Instructor Planning Guide
Activities
What activities are associated with this chapter?
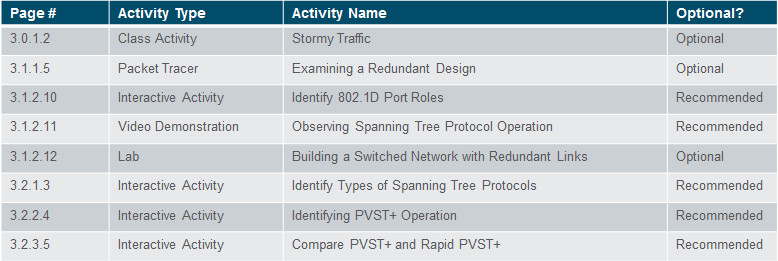
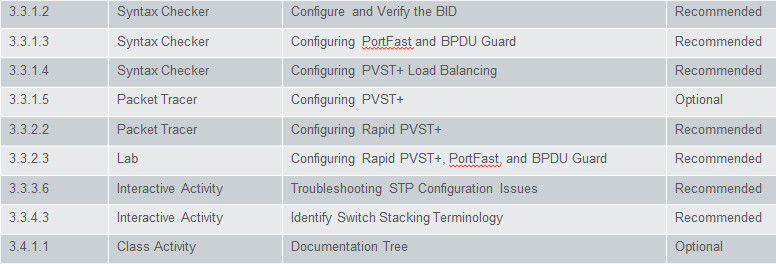
Assessment
Students should complete Chapter 3, “Assessment” after completing Chapter 3.
Quizzes, labs, Packet Tracers and other activities can be used to informally assess student progress.
Sections & Objectives
3.1 Spanning Tree Concepts
Build a simple switched network with redundant links.
Explain common problems in a redundant, switched network.
Build a simple, switched network using STP.
3.2 Varieties of Spanning Tree Protocols
Explain how different varieties of spanning tree protocols operate.
Describe the different spanning tree varieties.
Explain how PVST+ operates.
Explain how Rapid PVST+ operates.
3.3 Spanning Tree Configuration
Implement PVST+ and Rapid PVST+ in a switched LAN environment.
Configure PVST+ in a switched LAN environment.
Configure Rapid PVST+ in a switched LAN environment.
Analyze common STP configuration issues.
Chapter 3: STP
3.1 – STP Operation
3.1.1 – Spanning Tree
3.1.1.1 – Redundancy at OSI Layers 1 and 2
Switched networks commonly have redundant paths and
even redundant links between the same two devices.
- Redundant paths eliminate a single point of failure in order to improve reliability and availability.
- Redundant paths can cause physical and logical Layer 2 loops.
Spanning Tree Protocol (STP) is a Layer 2 protocol that
helps especially when there are redundant links.
Layer 2 loop issues
- Mac database instability – copies of the same frame being received on different ports.
- Broadcast storms – broadcasts are flooded endlessly causing network disruption.
- Multiple frame transmission – multiple copies of unicast frames delivered to the same destination.
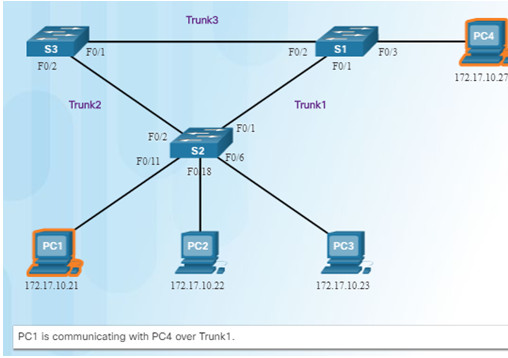
3.1.1.2 – Issues with Layer 1 Redundancy: MAC Database Instability
Ethernet frames do not have a time to live (TTL) field like the Layer 3 IP header has. This means that Ethernet has no mechanism to drop frames that propagate endlessly. This can result in MAC database instability.
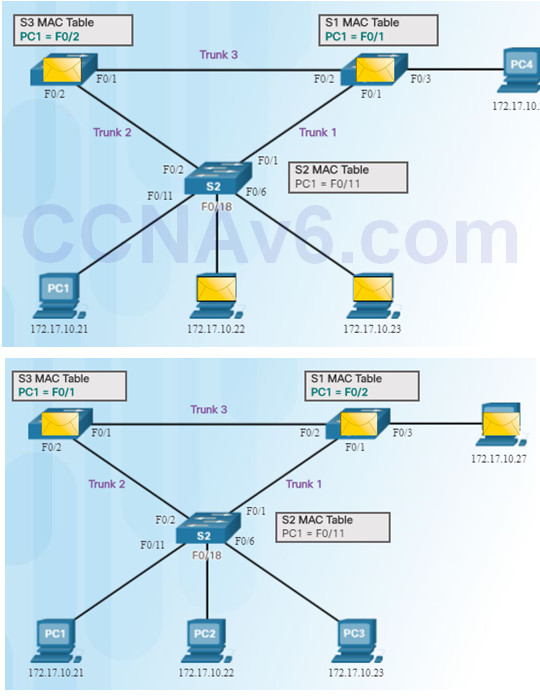
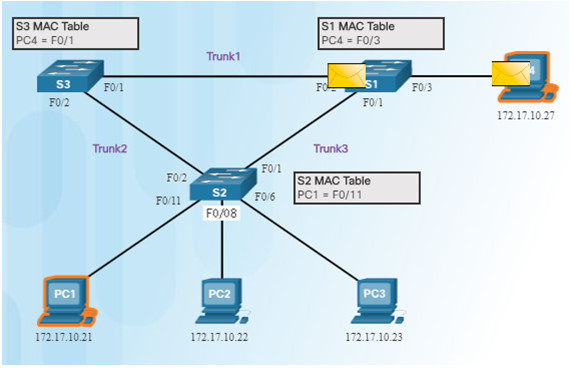
1. PC1 sends a broadcast frame to S2.
2.S2 updates the MAC address table for PC1’s MAC address on port 11.
3.S2 forwards the frame out all ports except the port the frame came in on. S1 and S3 receive the frame on a trunk and update their own MAC address tables that PC1 is reachable through the trunk port.
4.S1 and S3 send the frame out all ports except the port it came in on.
5.When S1 sends the frame out port 2 (Trunk 3), S3 updates the MAC address table to reflect that PC1 is now reachable through port 1.
- A host caught in a network loop is not accessible to other hosts.
- Due to constant changes in the MAC address table, Switches S3
and S1 do not know which port to forward frames.
3.1.1.3 – Issues with Layer 1 Redundancy: Broadcast Storms
Broadcast storm – so many broadcast frames in a Layer 2 loop that use all available bandwidth and make the network unreachable for legitimate network traffic.
