Lab Objective:
The objective of this lab exercise is for you to configure static routes and ACLs on Cisco routers.
Lab Purpose:
These are classic exam subjects you should be very familiar with. Rather than watch a video solution (if you have access to the video course), I have provided show runs and test commands where appropriate.
Certification Level:
This lab is suitable for both CCENT and CCNA certification exam preparation.
Lab Difficulty:
This lab has a difficulty rating of 5/10.
Readiness Assessment:
When you are ready for your certification exam, you should complete this lab in no more than 15 minutes.
Lab Topology:
Please use the following topology to complete this lab exercise:
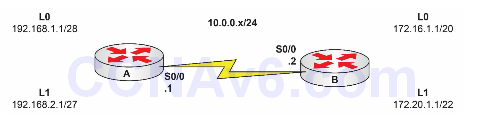
Task 1:
Configure the topology above. You should be able to ping across the Serial interface only because there are no routes from the Loopback networks.
Task 2:
Configure static routes on RouterA with an exit interface of its own Serial interface so it can reach the networks on the Loopbacks for RouterB. On RouterB, configure a default route so all traffic for any networks are sent out of the Serial interface.
Ping all networks to check connectivity.
Task 3:
Add an extended ACL on RouterB to permit Telnet traffic to host 172.16.1.1 from any host or network. All other Telnet traffic should be denied but all other IP traffic permitted. Ensure that you enable Telnet on the router for the vty lines.
Test your ACL on RouterB by telnetting to RouterB from RouterA. Telnetting to 172.16.1.1 should work but telnetting to the other Loopback or Serial IP addresses should fail.
Task 4:
Add a named ACL on Router A so that only hosts on network 192.168.2.0/27 can be pinged from hosts on network 172.16.1.0/20. All other ICMP traffic should be denied, but all other IP traffic should be permitted. Test your ACL on RouterA by pinging 192.168.2.1 from both Loopbacks on RouterB.
Solution
Show Runs
RouterA interface Loopback0 ip address 192.168.1.1 255.255.255.240 ! interface Loopback1 ip address 192.168.2.1 255.255.255.224 ! interface FastEthernet0/0 no ip address shutdown duplex auto speed auto ! interface Serial0/0 ip address 10.0.0.1 255.255.255.0 ip access-group stop_ping in clock rate 2000000 ! ip route 172.16.0.0 255.255.240.0 Serial0/0 ip route 172.20.0.0 255.255.252.0 Serial0/0 ! no ip http server no ip http secure-server ! ip access-list extended stop_ping permit icmp 172.16.1.0 0.0.15.255 192.168.2.0 0.0.0.31 deny icmp any any permit ip any any ! control-plane ! line con 0 exec-timeout 0 0 privilege level 15 logging synchronous line aux 0 exec-timeout 0 0 privilege level 15 logging synchronous line vty 0 4 login ! ! end RouterB interface Loopback0 ip address 172.16.1.1 255.255.240.0 ! interface Loopback1 ip address 172.20.1.1 255.255.252.0 ! interface FastEthernet0/0 no ip address shutdown duplex auto speed auto ! interface Serial0/0 ip address 10.0.0.2 255.255.255.0 ip access-group 100 in clock rate 2000000 ! interface FastEthernet0/1 no ip address shutdown duplex auto speed auto ! ip forward-protocol nd ip route 0.0.0.0 0.0.0.0 Serial0/0 ! ! no ip http server no ip http secure-server ! access-list 100 permit tcp any host 172.16.1.1 eq telnet access-list 100 deny tcp any any eq telnet access-list 100 permit ip any any ! control-plane ! line con 0 exec-timeout 0 0 privilege level 15 logging synchronous line aux 0 exec-timeout 0 0 privilege level 15 logging synchronous line vty 0 4 password cisco login line vty 5 903 password cisco login ! ! end
TEST:
R1#telnet 172.20.1.1 Trying 172.20.1.1 ... % Destination unreachable; gateway or host down R1#telnet 172.16.1.1 Trying 172.16.1.1 ... Open User Access Verification Password:
TEST:
R2#ping Protocol [ip]: Target IP address: 192.168.2.1 Repeat count [5]: Datagram size [100]: Timeout in seconds [2]: Extended commands [n]: y Source address or interface: 172.16.1.1 Type of service [0]: Set DF bit in IP header? [no]: Validate reply data? [no]: Data pattern [0xABCD]: Loose, Strict, Record, Timestamp, Verbose[none]: Sweep range of sizes [n]: Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.2.1, timeout is 2 seconds: Packet sent with a source address of 172.16.1.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/5/16 ms R2#ping Protocol [ip]: Target IP address: 192.168.2.1 Repeat count [5]: Datagram size [100]: Timeout in seconds [2]: Extended commands [n]: y Source address or interface: 172.20.1.1 Type of service [0]: Set DF bit in IP header? [no]: Validate reply data? [no]: Data pattern [0xABCD]: Loose, Strict, Record, Timestamp, Verbose[none]: Sweep range of sizes [n]: Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.2.1, timeout is 2 seconds: Packet sent with a source address of 172.20.1.1 U.U.U Success rate is 0 percent (0/5) R2#
