1. Describe and verify switching concepts
The following is a list of network services provided by switches:
- switches forward data link layer traffic
- switches create and maintain the MAC address table
- switches support segmenting collision domains
MAC address table
Every network device is assigned a unique hardware address from the manufacturer called a MAC address. The purpose of a MAC address is to provide a unique layer 2 identifier. That enables communication between devices of the same network segment (VLAN) or different segments. The switch forwarding decisions are based on the MAC address and assigned port.
- enable packet forwarding between hosts on the same VLAN
- globally unique network device identifier associated with a VLAN
The MAC (physical) address is 48 bits of hexidecimal numbering. The first 24 bits is a manufacturer OUI and the last 24 bits (bold) is a unique serial number (SN).
OUI | SN
0000.000a.aaaa
The switch builds a MAC address table comprised of MAC address, switch port and VLAN membership for each connected host. The switch creates a separate MAC address table for each configured VLAN. Any unicast flooding of a frame to learn a MAC address is for the assigned VLAN only.
The following IOS show command will list the contents of the MAC address table for a switch. Where there are multiple VLANs configured, the switch will list all MAC address tables for all VLANs in a single table listing. The switch builds and maintains a separate MAC address table for each VLAN configured.
switch# show mac address-table
Microsegmentation
The newer Ethernet Gigabit switch ports that support full-duplex operation have enabled microsegmentation. That eliminates collisions on the switch and dedicates all port bandwidth to the connected host. CSMA/CD is a method for detecting Ethernet collisions on older hubs and bridges. It is no longer required with full-duplex switch ports. Each frame is assigned a random time to re-send a frame when collisions occur.
Switching Methods
Cut-Through Switching
The cut-through switching technique optimizes performance by examining only the first six bytes (destination MAC address) of an Ethernet frame before making a forwarding decision. The switch does a MAC address table lookup for the destination MAC address and forwards the frame. The advantage is the forwarding decision is made before all of the frame arrives and thereby minimizing network latency.
Store-and-Forward Switching
The store-and-forward method is traditional switching where the frame is not forwarded until all of the frame has arrived. The switch copies the frame to memory before examining the destination MAC address and forwarding the frame.
Cisco Express Forwarding (CEF)
CEF is a layer 3 switching technique that creates FIB and adjacency tables for optimized packet forwarding. It is only available on routers and switch platforms with routing enabled and the required hardware.
MAC learning and Aging
MAC address learning occurs when the switch is first started and connected hosts start sending frames. In addition MAC learning is triggered when the aging time expires. The switch removes MAC address table entries every five minutes as a default.
The layer 2 broadcast is forwarded to all devices on a single broadcast (segment) domain. The switch creates the broadcast packet ffff.ffff.ffff as the destination MAC address and forwards it out all ports except where the frame was learned. The port where the frame was learned is the sending host. Note that broadcast frames are created and never learned from an inbound switch port. The following summarizes what happens when a host sends a packet to a server on the same VLAN for the first time.
1. The switch adds the source MAC address of the incoming frame if it is not listed in the MAC address table.
2. The switch does a MAC address table lookup for the destination MAC address.
3. The switch floods the frame using destination MAC address ffff.ffff.ffff out all ports except the port where the source MAC address was learned.
4. The server with the assigned MAC address responds with a frame that lists the MAC address.
5. The switch updates the MAC address table with the MAC address of the server. That is the destination MAC address for frames sent from the host.
6. The switch forwards the frames from the host to the server based on the switch port assigned to the server.
Unicast MAC Flooding
The switch will first flood the local VLAN segment (unicast MAC flooding) to determine if the host is local. The ARP broadcast is only sent for packet forwarding between local and remote hosts on different VLANs or subnets. Unknown unicast frames are retransmitted only to ports that belong to the same VLAN.
Broadcast Domain
The VLAN creates a broadcast domain that is defined by assigning switch port/s to the same VLAN. All hosts connected to switch ports of the same VLAN are part of the same broadcast domain. Creating multiple VLANs defines multiple broadcast domains. Switches do not forward broadcast or multicast traffic between VLANs minimizing bandwidth utilization compared with hubs and bridges. The switch only forwards unicasts, broadcasts and multicasts on the same segment (VLAN).
Frame Switching
The host sends packets with an IP header encapsulated in a frame. The source and destination IP address in the header are required for end-to-end connectivity. Layer 2 switches do not examine or understand IP addressing.
Switches and wireless access points are network devices that make forwarding decisions based on the destination MAC address in the frame. They do not change MAC addressing in the frame. Wireless access points are essentially bridges.
The switch does not rewrite MAC addressing in the frame header. It examines the source MAC address and destination MAC address. The source MAC address of the incoming frame is added to the MAC address table if it isn’t listed.
The switch examines the frame header for the destination MAC address and does a MAC address table lookup to make a forwarding decision. The frame is then forwarded out the switch port associated with the destination MAC address where the host is connected. Any destination MAC address that is not local is forwarded to the router. The IP addressing does not change between source and destination.
- switches use the MAC address in a frame to make forwarding decisions
- switches forward frames and don’t rewrite source or destination MAC address
Routers make forwarding decisions based on source and destination IP address. The router will do a routing table lookup then rewrite the source and destination MAC address in the frame header.
Frame Switching Examples
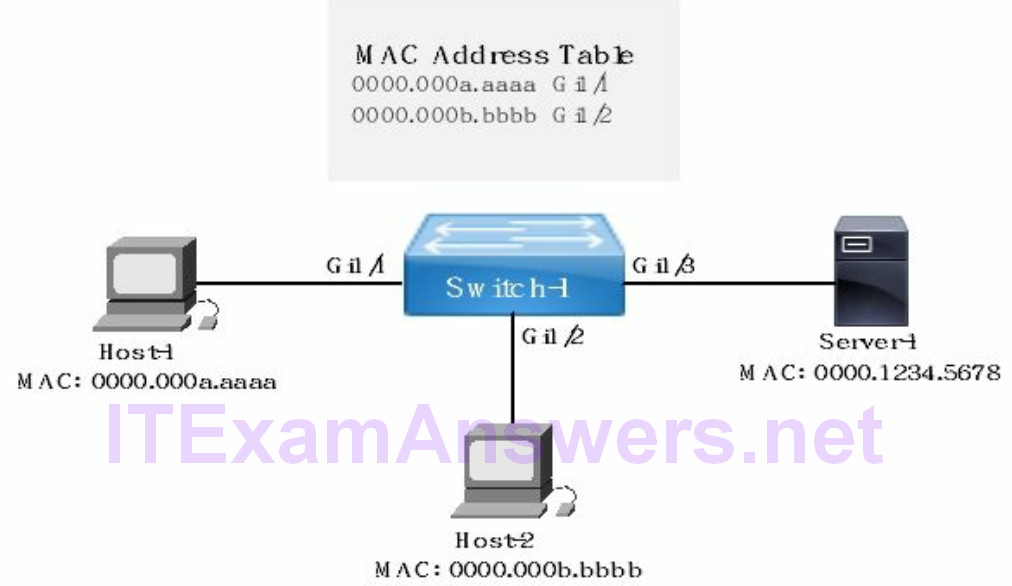
Example 1:
Refer to the network drawing where Host-1 has sent a packet to Server-1. The destination MAC address is unknown. The switch will unicast flood (learning) the frame out all ports except the port where the frame was learned from (Gi1/1). Server-1 with the matching destination MAC address receives the frame and sends a frame to Switch-1. The switch updates the MAC address table with the MAC address and associated port (Gi1/3) of Server-1.
