Time limit: 0
Quiz-summary
0 of 50 questions completed
Questions:
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
Information
CCNA Security v2.0 Chapter 1 Test Online
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading...
You must sign in or sign up to start the quiz.
You have to finish following quiz, to start this quiz:
Results
0 of 50 questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 points, (0)
| Average score |
|
| Your score |
|
Categories
- Not categorized 0%
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- Answered
- Review
-
Question 1 of 50
1. Question
1 pointsWhich are two best practices used to secure APIs? (Choose two.)Correct
Incorrect
-
Question 2 of 50
2. Question
1 pointsWhich type of threat actors use cybercrime attacks to promote what they believe in?Correct
Incorrect
-
Question 3 of 50
3. Question
1 pointsA company conducted a penetration test 6 months ago. However, they have acquired new firewalls and servers to strengthen the network and increase capacity. Why would an administrator request a new penetration test?Correct
Incorrect
-
Question 4 of 50
4. Question
1 pointsA network administrator performs a penetration test for a company that sells computer parts through an online storefront. The first step is to discover who owns the domain name that the company is using. Which penetration testing tool can be used to do this?Correct
Incorrect
-
Question 5 of 50
5. Question
1 pointsA penetration tester wants to quickly discover all the live hosts on the 192.168.0.0/24 network. Which command can do the ping sweep using the nmap tool?Correct
Incorrect
-
Question 6 of 50
6. Question
1 pointsA penetration tester runs the command nmap -sF -p 80 192.168.1.1 against a Windows host and receives a response RST packet. What conclusion can be drawn on the status of port 80?Correct
Incorrect
-
Question 7 of 50
7. Question
1 pointsWhich common tool is used by penetration testers to craft packets?Correct
Incorrect
-
Question 8 of 50
8. Question
1 pointsWhy should a tester use query throttling techniques when running an authorized penetration test on a live network?Correct
Incorrect
-
Question 9 of 50
9. Question
1 pointsWhy would an organization hire a red team?Correct
Incorrect
-
Question 10 of 50
10. Question
1 pointsMatch the healthcare sector term to the respective description.Correct
Incorrect
-
Question 11 of 50
11. Question
1 pointsWhich two elements are typically on the front of a credit card? (Choose two.)Correct
Incorrect
-
Question 12 of 50
12. Question
1 pointsWhat can be used to document the testing timeline in a rules of engagement document?Correct
Incorrect
-
Question 13 of 50
13. Question
1 pointsA cybersecurity firm has been hired by an organization to perform penetration tests. The tests require a secure method of transferring data over a network. Which two protocols could be used to accomplish this task? (Choose two.)Correct
Incorrect
-
Question 14 of 50
14. Question
1 pointsMatch penetration testing methodology and standard with the respective description.Correct
Incorrect
-
Question 15 of 50
15. Question
1 pointsWhich three practices are commonly adopted when setting up a penetration testing lab environment? (Choose three.)Correct
Incorrect
-
Question 16 of 50
16. Question
1 pointsAn organization wants to test its vulnerability to an employee with network privileges accessing the network maliciously. Which type of penetration test should be used to test this vulnerability?Correct
Incorrect
-
Question 17 of 50
17. Question
1 pointsRefer to the exhibit. A penetration is being prepared to run the EternalBlue exploit using Metasploit against a target with an IP address of 10.0.0.1/8 from the source PC with an IP address of 10.0.0.111/8. What two commands must be entered before the exploit command can be run? (Choose two.)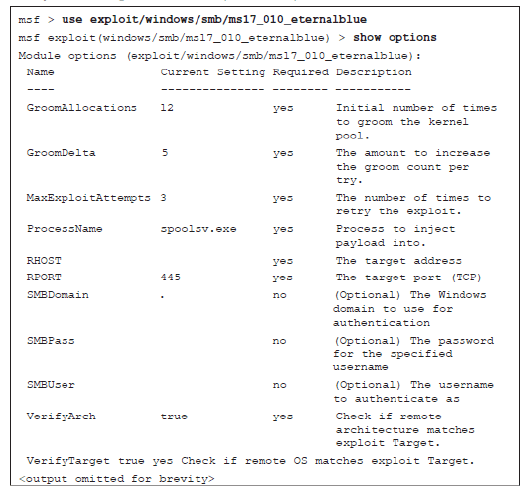 Correct
Correct
Incorrect
-
Question 18 of 50
18. Question
1 pointsA penetration tester runs the Nmap NSE script nmap –script smtp-open-relay.nse 10.0.0.1 command on a Kali Linux PC. What is the purpose of running this script?Correct
Incorrect
-
Question 19 of 50
19. Question
1 pointsRefer to the exhibit. What is the penetration tester trying to achieve by running this exploit?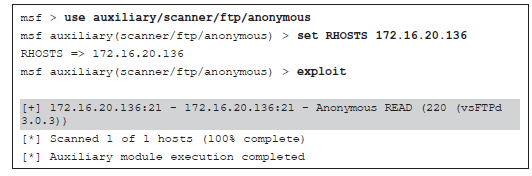 Correct
Correct
Incorrect
-
Question 20 of 50
20. Question
1 pointsA penetration tester deploys a rogue AP in the target wireless infrastructure. What is the first step that has to be taken to force wireless clients to connect to the rogue AP?Correct
Incorrect
-
Question 21 of 50
21. Question
1 pointsA cybersecurity student is learning about the Social-Engineer Toolkit (SET), and the student has discovered that this tool can be used to launch various social engineering attacks. Which two social engineering attacks can be launched using SET?Correct
Incorrect
-
Question 22 of 50
22. Question
1 pointsA threat actor spoofed the phone number of the director of HR and called the IT help desk with a login problem. The threat actor claims to be the director and wants the help desk to change the password. What method of influence is this cybercriminal using?Correct