- Causes a denial of service (DoS)
- Can develop in seconds and bring the network down
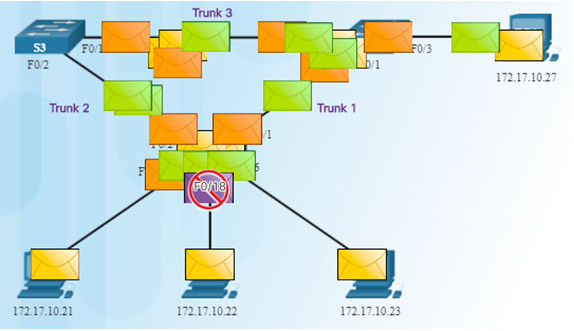
3.1.1.4 – Issues with Layer 1 Redundancy: Duplicate Unicast Frames
An unknown unicast frame is when the switch does not have the destination MAC address in its MAC address table and has to broadcast the frame out all ports except the port the frame was received on (the ingress port).
Unknown unicast frames sent onto a looped network can result in duplicate frames arriving at the destination device.
- PC1 sends a frame destined for PC4.
- S2 does not have PC4’s MAC address in the MAC address table so it forwards the frame out all ports including the trunks that lead to S1 and S3. S1 sends the frame to PC4. S3 also sends a copy of the frame over to S1 which delivers the same frame again to PC4.
3.1.1.5 – Packet Tracer – Examining a Redundant Design
3.1.1.5 Packet Tracer – Examining a Redundant Design
3.1.2 – STP Operation
3.1.2.1 – Spanning Tree Algorithm: Introduction
The Spanning Tree Protocol (STP) creates one logical path through the switch network (all destinations on the network).
- Blocks redundant paths that could cause a loop.
- STP sends bridge protocol data units (BPDUs) between Layer 2 devices in order to create the one logical path.
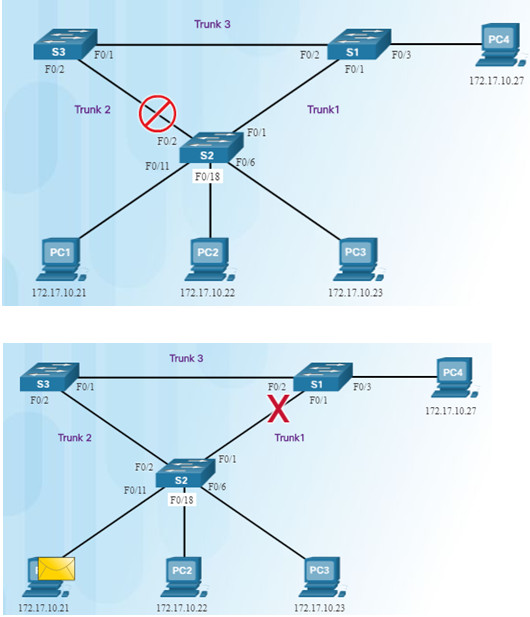
A port on S2 is blocked so traffic can only flow one way between any two devices.
When Trunk1 fails, the blocked port on S2 is unblocked and traffic can flow between S2 and S3.
3.1.2.2 – Spanning Tree Algorithm: Port Roles
Root bridge – one Layer 2 device in a switched network.
Root port – one port on a switch that has the lowest
cost to reach the root bridge.
Designated port – selected on a per-segment (each
link) basis, based on the cost to get back to root bridge
for either side of the link.
Alternate port – (RSTP only) backup port for the designated port when the other side is not a root port.
Backup port – (RSTP only) backup port for the root port.
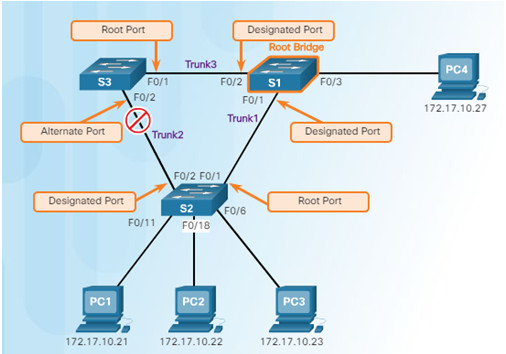
3.1.2.3 – Spanning Tree Algorithm: Root Bridge
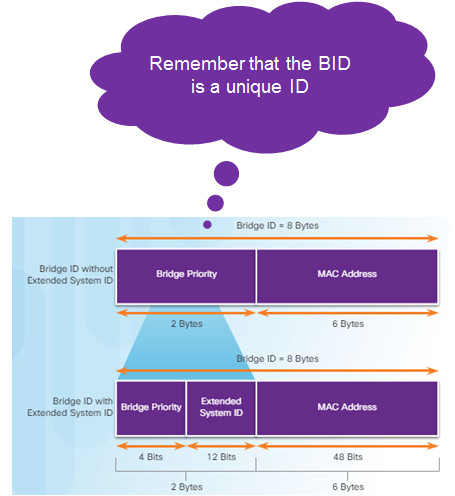
Lowest bridge ID (BID) becomes root bridge
- Originally BID had two fields: bridge priority and MAC address
- Bridge priority default is 32,768 (can change)
- Lowest MAC address (if bridge priority is not changed) becomes determinant for root bridge.
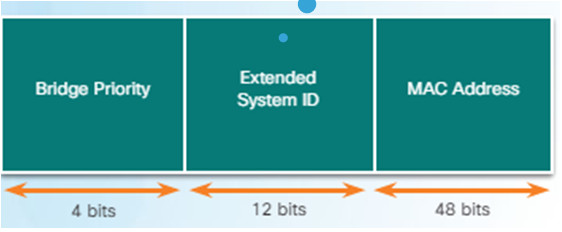
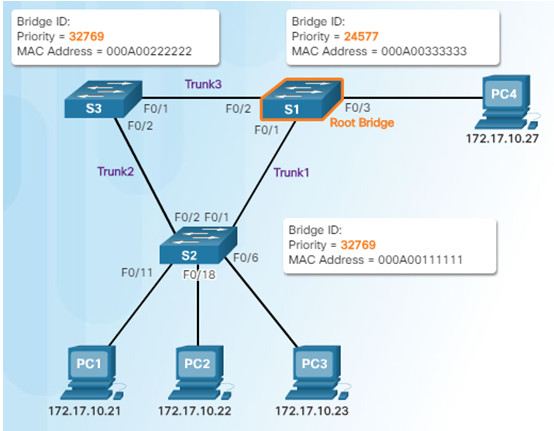
3.1.2.4 – Spanning Tree Algorithm: Root Path Cost
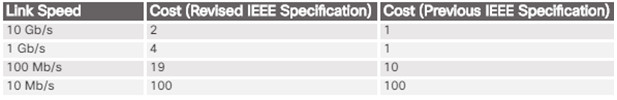
Root path cost is used to determine the role of the port and whether or not traffic is blocked.
Can be modified with the spanning-tree cost interface command.
