Multiple choice questions
1. Which two technologies can combine multiple physical switches into one logical switch? (Choose two.)
- GLBP
- HSRP
- VRRP
- VSS
- StackWise
2. Refer to the exhibit. Which two statements about router R1 are true?
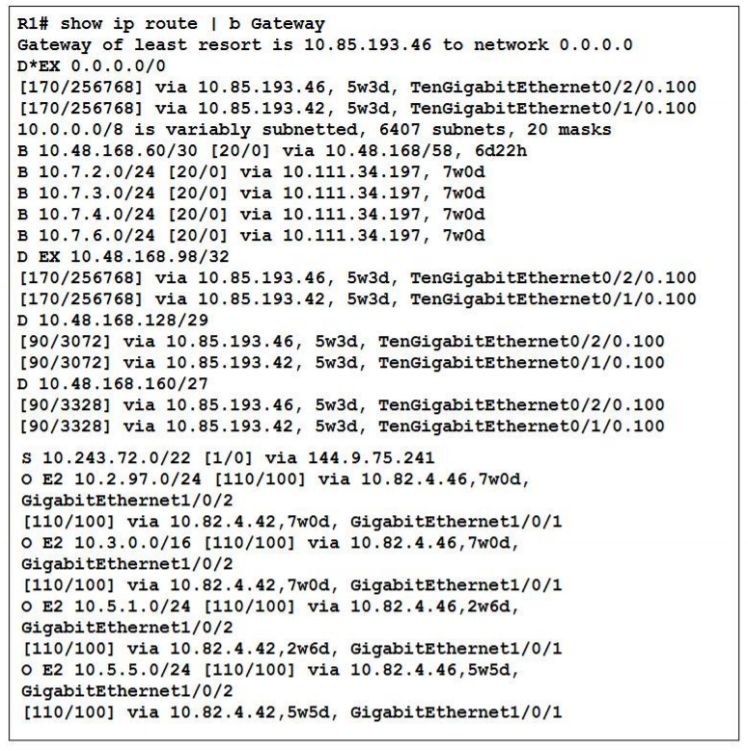
- At least three IGP routing protocols are running on the router
- At least two IGP routing protocols are running on the router
- The router has two EIGRP neighbors and one OSPF neighbor
- The router has an OSPF Area 0 adjacency with the device at 10.82.4.42
- The router is learning external OSPF and EIGRP routes
3. Which plane handles switching traffic through a Cisco router?
- data*
- performance
- control
- management
4. Which command must you enter to enable OSPFV2 in an IPV4 network?
- ip ospf hello-interval seconds
- router ospfv2 process-id
- router ospf value
- router ospf process-id
5. Which command should you enter to configure a single port to bypass the spanning-tree Forward and Delay timers?
- spanning-tree portfast bpdufilter default
- spanning-tree portfast
- spanning-tree portfast default
- spanning-tree portfast bpduguard default
6. Which two options are fields in an Ethernet frame? (Choose two.)
- frame check sequence
- header
- source IP address
- destination IP address
- type
7. Which two tasks can help you gather relevant facts when you troubleshoot a network problem? (Choose two.)
- Collect technical data from network management system and logging servers
- Ask question of the users who are effected by the problem
- Eliminate known issues first
- Define the problem in temrs of symtoms and causes
- Change one setting or component and then analyze the result
8. Which command should you use to display detailed information about EBGP peers?
- show ip bgp paths
- show ip bgp neighbors
- show ip bgp
- show ip bgp summary
9. Which are two common types of copper cable? (Choose two)
- Unshielded twisted pair
- Single-mode
- OM4
- Shieled twisted pair
- Multimode
10. Which port status does the interface enter when UDLD detects a unidirectional link?
- Errdisable
- Down/down
- Up/up
- Shutdown
11. Refer to the exhibit. How will switch SW2 handle traffic from VLAN 10 on SW1?

- It drops the traffic
- It sends the traffic to VLAN 10
- It sends the traffic to VLAN 1
- It sends the traffic to VLAN 100
12. Which VLAN ID is associated with the native VLAN?
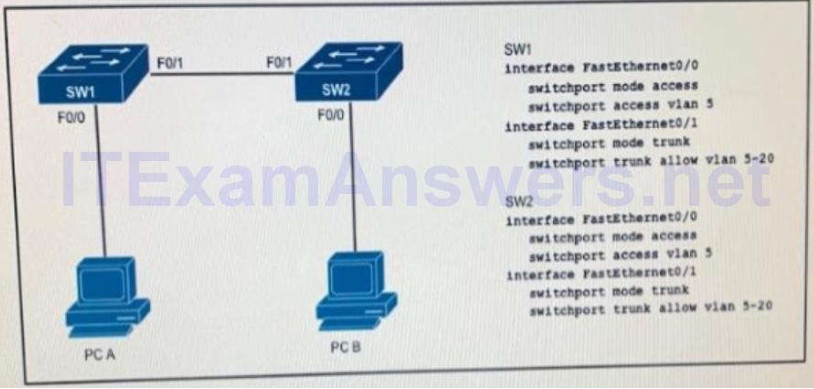
- VLAN 1
- VLAN 5
- VLAN 10
- VLAN 20
13. Which type of frame is larger than 9000 bytes?
- Baby giant
- Runt
- Giant
- Jumbo
14. Which command should you enter to configure an LLDP delay of 5 seconds?
- lldp reinit 5
- lldp reinit 5000
- lldp holdtime 5
- lldp timer 5000
15. Which command must you use to test DNS connectivity?
- Show interfaces
- Show hosts
- Ipconfig
- telnet
16. Which effect does the switchport trunk native vlan 10 command have?
- It configures the interface as a trunk port
- It sets VLAN 10 as the native VLAN on the trunk
- It prevents traffic on VLAN 1 from passing on the trunk
- It allows traffic from native VLAN 10 on the trunk
17. Which two TCP messages use a 32-bit number as part of the initial TCP handshake? (Choose two.)
- ACK
- RST
- SYN
- SYN-ACK
- FIN
18. How does a Cisco IP phone handle untagged traffic that it receives from an attached PC?
- It allows the traffic to pass through unchanged
- It tags the traffic with the native VLAN
- It tags the traffic with the default VLAN
- It drops the traffic
19. Which feature or protocol determines whether the QoS on the network is sufficient to support IP services?
- LLDP
- IP SLA
- CDP
- EEM
20. Which feature or protocol must you enable so that the output of the show interface trunk command include information about native VLAN mismatch?
- CDP
- RSTP
- DTP
- PortFast
21. Which two types of NAT addresses are used in a Cisco NAT device? (Choose two.)
- inside local
- inside global
- inside private
- outside private
- external global
- external local
22. Refer to the exhibit. What is the effect of the configuration?
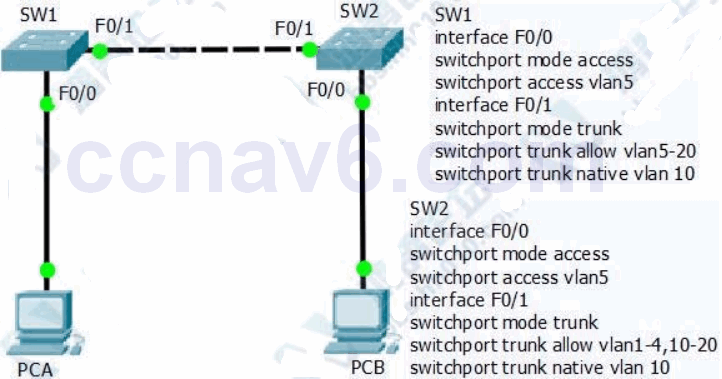
- Traffic from PC A is dropped when it uses the trunk to communicate with PC B
- Traffic from PC A is sent untagged when it uses the trunk to communicate with PC B
- Traffic from PC B is dropped when it uses the trunk to communicate with PC A
- Traffic from PC B is sent untagged when it uses the trunk to communicate with PCA
23. Which task should you perform before you use the APIC-EM Path Trace tool to perform ACL analysis?
- Verify that DNS is configured on the controller
- Execute a standard traceroute to the destination
- Verify that the devices of interest are included in the device inventory
- Configure the IP address from which to generate the trace
24. Which protocols does the internet layer in the TCP/IP model encapsulate? (Choose two.)
- TCP
- ICMP
- DNS
- ARP
- SMTP
25. Which two pins does an RJ-45 connector use to transmit data? (Choose two.)
- 1
- 2
- 3
- 4
- 6
26. Which IOS troubleshooting tool should you use to direct system messages to your screen?
- Log events
- APIC-EM
- Terminal monitor
- Local SPAN
27. Which two VLAN IDs indicate a default VLAN? (Choose two.)
- 0
- 1
- 1005
- 1006
- 4096
28. You notice that packets that are sent from a local host to a well-known service on TCP port 80 of a remote host are sometimes lost. You suspect an ACL issue. Which two APIC-EM Path Trace ACL-analysis options should you use to troubleshoot the problem? (Choose two.)
