1. Compare and contrast OSI and TCP/IP models
The following describe the network services at each layer of the OSI model. Each lower OSI layer provided services to the next higher layer. Effective troubleshooting should start from the physical layer and verify connectivity to the application layer.
Table 1 OSI Layer and Network Services
| application layer | network services to applications |
| network services to applications | data formatting, translation, encryption, encode |
| session layer | logical communication between host processes |
| transport layer | windowing, error recovery, segments, reliability |
| network layer | logical addressing, routing and path selection |
| data link layer | framing, media access control, MAC address |
| physical layer | putting binary bits on physical media |
Protocol Data Unit (PDU)
The Protocol Data Unit (PDU) is based on the headers added as data is encapsulated from the application layer data to the physical layer. The encapsulation process adds a header at each layer.
Layer 1 = bits, Layer 2 = frames, Layer 3 = packets, Layer 4 = segments
OSI Model Data Encapsulation
Each lower layer adds a header to the PDU from the next upper layer
- Segment encapsulates data from all upper layers (5-7)
- Packet encapsulates transport layer segment
- Frame encapsulates network layer packets
- Physical layer converts all to binary bits for transmission across the wire
The data link layer creates a frame with source and destination MAC address along with control information. The network layer creates a packet with IP addressing and control information. The transport layer divides a data stream into segments. Reliability and flow control information is added when the transport protocol is TCP.
TCP/IP Reference Model
The newer TCP/IP model is based on the popularity of TCP with internet connectivity and network applications. TCP/IP model is the industry standard for network connectivity. The TCP/IP model integrates the OSI model session layer, presentation layer and application layer into a single application layer.
TCP/IP Model OSI Model
Application Layer = Session, Presentation, Application Layer
Transport Layer = Transport Layer
Internet Layer = Network Layer
Network Layer = Physical Layer, Data Link Layer
2. Compare and contrast TCP and UDP protocols
The transport layer provides reliable host-to-host peering connectivity with TCP or UDP protocols. TCP is connection-oriented with handshake setup, flow control and sequencing. The purpose of error recovery and retransmission is to detect, prevent and correct packet drops. It is less efficient than UDP with increased overhead and packet processing.
UDP is faster than TCP however it is connectionless with no guarantee of packet delivery (best effort) and error detection only. The CRC/FCS checksum from the frame is checked and any UDP datagrams that have errors are discarded. Some applications such as video streaming prefer UDP where there is less latency resulting from retransmissions.
Inter-Application Communication
The session ID provides logical communication for each application process. It is at the OSI session layer where there is session setup and tear down. Each file download session for instance is assigned a unique session ID. The FTP download and web browser are separate applications that are each assigned a unique session ID. The port number or socket number identifies each application running on the same server. The server distinguishes where to forward arriving packets for each application based on port number.
Table 2 TCP/UDP Port Assignment
| Telnet | TCP 23 |
| SMTP | TCP 25 |
| FTP | TCP 21 |
| HTTP | TCP 80 |
| SNMP | UDP 161 |
| DNS | TCP/UDP 53 |
| HTTPS | TCP 443 |
| SSH | TCP 22 |
| TFTP | UDP 69 |
3. Describe the impact of infrastructure components in the enterprise
The firewall can inspect packets up to the application (layer 7). The only layer 3 device is the router however firewalls can provide routing services as well. The switch, wireless access point, wireless LAN controller and bridge are all layer 2 devices.
Table 3 Network Devices and OSI Layer
| firewall | layer 7 |
| wireless access point | layer 2 |
| wireless LAN controller | layer 2 |
| switch | layer 2 |
| router | layer 3 |
| bridge | layer 2 |
Broadcast and collision domains
Layer 2 network devices create a single broadcast domain (VLAN) with the initial default configuration. Assigning VLANs creates a broadcast domain for each VLAN. In addition routers and firewalls create a single broadcast domain per interface.
Collision domains are created on each full-duplex Ethernet interface. For example a switch with 48 ports create 48 separate collision domains however the uplink to the router is only a single collision domain. Wireless access points are half-duplex media that share a single collision domain among multiple clients. There is a single collision domain however on the switch uplink side.
