Time limit: 0
Quiz-summary
0 of 129 questions completed
Questions:
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
- 97
- 98
- 99
- 100
- 101
- 102
- 103
- 104
- 105
- 106
- 107
- 108
- 109
- 110
- 111
- 112
- 113
- 114
- 115
- 116
- 117
- 118
- 119
- 120
- 121
- 122
- 123
- 124
- 125
- 126
- 127
- 128
- 129
Information
Good Luck For You!
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading...
You must sign in or sign up to start the quiz.
You have to finish following quiz, to start this quiz:
Results
0 of 129 questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 points, (0)
| Average score |
|
| Your score |
|
Categories
- Not categorized 0%
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
- 97
- 98
- 99
- 100
- 101
- 102
- 103
- 104
- 105
- 106
- 107
- 108
- 109
- 110
- 111
- 112
- 113
- 114
- 115
- 116
- 117
- 118
- 119
- 120
- 121
- 122
- 123
- 124
- 125
- 126
- 127
- 128
- 129
- Answered
- Review
-
Question 1 of 129
1. Question
1 pointsWhat is a characteristic of a fault tolerant network?Correct
Incorrect
-
Question 2 of 129
2. Question
1 pointsThree bank employees are using the corporate network. The first employee uses a web browser to view a company web page in order to read some announcements. The second employee accesses the corporate database to perform some financial transactions. The third employee participates in an important live audio conference with other corporate managers in branch offices. If QoS is implemented on this network, what will be the priorities from highest to lowest of the different data types?Correct
Incorrect
-
Question 3 of 129
3. Question
1 pointsWhat is a benefit of using cloud computing in networking?Correct
Incorrect
-
Question 4 of 129
4. Question
1 pointsWhat is the function of the shell in an OS?Correct
Incorrect
-
Question 5 of 129
5. Question
1 pointsWhich connection provides a secure CLI session with encryption to a Cisco switch?Correct
Incorrect
-
Question 6 of 129
6. Question
1 pointsA network technician is attempting to configure an interface by entering the following command: SanJose(config)# ip address 192.168.2.1 255.255.255.0. The command is rejected by the device. What is the reason for this?Correct
Incorrect
-
Question 7 of 129
7. Question
1 pointsAn administrator uses the Ctrl-Shift-6 key combination on a switch after issuing the ping command. What is the purpose of using these keystrokes?Correct
Incorrect
-
Question 8 of 129
8. Question
1 pointsRefer to the exhibit. A network administrator is configuring access control to switch SW1. If the administrator uses a console connection to connect to the switch, which password is needed to access user EXEC mode?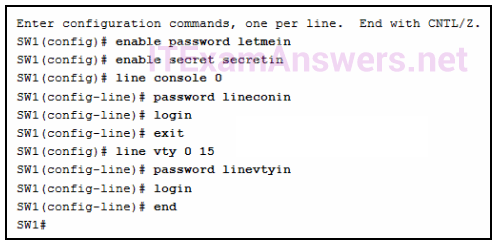 Correct
Correct
Incorrect
-
Question 9 of 129
9. Question
1 pointsOn which switch interface would an administrator configure an IP address so that the switch can be managed remotely?Correct
Incorrect
-
Question 10 of 129
10. Question
1 pointsWhat protocol is responsible for controlling the size of segments and the rate at which segments are exchanged between a web client and a web server?Correct
Incorrect
-
Question 11 of 129
