CCNA 1 Chapter 2 Exam Answers
Quiz-summary
0 of 29 questions completed
Questions:
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
Information
Good luck for you!
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading...
You must sign in or sign up to start the quiz.
You have to finish following quiz, to start this quiz:
Results
0 of 29 questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 points, (0)
| Average score |
|
| Your score |
|
Categories
- Not categorized 0%
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- Answered
- Review
-
Question 1 of 29
1. Question
1 pointsWhat is the function of the kernel of an operating software?Correct
Incorrect
Hint
Operating systems function with a shell, a kernel, and the hardware. The shell interfaces with the users, allowing them to request specific tasks from the device. The kernel provisions resources from the hardware to meet software requirements. The hardware functions by using drivers and their underlying electronics. The hardware represents the physical components of the device. -
Question 2 of 29
2. Question
1 pointsA network administrator needs to keep the user ID, password, and session contents private when establishing remote CLI connectivity with a switch to manage it. Which access method should be chosen?Correct
Incorrect
Hint
To be truly private a technician would use a Console connection however if remote management is required SSH provides a secure method. -
Question 3 of 29
3. Question
1 pointsWhich procedure is used to access a Cisco 2960 switch when performing an initial configuration in a secure environment?Correct
Incorrect
Hint
Telnet and SSH require active networking services to be configured on a Cisco device before they become functional. Cisco switches do not contain AUX ports. -
Question 4 of 29
4. Question
1 pointsWhich command or key combination allows a user to return to the previous level in the command hierarchy?Correct
Incorrect
Hint
End and CTRL-Z return the user to the privileged EXEC mode. Ctrl-C ends a command in process. The exit command returns the user to the previous level. -
Question 5 of 29
5. Question
1 pointsA router has a valid operating system and a configuration file stored in NVRAM. The configuration file contains an enable secret password but no console password. When the router boots up, which mode will display?Correct
Incorrect
Hint
If a Cisco IOS device has a valid IOS and a valid configuration file, it will boot into user EXEC mode. A password will be required to enter privileged EXEC mode. -
Question 6 of 29
6. Question
1 pointsWhich two functions are provided to users by the context-sensitive help feature of the Cisco IOS CLI? (Choose two.)Correct
Context-sensitive help provides the user with a list of commands and the arguments associated with those commands within the current mode of a networking device. A syntax checker provides error checks on submitted commands and the TAB key can be used for command completion if a partial command is entered.
Incorrect
Context-sensitive help provides the user with a list of commands and the arguments associated with those commands within the current mode of a networking device. A syntax checker provides error checks on submitted commands and the TAB key can be used for command completion if a partial command is entered.
-
Question 7 of 29
7. Question
1 pointsWhich information does the show startup-config command display?Correct
Incorrect
Hint
The show startup-config command displays the saved configuration located in NVRAM. The show running-config command displays the contents of the currently running configuration file located in RAM. -
Question 8 of 29
8. Question
1 pointsWhy is it important to configure a hostname on a device?Correct
Incorrect
Hint
It is important to configure a hostname because various authentication processes use the device hostname. Hostnames are helpful for documentation, and they identify the device during remote access. -
Question 9 of 29
9. Question
1 pointsWhich two host names follow the guidelines for naming conventions on Cisco IOS devices? (Choose two.)Correct
Incorrect
Hint
Some guidelines for naming conventions are that names should: Start with a letter Contain no spaces End with a letter or digit Use only letters, digits, and dashes Be less than 64 characters in length -
Question 10 of 29
10. Question
1 pointsHow does the service password-encryption command enhance password security on Cisco routers and switches?Correct
Incorrect
Hint
The service password-encryption command encrypts plaintext passwords in the configuration file so that they cannot be viewed by unauthorized users. -
Question 11 of 29
11. Question
1 pointsRefer to the exhibit. A network administrator is configuring the MOTD on switch SW1. What is the purpose of this command?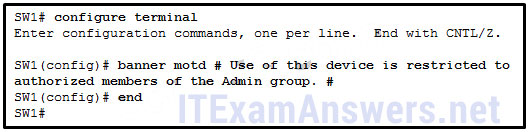 Correct
Correct
Incorrect
Hint
A banner message can be an important part of the legal process in the event that someone is prosecuted for breaking into a device. A banner message should make it clear that only authorized personnel should attempt to access the device. However, the banner command does not prevent unauthorized entry. -
Question 12 of 29
