Section 2 Tasks
- Read today’s lesson notes (below)
- Review yesterday’s lesson notes
- Read the ICND1 cram guide
The bread-and-butter work of any Cisco engineer is installing, configuring, and troubleshooting switches. Strangely enough, this is the weakest area for many of those engineers. Perhaps some people rely on the switches’ plug-and-play capabilities, or they try to work through issues as they crop up. This “fly by the seat of your pants” mentality backfires for many engineers when there is a switching-related issue.
I suggest that you give every subject in this book just a cursory read-over to start with, and then read them again a few times over, each time making notes or highlighting the main learning points.
Today you will learn about the following:
- CSMA/CD
- VLANs
- Configuring VLANs
- Troubleshooting VLANs
This module maps to the following CCNA syllabus requirements:
- Determine the technology and media access control method for Ethernet networks
- Identify basic switching concepts and the operation of Cisco switches
- Collision domains
- Broadcast domains
- Types of switching
- CAM table
- Configure and verify initial switch configuration, including remote access management
- Cisco IOS commands to perform basic switch setup
- Verify network status and switch operation using basic utilities such as ping, Telnet, and SSH
- Describe how VLANs create logically separate networks and the need for routing between them
- Explain network segmentation and basic traffic management concepts
- Configure and verify VLANs
Switching Basics
Carrier Sense, Multiple Access with Collision Detection
Carrier sense, multiple access with collision detection (CSMA/CD) can be broken down as follows: Carrier sense means that the wire is listened to in order to determine whether there is a signal passing along it. A frame cannot be transmitted if the wire is in use. Multiple access simply means that more than one device is using the cables on the segment. Finally, collision detection means that the protocol is running an algorithm to determine whether the frames on the wire have become damaged due to hitting another frame. In Figure 2.1 below, you can see the switch port listening to the wire.

Figure 2.1 – Port Listening to the Wire
If there is a collision on the wire, the detecting device(s) send a jamming signal informing other network devices that a collison has occurred, so they should not attempt to send data onto the wire. Then, the algorithm runs and generates a random interval to wait before retransmitting. It must still wait for the wire to be clear before sending a frame. Here is how Wikipedia describe the process:
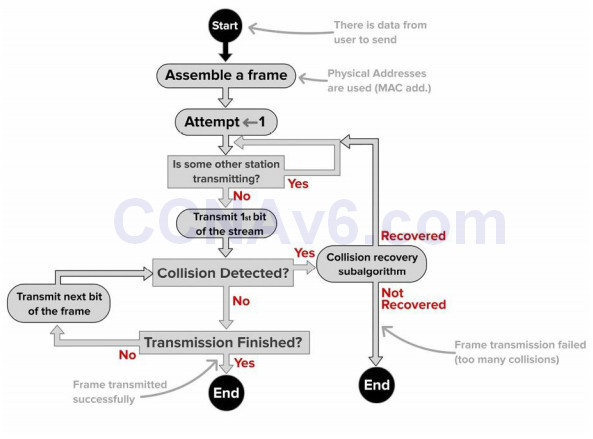
Figure 2.2 – CSMA/CD Process

Collision and Broadcast Domians
One of the main drawbacks of network hubs is that when there is a collision on the wire, that damaged frame is sent to all connected devices. One of the advantages of modern switches is that each port on the switch is considered to be a collision domain. In the event of a collision (not possible with full duplex) the damaged frame does not pass the interface. Figure 2.3 shows that a switch has been added to a small network using two hubs. The switch breaks the network into two collision domains.
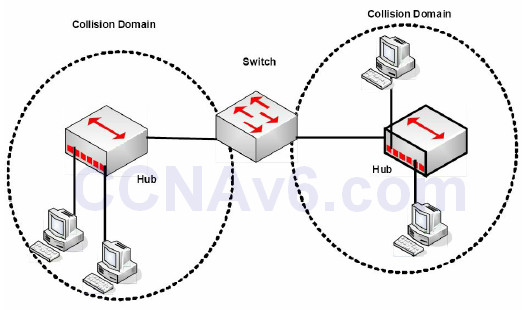
Figure 2.3 – A Switch Creates Two Collision Domains
Cisco commonly try to catch you out in the exam by asking whether switches reduce the amount of collision domains. In haste, you might be tempted to say they do but the opposite is actually the case, and this is a good thing. Switches increase the number of collision domains. It’s also worth noting that hubs can only work at half duplex due to the limitations of the technology. In Figure 2.4 below, four PCs are connected to a switch, creating four collision domains. Each PC has full use of 100Mbps bandwidth operating in full duplex.
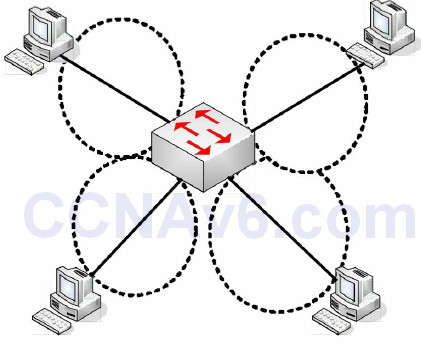
Figure 2.4 – Four Collision Domans
Switches (here we are talking about Layer 2 switches) do not separate Broadcast domains, routers do. If a switch receives a frame with a Broadcast destination address, then it must forward it out of all ports, apart from the port the frame was received on. A router is required to separate Broadcast domains. Figure 2.5 represents a small network using switches/bridges and a router to represent how collision domains are separated.
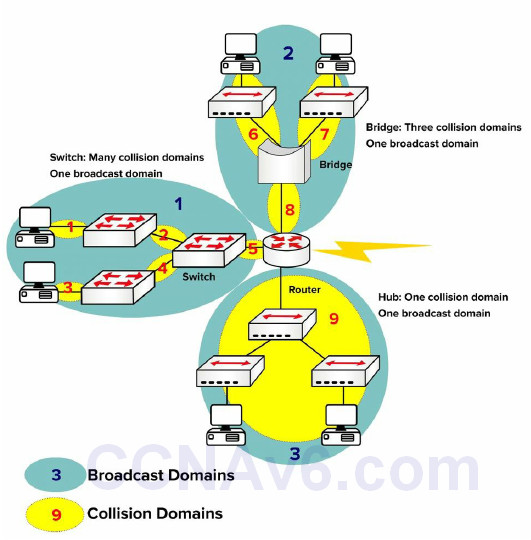
Figure 2.5 – Broadcast and Collision Domains
Auto-negotiation
You have already seen that issues can arise when you connect devices with different speeds and duplex settings. You can often upgrade one section of the network but have legacy equipment on another due to budget constraints. This can lead to duplex and speed mismatches, leading to errors and dropped frames. We will cover switch troubleshooting in more detail later.