11. Question
1 pointsWhat is an advantage to using a protocol that is defined by an open standard?Correct
Incorrect
-
Question 12 of 129
12. Question
1 pointsWhat are two benefits of using a layered network model? (Choose two.)Correct
Incorrect
-
Question 13 of 129
13. Question
1 pointsWhich two OSI model layers have the same functionality as two layers of the TCP/IP model? (Choose two.)Correct
Incorrect
-
Question 14 of 129
14. Question
1 pointsWhich name is assigned to the transport layer PDU?Correct
Incorrect
-
Question 15 of 129
15. Question
1 pointsA network engineer is measuring the transfer of bits across the company backbone for a mission critical database application. The engineer notices that the network throughput appears lower than the bandwidth expected. Which three factors could influence the differences in throughput? (Choose three.)Correct
Incorrect
-
Question 16 of 129
16. Question
1 pointsA network administrator is troubleshooting connectivity issues on a server. Using a tester, the administrator notices that the signals generated by the server NIC are distorted and not usable. In which layer of the OSI model is the error categorized?Correct
Incorrect
-
Question 17 of 129
17. Question
1 pointsWhich type of UTP cable is used to connect a PC to a switch port?Correct
Incorrect
-
Question 18 of 129
18. Question
1 pointsA network administrator is measuring the transfer of bits across the company backbone for a mission critical financial application. The administrator notices that the network throughput appears lower than the bandwidth expected. Which three factors could influence the differences in throughput? (Choose three.)Correct
Incorrect
-
Question 19 of 129
19. Question
1 pointsWhat is a characteristic of UTP cabling?Correct
Incorrect
-
Question 20 of 129
20. Question
1 pointsWhat are two characteristics of fiber-optic cable? (Choose two.)Correct
Incorrect
-
Question 21 of 129
21. Question
1 pointsWhat is a characteristic of the LLC sublayer?Correct
Incorrect
-
Question 22 of 129
22. Question
1 pointsA network team is comparing physical WAN topologies for connecting remote sites to a headquarters building. Which topology provides high availability and connects some, but not all, remote sites?Correct
Incorrect
-
Question 23 of 129
23. Question
1 pointsWhat method is used to manage contention-based access on a wireless network?Correct
Incorrect
-
Question 24 of 129
24. Question
1 pointsWhat are the three primary functions provided by Layer 2 data encapsulation? (Choose three.)Correct
Incorrect
-
Question 25 of 129
25. Question
1 pointsWhat will a host on an Ethernet network do if it receives a frame with a destination MAC address that does not match its own MAC address?Correct
Incorrect
-
Question 26 of 129
26. Question
1 pointsWhat are two examples of the cut-through switching method? (Choose two.)Correct
Incorrect
-
Question 27 of 129
27. Question
1 pointsWhat are two actions performed by a Cisco switch? (Choose two.)Correct
Incorrect
-
Question 28 of 129
28. Question
1 pointsWhich frame forwarding method receives the entire frame and performs a CRC check to detect errors before forwarding the frame?Correct