12. Question
1 pointsWhile trying to solve a network issue, a technician made multiple changes to the current router configuration file. The changes did not solve the problem and were not saved. What action can the technician take to discard the changes and work with the file in NVRAM?Correct
Incorrect
Hint
The technician does not want to make any mistakes trying to remove all the changes that were done to the running configuration file. The solution is to reboot the router without saving the running configuration. The copy startup-config running-config command does not overwrite the running configuration file with the configuration file stored in NVRAM, but rather it just has an additive effect. -
Question 13 of 29
13. Question
1 pointsWhich statement is true about the running configuration file in a Cisco IOS device?Correct
Incorrect
Hint
As soon as configuration commands are entered into a router, they modify the device immediately. Running configuration files can not be deleted nor are they saved automatically. -
Question 14 of 29
14. Question
1 pointsWhat are two characteristics of RAM on a Cisco device? (Choose two.)Correct
Incorrect
Hint
RAM stores data that is used by the device to support network operations. The running configuration is stored in RAM. This type of memory is considered volatile memory because data is lost during a power cycle. Flash memory stores the IOS and delivers a copy of the IOS into RAM when a device is powered on. Flash memory is nonvolatile since it retains stored contents during a loss of power. -
Question 15 of 29
15. Question
1 pointsWhich interface allows remote management of a Layer 2 switch?Correct
Incorrect
Hint
In a Layer 2 switch, there is a switch virtual interface (SVI) that provides a means for remotely managing the device. -
Question 16 of 29
16. Question
1 pointsWhich interface is the default SVI on a Cisco switch?Correct
Incorrect
Hint
An SVI is a virtual interface and VLAN 1 is enabled by default on Cisco switches. VLAN 99 must be configured to be used. FastEthernet 0/1 and GigabitEthernet 0/1 are physical interfaces. -
Question 17 of 29
17. Question
1 pointsWhy would a Layer 2 switch need an IP address?Correct
Incorrect
Hint
A switch, as a Layer 2 device, does not need an IP address to transmit frames to attached devices. However, when a switch is accessed remotely through the network, it must have a Layer 3 address. The IP address must be applied to a virtual interface rather than to a physical interface. Routers, not switches, function as default gateways. -
Question 18 of 29
18. Question
1 pointsWhat command can be used on a Windows PC to see the IP configuration of that computer?Correct
Incorrect
Hint
On a Windows PC, the ipconfig command can be used to verify the current IP configuration. The ping command can be used to verify connectivity to other network devices. The show interfaces and show ip interface brief commands are both Cisco IOS commands that are used to see the status of router and switch interfaces. -
Question 19 of 29
19. Question
1 pointsA technician is adding a new PC to a LAN. After unpacking the components and making all the connections, the technician starts the PC. After the OS loads, the technician opens a browser, and verifies that the PC can reach the Internet. Why was the PC able to connect to the network with no additional configuration?Correct
Incorrect
Hint
The new PC was preconfigured to use DHCP. When the PC is connected to a network that uses DHCP, it gets the IP address settings from the DHCP server that will allow it to function on the network. All devices require at least an IP address and subnet mask to function on a LAN. DNS does not automatically configure addresses on hosts. PC virtual interfaces are not universally compatible with LANs and do not necessarily provide a host with an IP address. At this place in the course, virtual interfaces are used on network switches. -
Question 20 of 29
20. Question
1 pointsWhat is a user trying to determine when issuing a ping 10.1.1.1 command on a PC?Correct
Incorrect
Hint
The ping destination command can be used to test connectivity. -
Question 21 of 29
21. Question
1 pointsRefer to the exhibit. A network technician is testing connectivity in a new network. Based on the test results shown in the exhibit, which device does the technician have connectivity with and which device does the technician not have connectivity with? (Choose two.)Correct
Incorrect
Hint
The exhibit shows ping tests to two devices. One device has the IP address of 192.168.1.2, which is switch 2. The other test is to the IP address of 192.168.1.21, which is host PC-C. For the first test, to switch 2, the results are successful, with four reply messages received. This means that connectivity exists to switch 2. For the second test, all four messages timed out. This indicates that connectivity does not exist to PC-C. -
Question 22 of 29
22. Question
1 pointsRefer to the exhibit. What three facts can be determined from the viewable output of the show ip interface brief command? (Choose three.) What three facts can be determined from the viewable output of the show ip interface brief command? (Choose three.)