- router with two switches connected = 2 collision domains
- wifi access point connected to switch = single collision domain
- switch port connected to router = single collision domain
- switch VLAN = single broadcast domain
- 48 port switch = 48 collision domains (1 per port)
- wifi access point with 100 clients = single collision domain
Example 1:
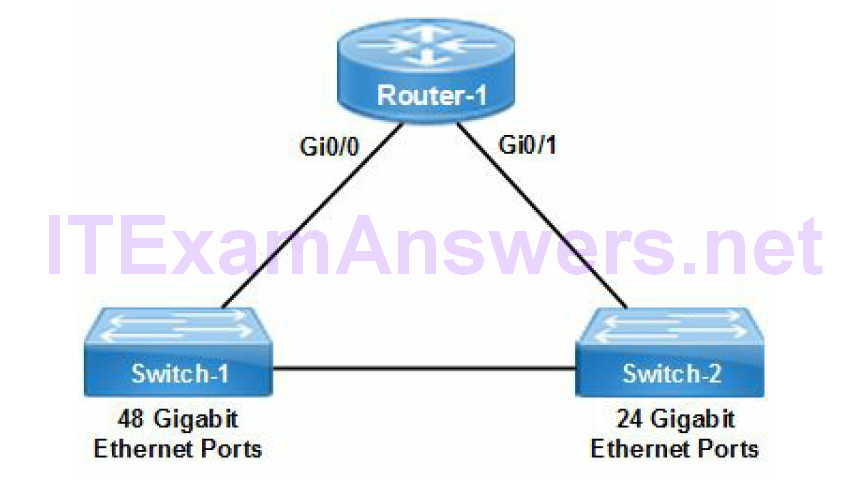
Refer to the network drawing. Each Gigabit switch port is a single collision domain.
There are 72 Gigabit Ethernet switch ports including 3 uplinks that create a maximum 75 available collision domains. There is a default VLAN 1 on each switch that defines a single broadcast domain between switches. In addition there is a separate broadcast domain for each router interface. The network topology defines 3 broadcast domains and 75 collision domains.
Wireless Access Point
The wireless access point is essentially a bridge where packets arrive and are forwarded based on MAC address. The access point however is a single broadcast domain with a shared collision domain.
The wireless RF cell is half-duplex media with CSMA/CA required for collision detection. There is a wired side of an access point with an Ethernet port uplink to a switch. The access point is similar to a desktop or IP phone where PortFast is enabled.
- wireless client transmits wireless signal from client adapter
- 802.11b/g clients cannot connect to 802.11a access points
- 802.11a clients cannot connect to 802.11b/g access points
- 802.11n clients can connect to 802.11a/b/g/n access points
- 802.11a/b/g/n clients can connect to 802.11n access points
- nearest access point that supports wireless signal responds
Wireless LAN Controller
The wireless LAN controller (WLC) is a layer 2 network device. The purpose of WLC is to manage wireless access points. It does not route packets however it does rewrite layer 2 frame header between wireless 802.11n and Ethernet format. The source and destination MAC address are updated as well. The following are primary characteristics of wireless LAN controllers:
- layer 2
- DHCP relay
- frame switching
- STP node
- proxy ARP
Advantages of wireless LAN controllers
- enable easier management and deployment of access points
- enable configuration of wireless user policies across the network
- dynamic RF management
4. Describe the effects of cloud resources on network architecture
The cloud is essentially an internet based service enabling connectivity from any device and from any location. The three primary traffic flows include the following:
Data Center Backhaul
Backhauling traffic from branch offices and customers is available. The traffic is routed through the data center DMZ and forwarded over direct links to the cloud. This topology often increases network latency and utilization on the internet routers.
Point-to-Point
Broadband point-to-point connectivity between branch offices and cloud. This is becoming the de facto standard for branch office connectivity. The DSL provides internet access for direct connectivity to cloud services.
Multipoint
Multipoint connectivity between data center routers and cloud. The internet routers at the data center are hubs for multiple WAN links to the same or different cloud services. It is effective in that each link is a direct point-to-point connection. Redundancy is available as well for failover to a secondary cloud service.
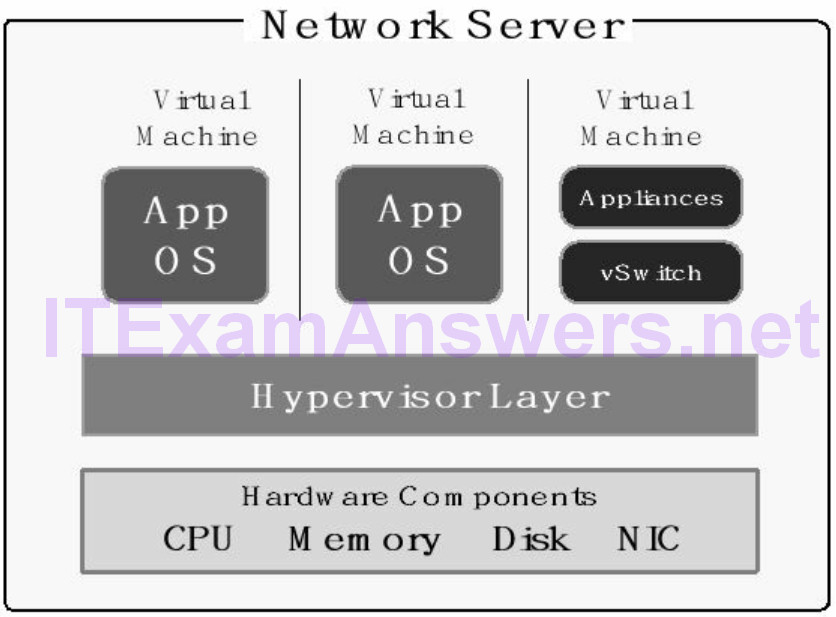
Virtualization Components
The primary components of a virtualized solution include hypervisor, virtual machine (VM) and server hardware. The number of virtual machines (VM) that can be supported on a single server is based on memory, CPU, switch uplink speed and hard disk space
1. Hypervisor manages requests from virtual machines for server hardware. The hypervisor abstracts (separates) the hardware layer from operating system. That enables applications and operating system software to run on any hardware platform.
