
05. Reviewing Routing Operations
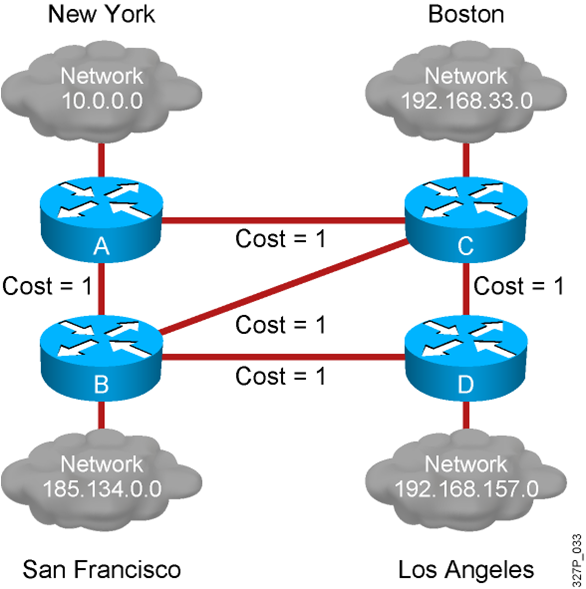
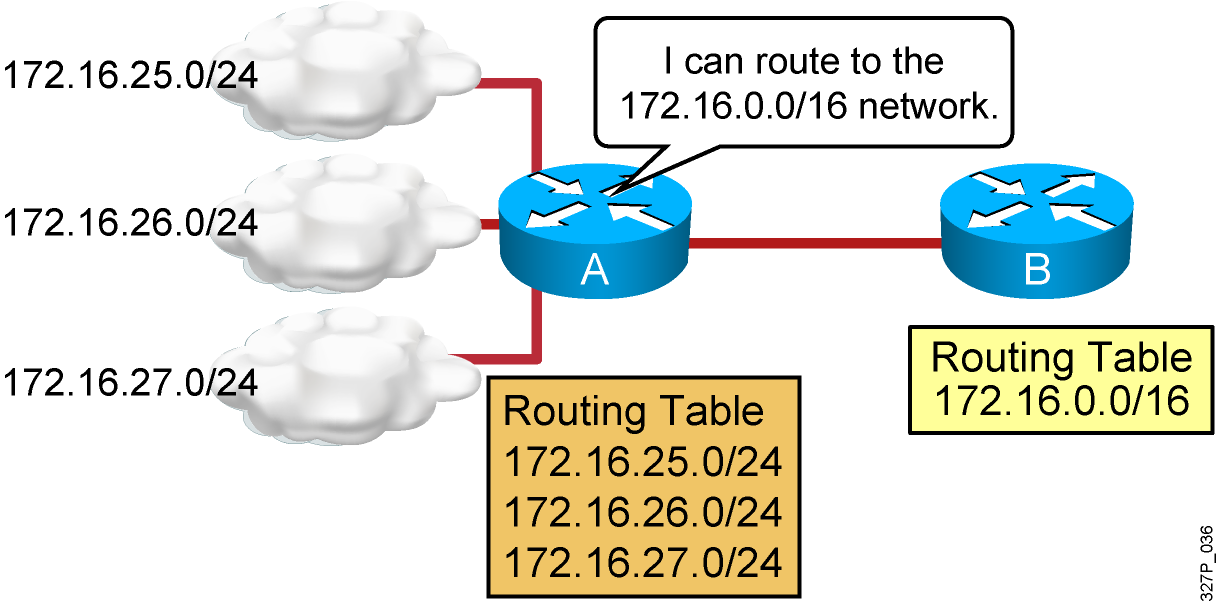
Static vs. Dynamic Routes What Is a Dynamic Routing Protocol? Routing protocols are used between routers to determine paths to remote networks and maintain those networks in the routing tables. After the path is determined, a router can route a routed protocol to the learned networks. …
04. Improving Performance with Spanning Tree
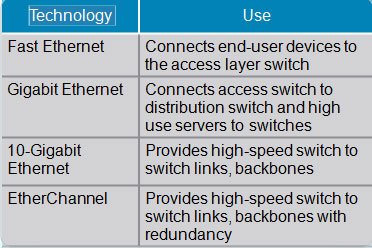
Interconnection Technologies Determining Equipment and Cabling Needs Each link provides adequate bandwidth for the total aggregate traffic over that link. Advantages of EtherChannel Logical aggregation of similar links between switches Load-shares across links Viewed as one logical port to STP Redundancy Redundant Topology Redundant topology …
03. Routing Between VLANs
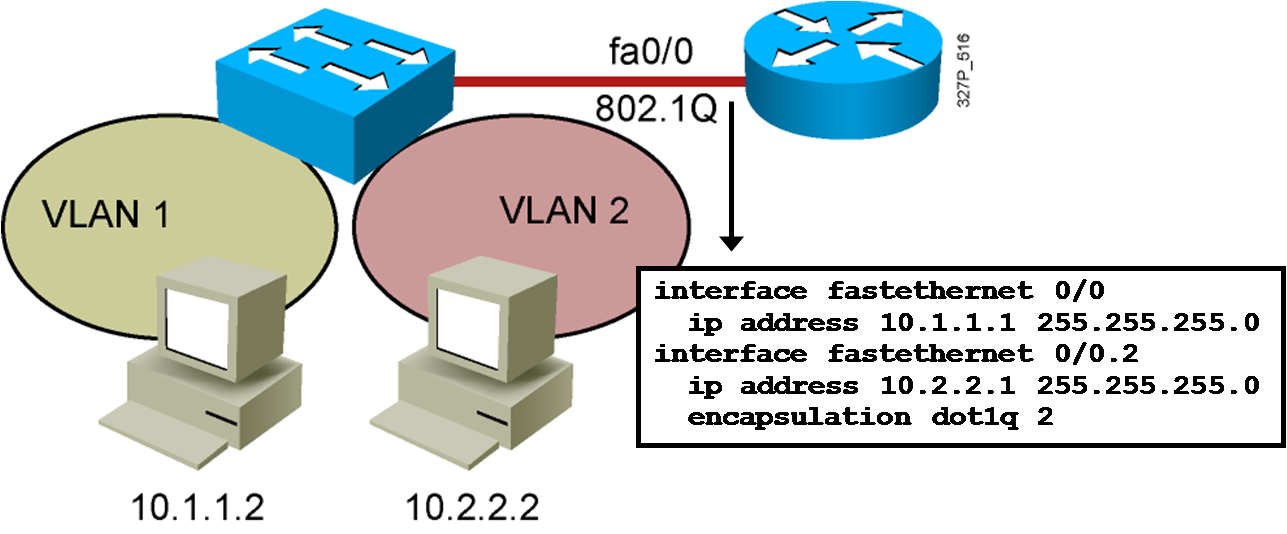
VLAN-to-VLAN Overview Network layer devices combine multiple broadcast domains. Dividing a Physical Interface into Subinterfaces Physical interfaces can be divided into multiple subinterfaces. Routing Between VLANs with 802.1Q Trunks Summary Inter-VLAN routing using a router on a stick utilizes an external router to pass traffic …