- Destination port
- Debug
- Performance Protocol
- QoS
- Protocol
29. Refer to the exhibit. When PC1 sends a packet to PC2, the packet has which source and destination IP addresses when it arrives at interface Gi0/0 on router R2?
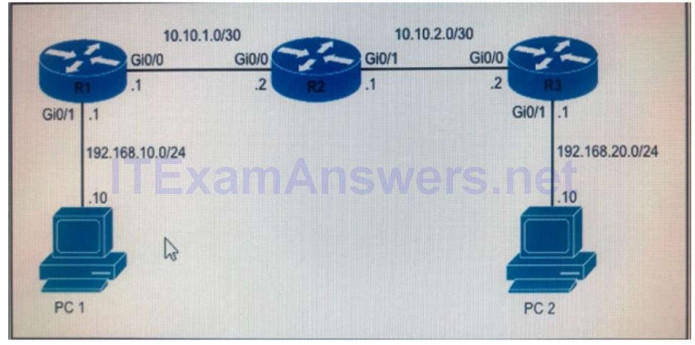
- Source 192.168.20.10 and destination 192.168.20.1
- Source 192.168.10.10 and destination 192.168.20.10
- Source 10.10.1.1 and destination 10.10.2.2
- Source 192.168.10.10 and destination 10.10.10.2
30. According to security best practices, which two actions must you take to protect an unused switch port? (Choose two.)
- Configure the port as an access port on a VLAN other than VLAN 1
- Configure the port as a trunk port
- Enable CDP
- Configure the port to automatically come online
- Administratively shut down the port
31. Which two statements correctly describe distance-vector routing protocols? ( Choose two.)
- they specify the next hop toward the destination subnet
- they require quick network convergence to support normal operations
- they generate a complete topology of the network
- they update other devices on the network when one device detects a topology change
- they use variety of metrics to identify the distance to a destination network
32. In which three ways is an IPv6 header simpler than an IPv4 header? (Choose three)
- Unlike IPv4 headers, IPv6 headers have a fixed length.
- IPv6 uses an extension header instead of the IPv4 Fragmentation field.
- IPv6 headers eliminate the IPv4 Checksum field.
- IPv6 headers use the Fragment Offset field in place of the IPv4 Fragmentation field.
- IPv6 headers use a smaller Option field size than IPv4 headers.
- IPv6 headers use a 4-bit TTL field, and IPv4 headers use an 8-bit TTL field.
33. Which two statements about exterior routing protocols are true? (Choose two.)
- BGP is the current standard exterior routing protocol
- Most modern networking supports both EGP and BGP for external routing
- Most modern networking supports both EGP and EIGRP for external routing
- They determine the optimal path between autonomous systems
- They determine the optimal path within an autonomous system
34. Which two actions must you take to correctly configure PPPoE on a client? (Choose two.)
- Create a BBA group and link it to the dialer interface
- Define a dialer interface
- Define a virtual template interface
- Create a dialer pool and bind it to the physical interface
- Create a dialer pool and bind it to the virtual template
35. Which two statements about MPLS are true? (Choose two)
- It provides automatic authentication
- It can carry multiple protocols, including IPv4 and IPv6
- It encapsulates all traffic in an IPv4 header
- It uses labels to separate and foward customer traffic
- It tags customer traffic using 802.1q
36. Frame flooding can occur in which circumstance?
- The destination IP address is missing from the route table
- The source IP address is missing from the route table
- The destination MAC address is missing from the CAM table
- The source MAC address is missing from the CAM table
37. Which three circumstances can cause a GRE tunnel to be in an up/down state? (Choose three.)
- The tunnel interface IP address is misconfigured.
- The tunnel interface is down.
- A valid route to the destination address is missing from the routing table.
- The tunnel address is routed through the tunnel itself.
- The ISP is blocking the traffic.
- An ACL is blocking the outbound traffic.
38. Which command should you enter to view the error log in an EIGRP for Ipv6 enviroment?
- Show ipv6 eigrp neighbors
- Show ipv6 eigrp traffic
- Show ipv6 eigrp topology
- Show ipv6 eigrp events
39. Which add prefix does OSPFv3 use when multiple IPv6 address are configured on a single interface?
- all prefix on the interface
- the prefix that the administrator configure for OSPFv3 use
- the lowest prefix on the interface
- the highest prefix on the interface
40. Which function does traffic shaping perform?
- It buffers and queues excess packets
- It buffers traffic without queuing it
- It queues traffic without buffering it
- It drops packets to control the output rate
41. Which two statements about RFC 1918 addresses are true? (Choose two.)
- They require Network Address Translation or Port Address Translation to access the Internet.
- They have reserved address space for Class A and Class B networks only.
- They must be registered.
- They provide security to end users when the users access the Internet.
- They increase network performance.
42. Which command can you use to test whether a switch supports secure connections and strong authentication?
- Router#ssh –v 1 –l admin 10.1.1.1
- Switch>ssh –v 1 –l admin 10.1.1.1
- Switch#ssh –l admin 10.1.1.1
- Router>ssh –v 2 –l admin10.1.1.1
43. Which feature or protocol is required for an IP SLA to measure UDP jitter?
- CDP
- LLDP
- EEM
- NTP
44. Refer to the exhibit. If all routers on this network run RIPv2, Which configurations should you apply to router R3 to produce this routing table?
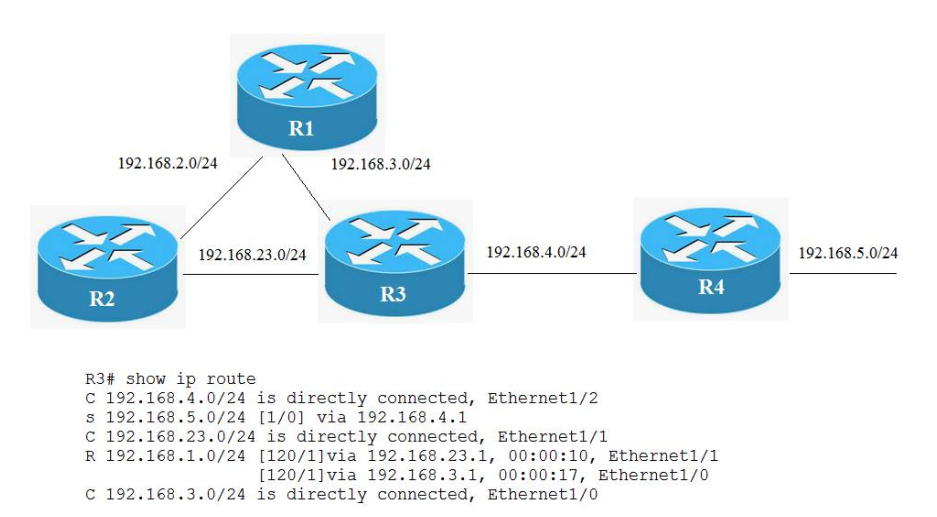
- router rip
network 192.168.3.0
network 192.168.4.0
network 192.168.23.0
passive-interface default - router rip
version 2
network 192.168.3.0
network 192.168.4.0
network 192.168.23.0
distance 50 - router rip
version 2
network 192.168.3.0
network 192.168.4.0
network 192.168.23.0
distance 70
passive-interface default - router rip
version 2
network 192.168.3.0
network 192.168.23.0
distance 50
45. Refer to the exhibit. The network administrator must establish a route by which London workstations can forward traffic to the Manchester workstations. What is the simplest way to accomplish this?