2. Virtual Machine (VM) is a virtual server with bundled applications and operating systems. Sends requests to hypervisor for hardware services. The virtual appliances (switch, firewall etc.) are network services bundled as a VM.
3. Server hardware includes CPU, memory, hard drive and network interface card.
The five primary characteristics of cloud computing architecture:
- resource pooling
- elastic capacity
- metered billing
- multi-tenancy
- anywhere access
Standard network services available from cloud service providers:
- redundancy
- VPN encryption
- SAN storage
Three primary services of the virtualization model:
- network access control
- tenant segmentation
- virtual machines (VM)
Cisco network virtualization model includes tenant segmentation, security policies and virtual machines. Tenant traffic is segmented with various techniques for path isolation. Network access is managed with security policies and virtualized network services are based on virtual machines (VM).
Virtualization Advantages
The primary advantages of virtualization include cost effectiveness, faster deployment, optimal hardware utilization and network management.
Cost Effective – fewer physical servers are required for the same number of applications. Less data center cabling, power and cooling is required.
Faster Deployment – virtual machines make deployment faster h bundled application that can be copied, distributed and activated when required. Virtualization enables easier disaster recovery as well with virtual machines.
Optimized Hardware Usage – server hardware is utilized at much higher rates with multiple virtual machines. That is preferable to physical servers staying idle when a single application is deployed.
Network Management – virtual servers (VMs) are abstracted from hardware making them agile, easier to manage and assign to servers. The network performance provided by virtualization is a disadvantage. The virtualized environment is a shared infrastructure model. There is often some increased network latency and less throughput than with a physical server. Encryption is available with physical and virtual servers as a network service.
5. Compare and contrast collapsed core and three-tier architectures
The traditional Cisco network design model is comprised of three distinct layers. Each layer provides network services for performance, redundancy, security and scalability.
- access layer
- distribution layer
- core layer
The new Cisco architecture promotes a collapsed core architecture. The collapsed core is comprised of an access layer and a core layer. The distribution layer is collapsed into the core layer along with associated services.
Collapsing (combining) the distribution layer and core layer into a single core layer requires fewer network devices and uplinks. The Layer 2 topology is simplified and STP issues have less effect on the switching infrastructure. It isn’t as scalable as the 3- tier model making it preferable for smaller data centers.
- easier management
- layer 2 optimization
- cost effective
6. Compare and contrast network topologies
Star Topology
The star topology or sometimes called hub and spoke is a point-to-point connection between multiple endpoints and a hub. It is most often deployed for connecting smaller branch offices to a hub or data center. There is no link redundancy making it the most cost effective.
Partial Mesh Topology
The partial mesh has at least two paths to a single or multiple upstream neighbor endpoint/s. It provides more link redundancy than the star topology along with increased cost. The hybrid topology is a customized solution comprised of at least two different topology types. For instance combining a partial mesh topology with a star topology.
Full Mesh Topology
The full mesh topology is referred to as any-to-any connectivity. It is characterized by a link that connects a single endpoint and all neighbor endpoints. It provides the maximum redundancy and is the most expensive. It is often deployed for connecting multiple data centers or where maximum link redundancy is required.
7. Select cabling type based on requirements
- straight-through cable = connect dissimilar network devices (switch to router)
- rollover cable = console port
- crossover cable = connect same class devices (switch to switch)
- serial cable = WAN interface (DTE/DCE)
Table 4 Ethernet Standards
| 1000Base-LX/LH | Single-mode Fiber, 1000 Mbps, 10 km |
| 1000Base-SX | Multi-mode Fiber, 1000 Mbps, 220-550m |
| Cat 5 | Copper, 100 Mbps, 100 m |
| Cat 5e | Copper, 1000 Mbps, 100 m |
| Cat 6 | Copper, 10 Gbps, 55 m |
| 1000Base-LX | Multi-mode Fiber (MMF), 1000 Mbps, 550 m |
| 1000Base-ZX | Single-mode Fiber (SMF), 1000 Mbps, 70 km |
8. Troubleshooting methodologies
The following describes the standard Cisco recommended troubleshooting methodology.