Incorrect
-
Question 23 of 50
23. Question
1 pointsWhich statement correctly describes a type of physical social engineering attack?Correct
Incorrect
-
Question 24 of 50
24. Question
1 pointsWhat is a characteristic of a pharming attack?Correct
Incorrect
-
Question 25 of 50
25. Question
1 pointsWhat kind of social engineering attack can be prevented by developing policies such as updating anti-malware applications regularly and using secure virtual browsers with little connectivity to the rest of the system and the rest of the network?Correct
Incorrect
-
Question 26 of 50
26. Question
1 pointsAn attacker enters the string ‘John’ or ‘1=1’ on a web form that is connected to a back-end SQL server causing the server to display all records in the database table. Which type of SQL injection attack was used in this scenario?Correct
Incorrect
-
Question 27 of 50
27. Question
1 pointsWhat are two examples of immutable queries that should be used as mitigation for SQL injection vulnerabilities? (Choose two.)Correct
Incorrect
-
Question 28 of 50
28. Question
1 pointsAn attacker enters the string 192.168.78.6;cat /etc/httpd/httpd.conf on a web application hosted on a Linux server. Which type of attack occurred?Correct
Incorrect
-
Question 29 of 50
29. Question
1 pointsWhich two misconfigured cloud authentication methods could leverage a cloud asset? (Choose two.)Correct
Incorrect
-
Question 30 of 50
30. Question
1 pointsMatch the cloud attack to the description.Correct
Incorrect
-
Question 31 of 50
31. Question
1 pointsWhat is the purpose of using the smtp-user-enum -M VRFY -u snp -t 10.0.0.1 command in Kali Linux?Correct
Incorrect
-
Question 32 of 50
32. Question
1 pointsMatch the mobile device security testing tool to the description.Correct
Incorrect
-
Question 33 of 50
33. Question
1 pointsMatch the mobile device attack to the description.Correct
Incorrect
-
Question 34 of 50
34. Question
1 pointsWhich two Bluetooth Low Energy (BLE) statements are true? (Choose two.)Correct
Incorrect
-
Question 35 of 50
35. Question
1 pointsMatch the insecure code practice to the description.Correct
Incorrect
-
Question 36 of 50
36. Question
1 pointsWhich C2 utility can be used to create multiple reverse shells?Correct
Incorrect
-
Question 37 of 50
37. Question
1 pointsRefer to the exhibit. The attacking system has a listener (port open), and the victim initiates a connection back to the attacking system. Which two resources can create this type of malicious activity? (Choose two.) Correct
Correct
Incorrect
-
Question 38 of 50
38. Question
1 pointsMatch the PowerSploit module/script to the respective description.Correct
Incorrect
-
Question 39 of 50
39. Question
1 pointsWhich two tools can create a remote connection with a compromised system? (Choose two.)Correct
Incorrect
-
Question 40 of 50
40. Question
1 pointsWhich two options are PowerSploit modules/scripts? (Choose two.)Correct
Incorrect
Hint
-
Question 41 of 50
41. Question
1 pointsWhy is it important to use Common Vulnerability Scoring System (CVSS) to reference the ratings of vulnerabilities identified when preparing the final penetration testing report?Correct
Incorrect
-
Question 42 of 50
42. Question
1 pointsA company hires a professional to perform penetration testing. The tester has identified and verified that one web application is vulnerable to SQL injection and cross-site scripting attacks. Which technical control measure should the tester recommend to the company?Correct
Incorrect
-
Question 43 of 50
43. Question
1 pointsThe IT security department of a company has developed an access policy for the datacenter. The policy specifies that the datacenter is locked between 5:30 pm through 7:45 am daily except for emergency access approved by the IT manager. What is the operational control implemented?Correct
Incorrect
-
Question 44 of 50
44. Question
1 pointsA security audit for a company recommends that the company implement multifactor authentication for the datacenter access. Which solution would achieve the goal?Correct
Incorrect
-
Question 45 of 50
45. Question
1 pointsWhat are three examples of the items a penetration tester must clean from systems as part of the post-engagement cleanup process? (Choose three.)Correct
Incorrect
-
Question 46 of 50
46. Question
1 pointsRefer to the exhibit. Which Python data structure is used? Correct
Correct
Incorrect
-
Question 47 of 50
47. Question
1 pointsWhich statement describes the concept of Bash shell in operating systems?Correct
Incorrect
-
Question 48 of 50
48. Question
1 pointsWhich three tools can be used to perform passive reconnaissance? (Choose three.)Correct
Incorrect
-
Question 49 of 50
49. Question
1 pointsAn attacker uses John the Ripper to crack a password file. The attacker issued the ~$ john –list=formats command in Kali Linux. Which information is the attacker trying to find?Correct
Incorrect
-
Question 50 of 50
50. Question
1 pointsWhat are two exploitation frameworks? (Choose two.)Correct
Incorrect