Incorrect
-
Question 29 of 129
29. Question
1 pointsRefer to the exhibit. If host A sends an IP packet to host B, what will the destination address be in the frame when it leaves host A?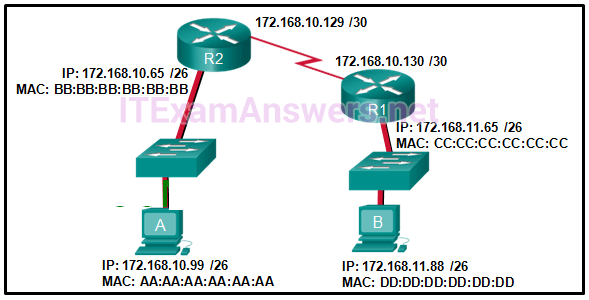 Correct
Correct
Incorrect
-
Question 30 of 129
30. Question
1 pointsWhat addresses are mapped by ARP?Correct
Incorrect
-
Question 31 of 129
31. Question
1 pointsWhat information is added during encapsulation at OSI Layer 3?Correct
Incorrect
-
Question 32 of 129
32. Question
1 pointsWhat are two services provided by the OSI network layer? (Choose two.)Correct
Incorrect
-
Question 33 of 129
33. Question
1 pointsRefer to the exhibit. The network administrator for a small advertising company has chosen to use the 192.168.5.96/27 network for internal LAN addressing. As shown in the exhibit, a static IP address is assigned to the company web server. However, the web server cannot access the Internet. The administrator verifies that local workstations with IP addresses that are assigned by a DHCP server can access the Internet, and the web server is able to ping local workstations. Which component is incorrectly configured?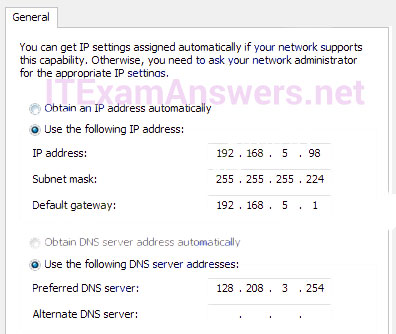 Correct
Correct
Incorrect
-
Question 34 of 129
34. Question
1 pointsWhy does a Layer 3 device perform the ANDing process on a destination IP address and subnet mask?Correct
Incorrect
-
Question 35 of 129
35. Question
1 pointsWhat are two functions of NVRAM? (Choose two.)Correct
Incorrect
-
Question 36 of 129
36. Question
1 pointsRefer to the exhibit. What will be the result of entering this configuration the next time a network administrator connects a console cable to the router and no additional commands have been entered?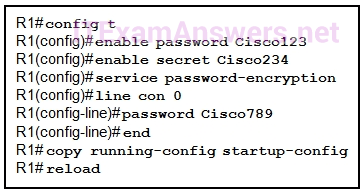 Correct
Correct
Incorrect
-
Question 37 of 129
37. Question
1 pointsWhat is the dotted decimal representation of the IPv4 address 11001011.00000000.01110001.11010011?Correct
Incorrect
-
Question 38 of 129
38. Question
1 pointsWhat are three characteristics of multicast transmission? (Choose three.)Correct
Incorrect
-
Question 39 of 129
39. Question
1 pointsWhat are the three ranges of IP addresses that are reserved for internal private use? (Choose three.)Correct
Incorrect
-
Question 40 of 129
40. Question
1 pointsWhat purpose does NAT64 serve in IPv6?Correct
Incorrect
-
Question 41 of 129
41. Question
1 pointsWhat is the most compressed representation of the IPv6 address 2001:0000:0000:abcd:0000:0000:0000:0001?Correct
Incorrect
-
Question 42 of 129
42. Question
1 pointsWhich range of link-local addresses can be assigned to an IPv6-enabled interface?Correct
Incorrect
-
Question 43 of 129
43. Question
1 pointsWhich three addresses are valid public addresses? (Choose three.)Correct
Incorrect
-
Question 44 of 129
44. Question
1 pointsRefer to the exhibit. On the basis of the output, which two statements about network connectivity are correct? (Choose two.)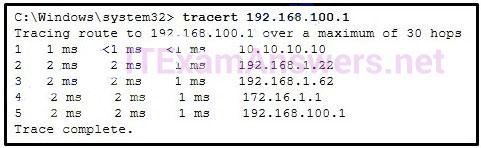 Correct
Correct
Incorrect
-
Question 45 of 129
45. Question
1 pointsWhat type of IPv6 address is FE80::1?Correct
Incorrect
-
Question 46 of 129