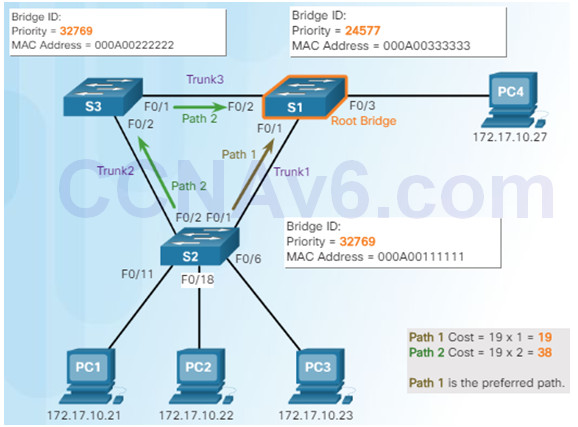
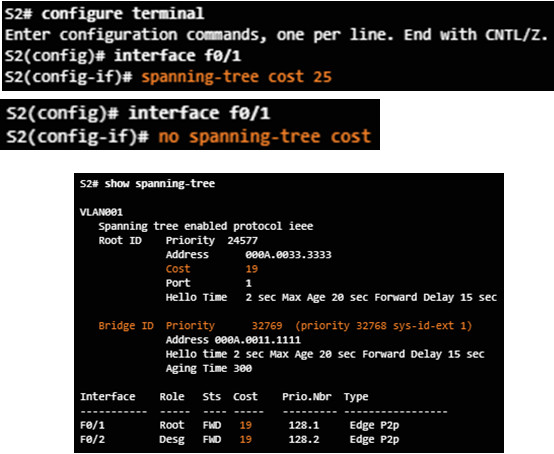
3.1.2.5 – Port Role Decisions for RSTP
S1 is root bridge
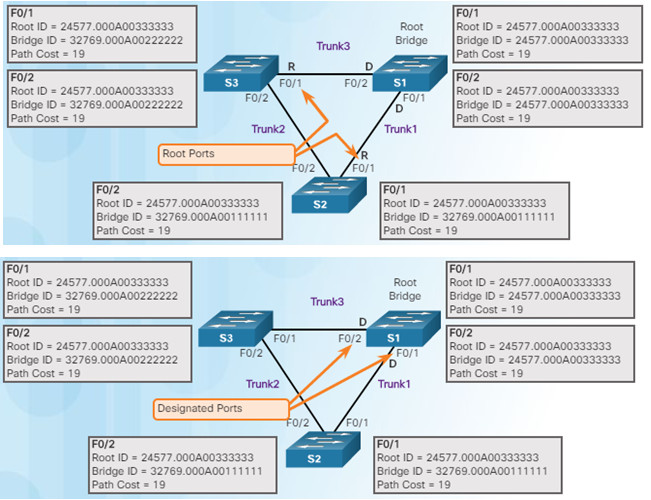
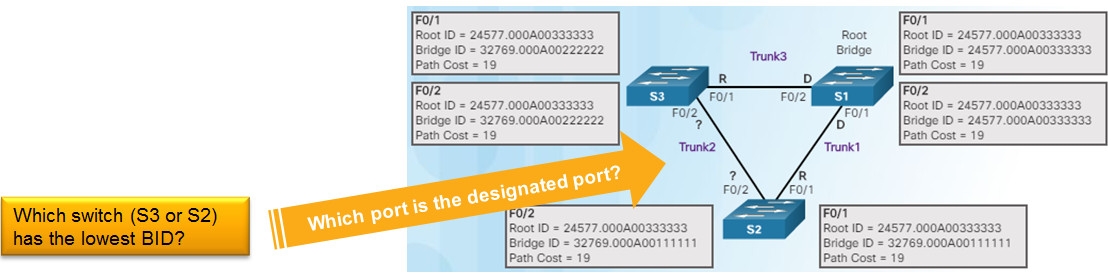
After S3 and S2 exchange BPDUs, STP determines that the F0/2 port on S2 becomes the designated port and the S3 F0/2 port becomes the alternate port, thus going into the blocking state so there is only one path through the switched network.
3.1.2.6 – Determine Designated and Alternate Ports
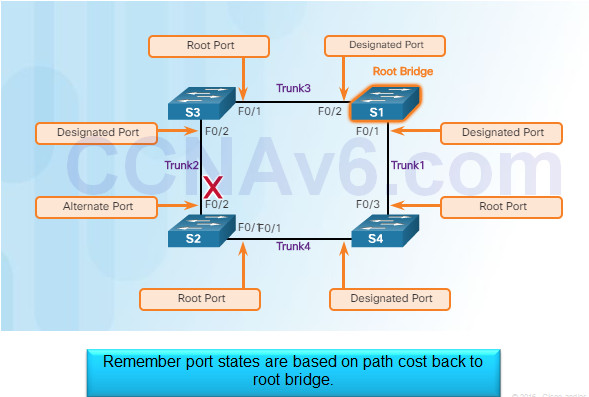
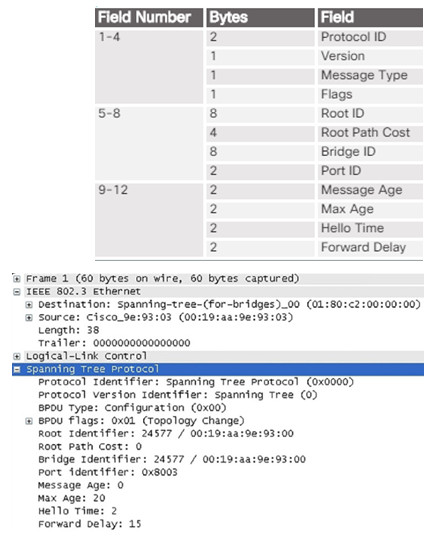
3.1.2.7 – 802.1D BPDU Frame Format
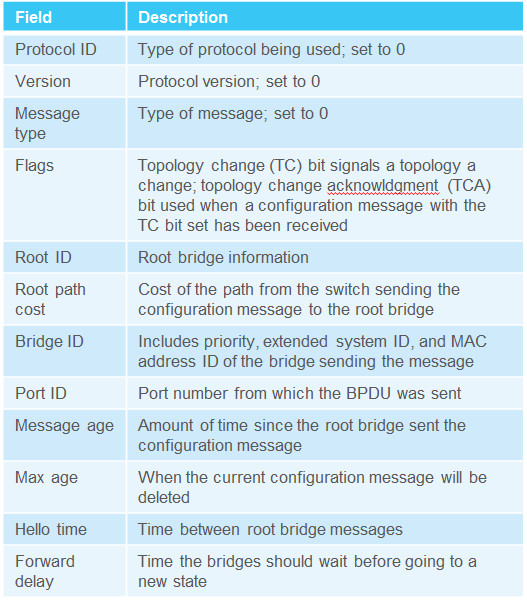
3.1.2.8 – 802.1D BPDU Propagation and Process
1.When a switch is powered on, it assumes it is the root bridge until BPDUs are sent and STP calculations are performed. S2 sends out BPDUs.