- Step 1: Identify problem
- Step 2: Collect information
- Step 3: Analyze data
- Step 4: Eliminate causes not relevant
- Step 5: Propose hypothesis
- Step 6: Verify with test plan
- Step 7: Solve problem
9. Configure, verify and troubleshoot IPv4 addressing and subnetting
It is important to understand how to convert from IPv4 decimal notation to binary for
subnetting and summarization.
- The binary system is based on ones (1) and zeros (0).
- There are 8 bits per octet, 4 octets per IPv4 address.
- The bit value is based on position.
- The bit set to 1 sets the value. The bit set to zero = 0
- There are 8 bits with 2 (nth power) so 2^8 – 1 = 255
- Per octet: set all bits to 1 = 255, set all bits to 0 = 0
| 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | =0 |
| 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | =255 |
| 8 | 7 | 6 | 5 | 4 | 3 | 2 | 1 | bit position |
| 128 | 64 | 32 | 16 | 8 | 4 | 2 | 1 | bit value |
Binary to Decimal Conversion
Converting binary number to an equivalent decimal number requires adding the values of each bit position set to (1) for each octet. The sum of each octet creates a dotted decimal value (IP address).
0 0 0 0 1 0 1 0 = 10
from right to left, 2nd bit = 2 and 4th bit = 8 = 2+8 = 10
Binary to Decimal Conversion
Converting the binary number to an equivalent decimal number requires adding the values of each bit position set to (1) for each octet. The sum of each octet creates a dotted decimal value (IP address).
00001010.01100100.00101000.10000000
(8+2) . (64+32+4) .(32+8) .128 = 10.100.40.128
Decimal to Binary Conversion
Converting IPv4 address 192.168.64.10 to an equivalent binary number requires setting specific bits for each octet to (1) value. The sum of each octet must add up to the decimal value for each octet.
192 . 168 . 64 . 10
11000000 . 10101000 . 01000000 . 00001010
(128+64) . (128+32+8) . 64 . (8+2)
Hexadecimal to Binary Conversion
IPv6 addressing is based on hexidecimal format instead of IPv4 octets. The IPv6 address is comprised of 32 hexidecimal values of 4 bits each. The IPv6 address is as a result 128 bits in length (4 bits x 32 hexidecimal values). Each hexidecimal number has 16 possible values that range from 0 to F derived from the lower 4 bits of an octet. The same values from 0-9 are used for IPv4 and IPv6 binary to decimal conversion. The values 10 to 15 however are A to F.
Hexidecimal D = 1 1 0 1
8 4 0 1 = 8 + 4 + 1 = 13 decimal
Hexidecimal F = 1 1 1 1
8 4 2 1 = 8 + 4 + 2 + 1 = 15 decimal
A = 10 (1010)
B = 11 (1011)
C = 12 (1100)
D = 13 (1101)
E = 14 (1110)
F = 15 (1111)
Converting FDA4 to binary = 1111 1101 1010 0100
F D A 4
IPv4 Address Classes
The following are the assignable classes for global IPv4 address space. The address range from 127.0.0.0 – 127.255.255.255 is reserved for host-based loopback address.
Class A = 0.0.0.0 – 127.255.255.255
Class B = 128.0.0.0 – 191.255.255.255
Class C = 192.0.0.0 – 223.255.255.255
Class D = 224.0.0.0 – 239.255.255.255 (multicast)
Class E = 240.0.0.0 – 255.255.255.255 (reserved)
Private IPv4 Addressing (RFC 1918)
RFC 1918 defines private IP address space from each address class. The private IP addressing is not public routable across the internet. The standard practice is for companies to assign private addressing to all inside hosts. NAT is deployed at the internet edge where private addresses are translated to public routable addresses.
The following are the RFC 1918 private IP address ranges:
10.0.0.0 – 10.255.255.255 /8
172.16.0.0 – 172.31.255.255 /12
192.168.0.0 – 192.168.255.255 /16
Classful Subnet Mask
Classful subnet masks are based on the default mask length for each IP class. That includes Class A = /8, Class B = /16 and Class C = /24. Any routing protocol that only supports classful subnet masks must use the default for the address class deployed. The default subnet mask implies subnetting is not configured for an address class.
