1. Configure and verify PPP and MLPPP WAN connectivity
The following describe the standard reasons for deploying WAN connectivity:
- enable connectivity between branch offices, data center and cloud
- information sharing among internal and external organizations
Serial Interfaces
Serial interfaces connect devices that are assigned as a DCE or DTE. The DCE provides clocking for the serial interface. The DTE is the device receiving the clock signal. The router is a DTE that connects to a DCE such as CSU/DSU or DSL modem.
DTE – DCE – [DCE ISP DCE] – DCE – DTE
The CSU/DSU terminates the digital local loop from the service provider network (ISP). Analog interfaces terminate an analog local loop and converts between digital and analog signaling. The Cisco default synchronous serial interface encapsulation type is HDLC. Verify WAN encapsulation with show interfaces command.
TCP-based applications require a three-way handshake for host-to-host connectivity.
1. host sends TCP SYN message to server with bit set
2. server sends TCP SYN/ACK message to host with bits set
3. host sends message to server with TCP ACK bit set
Point-to-Point Protocol (PPP)
The maximum speed supported on a single PPP link is T1/E1 however MLPPP enables bundling for increased bandwidth. Encapsulation must match between peering routers configured with PPP.
- LCP is Layer 2 protocol that establishes, manage and terminates the WAN connection.
- LCP negotiates PAP/CHAP authentication with the remote peer router.
- NCP provides protocol encapsulation for multiple layer 3 network protocols where configured.
The normal operational status for LCP (layer 2) is Open when the PPP link is working correctly. In addition NCP, IPCP and Multilink interface also show as Open.
IPCP is the Network Control Protocol (NCP) for IPv4 traffic across a PPP link. The client IP address request is processed through IPCP for a PPP link. In addition IPCP allows for requesting the IP address from a DHCP server.
PPP Configuration
The following IOS commands will enable PPP on serial interface 1/0/0 with CHAP
authentication and password cisco.
router(config)# interface serial1/0/0 router(config-if)# encapsulation ppp (enables PPP) router(config-if)# ppp authentication chap (enables CHAP) router(config-if)# ppp chap password cisco (password = cisco) router(config-if)# ppp chap hostname WAN-Router (hostname = WAN-Router)
CHAP/PAP Authentication
CHAP/PAP are authentication protocols that provides secure authentication across PPP/MLPPP serial interfaces. The authentication requires passwords and hostnames to match between local and remote peering routers.
- The number of retry attempts is controlled by the peer router. Messages are sent periodically to verify the peering device is authentic.
- There is no hashing available with PAP authentication. The username and password is sent as clear text only.
The following configures CHAP authentication with PAP as the fallback protocol:
router(config-if)# ppp authentication chap pap
Local Authentication
The first command aaa authentication ppp default local enables use of the local username database for authenticating the peer router.
The second command ppp authentication pap chap enables PAP and CHAP authentication. The router will attempt PAP authentication first then fallback to CHAP based on the configuration order.
router(config)# aaa authentication ppp default local router(config-if)# ppp authentication pap chap
Multilink PPP (MLPPP)
Multilink PPP (MLPPP) enables bundling of multiple links into a single logical link. That includes encapsulation of serial or broadband (Ethernet/DSL) WAN services. There is a limit of 10 links per serial bundle and 8 link per Ethernet/DSL bundle.
- interface multilink 10 (assigns bundle number)
- ip address 172.16.1.1 255.255.0.0
- no keepalive
- ppp multilink (enables multilink)
- ppp multilink group 10 (allow only physical link assigned to bundle 10)
Verify MLPPP
The following command will verify the interface status and encapsulation type for Multilink bundle 1.
router# show interfaces multilink 1
The following command displays the status of all bundle member (physical) interfaces. In addition any interface errors are listed as well.
router# show ppp multilink
Link Quality Monitoring
The purpose of Link Quality Monitoring (LQM) is to detect packet drop errors on a PPP WAN link. It provides error detection and correction across the PPP link. The link quality report packet (LQR) is sent across the WAN at regular intervals. The LQR calculates the percentage of packets transmitted from packets that were received. It is disabled by default however is configurable with the ppp quality [percent] command.
