168.1.2 ...Open [Connection to 192.168.1.2 closed by foreign host]
Protecting Enable Mode
Enable mode gives configuration access to the router, so you will want to protect this also. You can configure an enable secret or an enable password. In fact, you could have both at the same time, but this is a bad idea.
An enable password is unencrypted, so it can be seen in the router configuration. An enable secret is given level 5 (MD5) encryption, which is hard to break. Newer IOS releases (starting with 15.0(1)S) can also use level 4 (SHA256) encryption, which is superior to MD5 encryption (this level 5 encryption will be deprecated eventually). You can add the command service password encryption to your enable password, but this can be cracked easily because it is level 7 encryption (i.e., low security; Cisco calls it “over the shoulder security,” as it only requires someone looking over your shoulder to memorise a slightly harder phrase and then crack it using password 7 decryption tools on the Internet). You can see level 7 and level 5 encryption in the output below:
Router(config)#enable password cisco Router(config)#exit Router#show run enable password cisco Router(config)#enable password cisco Router(config)#service password-encryption Router#show run enable password 7 0822455D0A16 Router(config)#enable secret cisco Router(config)#exit Router#show run enable secret 5 $1$mERr$hx5rVt7rPNoS4wqbXKX7m0
Bear in mind that if you forget the enable password, you will have to perform a password recovery on the router or switch. Google the term for the particular model you are using because the process differs. For routers, it involves reloading the device, pressing the designated break key on your keyboard, setting the configuration register to skip the startup configuration file (usually to 0x2142), and then issuing a copy start run command so you can create a new password.
For switches, it is a bit more complicated (again, Google the term for the particular model you are using), but it can also be done using a little trick – hold down the MODE button for eight seconds while powering on the switch. The switch will boot up with a blank configuration, and the last startup configuration will be saved to the flash in the file named config.text.renamed so it can be copied back to running configuration and modified with another password.
Protecting User Access
Cisco IOS offers the ability to give users individual passwords and usernames, as well as access to a restricted list of commands. This would be useful if you have tiers of network support. An example of this is shown in the following output:
RouterA#config term Enter configuration commands, one per line. End with CNTL/Z. RouterA(config)#username paul password cisco RouterA(config)#username stuart password hello RouterA(config)#username davie password football RouterA(config)#line vty 0 4 RouterA(config-line)#login local RouterA(config-line)#exit RouterA(config)#exit
You can specify access levels for user accounts on the router. You may want, for example, junior network team members to be able to use only some basic troubleshooting commands. It is also worth remembering that Cisco routers have two modes of password security, User mode (Exec) and Privileged mode (Enable).
Cisco routers have 16 different privilege levels (0 to 15) available to configure, where 15 is full access, as illustrated below:
RouterA#conf t Enter configuration commands, one per line. End with CNTL/Z. RouterA(config)#username support privilege 4 password soccer LINE Initial keywords of the command to modify RouterA(config)#privilege exec level 4 ping RouterA(config)#privilege exec level 4 traceroute RouterA(config)#privilege exec level 4 show ip interface brief RouterA(config)#line console 0 RouterA(config-line)#password basketball RouterA(config-line)#login local ← password is needed RouterA(config-line)#^z
The support person logs in to the router and tries to go into configuration mode, but this command and any other command not available are not valid and cannot be seen:
RouterA con0 is now available Press RETURN to get started. User Access Verification Username: support Password: RouterA#config t ← not allowed to use this command ^ % Invalid input detected at ‘^’ marker.
You can see the default privilege levels at the router prompts:
Router>show privilege Current privilege level is 1 Router>en Router#show priv Router#show privilege Current privilege level is 15 Router#
Updating the IOS
Admittedly, updating the IOS can sometimes introduce new bugs or problems into your network, so it is best practice to do this on the advice of Cisco if you have a TAC support contract. In general, though, keeping your IOS up to date is highly recommended. Updating your IOS:
• Fixes known bugs
• Closes security vulnerabilities
• Offers enhanced features and IOS capabilities
Router Logging
Routers offer the ability to log events. They can send the log messages to your screen or a server if you wish. You should log router messages, and there are eight levels of logging severity available (you need to know them for the exam), as shown in bold in the output below:
logging buffered ? <0-7>Logging severity level alerts—Immediate action needed (severity=1) critical—Critical conditions (severity=2) debugging—Debugging messages (severity=7) emergencies—System is unusable (severity=0) errors—Error conditions (severity=3) informational—Informational messages (severity=6) notifications—Normal but significant conditions (severity=5) warnings—Warning conditions (severity=4)
You can send the logging messages to several places:
Router(config)#logging ? A.B.C.D IP address of the logging host buffered Set buffered logging parameters console Set console logging parameters host Set syslog server IP address and parameters on Enable logging to all enabled destinations trap Set syslog server logging level userinfo Enable logging of user info on privileged mode enabling
Logging messages will usually be displayed on the screen when you are consoled into the router. This can prove somewhat annoying if you are typing configuration commands. Here, I’m typing a command (underlined) when it’s interruped by a console logging message:
Router(config)#int f0/1 Router(config-if)#no shut Router(config-if)#end Router# *Jun 27 02:06:59.951: %SYS-5-CONFIG_I: Configured from console by console show ver *Jun 27 02:07:01.151: %LINK-3-UPDOWN: Interface FastEthernet0/1, changed state to up
You can either turn off logging messages with the no logging console command or you can set Farai says – “The command transport input all is enabled by default for all VTY lines, while transport input none is enabled by default for other lines.” them to not interrupt as you type with the logging synchronous command, which re-enters the line you were typing before being interrupted by the logging message (also available on VTY lines).
Router(config)#line con 0 Router(config-line)#logging synchronous Router(config-line)# Router(config-line)#exit Router(config)#int f0/1 Router(config-if)#shut Router(config-if)#exit Router(config)# *Jun 27 02:12:46.143: %LINK-5-CHANGED: Interface FastEthernet0/1, changed state to administratively down Router(config)#exit
It’s worth mentioning here that you won’t see console output when you are Telnetted (or using SSH) into the router. If you want to see logging messages when Telnetted in, then issue the terminal monitor command.
Simple Network Management Protocol (SNMP)
SNMP is a service you can use to manage your network remotely. It consists of a central station maintained by an administrator running the SNMP management software and smaller files (agents) on each of your network devices, including routers, switches, and servers.
Several vendors have designed SNMP software, including HP, Cisco, IBM, and SolarWinds. There are also open source versions available. This software allows you to monitor bandwidth and activity on devices, such as logins and port status.
You can remotely configure or shut down ports and devices using SNMP. You can also configure it to send alerts when certain conditions are met, such as high bandwidth or ports going down. We will cover SNMP in more detail on Section 40 because it is part of the ICND2 syllabus.
Securing the Switch
Prevent Telnet Access
Telnet traffic sends the password in clear text, which means that it could easily be read on the configuration or by a network sniffer, if one was attached to your network.
Telnet is actually disabled by default (i.e., you need to set a password and, optionally, a username to get it working). However, if you still want to have remote access to the management ports, you can enable SSH traffic to the switch with the transport input ssh command, which was discussed earlier.
Farai says – “The command transport input all is enabled by default for all VTY lines, while transport input none is
enabled by default for other lines.”
Enable SSH
When possible, you should always use SSH instead of Telnet and SNMP to access your switches. SSH stands for secure shell and allows a secure exchange of information between two devices on a network. SSH uses public-key cryptography to authenticate the connecting device. Telnet and SNMP versions 1 and 2 are unencrypted and susceptible to packet sniffing (SNMP version 3 offers confidentiality – encryption of packets to prevent snooping by an unauthorised source). SSH, on the other hand, is encrypted.
To enable SSH you must have a version of IOS that supports encryption. A quick way to find this out is the show version command. Look for K9 in the file name and/or the security statement of Cisco Systems.