Class A = 255.0.0.0 (/8)
Class B = 255.255.0.0 (/16)
Class C = 255.255.255.0 (/24)
Classless Subnet Mask
Classless subnet masks are referred to as variable length subnet mask (VLSM). They are any subnet mask that is not the default for a particular address class. They enable more specific routes to a destination. In addition subnetting is enabled to optimize available address space. The network portion of an IP address is shifted to the right or left. That changes the subnet mask length and enable subnetting. The number of subnets and host assignments available is based on the subnet mask length.
Example Subnet Masks:
255.0.0.0 = classful (default class A subnet mask)
255.255.224.0 = classless
255.255.255.248 = classless
255.255.0.0 = classful (default class B subnet mask)
255.255.255.0 = classful (default class C subnet mask)
Subnetting Example 1:
What network address would allow the maximum number of subnets for 172.16.1.0/23 with 30 hosts?
The subnet mask defines the network portion (bold) and host portion of an IP address. The subnet mask /23 (255.255.254.0) assigns 23 bits to the network portion and 9 bits to the host portion. The number of assignable hosts is 29 = 512 – 2.
network | host
172.16.1.0 = 10101100.00010000.0000000 1.00000000
255.255.254.0 = 11111111.11111111.1111111 0.00000000
network | host
255.255.255.224 = 11111111.11111111.11111111.111 00000
The question asked for a maximum of 30 hosts. The subnet mask is used to modify the network portion and consequently the host portion as well. Moving the subnet mask to the right will increase the network portion and decrease the host portion assignable. Assigning the rightmost 5 bits provides a maximum of 30 hosts (32 – 2). The network address and broadcast address cannot be assigned to hosts.
decimal 32 = 5 bits = 00000000
The host portion must be decreased from 9 bits to 5 bits. That will require increasing the subnet mask from /23 to /27.
subnet with 30 hosts = 172.16.1.0/27
Subnetting Example 2:
What IP address is assignable to a host based on a subnet mask of 255.255.255.224
A. 192.168.32.31
B. 192.168.32.29
C. 192.168.32.0
D. 192.168.33.1
Correct Answer: B
The network address and broadcast address are not assignable to hosts. The subnet multiple starts at 0 with multiples of 32 (0, 32, 64, 96, 128, 160, 192, 224).
network | host
11111111.11111111.11111111.111 00000
255. 255. 255. 224
1. 4th octet is subnetted
2. subnet multiple = 256 – 224 = 32
3. network address of subnet = 192.168.32.0
4. host range = first 5 bits = 25 = 32 – 2 = 30 host assignments
- network address = 192.168.32.0
- host range = 192.168.32.1 – 192.168.32.30
- broadcast address = 192.168.32.31
Subnetting Example 3:
Select the correct network address and subnet mask that allows at least ten web servers (hosts) to be assigned to the same subnet?
A. 192.168.100.0 255.255.255.252
B. 192.168.100.16 255.255.255.248
C. 192.168.100.16 255.255.255.240
D. 192.168.252.16 255.255.255.252
E. 192.168.100.8 255.255.255.252
The subnet mask defines the network portion and host portion of a subnetted address. Increasing the subnet mask length will increase the number of subnets available. Creating 10 host assignments for web servers requires at least 4 host bits. That allows for 14 host assignments where network and broadcast addresses are not assignable.
23 = 3 host bits = 8 – 2 = 6 host assignments
24 = 4 host bits = 16 – 2 = 14 host assignments
network portion = 32 bits – 4 bits = 28 bits (/28)
= 255.255.255.240
network (28 bits) | host (4 bits)
11111111.11111111.11111111.1111 0000
255. 255. 255. 240
The 255.255.255.240 (/28) subnet mask starts at the bit 5 of the 4th octet and has a binary value of 16. The subnets are multiples of 16 (0, 16, 32, 48 etc).
Correct Answer: 192.168.100.16/28
Subnetting Example 4:
What is the second IP address available for host assignment from 172.33.1.64/30?
A. 172.33.1.64
B. 172.33.1.65
C. 172.33.1.66
D. 172.33.1.1
Correct Answer (C)
The IP address is a nondefault Class A address. The subnet mask defines the number of bits assigned to the network portion and host portion. The /30 subnet mask creates a network portion of 30 bits and a host portion of 2 bits. The number of host assignments available with 2 bits = 22 = 4. The network address and broadcast address are not assignable to hosts. As a result the number of host assignments = 4 – 2 = 2 IP addresses. The following is a list of all IP addresses for subnet 172.33.1.64/30.