The IEEE offer a solution to this issue with auto-negotiation, which allows devices to agree on the speed and duplex settings before passing traffic. The speed is set to the speed of the slower device. In the output below, the speed can be set manually to 10Mbps or 100Mbps, or set to auto-negotiate:
Switch(config)#int f1/0/1 Switch(config-if)#speed ? 10 Force 10 Mbps operation 100 Force 100 Mbps operation auto Enable AUTO speed configuration
You can check the settings with the show interface x command:
Switch#show int f1/0/1 FastEthernet1/0/1 is down, line protocol is down (notconnect) Hardware is FastEthernet, address is 001e.13da.c003 (bia 001e.13da.c003) MTU 1600 bytes, BW 10000 Kbit, DLY 1000 usec, reliability 255/255, txload 1/255, rxload 1/255 Encapsulation ARPA, Loopback not set Keepalive set (10 sec) Auto-duplex, Auto-speed, media type is 10/100BaseTX
Bear in mind, though, that auto-negotiation may cause issues. This is why many production networks insist on configuring ports directly as 100/full or 1000/full for GigabitEthernet. According to Cisco:
Auto-negotiation issues can result from nonconforming implementation, hardware incapabilities, or software defects. When NICs or vendor switches do not conform exactly to the IEEE specification 802.3u, problems can result. Hardware incompatibility and other issues can also exist as a result of vendor-specific advanced features, such as autopolarity or cable integrity, which are not described in IEEE 802.3u for 10/100 Mbps autonegotiation (Cisco.com).
Switching Frames Switches
exist to switch frames (i.e., transport a frame from an incoming interface to the correct outgoing interface). Broadcast frames are switched out of all interfaces (except the interface on which they were received), as are frames with an unknown destination (not in the MAC table). In order to achieve this function, a switch performs three actions:
- Forwarding or filtering (dropping) frames based on destination MAC addresses
- Learning MAC addresses from incoming frames
- Using STP to prevent Layer 2 loops (STP will be covered in ICND2 Section 31)
In Figure 2.6 below, the switch filters the frame from leaving interface F0/2 and correctly forwards it out of F0/3 when sourcing from Host A (F0/1) destined for Host C:
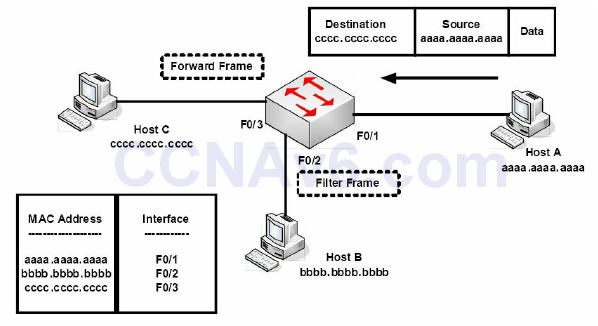
Figure 2.6 – Frame Filtering
If the destination address was not in the MAC address table, then the switch would have flooded the frame out of all interfaces, except the interface it was received on. The switch will also store MAC addresses for devices connected to another switch; however, the interface name will remain the same, so multiple MAC addresses will be listed with the same exit interface. This is a useful way to find a device on a network you are not familiar with. Figure 2.7 below illustrates this concept:
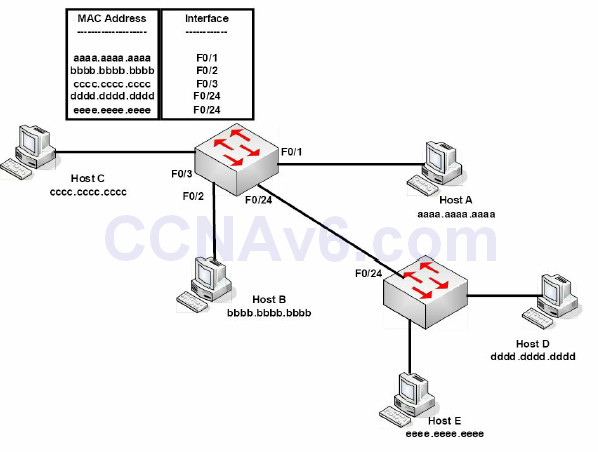
Figure 2.7 – Multiple MAC Addresses on the Same Interface
Any delay in passing traffic is known as latency. Cisco switches offer three ways to switch the traffic, depending upon how thoroughly you want the frame to be checked before it is passed on. The more checking performed, the more latency you will introduce to the switch. The three switching modes to choose from are:
- Cut-through
- Store-and-forward (default on modern switches)
- Fragment-free
Cut-through
Cut-through switching is the fastest switching method, meaning it has the lowest latency. The incoming frame is read up to the destination MAC address. Once it reaches the destination MAC address, the switch then checks its CAM table for the correct port to forward the frame out of and sends it on its way. There is no error checking, so this method gives you the lowest latency. The price, however, is that the switch will forward any frames containing errors.
The process of switching modes can best be described by using a metaphor. You are the bouncer at a nightclub and are asked to make sure that everyone who enters has a picture ID – you are not asked to make sure the picture matches the person, only that the ID has a picture. With this method of checking, people are surely going to move quickly to enter the establishment. This is how cut-through switching works.
Store-and-forward
Here, the switch reads the entire frame and copies it into its buffers. A cyclic redundancy check (CRC) takes place to check the frame for any errors. If errors are found, the frame is dropped. Otherwise, the switching table is examined and the frame forwarded. Store-and-forward ensures that the frame is at least 64 bytes but no larger than 1518 bytes. If the frame is smaller than 64 bytes or larger than 1518 bytes, then the switch will discard the frame.
Now imagine that once again you are the bouncer at a nightclub, only this time you have to make sure that the picture matches the person, and you must write down the name and address of everyone before they can enter. Checking IDs this way causes a great deal of delay, and this is how the store-and-forward method of switching works.
Store-and-forward switching has the highest latency of all the switching methods and is the default setting on the 2900 series switches.
Fragment-free (Modified Cut-through/Runt-free)
Since cut-through switching doesn’t check for errors and store-and-forward takes too long, we need a method that is both quick and reliable. Using the example of the nightclub bouncer, imagine you are asked to make sure that everyone has an ID and that the picture matches the person. With this method you have made sure everyone is who they say they are, but you do not have to take down all of their information. In switching, this is accomplished by using the fragment-free method of switching, which is the default configuration on lower-level Cisco switches.
Fragment-free switching is a modified variety of cut-through switching. The first 64 bytes of a frame are examined for any errors, and if none are detected, it will pass it on. The reasoning behind this method is that any errors are most likely to be found in the first 64 bytes of a frame.
As mentioned in the previous section, the minimum size of an Ethernet frame is 64 bytes; anything less than 64 bytes is called a “runt” frame. Since every frame must be at least 64 bytes before forwarding, this will eliminate the runts, and that is why this method is also known as “runt-free” switching.
Switching Concepts
The Need for Switches
Before switches were invented, every device on a network would receive data from every other device. Every time a frame was detected on the wire, the PC would have to stop for a moment and check the header to see whether it was the intended recipient. Imagine hundreds of frames going out on the network every minute. Every device would soon grind to a halt. Figure 2.8 below shows all the devices on the network; note that they all have to share the same bandwidth because they are connected by hubs, which only forward frames.