Switch#sh version Cisco IOS Software, C3560 Software (C3560-ADVIPSERVICES K9-M), Version 12.2(35)SE1, RELEASE SOFTWARE (fc1) Copyright (c) 1986-2006 by Cisco Systems, Inc. Compiled Tue 19-Dec-06 10:54 by antonio Image text-base: 0x00003000, data-base: 0x01362CA0 ROM: Bootstrap program is C3560 boot loader BOOTLDR: C3560 Boot Loader (C3560-HBOOT-M) Version 12.2(25r)SEC, RELEASE SOFTWARE (fc4) Switch uptime is 1 hour, 8 minutes System returned to ROM by power-on System image file is “flash:/c3560-advipservicesk9-mz.122-35.SE1.bin” This product contains cryptographic features and is subject to United States and local country laws governing import, export, transfer and use. Delivery of Cisco cryptographic products does not imply third-party authority to import, export, distribute or use encryption. Importers, exporters, distributors and users are responsible for compliance with U.S. and local country laws. By using this product you agree to comply with applicable laws and regulations. If you are unable to comply with U.S. and local laws, return this product immediately. A summary of U.S. laws governing Cisco cryptographic products may be found at: http://www.cisco.com/wwl/export/crypto/tool/stqrg.html If you require further assistance please contact us by sending email to [email protected]. --More
NOTE: If you do not have a security version of IOS, you must purchase a license for it.
For an encrypted connection , you will need to create a private/public key on the switch (see below). When you connect, use the public key to encrypt the data and the switch will use its private key to decrypt the data. For authentication, use your chosen username/password combination. Next, set the switch hostname and domain name because the private/public keys will be created using the hostname.domainname nomenclature. Obviously, it makes sense for the key to be named something representing the system.
Firstly, make sure that you have a hostname other than the default one, which is Switch. Next, add your domain name (this typically matches your FQDN in Windows Active Directory). Then, create the crypto key that will be used for encryption. The modulus will be the length of the keys you want to use, in the range from 360 to 2048, with the latter being the most secure; 1024 and above is considered secure. At this point, SSH is enabled on the switch. There are a few maintenance commands you should enter as well. The ip ssh time-out 60 will time out any SSH connection that has been idle for 60 seconds. The ip ssh authentication-retries 2 will reset the initial SSH connection if authentication fails two times. This will not prevent the user from establishing a new connection and retrying authentication. This process is illustrated in the output below:
Switch(config)#hostname SwitchOne SwitchOne(config)#ip domain-name mydomain.com SwitchOne(config)#crypto key generate rsa Enter modulus: 1024 SwitchOne(config)#ip ssh time-out 60 SwitchOne(config)#ip ssh authentication-retries 2
You can optionally enable SSH version 2 with the ip ssh version 2 command. Let’s take a look at one of the keys. In this example, the key was generated for HTTPS. Because the key was automatically generated when enabling HTTPS, the name will also be auto-generated.
firewall#show crypto key mypubkey rsa Key name: HTTPS_SS_CERT_KEYPAIR.server Temporary key Usage: Encryption Key Key is not exportable. Key Data: 306C300D 06092A86 4886F70D 01010105 00035B00 30580251 00C41B63 8EF294A1 DC0F7378 7EF410F6 6254750F 475DAD71 4E1CD15E 1D9086A8 BD175433 1302F403 2FD22F82 C311769F 9C75B7D2 1E50D315 EFA0E940 DF44AD5A F717BF17 A3CEDBE1 A6A2D601 45F313B6 6B020301 0001
To verify that SSH is enabled on the switch, enter the following command:
Switch#show ip ssh SSH Enabled - version 1.99 Authentication timeout: 120 secs; Authentication retries: 2 Switch#
If you have SSH enabled, you should probably disable Telnet and HTTP. When you enter the transport input command, any protocol entered after it is allowed. Any protocol not entered is not allowed. In the output below, you can see that only SSH is allowed:
line vty 0 15 transport input ssh
The following output shows that both SSH and Telnet are allowed:
line vty 0 15 transport input ssh telnet
You can disable HTTP access with one simple command:
Switch(config)#no ip http server
To view the status of the HTTP server on the switch:
Switch#show ip http server status HTTP server status: Disabled HTTP server port: 80 HTTP server authentication method: enable HTTP server access class: 0 HTTP server base path: flash:html Maximum number of concurrent server connections allowed: 16 Server idle time-out: 180 seconds Farai says – “You can encrypt the enable secret password with the service password-encryption command.” Server life time-out: 180 seconds Maximum number of requests allowed on a connection: 25 HTTP server active session modules: ALL HTTP secure server capability: Present HTTP secure server status: Enabled HTTP secure server port: 443 HTTP secure server ciphersuite: 3des-ede-cbc-sha des-cbc-sha rc4-128-md5 rc4-12 HTTP secure server client authentication: Disabled HTTP secure server trustpoint: HTTP secure server active session modules: ALL
You could also apply an access control list to the VTY lines and permit only SSH. We will cover access control lists on Section 9.
Set an Enable Secret Password
Global Configuration mode will permit a user to configure the switch or router and erase configurations, as well as reset passwords. You must protect this mode by setting a password or a secret password (which actually prevents the user from getting past User mode). The secret password will be displayed on the routers running the configuration file, whereas the enable secret password will be encrypted.
I’ve already mentioned that you can actually have both a password and an enable secret password on your router and switch, but this can cause confusion. Just set the enable secret password. The configuration file below illustrates how to issue a command without dropping back to Privileged mode by typing do before the command:
Switch1(config)#enable password cisco Switch1(config)#do show run Building configuration... Current configuration: 1144 bytes hostname Switch1 enable password cisco
Farai says – “You can encrypt the enable secret password with the service password-encryption command.”
You can erase most lines of configuration by issuing it again with the word no before the command. It is also worth noting that, as Farai says, you can issue a service passwordencryption command, but this only offers weak (level 7) encryption, whereas below, the secret password has strong (MD5) encryption :
Switch1(config)#no enable password Switch1(config)#enable secret cisco Switch1(config)#do show run Building configuration... Current configuration: 1169 bytes hostname Switch1 enable secret 5 $1$mERr$hx5rVt7rPNoS4wqbXKX7m0 [strong level 5 password]
Services
You should always disable the services you are not going to use. Cisco has done a good job by not enabling insecure or rarely used services/protocols; however, you might want to disable them just to make sure. There are some services that are helpful as well. The majority of services are found under the command service in Global Configuration mode.
Switch(config)# service ? compress-config Compress the configuration file config TFTP load config files counters Control aging of interface counters dhcp Enable DHCP server and relay agent disable-ip-fast-frag Disable IP particle-based fast fragmentation exec-callback Enable EXEC callback exec-wait Delay EXEC startup on noisy lines finger Allow responses to finger requests hide-telnet-addresses Hide destination addresses in telnet command linenumber enable line number banner for each exec nagle Enable Nagle’s congestion control algorithm old-slip-prompts Allow old scripts to operate with slip/ppp pad Enable PAD commands password-encryption Encrypt system passwords password-recovery Disable password recovery prompt Enable mode specific prompt pt-vty-logging Log significant VTY-Async events sequence-numbers Stamp logger messages with a sequence number slave-log Enable log capability of slave IPs tcp-keepalives-in Generate keepalives on idle incoming network connections tcp-keepalives-out Generate keepalives on idle outgoing network connections tcp-small-servers Enable small TCP servers (e.g., ECHO) telnet-zeroidle Set TCP window 0 when connection is idle timestamps Timestamp debug/log messages udp-small-servers Enable small UDP servers (e.g., ECHO)
Generally speaking, the most common services to enable/disable are listed below. The
description of the service is in brackets [ ].
• no service pad [packet assembler/disassembler, used in asynchronous networking; rarely used]
• no service config [prevents the switch from getting its config file from the network]
• no service finger [disables the finger server; rarely used]
• no ip icmp redirect [prevents ICMP redirects, which can be used for router poisoning]
• no ip finger [another way to disable the finger service]
• no ip gratuitous-arps [disable to prevent man-in-the-middle attacks]
• no ip source-route [disables user-provided hop-by-hop routing to destination]
• service sequence-numbers [in each log entry, gives it a number and increases sequentially]
• service tcp-keepalives-in [prevents the router from keeping hung management sessions open]
• service tcp-keepalives-out [same as service tcp-keepalives-in]
• no service udp-small-servers [disables echo, chargen, discard, daytime; rarely used]
• no service tcp-small-servers [disables echo, chargen, discard; rarely used]
• service timestamps debug datetime localtime show-timezone [timestamps each logged packet (in debug mode) with the date and time, using local time, and shows the timezone]
• service timestamps log datetime localtime show-timezone [timestamps each logged packet (not in debug mode) with the date and time, using local time, and shows the timezone – very useful for observing the log file (especially if the clock is set up correctly) ]
Change the Native VLAN
The native VLAN is used by the switch to carry specific protocol traffic, such as Cisco Discovery Protocol (CDP), VLAN Trunking Protocol (VTP), Port Aggregation Protocol (PAgP), and Dynamic Trunking Protocol (DTP) information. The default native VLAN is always VLAN 1; however, the native VLAN can be manually changed to any valid VLAN number (except for 0 and 4096, because these are in the reserved range of VLANs).