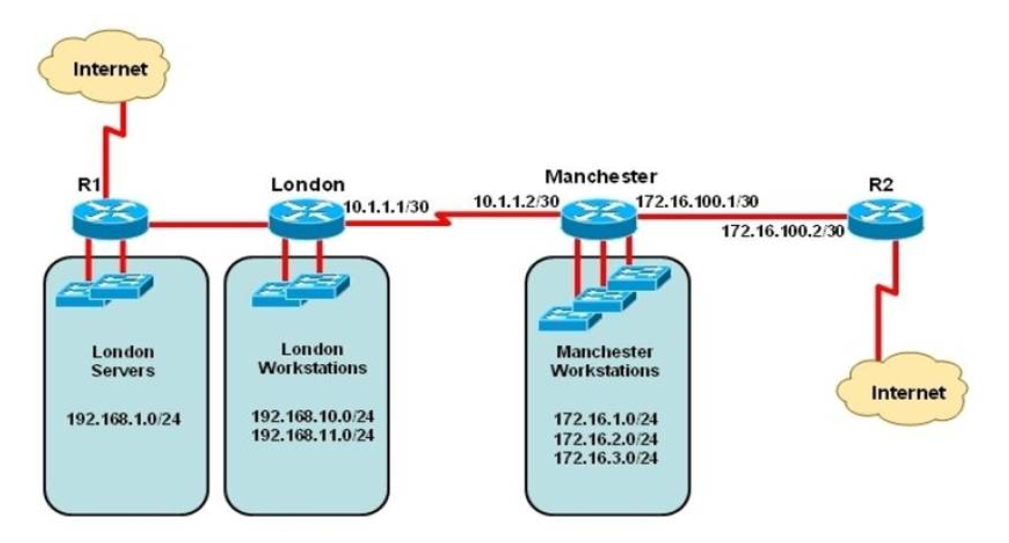
- Configure a dynamic routing protocol on London to advertise all routes to Manchester.
- Configure a dynamic routing protocol on London to advertise summarized routes to Manchester.
- Configure a dynamic routing protocol on Manchester to advertise a default route to the London router.
- Configure a static default route on London with a next hop of 10.1.1.1.
- Configure a static route on London to direct all traffic destined for 172.16.0.0/22 to 10.1.1.2.
- Configure Manchester to advertise a static default route to London.
46. Which two statements about static routing are true? (Choose two.)
- It provides only limited security unless the administrator performs additional configuration
- It allows packets to transit a different path if the topology changes
- Its initial implementation is more complex than OSPF
- Its default administrative distance is lower than EIGRP
- It allows the administrator to determine the entire path of a packet
47. Which three options are types of Layer 2 network attack? (Choose three)
- Spoofing attacks
- Vlan Hopping
- botnet attacks
- DDOS attacks
- ARP Attacks
- Brute force attacks
48. A BPDU guard is configured on an interface that has PortFast enabled. Which state does the interface enter when it receives a BPDU?
- Blocking
- Shutdown
- Listening
- Errdisable
49. Which three encapsulation layers in the OSI model are combined into the TCP/IP application layer? (Choose three)
- Session
- transport
- presentation
- application
- data-link
- network
50. Refer to the exhibit. If the router attempts to send a frame out of the interface, but the carrier is busy, which counter will increment?
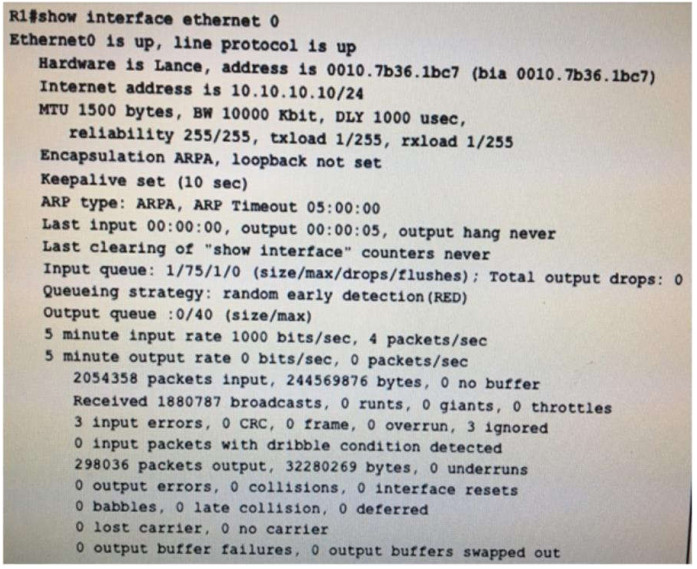
- Collisions
- Late collision
- Deferred
- Lost carrier
51. Which two statements about NTP operation are true? (Choose two.)
- Cisco routers can act only as NTP clients
- Cisco routers can act as both NTP authoritative servers and NTP clients
- NTP uses UDP over IP
- NTP uses TCP over IP
- Cisco routers can act only as NTP server
52. Which two pieces of information can you learn by viewing the routing table? (Choose two.)
- whether a route was tagged
- the interface on which traffic is sent
- whether access lists are blocking incoming routes
- whether routes were summarized
- whether a route was learned via IGP or EGP
53. Which port security violation mode drops traffic from unknown MAC addresses and sends an SNMP trap?
- Protect
- Resrict
- Shutdown
- Shutdown VLAN
54. Which two options are primary responsibilities of the APlC-EM controller? (Choose two.)
- lt automates network actions between different device types.
- lt provides robust asset management.
- lt tracks license usage and Cisco lOS versions.
- lt automates network actions between legacy equipment.
- lt makes network functions programmable.
55. Which component of an Ethernet frame is used to notify a host that traffic is coming?
- Type
- Preamable
- Start of frame delimiter
- Data field
56. Which address class includes network 191.168.0.1/27?
- Class C
- Class B
- Class D
- Class A
57. What is the default Syslog facility level?
- local4
- local5
- local6
- local7
58. What is the easiest way to verify the Layer 3 path from a router to host 192.168.2.1?
- Execute a traceroute form the router to host 192.168.2.1
- Add a static route for host 192.168.2.1 to the routing table of the router
- Use Telnet to connect the router to host 192.168.2.1
- Execute a ping form the router to host 192.168.2.1
59. Which Layer 2 protocol encapsulation type supports synchronous and asynchronous circuis and has built-in security mechanisms?
- HDLC
- PPP
- X.25
- Frame Relay
60. Which command must you enter to guarantee that an HSRP router with higher priority becomes the HSRP primary router after it is reloaded?
- standby 10 priority 150
- standby 10 preempt
- standby 10 version 2
- standby 10 version 1
61. Which command can you enter to display duplicate IP addresses that the DHCP server assigns?
- show ip dhcp conflict 10.0.2.12
- show ip dhcp database 10.0.2.12
- show ip dhcp server statistics
- show ip dhcp binding 10.0.2.12
62. Which two server types are used to support DNS lookup? (Choose two.)
- web server
- ESX host
- authoritative name server
- file transfer server
- name resolver
63. Which two statements about TACACS+ are true? (Choose two.)
- lt can run on a UNlX server.