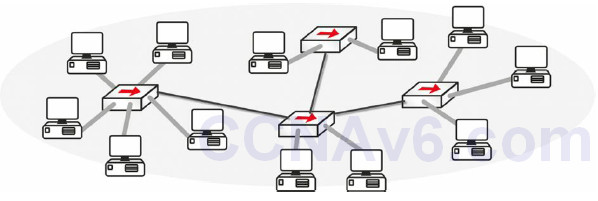
Figure 2.8 – Every Device Listens to Every Other Device
The Problem with Hubs
I mentioned before that hubs are simply multiport repeaters (see Figure 2.9). They take the incoming signal, clean it up, and then send it out of every port with a wire connected. They also create one huge collision domain.
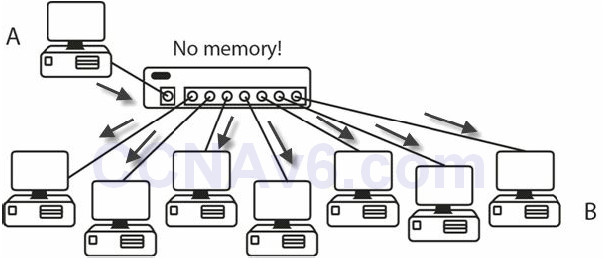
Figure 2.9 – Hubs Send the Frame Out of Every Port
Hubs are dumb devices. They have no way of storing MAC addresses, so each time Device A sends a frame to Device B, it is repeated out of every port. Switches, on the other hand, contain a memory chip known as an application-specific integrated circuit (ASIC), which builds a table listing which device is plugged into which port (see Figure 2.10). This table is held in Content Addressable Memory (CAM).
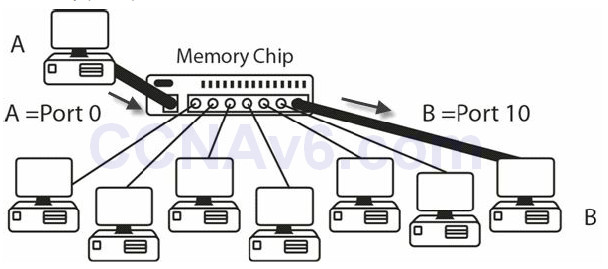
Figure 2.10 – Switches Build a Table of MAC Addresses
When first booted, a switch has no addresses stored in its CAM table (Cisco exams also refer to this as the MAC address table.) Once frames start to pass, the table builds. If no frames pass through the port for a specified period of time, then the entry ages out. In the following output, no frame has been sent through the switch yet:
Switch#show mac-address-table
Mac Address Table
-------------------------------------------
Vlan Mac Address Type Ports
---- ------ ---------- ---- ----
Switch#
There is no entry in the switch, but when you ping from one router to another (both attached to the switch), the table entry is built.
Router#ping 192.168.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.2, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 62/62/63 ms
Switch#show mac-address-table
Mac Address Table
-------------------------------------------
Vlan Mac Address Type Ports
---- ----------- -------- -----
1 0001.c74a.0a01 DYNAMIC Fa0/1
1 0060.5c55.da01 DYNAMIC Fa0/2
This entry means that any frames destined for the MAC addresses attached to FastEthernet ports 0/1 or 0/2 on the switch will be sent straight out of the relevant port. Any other frames would mean the switch would have to perform a one-off broadcast to see whether the destination devices were attached. You can see this with the period in the first of five pings above. The first ping times out whilst waiting for the switch to broadcast and receive a response from the destination router (80% success rate).
The show mac-address-table command is a very important one, so be sure to remember this both for the exam and for the real world.
You should already be aware of what a MAC address actually is, but as a brief refresher – MAC addresses are assigned to all devices to allow communication to take place at the Data Link Layer. You will see them assigned by vendors of Ethernet NICs, Ethernet interfaces on routers, and wireless devices. Here is the MAC address assigned to the Ethernet card on my laptop:
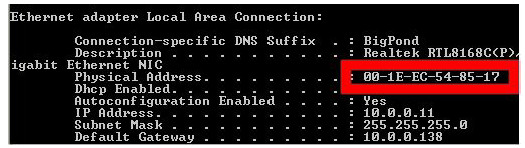
Vendors are assigned an address called an Organizationally Unique Identifier (OUI), which forms the first half of the MAC address. They are then free to create the second half of the address according to their own numbering system. A MAC address is 48 binary bits (we will cover binary and hex later on), so my address above consists of:
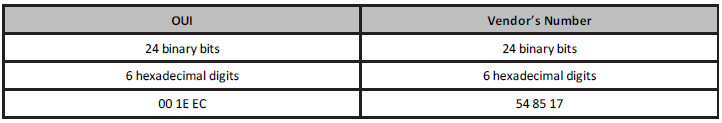
If a switch receives a frame on an interface, it will add the source MAC address to its table. If it knows the destination address, it will forward the frame out of the relevant interface. If the destination address is not known, it will broadcast the frame out of all interfaces, except the interface the frame was received on. If the switch receives a Broadcast frame (i.e., all Fs address), it will forward the frame out of all interfaces, except the interface it was received on. We cover hexadecimal addressing later. The broadcast process is illustrated in Figure 2.11 below:
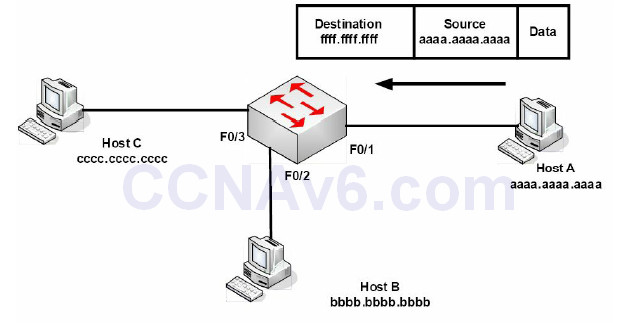
Figure 2.11 – Broadcast Frames Will Be Sent out of All Interfaces
Ethernet Frames
Ethernet has four different frame types available:
- Ethernet 802.3
- Ethernet II
- Ethernet 802.2 SAP
- Ethernet 802.2 SNAP
The first two Ethernet standards deal with the framing used for communication between network cards. They cannot identify the upper-layer protocols, which is where the 802.2 frames come in. You need only concern yourself with the 802.3 frame, which is shown below:

The IEEE 802.3 Ethernet frame consists of specific fields that have been determined by the IEEE committee:
• Preamble – synchronises and alerts the network card for the incoming data
• Start-of-frame delimiter (SFD) – indicates the start of the frame
• Destination address – the destination MAC address (can be Unicast, Broadcast, or Multicast)
• Source address – the MAC address of the sending host
• Length – defines the length of the Data field in the frame
• Data – the payload in the frame (this is the data being transferred)
• Frame-check sequence (FCS) – provides a cyclic redundancy check (CRC) on all data in the
frame
Initial Switch Configuration
You will connect to a new switch via the console port, the same as with any new router, because in order to connect via Telnet or SSH (more on these later), you will need to have at least a line or two of configuration on the switch already. Many of the initial configuration commands for the switch are the same for an initial router configuration.