You can verify the native VLAN with the commands (issued per interface) illustrated in the output below:
Switch#show interfaces FastEthernet0/1 switchport Name: Fa0/1 Switchport: Enabled Administrative Mode: trunk Operational Mode: trunk Administrative Trunking Encapsulation: dot1q Operational Trunking Encapsulation: dot1q Negotiation of Trunking: On Access Mode VLAN: 1 (default) Trunking Native Mode VLAN: 1 (default) Voice VLAN: none
Having ports in VLAN 1 is considered a security vulnerability which allows hackers to gain access to network resources. To mitigate this problem, it is advisable to avoid putting any hosts into VLAN 1. You can also change the native VLAN on all trunk ports to an unused VLAN:
Switch(config-if)#switchport trunk native vlan 888
NOTE: This is one of the key objectives in the CCNA syllabus, so bear it in mind.
You can also prevent native VLAN data from passing on the trunk with the command below:
Switch(config-if)#switchport trunk allowed vlan remove 888
Change the Management VLAN
You can also add an IP address to the switch to allow you to Telnet to it for management purposes. This is referred to as a Switch Virtual Interface (SVI). It is a wise precaution to have this management access in a VLAN other than VLAN 1, as shown in the output below:
Switch(config)#vlan 3 Switch(config-vlan)#interface vlan3 %LINK-5-CHANGED: Interface Vlan3, changed state to up Switch(config-if)#ip address 192.168.1.1 255.255.255.0
Turn Off CDP
Cisco Discovery Protocol (CDP) will be covered later, but for now, you just need to know that it is turned on by default on most routers and switches universally and per interface, and its function is to discover attached Cisco devices. You may not want other Cisco devices to see information about your network devices, so you can turn this off, at least on the devices at the edge of your network which connect to other companies or your ISP.
Farai says – “CDP is not enabled by default on all platforms, such as ASR routers, for example.”
In the output below, you can see how a router connected to my switch is able to see basic information when I issue the show cdp neighbor detail command:
Router#show cdp neighbor detail Device ID: Switch1 Entry address(es): Platform: Cisco 2960, Capabilities: Switch Interface: FastEthernet0/0, Port ID (outgoing port): FastEthernet0/2 Holdtime: 176 Version : Cisco Internetwork Operating System Software IOS (tm) C2960 Software (C2960-I6Q4L2-M), Version 12.1(22)EA4, RELEASE SOFTWARE(fc1) Copyright (c) 1986-2005 by Cisco Systems, Inc. Compiled Wed 18-May-05 22:31 by jharirba advertisement version: 2 Duplex: full Router#
The command below will turn off CDP for the entire device:
Switch1(config)#no cdp run
To turn off CDP for a particular interface, issue the following command:
Switch1(config)#int FastEthernet0/2 Switch1(config-if)#no cdp enable
Add a Banner Message
A banner message will show when a user logs in to your router or switch. It won’t offer any actual security but it will display a warning message of your choice. In the configuration below, I chose the letter Y as my delimiting character, which tells the router that I’ve finished typing my message:
Switch1(config)#banner motd Y Enter TEXT message. End with the character ‘Y’. KEEP OUT OR YOU WILL REGRET IT Y Switch1(config)#
When I Telnet to the switch from my router, I can see the banner message. The mistake was choosing Y as the delimiting character because it cuts off my message:
Router#telnet 192.168.1.3 Trying 192.168.1.3 ...Open KEEP OUT OR
Banner messages can be:
• Shown before the user sees the login prompt – MOTD (message of the day)
• Shown before the user sees the login prompt – Login
• Shown to the user after the login prompt – Exec (used when you want to hide information from unauthorised users)
Banner inputs as part of the labs in this book. I suggest that you learn to configure all three types and test them by logging in to the router. You will have different choices depending upon your platform and IOS:
Router(config)#banner ? LINE c banner-text c, where ‘c’ is a delimiting character exec Set EXEC process creation banner incoming Set incoming terminal line banner login Set login banner motd Set Message of the Day banner prompt-timeout Set Message for login authentication timeout slip-ppp Set Message for SLIP/PPP
Set a VTP Password
VTP ensures that accurate VLAN information is passed between the switches on your network. In order to protect these updates, you should add a VTP password on your switch (it should match on all switches in the VTP domain), as illustrated in the output below:
Switch1(config)#vtp domain 60days Changing VTP domain name from NULL to 60days Switch1(config)#vtp password cisco Setting device VLAN database password to cisco Switch1(config)#
Restrict VLAN Information
By default, switches permit all VLANs across the trunk links. You can change this by specifying which VLANs can pass, as illustrated in the following output:
Switch1(config)#int FastEthernet0/4 Switch1(config-if)#switchport mode trunk Switch1(config-if)#switchport trunk allowed vlan ? WORD VLAN IDs of the allowed VLANs when this port is in trunking mode add add VLANs to the current list all all VLANs except all VLANs except the following none no VLANs remove remove VLANs from the current list Switch1(config-if)#switchport trunk allowed vlan 7-12 Switch1#show interface trunk Port Mode Encapsulation Status Native vlan Fa0/4 on 802.1q trunking 1 Port Vlans allowed on trunk Fa0/4 7-12
Error Disable Recovery
A series of events can cause Cisco switches to put their ports into a special disabled mode called err-disabled. This basically means that a particular port has been disabled (shut down) due to an error. This error can have multiple causes, one of the most common being a violation of a port security policy. This is a normal behaviour when an unauthorised user tries to connect to a switch port and it prevents rogue devices from accessing the network.
An err-disabled port might look something like this:
Switch# show interface f0/1 FastEthernet0/1 is down, line protocol is down [err-disabled] .....
In order to re-activate an err-disabled interface, manual intervention is necessary via issuing the shutdown and no shutdown commands on the interface (referred to a bouncing the port by network engineers). However, some situations might require automatic recovery of the original port state instead of waiting for an administrator to manually enable the port. The err-disable recovery mode functions by configuring the switch to automatically re-enable an err-disabled port after a certain period, based on the event that generated the failure. This provides granularity in deciding which events can be monitored by the err-disable recovery function.
The command to do this is the errdisable recovery cause, entered under Global Router Configuration mode:
Switch(config)#errdisable recovery cause ? all Enable timer to recover from all causes bpduguard Enable timer to recover from bpdu-guard error disable state dtp-flap Enable timer to recover from dtp-flap error disable state link-flap Enable timer to recover from link-flap error disable state pagp-flap Enable timer to recover from pagp-flap error disable state rootguard Enable timer to recover from root-guard error disable state udld Enable timer to recover from udld error disable state ......
The errdisable recovery cause command can vary based on the device model, but the most common parameters are:
• all
• arp-inspection
• bpduguard
• dhcp-rate-limit
• link-flap
• psecure-violation
• security-violation
• storm-control
• udld
The time after which the port is automatically restored is 300 seconds by default on most platforms, but this can be manually configured with the errdisable recovery interval global configuration command:
Switch(config)#errdisable recovery interval ? <30-86400> timer-interval(sec)
The show errdisable recovery command will provide information about the active features monitored by the err-disable recovery function and about the interfaces being monitored, including the time left until the interface is enabled.
Switch#show errdisable recovery ErrDisable Reason Timer Status ----------------- --------------arp-inspection Disabled bpduguard Disabled channel-misconfig Disabled dhcp-rate-limit Disabled dtp-flap Disabled gbic-invalid Disabled inline-power Disabled l2ptguard Disabled link-flap Disabled mac-limit Disabled link-monitor-failure Disabled loopback Disabled oam-remote-failure Disabled pagp-flap Disabled port-mode-failure Disabled psecure-violation Enabled security-violation Disabled sfp-config-mismatch Disabled storm-control Disabled udld Disabled unicast-flood Disabled vmps Disabled Timer interval: 300 seconds Interfaces that will be enabled at the next timeout: Interface Errdisable reason Time left(sec) --------- ----------------- -------------- Fa0/0 psecure-violation 193
External Authentication Methods
Rather than store usernames and passwords locally, you can use a server which typically runs either AAA or TACACS+. The advantage to this method is not having to manually enter usernames and passwords on each individual router and switch. Instead, they are stored on the server database.