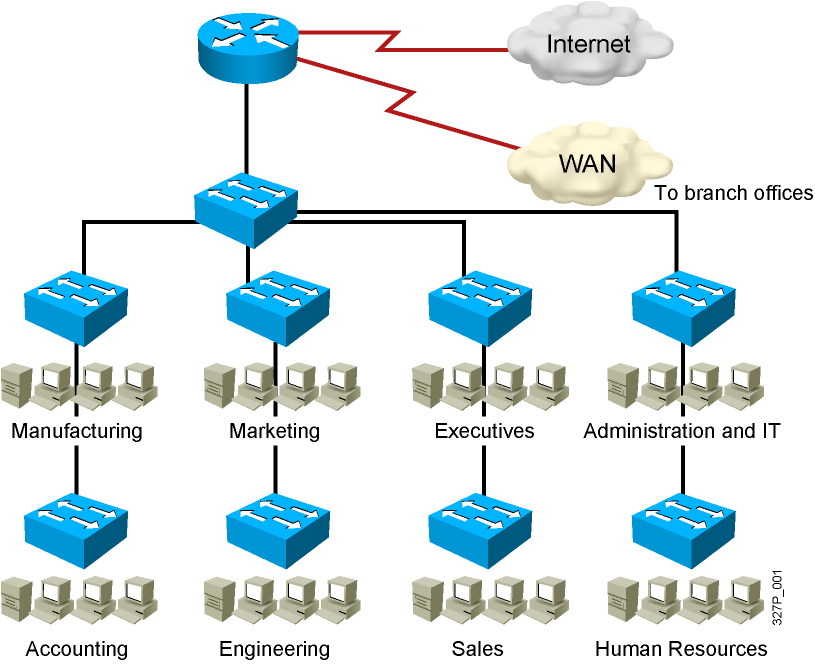
02. Implementing VLANs and Trunks
Issues in a Poorly Designed Network Unbounded failure domains Large broadcast domains Large amount of unknown MAC unicast traffic Unbounded multicast traffic Management and support challenges Possible security vulnerabilities VLAN Overview Segmentation Flexibility Security Designing VLANs for an Organization VLAN design must take into consideration the implementation of a …
CCNA Security v2.0 Final Exam Answers 100%
Implementing Network Security (Version 2.0) – CCNAS Final Exam Answers Full 100% Scored 1. Which security implementation will provide control plane protection for a network device? encryption for remote access connections AAA for authenticating management access routing protocol authentication NTP for consistent timestamps on logging messages 2. What …
CCNA Security v2.0 Chapter 11 Exam Answers
1. Which security test is appropriate for detecting system weaknesses such as misconfiguration, default passwords, and potential DoS targets? vulnerability scanning* network scanning integrity checkers penetration testing 2. How does network scanning help assess operations security? It can simulate attacks from malicious sources. It can log abnormal activity. …