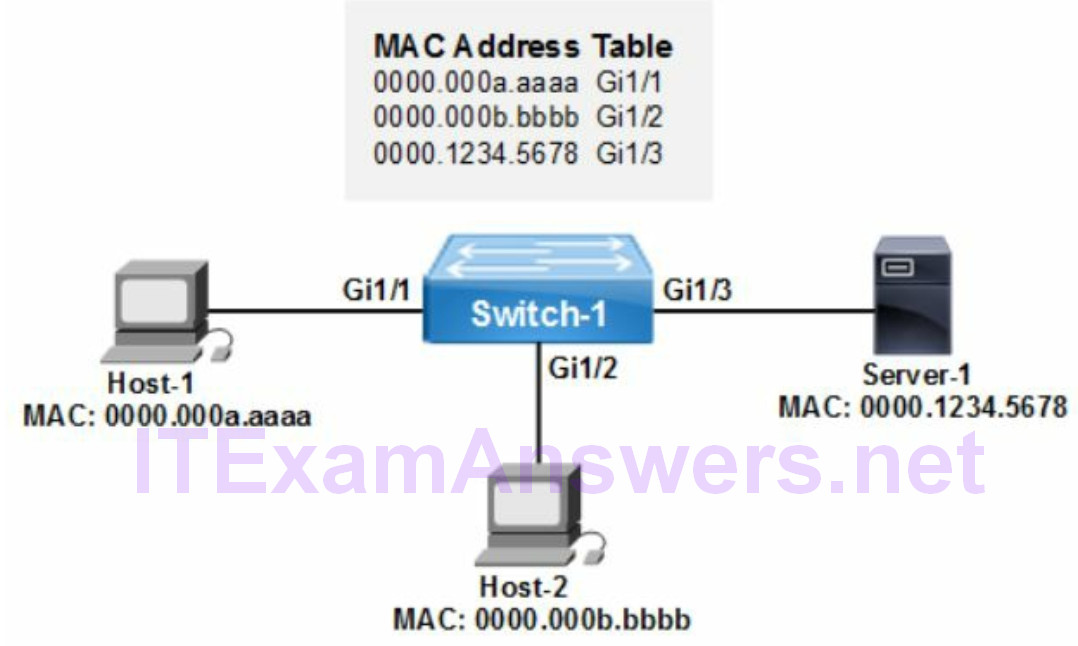
Example 2:
Refer to the network drawing where Host-2 has sent a packet to Server-1. The switch will examine the source and destination MAC address of the frame arriving on port Gi1/2 from Host-2. The MAC address table has no entry for either MAC address. The switch will then add the source MAC address (Host-2) to the MAC table. In addition the switch will unicast flood (MAC learning) the frame out all ports except the port where the frame was learned from (Gi1/2). Server-1 with the matching destination MAC address receives the frame and sends a frame to the switch. The switch updates the MAC address table with the MAC address of Server-1.
- 0000.000b.bbbb will be added to the MAC address table
- frame will be forwarded out all active switch ports except port Gi1/2
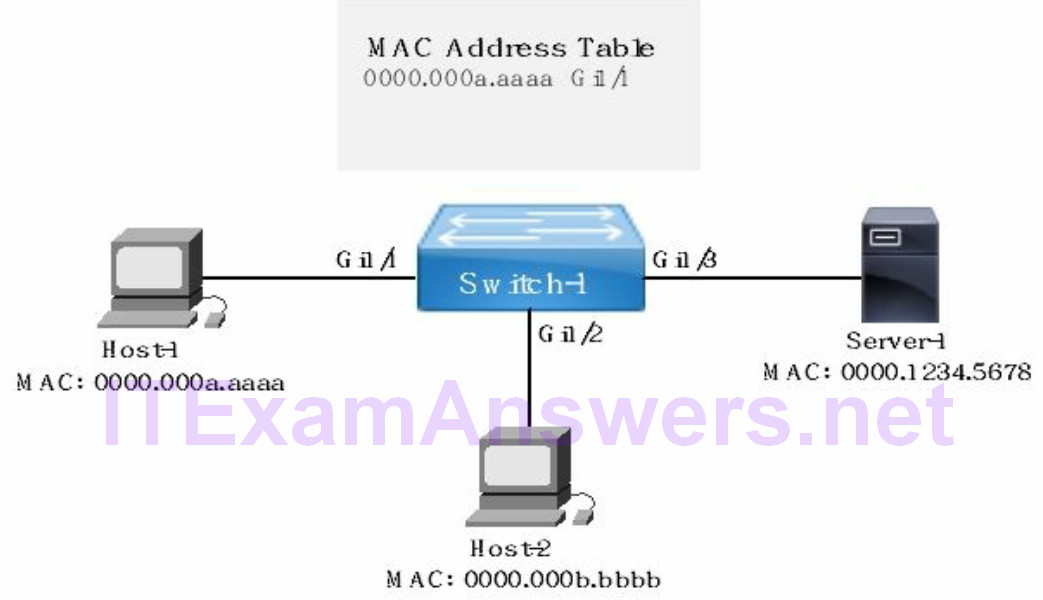
Example 3:
Refer to the network drawing where Host-2 has sent a packet to Server-1. Switch-1 will examine the incoming frame from Host-2 arriving on port Gi1/2. The switch will do a MAC table lookup based on the destination MAC address. The switch determines the destination MAC address is assigned to Server-1. The frame is forwarded to port Gi1/3 associated with Server-1.