TACACS+ stands for Terminal Access Controller Access Control System Plus. It is a Cisco proprietary protocol that uses TCP port 49. TACACS+ provides access control for network devices, including routers, and network access servers via one or more centralised servers.
RADIUS stands for Remote Authentication Dial-In User Service. It is a system of distributed network security that secures remote access to the network and a client/server protocol that uses UDP. RADIUS is open standard.
If you have TACACS+ or RADIUS, you may wish to enable Authentication, Authorization, and Accounting (AAA). AAA is installed on a server and monitors a database of user accounts for the network. Users’ access, protocols, connections, and disconnect reasons, as well as many other features, can be monitored.
Routers and switches can be configured to query the server when a user attempts to log in. The server then validates the user. You should not be expected to configure these protocols for the CCNA exam.
Router Clock and NTP
The time on a switch is often overlooked; however, it is very important. When you encounter security violations, SNMP traps, or logging of events, it uses a timestamp. If the time on your switch is incorrect, it will be difficult figuring out when the event happened. For example, let’s take a look at the switch below and check the time:
Switch#show clock *23:09:45.773 UTC Tue Mar 2 1993
The time is not accurate, so let’s change it. But first, let’s set some attributes:
clock timezone CST -6 clock summer-time CDT recurring clock summer-time CST recurring 2 Sun Mar 2:00 1 Sun Nov 2:00
First, let’s set the time zone. I’m in the Central time zone and I’m 6 hours off of GMT. Next, tell the switch that summertime (the time change) is recurring. Finally, set what the summertime time really is. Now, let’s set the time and date:
Switch#clock set 14:55:05 June 19 2007 Switch# 1d23h: %SYS-6-CLOCKUPDATE: System clock has been updated from 17:26:01 CST Tue Mar 2 1993 to 14:55:05 CST Tue Jun 19 2007, configured from console by console. Switch#show clock 14:55:13.858 CST Tue Jun 19 2007
Notice that the clock was set in Enable mode, not Configuration mode. Alternatively, you can use NTP. NTP stands for Network Time Protocol and it allows you to synchronise your switch’s clock to an atomic clock, ensuring very accurate time.
Switch(config)#ntp server 134.84.84.84 prefer Switch(config)#ntp server 209.184.112.199
You can see whether your clock has synchronised with your NTP sources with the following two commands:
Switch#show ntp associations Switch#show ntp status
We will cover NTP in more detail on Section 40.
Shut Down Unused Ports
Unused or “empty” ports within any network device pose a security risk, as someone might plug a cable into them and connect an unauthorised device to the network. This can lead to a number of issues, including:
• Network not functioning as it should
• Network information vulnerable to outsiders
This is why you should shut down every port that is not used on routers, switches, and other network devices. Depending upon the device, the shutdown state might be the default, but you should always verify this.
Shutting down a port is done with the shutdown command under the Interface Configuration mode:
Switch#conf t Switch(config)#int fa0/0 Switch(config-if)#shutdown
You can verify a port is in the shutdown state in multiple ways, one of which is using the show ip interface brief command:
Router(config-if)#do show ip interface brief Interface IP-Address OK? Method Status Protocol FastEthernet0/0 unassigned YES unset administratively down down FastEthernet0/1 unassigned YES unset administratively down down
Note that the administratively down status means that the port has been manually shut down. Another way to verify the shutdown state is using the show interface command:
Router#show interface fa0/0 FastEthernet0/0 is administratively down, line protocol is down Hardware is Gt96k FE, address is c200.27c8.0000 (bia c200.27c8.0000) MTU 1500 bytes, BW 10000 Kbit/sec, DLY 1000 usec, ......
Cisco Discovery Protocol (CDP)
Now is as good a time as any to discuss Cisco Discovery Protocol.
CDP is a hot exam topic because it provides a means to discover information about network devices before any configuration has been applied. This is a very useful troubleshooting tool; however, it also presents a security risk.
CDP is Cisco proprietary, which means it will only work on Cisco devices. It is a Layer 2 service used by devices to advertise and discover basic information about directly connected neighbours. The IEEE version of CDP is Link Layer Discovery Protocol (LLDP), but this is not included in the CCNA syllabus.
Because CDP is a Layer 2 service it does not require IP addresses to be conifigured in order to exchange information. The interface need only be enabled. If an IP address is configured, then this will be included in the CDP message.
CDP is a very powerful troubleshooting tool and you will be expected to understand how to use it in the exam. Figure 4.1 below shows CDP outputs from Router 0. Imagine if you were asked to troubleshoot this network but had no topology diagram to work from.
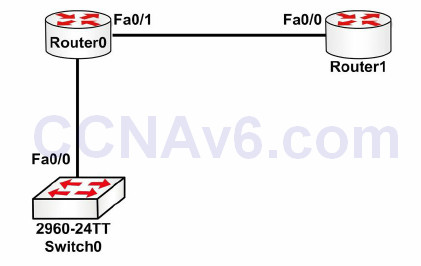
Figure 4.1 – CDP Outputs from Router 0
The following configuration outputs correspond to Figure 4.1:
Router0#show cdp neighbors Capability Codes: R - Router, T - Trans Bridge, B - Source Route Bridge, S - Switch, H -Host, I - IGMP, r - Repeater, P - Phone Device ID Local Interface Holdtime Capability Platform Port Switch Fas 0/0 165 S 2960 Fas 0/1 Router Fas 0/1 169 R C1841 Fas 0/0 Router0#
You can see more information by adding the detail command to the end:
Router0#show cdp neighbors detail Device ID: Switch Entry address(es): Platform: cisco 2960, Capabilities: Switch Interface: FastEthernet0/0, Port ID (outgoing port): FastEthernet0/1 Holdtime: 178 Version : Cisco IOS Software, C2960 Software (C2960-LANBASE-M), Version 12.2(25)FX, RELEASE SOFTWARE (fc1) Copyright (c) 1986-2005 by Cisco Systems, Inc. Compiled Wed 12-Oct-05 22:05 by pt_team advertisement version: 2 Duplex: full --------------------------- Device ID: Router Entry address(es): IP address : 192.168.1.2 Platform: cisco C1841, Capabilities: Router Interface: FastEthernet0/1, Port ID (outgoing port): FastEthernet0/0 Holdtime: 122 Version : Cisco IOS Software, 1841 Software (C1841-ADVIPSERVICESK9-M), Version 12.4(15)T1, RELEASE SOFTWARE (fc2) Technical Support: http://www.cisco.com/techsupport Copyright (c) 1986-2007 by Cisco Systems, Inc. Compiled Wed 18-Jul-07 04:52 by pt_team advertisement version: 2 Duplex: full
Now you can see the IOS release, model, IP address, and other information. Remember that you still haven’t configured an IP address on Router 0 yet.
We’ve already covered how to disable CDP on the device or interface only. Two other commands are show cdp, which displays protocol information for the device, and show cdp entry <Router>, which shows information about a specific device by imputting the name. I recommend that you spend some time checking CDP outputs during the labs you will configure in this guide.
Router0#show cdp Global CDP information: Sending CDP packets every 60 seconds Sending a holdtime value of 180 seconds Sending CDPv2 advertisements is enabled Router0#show cdp ? entry Information for specific neighbor entry interface CDP interface status and configuration neighbors CDP neighbor entries traffic CDP statistics | Output modifiers <cr>
Switch Port Security
The port security feature is a dynamic Catalyst switch feature that secures switch ports, and ultimately the CAM table, by limiting the number of MAC addresses that can be learned on a particular port or interface. With the port security feature, the switch maintains a table that is used to identify which MAC address (or addresses) can access which local switch port. Additionally, the switch can also be configured to allow only a certain number of MAC addresses to be learned on any given switch port. Port security is illustrated below in Figure 4.2:
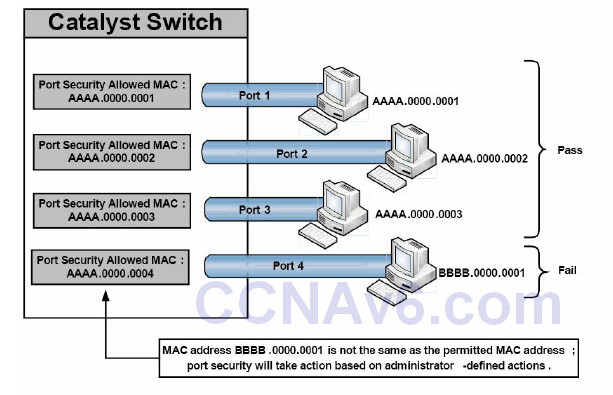
Figure 4.2 – Port Security Operation
Figure 4.2 shows four ports on a Catalyst switch configured to allow a single MAC address via the port security feature. Ports 1 through 3 are connected to hosts whose MAC address matches the address permitted by port security. Assuming no other filtering is in place, these hosts are able to forward frames through their respective switch ports. Port 4, however, has been configured to allow a host with MAC address AAAA.0000.0004, but instead a host with MAC address BBBB.0000.0001 has been connected to this port. Because the host MAC and the permitted MAC are not the same, port security will take appropriate action on the port as defined by the administrator. The valid port security actions will be described in detail in a subsequent section.
