1. Configure, verify and troubleshoot port security
Static
Switch ports configured with port security only accept frames from addresses that have been dynamically learned or manually configured. The switch port enabled with port security would deny access based on an unknown MAC address. Port security default setting is to allow only one MAC address per switch port.
Dynamic
The following IOS command enables port security on an access switch port. The MAC address of the connected host is learned dynamically and added to the MAC address table. The MAC address persists in the switch table until the switch is powered off. In addition the MAC address is deleted from the MAC address table when the host is disconnected from the switch.
switch(config-if)# switchport port-security
Sticky
The following statements describe primary characteristics of port security.
- The sticky keyword adds dynamically learned addresses to the running configuration script.
- The sticky MAC addresses do not age out of the MAC address table.
- The switch does have to relearn the MAC addresses after every reboot unless the running configuration is saved to startup configuration file.
- Removing the sticky keyword causes dynamically learned the MAC addresses to persist in the MAC address table only for the connected session
switch(config-if)# switchport port-security (enables port security) switch(config-if)# switchport port-security mac-address sticky (add MAC address 0000.000a.aaaa to running configuration) switch(config-if)# switchport port-security maximum 1 (1 device only)
Max MAC addresses
The following port security interface commands prevent connecting a hub or any second device to a shared switch port.
switch(config-if)# switchport mode access switch(config-if)# switchport port-security maximum 1
Violation actions
The four configurable violation modes include protect, restrict, shutdown and shutdown VLAN. The switch interface can add up to the maximum number of allowed MAC addresses to the address table.
The security violation is triggered when there is an attempt from a host with a MAC address not in the MAC address table. Duplicate MAC address error causes a violation as well. The restrict mode causes the switch to drop all packets from an unknown source. SNMP trap alerts are sent, syslog messages are logged and the violation counter is incremented. Protect mode only sends a security violation notification.
The following 802.1X switch port states occur when there is a security violation.
- restrict
- errdisable
Errdisable recovery
The following IOS global configuration command will re-enable a switch port interface in err-disable state caused by a port security violation. The default setting is to reTechnet24.ir enable the port with shutdown and no shutdown interface configuration commands.
switch(config)# errdisable recovery cause psecure-violation
Verify Port Security
Each of the following IOS commands can verify port security is configured on a switch port interface. In addition show port-security interface command provides status information.
switch# show port-security interface gigabitethernet 1/1 switch# show running-config
2. Describe common access layer threat mitigation techniques
802.1X Port-Based Authentication
802.1X authentication is an open standard supporting multi-vendor network devices. It is an IEEE protocol that authenticates hosts requesting network access. User authentication of clients is enabled from switch ports where there is public access. The RADIUS server authenticates a username and password. In addition there is MAC authentication bypass available. The host MAC address is used as the username and password for identity.
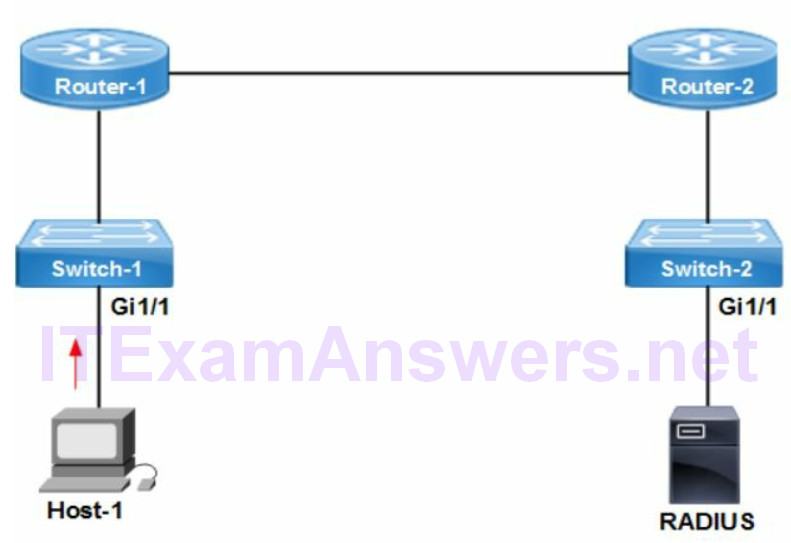
Cisco port security is hardware (MAC) based authentication. It controls the MAC address/s allowed and number of devices. The following correctly describe the features of 802.1X port-based authentication:
- prevent unauthorized hosts from connecting to network
- RADIUS based user authentication
- supports MAC address authentication
- monitor mode collects and analyzes authentication requests
The host connected to an 802.1X enabled switch port waits for an EAP request/identity frame from the switch. The client can initiate authentication by sending EAPOL-start frame if the EAP request/identity frame isn’t sent. The following are three common causes for 802.1X authentication to fail.
