7.4.1.1 FTP Denied (Instructor Version – Optional Lab)
Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or to provide additional practice.
Objective
Implement packet filtering using extended IPv4 ACLs according to networking requirements (to include named and numbered ACLs).
Students will use Packet Tracer to write and apply an ACL to deny a particular host from accessing the FTP process on their small- to medium-size business network.
Scenario
It was recently reported that viruses are on the rise within your small- to medium-sized business network. Your network administrator has been tracking network performance and has determined that one particular host is constantly downloading files from a remote FTP server. This host just may be the virus source perpetuating throughout the network!
Use Packet Tracer to complete this activity. Write a named ACL to deny the host access to the FTP server. Apply the ACL to the most effective interface on the router.
To complete the physical topology, you must use:
- One PC host station
- Two switches
- One Cisco 1941 series Integrated Services Router
- One server
Using the Packet Tracer text tool, record the ACL you prepared. Validate that the ACL works to deny access to the FTP server by trying to access the FTP server’s address. Observe what happens while in simulation mode.
Save your file and be prepared to share it with another student, or with the entire class. (Instructor choice)
Reflection
1. What was the most difficult part of completing this modeling activity?
__________________________________________________
Answers will vary – writing the ACL, naming it, applying it, changing it, etc.
2. How often do you think network administrators need to change their ACLs on their networks?
__________________________________________________
ACLs are implemented to address security issues, regulate network traffic, and provide stability to the operation of a network. Therefore, any time network performance, security and stability degrade, ACLs should be considered as one way to mitigate those network challenges.
3. Why would you consider using a named extended ACL instead of a regular extended ACL?
__________________________________________________
Named ACLs are easy to correct or change – you can edit the ACL statements by line and use the “no…” command. This saves time in having to rewrite and reapply an entire ACL to a network.
Packet Tracer Example (topology, ACL names and IP addresses will vary)
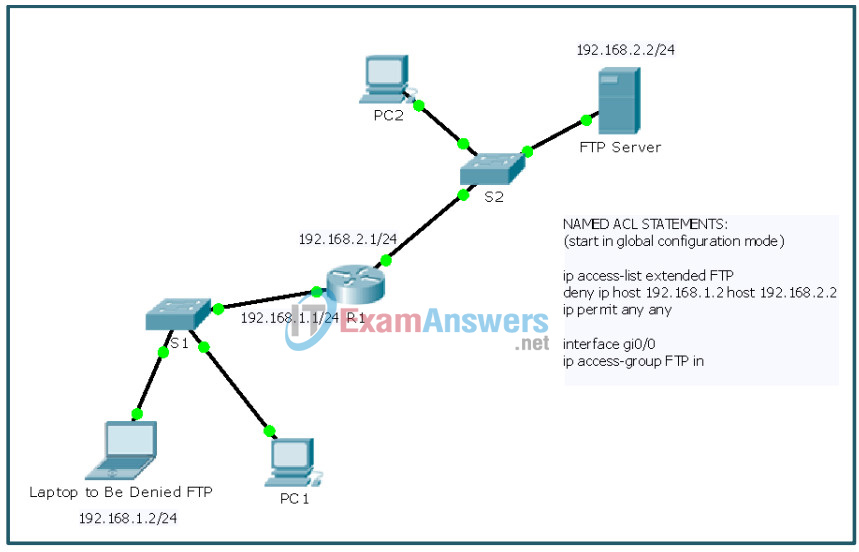
Instructor Note: Identify elements of the model that map to IT-related content:
- ACLs are processes that determine whether to permit or deny network traffic.
- Criteria must be established in advance of permitting or denying network traffic.
- The order of importance must be established when developing criteria for permitting or denying network participation.
- A named ACL saves time vs. using a regular extended or standard ACL if when corrections must be made to the configuration of the ACL or to its placement.
- ACLs must be tested for the validity of their operation, as an ACL may need to be rewritten and/or reapplied correctly if it does not work correctly.