The port security feature is designed to protect the switched LAN from two primary methods of attack. These attack methods, which will be described in the following sections, are:
• CAM table overflow attacks
• MAC spoofing attacks
CAM Table Overflow Attacks
Switch CAM tables are storage locations that contain lists of known MAC addresses on physical ports, as well as their VLAN parameters. Dynamically learned contents of the switch CAM table, or MAC address table, can be viewed by issuing the show mac-address-table dynamic command, as illustrated in the following output:
VTP-Server-1#show mac-address-table dynamic Mac Address Table -------------------------------------------Vlan Mac Address Type Ports ---- ----------- -------- -----2 000c.cea7.f3a0 DYNAMIC Fa0/1 2 0013.1986.0a20 DYNAMIC Fa0/2 6 0004.c16f.8741 DYNAMIC Fa0/3 6 0030.803f.ea81 DYNAMIC Fa0/4 8 0004.c16f.8742 DYNAMIC Fa0/5 8 0030.803f.ea82 DYNAMIC Fa0/6 Total Mac Addresses for this criterion: 6
Switches, like all computing devices, have finite memory resources. This means that the CAM table has a fixed, allocated memory space. CAM table overflow attacks target this limitation by flooding the switch with a large number of randomly generated invalid source and destination MAC addresses until the CAM table fills up and the switch is no longer able to accept new entries. In such situations, the switch effectively turns into a hub and simply begins to broadcast all newly received frames to all ports (within the same VLAN) on the switch, essentially turning the VLAN into one big Broadcast domain.
CAM table attacks are easy to perform because common tools, such as MACOF and DSNIFF, are readily available to perform these activities. While increasing the number of VLANs (which reduces the size of Broadcast domains) can assist in reducing the effects of CAM table attacks, the recommended security solution is to configure the port security feature on the switch.
MAC Spoofing Attacks
MAC address spoofing is used to spoof a source MAC address in order to impersonate other hosts or devices on the network. Spoofing is simply a term that means masquerading or pretending to be someone you are not. The primary objective of MAC spoofing is to confuse the switch and cause it to believe that the same host is connected to two ports, which causes the switch to attempt to forward frames destined to the trusted host to the attacker as well. Figure 4.3 below shows the CAM table of a switch connected to four different network hosts:
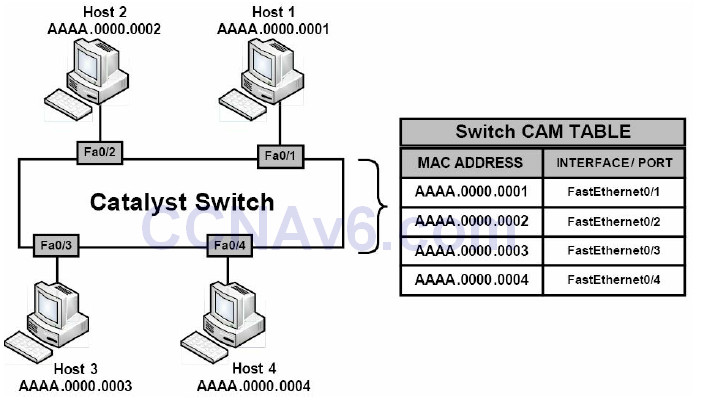
Figure 4.3 – Building the Switch CAM Table
In Figure 4.3, the switch is operating normally and, based on the CAM table entries, knows the MAC addresses for all the devices connected to its ports. Based on the current CAM table, if Host 4 wanted to send a frame to Host 2, the switch would simply forward the frame out of its FastEthernet0/2 interface toward Host 2.
Now, assume that Host 1 has been compromised by an attacker who wants to receive all traffic destined for Host 2. By using MAC address spoofing, the attacker crafts an Ethernet frame using the source address of Host 2. When the switch receives this frame, it notes the source MAC address and overwrites the CAM table entry for the MAC address of Host 2, and points it to port FastEthernet0/1 instead of FastEthernet0/2, where the real Host 2 is connected. This concept is illustrated below in Figure 4.4:
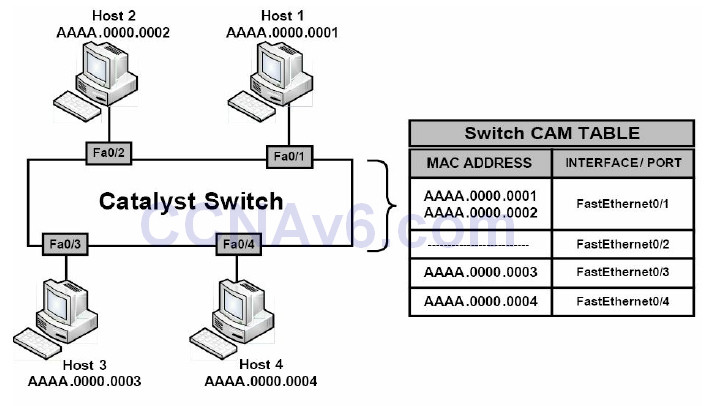
Figure 4.4 – MAC Address Spoofing
Referencing Figure 4.4, when Host 3 or Host 4 attempts to send frames to Host 2, the switch will forward them out of FastEthernet0/1 to Host 1 because the CAM table has been poisoned by a MAC spoofing attack. When Host 2 sends another frame, the switch relearns its MAC address from FastEthernet0/2 and rewrites the CAM table entry once again to reflect this change. The result is a tug-of-war between Host 2 and Host 1 as to which host owns this MAC address.
In addition, this confuses the switch and causes repetitive rewrites of MAC address table entries, causing a Denial of Service (DoS) attack on the legitimate host (i.e., Host 2). If the number of spoofed MAC addresses used is high, this attack could have serious performance consequences for the switch that is constantly rewriting its CAM table. MAC address spoofing attacks can be mitigated by implementing port security.
Port Security Secure Addresses
The port security feature can be used to specify which specific MAC address is permitted access to a switch port, as well as to limit the number of MAC addresses that can be supported on a single switch port. The methods of port security implementation described in this section are as follows:
• Static secure MAC addresses
• Dynamic secure MAC addresses
• Sticky secure MAC addresses
Static secure MAC addresses are statically configured by network administrators and are stored in the MAC address table, as well as in the switch configuration. When static secure MAC addresses are assigned to a secure port, the switch will not forward frames that do not have a source MAC address that matches the configured static secure MAC address or addresses.
Dynamic secure MAC addresses are dynamically learned by the switch and are stored in the MAC address table. However, unlike static secure MAC addresses, dynamic secure MAC address entries are removed from the switch when the switch is reloaded or powered down. These addresses must then be relearned by the switch when it boots up again.
Sticky secure MAC addresses are a mix of static secure MAC addresses and dynamic secure MAC addresses. These addresses can be learned dynamically or configured statically and are stored in the MAC address table, as well as in the switch running configuration. This means that when the switch is powered down or rebooted, it will not need to dynamically discover the MAC addresses again because they are already saved in the configuration file (if you save the running configuration).
Port Security Actions
Once port security has been enabled, administrators can define the actions the switch will take in the event of a port security violation. Cisco IOS software allows administrators to specify four different actions to take when a violation occurs, as follows:
• Protect
• Shutdown (default)
• Restrict
• Shutdown VLAN (outside of the CCNA syllabus)
The protect option forces the port into Protected Port mode. In this mode, the switch will simply discard all Unicast or Multicast frames with unknown source MAC addresses. When the switch is configured to protect a port, it will not send out a notification when operating in Protected Port mode, meaning that administrators would never know when any traffic was prevented by the switch port operating in this mode.