46. Question
1 pointsHow many valid host addresses are available on an IPv4 subnet that is configured with a /26 mask?Correct
Incorrect
-
Question 47 of 129
47. Question
1 pointsA site administrator has been told that a particular network at the site must accommodate 126 hosts. Which subnet mask would be used that contains the required number of host bits?Correct
Incorrect
-
Question 48 of 129
48. Question
1 pointsA network administrator wants to have the same subnet mask for three subnetworks at a small site. The site has the following networks and numbers of devices: Subnetwork A: IP phones – 10 addresses Subnetwork B: PCs – 8 addresses Subnetwork C: Printers – 2 addresses What single subnet mask would be appropriate to use for the three subnetworks?Correct
Incorrect
-
Question 49 of 129
49. Question
1 pointsHow many hosts are addressable on a network that has a mask of 255.255.255.248?Correct
Incorrect
-
Question 50 of 129
50. Question
1 pointsWhich subnet would include the address 192.168.1.96 as a usable host address?Correct
Incorrect
-
Question 51 of 129
51. Question
1 pointsWhat subnet mask is needed if an IPv4 network has 40 devices that need IP addresses and address space is not to be wasted?Correct
Incorrect
-
Question 52 of 129
52. Question
1 pointsWhat are two characteristics shared by TCP and UDP? (Choose two.)Correct
Incorrect
-
Question 53 of 129
53. Question
1 pointsWhy are port numbers included in the TCP header of a segment?Correct
Incorrect
-
Question 54 of 129
54. Question
1 pointsRefer to the exhibit. Consider the IP address of 192.168.10.0/24 that has been assigned to a high school building. The largest network in this building has 100 devices. If 192.168.10.0 is the network number for the largest network, what would be the network number for the next largest network, which has 40 devices?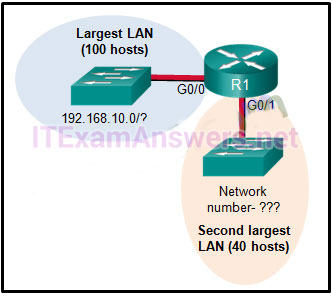 Correct
Correct
Incorrect
-
Question 55 of 129
55. Question
1 pointsWhich statement is true about variable-length subnet masking?Correct
Incorrect
-
Question 56 of 129
56. Question
1 pointsIn what two situations would UDP be the preferred transport protocol over TCP? (Choose two.)Correct
Incorrect
-
Question 57 of 129
57. Question
1 pointsWhat important information is added to the TCP/IP transport layer header to ensure communication and connectivity with a remote network device?Correct
Incorrect
-
Question 58 of 129
58. Question
1 pointsWhat is the TCP mechanism used in congestion avoidance?Correct
Incorrect
-
Question 59 of 129
59. Question
1 pointsWhich scenario describes a function provided by the transport layer?Correct
Incorrect
-
Question 60 of 129
60. Question
1 pointsA user opens three browsers on the same PC to access www.cisco.com to search for certification course information. The Cisco web server sends a datagram as a reply to the request from one of the web browsers. Which information is used by the TCP/IP protocol stack in the PC to identify which of the three web browsers should receive the reply?Correct
Incorrect
-
Question 61 of 129
61. Question
1 pointsWhat are two ways that TCP uses the sequence numbers in a segment? (Choose two.)Correct
