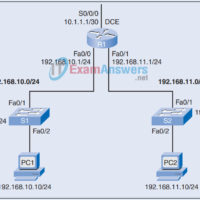
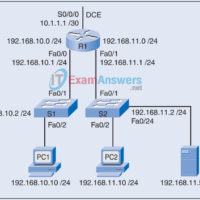
1. Which statements correctly describe Cisco access control lists? (Choose two.) Extended ACLs are created in interface configuration mode. Extended ACLs filter traffic based on source and destination IP, port number, and protocol. Standard IP ACLs are numbered 1 to 99, and extended ACLs are numbered 100 to …
1. A technician is attempting to explain broadband technology to a customer. Which descriptions should he use to educate the customer? (Choose two.) It includes dialup connections using POTS. It is incompatible with multiplexing. It uses a wide band of frequencies. It offers sustained speeds of 128 kbps …
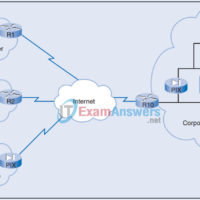
1. Which statements are true about the DHCP server functions? (Choose two.) When a client requests an IP address, the DHCP server searches the binding table for an entry that matches the client’s MAC address. If an entry exists, the corresponding IP address for that entry is returned …
1. Match each item with its appropriate diagram type: Cable type IP address and subnet Connection type Device ID Operating system version Device type and model Routing protocols Connector type A. Physical diagram B. Logical diagram 2. What is one symptom of a physical layer problem? High CPU …
CCNA 2 Routing and Switching Essentials v5 Chapter 1: Introduction to Switched Networks – Check Your Understanding Questions Answers 1. Which three options correctly associate a layer of the hierarchical design model with the function of that layer? (Choose three.) Core – end device connectivity Distribution – aggregation …
Endpoint Security Exam Answers 1.6.2 Cybersecurity Threats, Vulnerabilities, and Attacks Quiz 2.3.2 Securing Networks Quiz 3.4.2 Attacking the Foundation Quiz 4.4.2 Attacking What We Do Quiz 5.4.2 Wireless Network Communication Quiz 6.3.2 Network Security Infrastructure Quiz Checkpoint Exam: Network Security 7.5.2 The Windows Operating System Quiz 8.8.2 Linux …
10.4.2 Cybersecurity Principles, Practices, and Processes Quiz Answers 1. What is identified by the first dimension of the cybersecurity cube? knowledge goals rules safeguards tools 2. What type of cybersecurity laws protect you from an organization that might want to share your sensitive data? privacy nonrepudiation authentication confidentiality …
9.5.2 Endpoint Protection Quiz Answers 1. Which antimalware software approach can recognize various characteristics of known malware files to detect a threat? signature-based routing-based heuristics-based behavior-based 2. Match the Apple system security feature to its purpose. 3. Which device in a LAN infrastructure is susceptible to MAC address-table …
8.8.2 Linux Basics Quiz Answers 1. An author is uploading one chapter document from a personal computer to a file server of a book publisher. What role is the personal computer assuming in this network model? master slave client server transient 2. In the context of a Linux …
7.5.2 The Windows Operating System Quiz Answers 1. When a user makes changes to the settings of a Windows system, where are these changes stored? Control Panel boot.ini win.ini Registry 2. For security reasons a network administrator needs to ensure that local computers cannot ping each other. Which …