The shutdown option places a port in an err-disabled state when a port security violation occurs. The corresponding port LED on the switch is also turned off when this configured action mode is used. In Shutdown mode, the switch sends out an SNMP trap and a syslog message, and the violation counter is incremented. This is the default action taken when port security is enabled on an interface.
The restrict option is used to drop packets with unknown MAC addresses when the number of secure MAC addresses reaches the administrator-defined maximum limit for the port. In this mode, the switch will continue to restrict additional MAC addresses from sending frames until a sufficient number of secure MAC addresses is removed, or the number of maximum allowable addresses is increased. As is the case with the shutdown option, the switch sends out an SNMP trap and a syslog message, and the violation counter is incremented.
The shutdown VLAN option is similar to the shutdown option; however, this option shuts down a VLAN instead of the entire switch port. This configuration could be applied to ports that have more than one single VLAN assigned to them, such as a voice VLAN and a data VLAN, as well asto trunk links on the switches.
Configuring Port Security
Before configuring port security, it is recommended that the switch port be statically configured as a Layer 2 access port (it can only be configured on static access or trunk ports, not on dynamic ports). This configuration is illustrated in the following output:
VTP-Server-1(config)#interface FastEthernet0/1 VTP-Server-1(config-if)#switchport VTP-Server-1(config-if)#switchport mode access
NOTE: The switchport command is not required in Layer 2-only switches, such as the Catalyst 2950 and Catalyst 2960 series switches. However, it must be used on Multilayer switches, such as the Catalyst 3750, Catalyst 4500, and Catalyst 6500 series switches.
By default, port security is disabled; however, this feature can be enabled using the
switchportport-security [mac-address {mac-address} [vlan {vlan-id | {access | voice}}] | macaddress
{sticky} [mac-address | vlan {vlan-id | {access | voice}}] [maximum {value} [vlan
{vlan-list | {access | voice}}]]
interface configuration command. The options that areavailable with this command are described below in Table 4.1:
Table 4.1 – Port Security Configuration Keywords
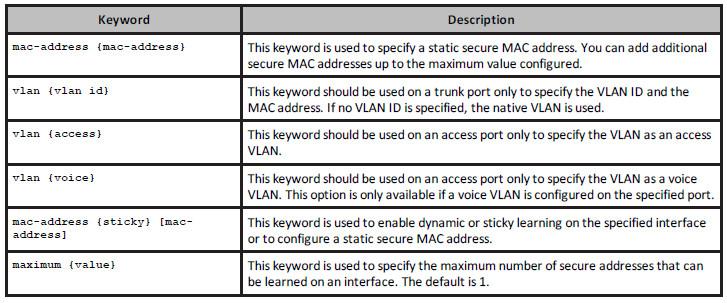
Configuring Static Secure MAC Addresses
The following output illustrates how to enable port security on an interface and to configure a static secure MAC address of 001f:3c59:d63b on a switch access port:
VTP-Server-1(config)#interface GigabitEthernet0/2 VTP-Server-1(config-if)#switchport VTP-Server-1(config-if)#switchport mode access VTP-Server-1(config-if)#switchport port-security VTP-Server-1(config-if)#switchport port-security mac-address 001f.3c59.d63b
The following output illustrates how to enable port security on an interface and to configure a static secure MAC address of 001f:3c59:d63b in VLAN 5 on a switch trunk port:
VTP-Server-1(config)#interface GigabitEthernet0/2 VTP-Server-1(config-if)#switchport VTP-Server-1(config-if)#switchport trunk encapsulation dot1q VTP-Server-1(config-if)#switchport mode trunk VTP-Server-1(config-if)#switchport port-security VTP-Server-1(config-if)#switchport port-security mac-address 001f.3c59.d63b vlan 5
The following output illustrates how to enable port security on an interface and to configure a static secure MAC address of 001f:3c59:5555 for VLAN 5 (the data VLAN) and a static secure MAC address of 001f:3c59:7777 for VLAN 7 (the voice VLAN) on a switch access port:
VTP-Server-1(config)#interface GigabitEthernet0/2 VTP-Server-1(config-if)#switchport VTP-Server-1(config-if)#switchport mode access VTP-Server-1(config-if)#switchport access vlan 5 VTP-Server-1(config-if)#switchport voice vlan 7 VTP-Server-1(config-if)#switchport port-security VTP-Server-1(config-if)#switchport port-security maximum 2 VTP-Server-1(config-if)#switchport port-security mac-address 001f.3c59.5555 vlan access VTP-Server-1(config-if)#switchport port-security mac-address 001f.3c59.7777 vlan voice
It is very important to remember that when enabling port security on an interface that is also configured with a voice VLAN in conjunction with the data VLAN, the maximum allowed secure addresses on the port should be set to 2. This is performed via the switchport port-security maximum 2 interface configuration command, which is included in the output above.
One of the two MAC addresses is used by the IP phone and the switch learns about this address on the voice VLAN. The other MAC address is used by a host (such as a PC) that may be connected to the IP phone. This MAC address will be learned by the switch on the data VLAN.
Verifying Static Secure MAC Address Configuration
Global port security configuration parameters can be validated by issuing the show portsecurity command. The following shows the output printed by this command based on default values:
VTP-Server-1#show port-security Secure Port MaxSecureAddr CurrentAddr SecurityViolation Security Action (Count) (Count) (Count) ------------------------------------------------------- Gi0/2 1 1 0 Shutdown ------------------------------------------------------------------ Total Addresses in System : 1 Max Addresses limit in System : 1024
As seen in the output above, by default, only a single secure MAC address is permitted per port. In addition, the default action in the event of a violation is to shut down the port. The text in bold indicates that only a single secured address is known, which is the static address configured on the interface. The same can also be confirmed by issuing the show port-security interface [name] command, as illustrated in the following output:
VTP-Server-1#show port-security interface gi0/2 Port Security : Enabled Port status : SecureUp Violation mode : Shutdown Maximum MAC Addresses : 1 Total MAC Addresses : 1 Configured MAC Addresses : 1 Sticky MAC Addresses : 0 Aging time : 0 mins Aging type : Absolute SecureStatic address aging : Disabled Security Violation count : 0
NOTE: The modification of the other default parameters in the output above will be described in detail as we progress through this section.
To see the actual configured static secure MAC address on the port, the show port-security address or the show running-config interface [name] command must be used. The following output illustrates the show port-security address command:
VTP-Server-1#show port-security address
Secure Mac Address Table
------------------------------------------------------------------
Vlan Mac Address Type Ports Remaining Age
(mins)
---- ----------- ---- ----- -----------
1 001f.3c59.d63b SecureConfigured Gi0/2
--------------------------------------------------------------------
Total Addresses in System : 1
Max Addresses limit in System : 1024
Configuring Dynamic Secure MAC Addresses
By default, when port security is enabled on a port, the port will dynamically learn and secure one MAC address without any further configuration from the administrator. To allow the port to learn and secure more than a single MAC address, the switchport port-security maximum [number] command must be used. Keep in mind that the [number] keyword is platformdependent and will vary on different Cisco Catalyst switch models.
Real-World Implementation
In production networks with Cisco Catalyst 3750 switches, it is always a good idea to determine what the switch will be used for, and then select the appropriate Switch Database Management (SDM) template via the sdm prefer {access | default | dual-ipv4-and-ipv6 {default | routing | vlan} | routing | vlan} [desktop] global configuration command.
Each template allocates system resources to best support the features being used or that will be used. By default, the switch attempts to provide a balance between all features. However, this may impose a limit on the maximum possible values for other available features and functions. An example would be the maximum possible number of secure MAC addresses that can be learned or configured when using port security.