Troubleshooting PPP/MLPPP
- IP address and/or subnet mask is misconfigured on an interface
- static route next hop address does not point to the remote tunnel interface
- CHAP password and hostname mismatch with peering neighbor
- encapsulation type mismatch
The command show ppp multilink is used to verify all active member links of a multilink bundle. It confirms the multilink interface is up and forwarding packets. In addition the bundle name is listed and number of packet drops.
The command debug ppp negotiation is used to troubleshoot PPP link errors. The output lists LCP link establishment and PAP/CHAP negotiation with the remote router. IPCP packets such as IP address requests are displayed as well. Refer to the network topology drawing. Host-1 cannot send packets to Server-1. Select two possible causes based on the results of show ip interface brief command?
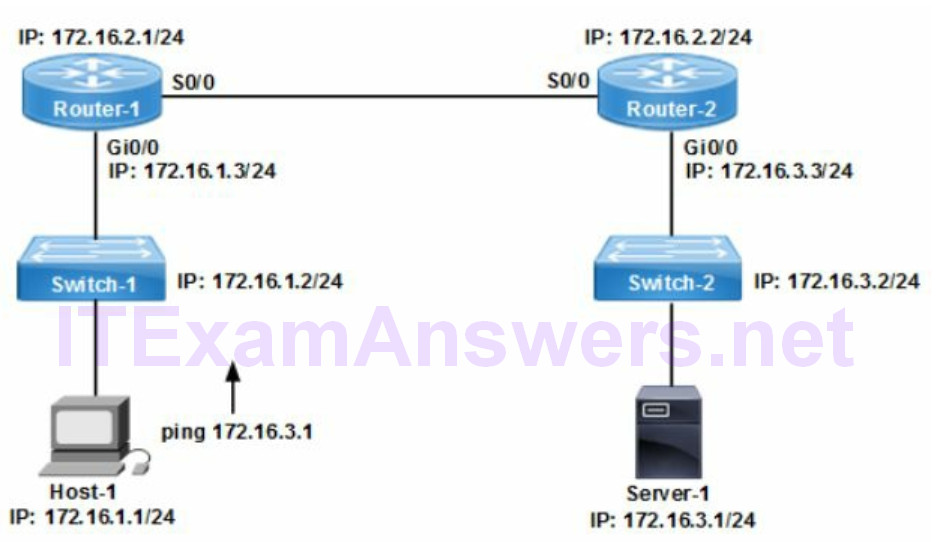
router-1# show ip interface brief Interface IP address OK Method Status Protocol FastEthernet0/0 172.16.1.3 YES NVRAM up up FastEthernet0/1 Unassigned YES Manual admin down down Serial0/0 172.16.2.1 YES Unset up down Serial0/1 Unassigned YES Manual admin down down
A. clocking error between routers
B. cabling issue
C. serial line encapsulation mismatch between routers
D. Router-2 interface Serial0/0 (S0/0) is administratively down
E. Router-1 is configured with the wrong subnet mask
F. Router-2 loopback is assigned the wrong subnet mask
Correct Answers (A,C)
The IOS command show ip interface brief displays the operational status for all network interfaces with an assigned IP address. The Status column is layer 1 Ethernet signaling while the Protocol column is layer 2 data link connectivity. Router-1 interface S0/0 (172.16.2.1) is up/down confirming the problem is line protocol (layer 2). Typical Layer 2 causes include clocking errors and encapsulation mismatch between routers.
2. Configure, verify and troubleshoot PPPoE client-side interfaces
PPPoE encapsulates PPP frames inside Ethernet frames. PPP enables authentication, encryption and compression for PPPoE sessions across the internet. PPPoE over Ethernet client feature for Cisco routers has a client/server peering model.
The client router is at the customer premises and the server device is at the ISP. It is typically deployed for DSL connectivity from a Cisco router with Ethernet only interfaces. The DSL modem is connected to the Cisco router Ethernet interface.