2.S3 compares its root ID with the BPDU from S2. S2 is lower so S3 updates its root ID.
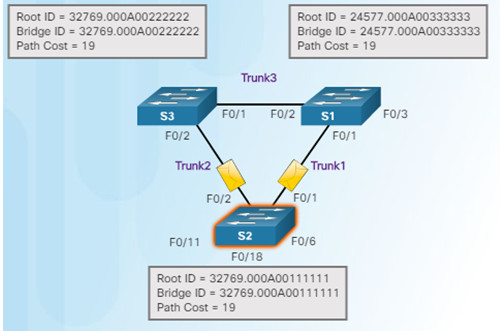
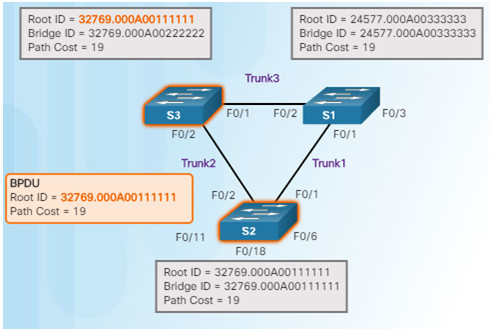
3.S1 receives the same information from S2 and because S1 has a lower BID, it ignores the information from S2.
4.S3 sends BPDUs out all ports indicating that S2 is root bridge.
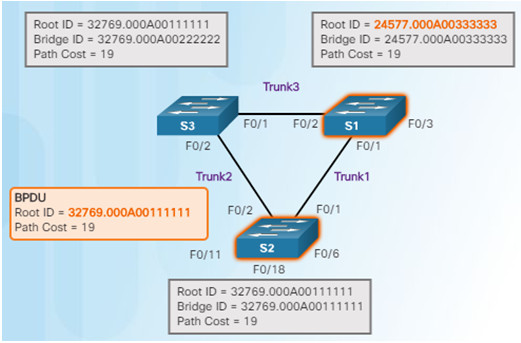
5.S2 compares the info from S3 so S2 still thinks it is root bridge.
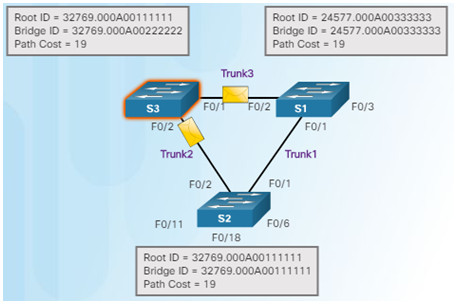
6.S1 gets the same information from S3 (that S2 is root bridge), but because S1 has a lower BID, the switch ignores the information in the BPDU.
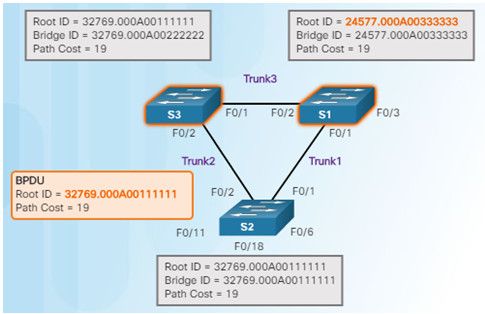
7. S1 now sends out BPDUs out all ports. The BPDU contains information designated S1 as root bridge.
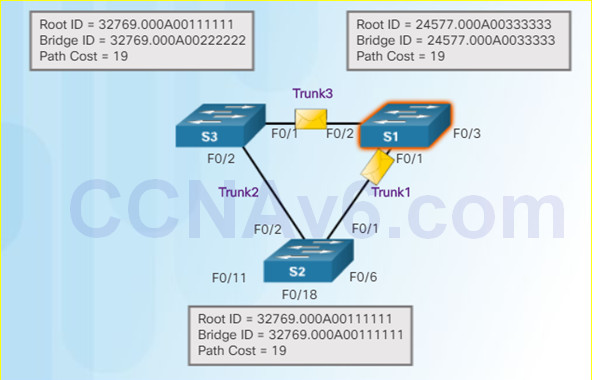
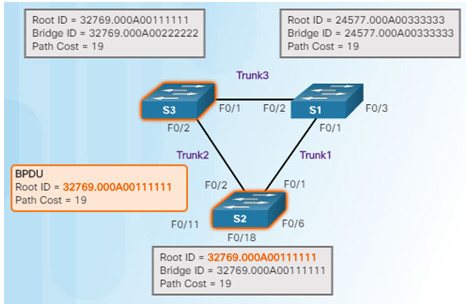
8.S3 compares the info from S1 so S3 now sees that the BID from S1 is lower than its stored root bridge information which is currently showing that S2 is root bridge. S3 changes the root ID to the information received from S1.
9.S2 compares the info from S1 so S2 now sees the BID from S1 is lower than its own BID. S2 now updates its own information showing S1 as root bridge.
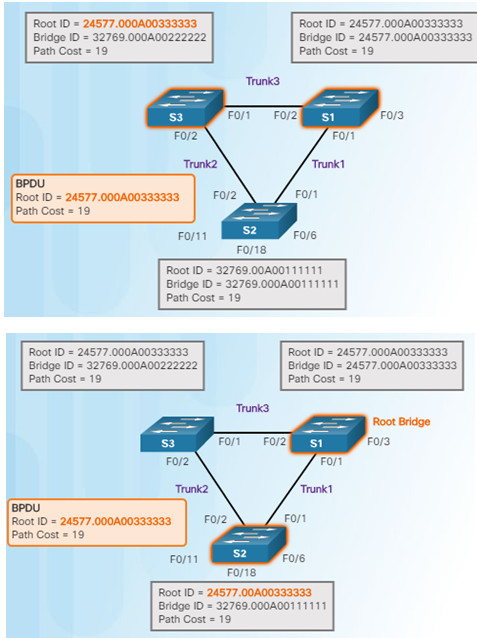

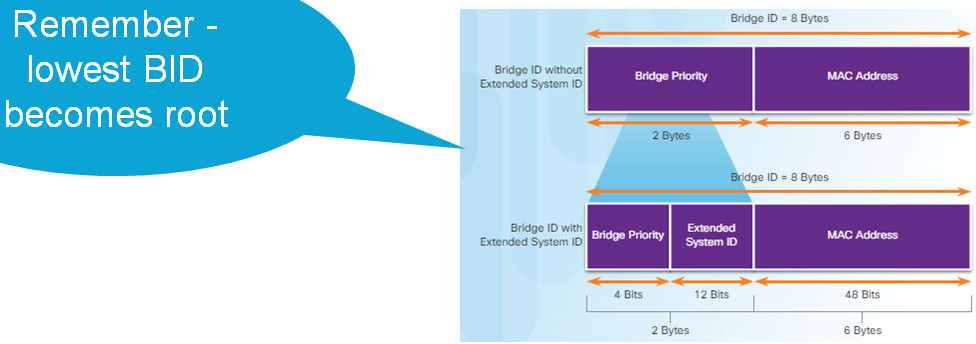
3.1.2.9 – Extended System ID
If priorities are all set to the default, lowest MAC address is the determining factor in lowest BID.