- host (client) does not have 802.1X compliant software
- host (client) MAC address is not permitted
- no connectivity to RADIUS server
The following IOS command enables 802.1X with switch-side authentication.
switch(config-if)# authentication port-control auto
The following IOS show command will list the authorized state of an 802.1X client along with host mode and timer configuration.
switch# show dot1x interface [interface-id] details
The data VLAN and voice VLAN must be assigned to a separate VLAN ID. That is required for connecting a Cisco IP phone to an 802.1X enabled switch port.
DHCP snooping
DHCP snooping is a security feature that acts like a firewall between untrusted hosts and trusted DHCP servers.
The services provided by DHCP snooping include the following:
- permit DHCP packet types to trusted ports only
- prevent rogue DHCP servers from offering IP addresses to hosts
DHCP snooping feature is enabled both globally per network device and per VLAN. The network administrator would enable snooping on VLAN/s assigned to switch access ports and trunk uplink connected to the router. Typically the hosts VLANs are configured for snooping.
For DHCP snooping to work properly, all DHCP servers must be connected to the switch through trusted interfaces. In addition all untrusted DHCP messages are forwarded only to trusted interfaces.
The following statements are true of a switch trusted interface:
- DHCP snooping trust interfaces are enabled on a Layer 2 Ethernet interface or port channel to forward all DHCP broadcast messages.
- Trusted interface must have Layer 3 reachability to DHCP servers.
- The switch uplink is typically enabled as a DHCP trusted interface for that purpose. That provides connectivity to the router for packet forwarding to DHCP servers on remote subnets.
DHCP Snooping Configuration
switch(config)# ip dhcp snooping (enables globally) switch(config)# ip dhcp snooping vlan 10 (enable snooping on vlan 10) switch(config)# interface gigabitethernet1/1 (uplink to router) switch(config-if)# ip dhcp snooping trust (configures interface as trusted)
Configure switch ports with DHCP clients (hosts) as untrusted with no ip dhcp snooping trust interface level command.
Nondefault Native VLAN
The native VLAN is used to forward untagged packets across a switch trunk. Management traffic STP and DTP are always sent across native VLAN. The default native VLAN is assigned to VLAN 1. That is the same as the default management VLAN for switches. The native VLAN should not be assigned to VLAN 1 to prevent security or STP issues. As a result assigning a Nondefault native VLAN is a security best practice. The following are correct statements for the Nondefault native VLAN:
- native VLAN must match between connected switches
- forwards untagged packets (STP and DTP) across a switch trunk
- native VLAN for switch trunk port should not be assigned the default VLAN 1
The following command configures a Nondefault native VLAN 999 instead of the default VLAN 1. It is configured on all switch port interfaces assigned as trunk ports. Note that control traffic CDP, PAgP and VTP is always forwarded across VLAN 1
switch(config-if)# switchport trunk native vlan 999
3. Configure, verify and troubleshoot IPv4 and IPv6 access lists
Standard ACL
There are some recommended best practices when creating and applying access control lists (ACL). The network administrator should apply a standard access list closest to the destination. The standard access list is comprised of a source IP address and wildcard mask. It is very general and can inadvertently filter traffic incorrectly. Applying the standard access list near the destination where filtering is required prevents possible over filtering. The standard access list allows for only specifying a source address and wildcard mask. The wildcard mask is used for filtering purposes.