- network (subnet) address = 172.33.1.64
- first assignable host IP address = 172.33.1.65
- second assignable host IP address = 172.33.1.66
- broadcast address = 172.33.1.67
network | host
172.33.1.64 = 10101100.00100001.00000001.010000 00
255.255.255.252 = 11111111.11111111.11111111.111111 00
The rightmost bit of the subnet mask (network bits) determines the subnet multiple and where it starts. For this example, bit 3 of the 4th octet has a binary value of 4. The subnet multiple starts at 0 with multiples of 4 (0, 4, 8, 12 etc). The next available subnet is 172.33.1.68/30. Interfaces on the same router must be assigned to different subnets.
Wildcard Masks
The wildcard mask is a technique for matching specific IP address or range of IP addresses. It is used by routing protocols and access control lists (ACL) to manage routing and packet filtering.
The wildcard mask is an inverted mask where the matching IP address or range is based on 0 bits. The additional bits are set to 1 as no match required. The wildcard 0.0.0.0 is used to match a single IP address. Wildcard mask for 255.255.224.0 is 0.0.31.255 (invert the bits so zero=1 and one=0)
11111111.11111111.111 00000.00000000 = subnet mask
00000000.00000000.000 11111.11111111 = wildcard mask
Example 1: Classful Wildcard Mask
The following wildcard will only match on the 192.168.3.0 subnet and not match on everything else. This could be used with an ACL for instance to permit or deny a subnet. It could define a single subnet to advertise from OSPF as well.
192.168.3.0 0.0.0.255
192. 168. 3. 0
11000000.10101000.00000011.00000000
00000000.00000000.00000000.11111111 = 0.0.0.255
Example 2: Classless Wildcard Mask
The classless wildcard can filter based on any network boundary. The following wildcard mask matches on the subnet 192.168.4.0 serial link only. It is the equivalent of 255.255.255.252 subnet mask.
192. 168. 4. 0
11000000.10101000.00000100.00000000
00000000.00000000.00000000.00000011 = 0.0.0.3
192.168.4.0 0.0.0.3 = match on 192.168.4.1 and 192.168.4.2
The CIDR notation denotes the number of bits in the subnet mask. For instance a class C address with subnet mask 255.255.255.240 = /28
Summarization
Refer to the network topology drawing and select the IP address that will summarize all of the routes advertised to Router-1?
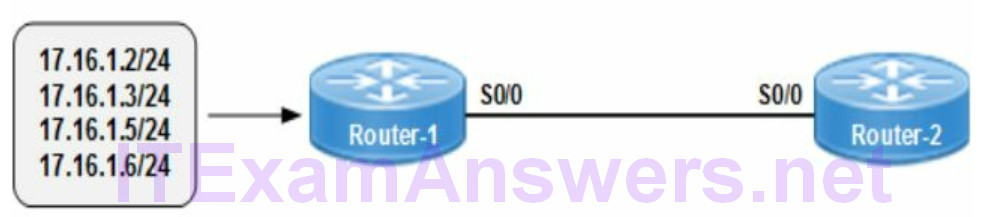
Summarization aggregates (includes) all bits that are common to all IP addresses. The example has four different IP addresses with /24 subnet mask. Start from the left and move right until the bits are mismatched (non-common). The common bits all occur up to and including bit 29. That translates to a /29 subnet mask (255.255.255.248) assigning 29 bits to the network portion. The /29 subnet mask can summarize IP address range 172.16.1.0 – 172.16.1.7
172.16.1.2/24 = 10101100.00010000.00000001.00000 010
172.16.1.3/24 = 10101100.00010000.00000001.00000 011
172.16.1.5/24 = 10101100.00010000.00000001.00000 101
172.16.1.6/24 = 10101100.00010000.00000001.00000 110
The summary address is obtained from the common bits that include all IP addresses ignoring the 3 non-common bits. The single summarized address is an aggregate that can advertise all included IP addresses.
Summary Address = 172.16.1.0/29
10. Compare and contrast IPv4 address types
The following describe the standard network message types. Multicasting forwards the same packet to multiple destinations providing most efficient bandwidth utilization.
Table 6 Network Message Types
| unicast | packet sent from a single source to a single destination |
| multicast | packet sent from a single source to a destination group |
| broadcast | packet sent from a single source to all hosts on a VLAN |
| anycast | packet sent from a single source to nearest destination |
11. Describe the need for private IPv4 addressing
There are various advantages to private IP addressing that has enabled deployment across the enterprise network. The number of public IP addresses available has decreased over the past 10 years. They are now only assignable for internet access.
RFC 1918 private address space cannot be routed across the internet. There are thousands of private IP addresses that are mapped to a single public IP address with Network Address Translation (NAT). As a result public address space conservation is a primary advantage. The reuse of IP address space maximizes private IP addressing available to all companies. Host addresses are not advertised across the public internet for increased security. Intranet connectivity is enabled and at a lower cost than public addresses. The hosts can be deployed as well without internet connectivity.