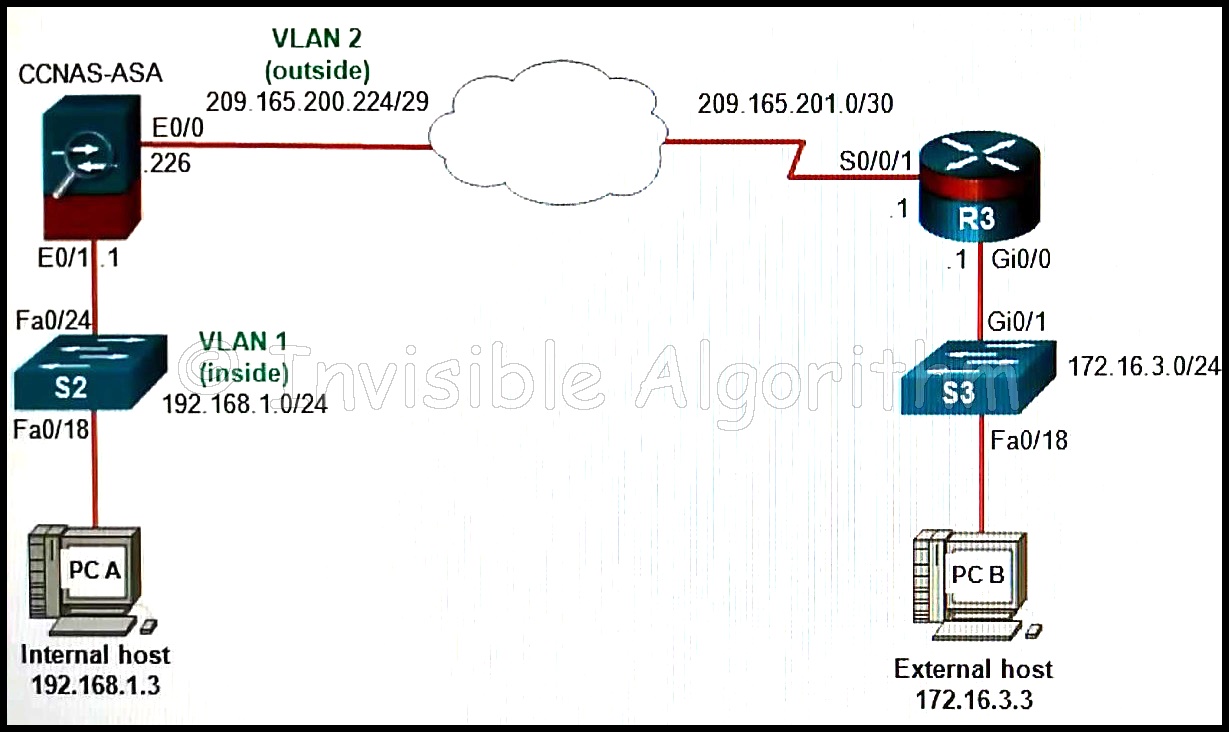
CCNA Security v2.0 Chapter 10 Exam Answers
1. Which ASDM configuration option is used to configure the ASA enable secret password? Device Setup* Monitoring Interfaces Device Management 2. Refer to the exhibit. Which Device Setup ASDM menu option would be used to configure the ASA for an NTP server? Startup Wizard Device Name/Password Routing Interfaces …
CCNA Security v2.0 Chapter 9 Exam Answers
1. Refer to the exhibit. A network administrator is configuring the security level for the ASA. What is a best practice for assigning the security level on the three interfaces? Outside 40, Inside 100, DMZ 0 Outside 0, Inside 35, DMZ 90 Outside 100, Inside 10, DMZ 40 …

CCNA Security v2.0 Chapter 8 Exam Answers
1. When is a security association (SA) created if an IPsec VPN tunnel is used to connect between two sites? after the tunnel is created, but before traffic is sent only during Phase 2 only during Phase 1 during both Phase 1 and 2* 2. In which situation …