The following output illustrates how to configure a switch port to dynamically learn and secure up to two MAC addresses on interface GigabitEthernet0/2:
VTP-Server-1(config)#interface GigabitEthernet0/2 VTP-Server-1(config-if)#switchport VTP-Server-1(config-if)#switchport mode access VTP-Server-1(config-if)#switchport port-security VTP-Server-1(config-if)#switchport port-security maximum 2
Verifying Dynamic Secure MAC Addresses
Dynamic secure MAC address configuration can be verified using the same commands as those illustrated in the static secure address configuration examples, with the exception of the show running-config command. This is because, unlike static or sticky secure MAC addresses, all dynamically learned addresses are not saved in the switch configuration and are removed if the port is shut down. These same addresses must then be relearned when the port comes back up. The following output illustrates the show port-security address command, which shows an interface configured for secure dynamic MAC address learning:
VTP-Server-1#show port-security address
Secure Mac Address Table
------------------------------------------------------------------
Vlan Mac Address Type Ports Remaining Age
(mins)
---- ----------- ---- ----- ------------
1 001d.09d4.0238 SecureDynamic Gi0/2 -
1 001f.3c59.d63b SecureDynamic Gi0/2 -
------------------------------------------------------------------
Total Addresses in System : 2
Max Addresses limit in System : 1024
Configuring Sticky Secure MAC Addresses
The following output illustrates how to configure dynamic sticky learning on a port and restrict the port to dynamically learn up to a maximum of 10 MAC addresses:
VTP-Server-1(config)#interface GigabitEthernet0/2 VTP-Server-1(config-if)#switchport VTP-Server-1(config-if)#switchport mode access VTP-Server-1(config-if)#switchport port-security VTP-Server-1(config-if)#switchport port-security mac-address sticky VTP-Server-1(config-if)#switchport port-security maximum 10
Based on the configuration above, by default, up to 10 addresses will be dynamically learned on interface GigabitEthernet0/2 and will be added to the current switch configuration. When sticky address learning is enabled, MAC addresses learned on each port are automatically saved to the current switch configuration and added to the address table. The following output shows the dynamically learned MAC addresses (in bold font) on interface GigabitEthernet0/2:
VTP-Server-1#show running-config interface GigabitEthernet0/2 Building configuration... Current configuration : 550 bytes ! interface GigabitEthernet0/2 switchport switchport mode access switchport port-security switchport port-security maximum 10 switchport port-security mac-address sticky switchport port-security mac-address sticky 0004.c16f.8741 switchport port-security mac-address sticky 000c.cea7.f3a0 switchport port-security mac-address sticky 0013.1986.0a20 switchport port-security mac-address sticky 001d.09d4.0238 switchport port-security mac-address sticky 0030.803f.ea81 ...
The MAC addresses in bold text in the output above are dynamically learned and added to the current configuration. No manual administrator configuration is required to add these addresses to the configuration. By default, sticky secure MAC addresses are not automatically added to the startup configuration (NVRAM). To ensure that this information is saved to NVRAM, which means that these addresses are not relearned when the switch is restarted, it is important to remember to issue the copy running-config startup-config command, or the copy system:running-config nvram:startup-config command, depending upon the IOS version of the switch on which this feature is implemented. The following output illustrates the show port-security address command on a port configured for sticky address learning:
VTP-Server-1#show port-security address
Secure Mac Address Table
------------------------------------------------------------------
Vlan Mac Address Type Ports Remaining Age
(mins)
---- ----------- ---- ----- ------------
1 0004.c16f.8741 SecureSticky Gi0/2 -
1 000c.cea7.f3a0 SecureSticky Gi0/2 -
1 0013.1986.0a20 SecureSticky Gi0/2 -
1 001d.09d4.0238 SecureSticky Gi0/2 -
1 0030.803f.ea81 SecureSticky Gi0/2 -
-------------------------------------------------------------------
Total Addresses in System : 5
Max Addresses limit in System : 1024
You can also set an aging time and type on the switch, but this is going beyond the CCNA-level requirements. (Have a try on your own time if you wish.)
Configuring the Port Security Violation Action
As stated earlier, Cisco IOS software allows administrators to specify four different actions to take when a violation occurs, as follows:
• Protect
• Shutdown (default)
• Restrict
• Shutdown VLAN (this is outside the CCNA syllabus)
These options are configured using the switchport port-security [violation {protect | restrict | shutdown | shutdown vlan}] interface configuration command. If a port is shut down due to a security violation, it will show as errdisabled, and the shutdown and then no shutdown command will need to be applied to bring it back up.
Switch#show interfaces FastEthernet0/1 status Port Name Status Vlan Duplex Speed Type Fa0/1 errdisabled 100 full 100 100BaseSX
Cisco do want you to know which violation action triggers an SNMP message for the network
administrator and a logging message, so here is that information for you in Table 4.2 below:
Table 4.2 – Port Security Violation Actions
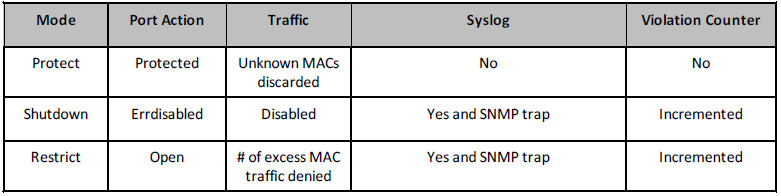
Make sure that you memorise the table above for the exam!
The following output illustrates how to enable sticky learning on a port for a maximum of 10 MAC addresses. In the event that an unknown MAC address (e.g., an eleventh MAC address) is detected on the port, the port will be configured to drop the received frames:
VTP-Server-1(config)#interface GigabitEthernet0/2 VTP-Server-1(config-if)#switchport port-security VTP-Server-1(config-if)#switchport port-security mac-address sticky VTP-Server-1(config-if)#switchport port-security maximum 10 VTP-Server-1(config-if)#switchport port-security violation restrict
Verifying the Port Security Violation Action
The configured port security violation action is validated via the show port-security command, as shown in the following output:
VTP-Server-1#show port-security Secure Port MaxSecureAddr CurrentAddr SecurityViolation Security Action (Count) (Count) (Count) Gi0/2 10 5 0 Restrict Total Addresses in System : 5 Max Addresses limit in System : 1024
If logging is enabled and either the Restrict mode or the Shutdown Violation mode is configured on the switch, messages similar to those shown in the following output will be printed on the switch console, logged into the local buffer, or sent to a syslog server:
VTP-Server-1#show logging ... [Truncated Output] ... 04:23:21: %PORT_SECURITY-2-PSECURE_VIOLATION: Security violation occurred, caused by MAC address 0013.1986.0a20 on port Gi0/2. 04:23:31: %PORT_SECURITY-2-PSECURE_VIOLATION: Security violation occurred, caused by MAC address 000c.cea7.f3a0 on port Gi0/2. 04:23:46: %PORT_SECURITY-2-PSECURE_VIOLATION: Security violation occurred, caused by MAC address 0004.c16f.8741 on port Gi0/2.
One final point is that switch security can be configured on Packet Tracer, but many of the commands and show commands don’t work.
Section 4 Questions
1. Write out the two ways of configuring console passwords. Write the actual commands.
2. Which command will permit only SSH traffic into the VTY lines?
3. Which command will encrypt a password with level 7 encryption?
4. Name the eight levels of logging available on the router.
5. Why would you choose SSH access over Telnet?
6. Your three options upon violation of your port security are protect, _______, and _______.
7. How would you hard set a port to accept only MAC 0001.c74a.0a01?
8. Which command turns off CDP for a particular interface?
9. Which command turns off CDP for the entire router or switch?
10. Which command adds a password to your VTP domain?
11. Which command would permit only VLANs 10 to 20 over your interface?
Section 4 Answers
1. The password xxx and login local commands (username and password previously configured).
2. The transport input ssh command.
3. The service password-encryption command.
4. Alerts, critical, debugging, emergencies, errors, informational, notifications, and warnings.
5. SSH offers secure, encrypted traffic.
6. Shutdown and restrict.
7. Issue the switchport port-security mac-address x.x.x.x command.
8. The no cdp enable command.
9. The no cdp run command.
10. The vtp password xxx command.
11. The switchport trunk allowed vlan 10-20 command.
Section 4 Labs
Basic Router Security Lab
Topology
Purpose
Learn some basic steps to take to lock down your router.
Walkthrough
1. Log in using Protect Enable mode with an enable secret password. Test this by logging out of Privileged mode and then logging back in.
Router#conf t Enter configuration commands, one per line. End with CNTL/Z. Router(config)#enable secret cisco Router(config)#exit Router# %SYS-5-CONFIG_I: Configured from console by console Router#exi Router con0 is now available Press RETURN to get started. Router>en Password: Router#
2. Set an enable password and then add service password encryption. This is rarely done on live routers because it is not secure.
