1.4.3 Quiz – Introduction to Ethical Hacking and Penetration Testing Answers
1. Which statement best describes the term ethical hacker?
- a person who uses different tools than nonethical hackers to find vulnerabilities and exploit targets
- a person that is financially motivated to find vulnerabilities and exploit targets
- a person that is looking to make a point or to promote what they believe
- a person who mimics an attacker to evaluate the security posture of a network
Explanation: The term ethical hacker describes a person who acts as an attacker and evaluates the security posture of a computer network to minimize risk. Ethical hacker uses the same tools to find vulnerabilities and exploit targets as nonethical hackers.
2. Which threat actor term describes a well-funded and motivated group that will use the latest attack techniques for financial gain?
- hacktivist
- state-sponsored attacker
- organized crime
- insider threat
Explanation: Several years ago, the cybercrime industry took over the number-one spot for the most profitable illegal industry, attracting a new type of cyber-criminal. Organized crime goes where the money is. It consists of very well-funded and motivated groups that will typically use any of the latest attack techniques to gain access to information systems.
3. Which type of threat actor uses cybercrime to steal sensitive data and reveal it publicly to embarrass a target?
- organized crime
- hacktivist
- insider threat
- state-sponsored attacker
Explanation: Hacktivists are threat actors who are not motivated by money. They are looking to make a point, promoting a political agenda or social change, using cybercrime as the method of attack.
4. What is a state-sponsored attack?
- An attack perpetrated by a well-funded and motivated group that will typically use the latest attack techniques for financial gain.
- An attack perpetrated by governments worldwide to disrupt or steal information from other nations.
- An attack perpetrated by disgruntled employees inside an organization.
- An attack is perpetrated to steal sensitive data and then reveal it to the public to embarrass or financially affect a target.
Explanation: Cyber war and cyber espionage are two terms that fit into the category of a state-sponsored attack. Many governments worldwide use cyber attacks to steal information from opponents and cause disruption.
5. What is an insider threat attack?
- An attack perpetrated by a well-funded and motivated group that will typically use the latest attack techniques for financial gain.
- An attack perpetrated by governments worldwide to disrupt or steal information from other nations.
- An attack perpetrated by disgruntled employees inside an organization.
- An attack is perpetrated to steal sensitive data and then reveal it to the public to embarrass or financially affect a target.
Explanation: An insider threat is a threat that comes from inside an organization. Insider threats are often normal employees tricked into divulging sensitive information or mistakenly clicking on links that allow attackers to access the computers. However, they could also be malicious insiders, possibly motivated by revenge or money.
6. What kind of security weakness is evaluated by application-based penetration tests?
- firewall security
- logic flaws
- wireless deployment
- data integrity between a client and a cloud provider
Explanation: Application-based penetration test focus on testing for security weaknesses in enterprise applications. These weaknesses can include but are not limited to misconfigurations, input validation issues, injection issues, and logic flaws.
7. What two resources are evaluated by a network infrastructure penetration test? (Choose two.)
- AAA servers
- CSPs
- web servers
- IPSs
- back-end databases
Explanation: The network infrastructure penetration test is focused on evaluating the actual network infrastructure’s security posture, including the switches, routers, firewalls, and supporting resources, such as AAA servers and IPSs. Application-based penetration tests evaluate web servers and back-end databases. Cloud service providers (CSPs) are evaluated by penetration testing in the cloud.
8. When conducting an application-based penetration test on a web application, the assessment should also include testing access to which resources?
- AAA servers
- cloud services
- switches, routers, and firewalls
- back-end databases
Explanation: The application-based penetration test focuses on testing for security weaknesses in enterprise applications. These weaknesses can include but are not limited to misconfigurations, input validation issues, injection issues, and logic flaws. Because a web application is typically built on a web server with a back-end database, the testing scope also normally includes the database.
9. What is the purpose of bug bounty programs used by companies?
- reward security professionals for finding vulnerabilities in the systems of the company
- reward security professionals for discovering malicious activities by attackers in the systems of the company
- reward security professionals for fixing vulnerabilities in the systems of the company
- reward security professionals for breaking into a corporate facility to expose weaknesses in the physical perimeter
Explanation: Companies (e.g., Microsoft, Apple, Cisco) and government institutions (e.g., the U.S. Department of Defense) use bug bounty programs to reward security professionals when they find vulnerabilities in websites, applications, or any system. This enables the organization to fix these vulnerabilities before threat actors exploit them.
10. What characterizes a partially known environment penetration test?
- The tester must test the electrical grid supporting the infrastructure of the target.
- The tester is provided with a list of domain names and IP addresses in the scope of a particular target.
- The test is a hybrid approach between unknown and known environment tests.