The client mode router requests an IP address from the ISP with IPCP negotiation. In addition the client mode router negotiates authentication with the ISP server. PPPoE client mode enables multiple hosts on an Ethernet segment to access DSL services.
The PPPoE client is uniquely identified with a MAC address and session ID. There is a MAC address exchange between peers before NCP (layer 3) starts. That is required to identify the MAC address of the remote peer router.
The session ID is assigned to the PPPoE session after MAC address discovery. Peer authentication is negotiated during the PPPoE session phase.
The interface dialer 1 command negotiates an IP address from the PPPoE server with IPCP. The virtual-template is configured on the PPPoE server to allocate IP addresses to clients. The command pppoe-client dial-pool-number 1 binds the physical interface to the dialer interface on the PPPoE client.
The following table compares PPP and PPPoE characteristics and usage.
Table 1: Comparing PPP and PPPoE feature characteristics
| peer to peer | PPP |
| security features | PPP |
| serial lines | PPP |
| router | PPP |
| multipoint broadcast | PPPoE |
| easy to deploy | PPPoE |
| la yer 2 transport independent |
PPPoE |
| Ethernet only router | PPPoE |
| bridge | PPPoE |
Enable PPPoE
The following commands enable PPPoE on a client interface:
router (config-if)# pppoe enable router (config-if)# pppoe-client dial-pool-number 1
3. Configure, verify and troubleshoot GRE tunnel connectivity
The purpose of GRE is to enable routing protocols across the WAN. It is typically deployed to support routing protocol advertisements across a VPN. That is accomplished by tunneling (encapsulating) the routing protocol.
The two primary advantages of GRE tunneling include the following:
- routing protocol support across the internet
- increase hop count for layer 3 protocols
Some advantages of GRE/DMVPN connectivity include the following:
- lower support costs and scalability
- tunnel multiple protocols across the internet
- increase the hop count where required
- dynamic VPN tunnel setup and configuration
- enable increased security with VPN encryption
- redundant (backup) tunnels across the internet
GRE assigns a tunnel source and tunnel destination IP address. They are public (NBMA) routable IP addresses. In addition the tunnel source address refers to a local interface. The tunnel destination address is the remote router interface.
- public routable IP address
- local router interface
Next Hop Resolution Protocol (NHRP) enables the dynamic tunnel setup between hub and spokes. There is an automatic detection of all spoke public IP addresses (NBMA). The public routable (tunnel source) IP address is dynamically assigned to the spoke (branch) by the ISP. The spoke registers the NBMA IP address with the hub router.
NHRP at the hub router maps the spoke tunnel source address to spoke tunnel interface. The tunnel interface (logical) is the private IP address. The hub router at the data center builds a table with mappings for all connected spoke routers. The tunnel interface is often a loopback address. Packet forwarding is enabled with next hop addressing (routes) between hub router and all connected spokes.
GRE is a stateless protocol with no flow control and assigned IP protocol 47. GRE tunneling provides no security at all for packets traversing the internet. IPsec provides encryption and authentication for GRE tunnels.
Refer to the network drawing. The GRE tunnel is configured with a Tunnel (virtual) interface and a public routable Tunnel source IP address is shown for each peering router.
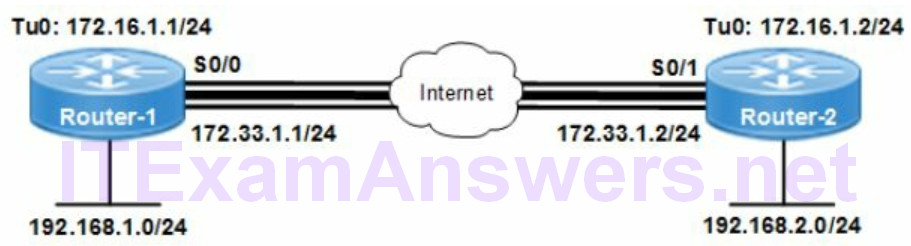
GRE Tunnel interface IP addresses are from the private network and not routable. They are assigned to the Tunnel interface on each router with a number. The network topology drawing assigned the following IP addresses to Tunnel0 (Tu0) interface.