- switch will examine the frame and do a MAC address table lookup
- frame is forwarded out switch port Gi1/3
2. Interpret Ethernet frame format
The Cyclic Redundancy Check (CRC) is a number (FCS) calculated on each frame received to verify data integrity. The layer 2 frame is discarded if the received FCS number doesn’t match the original. It is an error detection technique and not error recovery. Any error detection and/or error recovery is managed by transport layer 4 protocols. The source MAC address (SA) and destination MAC address (DA) are 6 bytes. The following are the fields that comprise an Ethernet frame.
- FCS
- type/length
- preamble
- source MAC address (6 bytes)
- destination MAC address (6 bytes)
- payload (variable)
3. Troubleshoot interface and cabling errors
Show Interfaces
The results provided by the show interfaces command include layer 1 and layer 2 status information for all or individual network interfaces (ethernet, serial etc).
Interface = Layer 1, Line protocol = Layer 2
The possible interface states for interface and line protocol include up, down or administratively down. The normal status of an Ethernet interface is up/up. The shutdown command would change interface status to admin down. (i.e down/down). It is not possible to have line protocol in up state when the interface is down (down/up). The following commands verify interface and line protocol status for a switch interface:
- switch# show interfaces
- switch# show protocols
switch# show interfaces fastethernet1/1
FastEthernet 1/1 up, line protocol up (normal state)
Typical Interface Errors:
Layer 1 = cabling, switch configuration mismatches (speed/duplex) errors.
Layer 2 = encapsulation mismatch, spanning tree, clocking errors.
This example has the interface (layer 1) up and line protocol (layer 2) down. The Ethernet signaling is working and there are no issues with cabling. The problem is at the data link layer or higher. It is possible as well that layer 3 routing or IP addressing issues are causing the error however that is unknown.
switch# show interfaces fastethernet0/1
FastEthernet 0/1 up, line protocol down
The show interfaces command provide the following operational status and configuration settings.
switch# show interfaces
- interface status
- interface errors
- encapsulation
- MAC address
- IP address
- subnet mask
- MTU size
Duplex Setting
The Gigabit Ethernet switch port supports full-duplex traffic between the host and network switch. That eliminates collisions and creates a collision domain per port. The fact that there are no collisions increase throughput and decreases network latency. Hosts connected to a full-duplex switch port create a collision domain per port.
Traffic can be sent simultaneously in both directions between the host and network switch. That effectively doubles the bandwidth available from 1 Gbps to 2 Gbps. The default setting for Ethernet Gigabit and higher is full-duplex mode.
Gigabit Ethernet switch ports have eliminated collisions unless there is a configuration error or hardware issue. Collisions are caused most often when there is a duplex mismatches on connected interfaces. In addition collisions can occur when there is a bad network interface card (NIC) or cabling error. The switch increments collision counter error after sending 512 bits of a frame.
The following are preferred duplex settings to minimize interface errors on switch links:
- configure full-duplex setting on both switch link interfaces
- configure auto-negotiation on both switch link interfaces
Duplex mismatches with a neighbor interface can cause the following interface errors:
- collisions
- input errors
- CRC errors
- slow performance
The cause of collisions on a broadcast domain (VLAN) instead of interfaces are typically the result of duplex mismatches and faulty network interface card (NIC).
Ethernet Interface MTU
MTU refers to the maximum size (bytes) of an Ethernet frame. The default Ethernet MTU is 1500 bytes. The frame is comprised of a header and payload (data). The header is a fixed size with fields for control and MAC addressing. Decreasing the MTU size would decrease the payload amount (bytes) that can be transmitted.
- default = 1500 bytes
- jumbo = 9216 bytes
- baby giant = 1600 bytes
- runt = < 64 bytes
The output of show interfaces is used for troubleshooting various Layer 1and layer 2 interface errors. Layer 2 errors include runts, giants, collisions and CRC errors. The most common cause of CRC and runts is collisions. Giant frames result from either a bad NIC card or an MTU configuration error.
Ethernet interfaces that are in err-disabled state cannot send or receive frames and are essentially shutdown. It is a layer 2 error and the cause is operational or a configuration mismatch. The following are some typical causes of err-disabled state:
- duplex mismatch
- port security violation
- EtherChannel mode mismatch
- UDLD errors
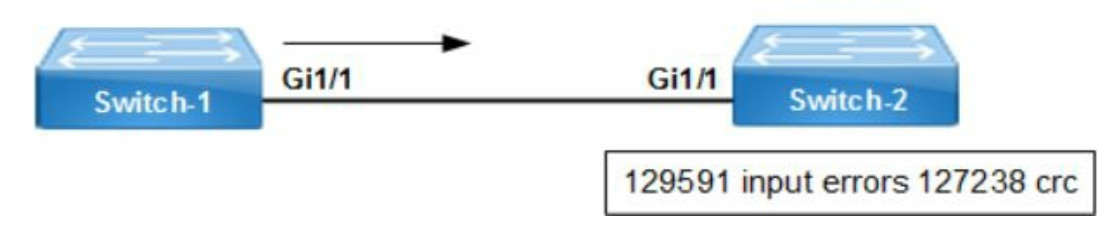
Troubleshooting Example:
Refer to the network drawing. There are a high number of input errors and CRC errors on Switch-2. That indicates there is a layer 1 issue between the switches. Switch-1 is sending frames that are corrupt when they arrive at Switch-2. The most probable cause is duplex mismatch between the switch interfaces or cabling errors.
The switch ports must agree on the duplex setting. Gigabit Ethernet ports do not use half-duplex at all. The Cisco switch default setting is duplex auto (for full-duplex mode. There is however the option to hard code with the interface command duplex full.
The speed setting must match between switches as well. That is configured with the speed auto command or hard code with speed 1000. Since the frames were arriving at Switch-2, verify the duplex setting on Switch-1 to start with. Cabling defects require replacement when the correct cable type is currently used to fix layer 1 issues
4. Configure, verify and troubleshoot VLANs
The primary purpose of a VLAN is to create a broadcast domain defined by assigning a single or multiple switch ports. All unicast, broadcast and multicast traffic is limited to the VLAN. That conserves bandwidth usage across the switching infrastructure.
The following are the guidelines for deploying VLANs to a Cisco switch.
