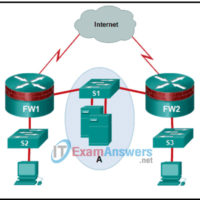
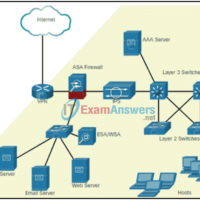
6.3.2 Network Security Infrastructure Quiz Answers 1. What is the purpose of a personal firewall on a computer? to protect the computer from viruses and malware to increase the speed of the Internet connection to protect the hardware against fire hazard to filter the traffic that is moving …
5.4.2 Wireless Network Communication Quiz Answers 1. City Center Hospital provides WLAN connectivity to its employees. The security policy requires that communication between employee mobile devices and the access points must be encrypted. What is the purpose of this requirement? to ensure that users who connect to an …
4.4.2 Attacking What We Do Quiz Answers 1. Which action best describes a MAC address spoofing attack? altering the MAC address of an attacking host to match that of a legitimate host bombarding a switch with fake source MAC addresses forcing the election of a rogue root bridge …
3.4.2 Attacking the Foundation Quiz Answers 1. Which field in an IPv6 packet is used by the router to determine if a packet has expired and should be dropped? TTL Hop Limit Address Unreachable No Route to Destination 2. An attacker is using a laptop as a rogue …
2.3.2 Securing Networks Quiz Answers 1. Which security measure is typically found both inside and outside a data center facility? a gate exit sensors security traps biometrics access continuous video surveillance 2. What is hyperjacking? taking over a virtual machine hypervisor as part of a data center attack …
1.6.2 Cybersecurity Threats, Vulnerabilities, and Attacks Quiz Answers 1. What type of attack occurs when data goes beyond the memory areas allocated to an application? SQL injection RAM injection RAM spoofing Buffer overflow 2. Which of the following statements describes a distributed denial of service (DDoS) attack? An …
Ethical Hacker Exam Answers Online Test 1.4.3 Quiz – Introduction to Ethical Hacking and Penetration Testing 2.4.3 Quiz – Planning and Scoping a Penetration Testing Assessment 3.5.3 Quiz – Information Gathering and Vulnerability Scanning 4.6.3 Quiz – Social Engineering Attacks 5.3.3 Quiz – Exploiting Wired and Wireless Networks …
1.4.3 Quiz – Introduction to Ethical Hacking and Penetration Testing Answers 1. Which statement best describes the term ethical hacker? a person who uses different tools than nonethical hackers to find vulnerabilities and exploit targets a person that is financially motivated to find vulnerabilities and exploit targets a …
2.4.3 Quiz – Planning and Scoping a Penetration Testing Assessment Answers 1. A contractor is hired to review and perform cybersecurity vulnerability assessments for a local health clinic facility. Which U.S. government regulation must the contractor understand before the contractor can start? GDPR GLBA HIPAA FedRAMP 2. An …
3.5.3 Quiz – Information Gathering and Vulnerability Scanning Answers 1. Which two tools could be used to gather DNS information passively? (Choose two.) Recon-ng Dig Wireshark Nmap ExifTool 2. When performing passive reconnaissance, which Linux command can be used to identify the technical and administrative contacts of a …