It’s well worth issuing a show version command (see the output below) on any device you connect to for the first time. You will also be expected to know in the exam which show command provides which information. Most of the time you won’t have access to the emulator to get the answer, so you will have to do it from memory.
The show version command provides a lot of useful information, including:
• Switch uptime
• Model
• IOS release
• Reason for last reload
• Interfaces and type
• Memory installed
• Base MAC address
Switch>en Switch#show version Cisco IOS Software, C2960 Software (C2960-LANBASE-M), Version 12.2(25)FX, RELEASE SOFTWARE (fc1) Copyright (c) 1986-2005 by Cisco Systems, Inc. Compiled Wed 12-Oct-05 22:05 by pt_team ROM: C2960 Boot Loader (C2960-HBOOT-M) Version 12.2(25r)FX, RELEASE SOFTWARE (fc4) System returned to ROM by power-on Cisco WS-C2960-24TT (RC32300) processor (revision C0) with 21039K bytes of memory. 24 FastEthernet/IEEE 802.3 interface(s) 2 GigabitEthernet/IEEE 802.3 interface(s) 63488K bytes of flash-simulated non-volatile configuration memory. Base Ethernet MAC Address : 0090.2148.1456 Motherboard assembly number : 73-9832-06 Power supply part number : 341-0097-02 Motherboard serial number : FOC103248MJ Power supply serial number : DCA102133JA Model revision number : B0 Motherboard revision number : C0 Model number : WS-C2960-24TT System serial number : FOC1033Z1EY Top Assembly Part Number : 800-26671-02 Top Assembly Revision Number : B0 Version ID : V02 CLEI Code Number : COM3K00BRA Hardware Board Revision Number : 0x01 Switch Ports Model SW Version SW Image ------ ----- ----- ---------- --------------- * 1 26 WS-C2960-24TT 12.2 C2960-LANBASE-M Configuration register is 0xF
I know we haven’t covered VLANs yet, but for now, consider a VLAN a logical Local Area Network where devices could be anywhere on the network physically but, as far as they are concerned, they are all directly connected to the same switch. In the configuration below, by default, all ports on the switch are left in VLAN 1:
Switch#show vlan
VLAN Name Status Ports
---- ------- ------ ------------------------------1 default active Fa0/1, Fa0/2, Fa0/3, Fa0/4,
Fa0/5, Fa0/6, Fa0/7, Fa0/8,
Fa0/9, Fa0/10, Fa0/11, Fa0/12,
Fa0/13, Fa0/14, Fa0/15, Fa0/16,
Fa0/17, Fa0/18, Fa0/19, Fa0/20,
Fa0/21, Fa0/22, Fa0/23, Fa0/24,
If you want to add an IP address to the switch in order to connect to it over the network (known as a management address), you simply add an IP address to the VLAN; in this instance, it will be VLAN1:
Switch#conf t Enter configuration commands, one per line. End with CNTL/Z. Switch(config)#interface vlan1 Switch(config-if)#ip add 192.168.1.3 255.255.255.0 Switch(config-if)# ← hold down Ctrl+Z keys now Switch#show interface vlan1 Vlan1 is administratively down, line protocol is down Hardware is CPU Interface, address is 0010.1127.2388 (bia 0010.1127.2388) Internet address is 192.168.1.3/24
VLAN1 is shut down by default so you would have to issue a no shut command to open it. You should also tell the switch where to send all IP traffic because a Layer 2 switch has no ability to build a routing table; this is illustrated in the output below:
Switch#conf t Enter configuration commands, one per line. End with CNTL/Z. Switch(config)#ip default-gateway 192.168.1.1 Switch(config)#
If you have more than one switch on your network, you will want to change the default hostname of your switch so it can be identified more easily when remotely connected (see configuration line below). Imagine trying to troubleshoot five switches from a remote Telnet connection when they are all named “Switch.”
Switch(config)#hostname Switch1
If you would like to Telnet (or SSH) to the switch over the network, you will need to enable this protocol as well. Remote access to the switch is disabled by default:
Switch1#conf t Enter configuration commands, one per line. End with CNTL/Z. Switch1(config)#line vty 0 15 Switch1(config-line)#password cisco Switch1(config-line)#login
Please add the commands above to a switch, and then connect to it from another device (on the same subnet) to test your configuration. This is a fundamental CCNA topic.
VTYs are virtual ports on a router or switch used for Telnet or secure Telnet (SSH) access. They are closed until you configure an authentication method for VTY lines (the simplest way is to add a password to them and the login command). You can often see ports 0 to 4, inclusive, or 0 to 15. One way to learn how many you have available is to type a question mark after the number zero, or use the show line command, as illustrated in the output below:
Router(config)#line vty 0 ?
<1-15> Last Line number
Router#show line
Tty Typ Tx/Rx A Modem Roty AccO AccI Uses Noise Overruns Int
* 0 CTY - - - - - 0 0 0/0
1 AUX 9600/9600 - - - - - 0 0 0/0 *
2 VTY - - - - - 2 0 0/0
3 VTY - - - - - 0 0 0/0
4 VTY - - - - - 0 0 0/0
5 VTY - - - - - 0 0 0/0
6 VTY - - - - - 0 0 0/0
CTY is the console line, whilst VTY lines are for Telnet connections and AUX is the auxilliary port.
For a more secure access method, you can permit only SSH connections into the switch, which means the traffic will be encrypted. You will need a security image on your switch in order for this to work, as shown in the output below:
Switch1(config-line)#transport input ssh
Now, Telnet traffic will not be permitted into the VTY ports.
Please configure all of these commands on a switch. Just reading them will not help you recall them come exam day!