- lt authenticates against the user database on the local device.
- lt is more secure than AAA authentication.
- lt is enabled on Cisco routers by default.
- lt uses a managed database.
64. Which cloud service that usually provides software beyond the basic operating system is normally used for development?
- Platform-as-a-service
- Database-as-a-service
- Infrastructure-as-a-service
- Software-as-a-service
65. Which two statements describe key differences between single- and dual-homed WAN connections? (Choose two)
- Dual-homed WAN connections are more expensive than single-homed connections
- Dual-homed WAN connections have more management-application overhead than single-homed connections
- Dual-homed WAN connections require more skill to administer than single-homed connections
- Dual-homed WAN connections have a simpler topology than single-homed connections
- Dual-homed WAN connections have higher WAN speed than single- homed connections
66. Which two pieces of information about a Cisco device can Cisco Discovery Protocol communicate? (Choose two.)
- The spanning-tree priority
- The spanning-tree protocol
- The native VLAN
- The VTP domain
- The trunking protocol
67. Which keyboard shortcut can you use to exit the System Configuration Dialog on a Cisco networking device and return to privileged EXEC mode without making changes?
- Shift – Esc
- Ctrl-V
- Ctrl-C
- Ctrl-Alt-Delete
68. After you configure a DHCP server on VLAN 10 to service clients on VLAN 10 and VLAN 20, clients on VLAN 10 are given IP address assignments, but clients on VLAN 20 fail to receive IP addresses. Which action must you take to correct the problem?
- Configure the default gateway in the DHCP server configuration.
- Configure a separate DHCP server on VLAN 20.
- Configure the DNS name option in the DHCP server configuration.
- Configure the ip helper-address command in the DHCP server configuration.
69. Which two benefits can you get by stacking Cisco switches?(choose two)
- Each switch in the stack handles the MAC table independently from the others
- You can add or remove switches without taking the stack down.
- Each switch in the stack can use a different IOS image
- The stack enables any active member to take over as the master switch if the existing master fails.
- You can license the entire stack with a single master license
70. Refer to the exhibit. Which two statements about the network enviroment of router R1 must be true? (Choose two)
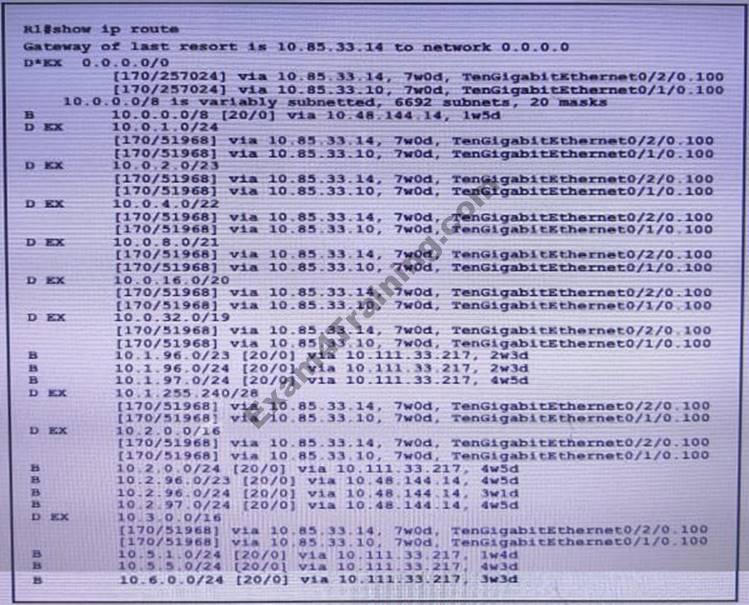
- A static default route to 10.85.33.14 was defined
- There are 20 different network masks within the 10.0.0.0/8 network
- Ten routes are equally load-balanced between Te0/1/0.100 and Te0/2/0.100
- The 10.0.0.0/8 network was learned via external EIGRP
- The EIGRP administrative distance was manually changed from 90 to 170
71. Which NAT function can map multiple inside addresses to a single outside address?
- PAT
- SFTP
- RARP
- ARP
- TFTP
72.
interface Loopback0 ip address 172.16.1.33 255.255.255.224 router bgp 999 neighbor 10.1.5.2 remote-as 65001
Refer to the exhibit . Which Command do you enter so that R1 advertises the loopback0 interface to the BGP Peers?
- Network 172.16.1.32 mask 255.255.255.224
- Network 172.16.1.0 0.0.0.255
- Network 172.16.1.32 255.255.255.224
- Network 172.16.1.33 mask 255.255.255.224
- Network 172.16.1.32 mask 0.0.0.31
- Network 172.16.1.32 0.0.0.31
73. Refer to the exhibit. Which statement about the interface that generated the output is true?
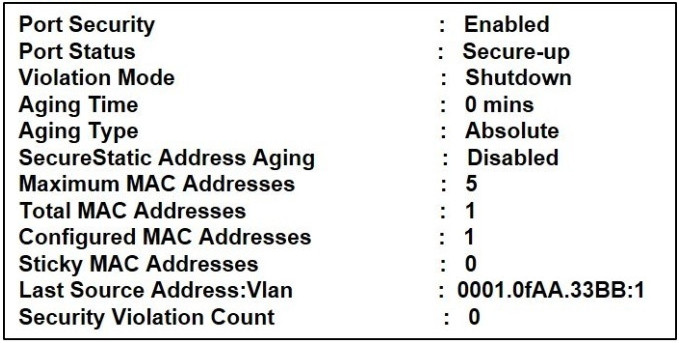
- one secure MAC address is dynamically learned on the intertace.
- a syslog message is generated when a violation occurs
- five secure MAC addresses are dynamically learned on the interface.
- one secure MAC address is manually configured on the interface.
74. Which two conditions can be used to elect the spanning-tree root bridge?(choose two)
- the highest MAC address
- the lowest MAC address
- the highest port priority
- the lowest system ID
- the lowest switch priority
75. Which definition of default route is true?
- A route that is manually configured.
- A route used when a destination route is missing.
- A route to the exact /32 destination address
- Dynamic route learned from the server.
76. Which type of device should you use to preserve IP addresses on your network?
- firewall
- WLAN controller
- load balancer
- intrusion prevention device
77. Refer to the exhibit. Users in your office complaining that they cannot connect to the servers at a remote site. When troubleshooting, you find that you can successfully reach the servers from router R2. What is the most likely reason that the other users are experiencing connection failure?
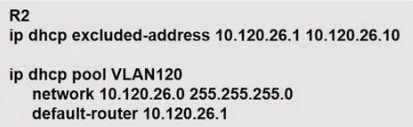
- Interface ports are shut down on the remote servers
- The DHCP address pool has been exhausted
- VLSM is missconfigured between the router interface and the DHCP Pool
- The ip helper-address command is missing on the R2 interface that connects to the switch
78. Which network appliance checks the state of a packet to determine whether the packet is legitimate?
- The LAN controller
- The firewall
- The Layer 2 switch
- The load balancer
79. You apply a new inbound access list to routers, blocking UDP packets to the HSRP group. Which two effectsdoes this action have on the HSRP group process? (Choose two.)
- HSRP redundancy works as expected
- Both the active and standby routers become active
- The active router immediately becomes the standby router.
- HSRP redundancy fails.
- The routers in the group generate duplicate IP address warnings
80. Which feature can cause a port to shut down immediately after a switch reboot?
- COPP
- PortFast
- DTP
- port security
81. What happens to new traffic that is sent to a destination MAC address after the MAC aging time expires?
- It is dropped
- It is flooded
- It is queued
- It is process-switched
82. Which two command sequences must you configure on a switch to establish a Layer 3 EtherChannel with an open-standard protocol? (choose two)
- interface GigabitEthernet0/0/1
channel-group 10 mode on - interface port-channel 10
switchport
switchport mode trunk - interface port-channel 10
no switchport
ip address 172.16.0.1 255.255.255.0 - interface GigabitEthernet0/0/1
channel-group 10 mode auto - interface GigabitEthernet0/0/1
channel-group 10 mode active
83. Which two statements about IPv4 multicast traffic are true? (Choose two.)
- It burdens the source host without affecting remote hosts.