Correct
Incorrect
Hint
Vlan1 is the default SVI. Because an SVI has been configured, the switch can be configured and managed remotely. FastEthernet0/0 is showing up and up, so a device is connected. -
Question 23 of 29
23. Question
1 pointsAn administrator is configuring a switch console port with a password. In what order will the administrator travel through the IOS modes of operation in order to reach the mode in which the configuration commands will be entered? (Not all options are used.)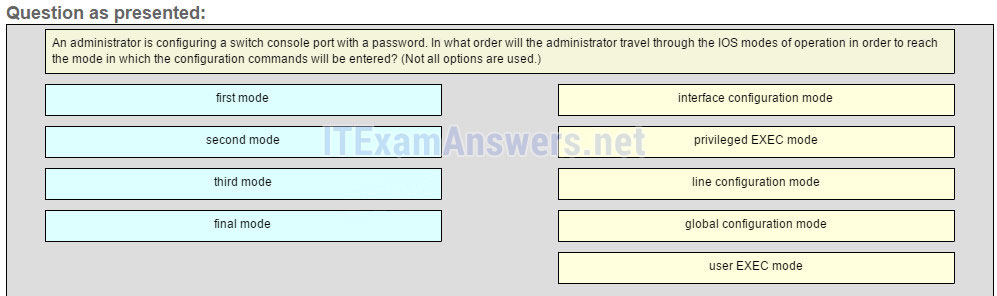
Sort elements
- privileged EXEC mode
- line configuration mode
- global configuration mode
- user EXEC mode
- interface configuration mode
-
second mode
-
final mode
-
third mode
-
first mode
Correct
Incorrect
Hint
The configuration mode that the administrator first encounters is user EXEC mode. After the enable command is entered, the next mode is privileged EXEC mode. From there, the configure terminal command is entered to move to global configuration mode. Finally, the administrator enters the line console 0 command to enter the mode in which the configuration will be entered. -
Question 24 of 29
24. Question
1 pointsMatch the definitions to their respective CLI hot keys and shortcuts. (Not all options are used.)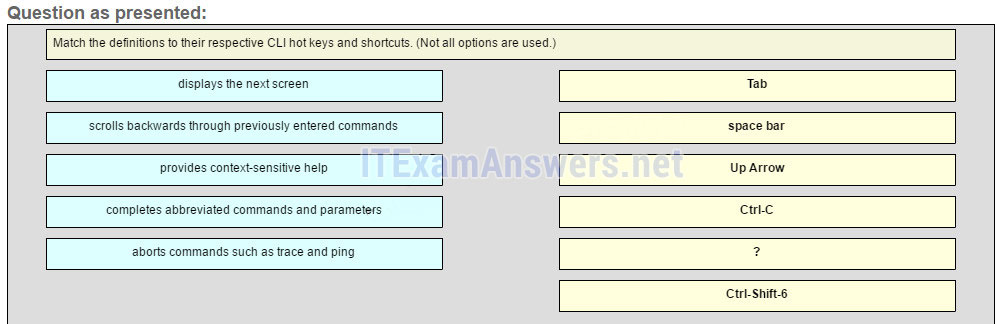
Sort elements
- Tab
- Space bar
- Up arrow
- ?
- Ctr-Shift 6
- Ctrl-C
-
completes abbreviated commands and parameters
-
displays the next screen
-
scrolls backwards through previously entered commands
-
provides context-sensitive help
-
aborts commands such as trace and ping
Correct
Incorrect
Hint
The shortcuts with their functions are as follows: – Tab – Completes the remainder of a partially typed command or keyword – Space bar – displays the next screen – ? – provides context-sensitive help – Up Arrow – Allows user to scroll backward through former commands – Ctrl-C – cancels any command currently being entered and returns directly to privileged EXEC mode – Ctrl-Shift-6 – Allows the user to interrupt an IOS process such as ping or traceroute -
Question 25 of 29
25. Question
1 pointsIn your opinion (this has no bearing on your grade), please indicate how enthusiastic you are about the content of this course and the things you’re learning (or have learned):Correct
Incorrect
-
Question 26 of 29
26. Question
1 pointsIn your opinion (this has no bearing on your grade), please indicate your interest in this course:Correct
Incorrect
-
Question 27 of 29
27. Question
1 pointsWhat is the function of the kernel of an operating system?Correct
Incorrect
Hint
Operating systems function with a shell, a kernel, and the hardware. The shell interfaces with the users, allowing them to request specific tasks from the device. The kernel provisions resources from the hardware to meet software requirements. The hardware functions by using drivers and their underlying electronics. The hardware represents the physical components of the device. -
Question 28 of 29
28. Question
1 pointsA router with a valid operating system contains a configuration file stored in NVRAM. The configuration file has an enable secret password but no console password. When the router boots up, which mode will display?Correct
Incorrect
Hint
If a Cisco IOS device has a valid IOS and a valid configuration file, it will boot into user EXEC mode. A password will be required to enter privileged EXEC mode. -
Question 29 of 29
29. Question
1 pointsIn your opinion (this has no bearing on your grade), please rate your motivation to do well in this course:Correct
Incorrect

this has no bearing on your grade: incorrect LOL
This is great!
However I’ve spotted a few answers marked with a star (*) in the end that obviously calls to the correct answer. Might you remove those stars our from the correct answers?
I will make it more challenging :)
how can I move to the next question?
hit “check” then “next”, so easy :)
alv prro
There is an error:
Match the definitions to their respective CLI hot keys and shortcuts. (Not all options are used.)
– I am not sure why but I have answare – Ctrl+Shift+6 which is not correct…..
you’re right
CTRL+C interrupts ping in windows. CTRL+Shift+6 interrupts pings in CLI
i think there is an error on the answers of the second question