The priority value can be modified to influence root bridge elections.
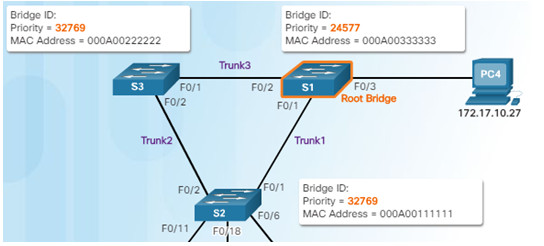
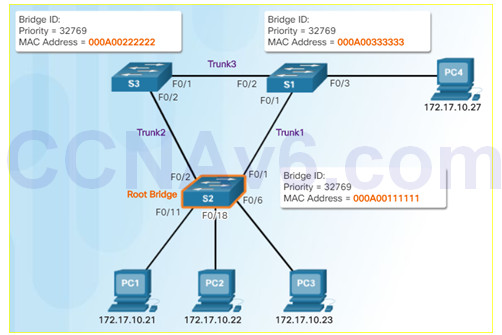
3.1.2.11 – Video Demonstration – Observing Spanning Tree Protocol Operation

3.1.2.12 – Lab – Building a Switched Network with Redundant Links
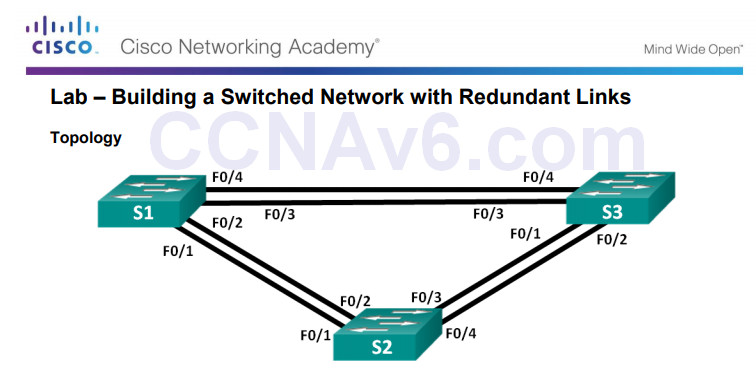
3.1.2.12 Lab – Building a Switched Network with Redundant Links
3.2 – STP
3.2.1 – Varieties of Spanning Tree Protocols
3.2.1.1 – Types of Spanning Tree Protocols
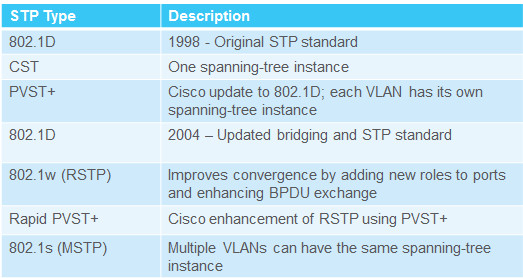
3.2.1.2 – Characteristics of Spanning Tree Protocols
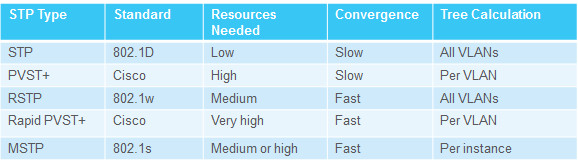
3.2.1 – Varieties of Spanning Tree Protocols
3.2.2.1 – Overview of PVST+
Original 802.1D defines a common spanning tree
- One spanning tree instance for the switched network (no matter how many VLANs)
- No load sharing
- One uplink must block for all VLANs
- Low CPU utilization because only one instance of STP is used/calculated
Cisco PVST+ – each VLAN has its own spanning tree instance
- One port can be blocking for one VLAN and forwarding for another VLAN
- Can load balance
- Can stress the CPU if a large number of VLANs are used
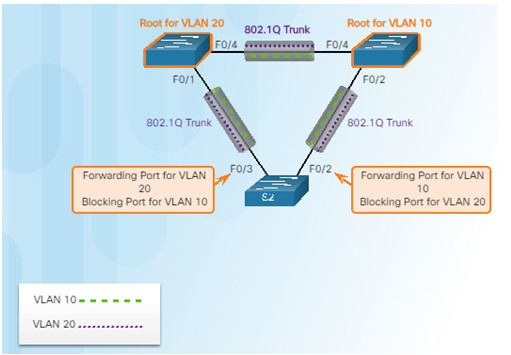
3.2.2.2 – Port States and PVST+ Operation
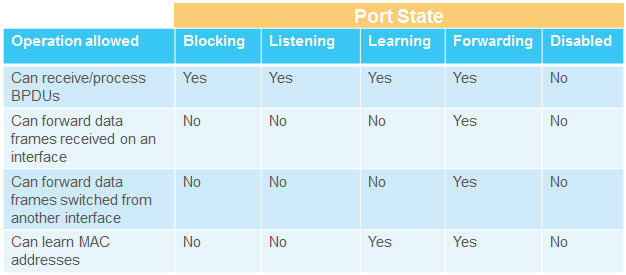
3.2.2.3 – Extended System ID and PVST+ Operation
The extended system ID field ensures each switch has a unique BID for each VLAN.
The VLAN number is added to the priority value.
