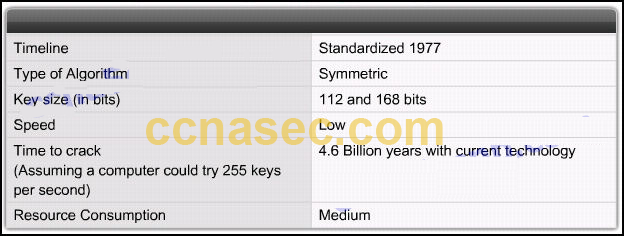
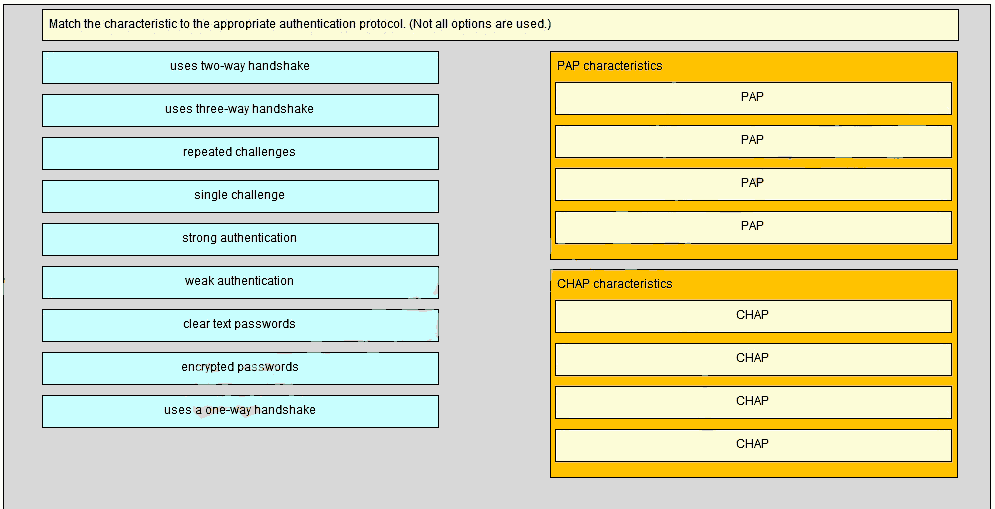
1. What is the purpose of a nonrepudiation service in secure communications? to ensure that encrypted secure communications cannot be decoded to confirm the identity of the recipient of the communications to provide the highest encryption level possible to ensure that the source of the communications is confirmed* …
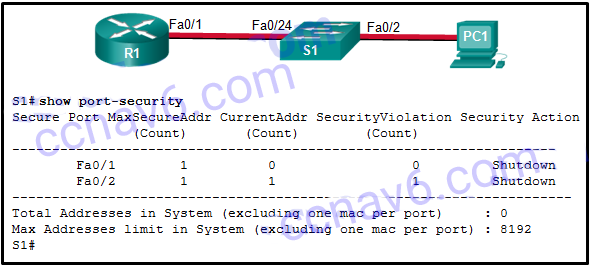
1. Which type of VLAN-hopping attack may be prevented by designating an unused VLAN as the native VLAN? DTP spoofing DHCP spoofing VLAN double-tagging* DHCP starvation 2. What component of Cisco NAC is responsible for performing deep inspection of device security profiles? Cisco NAC Profiler Cisco NAC Agent* …
