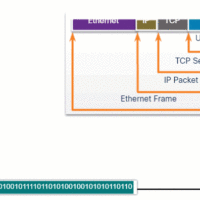
5.0 Introduction 5.0.1 Why Should I Take this Module? We all communicate on networks daily. Looking at social media, streaming video, or researching information on the internet are common activities that we normally don’t think much about. However, numerous technological processes are at work to bring us the …
4.0 Introduction 4.0.1 Why Should I Take this Module? Linux is an open-source operating system that is fast, powerful, and highly customizable. It is built for network use as either a client or server. Linux is well-loved by a large community of users, including cybersecurity personnel. Study this …
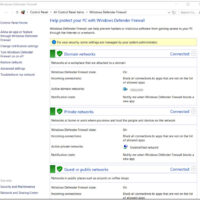
3.0 Introduction 3.0.1 Why Should I Take this Module? From its humble beginnings over 35 years ago in 1985, the Windows operating system has seen many iterations; from Windows 1.0 to today’s current desktop version, Windows 10, and server version, Windows Server 2019. This module covers some of …
2.0 Introduction 2.0.1 Why Should I Take this Module? If you are taking this course, you may be considering a career in CyberOps security. What technologies do you need to be aware of? What types of jobs are available? Where can you find those jobs? Keep reading to …
1.0 Introduction 1.0.1 First Time in This Course CyberOps Associate v1.0 covers knowledge and skills needed to successfully handle the tasks, duties, and responsibilities of an associate-level Security Analyst working in a Security Operations Center (SOC). Upon completion of the CyberOps Associate v1.0 course, students will be able …
CyberOps Associate (Version 1.0) – CyberOps Associate (200-201) Certification Practice Exam 1. Match the definition to the Microsoft Windows term. (Not all options are used.) Case 2 2. What are two motivating factors for nation-state sponsored threat actors? (Choose two.) industrial espionage showing off their hacking skill disruption …
28.4.12 Lab – Incident Handling (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives Apply your knowledge of security incident handling procedures to formulate questions about given incident scenarios. Background / Scenario Computer security incident response has …
27.2.16 Lab – Investigating an Attack on a Windows Host (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives In this lab you will: Part 1: Investigate the Attack with Sguil Part 2: Use Kibana to Investigate …
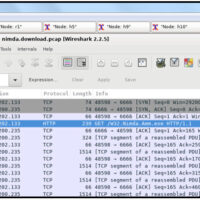
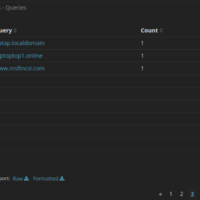
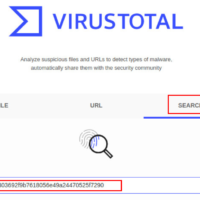
27.2.15 Lab – Investigating a Malware Exploit (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives In this lab you will: Part 1: Use Kibana to Learn About a Malware Exploit Part 2: Investigate the Exploit with …
27.2.14 Lab – Isolate Compromised Host Using 5-Tuple (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives In this lab, you will review logs that were gathered during the exploitation of a documented vulnerability to determine the …