- The tester should not have prior knowledge of the organization and infrastructure of the target.
Explanation: A partially known environment penetration test, previously known as gray-box, is somewhat of a hybrid approach between unknown- and understood- environment tests. With partially known environment testing, the testers may be provided credentials but not full network infrastructure documentation.
11. What characterizes a known environment penetration test?
- The test is somewhat of a hybrid approach between unknown and known environment tests.
- The tester could be provided with network diagrams, IP addresses, configurations, and user credentials.
- The tester should not have prior knowledge of the organization and infrastructure of the target.
- The tester may be provided only the domain names and IP addresses in the scope of a particular target.
Explanation: In a known-environment penetration test (previously known as a white box), the tester starts with significant information about the organization and the infrastructure. The tester would normally be provided with network diagrams, IP addresses, configurations, and user credentials. This type of test aims to identify as many holes as possible.
12. Which type of penetration test would only provide the tester with limited information such as the domain names and IP addresses in the scope?
- known-environment test
- partially known environment test
- unknown-environment test
- OWASP Web Security Testing Guide
Explanation: In an unknown-environment penetration test (previously known as black-box), the tester typically only has a very limited amount of information. For instance, the tester may only provide the domain names and IP addresses in scope for a particular target. The tester would have yet to gain prior knowledge of the organization’s target and infrastructure.
13. Match the penetration testing methodology to the description.
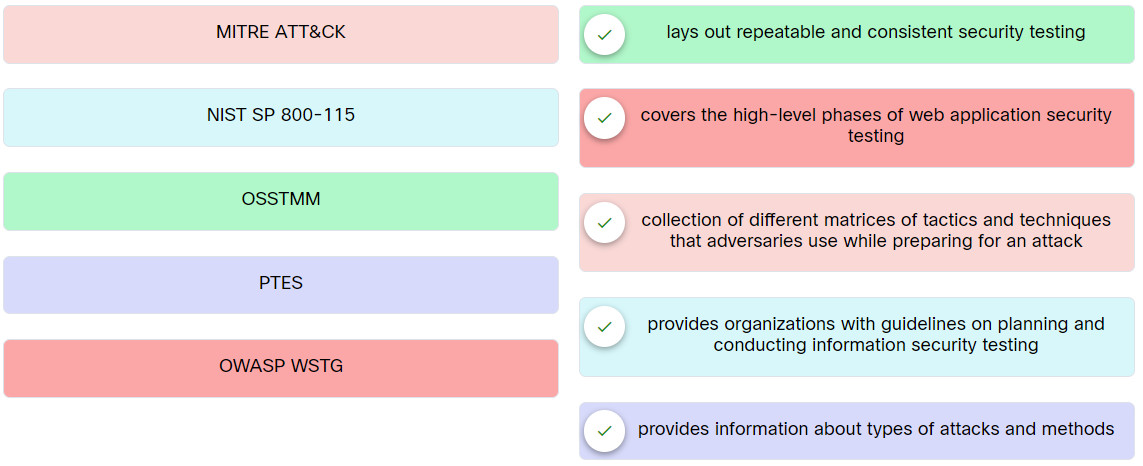
Explanation: Place the options in the following order:
| MITRE ATT&CK |
collection of different matrices of tactics and techniques that adversaries use while preparing for an attack |
| OWASP WSTG |
covers the high-level phases of web application security testing |
| NIST SP 800-115 |
provides organizations with guidelines on planning and conducting information security testing |
| OSSTMM |
lays out repeatable and consistent security testing |
| PTES |
provides information about types of attacks and methods |
14. Which three options are phases in the Penetration Testing Execution Standard (PTES)? (Choose three.)
- Threat modeling
- Penetration
- Reporting
- Enumerating further
- Network mapping
- Exploitation
Explanation: Penetration Testing Execution Standard (PTES) provides information about types of attacks and methods, and it provides information on the latest tools available to accomplish the testing methods outlined. It involves seven phases: Pre-engagement interactions, Intelligence gathering, Threat modeling, Vulnerability analysis, Exploitation, Post-exploitation, and Reporting.
15. Which two options are phases in the Information Systems Security Assessment Framework (ISSAF)? (Choose two.)
- Pre-engagement interactions
- Maintaining access
- Reporting
- Post-exploitation
- Vulnerability identification
Explanation: Information Systems Security Assessment Framework (ISSAF) is a penetration methodology with the following phases: Information gathering, Network mapping, Vulnerability identification, Penetration, Gaining access and privilege escalation, Enumerating further, Compromising remote users/sites, Maintaining access, and Covering the tracks.
