9.2.2.5 Packet Tracer – Configuring Dynamic NAT (Instructor Version)
Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only.
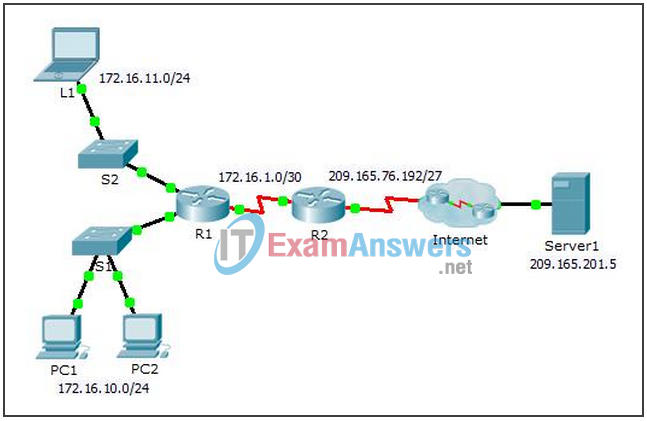
Topology
Objectives
- Part 1: Configure Dynamic NAT
- Part 2: Verify NAT Implementation
Part 1: Configure Dynamic NAT
Step 1: Configure traffic that will be permitted.
On R2, configure one statement for ACL 1 to permit any address belonging to 172.16.0.0/16.
R2(config)# access-list 1 permit 172.16.0.0 0.0.255.255
Step 2: Configure a pool of address for NAT.
Configure R2 with a NAT pool that uses all four addresses in the 209.165.76.196/30 address space.
R2(config)# ip nat pool any-name-here 209.165.76.196 209.165.76.199 netmask 255.255.255.252
Notice in the topology there are 3 network ranges that would be translated based on the ACL created. What will happen if more than 2 devices attempt to access the Internet?
The additional devices would be denied access until one of the previous translations timed out freeing up an address to use.
Step 3: Associate ACL1 with the NAT pool.
R2(config)# ip nat inside source list 1 pool any-name-here
Step 4: Configure the NAT interfaces.
Configure R2 interfaces with the appropriate inside and outside NAT commands.
R2(config)# interface s0/0/0 R2(config-if)# ip nat outside R2(config-if)# interface s0/0/1 R2(config-if)# ip nat inside
Part 2: Verify NAT Implementation
Step 1: Access services across the Internet.
From the web browser of L1, PC1, or PC2, access the web page for Server1.
Step 2: View NAT translations.
View the NAT translations on R2.
R2# show ip nat translations