- global address space conservation
- network security
- enables intranet connectivity
- less costly than public addresses
- assign to hosts without internet connections
12. Select appropriate IPv6 addressing based on requirements
The /48 network address block is a typical assignment to an enterprise network. It provides 16 bits for subnetting as part of the /64 network prefix. In addition there is a /64 (64 bits) available for host address portion. Each number or letter of an IPv6 address is a hexidecimal value comprised of 4 bits with 16 possible values from 0 to F. The subnet portion has 16 bits that can be assigned with variable subnet masks.
- IPv6 address = 2001:AD7:4312:1D34.0000:0000:0000:0001/128
- single subnet = 2001:AD7:4312:1D34::/64
- 65,535 subnets (16 bits) = 2001:AD7:4312::/48
- network prefix = 2001:AD7:4312::/48
- network prefix + subnets = 2001:AD7:4312:0000::/64
- host identifier = 0000:0000:0000:0000/64 – FFFF:FFFF:FFFF:FFFF/64
regions data centers subnets
0000 0000 0000 0000
The first 4 bits (49 – 52) can be assigned to identify regions (bold). The second group of 4 bits (53 – 56) can be assigned to identify data centers. The remaining group of 8 bits (57 – 64) are assigned to subnets for each data center.
- regions = /52
- data centers = /56
- data center subnets = /64
The number of regions, data centers and number of subnets per data center determine the subnets masks selected. For example with only 3 regions, the /50 subnet mask with 2 bits (49-50) would provide the required 4 region identifiers. The following IPv6 address ranges are assigned to regions, data centers and subnets per data center.
16 regions: 2001:AD7:4312:1000::/52 – 2001:AD7:4312:F000::/52
16 data centers: 2001:AD7:4312:0000::/56 – 2001:AD7:4312:0F00::/56
DC subnets: 2001:AD7:4312:0000::/64 – 2001:AD7:4312:00FF::/64
13. Configure, verify and troubleshoot IPv6 addressing
IPv6 is based on hexidecimal notation with values from number 0-9 and A to F. IPv6 addressing is comprised of 8 groups with 4 hexidecimal values of 4 bits each for 16 bits per group. The 16 bits per group x 8 groups equals 128 bits per IPv6 address.
The IPv6 address is comprised of a 64 bit network prefix and a 64 bit interface identifier. The 64 bit network prefix is comprised of a 48 bit routing prefix and 16 bit local subnet ID. The network prefix is similar to the IPv4 network address portion. The interface identifier is similar to the IPv4 host address portion. The subnet ID allows for variable length subnets that identify VLANs, departments, buildings and cities for instance. Regional Internet Registry (RIR) assigns IPv6 addresses to end users.
- multiple IPv6 addresses are assignable per interface
- hop limit is a new field of IPv6 packet is equivalent to IPv4 TTL field
- flow label field is new to IPv6 packet
- features that used broadcast messaging is now provided with multicasting
Advantages of IPv6 Addressing
- scalability
- no broadcasts
- address autoconfiguration
IPv6 Addressing Rules
- double colon :: can summarize multiple consecutive zeros for multiple groups
- only one double colon is permitted per IPv6 address
- multiple zeros in a single group can be summarized with a single zero.
- leading zeros in a single group can be deleted
- no less than 8 groups including zero groups
Any IPv6 address with less than 8 groups must have double colon to summarize consecutive zero groups.
Example 1:
What is the alternate equivalent notation for the following IPv6 address?
2001:25D3:0000:0000:009F:CD2A:0000:332E
A. 2001:25D3:9F::CD2A:0000:332E
B. 2001:25D3:9F:CD2A:0:332E
C. 2001:25D3::9F:CD2A:0:332E
D. 2001:25D3:0:009F:CD2A:332E
The correct IPv6 address 2001:25D3::9F:CD2A:0:332E does the following:
1. Minimizes multiple zero groups (group 3 and 4) to a double colon ::
2. Deletes leading zeros from a single group (group 5)
3. Minimizes a single group with all zeros to single zero :0: (group 7)
A. 2001:25D3:9F::CD2A:0000:332E
(double colon in wrong location and group 7 not summarized to single zero)
B. 2001:25D3:9F:CD2A:0:332E
(zero groups 3 and 4 removed instead of being summarized to double colon)
D. 2001:25D3:0:009F:CD2A:332E
(group 3 and group 4 should summarizes to double colon :: and not a single zero.
group 5 leading zeros were not deleted and group 7 removed instead of a single zero)
Example 2:
Select the valid IPv6 address from the following list?