- It uses a minimum amount of network bandwidth.
- It is bandwidth-intensive.
- It simultaneously delivers multiple streams of data.
- It is the most efficient way to deliver data to multiple receivers.
84. Which command can you enter on a switch to display the IP addresses associated with connected devices?
- Show cdp neighbors detail
- Show cdp neighbor
- Show cdp interface
- Show cdp traffic
85. Which two tasks should you perform to begin troubleshooting a network problem? (Choose two.)
- Analyze the results
- Implement an action plan
- Define the problem as a set of symptoms and causes
- Gather all the facts
- Monitor and verify the resolution
86. Which IPv6 address is the all-router multicast group?
- FF02::1
- FF02::2
- FF02::3
- FF02::4
87. Which three statements about HSRP operation are true? (Choose three.)?
- The virtual IP address and virtual MAC+K44C address are active on the HSRP Master router.
- The HSRP default timers are a 3 second hello interval and a 10 second dead interval.
- HSRP supports only clear-text authentication
- The HSRP virtual IP address must be on a different subnet than the routers’ interfaces on the same LAN.
- The HSRP virtual IP address must be the same as one of the router’s interface addresses on the LAN.
- HSRP supports up to 255 groups per interface, enabling an administrative form of load balancing.
88. Which protocol does ipv6 use to discover other ipv6 nodes on the same segment?
- CLNS
- TCPv6
- NHRP
- NDP
- ARP
89. Which value is used to build the CAM table?
- destination IP address
- source IP address
- destination MAC address
- source MAC address
90. How does a router handle an incoming packet whose destination network is missing from the routing table?
- it broadcast the packet to each interface on the router
- it discards the packet
- it broadcasts the packet to each network on the router
- it routes the packet to the default route
91. Refer to the exhibit. The server on this network is configured with an MTU of 9216, and the two interfaces on router R1 and configured for MTUs of 2000 and 3000, as shown. What is the largest packet size that can pass between the workstation and the server?
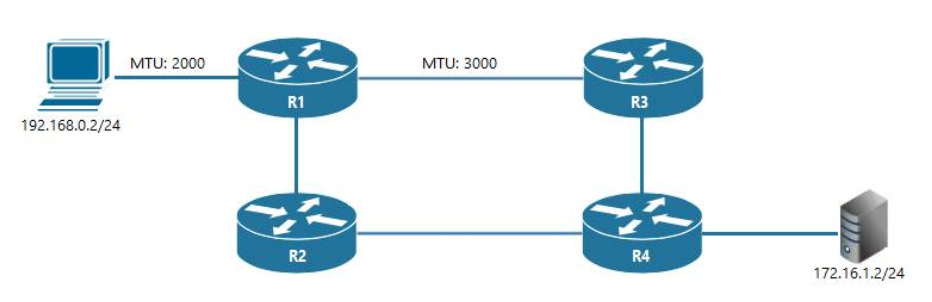
- 1500 bytes
- 2000 bytes
- 3000 bytes
- 9216 bytes
92. A national retail chain needs to design an IP addressing scheme to support a nationwide network. The company needs a minimum of 300 sub-networks and a maximum of 50 host addresses per subnet. Working with only one Class B address, which of the following subnet masks will support an appropriate addressing scheme? (Choose two.)
- 255.255.255.0
- 255.255.255.128
- 255.255.252.0
- 255.255.255.224
- 255.255.255.192
- 255.255.248.0
93. Which two statements correctly describe the ping utility? (Choose two.)
- It uses UDP
- It can identify the source of an ICMP “time exceeded” message
- It uses ICMP
- It can identify the path that a packet takes to a remote device
- It can verify connectivity to a remote device without identifying the path
94. Refer to the exhibit. The following commands are executed on interface fa0/1 of 2950Switch.
2950Switch(config-if)#switchport port-security mac-address sticky 2950Switch(config-if)#switchport port-security maximum 1
The Ethernet frame that is shown arrives on interface fa0/1. What two functions will occur when this frame is received by 2950Switch? (Choose two.)
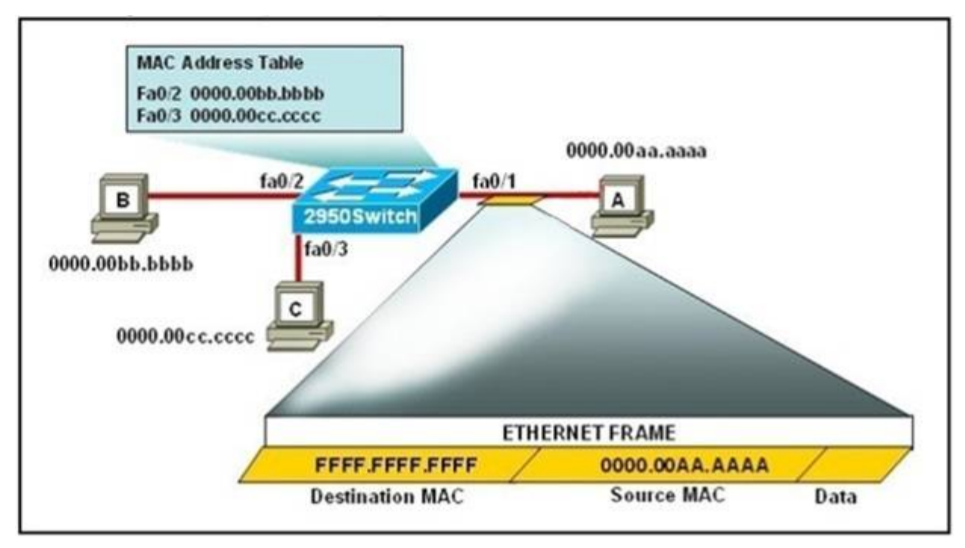
- The MAC address table will now have an additional entry of fa0/1 FFFF.FFFF.FFFF.
- Only host A will be allowed to transmit frames on fa0/1.
- This frame will be discarded when it is received by 2950Switch.
- All frames arriving on 2950Switch with a destination of 0000.00aa.aaaa will be forwarded out fa0/1.
- Hosts B and C may forward frames out fa0/1 but frames arriving from other switches will not be forwarded out fa0/1.
- Only frames from source 0000.00bb.bbbb, the first learned MAC address of 2950Switch, will be forwarded out fa0/1.
95. Which two statements about stateful firewalls in an enterprise network are true?
- They can use information about previous packets to make decisions about future packets.
- They are most effective when placed in front of the router connected to the Internet.
- they are more susceptible to DoS attacks than stateless firewalls.
- they can track the number of active TCP connections.
- They can filter HTTP and HTTPS traffic in the inbound direction only.
96. Which three statements about IPv6 address fd14:920b:f83d:4079::/64 are true? (Choose three)
- The subnet ID is 14920bf83d
- The subnet ID is 4079
- The global ID is 14920bf83d
- The address is a link-local address
- The global ID is 4079
- The address is a unique local address
97. Which two pieces of information can you determine from the output of the show ntp status command? (Choose two.)
- whether the clock is synchronized
- the IP address of the peer to Which the clock is synchronized
- the NTP version number of the peer
- whether the NTP peer is statically configured
- the configured NTP servers
98. Which QOS feature can drop traffic that exceeds the committed access rate?
- weighted fair queuing
- FIFO
- policing
- shaping
99. Which two address spaces are valid Class B IPv4 ranges that are non-routable to the Internet? (Choose two.)
- 10.0.0.0 through 10.0.255.255
- 169.254.0.0 through 169.254.255.255
- 172.16.0.0 through 172.31.255.255
- 172.16.0.0 through 172.32.255.255
- 192.168.0.0 through 192.168.255.255
100. Which two statements about the ip default-network command are true? (Choose two.)
- It specifies the network that is used when the device finds an exact match in the routing table.