Virtual Local Area Networks (VLANs)
As you have already seen, a switch breaks a collision domain. Taken a step further, a router breaks a Broadcast domain, which means a network would look something like the following figure:
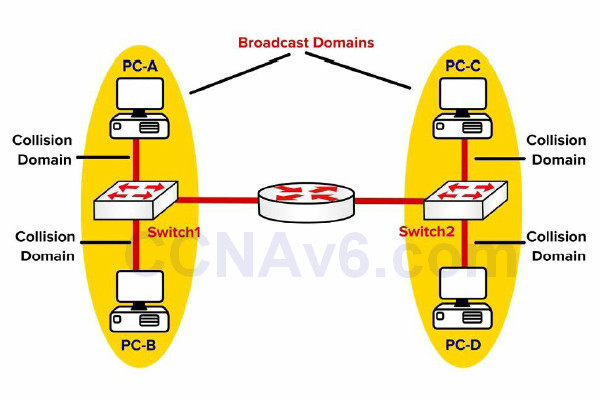
Figure 2.13 – Routers Separate Broadcast Domains
Before we continue, let’s discuss what a LAN really is. A LAN is essentially a Broadcast domain. In the network shown in Figure 2.13, if PC-A sends a Broadcast, it will be received by PC-B but not by PC-C or PC-D. This is because the router breaks the Broadcast domain. Now you can use virtual LANs (VLANs) to put switch ports into different Broadcast domains, as illustrated in the figure below:
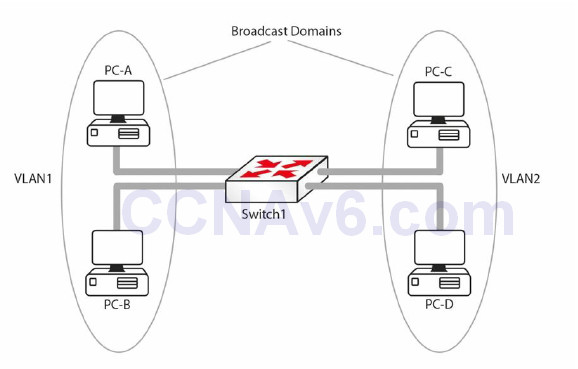
Figure 2.14 – Broadcast Domains with VLAN
In Figure 2.14, the Layer 2 network has been divided into two Broadcast domains using VLANs. Now a Broadcast sent by PC-A will be received by PC-B but not by PC-C and PC-D. Without VLANs PC-C and PC-D would have received the Broadcasts sent by PC-A. The following are some advantages of VLANs:
• Containing Broadcasts within a smaller group of devices will make the network faster.
• Saves resources on devices because they process less Broadcasts.
• Added security by keeping devices in a certain group (or function) in a separate Broadcast domain. A group, as implied here, can mean department, security level, etc. For example, devices belonging to a development or testing lab should be kept separate from the production devices.
• Flexibility in expanding a network across a geographical location of any size. For example, it does not matter where in the building a PC is. It thinks it is on the same segment of the network as any other PC configured to be in the same VLAN. In Figure 2.15 below, all hosts in VLAN 1 can talk to each other, even though they are on different floors. The VLAN is transparent or invisible to them.
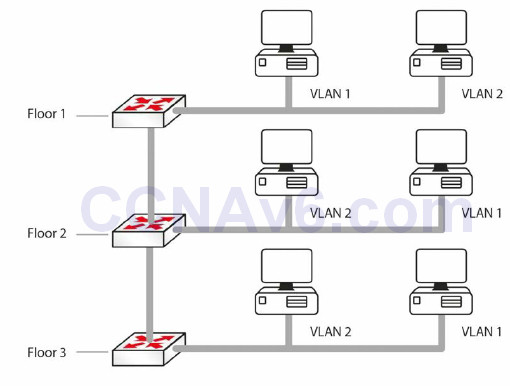
Figure 2.15 – VLANs Remove the Physical Boundaries from a LAN
VLAN Marking
Although vendors used individual approaches to create VLANs, a multi-vendor VLAN must be carefully handled to deal with interoperability issues. For example, Cisco developed the ISL standard that operates by adding a new 26-byte header, plus a new 4-byte trailer, encapsulating the original frame. To solve incompatibility problems, IEEE developed 802.1Q, a vendor-independent method to create interoperable VLANs.
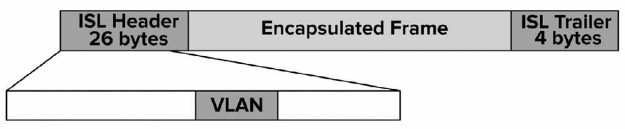
Figure 2.16 – ISL Marking Method
802.1Q is often referred to as frame tagging because it inserts a 32-bit header, called a “tag,” into the original frame, after the Source Address field, without modifying other fields. The next 2 bytes after the Source Address field hold a registered Ethernet type value of 0x8100, which implies the frame contains an 802.1Q header. The next 3 bits represent the 802.1P User Priority field and are used as Class of Service (CoS) bits in Quality of Service (QoS) techniques. The next subfield is a 1-bit Canonical Format Indicator, followed by the VLAN ID (12 bits). This gives us a total of 4096 VLANs when using 802.1Q.
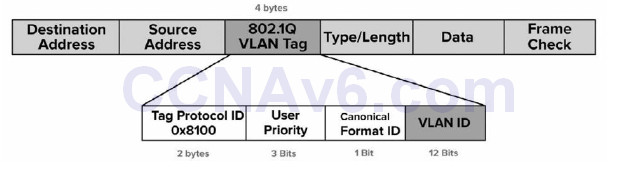
Figure 2.17 – 802.1Q Marking Method
A port that carries data from multiple VLANs is called a trunk. It can use either the ISL or the 802.1Q protocols. A special concept in the 802.1Q world is “native VLAN.” This is a particular type of VLAN in which frames are not tagged. The native VLAN’s purpose is to allow a switch to use 802.1Q trunking (multiple VLANs on a single link) on an interface, but if the other device does not support trunking, the traffic for the native VLAN can still be sent over the link. If a switch receives any untagged traffic over a trunk link, it will assume it is destined for the native VLAN. Cisco uses VLAN 1 as the default native VLAN.
VLAN Membership
There are two common ways to associate ports with VLANs – statically or dynamically.
With static VLAN assignment or configuration, the ports on the switch are configured by the network administrator to be in different VLANs, and the relevant device is then connected to the port. If the user needs to move to another part of the building, this will require the administrator to change the configuration on the switch. All switch ports belong to VLAN 1 by default.
Dynamic VLAN assignment allows devices to join a specific VLAN based on the MAC address of the device. This gives the administrator the flexibility to allow users to connect to any switch or move around the building without having to change the configuration on the switch. This is achieved using a VLAN Management Policy Server (VMPS).
Please note that since each VLAN is a different Broadcast domain, this means:
• Hosts in one VLAN cannot reach hosts in another VLAN, by default
• A Layer 3 device is needed for inter-VLAN communication (this will be covered later)
• Each VLAN needs its own subnet, for example, VLAN 1 – 192.168.1.0/24, VLAN 2 – 192.168.2.0/24
• All hosts in a VLAN should belong to the same subnet
VLAN Links
We know that one switch can have hosts connected to multiple VLANs. But what happens when traffic goes from one host to another? For example, in Figure 2.15 above, when the host in VLAN 1 on Floor 1 tries to reach the host in VLAN 1 on Floor 2, how will the switch on Floor 2 know which VLAN the traffic belongs to?
Switches use a mechanism called “frame tagging” to keep traffic on different VLANs separate. The switch adds a header on the frame, which contains the VLAN ID. In Figure 2.15, the switch on Floor 1 will tag the traffic originating from VLAN 2 and pass it to Switch 2, which will see the tag and know that the traffic needs to be kept within that VLAN. Such tagged traffic can only flow across special links called trunk links. VLAN 1 is usually designated as the native VLAN and traffic on the native VLAN is not tagged. We will cover native VLANs in more detail later.
Switch ports (within the scope of the CCNA exam) can be divided into the following:
• Access links or ports
• Trunk links or ports
• Dynamic (this will be discussed shortly)
Access Links
A switch port, which is defined as an access link, can be a member of only one VLAN. The device connected to the access link is not aware of the existence of any other VLANs. The switch will add a tag to a frame as it enters an access link from the host and remove the tag when a frame exits the switch access link towards the host. Access links are used to connect to hosts, but they can also be used to connect to a router. Trunk links are covered in the following section.