A. 2001:0000:12D4::043D::1
B. 2001:1234:4567:AD:12DE:1
C. FEC0:ABCD:9WCD:0067::2A4
D. 2001:AD:654C:1234::9
Options A, B and C have features that are not valid with IPv6 addressing. The following explains the issues with each address:
Option A – has double colons :: occurring twice. The double colon is only permitted once per IPv6 address. 2001:0000:12D4::043D::1
Option B – has only 6 groups. IPv6 requires 8 groups (8 x 16 bits = 128 bits). Any IPv6 address with less than 8 groups must have double colon to summarize zero groups. 2001:1234:4567:AD:12DE:1
Option C – has an illegal value (W). IPv6 is based on hexidecimal notation with values from 0 to F hexidecimal. FEC0:ABCD:9WCD:0067::2A4
IPv4 to IPv6 transition methods
The solutions available for IPv4 to IPv6 transition include tunneling and translation.
- ISATAP Tunneling
- NAT Proxy and Translation (NAT-PT)
- Teredo Tunneling
- 6to4 Tunneling
IPv6 Duplicate Address Detection
IPv6 duplicate address detection is required on all unicast IPv6 addresses assigned to an interface. The detection starts with Stateless Address Autoconfiguration (SLAAC) assigning an IPv6 link-local address to a node. The network interface state is tentative during the detection process. The network administrator can enable duplicate address detection again by assigning a new IPv6 address.
There are a variety of IPv6 address states based on the operational status of the interface and duplicate address detection. The IPv6 address state is pending while the associated network interface is administratively down. The following statements correctly describe what happens when a router detects an IPv6 duplicate address.
- duplicate global addresses are not used on interfaces where they are assigned.
- IPv6 packet forwarding is disabled on interface with duplicate link-local address.
- IPv6 addresses are all disabled on any interface that has a duplicate link-local address until it is resolved.
14. Configure and verify IPv6 Stateless Address Auto Configuration
IPv6 makes addressing easier when autoconfiguration is enabled. There is a unique link-local address assigned automatically to the interface. Enabling SLAAC however does not send DNS server addressing to clients. The feature only provides an IP address and default gateway to clients. The following methods are available for assigning IPv6 addresses that are not static (manual) assignment.
Stateful DHCPv6
Stateful DHCPv6 is most similar to DHCPv4 for IPv4 addressing. The IPv6 client sends a broadcast request to the nearest DHCPv6 server for IP address configuration. The DHCPv6 server assigns the IPv6 address and any additional required addressing configuration such as default gateway, DNS server etc.
Stateless DHCPv6
Stateless DHCPv6 feature uses Stateless Address Autoconfiguration (SLAAC) for assigning an IPv6 address and default gateway to clients. The feature does however require a DHCPv6 server for sending a variety of additional IP configuration settings including DNS server address to clients.
Stateless Address Autoconfiguration (SLAAC)
Stateless autoconfiguration generates a unique link-local address based on EUI-64 format. The IPv6 address is based on the network prefix sent in Router Advertisement (RA) from the local router. In addition SLAAC obtains the default gateway from Router Advertisements to configure clients. IPv6 processing is automatically enabled on an interface as soon as an IPv6 address is assigned to the interface. The IPv6 interface state is the status based on an autoconfiguration address request.
Tentative: address is being verified with duplicate address detection.
Valid: address can send and receive unicast traffic.
Preferred: address can send and receive unicast traffic.
Deprecated: address can send/receive unicasts though not recommended.
Invalid: address cannot be used to send or receive unicast traffic.
IPv6 Address Configuration
The following IOS command assigns a static IPv6 address to a router interface. The ipv6 enable command is not required when an IPv6 address is already assigned to an interface.
router(config-if)# ipv6 address 2001:AF42:1212:4F32::32/64
The following IOS command enables autoconfiguration on a network interface. The ipv6 enable command is not required.
router(config-if)# ipv6 address autoconfig
Verify IPv6 Addressing
The following IOS command will show the status of an IPv6 enabled interface.
router# show ipv6 interface
15. Compare and contrast IPv6 address types
Table 7 IPv6 Address Types
| global unicast address | internet routable with global routing prefix |
| multicast address | prefix FF00::/8 (send to group members) |
| unique local address | private network, not internet routable, starts with FD00::/8 |
| link-local address | mandatory, auto-configured, local subnet only, used for routing adjacency, prefix FE80::/64 |
| loopback address | universal, assigned to each interface, prefix ::1/128 |
| anycast address | send to any member of a group that is nearest and available, typically default route ::/0 |
| unspecified address | source address for initializing host, :1/128 |

In the 9. Configure, verify and troubleshoot IPv4 addressing and subnetting, the formula of the power of two is wrong.
“There are 8 bits with 2 (nth power) so 28 = 255” should be “2^8-1 = 255”.
Fixed, thanks for comment :)