- Example – VLAN 2 priority is 32770 (default value of 32768 plus the VLAN number of 2 equals 32770)
- Can modify the priority number to influence the root bridge decision process
Reasons to select a particular switch as root bridge
- Switch is positioned such that most traffic patterns flow toward this particular switch
- Switch has more processing power (better CPU)
- Switch is easier to access and manage remotely
3.2.3.1 – Overview of Rapid PVST+
Rapid PVST+ speeds up STP recalculations and converges quicker
- Cisco version of RSTP
Two new port types
- Alternate port (DIS)
- Backup port
Independent instance of RSTP runs for each VLAN
Cisco features such as UplinkFast and BackboneFast are not compatible with switches that run RSTP
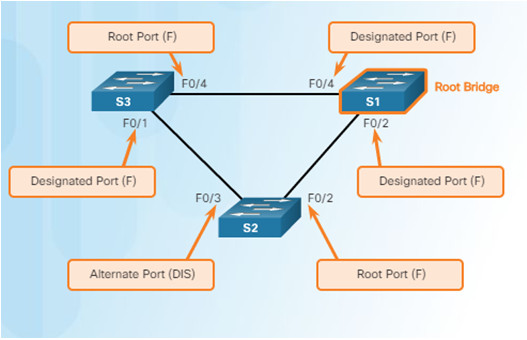
3.2.3.2 – RSTP BPDUs
RSTP uses type 2, version 2 BPDUs
- Original version was type 0, version 0
A switch using RSTP can work with and communicate with a switch running the original 802.1D version
BPDUs are used as a keepalive mechanism
- 3 missed BPDUs indicates lost connectivity
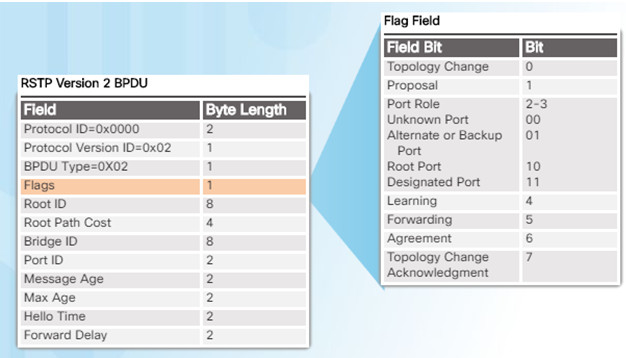
3.2.3.3 – Edge Ports
Has an end device connected – NEVER another switch
Immediately goes to the forwarding state
Functions similar to a port configured with Cisco PortFast
Use the spanning-tree portfast command
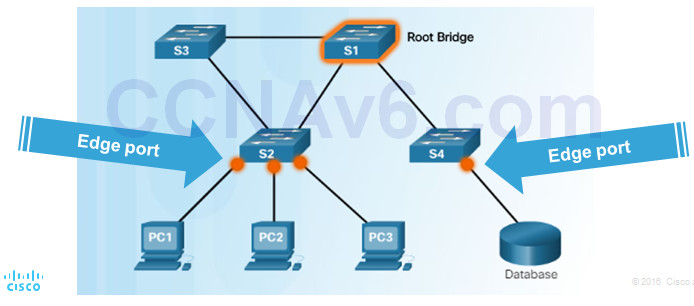
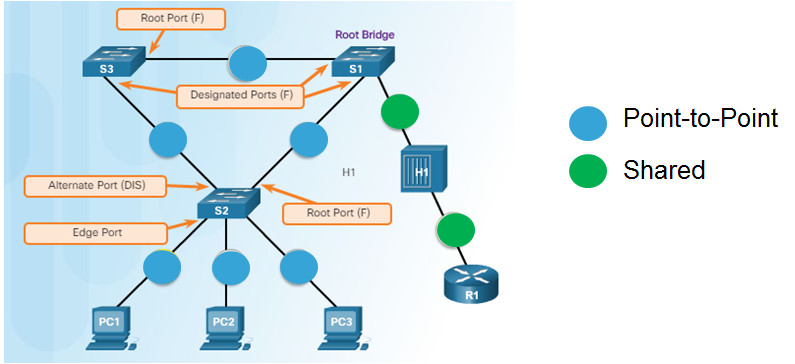
3.2.3.4 – Link Types
Point-to-Point – a port in full-duplex mode connecting from one switch to another switch or from a device to a switch
Shared – a port in half-duplex mode connecting a hub to a switch
3.3 – Spanning Tree Configuration
3.3.1 – PVST+ Configuration
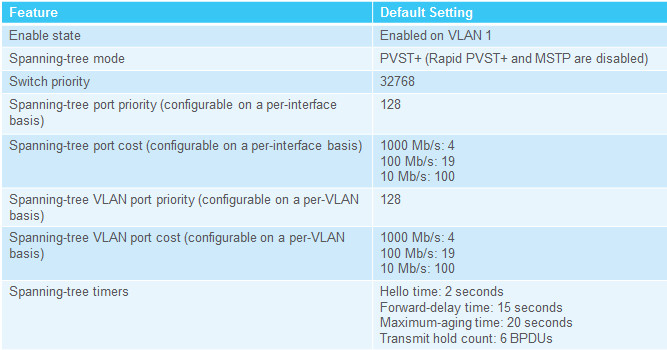
3.3.1.1 – Catalyst 2960 Default Configuration
3.3.1.2 – Configuring and Verifying the Bridge ID
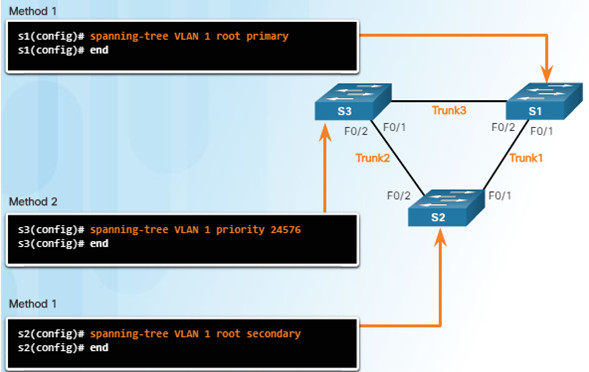
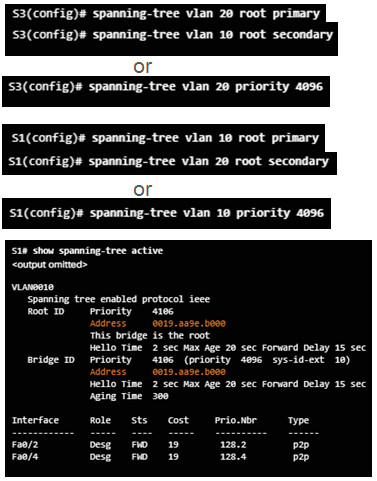
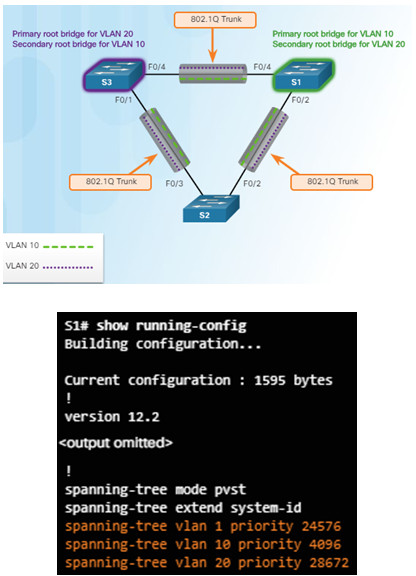
Two ways to influence the root bridge election process
- Use the spanning-tree vlan x root primary or secondary command.
- Change the priority value by using the spanning-tree vlan x priority x command.
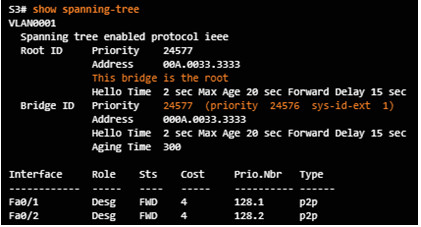
Verify the bridge ID and root bridge election by using the show spanning-tree command.