- Normal Range VLANs = 1 – 1005
- Extended Range VLANs = 1006 – 4094
- VLAN 1, 1002 – 1005 are automatically created and cannot be deleted
- VLAN 1006 – 4094 cannot be pruned from a trunk
All switch ports are assigned to VLAN 1 as a default configuration for Cisco switches. In addition VLAN 1 is used for management traffic and cannot be deleted. The normal range VLANs (2-1001) can be added, modified and deleted from the switch. Cisco recommends assigning all data and voice traffic to a non-default VLAN.
Advantages of VLANs
VLANs do not prevent broadcast storms, they minimize the size and effect of the broadcast storm on neighbor switches and hosts. The VLAN is a broadcast domain and as such broadcasts are not advertised outside of the VLAN minimizing bandwidth usage and multicast traffic.
1. Enable access to network services based on logical requirements such as company organization and department.
2. Network security is optimized with VLANs by segmenting sensitive traffic and segmenting it from other network traffic.
3. Bandwidth efficiency is accomplished through segmenting traffic into smaller broadcast domains. Unicasts, broadcasts and multicasts are not forwarded between VLANs minimizing bandwidth utilization.
4. Ease add/move/delete administration of hosts on the network and scalability for larger enterprise deployments.
Access ports (data and voice)
The switch access port provides connectivity for access devices such as a desktops, servers and wireless access points. The switch port can only be assigned one VLAN unless you are connecting an IP phone. The data VLAN and voice VLAN is permitted on an access port with the following configuration commands.
switch(config)# interface fastethernet0/1
switch(config-if)# switchport mode access (configure access port mode for Fa0/1)
switch(config-if)# switchport access vlan 9 (assign vlan 9 to data traffic)
switch(config-if)# switchport voice vlan 10 (assign vlan 10 to voice traffic)
The following commands list all VLANs configured on a switch. That includes VLAN number, VLAN name, status and port assigned.
switch# show vlan
switch# show vlan brief
The following command is used to verify any/all switch ports assigned to a single VLAN.
switch# show vlan id [vlan]
The Cisco switch port supports access mode or trunk mode. The network administrator configures the port mode when enabling the interface. The standard layer 2 switch port is referred to as an access port. Switch access ports that receives a packet with an 802.1q tag in the header will discard the packet without learning source MAC address.
Interface Range
The following IOS command creates and assigns VLAN 10 to switch port range Gi1/1 through Gi1/24 interfaces. There is no requirement to first create the VLAN in global configuration mode. The vlan.dat file is the VLAN database where the switch VLAN configuration is stored.
switch(config)# interface range gigabitethernet1/1-24
switch(config-if)# switchport mode access
switch(config-if)# switchport access vlan 10
Switchport Command
The administrative mode is the switch port configuration and operational mode is the interface status. The switch won’t setup a trunk unless the switch port mode on both switch ports are configured to trunk VLANs.
Administrative Mode
- trunk
- dynamic desirable
- dynamic auto
- static access
Operational Mode
- trunk
- static access
- down
Default VLAN
VLAN 1 is the default for any Cisco switch that has no initial configuration. The primary purpose of VLAN 1 is to forward management traffic between switches. The following statements correctly describe VLAN 1:
- All switch ports are assigned to VLAN 1 as a default.
- Default VLAN 1 forwards management traffic and cannot be deleted.
- Assigning data and/or voice traffic to VLAN 1 creates a security vulnerability.
Default Gateway
The ip default-gateway command on a switch configures the IP address of the router interface to forward packets when the destination is on a different VLAN or subnet.
The following IOS command will configure a connected upstream router as the default gateway for the switch. The router has an interface with IP address 172.16.1.254 on interface Gi0/1. The switch forwards packets to the default gateway for layer 3 services. That could include ARP requests, Inter-VLAN routing and remote subnet connectivity.
switch-1(config)# ip default-gateway 172.16.1.254
Refer to the network drawing. The default gateway is the upstream layer 3 device (router) that provides routing services. The default gateway for Host-1 is 172.16.1.254. The IP address of the directly connected interface (Gi0/0) to the layer 2 switch is assigned as default gateway for the host. The host, switch and default gateway must be in the same subnet.
Default Cisco switch configuration
- single broadcast domain (VLAN 1)
- all hosts are in the same broadcast domain
- switch port mode is unassigned
- switch with lowest MAC address is the root bridge
- VTY lines are not enabled
5. Configure, verify and troubleshoot Inter-switch connectivity
Trunk Ports
The purpose of a switch trunk is to forward multiple VLANs between switches. The switch port must be configured for trunk mode to enable forwarding of multiple VLANs. That allows communication between hosts assigned to the same VLAN that spans switches. Forwarding multiple VLANs across a switch link requires trunk mode to enable the VLAN tagging feature.
switch(config-if)# switchport mode trunk
The following show commands display configuration information for all trunk interfaces.
switch# show interfaces trunk
switch# show interface switchport
The IOS commands display the following trunk operational and configuration settings:
- tunk operational status
- switch port members
- VLANs allowed
- native VLAN
- encapsulation type
- trunk mode
Configuring a switch port as a trunk requires enabling trunk mode and 802.1q encapsulation. The following trunk is static and DTP trunk negotiation is not used.
switch(config)# interface fastethernet0/1
switch(config-if)# switchport mode trunk
switch(config-if)# encapsulation dot1q
switch(config-if)# end
Native VLAN
The native VLAN is used to forward control traffic across the switch trunk. Changing the native VLAN from VLAN 1 to any available nondefault VLAN is a Cisco security best practice. There are security vulnerabilities associated with the default VLAN 1. In addition STP issues are minimized by selecting a nondefault VLAN instead of VLAN 1.
Control traffic (CDP, PAgP, VTP, STP and DTP) always uses VLAN 1 and travel on the native VLAN (untagged traffic) by default. The trunk tags all data VLANs for identification purposes. The untagged traffic is separated from data traffic as a result.
None of the control traffic except STP and DTP are forwarded across the native VLAN when the native VLAN is changed to a nondefault value. STP and DTP are management protocols that must be untagged across trunk links.
The following command changes the native VLAN from default VLAN 1 to VLAN 999.
switch(config-if)# switchport trunk native vlan 999
The native VLAN configured on a trunk link must match between switches to forward untagged packets across the trunk correctly. VLAN hopping is a security vulnerability caused by native VLAN mismatch. STP and DTP can detect native VLAN mismatches.
VLAN Pruning
The purpose of VLAN pruning is to permit or deny VLANs across a switch trunk. The Cisco default is to allow all VLANs across the trunk. The switch is configured for VLAN pruning won’t forward specific VLANs across a switch trunk. The local switch alerts the neighbor switch of all local VLANs that are not active (not configured).