- It requires IP routing to be disabled on the device.
- It specifies the network that is used when the device cannot find an exact match in the routing table.
- It requires IP routing to be enabled on the device.
- It can be configured on a Layer 2 switch to specify the next hop.
101. Which command can you enter to determine whether serial interface 0/2/0 has been configured using HDLC encapsulation?
- router#show platform
- router#show interfaces Serial 0/2/0
- router#show ip interface s0/2/0
- router#show ip interface brief
102. Refer to the exhibit. Which two pieces of information can you determine from the EIGRP topology table?(Choose two.)
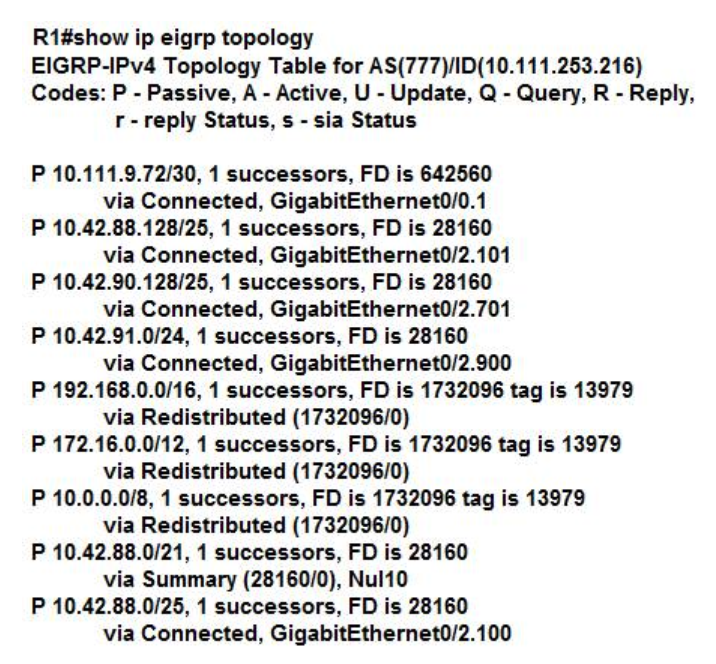
- The EIGRP neighbor IP address is 10.111.253.216.
- Route 10.42.91.0/24 has a tag of 28160.
- The reported distance of 10.0.0.0/8 is 0.
- Route 10.42.88.0/21 has an administrative distance of 28160.
- Each route has only one best path.
103. Which value must you configure on a device before EIGRP for IPV6 can start running?
- process ID
- router ID
- loopback interface
- public IP address
104. Which two statements about link-state routing protocols are true? (Choose two.)
- Link-state routing protocols use split horizon to avoid routing loops.
- Each router determines its own path to a destination.
- Each router maintains its own unique routing database.
- Each router shares a database of known routes.
- Each router is aware only of its neighbor routers.
105. Refer to the exhibit.
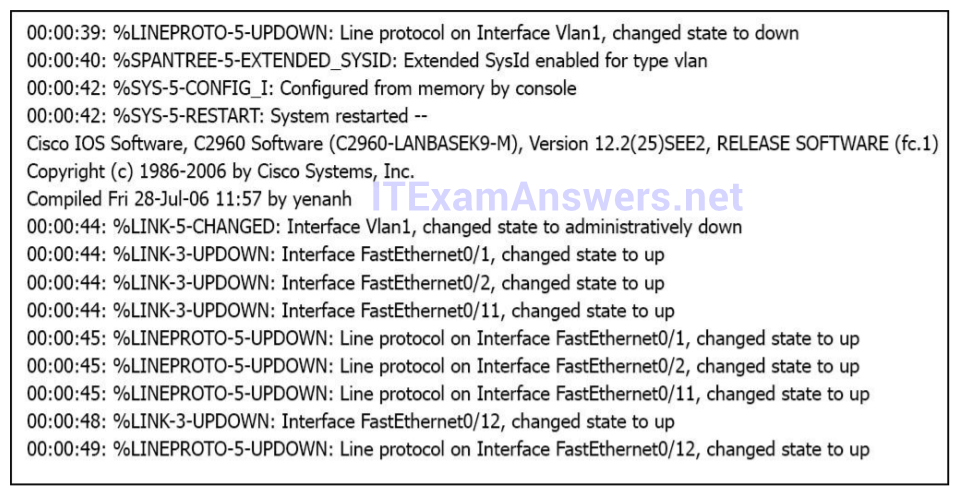
Which of these statements correctly describes the state of the switch once the boot process has been completed?
- The switch will need a different IOS code in order to support VLANs and ST.
- Remote access management of this switch will not be possible without configuration change.
- As FastEthernet0/12 will be the last to come up, it will be blocked by STP.
- More VLANs will need to be created for this switch.
106. Which effete does the aaa new-model coniguration commandhave?
- It enables AAA services on the device
- It configures the device to connect to a RADIUS server for AAA
- It associates a RADIUS server to an AAA group.
- It configures a local user on the device.
107. What SNMP message alerts the manager to a condition on the network?
- trap
- get
- response
- capture
108. Which three are valid modes for a switch port used as a VLAN trunk? (choose three)
- Desirable
- Auto
- On
- Blocking
- Transparent
- Forwarding
109. Which two statements about DNS lookup operations are true? (Choose two)
- They use destination port 53
- When the primary IP address of the destination is down, the DNS server can forward the client to an alternative IP address
- The client sends a request for IP address to domain name resolution to the DNS server
- The client sends a request for domain name to IP address resolution to the DNS server
- The DNS server pings the destination to verify that is available
110. Which configuration register value can you set on a Cisco device so that it ignores the NVRAM when it boots?
- 0x2124
- 0x2120
- 0x2142
- 0x2102
111. Which IP address can send traffic to all hosts on network 10.101.0.0/16?
- 10.101.0.1
- 10.101.254.254
- 10.101.255.255
- 224.0.0.1
112. Which command can you enter to configure a local username with an encrypted password and EXEC mode user privileges?
- Router(config)#username jdone privilege 1 password 7 08314D5D1A48
- Router(config)#username jdone privilege 1 password 7 PASSWORD1
- Router(config)#username jdone privilege 15 password 0 08314D5D1A48
- Router(config)#username jdone privilege 15 password 0 PASSWORD1
113. Which command would you configure globally on a Cisco router that would allow you to view directly connected Cisco devices?
- enable cdp
- cdp enable
- cdp run
- run cdp
114. Which WAN topology is most appropriate for a centrally located server farm with several satellite branches?
- star
- hub and spoke
- point-to-point
- full mesh
115. Which task must you perform to enable an IOS device to use DNS services?
- configure a relay agent information reforwarding policy
- configure manual bindings
- configure the relay agent information option
- configure a name server
116. Which command allows you to set the administrative distance for EIGRP for IPv6?
- ipv6 next-hop-self eigrp
- ipv6 bandwidth-percent eigrp
- metric weights
- ipv6 summary-address eigrp
117. On Which combinations are standard access lists based?
- destination address and wildcard mask
- destination address and subnet mask
- source address and subnet mask
- source address and wildcard mask
118. Which command must you enter to configure a DHCP relay?
- ip dhcp relay
- ip address dhcp
- ip helper-address
- ip dhcp pool
119. What are two reasons to use multicast to deliver video traffic, instead of unicast or broadcast? (Choose two.)
- It provides reliable TCP transport
- It enables multiple clients to send video streams simultaneously
- It enables multiple clients to receive the video stream simultaneously
- It enables multiple servers to send video streams simultaneously
- It supports distributed applications
120. Which two criteria must be met to support the ICMP echo IP SLA? (Choose two)
- The destination device must support the echo protocol
- default gateway must be configured for the source and destination devices
- The source device must be running Layer 2 services.