Trunking
A switch port usually will connect either to a host on the network or to another network switch, router, or server. If this is the case, then the link may need to carry traffic from several VLANs. In order to do this, each frame needs to identify which VLAN it is from. This identification method is known as frame tagging, and all frames are tagged before passing over the trunk link, apart from the native VLAN. The tag in the frame contains the VLAN ID. When the frame reaches the switch where the destination host resides, the tag is removed.
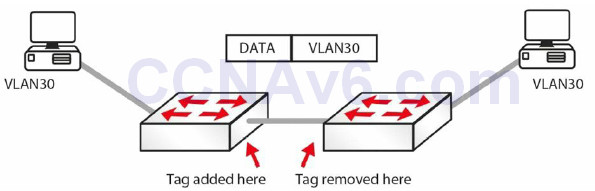
Figure 2.18 – VLAN Tagging
VLAN trunks are used to carry data from multiple VLANs. To differentiate one VLAN frame from another, all frames sent across a trunk link are specially tagged so that the destination switch knows which VLAN the frame belongs to. ISL and 802.1Q are the two primary encapsulation methods which can be used to ensure that VLANs that traverse a switch trunk link can be uniquely identified.
ISL is Cisco proprietary; however, the model tested in the CCNA exam is the 2960 switch, which only recognises 802.1Q. We cover it here for completeness and in case you have to configure an older switch model.
![]()
802.1Q differs from ISL in several ways. The first significant difference is that 802.1Q supports up to 4096 VLANs, whereas ISL supports up to 1000. Another significant difference is that of the native VLAN concept used in 802.1Q. By default, all frames from all VLANs are tagged when using 802.1Q. The only exception to this rule is frames that belong to the native VLAN, which are not tagged.
However, keep in mind that it is possible to specify which VLAN will not have frames tagged by specifying that VLAN as the native VLAN on a particular trunk link. For example, to prevent tagging of frames in VLAN 400 when using 802.1Q, you would configure that VLAN as the native VLAN on a particular trunk. IEEE 802.1Q native VLAN configuration will be illustrated in detail later.
The following summarises some features of 802.1Q:
• Supports up to 4096 VLANs
• Uses an internal tagging mechanism, modifying the original frame
• Open standard protocol developed by the IEEE
• Does not tag frames on the native VLAN; however, all other frames are tagged
The following is a short sample configuration of a switch. I have included the switchport command, which tells the switch to act as a switch port for Layer 2, as opposed to Layer 3.
Sw(config)#interface FastEthernet 0/1 Sw(config-if)#switchport Sw(config-if)#switchport mode trunk Sw(config-if)#switchport trunk encapsulation dot1q Sw(config-if)#exit
Of course, on a 2960 switch, the encapsulation command won’t be recognised because there is only one type available. You will need to set the interface as a trunking interface when connecting to another switch to allow VLANs to be tagged. The same thing goes for the switchport command. Again, I cover this because in the real world you may well have to configure a Layer 3 switch, and if we stuck strictly to the 2960 model, you may become confused, which we don’t want!
A trunk link on a switch can be in one of five possible modes:
• On – forces the port into permanent trunking mode. The port becomes a trunk, even if the
connected device does not agree to convert the link into a trunk link.
• Off – the link is not used as a trunk link, even if the connected device is set to “trunk.”
• Auto – the port is willing to become a trunk link. If the other device is set to “on” or “desirable,” then the link becomes a trunk link. If both sides are left as “auto,” then the link will never become a trunk, as neither side will attempt to convert.
• Desirable – the port actively tries to convert to a trunk link. If the other device is set to “on,” “auto,” or “desirable,” then the link will become a trunk link.
• No-negotiate – prevents the port from negotiating a trunk connection. It will be forced into an access or trunk mode as per the configuration.
Configuring VLANs
Now that you understand VLANs and trunk links, let’s configure the network shown in Figure 2.19 below. You will need to configure the switches such that the hosts on fa0/1 are in VLAN 5 and the link on port fa0/15 is a trunk link.
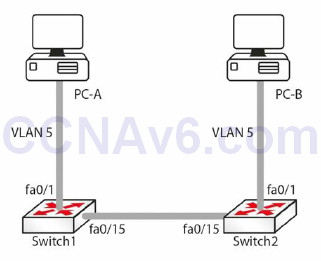
Figure 2.19 – Test Network
Before assigning ports to VLANs, the VLAN itself must be created using the vlan <vlan#> global configuration command. This will put you into VLAN Configuration mode, where a descriptive name can be given to the VLANs. Here is an example:
Switch1(config)#vlan 5 Switch1(config-vlan)#name RnD Switch2(config)vlan 5 Switch2(config-vlan)#name RnD
To see which VLANs exist on a switch, use the show vlan command. The output will be similar to the one below:
Switch1#show vlan VLAN Name Status Ports ---- -------- ------- -------------------------------------------- 1 default active Fa0/1, Fa0/2, Fa0/3, Fa0/4 Fa0/5, Fa0/6, Fa0/7, Fa0/8 Fa0/9, Fa0/10, Fa0/11, Fa0/12, Fa0/13 Fa0/14, Fa/15, Fa0/16, Fa0/17, Fa0/18 ... [Truncated Output] ... 5 RnD active ... [Truncated Output]
Let’s assign port fa0/1 to VLAN 5 using the switchport access vlan [vlan#] interface configuration command:
Switch1(config)#int fa0/1 Switch1(config-if)#switchport access vlan 5 Switch2(config)#int fa0/1 Switch2(config-if)#switchport access vlan 5
On a Layer 3-capable switch, such as the 3560, you would have to set the port manually to
access it with the switchport mode access command before putting it into a VLAN. Now let’s
look at the output for the show vlan command:
Switch1#show vlan VLAN Name Status Ports ---- ---- ----- -------------------------------------------- 1 default active Fa0/2, Fa0/3, Fa0/4, Fa0/5, Fa0/6, Fa0/7, Fa0/8, Fa0/9, Fa0/10, Fa0/11, Fa0/12, Fa0/13, Fa0/14, Fa/15, Fa0/16, Fa0/17, Fa0/18 ... [Truncated Output] ... 5 RnD active Fa0/1 ... [Truncated Output]
Note that fa0/1 is now assigned to VLAN 5. Let’s configure interface fa0/15 on both switches as trunk links. It should be noted here that the default mode on (the 3550 model) switch ports is desirable (on the 3560 model it’s auto, so check your platform notes). Dynamic Trunking Protocol (DTP) will cause fa0/15 on both switches to become ISL trunk links. We will cover DTP in the next lesson, but I wanted to mention it here briefly. This can be verified using the show interface trunk command:
Switch1#show interface trunk Port Mode Encapsulation Status Native vlan Fa0/15 desirable n-isl trunking 1
Note that the mode is desirable and the encapsulation is ISL (“n” stands for negotiated).