Any VLANs that are not configured are pruned by the neighbor switch to minimize unicast, broadcast and multicast traffic across the trunk. The Cisco default trunk configuration allows all VLANs from the range 1 – 4094 across the trunk.
The following IOS command will only allow VLAN 10, VLAN 11 and VLAN 12 across the trunk. The network administrator can add or remove VLANs after that IOS command is issued based on requirements. The command permits commas for multiple nonconsecutive VLANs or hyphen to specify a range of consecutive VLANs.
switch(config-if)# switchport trunk allowed vlan 10-12
The add | remove keyword only applies after pruning has already occurred on the trunk interface to limit the VLANs allowed from the default range (1-4094). Configure the following IOS command to allow only a single VLAN or multiple VLANs. Cisco switches permit assigning a range of VLANs as well.
switch(config-if)# switchport trunk allowed vlan add [vlan id, vlan id, …]
The following IOS command will remove VLAN 10 from the trunk. That will filter all traffic from that VLAN so it cannot traverse the trunk link between switches. To remove a range of consecutive VLANs such as from VLAN 1 to VLAN 100 inclusive, use a hyphen (1-100). For a non-consecutive list such as VLAN 1 and VLAN 10,11,12 use commas and hyphens (1,10-12).
switch(config-if)# switchport trunk allowed vlan remove 10
The following IOS interface command will add VLAN 12 to the trunk interface. That will permit all traffic from that VLAN so it can traverse the trunk link between switches. To add a range of consecutive VLANs such as from VLAN 1 to VLAN 100 inclusive, use a hyphen (1-100). For the example where there is a non-consecutive list such as VLAN 1 and VLAN 10,11,12 use commas and hyphens (1,10-12).
switch(config-if)# switchport trunk allowed vlan add 12
Dynamic Trunking Protocol (DTP)
The switch port is configured as a trunk to enable trunking. The trunk is setup with a neighbor switch using static or dynamic negotiation. The static trunk is a manual configuration that isn’t based on any negotiation protocol.
- DTP enables dynamic negotiation of a trunk between two switches.
- DTP modes are nonegotiate, desirable and auto.
- DTP is enabled by default
The DTP request frames are sent to the neighbor switch to negotiate the trunk setup. Cisco switches use the default auto mode. The switch port configured with desirable or auto mode listen for DTP requests. In addition the switch port configured with desirable mode actively sends DTP frames to establish trunk with neighbor.
The switches on both sides of the link are configured with the command switchport mode trunk. It is equivalent to the on keyword for dynamic trunking. DTP provides dynamic negotiation based on the switchport mode dynamic auto or switchport mode dynamic desirable commands.
The following describe the effect of each static and DTP mode:
switchport mode access = no trunking
switchport mode trunk = static (on) mode
switchport mode dynamic auto = listens for DTP requests
switchport mode dynamic desirable = listens/sends DTP requests
switchport mode nonegotiate = disable DTP
The following describes how each switch mode affects trunk setup between local and remote switches. Access mode is equivalent to a switch access port (no trunk). The on mode is configured manually at the switch (static trunk) and not a DTP mode.
Table 1. Dynamic Trunking Protocol Modes
| local switch | neighbor switch | result |
|---|---|---|
| auto | auto | access port |
| auto | desirable | trunk |
| auto | on | trunk |
| desirable | on | trunk |
| desirable | desirable | trunk |
| nonegotiate | nonegotiate | access port |
| nonegotiate | on | trunk |
When two connected ports are connected and at least one of the ports is configured as desirable, the two switches will negotiate the formation of a trunk across the link. DTP auto mode supports access mode and trunk mode. The neighbor incoming negotiation would determine whether the switch port operational mode is trunk or static access.
DTP auto allows the port to negotiate DTP if the other side is set to trunk or desirable. The nonegotiate mode is configured on both switch interfaces that do not support DTP mode or should not establish trunking. The following are methods for disabling DTP on a switch link:
- switchport nonegotiate
- switchport mode access
- static trunk
Troubleshooting
The following are common causes of trunking errors:
- VLAN mismatches
- incorrect trunk mode
- VLANs not allowed (pruned)
VLAN Trunking Protocol (VTP)
- VTP enable VLAN configuration automatically across multiple switches
- VTP enables synchronization of VLANs between subnets
VTP Requirements
- configure all switch uplink ports to trunk
- designate at least one VTP server
- configure all switches with the same VTP domain name and password
- switch must be in VTP server or transparent mode before configuring VLANs
Primary VTP v2 feature enhancements:
- Token Ring VLANs
- VLAN consistency check
- transparent mode switch forwards VTP advertisements with no version check
The VTP modes assignable to a Cisco switch are client, server and transparent. The default mode is server when enabling VTP.
802.1q Encapsulation
Trunking enables forwarding of multiple VLANs across a single switch link. Ports between switches must be configured with trunk mode to forward multiple VLANs across a switch link. The 802.1q protocol is an encapsulation method that enables forwarding of multiple VLANs across the switch link. The 802.1q tag has a 12 bit VLAN ID field used for identifying VLAN membership of the frame.
The switch adds an 802.1q tag to each Ethernet frame with VLAN membership. That allows the switches to identify the VLAN for each arriving frame. The Ethernet frame header is modified as a result of adding the VLAN tag. That requires recalculation of the FCS value used for CRC.
The following are the primary characteristics of 802.1q encapsulation.
- open standard for multi-vendor switch connectivity
- Cisco switch default setting
- provides VLAN tagging across a switch trunk
6. Configure, verify and troubleshoot STP protocols
The primary reason for deploying Spanning Tree is to prevent layer 2 loops and broadcast storms where frames are forwarded in a loop between switches. The most current STP protocol supports per VLAN instances (PVST+).
Redundant topologies are characterized by multiple paths that could cause layer 2 loops. STP is deployed to forward and block specific ports to eliminate forwarding loops between switches. Specific problems caused by redundant topology include sending multiple frames, broadcast storms and MAC address table instability. Some possible problems that can occur when configuring redundant links between switches:
- additional frames sent
- broadcast storms
- MAC address table instability
STP creates a loop free layer 2 topology by configuring some switch ports to forward traffic and some to block traffic. That is based on electing a root bridge. The switch with the lowest bridge ID is elected root bridge. The bridge ID is comprised of priority setting and MAC address. STP calculates lowest path cost for each neighbor interface to the root bridge. The neighbor switch port that receives the best BPDU (least cost to the root bridge) is assigned root port for that switch.