- The source and destination devices must be Cisco devices
- The source device must be a Cisco device but the destination device can be from any vendor
121. In a CDP enviroment, what happens when the CDP interface on an adjacent device is configured without an IP address?
- CDP operates normally, but it cannot provide IP address information for that neighbor
- CDP uses the IP address of another interface for that neighbor
- CDP operates normally, but it cannot provide any information for that neighbor
- CDP becomes inoperable on that neighbor
122. Which benefit of implementing a dual-homed WAN connection instead of a single-homed connection is true?
- Only dual-homed connections support recursive routing
- Only dual-homed connections enable an individual router to tolerate the loss of a network link
- Only dual-homed connections support split horizon with EIGRP
- Only dual-homed connections support OSPF in conjunction with BGP
123. Which three elements are field in a basic Ethernet data frame? (Choose three.)
- Preamble
- Frame Check Sequence
- Header Checksum
- Length/Type
- Time to Live
- Version
124. Which option is the primary purpose of traffic shaping?
- providing best-effort service
- enabling policy-based routing
- enabling dynamic flow identification
- limiting bandwidth usage
125. Which three statements about Syslog utilization are true? (Choose three.)
- Utilizing Syslog improves network performance
- The Syslog server automatically notifies the network administrator of network problems
- A Syslog server provides the storage space necessary to store log files without using router disk space
- There are more Syslog messages available within Cisco IOS than there are comparable SNMP trap messages.
- Enabling Syslog on a router automatically enables NTP for accurate time stamping
- A Syslog server helps in aggregation of logs and alerts.
126. In which two formats can the IPv6 address fd15:0db8:0000:0000:0700:0003:400F:572B be written? (Choose two.)
- fd15:0db8:0000:0000:700:3:400F:527B
- fd15:0db8::7:3:4F:527B
- fd15::db8::700:3:400F:527B
- fd15:db8::700:3:400F:572B
- fd15:db8:0::700:3:4F:527B
127. Which API uses HTTP messages to transfer data to applications residing on different hosts?
- OpenStack
- REST
- OpenFlow
- OpFlex
128. Which Rapid PVST+ port role provides a different path to the root bridge?
- backup
- forwarding
- alternate
- designated
129. It you change the weight and distance parameters on a device with an establshed BGP neighbor, Which additional task must you perfom to allow the two devices to continue exchanging routes?
- Reset the BGP connections on the device
- Reset the gateway interface
- Clear the IP routes on the device
- Change the weight and distance settings on the other device to match
130. Which address block identifies all link-local addresses?
- FC00::/7
- FC00::/8
- FE80::/10
- FF00::/8
132. Which chassis-aggregation technology combines two physical switches into one virtual switch?
- VSS
- LACP
- VRRP
- StackWise
133. Which functionality does split horizon provide?
- It prevents switching loops in distance-vector protocols.
- It prevents switching loops in link-state protocols.
- It prevents routing loops in distance-vector protocols.
- It prevents routing loops in link-state protocols.
134. Which command can you execute to set the user inactivity timer to 10 seconds?
- SW1(config-line)#exec-timeout 0 10
- SW1(config-line)#exec-timeout 10
- SW1(config-line)#absolute-timeout 0 10
- SW1(config-line)#absolute-timeout 10
135. Which two statements about stacking Cisco switches are true ?(choose two)
- It enables the administrator to manage multiple switches from a single management interface
- The administrator can create only one stack of switches in a network which is under the same administrative domian
- When a new master switch is elected,it queries the previous master for its running configuration
- The administrator can add additional switches to the stack as demand increases
- Each switch manages its own MAC address table
136. Which command can you enter on a Cisco IOS device to enable a scheduled algorithm that directs lookup calls to multiple DNS hosts?
- ip name-server 192.168.10.14 192.168.10.15
- ip domain list
- ip domain lookup
- ip domain round-robin
137. Which two benefits are provided by cloud resources to an enterprise network? (Choose two.)
- complexity at higher cost
- on-demand scalability
- flexibility
- easy access with low security
- full control of infrastructure
138. Which IEEE mechanism is responsible for the authentication of devices when they attempt to connect to a local network?
- 802.1x
- 802.11
- 802.2x
- 802.3x
139. Which command should you enter to configure a device as an NTP server?
- ntp peer
- ntp server
- ntp master
- ntp authenticate
140. Which switching method checks for CRC errors?
- Layer 3
- Store-and-forward
- fragment-free
- cut-through
141. Which type of address is the public IP address of a NAT device?
- outside public
- inside local
- inside global
- inside public
- outside global
- outside local
142. Refer to the exhibit. What is the effect of the given configuration?
Switch#configuration terminal Switch#interface VLAN 1 Switch(config-if)#ip address 192.168.2.2 255.255.255.0 Switch(config-if)#end
- It configures an inactive switch virtual interface.
- It configures an active management interface.
- It configures the native VLAN.
- It configures the default VLAN.
143. Based on the output below from SwitchB, which statement is true?
- The MAC address of the root bridge is 0017.596d.1580.
- The Fa0/11 role confirms that SwitchB is the root bridge for VLAN 40.
- SwitchB is not the root bridge, because not all of the interface roles are designated.
- VLAN 40 is running the Per VLAN Spanning Tree Protocol.
144. Refer to the exhibit
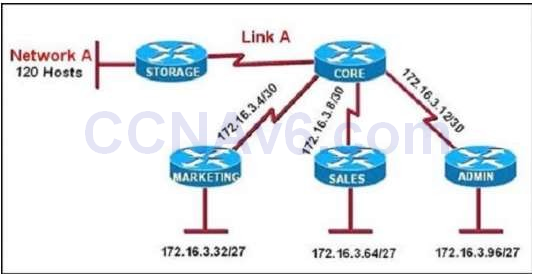
All of the routers in the network are configured with the ip subnet-zero command. Which network addresses should be used for Link A and Network A? (Choose two.)
- Link A 172.16.3.0/30
- Link A 172.16.3.112/30
- Network A 172.16.3.48/26
- Network A 172.16.3.128/25
- Link A 172.16.3.40/30
- Network A 172.16.3.192/26
145. Which three ports will be STP designated ports if all the links are operating at the same bandwidth? (Choose three.)
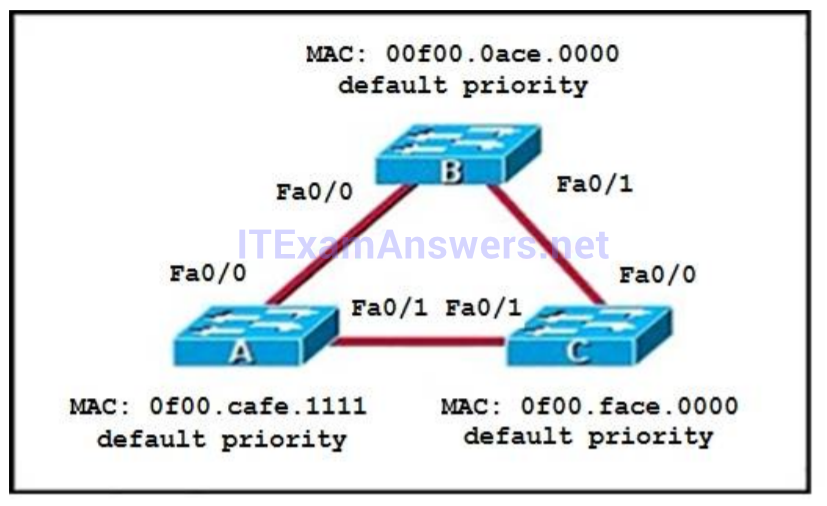
- Switch B – F0/0
- Switch A – Fa0/1
- Switch B – Fa0/1
- Switch C – F0/1
- Switch A – Fa0/0
- Switch C – Fa0/0
146. Which symbol in the APIC-EM Path Trace tool output indicates that an ACL is present and might deny packets?
Correct Answer: C
147. When you are troubleshooting an ACL issue on a router, Which command would you use to verify Which interfaces are affected by the ACL?