Incorrect
-
Question 62 of 129
62. Question
1 pointsWhich two tasks are functions of the presentation layer? (Choose two.)Correct
Incorrect
-
Question 63 of 129
63. Question
1 pointsWhich three statements characterize UDP? (Choose three.)Correct
Incorrect
-
Question 64 of 129
64. Question
1 pointsWhat is a key characteristic of the peer-to-peer networking model?Correct
Incorrect
-
Question 65 of 129
65. Question
1 pointsA technician can ping the IP address of the web server of a remote company but cannot successfully ping the URL address of the same web server. Which software utility can the technician use to diagnose the problem?Correct
Incorrect
-
Question 66 of 129
66. Question
1 pointsWhich domain name would be an example of a top-level domain?Correct
Incorrect
-
Question 67 of 129
67. Question
1 pointsA PC obtains its IP address from a DHCP server. If the PC is taken off the network for repair, what happens to the IP address configuration?Correct
Incorrect
-
Question 68 of 129
68. Question
1 pointsWhen planning for network growth, where in the network should packet captures take place to assess network traffic?Correct
Incorrect
-
Question 69 of 129
69. Question
1 pointsA wireless host needs to request an IP address. What protocol would be used to process the request?Correct
Incorrect
-
Question 70 of 129
70. Question
1 pointsWhich example of malicious code would be classified as a Trojan horse?Correct
Incorrect
-
Question 71 of 129
71. Question
1 pointsWhen applied to a router, which command would help mitigate brute-force password attacks against the router?Correct
Incorrect
-
Question 72 of 129
72. Question
1 pointsA network technician suspects that a particular network connection between two Cisco switches is having a duplex mismatch. Which command would the technician use to see the Layer 1 and Layer 2 details of a switch port?Correct
Incorrect
-
Question 73 of 129
73. Question
1 pointsWhere are Cisco IOS debug output messages sent by default?Correct
Incorrect
-
Question 74 of 129
74. Question
1 pointsMatch the description with the associated IOS mode. (not all options are used.)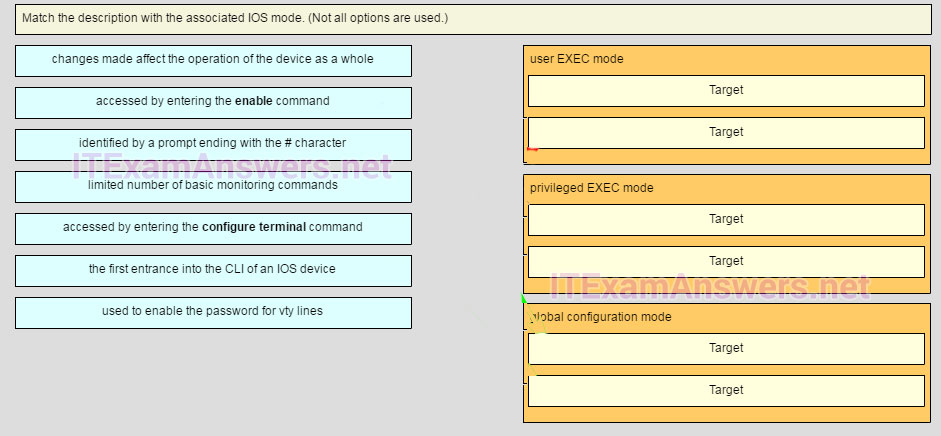
Sort elements
- changes made affect the operation of the device as a whole
- accessed by entering the configure terminal command
- limited number of basic monitoring commands
- the first entrance into the CLI of an IOS device
- accessed by entering the enable command
- identified by a prompt ending with the # character
- used to enable the password forvty lines
-
Global configuration mode - Target A
-
Global configuration mode - Target B
-
User EXEC mode - target A
-
User EXEC mode - target B
-
privileged EXEC mode - target A
-
privileged EXEC mode - target B
Correct
Incorrect
-
Question 75 of 129
75. Question
1 pointsRefer to the exhibit. Match the packets with their destination IP address to the exiting interfaces on the router. (Not all targets are used.)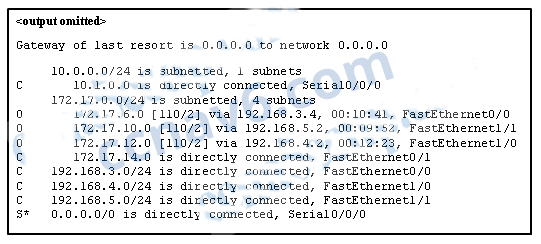
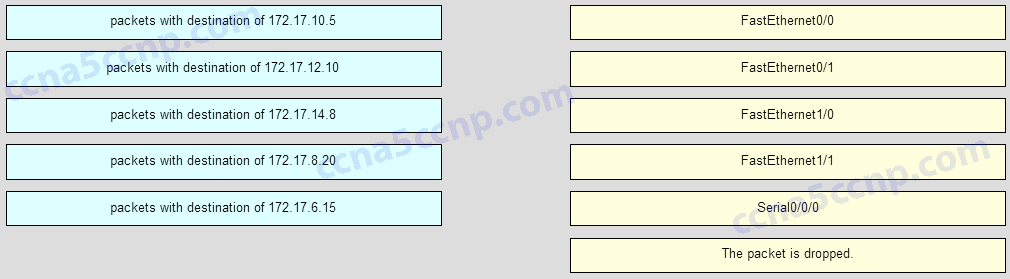
Sort elements
- FastEthernet0/0
- FastEthernet0/1
- FastEthernet1/0
- FastEthernet1/1
- Serial0/0/0
- The packet is dropped.