172.16.1.1/24 = Tunnel0 interface IP address (Router-1)
172.16.1.2/24 = Tunnel0 interface IP address (Router-2)
GRE Tunnel source IP addresses are public routable and assigned by the ISP. They are assigned to the public facing physical interface on each router. The Tunnel source IP address assigned to the remote router is referred to as the Tunnel destination IP address. The network topology drawing assigned the following IP addresses.
172.33.1.1/24 = GRE tunnel source IP address (Router-1)
172.33.1.2/24 = GRE tunnel source IP address (Router-2)
The following command will enable GRE tunnel support across the DMVPN.
router(config-if)# tunnel mode gre multipoint
The IOS command show interface tunnel 1 is used to verify tunnel interface status (up/up), configured settings and performance. The running-config command is used to verify all GRE configuration and static routes. The next hop address of each local static route must point to the remote tunnel interface.
router# show interface tunnel 1 router# show running-config
4. Describe WAN topology options
1. Point-to-Point topology is used for direct connectivity of network devices.
2. Hub and Spoke is a star topology that provides connectivity to the hub and between endpoints (branch offices). The hub and spoke topology is deployed with DMPVN connectivity.
3. Full Mesh topology provides a link to and between all endpoints for any-to-any connectivity.
WAN homing describes the network topology between customer and ISP for internet access. In addition along with topology there are levels of redundancy. The following are correct statements concerning WAN homing topologies.
- Dual homed provides link redundancy
- Single homed provides no link redundancy
- Dual homed provides two connections to same ISP
5. Describe WAN access connectivity options
The following table summarizes characteristics of WAN access protocols:
Table 2: Characteristics of WAN Access Connectivity Protocols
| SSL VPN | web-based encryption, dynamic, easy to deploy, granular application security |
| MPLS | branch office, multiprotocol support, WAN access solution, layer 2.5, layer 3 VPN |
| IPsec VPN | static VPN, private, point-to-point topology, difficult to deploy, router peering |
| DMVPN | internet-based VPN, layer 3, cloud connectivity, IWAN, dynamic |
| Metro Ethernet | easy to deploy, layer 2, bandwidth on demand, distance limits |
| PPPoE | internet-based, layer 2, DSL, cable, static configuration |
Multiprotocol Label Switching (MPLS)
MPLS is a layer 2.5 WAN transport solution that encapsulates layer 2 transport protocols. Internet routing is provided to customers across the MPLS network. MPLS segments customer traffic streams with a label and tag. The following are four standard advantages available with MPLS:
- multiprotocol transport
- IPv4 and IPv6 support
- any-to-any connectivity
- QoS support
Three advantages of DMVPN connectivity over traditional services:
- scalability
- increased security
- cost effective
Standard VPN services are characterized by the following attributes:
- privacy (data encryption)
- data integrity (hashing)
- authentication (RSA)
6. Configure and verify single-homed branch Connectivity with eBGP
BGP is a routing protocol with connectivity based on TCP transport. The BGP router ID provides recovery from TCP session collisions. The highest loopback IP address is assigned as router ID by default.
The local router identify a BGP neighbor based on IP address and autonomous system number for peering purposes. BGP advertises routes based on the configured static routes (ip route) and the network command.
eBGP Configuration
The following commands will configure a BGP routing instance and assign it to AS 10.
The neighbor command creates an eBGP session with the remote router based on the neighbor IP address 172.16.1.2 and AS 40. The network command advertises the specific subnet 10.10.34.1/24 to the BGP neighbor.