The BPDU is a Spanning Tree Protocol message that is sent between switches. The hello timer setting is the interval between BPDU advertisements. The BPDU messages contains STP information from the sending switch. That includes STP timers, root bridge ID, sender bridge ID and port (path) cost.
STP will assign a port type to each switch port uplink and an STP interface state for each port as well. The purpose is to create a loop free layer 2 topology. The switching infrastructure is Layer 2 converged when spanning tree has elected a root bridge, designated ports, root ports, backup ports and alternate ports. In addition RSTP switch ports are forwarding or discarding. Frames are forwarded after trunk is established (where applicable) and STP election has occurred. There are four STP port states with the original 802.1d STP:
- Blocking
- Listening
- Learning = populating MAC address table
- Forwarding
STP mode (PVST+ and RPVST+)
Per VLAN Spanning Tree Plus (PVST+) enables a separate 802.1d spanning tree instance per VLAN. It was developed to support 802.1q encapsulation for Cisco devices only. The original 802.1d standard was designed for a single broadcast domain. VLAN based spanning tree for any switching topology permits only one root bridge per VLAN.
Per VLAN Spanning Tree (PVST) assigns one root bridge per VLAN. Spanning Tree Protocol elects only one root port to a switch where there are redundant links. The root port transitions to forwarding state and sends frames to the root bridge. There is a root port elected for every neighbor that connects to the root bridge (switch). All switch uplinks for the root bridge are designated ports and transitioned to forwarding state.
The default VLAN bridge priority value for a Cisco switch is 32768. The switch with the lowest MAC address is elected as the root bridge when priority values are equal. The interface port priority setting can change the preferred forwarding interface on a switch.
The newer 802.1w (RSTP) standard is comprised of three port states. They include discarding, learning and forwarding. The discarding state is new to RPVST and equivalent to the blocking and listening states of older 802.1d protocol. The single RSTP discarding state enables faster convergence
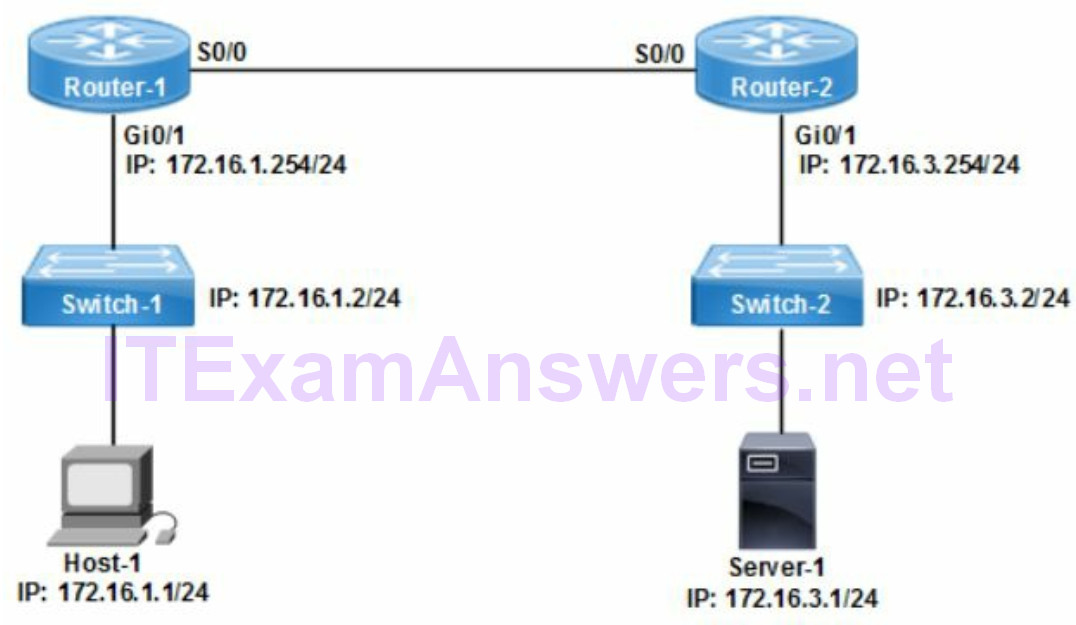
Verify PVST+
Refer to the exhibit. The IOS command show spanning-tree vlan 10 provides per VLAN spanning tree status for VLAN 10. The rstp indicates 802.1w is enabled and Switch-1 is assigned as the root bridge for VLAN 10. The root bridge priority (28682) is lower than the default 32768. Root bridge ports are always designated ports and in forwarding state.
- rstp = state of discarding, learning or forwarding
- root bridge priority is lower than the default value for spanning tree.
- all root bridge ports are designated ports are in a forwarding state.
- local switch is the root bridge for VLAN 10
The following IOS global configuration command enables RSTP on a switch.
switch(config)# spanning-tree mode rapid-pvst
The advantage of Rapid Spanning Tree Protocol (RSTP) is faster layer 2 convergence than the older 802.1 standard. The newer standard is 802.1w and includes the following features to minimize convergence time.
- BPDUs are now advertised from all switches instead of from the root bridge only.
- The amount of time is decreased to three hello packets (BPDUs) before detecting root switch link failure.
- Three port states: discarding, learning and forwarding for faster convergence.
- RSTP convergence includes forwarding and discarding states.
- There are two additional STP port types: alternate and backup.
- RSTP is compatible with the original IEEE 802.1d STP
Alternate Port
Replaces the 802.1d blocking state. The alternate port as with all RSTP ports are actively forwarding or discarding. The discarding is equivalent to the older listening state. It transitions from discarding to forwarding immediately when the designated port fails so there is no waiting for convergence.
Backup Port
Requires a hub with two switch links (single collision domain) to provide additional redundancy for faster convergence to the access layer. The RSTP proposal/agreement process is based on a handshake between point-to-point neighbor switch links. It provides current root bridge state information to all switches. It is not a timer-based proposal/agreement as with the original 802.1d (STP).
STP Root Bridge Selection
The default priority of a Cisco switch is 32768. STP selects the root bridge (switch) with the lowest priority. The switch with the lowest bridge ID is elected when all switches have the same priority. The bridge ID is calculated from the priority setting and MAC address. The switch with the lowest MAC address becomes the root bridge as a result.
The Spanning Tree election assigns root bridge along with designated ports, root ports and alternate ports to neighbor switches. The root port is a switch port on a neighbor switch that has the least cost path to the root bridge. It is a primary forwarding link to the root bridge.