Extended ACL
The extended access list should be applied closest to the source. The extended access list is granular (specific) and filters traffic based on stringent requirements. It includes source address, destination address, protocols and port numbers. Applying an extended access list closest to the source prevents traffic that should be filtered from traversing the network. That conserves bandwidth and additional processing required at each router hop from source to destination. Some access control lists (ACL) are comprised of multiple statements. The ordering of statements is key to the ACL working as expected. The router starts from the top (first) and cycles through all statements until a matching statement is found.
The packet is dropped where no match exists. The network administrator should order ACL statements from most specific to least specific. Assigning least specific statements first will sometimes cause a match to occur with an ACL that wasn’t intended for that packet. As a result the match on the intended ACL statement never occurs.
The more specific ACL statement is characterized by source and destination addresses with shorter wildcard masks (more zeros). In addition protocols and port numbers are often specified. The first ACL statement is more specific than the second ACL statement. There is an implicit deny any any statement added to the end of each ACL.
permit tcp 192.168.1.0 0.0.0.255 host 10.10.64.1 eq 23 deny tcp any any eq 23
Example 1:
The Cisco ACL for IPv4 and IPv6 use similar syntax from left to right. For instance the ACL reads as – deny tcp traffic from host address (source) to host address (destination). All web-based applications are TCP-based and as such requires deny tcp. The eq www specifies the TCP-based application to deny.
reads as - deny http from host 2001:0:AD03::1 to 2001:34F:20DC:24DE::1F
The deny tcp with no application specified will deny traffic from all TCP applications (Telnet, FTP, SSH etc). It would however allow all UDP-based application traffic. The deny ipv6 host command when configured won’t allow UDP or TCP traffic. IP is a lower layer protocol and required for higher layer protocols.
Example 2:
Refer to the network topology drawing. What ACL statements are required to configure the following security requirements?
deny telnet traffic from 10.0.0.0/8 subnets to Router-2
deny http traffic from 10.0.0.0/16 subnets to Router-2
permit any traffic not matching
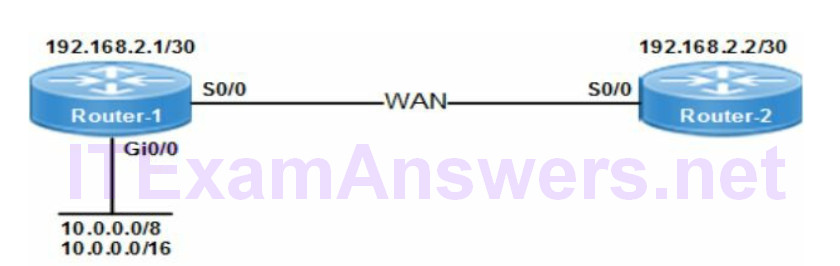
The following IOS commands will configure the correct ACLs based on the security requirements:
router-1(config)# access-list 100 deny tcp 10.0.0.0 0.255.255.255 any eq 23 router-1(config)# access-list 100 deny tcp 10.0.0.0 0.0.255.255 any eq 80 router-1(config)# access-list 100 permit ip any any
The other options have either a wrong wildcard mask, application port number or no permit ip any any statement. All extended access control lists must have a permit all source and destination traffic with permit ip any any as a last ACL statement.
The other options have either a wrong wildcard mask, application port number or no permit ip any any statement. All extended access control lists must have a permit all source and destination traffic with permit ip any any as a last ACL statement.
The following examples describe syntax for source and destination ports. Note that hosts in the context of ACLs refer to desktop, server or network devices. Configuring both ACL statements would filter traffic from the source and to the source as well.
permit tcp any any eq 80
Allows all traffic with destination port 80 (http) from any host to any destination
permit tcp any eq 80 any
Allows all traffic with source port 80 (http) from any host to any destination
Applying ACL to Router Interface
The ACL must be applied to an interface for it to inspect and filter traffic. In addition the in | out keywords specify the direction to filter packets at the interface. The out keyword applies ACL rules to all outgoing traffic on an interface. The in keyword applies ACL rules to all incoming traffic on an interface.