Router(config)#no enable secret Router(config)#enable password cisco Router(config)#service pass Router(config)#service password-encryption Router(config)#exit Router# %SYS-5-CONFIG_I: Configured from console by console Router#show run Building configuration... Current configuration: 480 bytes ! version 12.4 no service timestamps log datetime msec no service timestamps debug datetime msec service password-encryption ! hostname Router ! enable password 7 0822455D0A16
3. Protect the Telnet lines. Set a local username and password and have users enter this when connecting to the router.
Router(config)#line vty 0 ? <1-15> Last Line number <cr> Router(config)#line vty 0 15 Router(config-line)#login local Router(config-line)#exit Router(config)#username in60days password cisco Router(config)#
You have tested Telnet before, but feel free to add a PC and Telnet into the router so you are prompted for a username and password.
4. Protect the console port with a password. Set one directly on the console port.
Router(config)#line console 0 Router(config-line)#password cisco
You can test this by unplugging and plugging your console lead back into the router. You can also protect the auxiliary port on your router if you have one:
Router(config)#line aux 0 Router(config-line)#password cisco
5. Protect the Telnet lines by permitting only SSH traffic in. You can also permit only SSH traffic outbound. You will need a security image for this command to work.
Router(config)#line vty 0 15 Router(config-line)#transport input ssh Router(config-line)#transport output ssh
6. Add a banner message of the day (MOTD). Set the character which tells the router you have finished your message as “X” (the delimiting character).
Router(config)#banner motd X Enter TEXT message. End with the character ‘X’. Do not use this router without authorization. X Router(config)# Router(config)#exit Router# %SYS-5-CONFIG_I: Configured from console by console Exit Router con0 is now available Press RETURN to get started. Do not use this router without authorization. Router>
7. Turn off CDP on the entire router. You could disable it on an interface only with the no cdp enable interface command.
Router(config)#no cdp run
You can test whether this is working by connecting a switch or router to your router before you turn off CDP and issuing the show cdp neighbor (detail) command.
8. Set the router to send logging messages to a host on the network.
Router#conf t Enter configuration commands, one per line. End with CNTL/Z. Router(config)#logging ? A.B.C.D IP address of the logging host buffered Set buffered logging parameters console Set console logging parameters host Set syslog server IP address and parameters on Enable logging to all enabled destinations trap Set syslog server logging level userinfo Enable logging of user info on privileged mode enabling Router(config)#logging 10.1.1.1
Basic Switch Security Lab
Topology

Please note that your switch will need to have a security image which permits basic security settings.
Purpose
Learn how to apply basic security settings to a Cisco switch.
Walkthrough
1. Connect a PC or laptop to your switch. In addition, set up a console connection for your configuration. The port to which you connect your PC will be the one you configure security settings on in this lab. I have chosen FastEthernet 0/1 on my switch.
2. Log in to the VTY lines and set up Telnet access referring to a local username and password.
Switch#conf t Enter configuration commands, one per line. End with CNTL/Z. Switch(config)#line vty 0 ? <1-15> Last Line number <cr> Switch(config)#line vty 0 15 Switch(config-line)#? Switch(config-line)#login local Switch(config-line)#exit Switch(config)#username in60days password cisco Switch(config)#
3. Add an IP address to VLAN 1 on the switch (all ports are in VLAN 1 automatically). Additionally, add the IP address 192.168.1.1 to your PC’s FastEthernet interface.
Switch(config)#interface vlan1 Switch(config-if)#ip address 192.168.1.2 255.255.255.0 Switch(config-if)#no shut %LINK-5-CHANGED: Interface Vlan1, changed state to up %LINEPROTO-5-UPDOWN: Line protocol on Interface Vlan2, changed state to up Switch(config-if)#^Z ← press Ctrl+Z keys Switch# Switch#ping 192.168.1.1 ← test connection from switch to PC Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.1.1, timeout is 2 seconds: .!!!! Success rate is 80 percent (4/5), round-trip min/avg/max = 31/31/32 ms Switch#
4. Test Telnet by Telnetting from your PC to your switch.
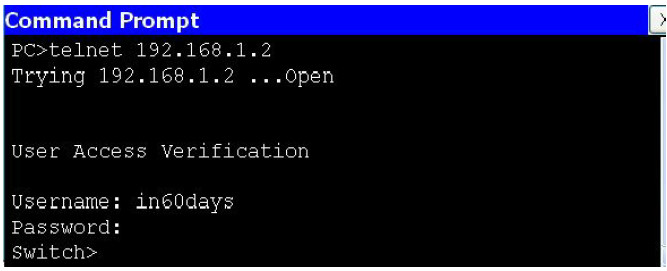
5. Your IT manager changes his mind and wants only SSH access, so change this on your VTY lines. Only certain models and IOS versions will support the SSH command.
Switch(config)#line vty 0 15 Switch(config-line)#transport input ssh
6. Now Telnet from your PC to the switch. Because only SSH is permitted, the connection should fail.
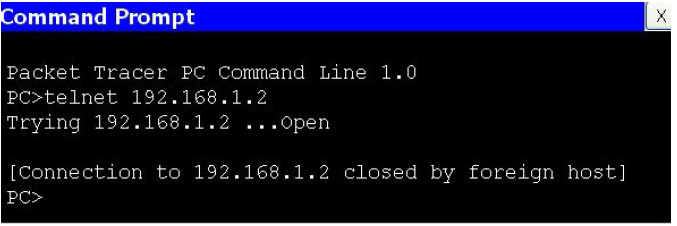
7. Set port security on your switch for the FastEthernet port. It will fail if you have not hard set the port to access (as opposed to dynamic or trunk).
Switch(config)#interface FastEthernet0/1 Switch(config-if)#switchport port-security Command rejected: FastEthernet0/1 is a dynamic port. Switch(config-if)#switchport mode access Switch(config-if)#switchport port-security Switch(config-if)#
8. Hard set the MAC address from your PC to be permitted on this port. You can check this with the ipconfig/all command on your PC command line. Then check the port security status and settings.
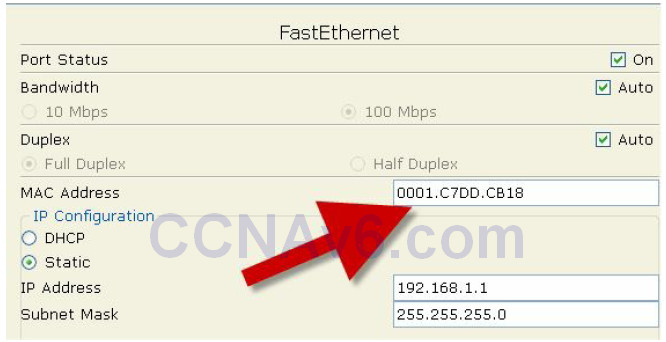
Switch(config-if)#switchport port-security mac-address 0001.C7DD.CB18 Switch(config-if)#^Z Switch#show port-security int FastEthernet0/1 Port Security : Enabled Port Status : Secure-up Violation Mode : Shutdown Aging Time : 0 mins Aging Type : Absolute SecureStatic Address Aging : Disabled Maximum MAC Addresses : 1 Total MAC Addresses : 1 Configured MAC Addresses : 0 Sticky MAC Addresses : 0 Last Source Address:Vlan : 0001.C7DD.CB18:1 Security Violation Count : 0
9. Change the MAC address on your PC, or if you can’t do this, plug another device into the switch port. This should make the port shut down due to a breach in the security settings. The screenshot below shows where you would change the MAC address in Packet Tracer.
10. You should see your FastEthernet port go down immediately.
Switch# %LINK-5-CHANGED: Interface FastEthernet0/1, changed state to administratively down %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/1, changed state to down %LINEPROTO-5-UPDOWN: Line protocol on Interface Vlan1, changed state to down Switch# %SYS-5-CONFIG_I: Configured from console by console Switch#show port-security interface FastEthernet0/1 Port Security : Enabled Port Status : Secure-shutdown Violation Mode : Shutdown Aging Time : 0 mins Aging Type : Absolute SecureStatic Address Aging : Disabled Maximum MAC Addresses : 1 Total MAC Addresses : 0 Configured MAC Addresses : 0 Sticky MAC Addresses : 0 Last Source Address:Vlan : 0001.C7DD.CB19:1 Security Violation Count : 1
NOTE: Please repeat this lab until you understand the commands and can type them without looking at the Walkthrough section (and do the same for all the other labs in this book).