3.3.1.3 – PortFast and BPDU Guard
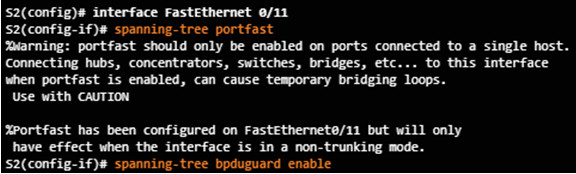
PortFast is used on ports that have end devices attached.
- Puts a port in the forwarding state
- Allows DHCP to work properly
BPDU Guard disables a port that has PortFast configured on it if a BPDU is received
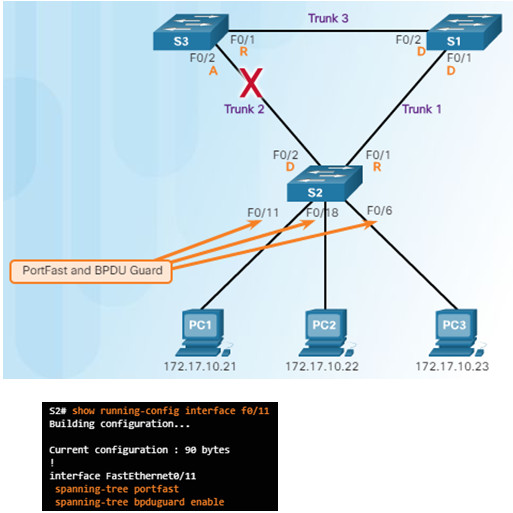
3.3.1.4 – PVST+ Load Balancing
3.3.1.5 – Packet Tracer – Configuring PVST+
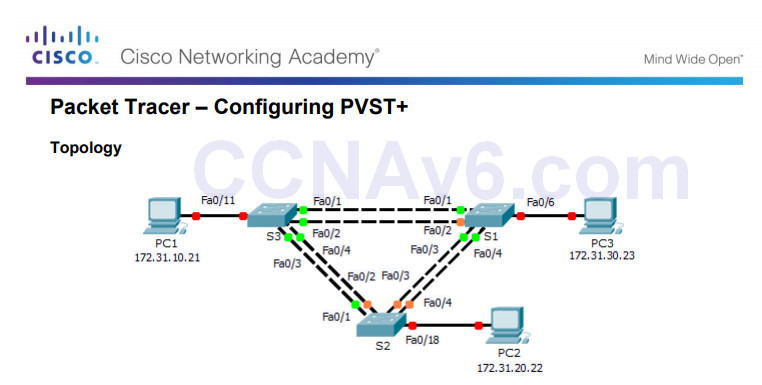
3.3.1.5 Packet Tracer – Configuring PVST
3.3.2 – Rapid PVST+ Configuration
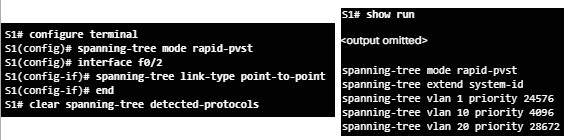
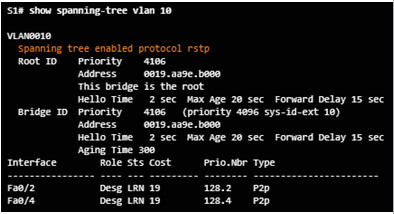
3.3.2.1 – Spanning Tree Mode
Rapid PVST+ supports RSTP on a per-VLAN basis.
- Default on a 2960 is PVST+.
- The spanning-tree mode rapid-pvst puts a switch into Rapid PVST+ mode.
- The spanning-tree link-type point-to-point interface command designates a particular port as a point-to-point link (does not have a hub attached).
- The clear spanning-tree detected-protocols privileged mode command is used to clear STP.
3.3.2.2 – Packet Tracer – Configuring Rapid PVST+
3.3.2.2 Packet Tracer – Configuring Rapid PVST
3.3.2.3 – Lab – Configuring Rapid PVST+, PortFast, and BPDU Guard
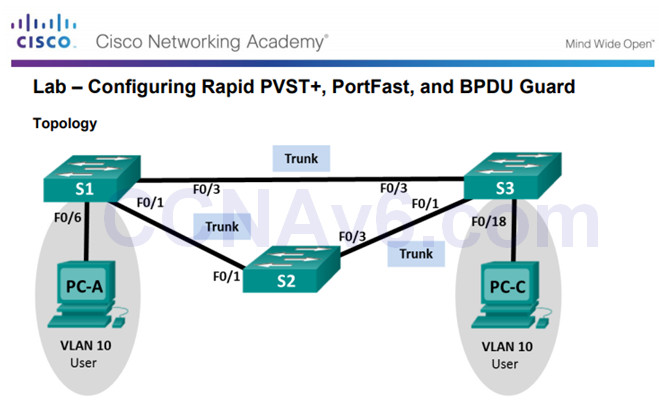
3.3.2.3 Lab – Configuring Rapid PVST+, PortFast, and BPDU Guard
3.3.3 – STP Configuration Issues
3.3.3.1 – Analyzing the STP Topology
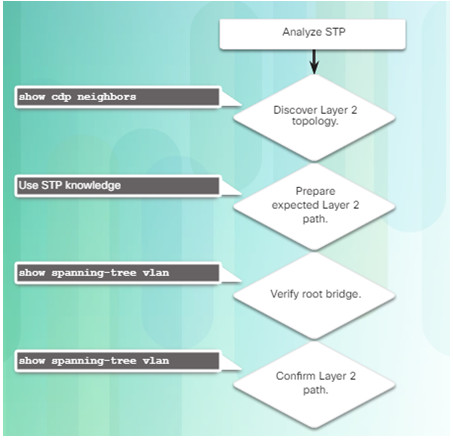
3.3.3.2 – Expected Topology Versus Actual Topology
Ensure that the spanning-tree topology matches what is expected.
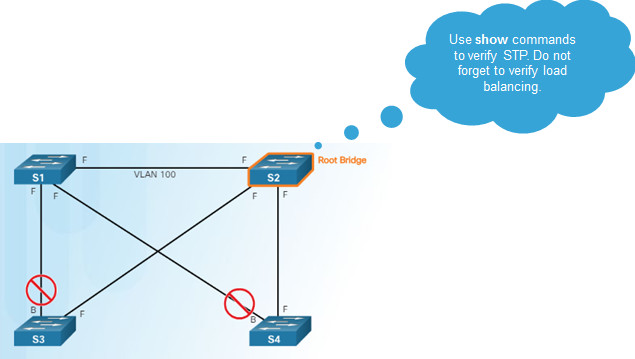
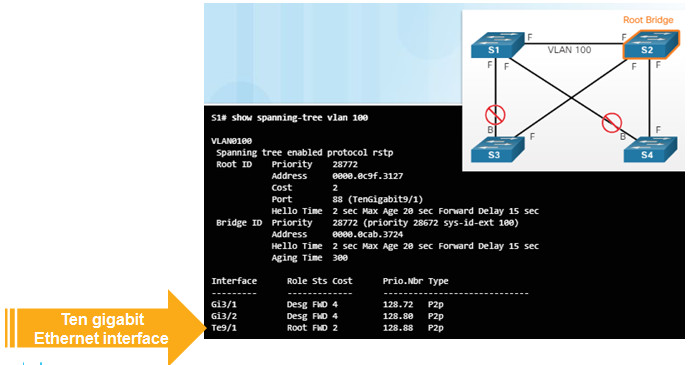
3.3.3.3 – Overview of Spanning Tree Status
Use the show spanning-tree and show spanning-tree vlan x commands to verify the STP status.