1. In configuring a Cisco router to prepare for IPS and VPN features, a network administrator opens the file realm-cisco.pub.key.txt, and copies and pastes the contents to the router at the global configuration prompt. What is the result after this configuration step? The router is authenticated with the …
1. In addition to the criteria used by extended ACLs, what conditions are used by a classic firewall to filter traffic? TCP/UDP source and destination port numbers TCP/IP protocol numbers IP source and destination addresses application layer protocol session information 2. A router has been configured as a …
1. A user complains about not being able to gain access to a network device configured with AAA. How would the network administrator determine if login access for the user account is disabled? Use the show aaa local user lockout command.* Use the show running-configuration command. Use the …
1. Which two characteristics apply to role-based CLI access superviews? (Choose two.) A specific superview cannot have commands added to it directly.* CLI views have passwords, but superviews do not have passwords. A single superview can be shared among multiple CLI views. Deleting a superview deletes all associated …
1. What method can be used to mitigate ping sweeps? using encrypted or hashed authentication protocols installing antivirus software on hosts deploying antisniffer software on all network devices blocking ICMP echo and echo-replies at the network edge* 2. What are the three major components of a worm attack? …
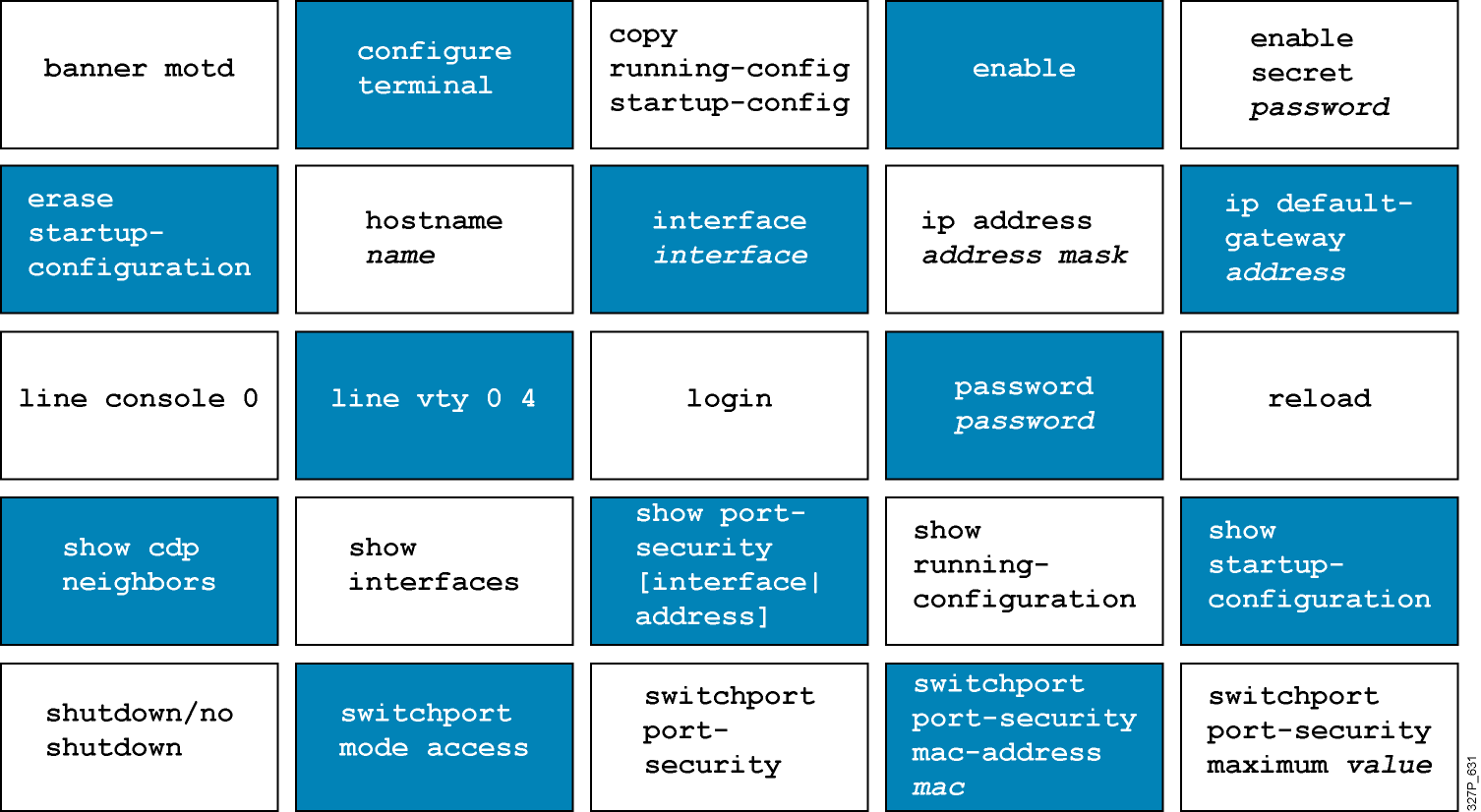
Cisco IOS User Interface Functions The CLI is used to enter commands. Operations vary between routers and switches, but both use the same CLI. The Enter key