Example 1:
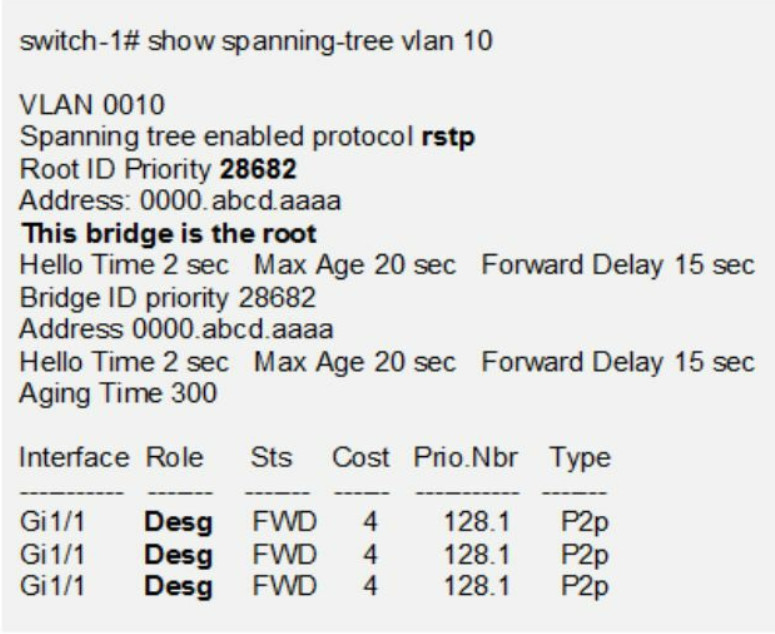
Refer to the network drawing. The root bridge switch ports are all assigned as designated ports by STP. The switch with the lowest bridge ID is assigned as root bridge. The switch priorities are all equal (32768) so the switch with the lowest MAC address is elected root bridge. The designated ports of a root bridge connect to the root port of non-root bridge (switch) neighbors. The root port of a non-root bridge is the switch port with the lowest cost to the root bridge. That is a directly connected switch port with the highest bandwidth. That creates the primary links for switch traffic.
The lowest MAC address is calculated from left to right per hexidecimal number. All numbers match until number 9 where Switch-3 has the lower (a) compared with Switch- 2 (b) and Switch-1 (c). As a result, Switch-3 is elected as root bridge. In addition all switch ports on a root bridge are all designated ports.
Switch-1 = 0000.abcd.cccc
Switch-2 = 0000.abcd.bbbb
Switch-3 = 0000.abcd.aaaa = root bridge
The non-root switches are assigned a designated port as well to forward BPDUs on the network segment. The designated port connects to a neighbor non-root bridge. The nonroot switches compare link cost (bandwidth) for that switch link (network segment).
The switch port with the lower cost (highest bandwidth) is the designated port for that link. When the switch ports are equal-cost, the port of the non-root switch with the lower bridge ID is assigned as a designated port.
The two non-root switches are Switch-1 and Switch-2. There is a single Gigabit Ethernet link connecting the non-root switches. As a result the switch port cost to the network segment is equal. The port of the non-root switch with the lower bridge ID is assigned as a designated port when path costs are equal. Switch-2 has a lower bridgeID than Switch-1. As a result Switch-2 port Gi1/2 is a designated port as well. Switch-1 port Gi1/2 is blocking/alternate port type to prevent layer 2 loops.
Switch-1
- Gi1/1 = Root Port
- Gi1/2 = Blocking/Alternate Port
Switch-2
- Gi1/1 = Root Port
- Gi1/2 = Designated Port
Switch-3
- Gi1/1 = Designated Port
- Gi1/2 = Designated Port
Example 2:
The bridge ID is a numerical value for a switch based on the priority setting and MAC address. The bridge ID is calculated by STP to assign the root bridge for a VLAN. The switch with the lowest bridge ID is elected as root bridge. The lowest MAC address becomes the tie breaker when none of the switches have the lowest priority.
The example has two switches (option C and option D) with the same lowest priority of 28673. The tie breaker is the switch with the lower MAC address. Counting from right to left, the 1 of option D is lower than A of option C. Hexidecimal A is equivalent to the number 10. The switch from option D is elected as root bridge.
28673: 0000.000a.aaaa
28673: 0000.0001.2345
7. Configure, verify and troubleshoot STP STP Enhancements
PortFast
Spanning Tree Protocol (STP) enhancements are designed to optimize network convergence. The uplink interfaces that connect switches are part of STP election. The switching topology is often complex with multiple redundant links. The access layer connects hosts on single point-to-point links where Layer 2 loops do not occur.
PortFast is enabled on access switch ports where hosts and wireless access points are connected. That allows the switch ports to transition from disabled or blocking state to forwarding state immediately on startup. The following IOS command enables PortFast on a switch access port.
switch(config-if)# spanning-tree portfast
BPDU guard
The purpose of BPDU guard is to err-disable (shutdown) an access switch port when BPDUs are received from a network device. BPDU guard is enabled on an access switch port or globally where hosts and supported devices connect. BPDU guard is configured on switch interface to prevent network devices from affecting the STP topology. For instance connecting a new switch to your cubicle jack triggers an STP recalculation. The new switch is now connected to an access switch port causing a layer 2 topology change notification. The consequences could include a new root bridge election. The following command enables BPDU guard on a switch access port.
switch(config-if)# spanning-tree bpduguard enable
8. Configure and verify Layer 2 protocols
Cisco Discovery Protocol (CDP)
CDP is a Layer 2 Cisco proprietary neighbor discovery protocol. The purpose is to discover operational and configuration information for directly connected Cisco devices. The purpose of CDP is to detect and relay device information to neighbor devices.
In addition Cisco CDP can only detect Cisco devices including IP phones. The Cisco IP phone appears to CDP as a unique neighbor device with an IP address. During bootup, the IP phone receives voice VLAN configuration from the access switch.
Configure CDP
CDP is enabled on Cisco devices globally by default including network interfaces. The following command re-enables CDP globally after it has been disabled.
switch(config)# cdp run
The following interface level command re-enables CDP on a specific network interface after it has been disabled.
switch(config-if)# cdp enable
There is additional neighbor configuration information available with the detail keyword used with show cdp neighbor IOS command. The detail keyword includes IOS version of connected neighbors.
switch# show cdp neighbor detail
- CDP is enabled by default both globally and on all network interfaces.
