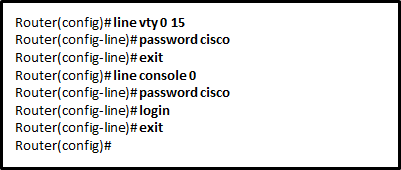
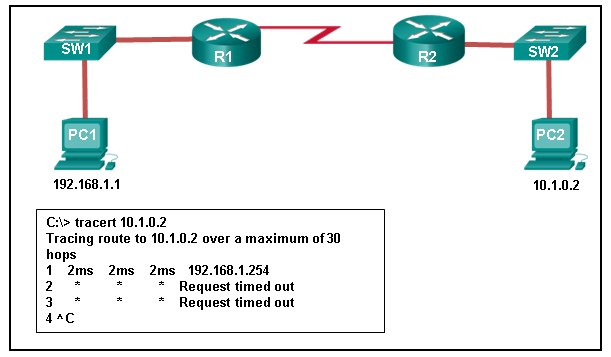
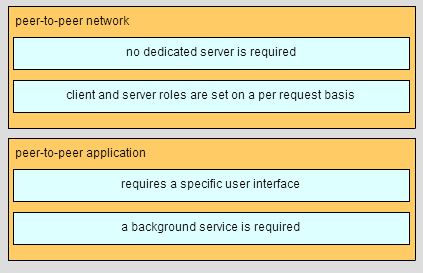
CCNA 1 Final v5.0 Exam Answers 2015 100% PDF Download 1. Which communication tool allows real-time collaboration? wiki e-mail weblog instant messaging 2. A host is accessing a Web server on a remote network. Which three functions are performed by intermediary network devices during this conversation? (Choose three.) …
CCNA 1 Practice Final v5.0 Exam Answers 2015 (100%) PDF Download 1. A host is accessing a Web server on a remote network. Which three functions are performed by intermediary network devices during this conversation? (Choose three.) regenerating data signals acting as a client or a server providing …
CCNA 1 Chapter 11 v5.0 Exam Answers 2015 (100%) PDF Download 1. Which network design consideration would be more important to a large corporation than to a small business? Internet router firewall low port density switch redundancy 2. Which protocol supports rapid delivery of streaming media? SNMP TCP …
CCNA 1 Chapter 10 v5.0 Exam Answers 2015 (100%) PDF Download 1. Which three layers of the OSI model provide similar network services to those provided by the application layer of the TCP/IP model? (Choose three.) physical layer session layer transport layer application layer presentation layer data link …
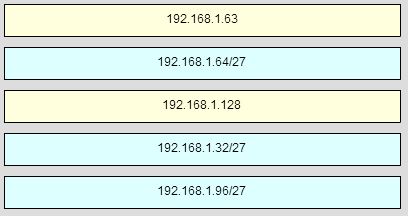
CCNA 1 Chapter 9 v5.0 Exam Answers 2015 (100%) PDF Download 1. Refer to the exhibit. How many broadcast domains are there? CCNA 1 Chapter 9 Exam Answer 001 (v5.02, 2015) 1 2 3 4 2. How many usable host addresses are there in the subnet 192.168.1.32/27? 32 …
CCNA 1 Chapter 8 v5.0 Exam Answers 2015 (100%) PDF Download 1. How many bits are in an IPv4 address? 32 64 128 256 2. Which two parts are components of an IPv4 address? (Choose two.) subnet portion network portion logical portion host portion physical portion broadcast portion …
CCNA 1 Chapter 7 v5.0 Exam Answers 2015 (100%) PDF Download 1. What is a socket? the combination of the source and destination IP address and source and destination Ethernet address the combination of a source IP address and port number or a destination IP address and port …
CCNA 1 Chapter 6 v5.0 Exam Answers 2015 (100%) PDF Download 1. When connectionless protocols are implemented at the lower layers of the OSI model, what are usually used to acknowledge the data receipt and request the retransmission of missing data? connectionless acknowledgements upper-layer connection-oriented protocols Network layer …
CCNA 1 Chapter 5 v5.0 Exam Answers 2015 (100%) PDF Download 1. Which statement is true about MAC addresses? MAC addresses are implemented by software. A NIC only needs a MAC address if connected to a WAN. The first three bytes are used by the vendor assigned OUI. …
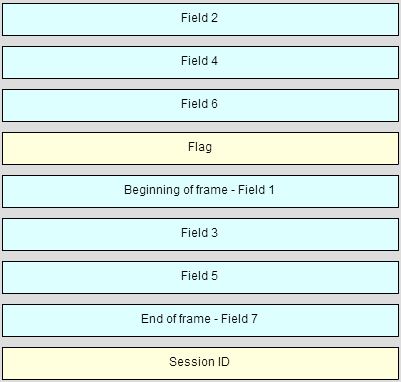
CCNA 1 Chapter 4 v5.0 Exam Answers 2015 (100%) PDF Download 1. Which layer of the OSI model is responsible for specifying the encapsulation method used for specific types of media? application transport data link physical 2. Which statement describes signaling at the physical layer? Sending the signals …