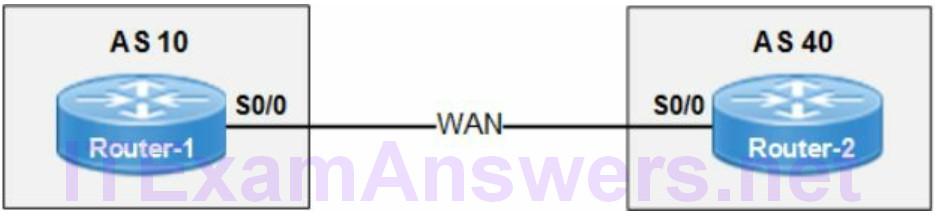
- enable BGP with local AS 10
- add eBGP peering neighbor from AS 40
- assign IP address 172.16.1.2 to remote peer
- advertise network 10.10.34.1/24 to remote peer
r1(config)# router bgp 10 r1(config-router)# neighbor 172.16.1.2 remote-as 40 r1(config-router)#network 10.10.34.1 mask 255.255.255.0
The eBGP session is created when BGP routers assigned to different BGP autonomous systems (AS) are peering.
The network command advertises the network prefixes assigned. In addition the network 0.0.0.0 command advertises the default route in the routing table. The BGP network command must match route installed in local routing table.
Verify eBGP Connectivity
The following command lists all BGP peers for the local router and neighbor adjacency state. The normal adjacency state is Established for a BGP session when routing updates are exchanged.
router# show ip bgp neighbors
The IOS command show ip bgp summary provides a quick summarized lists of all BGP neighbor connections. That includes BGP AS number and up/down connection status. There is memory usage and session activity listed as well.
router# show ip bgp summary
7. Describe basic QoS concepts
Table 3: Characteristics of Standard QoS Techniques
| class map | access groups, traffic matching |
| classification | class of service, DSCP, NBAR, access list |
| congestion avoidance | WRED, tail drop, thresholds |
| service-policy | attach policy to interface |
| bandwidth management | shaping, policing |
| policy map | traffic marking, point to class map |
| congestion management | FIFO, WFQ, PQ, CBWFQ (queuing) |
QoS is only applied when network congestion is detected. The purpose is to manage the available network bandwidth for optimizing network performance. QoS techniques are enabled to decrease latency, packet loss and jitter. It is particularly significant to delay sensitive voice and video traffic.
The following are primary reasons for deploying QoS on a network:
- guarantee SLAs for defined traffic classes
- avoid and manage network congestion
- prioritize traffic classes and assign bandwidth
- minimize packet loss and network latency
Packet Marking
The only network interface that supports Class of Service (CoS) marking is an Ethernet switch trunk. The 802.1q tag is added to an Ethernet frame when trunking is enabled. The 802.1q field is used for VLAN membership tagging. That allows forwarding of multiple VLANs between switches. There is a 3 bit field used for CoS marking and prioritization (queuing) of traffic. Type of Service (ToS) is an 8-bit field in IP packet for DSCP packet marking
Class of Service (CoS)
Routers can only examine the CoS marking of a frame and trust or remark the layer 3 packet. The router would specifically strip off the original frame and rewrite MAC addressing. In addition the router would either trust the CoS value or rewrite a DSCP value equal to the CoS marking. Layer 2 switches are configured with a trust state that determines frame handling.