- The default CDP update timer = 60 seconds.
Link Layer Discovery Protocol (LLDP)
LLDP is the open standard counterpart to Cisco CDP for network discovery in a multivendor environment. Cisco supports LLDP (IEEE 802.1ab) and thereby optimizing autodiscovery and network management. The network devices share identity and feature support functionality via LLDP and with neighbors.
- The default packet update interval for LLDP is 30 seconds.
- LLDP is an open standard network discovery protocol specified with IEEE 802.1ab standard.
- Cisco IP phones are enabled for LLDP when LLDP packets are first sent from the phone to the switch.
The following global configuration command enables LLDP globally on a Cisco switch.
switch(config)# lldp run
The following IOS interface level command enables a Cisco switch to receive LLDP packets on an interface.
switch(config-if)# lldp receive
Verify LLDP
Table 2: Show Commands to Verify LLDP Status
| show lldp | verify LLDP is enabled, global timers |
| show lldp neighbors detail | Ethernet media, interface description |
| show lldp interface | list all LLDP interfaces enabled |
9. Configure, verify and troubleshoot EtherChannel
EtherChannel bundles multiple physical switch links between switches into a single logical link. It is sometimes referred to as switch port aggregation. The advantages include fault tolerance (redundancy) and high speed connectivity between switches. Cisco switches support assigning a maximum 8 ports to a single Etherchannel bundle. LACP supports a maximum 16 ports however only 8 can be active simultaneously. The additional ports are used for failover purposes.
Traffic from a previously single Gigabit Ethernet port can now forward traffic across a logical link at higher speed. For instance bundling four separate Gigabit Ethernet links into a single EtherChannel creates a 4 Gbps link. In addition all traffic is forwarded across all available links when any single link isn’t available.
The options for configuring EtherChannel include static or dynamic protocols:
1. Static does not provide any dynamic trunk negotiation. The channel-group is configured with on keyword for all switches ports on both switches assigned to the EtherChannel.
2. PAgP is a Cisco proprietary protocol that provides dynamic negotiation of an EtherChannel link. It supports Cisco network devices only and configured with the channel-group command. The four PAgP modes include on, off, auto and desirable.
3. LACP is an open standard that supports EtherChannel between different switch vendors. It supports negotiating of dynamic EtherChannel links as well. The four modes supported include on, off, active and passive.
Port Channel
There are Layer 2 and Layer 3 port channel interfaces. The channel-group number binds the port channel interface to an Etherchannel. The Layer 2 port channel is a logical interface comprised of Etherchannel access ports or trunk ports. The Layer 2 port channel is created automatically based on the channel-group number. The supported channel-group numbers are 1 – 4096. The Layer 3 port channel is a routed logical interface comprised of EtherChannel access ports or trunk ports. The following is an example of a Layer 3 port channel
switch(config)# interface port-channel 1
switch(config-if)# no switchport
switch(config-if)# ip address 172.16.1.1 255.255.255.0
The following show command lists the port channel and line protocol interface status (up/up). In addition the port channel members are listed along with interface errors.
switch# show interface port-channel [number]
Troubleshooting EtherChannel
The following settings must match on EtherChannel switch ports that connect switches. The port state is err-disabled when the Etherchannel interface is misconfigured.
- duplex
- speed
- protocol mode
- switchport mode
- VLAN
- STP
- native VLAN
Example:
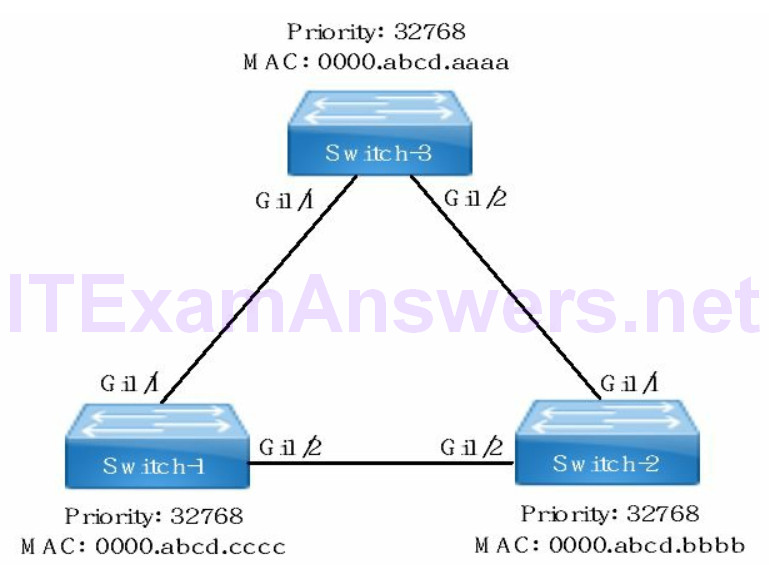
Host-1 from VLAN 10 cannot communicate with Server-1 assigned to VLAN 10.
The network topology drawing is an EtherChannel between two switches connecting Host-1 to Server-1. In addition Host-1 and Server-1 are on the same subnet and same VLAN. It is a layer 2 configuration similar to any data center design. The access ports are forwarding single VLAN (no trunk required).
1. All switch ports assigned to an EtherChannel must be configured with matching settings to prevent err-disable state. The speed, duplex, switchport mode, STP, VLAN membership and protocol mode (PAgP/LACP) must match for each port.
2. Switch-1 (Gi1/1) to Switch-2 (Gi1/1) have a PAgP mode mismatch between switch ports. EtherChannel requires desirable mode on at least one switch port to enable it.
3. Switch-1 (Gi1/2) to Switch-2 (Gi1/2) have a duplex and speed mismatch between switch ports. The correct settings for Gigabit speed or higher is 1000 or auto. The supported duplex setting is half, full or auto however full-duplex is the Cisco default.
EtherChannel across a trunk link requires the native VLAN, allowed VLANs and encapsulation type to match as well.
10. Describe the benefits of switch stacking and chassis aggregation
Switch Stacking creates a single logical switch from up to nine Catalyst switches where supported. The advantages include easier management of a single switch instead of multiple switches. In addition there is faster network convergence with fewer switch uplinks to neighbors.
The Stack elects a stack master switch and a standby master switch. There is 1:N (multiple switch failover) redundancy per stack. Every switch is eligible for election as master or standby. The Stacking cable provides redundant data paths between stack neighbors. Link redundancy is enabled with Cross-stack EtherChannel between stacks.