The ACL is applied with interface level IOS command ip access-group 100 out. The ACL is removed with no ip access-group command from the interface.
The ip access-group in | out command refers to an ACL by name or number. The access-class in | out command filters VTY line access only. There is only one access list that can be applied inbound or outbound per interface per layer 3 protocol
The output from show ip interface command lists the ACL, interface and direction.
Named ACL
Named ACLs are similar to extended ACLs and allow for dynamically adding or deleting ACL statements without having to delete and rewrite all lines. There is of course less CPU utilization required as well. They are easier to manage and enable troubleshooting of network issues.
Dynamic ACL
The dynamic ACL provides temporary access to the network for a remote user. The ACL configured defines the type of access permitted and the source IP address and timeout value for network access. It is designed for instance to permit a contractor or remote user temporary access to network services
IPv6 ACL Support
The following are three primary differences between IPv4 and IPv6 support for access control lists (ACL).
- IPv6 supports only named ACLs
- IPv6 permits ICMP neighbor discovery (ARP) as implicit default
- IPv6 denies all traffic as an implicit default for the last line of the ACL
Proper ACL operation requires permit ipv6 any any (all traffic) as a last statement to permit any traffic not matching an ACL. In addition it prevents all traffic from being blocked when there are no ACL permit statements.
The ACL sequence number determines the order of inspection and where any new ACL is added in the list. The new ACL is added to bottom of the list when no sequence numbers are specified
Verify ACL
The following IOS command lists all IPv4 ACLs configured on a router.
router# show access-lists
The following IOS command lists all IPv6 ACLs configured on a router.
router# show ipv6 access-list
Troubleshooting ACLs
- missing permit ip any any statement
- incorrect order of statements
- incorrect application port number
- incorrect interface or direction applied
4. Verify ACLs using the APIC-EM Path Trace ACL Analysis Tool
Path Trace (PT) is a feature available with Cisco APIC-EM that can identify the exact path between two endpoints. The trace is determined based on the endpoint IP addresses and a 5-tuple description for a flow. This helps automate inspection and enable cost effective faster troubleshooting. The following are correct statements concerning Path Trace:
- endpoint support for hosts and/or layer 3 interfaces
- enable automated network troubleshooting
- identify redundant and shadow ACL rules
Network discovery is required before starting ACL Path Trace. In addition SSH or Telnet is required to enable APIC-EM controller access to the devices. The network discovery feature collects information on devices and builds an inventory database.
ACL Path Trace analyzes how a flow is affected by any ACLs deployed on the path. After the path between source and destination is calculated, the ACL Trace analyzes both ingress and egress interfaces of all devices on the path. The analysis is cumulative per ACL and not end-to-end path.
The following are correct statements concerning ACL Path Trace operation:
- Path is calculated between endpoints (source and destination IP address)
- ACL Path Trace analyzes how a flow is affected by ACLs deployed on the path and for troubleshooting ACL issues.
- Cisco ACL Path Trace is supported on layer 3 interfaces only
5. Configure, verify and troubleshoot basic device hardening
Local Authentication
The following IOS command will configure a username called cisconet with user EXEC mode privilege. In addition the password for the manually configured account is cisco. The same command is used on Cisco Catalyst switches and routers. Privilege level 15 is the highest privilege level and level 1 (user EXEC mode) is the lowest.
device(config)# username cisconet privilege 1 password cisco
Hidden Password
The following IOS command will configure a username called admin with privilege level 15 and a hidden password. The 7 designates the password as hidden (encrypted) with the configuration script. The encrypted password is copy/pasted to the command line. The service password-encryption command must be enabled on the network device for type 7 encryption.
device(config)# username admin privilege 15 password 7 [encrypted password]
Enable Password
The following IOS commands will configure an enable password on a Cisco switch or router. The enable password will be required before access to privileged EXEC mode is allowed (switch#). That mode then allows access to global configuration mode.
device> configure terminal device# enable device(config)# enable password cisco
Line Console
The following commands will assign password cisco to the switch or router console port. Any login attempt to the console port will require that password.
device(config)# line console 0 device(config-line)# password cisco device(config-line)# login
Service Password-Encryption
The purpose of service password-encryption command is to encrypt passwords in the running and startup configuration scripts. It applies to all passwords except secret passwords. It makes device passwords unreadable for security purposes. That includes authentication key, enable, console, VTY and BGP neighbor passwords. It does not however encrypt secret passwords.