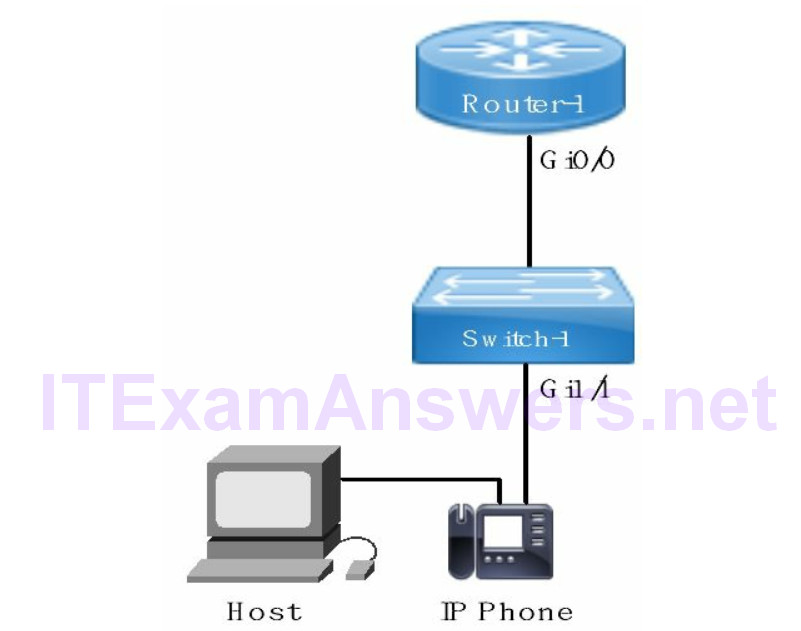
Cisco IP phones mark all voice traffic to the switch with default CoS 5. In addition a trunk is created from the IP phone to the switch when the voice VLAN feature is enabled. The trunk tags voice packets from the phone and data from the host to an access port on the switch.
Trust State
The trust state of a switch determines how the packet marking is interpreted for ingress traffic. The default trust setting for a Cisco switch is untrusted. The switch will remark the CoS or DSCP value to zero (0) for all ingress packets on an untrusted interface.
The switch will examine an ingress packet and forward it unaltered when trust state is enabled. For instance voice packets marked as Cos 5 from an IP phone are forwarded with that value. Packets from a host are remarked from a default zero (0) to a configured value on a trusted interface.
Defining trust boundaries across the network topology affects how packets markings are processed. All network devices within a trust boundary won’t remark packets as they traverse. The following are key points for QoS trust boundary configuration.
- packets from a trusted device are not remarked on upstream device
- trust boundary defines the point where trusted packets start
- trust boundary is configured with mls qos trust cos | dscp command
Compare Shaping and Policing
The following statements describe the supported features for shaping and policing. In addition the differences are noted as well.
- Policing does not queue packets
- Shaping does support packet queueing
- Policing is applied to ingress and egress interfaces
- Policing drops or remarks traffic that exceed CIR
There is no support for traffic shaping on ingress interfaces (egress only). In addition policing does allow access lists as a classification method.
Traffic Policing
Traffic policing allows you to control the maximum rate of traffic transmitted or received on an interface. Traffic policing is often configured on interfaces at the edge of a network to limit ingress and/or egress traffic. The standard configuration is to transmit packets less than or equal to CIR and drop or remark packets that exceed CIR.
The primary purpose of traffic policing is to provide multiple options for packet handling based on allowed data rate and burst rate. The conditions include conforming, exceeding and violating. The actions include forward, remark or drop. The following describe each condition and the action available.
conforming = packet is forwarded or remarked
exceeding = packet has exceeded limits and is dropped or remarked
violating = data rate is faster than CIR and allowed, dropped or remarked
Note that remark can refer to either marking up or down of a packet. The network administrator could decide for instance to remark packet to a higher (preferred) DSCP marking in the Type of Service (ToS) field of an IP header.
The following table summarizes the standard queuing techniques available:
Table 4: Standard Queuing Techniques
| Priority Queuing | traffic assigned to queue is emptied first |
| FIFO | default hardware queuing (QoS disabled) |
| WFQ | assigns bandwidth based on weights |
| WRED | congestion avoidance to avoid queue tail drops |
| CBWFQ | assigns specific bandwidth to traffic classes |
Congestion Management
Congestion points where QoS is most recommended and crucial include aggregation uplinks and LAN to WAN transition. The bandwidth assigned to the priority queue (PQ) is allocated whether the interface is congested or not. It works as a minimum bandwidth guaranteed to the assigned traffic class at all times. Packets assigned to the priority queue are discarded when the bandwidth is exceeded.
The bandwidth assigned to Class Based Weighted Fair Queues (CBWFQ) are used only when there is congestion. That allocated bandwidth is available to all traffic classes until then. In addition they are serviced (dequeued) only after the priority queue is emptied.
