2.0.1.2 Class Activity – PPP Persuasion (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives Describe the benefits of using PPP over HDLC in a WAN. This activity can be completed individually or in small groups of …
1.3.1.1 Class Activity – WAN Device Modules (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objective Select WAN access technologies to satisfy business requirements in a small-to-medium-sized business network. Instructor Note: This activity can be completed individually …
1.2.4.3 Lab – Researching WAN Technologies (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives Part 1: Investigate Dedicated WAN Technologies and Providers Part 2: Investigate a Dedicated Leased Line Service Provider in Your Area Background / …
1.0.1.2 Class Activity – Branching Out (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objective Describe WAN access technologies available to small-to-medium-sized business networks. Instructor Note: This activity is can be completed individually or in small groups …
Endpoint Security (ESec) Final Exam Answers (Course Final Exam) 1. Which two commands could be used to check if DNS name resolution is working properly on a Windows PC? (Choose two.) ping cisco.com net cisco.com ipconfig /flushdns nslookup cisco.com nbtstat cisco.com 2. A technician notices that an application …
OS and Endpoint Security Checkpoint Exam – Endpoint Security (ESec) Module 7 – 10 Group Exam Answers (Module Group Exam 2) 1. What principle prevents the disclosure of information to unauthorized people, resources, and processes? confidentiality integrity accounting availability nonrepudiation 2. A user is proposing the purchase of …
Network Security Checkpoint Exam – Endpoint Security (ESec) Module 1 – 6 Group Exam Answers (Module Group Exam 1) 1. The employees in a company receive an email stating that the account password will expire immediately and requires a password reset within 5 minutes. Which statement would classify …
Cyber Threat Management (CyberTM) Course Final Exam Answers 1. What are three disclosure exemptions that pertain to the FOIA? (Choose three.) law enforcement records that implicate one of a set of enumerated concerns information specifically non-exempt by statue confidential business information non-geological information regarding wells national security and …
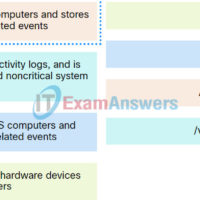
Checkpoint Exam: Incident Response – Cyber Threat Management (CyberTM) Module 6 Group Exam Answers 1. Which type of data would be considered an example of volatile data? temp files web browser cache memory registers log files 2. Keeping data backups offsite is an example of which type of …
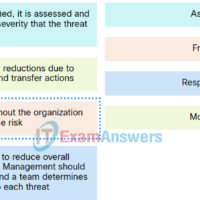
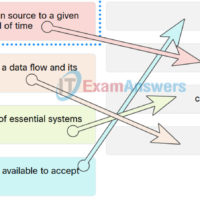
Checkpoint Exam: Vulnerability Assessment and Risk Management – Cyber Threat Management (CyberTM) Module 1 – 5 Group Exam Answers 1. A company has had several incidents involving users downloading unauthorized software, using unauthorized websites, and using personal USB devices. The CIO wants to put in place a scheme …