3.3.3.4 – Spanning Tree Failure Consequences
NEVER turn STP off; this can cause a switched network to be unusable – Remember that there is not a TTL mechanism at Layer 2.
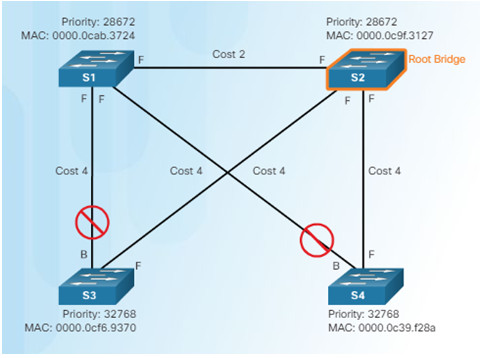
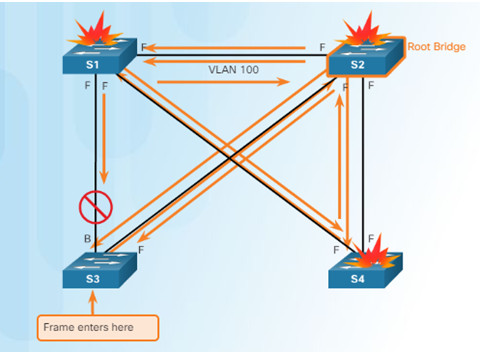
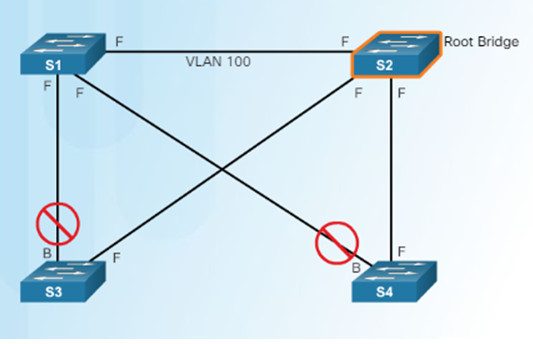
3.3.3.5 – Repairing a Spanning Tree Problem
Manually remove redundant links (physically remove the cable OR through configuration, if possible).
- Determine and repair the cause of the spanning tree failure.
- If unable to determine the problem, reinstall cables one at a time (or re-enable the ports) to locate the issue.
3.3.4 – Switch Stacking and Chassis Aggregation
3.3.4.1 – Switch Stacking Concepts
Can connect up to nine 3750 switches
One switch (the stack master) controls the operation of the stack
- If this switch goes down, a new stack master is elected
Appears as one entity to the network
- Stack is assigned one IP address
Each switch has a unique stack member number
- Can configure a priority value to determine which switch is stack master
- Highest stack member priority value is stack master
The stack master has the saved and running configuration files for the entire stack.
- Only one configuration file to manage and maintain
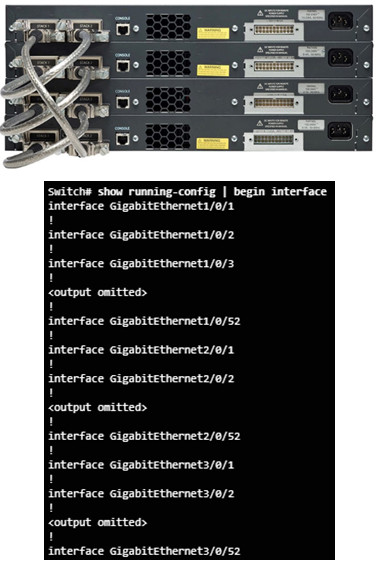
Each stack appears as one spanning tree instance
Can add switches without affecting the STP diameter (the maximum number of switches data must cross to connect between any two switches)
- IEEE recommends a maximum diameter of 7 switches for default STP timers
- Default STP timers are hello – 2 seconds, max age – 20 seconds,
forward delay timer – 15 seconds
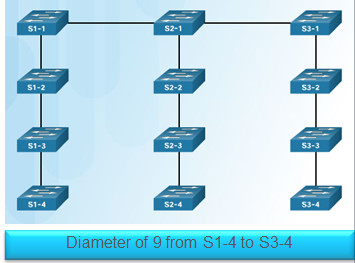
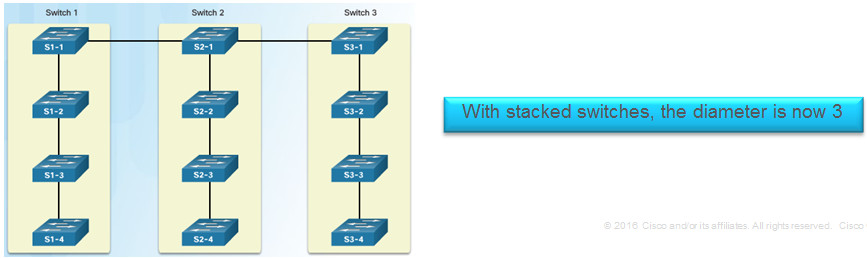
3.4 – Summary
3.4.1 – Conclusion
- Build a simple switched network with redundant links.
- Explain how different varieties of spanning tree protocols operate
- Implement PVST+ and Rapid PVST+ in a switched LAN environment.
3.4.1.1 Documentation Tree Instructions
3.4.1.1 Documentation Tree Instructions
Module 3 New Terms and Commands
| •Broadcast storm
•MAC database instability •Spanning tree algorithm •Spanning Tree Protocol •BPDU •Loop-free path •RSTP •MSTP •IEEE 802.1D •Root port •Designated port •Alternate port •Backup port •Spanning Tree instance •BID •Root ID |
•Bridge priority value
•Root path cost •show spanning-tree •spanning-tree cost •Extended system ID •CST •PVST+ •802.1w •Rapid PVST+ •802.1s •Edge port •Point-to-point link •Shared link •spanning-tree portfast •spanning-tree VLAN root primary |
•spanning-tree VLAN root secondary
•spanning-tree VLAN priority •spanning-tree bpduguard enable •show spanning-tree active •spanning-tree mode rapid-pvst •show spanning-tree vlan •spanning-tree link-type point-to-point •clear spanning-tree detected-protocols •show cdp neighbors •Switch stack •Stack master |