-
packets with destination of 172 17.6 15
-
packets with destination of 172 17.14 8
-
packets with destination of 172 17.12 10
-
packets with destination of 172 17.10.5
-
packets with destination of 172.17.8.20
Correct
Incorrect
-
Question 76 of 129
76. Question
1 pointsRefer to the exhibit. An administrator is testing connectivity to a remote device with the IP address 10.1.1.1. What does the output of this command indicate?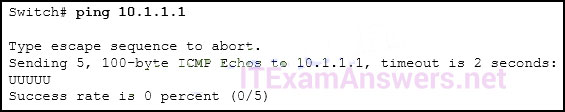 Correct
Correct
Incorrect
-
Question 77 of 129
77. Question
1 pointsA user is unable to reach the web site when typing http://www.cisco.com in a web browser, but can reach the same site by typing http://72.163.4.161. What is the issue?Correct
Incorrect
-
Question 78 of 129
78. Question
1 pointsA company is expanding its business to other countries. All branch offices must remain connected to corporate headquarters at all times. Which network technology is required to support this requirement?Correct
Incorrect
-
Question 79 of 129
79. Question
1 pointsA home user is looking for an ISP connection that provides high speed digital transmission over regular phone lines. What ISP connection type should be used?Correct
Incorrect
-
Question 80 of 129
80. Question
1 pointsHow does quality of service help a network support a wide range of applications and services?Correct
Incorrect
-
Question 81 of 129
81. Question
1 pointsWhat source IP address does a router use by default when the traceroute command is issued?Correct
Incorrect
-
Question 82 of 129
82. Question
1 pointsAfter making configuration changes on a Cisco switch, a network administrator issues a copy running-config startup-config command. What is the result of issuing this command?Correct
Incorrect
-
Question 83 of 129
83. Question
1 pointsRefer to the exhibit. A network administrator is configuring access control to switch SW1. If the administrator has already logged into a Telnet session on the switch, which password is needed to access privileged EXEC mode?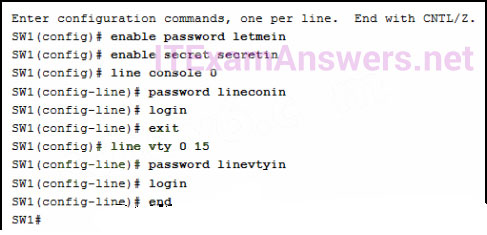 Correct
Correct
Incorrect
-
Question 84 of 129
84. Question
1 pointsMatch each item to the type of topology diagram on which it is typically identified. (Not all options are used.)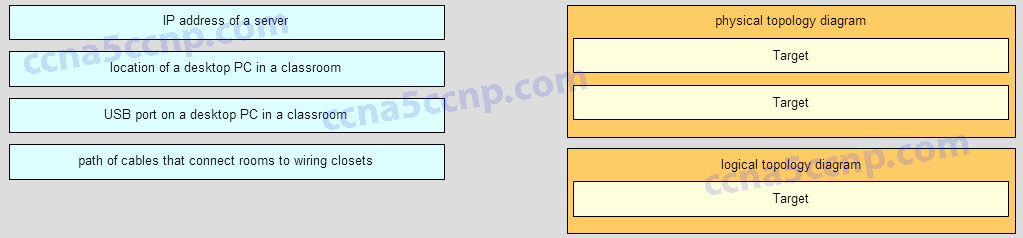
Sort elements
- location of a desktop PC in a classroom
- path of cables that connect rooms to wiring closets
- IP address of a server
- USB port on a desktop PC in a classroom
-
Physical topology diagram A
-
Physical topology diagram B
-
Logical topology diagram A
Correct
Incorrect
-
Question 85 of 129
85. Question
1 pointsWhich connection provides a secure CLI session with encryption to a Cisco network device?Correct
Incorrect
-
Question 86 of 129
86. Question
1 pointsWhat function does pressing the Tab key have when entering a command in IOS?Correct
Incorrect
-
Question 87 of 129
87. Question
1 pointsWhat layer is responsible for routing messages through an internetwork in the TCP/IP model?Correct
Incorrect
-
Question 88 of 129
88. Question
1 pointsWhich statement accurately describes a TCP/IP encapsulation process when a PC is sending data to the network?Correct
Incorrect
-
Question 89 of 129
89. Question
1 pointsWhat unique address is embedded in an Ethernet NIC and used for communication on an Ethernet network?Correct
Incorrect
-
Question 90 of 129
90. Question
1 pointsWhich procedure is used to reduce the effect of crosstalk in copper cables?Correct
Incorrect
-
Question 91 of 129
91. Question
1 pointsDuring the encapsulation process, what occurs at the data link layer for a PC connected to an Ethernet network?Correct
Incorrect
-
Question 92 of 129
92. Question
1 pointsWhat are two characteristics of Ethernet MAC addresses? (Choose two.)Correct