The following IOS command is used to encrypt all plain-text passwords on a Cisco device. The passwords are encrypted in the running configuration and startup configuration script.
router(config)# service password-encryption
Secret Password
The following IOS command will configure a username called admin with privilege level 15 and a hidden secret password. The 5 designates the password as secret and hidden (encrypted) with the configuration script.
device(config)# username admin privilege 15 secret 5 [encrypted password]
The secret encrypted password is copy/pasted to the command line. It is common to copy the encrypted password from another network device. Secret passwords are based on MD5 hash algorithm that is uncrackable making them more secure than type 7 passwords. In addition the secret password is encrypted automatically and do not require service password-encryption.
Access to device (Source address, Telnet/SSH)
VTY Lines
The following IOS commands will enable Telnet login, configure password cisco and timeout value of 5 minutes for the default VTY lines (0 4). Note that an enable password must be configured on the device as well for Telnet to work correctly.
device(config)# line vty 0 4 device(config-line)# password cisco device(config-line)# login device(config-line)# exec-timeout 5
Login Local
The IOS command login local enables the use of the local database for VTY line access. The username and password is manually configured in the local device database for user authentication. The same IOS command is used to configure console access as well. Any AAA server configuration with TACACS or RADIUS takes precedence over any login local when configured.
device(config-line)# login local
Device Management Protocols
The following IOS command allows only SSH protocol traffic inbound to the default VTY lines (0 4). It will deny all other protocols inbound access to the VTY lines including Telnet. The Cisco default is to allow all protocols inbound and outbound access.
device(config-line)# transport input ssh
The following describe usage of the transport command to filter protocols.
The input | output keyword determines whether inbound or outbound traffic is permitted with the default to allow all inbound and outbound traffic.
device(config-line)# transport input all (default) = allow all protocols (telnet, ssh etc.) device(config-line)# transport input telnet ssh = allow Telnet and SSH only
The following password types are encrypted:
- SSH session password
- password type 7
- enable secret password
Login banner
The following IOS command configures an MOTD banner for a Cisco device.
device(config)# banner motd ^ enter text ^
6. Describe device security using AAA with TACACS+ and RADIUS
The AAA security model includes authentication, authorization and accounting.
- authentication verifies user identity for approving access to the server
- authorization allows user access to applications and data on the server
- accounting provides audit trail of transactions for security analysis and forensics
The following table lists characteristics and features supported with AAA server types.
Table 1: Characteristics and Features of AAA Servers
| TACACS+ | Cisco proprietary |
| RADIUS | multi-vendor open standard |
| TACACS+ | TCP |
| RADIUS | UDP |
| TACACS+ | separates authentication, authorization and accounting |
| RADIUS | integrates authentication and authorization |
| TACACS+ | encrypts all communication |
| RADIUS | encrypts passwords only |
The following is a list of disadvantages with using AAA server authentication:
- AAA server is a single point of failure
- local account is required as a backup on network devices
- same AAA password is used for multiple network devices
The following are three advantages of TACACS+ over RADIUS server.
- TACACS+ supports 15 privilege levels
- TACACS+ enables controls for user authorization levels
- TACACS+ allow for device administration
TACACS+ is a server-based authentication protocol that allows defining of authorization policies per group. As a result TACACS+ is well suited to managing the access security for thousands of network devices. RADIUS is limited to privilege mode with network access and authentication only.
- wireless authentication
- 802.1x port-based authentication
The user will often complain that access to a particular network device is not available. The following command will verify the login access for AAA user account is disabled.
device# show aaa local user lockout
Local AAA
The local AAA authentication method will use the local username and password database configured on the router. The IOS command aaa authentication login default local enables AAA authentication to use the device local username database. There is an option as well to configure local authentication as failover for AAA as well.