The following output shows how to configure the trunk to use ISL trunking:
Switch1(config)#interface fa0/15 Switch1(config-if)#switchport trunk encapsulation isl Switch1(config-if)#switchport mode trunk Switch2(config)#interface fa0/15 Switch2(config-if)#switchport trunk encapsulation isl Switch2(config-if)#switchport mode trunk
The switchport trunk encapsulation command sets the trunking protocol on the port, and the switchport mode trunk command sets the port to trunking. The output for the show interface trunk command will now look like this:
Switch2#show interface trunk Port Mode Encapsulation Status Native vlan Fa0/15 on isl trunking 1
Note that the encapsulation is now ISL instead of N-ISL. This is because this time the protocol was not negotiated but configured on the interface.
IMPORTANT NOTE: Trunk encapsulation needs to be configured on the switch port before setting it to trunk mode. Please note that this does not apply to switch model 2960 (currently used for the CCNA syllabus), which can only use dot1q (another name for 802.1Q) encapsulation. For this reason, the switchport trunk encapsulation command will not work on the 2960 switch.
Similarly, you can configure the switch port to use 802.1Q instead of ISL, as illustrated in the output below:
Switch1(config)#interface fa0/15 Switch1(config-if)#switchport trunk encapsulation dot1q Switch1(config-if)#switchport mode trunk Switch2(config)#interface fa0/15 Switch2(config-if)#switchport trunk encapsulation dot1q Switch2(config-if)#switchport mode trunk
The show interface trunk output now looks like this:
Switch2#show interface trunk Port Mode Encapsulation Status Native vlan Fa0/15 on 802.1q trunking 1
Note that the native VLAN is 1. That is the default native VLAN on an 802.1Q trunk and it can be changed using the switchport trunk native vlan <vlan#> command. The native VLAN of each port on the trunk must match. This command is part of the CCNA syllabus and is considered a security measure.
IMPORTANT NOTE: Switches remember all VLAN info, even when reloaded. If you want your switch to boot with a blank configuration, then you will need to issue the delete vlan.dat command on your switch, as shown in the output below. This applies to live switches only, not switch emulators such as Packet Tracer.
SwitchA#dir flash: Directory of flash:/ 1 -rw- 3058048 <no date> c2960-i6q4l2-mz.121-22.EA4.bin 2 -rw- 676 <no date> vlan.dat 64016384 bytes total (60957660 bytes free) SwitchA# SwitchA#delete vlan.dat Delete filename [vlan.dat]? Delete flash:/vlan.dat? [confirm] SwitchA#dir flash: Directory of flash:/ 1 -rw- 3058048 <no date> c2960-i6q4l2-mz.121-22.EA4.bin 64016384 bytes total (60958336 bytes free) SwitchA#
Basic Switching Troubleshooting
In theory, once a device is configured and working it should stay that way, but, often, you will be working on a network which you didn’t configure, or you will be working on a shift pattern supporting many unfamiliar networks on which changes have been made, causing one or more issues for the company. I suggest you revist this section after completing a few labs in this guide as the days progress.
Common Switch Issues
Can’t Telnet to Switch
The first question is was Telnet ever working? If it was and is no longer, then perhaps somebody has made a change on the switch, reloaded it, and lost the configuration, or a device is now blocking Telnet traffic somewhere on the network:
Switch#telnet 192.168.1.1 Trying 192.168.1.1 ...Open [Connection to 192.168.1.1 closed by foreign host]
The first thing to check is whether Telnet has actually been enabled on the switch (see the output below). Around 80% of errors on the network are due to silly mistakes or oversights, so never presume anything, and check out everything personally, rather than relying on other people’s words.
A simple show run command will reveal the switch configuration. Under the vty lines, you will see whether Telnet has been enabled. Note that you will need to have the login or login local (or configured AAA, which is beyond the scope of the CCNA exam) command under the vty lines and the password command, as shown below:
line vty 0 4 password cisco login line vty 5 15 password cisco login
The login local command tells the switch or router to look for a username and password configured on it, as illustrated in the output below:
Switch1#sh run Building configuration... Current configuration : 1091 bytes! version 12.1 hostname Switch1 username david privilege 1 password 0 football line vty 0 4 password cisco login local line vty 5 15 password cisco login local ... [Truncated Output]
Can’t Ping the Switch
Find out why the person wants to ping the switch in the first place. If you do want to ping a switch, there needs to be an IP address configured on it; in addition, the switch needs to know how to get traffic back out (the default gateway).
Can’t Ping through the Switch
If a ping through the switch is unsuccessful, then check to ensure that the end devices are in
the same VLAN. Each VLAN is considered a network and for this reason must have a different
address range from any other VLAN. In order for one VLAN to reach another, a router must
route the traffic.
Interface Issues
By default, all router interfaces are closed to traffic and switch interfaces are open. If you find
that your switch has had its interfaces administratively shut, to open it, the interface must be
set with the no shut interface-level command:
Switch1(config)#int FastEthernet0/3 Switch1(config-if)#no shut
Layer 2 interfaces can be set in three modes: trunk, access, or dynamic. Trunk mode lets the switch connect to another switch or a server. Access mode is for an end device, such as a PC or a laptop. Dynamic mode lets the switch detect which setting to select.
The default on platforms such as the 3550 model switch is usually dynamic desirable, but please check your model’s settings and release notes on Cisco.com. For the CCNA exam, you will be asked to configure a 2960 model switch. It will select the mode dynamically unless you hard set it to trunk or access mode:
Switch1#show interfaces switchport Name: Fa0/1 Switchport: Enabled Administrative Mode: dynamic auto
The default can easily be changed, as shown in the output below:
Switch1#conf t Enter configuration commands, one per line. End with CNTL/Z. Switch1(config)#int FastEthernet0/1 Switch1(config-if)#switchport mode ? access Set trunking mode to ACCESS unconditionally dynamic Set trunking mode to dynamically negotiate access or trunk mode trunk Set trunking mode to TRUNK unconditionally Switch1(config-if)#switchport mode trunk %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/1, changed state to down Switch1(config-if)#^Z Switch1# %SYS-5-CONFIG_I: Configured from console by console Switch1#show interfaces switchport Name: Fa0/1 Switchport: Enabled Administrative Mode: trunk Operational Mode: trunk
More Interface Issues
Switch port default settings are auto-detect duplex and auto-detect speed. If you plug a 10Mbps device into a switch running at half duplex (if you could even find such a device), then the port should detect this and work. This isn’t always the case, though, so the generic advice is to hard set the switch port speed and duplex, as illustrated in the output below:
Switch1#show interfaces switchport Name: Fa0/1 Switchport: Enabled Administrative Mode: dynamic auto Switch1#show interface FastEthernet0/2 FastEthernet0/2 is up, line protocol is up (connected) Hardware is Lance, address is 0030.f252.3402 (bia 0030.f252.3402) BW 100000 Kbit, DLY 1000 usec, reliability 255/255, txload 1/255, rxload 1/255 Encapsulation ARPA, loopback not set Keepalive set (10 sec) Full-duplex, 100Mb/s Switch1(config)#int fast 0/2 Switch1(config-if)#duplex ? auto Enable AUTO duplex configuration full Force full-duplex operation half Force half-duplex operation Switch1(config-if)#speed ? 10 Force 10Mbps operation 100 Force 100Mbps operation auto Enable AUTO speed configuration
Signs of duplex mismatches (apart from error messages) include input and CRC errors on the interface, as illustrated in the output below. Please also see the Layer 1 and Layer 2 Troubleshooting sections in Section 15 of the ICND1 section.