Incorrect
-
Question 93 of 129
93. Question
1 pointsIf a device receives an Ethernet frame of 60 bytes, what will it do?Correct
Incorrect
-
Question 94 of 129
94. Question
1 pointsUnder which two circumstances will a switch flood a frame out of every port except the port that the frame was received on? (Choose two.)Correct
Incorrect
-
Question 95 of 129
95. Question
1 pointsWhich switching method has the lowest level of latency?Correct
Incorrect
-
Question 96 of 129
96. Question
1 pointsWhich two commands can be used on a Windows host to display the routing table? (Choose two.)Correct
Incorrect
-
Question 97 of 129
97. Question
1 pointsWhich two functions are primary functions of a router? (Choose two.)Correct
Incorrect
-
Question 98 of 129
98. Question
1 pointsWhat is the binary representation of 0xCA?Correct
Incorrect
-
Question 99 of 129
99. Question
1 pointsAt a minimum, which address is required on IPv6-enabled interfaces?Correct
Incorrect
-
Question 100 of 129
100. Question
1 pointsWhich service provides dynamic global IPv6 addressing to end devices without using a server that keeps a record of available IPv6 addresses?Correct
Incorrect
-
Question 101 of 129
101. Question
1 pointsWhat is the purpose of the command ping ::1?Correct
Incorrect
-
Question 102 of 129
102. Question
1 pointsHow many usable IP addresses are available on the 192.168.1.0/27 network?Correct
Incorrect
-
Question 103 of 129
103. Question
1 pointsWhat is the process of dividing a data stream into smaller pieces before transmission?Correct
Incorrect
-
Question 104 of 129
104. Question
1 pointsWhen IPv4 addressing is manually configured on a web server, which property of the IPv4 configuration identifies the network and host portion for an IPv4 address?Correct
Incorrect
-
Question 105 of 129
105. Question
1 pointsWhich two roles can a computer assume in a peer-to-peer network where a file is being shared between two computers? (Choose two.)Correct
Incorrect
-
Question 106 of 129
106. Question
1 pointsWhich two protocols operate at the highest layer of the TCP/IP protocol stack? (Choose two.)Correct
Incorrect
-
Question 107 of 129
107. Question
1 pointsWhat is one difference between the client-server and peer-to-peer network models?Correct
Incorrect
-
Question 108 of 129
108. Question
1 pointsWhat is the function of the HTTP GET message?Correct
Incorrect
-
Question 109 of 129
109. Question
1 pointsWhich networking model is being used when an author uploads one chapter document to a file server of a book publisher?Correct
Incorrect
-
Question 110 of 129
110. Question
1 pointsWhat network service resolves the URL entered on a PC to the IP address of the destination server?Correct
Incorrect
-
Question 111 of 129
111. Question
1 pointsA network engineer is analyzing reports from a recently performed network baseline. Which situation would depict a possible latency issue?Correct
Incorrect
-
Question 112 of 129
112. Question
1 pointsWhich firewall feature is used to ensure that packets coming into a network are legitimate responses to requests initiated from internal hosts?Correct
Incorrect
-
Question 113 of 129
113. Question
1 pointsWhat is one indication that a Windows computer did not receive an IPv4 address from a DHCP server?Correct
Incorrect
-
Question 114 of 129
114. Question
1 pointsWhich command can an administrator issue on a Cisco router to send debug messages to the vty lines?Correct
Incorrect
-
Question 115 of 129
115. Question
1 pointsFill in the blank.- During data communications, a host may need to send a single message to a specific group of destination hosts simultaneously. This message is in the form of a (Multicast) message.
