- What is the authoritative source for an address lookup?
- A. a recursive DNS search*
- B. the operating system cache
- C. the ISP local cache
- D. the browser cache
- Which feature builds a FIB and an adjacency table to expedite packet forwarding?
- A. cut through
- B. fast switching
- C. process switching
- D. Cisco Express Forwarding*
Show (Hide) Explanation/ReferenceCisco Express Forwarding (CEF) provides the ability to switch packets through a device in a very quick and efficient way while also keeping the load on the router’s processor low. CEF is made up of two different main components: the Forwarding Information Base (FIB) and the Adjacency Table. These are automatically updated at the same time as the routing table.The Forwarding Information Base (FIB) contains destination reachability information as well as next hop information. This information is then used by the router to make forwarding decisions. The FIB allows for very efficient and easy lookups.
The adjacency table is tasked with maintaining the layer 2 next-hop information for the FIB.
- Which two statements about late collisions are true? (Choose two)
- A. They may indicate a duplex mismatch.*
- B. By definition, they occur after the 512th bit of the frame has been transmitted.*
- C. They indicate received frames that did not pass the FCS match.
- D. They are frames that exceed 1518 bytes.
- E. They occur when CRC errors and interference occur on the cable.
Show (Hide) Explanation/ReferenceA late collision is defined as any collision that occurs after the first 512 bits of the frame have been transmitted. The usual possible causes are full-duplex/half-duplex mismatch, exceeded Ethernet cable length limits, or defective hardware such as incorrect cabling, non-compliant number of hubs in the network, or a bad NIC.Note: On an Ethernet connection, a duplex mismatch is a condition where two connected devices operate in different duplex modes, that is, one operates in half duplex while the other one operates in full duplex.
- What feature uses a random time to re-sent a frame?
- A. CSMA/CA
- B. ?
- C. ?
- D. CSMA/CD*
- Which command can you enter to verify echo request and echo reply?
- A. ping*
- B. traceroute
- C. tracert
- D. telnet
Show (Hide) Explanation/ReferenceThe ping command first sends an echo request packet to an address, then waits for an echo reply. The ping is successful only if:
+ The echo request gets to the destination, and
+ The destination is able to get an echo reply back to the source within a predetermined time called a timeout. The default value of this timeout is two seconds on Cisco routers. - Two features of the extended ping command? (Choose two)
- A. It can send a specific number of packet*
- B. It can send packet from specified interface of IP address*
- C. It can resolve the destination host name
- D. It can ping multiple host at the same time
Show (Hide) Explanation/ReferenceThere are many options to choose when using extended ping. Below shows the options that we can choose: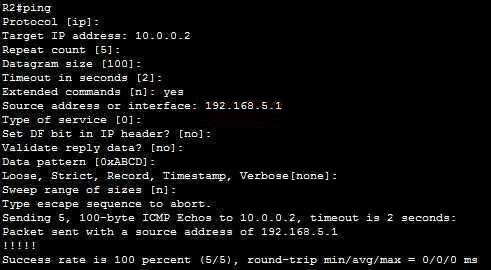
In which:
+ Repeat count [5]: Number of ping packets that are sent to the destination address. The default is 5 -> A is correct.
+ Source address or interface: The interface or IP address of the router to use as a source address for the probes -> B is correct.For more information about extended ping, please read: http://www.cisco.com/c/en/us/support/docs/ip/routing-information-protocol-rip/13730-ext-ping-trace.html
- What utility is used for shadowed rules?
- A. Create an action plan
- B. Implement an action plan*
- C. Gather facts
- D. ?
Show (Hide) Explanation/ReferenceWe are not sure about this question. But below is information about the shadowed rule for your reference.Shadowed Rule: These are rules that will never be executed because of improper access-list order. A shadowed rule occurs when a general rule precedes a specific one. For example, if the first rule that says “allow all outbound web traffic” and then a second rule (lie under the first rule) says “deny all outbound traffic to Google” the second rule will never be executed.
The following is a simple example of shadowed rules:
access-list acl permit ip 1.0.0.0 255.0.0.0 any
access-list acl permit ip 1.1.0.0 255.255.0.0 any-> The second rule never matches.
- In which two situations should you use out-of-band management?
- A. when a network device fails to forward packets*
- B. when you require ROMMON access*
- C. when management applications need concurrent access to the device
- D. when you require administrator access from multiple locations
- E. when the control plane fails to respond
- Which command shows your active Telnet connections?
- A. show sessions *
- B. show cdp neighbors
- C. show users
- D. show queue
Show (Hide) Explanation/ReferenceThe “show users” shows telnet/ssh connections to your router while “show sessions” shows telnet/ssh connections from your router (to other devices). The question asks about “your active Telnet connections”, meaning connections from your router so the answer should be A. - Which symptom can cause duplex mismatch problem?
- A. no earner
- B. collisions on interface*
- C. giants
- D. CRC errors
- What feature you should use to analyse and monitor your traffic for troubleshooting?
- A. RSPAN
- B. SPAN
- C. Netflow*
- D. SNMP
CCNA 200-125 Exam: Miscellaneous Questions With Answers
Subscribe
0 Comments