Switch#show interface f0/1 FastEthernet0/1 is down, line protocol is down (disabled) Hardware is Lance, address is 0030.a388.8401 (bia 0030.a388.8401) BW 100000 Kbit, DLY 1000 usec, reliability 255/255, txload 1/255, rxload 1/255 Encapsulation ARPA, loopback not set Keepalive set (10 sec) Half-duplex, 100Mb/s input flow-control is off, output flow-control is off ARP type: ARPA, ARP Timeout 04:00:00 Last input 00:00:08, output 00:00:05, output hang never Last clearing of “show interface” counters never Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0 Queueing strategy: fifo Output queue :0/40 (size/max) 5 minute input rate 0 bits/sec, 0 packets/sec 5 minute output rate 0 bits/sec, 0 packets/sec 956 packets input, 193351 bytes, 0 no buffer Received 956 broadcasts, 0 runts, 0 giants, 0 throttles 755 input errors, 739 CRC, 0 frame, 0 overrun, 0 ignored, 0 abort 0 watchdog, 0 multicast, 0 pause input 0 input packets with dribble condition detected 2357 packets output, 263570 bytes, 0 underruns 0 output errors, 0 collisions, 10 interface resets 0 babbles, 0 late collision, 0 deferred 0 lost carrier, 0 no carrier 0 output buffer failures, 0 output buffers swapped out
Hardware Issues
As with any electrical device, ports on a switch can fail or work only part of the time, which is harder to troubleshoot. Engineers often test the interface by plugging a known working device into another port on the switch. You can also bounce a port, which means applying the shut command and then the no shut command to it. Swapping the Ethernet cable is also a common troubleshooting step. Other common switch problems and solutions are shown in Figure 2.20 below.
Please check the documentation for your switch because, as well as featuring system and port LEDs, each port can display flashing or solid red, amber, and green, indicating normal function or port/system issues.
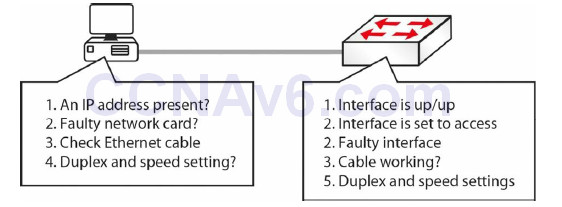
Figure 2.20 – Common Switch Problems and Solutions
VLAN Assignment Issues
Networks in small environments are relatively easy to manage because a limited number of features need to be implemented in order to achieve the business’s goals. However, in an enterprise environment you won’t be using small workgroup switches and SOHO devices. Rather, you will use high-end devices that are capable of optimising the traffic flow by offering a number of advanced functionalities.
One particular feature that might be configured in such an environment is logically separating different network areas using VLANs. Issues can appear when you have configuration issues related to a particular VLAN and this can become difficult to troubleshoot. One way of doing this is analysing the entire configuration on the switch and trying to identify the problem.
VLAN-related problems are usually detected by observing the lack of connectivity between network hosts (e.g., a user cannot ping a server), even though Layer 1 seems to operate without problems. One important characteristic of VLAN-related problems is that they do not generate any performance degradation on the network. If you misconfigure a VLAN, the connection will simply not work, especially considering that they usually separate IP subnets so that only devices within the same VLAN will be able to communicate with each other.
The first step in troubleshooting VLAN problems is to review the documentation and the logical diagrams developed in the design phase so you can identify the span area for each VLAN, including the associated devices and ports on each switch. The next step is to inspect each switch configuration and try to find the problem by comparing them with the documented solution.
You should also verify the IP addressing scheme. If you are statically assigning IP addresses to devices, you may want to go back and check the device to ensure that it has the proper IP address and subnet mask combination. If there are any mistakes in the IP addressing scheme, like configuring devices on the wrong network or with a wrong subnet mask/default gateway, then you are going to have connectivity problems, even though you have the correct VLAN configured on the switch.
You will also want to confirm that the trunk configuration on the switches is correct. If you have multiple switches, there are usually uplinks between them and VLANs carried across those uplinks. These inter-switch links are often configured as trunks to allow communication across multiple VLANs. The VLAN has to be a member of the trunk group if data is to be sent from one switch to the other, so you also have to make sure that the switch configuration on both sides is set up properly.
Finally, if you move a device to another VLAN, you will have to make changes to both the switch and the client because the client will have a different IP address in a different IP subnet as a result of that move.
If you follow all of these VLAN troubleshooting methods, you can be sure that when plugging in devices for the first time or moving them from VLAN to VLAN, you will have the exact connectivity you desired.
Section 2 Questions
1. Switches contain a memory chip known as an _______, which builds a table listing which device is plugged into which port.
2. The _______ _______-_______-_______ command displays a list of which MAC addresses are connected to which ports.
3. Which two commands add an IP address to the VLAN?
4. Which commands will enable Telnet and add a password to the switch Telnet lines?
5. How do you permit only SSH traffic into your Telnet lines?
6. What is the most likely cause of Telnet to another switch not working?
7. Switches remember all VLAN info, even when reloaded. True or False?
8. A switch interface can be in which of three modes?
9. How do you set a switch to be in a specific mode?
10. Which commands will change the switch duplex mode and speed?
Section 2 Answers
1. ASIC.
2. show mac-address-table.
3. The interface vlan x command and the ip address x.x.x.x command.
4.
Switch1(config)#line vty 0 15
Switch1(config-line)#password cisco
Switch1(config-line)#login
5. Use the Switch1(config-line)#transport input ssh command.
6. The authentication method is not defined on another switch.
7. True.
8. Trunk, access, or dynamic mode.
9. Apply the switchport mode <mode> command in Interface Configuration mode.
10. The duplex and speed commands.
Section 2 Lab
Switching Concepts Lab
Please log on to a Cisco switch and enter the commands explained in this module. This should
include:
• Configure different port speeds/auto-negotiation on various switch ports
• Verify the port parameters with the show run and the show interface commands
• Issue a show version command to see the hardware details and IOS version
• Verify the switch MAC address table
• Configure a password on the VTY lines
• Define a couple of VLANs and assign names to them
• Assign a VLAN to a port configured as switchport access
• Configure a port as a trunk (ISL and 802.1Q) and assign VLANs to the trunk
• Verify VLAN configuration using the show vlan command
• Verify interface trunking and VLAN configuration using the show interface switchport command and the show interface trunk command
• Delete the “vlan.dat” file