Correct
Incorrect
-
Question 116 of 129
116. Question
1 pointsA medium-sized business is researching available options for connecting to the Internet. The company is looking for a high speed option with dedicated, symmetric access. Which connection type should the company choose?Correct
Incorrect
-
Question 117 of 129
117. Question
1 pointsWhat is the purpose of having a converged network?Correct
Incorrect
-
Question 118 of 129
118. Question
1 pointsWhat characteristic of a network enables it to quickly grow to support new users and applications without impacting the performance of the service being delivered to existing users?Correct
Incorrect
-
Question 119 of 129
119. Question
1 pointsAfter several configuration changes are made to a router, the copy running-configuration startup-configuration command is issued. Where will the changes be stored?Correct
Incorrect
-
Question 120 of 129
120. Question
1 pointsRefer to the exhibit. From global configuration mode, an administrator is attempting to create a message-of-the-day banner by using the command banner motd V Authorized access only! Violators will be prosecuted! V When users log in using Telnet, the banner does not appear correctly. What is the problem? Correct
Correct
Incorrect
-
Question 121 of 129
121. Question
1 pointsWhat are three characteristics of an SVI? (Choose three.)Correct
Incorrect
-
Question 122 of 129
122. Question
1 pointsA technician configures a switch with these commands:SwitchA(config)# interface vlan 1 SwitchA(config-if)# ip address 192.168.1.1 255.255.255.0 SwitchA(config-if)# no shutdownWhat is the technician configuring?Correct
Incorrect
-
Question 123 of 129
123. Question
1 pointsIn computer communication, what is the purpose of message encoding?Correct
Incorrect
-
Question 124 of 129
124. Question
1 pointsWhat is a characteristic of multicast messages?Correct
Incorrect
-
Question 125 of 129
125. Question
1 pointsA large corporation has modified its network to allow users to access network resources from their personal laptops and smart phones. Which networking trend does this describe?Correct
Incorrect
-
Question 126 of 129
126. Question
1 pointsTrue or False. A dedicated server is not needed when implementing a peer-to-peer network.Correct
Incorrect
-
Question 127 of 129
127. Question
1 pointsWhich term refers to a network that provides secure access to the corporate offices by suppliers, customers and collaborators?Correct
Incorrect
-
Question 128 of 129
128. Question
1 pointsWhat subnet mask is required to support 512 subnets on networks 172.28.0.0/16?Correct
Incorrect
-
Question 129 of 129
129. Question
1 pointsA DHCP server is used to IP addresses dynamically to the hosts on a network. The address pool is configured with 10.29.244.0/25. There are 19 printers on this network that need to use reserve static IP addresses from the pool. How many IP address in the pool are left to be assign to other hosts?Correct
Incorrect

Thank you.
hello this question still valid nowdays since i have the test in 2 weeks thanx in advance!
Hello are the questions and answers still valid for v6.00?
Yes, it still valid for v6
is that exam answers valid to today or?
Hello , I’m going to take the “Introduction to networks” exam next week , which questions are included ?
Thank you in advance.
https://itexamanswers.net/ccna-1-final-exam-answers-v5-1-v6-0-introduction-to-networks.html
Questions/Answers is still valid, include sections: “Version 6.0” and “New Questions (v6.0)”
Can you make the Final exam like the chapter exam 1-11 where you click the answer and then they will show you the answer right away, not like this please. its more harder this way
unfortunately, final exam has no hint
Thanks so much!
I’m writing ccna1 next week. Is this information up-to-date?
It was the latest updates, we hope to know your test results. Good luck!
The answer for question 36 is incorrect, option 3 would be the answer. The reload command only goes back to the start up configuration file, and since the running-config file was copied to startup-config, the passwords would effectively become part of the startup-config. Please change this.
Thanks for reply! answers is still option 4: The administrator will be presented with the R1> prompt
Because exhibit don’t have “login” command after “password Cisco789” command :)
you need to put “login” to make the line password active
I don’t think so. Try it on the real equipment
You will really be in user exec modus from the moment you open your terminal without need of typing any password. (As long as you connect with console cable)
Are these answers on the CCNA 1 exam?????
In question 38, an answer is missing
thank you, i have edited it
very informitive
Hay am Richard how can I get the notes or books which can guide me so that I can approach again
so if im going to the exam this week, these are the exact questions that i will be tested about ?