16. Which two options are phases in the Open Source Security Testing Methodology Manual (OSSTMM)? (Choose two.)
- Vulnerability Analysis
- Maintaining Access
- Work Flow
- Network Mapping
- Trust Analysis
Explanation: The Open Source Security Testing Methodology Manual (OSSTMM) is a document that lays out repeatable and consistent security testing. It has the following key sections: Operational Security Metrics, Trust analysis, Workflow, Human security testing, Physical security testing, Wireless security testing, Telecommunications security testing, Data networks security testing, Compliance regulations, and Reporting with the Security Test Audit Report (STAR).
17. Which penetration testing methodology is a comprehensive guide focused on web application testing?
- MITRE ATT&CK
- OWASP WSTG
- NIST SP 800-115
- OSSTMM
Explanation: OWASP Web Security Testing Guide (WSTG) is a comprehensive guide focused on web application testing. It is a compilation of many years of work by OWASP members. It covers the high-level phases of web application security testing and digs deeper into the testing methods used.
18. Which option is a Linux distribution that includes penetration testing tools and resources?
Explanation: Black-Arch (blackarch.org), Kali Linux (kali.org), and Parrot OS (parrotsec.org) are Linux distributions that include penetration testing tools and resources. Social-Engineer Toolkit (SET) is an excellent tool for performing social engineering testing campaigns. OWASP is a nonprofit organization with local chapters worldwide that provides significant guidance on securing applications. Penetration Testing Execution Standard (PTES) is a penetration testing standard that provides information about types of attacks and methods.
19. Which option is a Linux distribution URL that provides a convenient learning environment about pen testing tools and methodologies?
- vmware.com
- attack.mitre.org
- parrotsec.org
- virtualbox.org
Explanation: Many different Linux distributions include penetration testing tools and resources, such as Kali Linux (kali.org), Parrot OS (parrotsec.org), and Black-Arch (blackarch.org). These Linux distributions provide a very convenient environment to learn about the different security tools and methodologies used in pen testing.
20. What does the “Health Monitoring” requirement mean when setting up a penetration test lab environment?
- The tester needs to be sure that a lack of resources is not the cause of false results.
- The tester needs to be able to determine the causes when something crashes.
- The tester needs to ensure controlled access to and from the lab environment and restricted access to the internet.
- The tester validates a finding running the same test with a different tool to see if the results are the same.
Explanation: Some requirements for a typical penetration testing environment are:
Closed network: the tester needs to ensure controlled access to and from the lab environment and restricted access to the Internet
Health monitoring: when something crashes, the tester needs to be able to determine why it happened
Sufficient hardware resources: the tester needs to be sure that a lack of resources is not the cause of false results
Duplicate tools: a way to validate a finding is to run the same test with a different tool to see if the results are the same
21. Which tool would be useful when performing a network infrastructure penetration test?
- vulnerability scanning tool
- bypassing firewalls and IPSs tool
- interception proxies tool
- mobile application testing tool
Explanation: The tools used in penetration testing depend on the type of testing to be done. Network infrastructure penetration test might include tools for sniffing or manipulating traffic, flooding network devices, and bypassing firewalls and IPSs.
22. Which tool should be used to perform an application-based penetration test?
- sniffing traffic tool
- bypassing firewalls and IPSs tool
- interception proxies tool
- cracking wireless encryption tool
Explanation: The tools used in penetration testing depend on the type of testing to be done. Application-based penetration tests might include tools explicitly built for scanning and detecting web vulnerabilities and manual testing tools such as interception proxies.
23. Which tools should be used to perform a wireless infrastructure penetration test?
- web vulnerability detection tools
- traffic manipulation tools
- proxy interception tools
- de-authorizing network devices tools
Explanation: The tools used in penetration testing depend on the type of testing to be done. Wireless infrastructure penetration tests might use tools to crack wireless encryption, de-authorize network devices, and perform on-path attacks (also called man-in-the-middle attacks).
24. Which tools should be used for testing the server and client platforms in an environment?
- cracking wireless encryption tools
- vulnerability scanning tools
- interception proxies tools
- de-authorizing network devices tools
Explanation: For testing the server and client platforms in an environment, several automated vulnerability scanning tools can be used to identify things such as outdated software and misconfigurations. For testing the robustness of protocols, fuzzing tools are typically used.
25. Sometimes a tester cannot virtualize a system to do the proper penetration testing. What action should be taken if a system cannot be tested in a virtualized environment?
- a full backup of the system
- rebuild the system after any test is performed
- adopt penetration test tools that will certainly not damage the system
- a complete report with recommended repairs
Explanation: Being able to recover your production environment is important for many reasons. When doing penetration testing, the tester will break things no matter what tools are adopted. Sometimes when things are broken, they do not recover without support. Using some virtual environment is ideal as it offers snapshots and restore features for the system state. In such a case that the system cannot be virtualized, having a full backup of the system or environment is required.