instructs a device to parse and execute a command. The CLI uses a hierarchy of commands in its configuration-mode structure. Users …
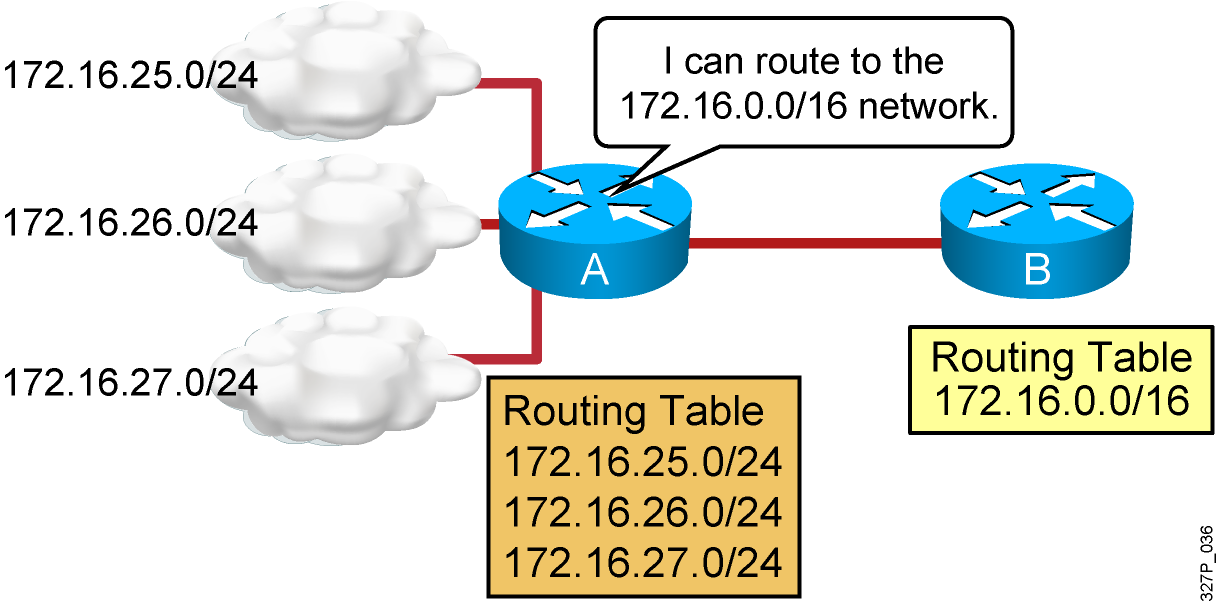
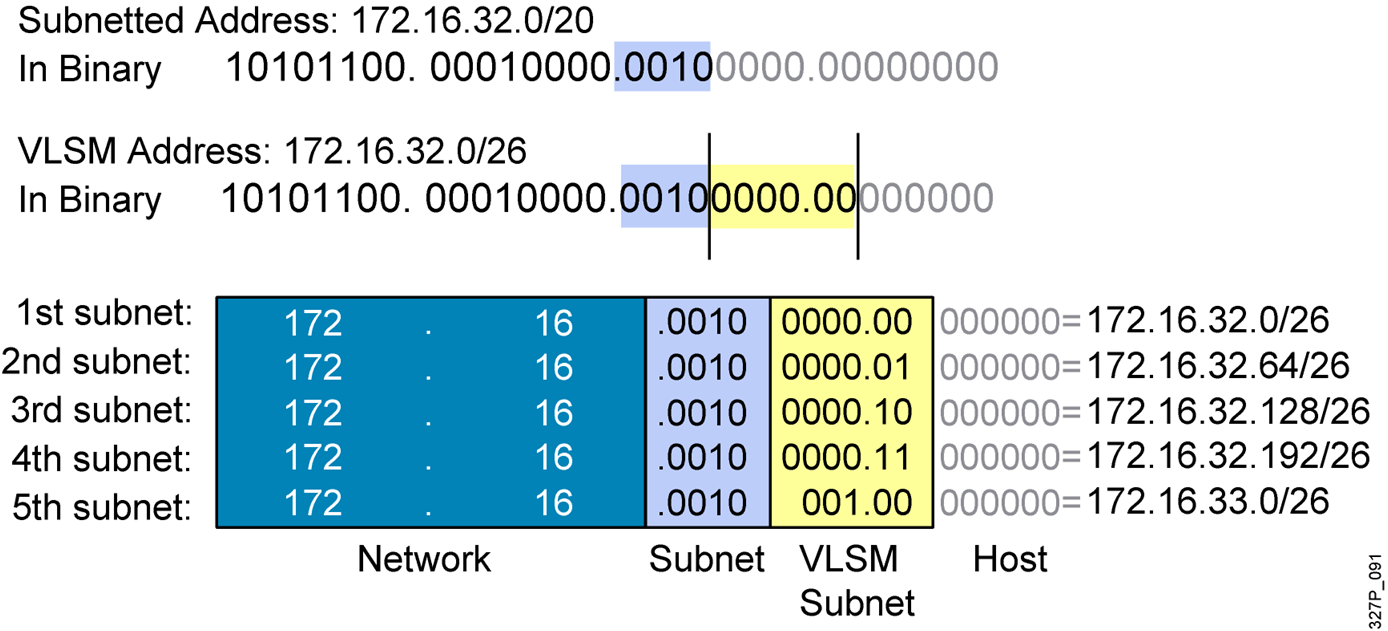
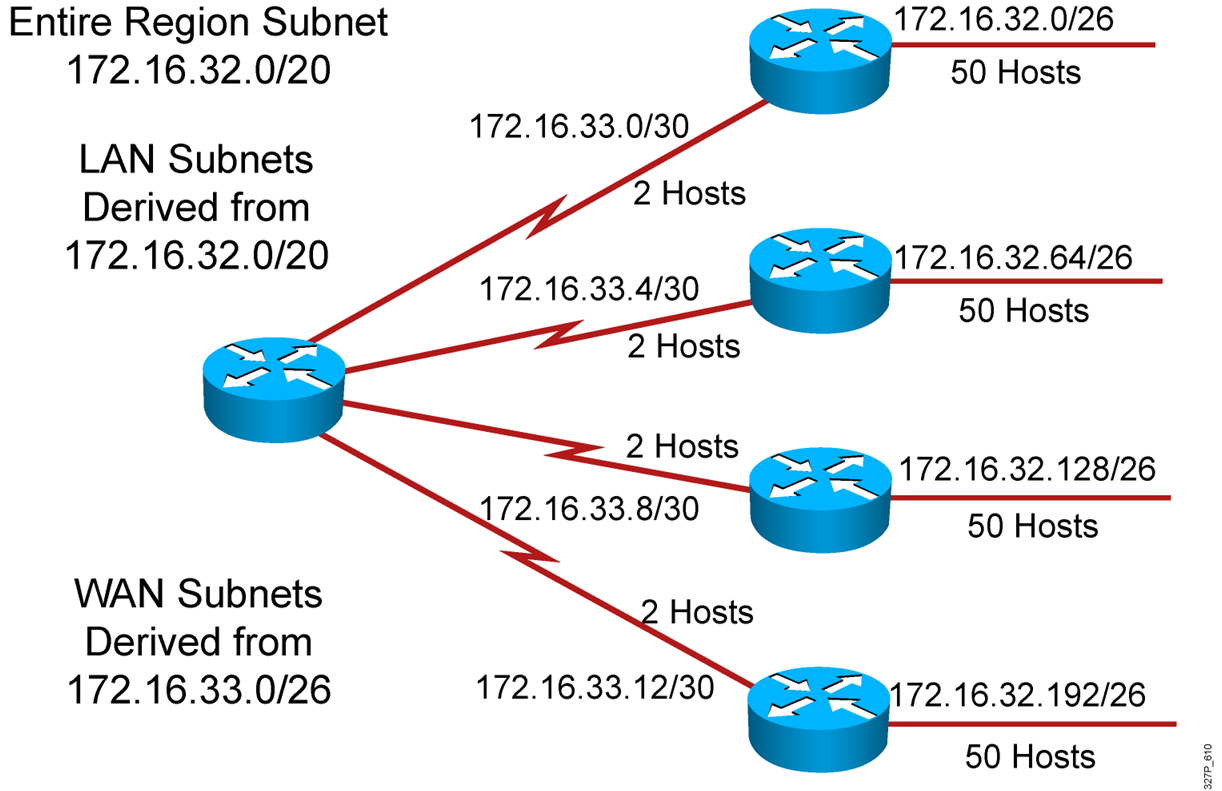
1 Why is it useful categorize networks by size when discussing network design? Knowing the number of connected devices will define how many additional layers will be added to the three-tier hierarchical network design. Knowing the number of connected devices will define how many multilayer switches will be …
Version 6.0: 1. Which statement best describes a WAN? A WAN interconnects LANs over long distances. A WAN is a public utility that enables access to the Internet. WAN is another name for the Internet. A WAN is a LAN that is extended to provide secure remote network …