- show ip access-lists
- show access-lists
- show interface
- show ip interface
- list ip interface
148. Which two tasks does a router perform when it receives a packet that is being forwarded from one network to another? (Choose two.)
- It removes the Layer 2 frame header and trailer
- It encapsulates the Layer 2 packet
- It removes the Layer 3 frame header and trailer
- It examines the routing table for the best path to the destination IP address of the packet
- It examines the MAC address table for the forwarding interface
149. Which circumstances is a common cause of late collisions?
- overload hardware queues
- native VLAN mismatch
- duplex mismatch
- software misconfiguration
150. Which PPP subprotocol negotiates authentication options?
- NCP
- LCP
- ISDN
- DLCI
- SLIP
151. What are two requirements for an HSRP group? (Choose two.)
- exactly one active router
- one or more standby routers
- one or more backup virtual routers
- exactly one standby active router
- exactly one backup virtual router
152. Which three statements about IPv6 prefixes are true? (Choose three.)
- FEC0::/10 is used for IPv6 broadcast.
- FC00::/7 is used in private networks.
- FE80::/8 is used for link-local unicast.
- FE80::/10 is used for link-local unicast.
- 2001::1/127 is used for loopback addresses.
- FF00::/8 is used for IPv6 multicast.
153. Which technology in a service provider environment can use labels to tunnel custormer data?
- Metro Ethernet
- DMVPN
- MPLS
- PPPOE
154. Which two statements about IGP and EGP routing protocols are true? (Choose two.)
- Service providers use OSPF and IS-IS for intra-AS routing
- EGP routing protocols are used to connect multiple IGP networks
- IGP routing protocols are used within internal networks
- OSPF, EIGRP, and BGP are categorized as IGP routing protocols.
- Service providers use EGP and BGP for intra-AS routing
155. Which command should you enter to configure a single port to disabled infenior BPDU?
- spanning-tree portfast bpduguard
- spanning-tree guard root
- spanning-tree portfast default
- spanning-tree portfast bpdufilter
156. Which configuration register setting do you use to bypass the password that is stored in the startup configuration?
- 0xFFFF
- 1×2102
- 0x2102
- 0x2142
157. Which LLDP extension provides additional support for VoIP?
- TLV
- LLDP-MED
- LLDP-VOIP
- LLDPv3
158. Which command is needed to send RIPv2 updates as broadcast when configured for RIPv2?
- ip rip v2-broadcast
- ip rip receive version 1
- ip rip receive version 2
- version 2
159. Which two statements about private addresses are true? (Choose two.)
- By default, Class C private networks support up to 255 subnets.
- Network 192.168.25.0/28 supports 14 usable private host addresses.
- The 172.16.X.X/16 private Class B network supports over 1 millon addresses.
- Addresses in the range 172.16.0.1 to 172.32.255.254 are defined as Class B private addresses.
- Network 10.1.1.0/29 supports 16 usable private host addresses.
160. Which option is the benefit of implementing an intelligent DNS for a cloud computing solution?
- It reduces the need for a backup data center.
- It can redirect user requests to locations that are using fewer network resources.
- It enables the ISP to maintain DNS records automatically.
- It eliminates the need for a GSS.
161. Which two characteristics of an ICMP echo-based IP SLA are true? (Choose two)
- It can use RSPAN to report network statistics to a designated remote port
- It aggregates traffic statistics for reporting on a configurable basis
- It requires a remote device to log and maintain collected data
- It measures traffic to determine the reliability of a connection from a Cisco router to a designated end device
- It generates continuous traffic to monitor network performance
162. Which two values must you specify to define a static route? (Choose two.)
- destination network and mask
- incoming interface
- administrative distance of the route
- source network and mask
- next-hop address or exit interface
163. To enable router on a stick on a router subinterface, which two steps must you perform? (Choose two.)
- Configure an IP route to the VLAN destination network.
- Configure encapsulation dot1q.
- Configure a default to route traffic between subinterfaces.
- Configure full duplex and speed.
- Configure the subinterface with an IP address.
164. When a switch is running in VTP server mode, VLAN configuration information is stored in which file?
- vlan.dat
- startup-config
- vlan.config
- config.text
165. Which two commands can you use to configure an LACP EtherChannel? (Choose two.)
- channel-group 10 mode auto
- channel-group 10 mode active
- channel-group 10 mode on
- channel-group 10 mode desirable
- channel-group 10 mode passive
166. What is the first step in the NAT configuration process?
- Define inside and outside interfaces
- Define public and private IP addresses
- Define IP address pools
- Define global and local interfaces
167. You are configuring a 100-Mb fast Ethernet connection between a PC and Switch. Which action must you take to configure the speed one each of the two interfaces?
- Set the switch port to auto-negotiate and the PC interface to 100 Mb
- Set both interfaces to auto-negotiate.
- Set the switch port to 100 Mb and the PC interface to auto-negotiate.
- Set both interfaces to 100 Mb
168. Which feature is automatically enabled on voice VLAN port?
- 802.1x
- 802.1Q
- PortFast
- Port Security
169. Which three commands can you use to set a router boot image? (Choose three.)
- Router(config)# boot system flash c4500-p-mz.121-20.bin
- Router(config)# boot system tftp c7300-js-mz.122-33.SB8a.bin
- Router(config)#boot system rom c7301-advipservicesk9-mz.124-24.T4.bin
- Router> boot flash:c180x-adventerprisek9-mz-124-6T.bin
- Router(config)#boot flash:c180x-adventerprisek9-mz-124-6T.bin
- Router(config)#boot bootldr bootflash:c4500-jk9s-mz.122-23f.bin
170. Which MAC protocol sets a random timer to reattempt communication?
- RARP
- CSMA/CA
- CSMA/CD
- IEEE 802.1x
171. Where does a switch maintain DHCP snooping information?
- in the MAC address table
- in the CAM table
- in the DHCP binding database
- in the VLAN database
172. A network administrator enters the following command on a router:logging trap 3 . What are three message types that will be sent to the Syslog server?(choose three)
- warning
- informational
- error
- emergency
- debug
- critical
173. Which two statements about RIPv2 are true? (Choose two.)
- It does not support clear text authentication, similar to RIPv1
- It supports CIDR and VLSM
- It stores RIP neighbor adjacency information in a neighbor table
- It uses the Bellman-Ford routing algorithm
- It sends periodic updates via broadcast
174. Which two differences between distance-vector and link-state routing protocols are true? (Choose two.)
- Only link-state routing use the Bellman-Ford algorithm
- Only distance-vector routing protocols send full routing table updates
- Distance-vector routing protocols are less susceptible to loops than link-state protocols
- Link-state routing protocols offer faster convergence than distance-vector protocols during network changes
- Only distance-vector routing protocols maintain identical topology tables on all connected neighbors
175. Which option is the main function of congestion management?
- discarding excess traffic
- queuing traffic based on priority
- classifying traffic
- providing long-term storage of buffered data
176. Which two functions describe benefits of aggregated chassis technology? ( choose two)?
- it reduces management overhead.
- switches can be located anywhere regardless of there physical location.
- it requires only 1 IP add per VLAN.
- it requires only 3 IP add per VLAN.
- it supports HSRP VRRP GLBP.
- it support redundant configuration files.
177. Which three statements describe the reasons large OSPF networks use a hierarchical design? (Choose three.)
- to confine network instability to single areas of the network.
- to reduce the complexity of router configuration
- to speed up convergence
- to lower costs by replacing routers with distribution layer switches
- to decrease latency by increasing bandwidth
- to reduce routing overhead
178. When troubleshooting client DNS issues, which two tasks must you perform? (Choose two.)
- Ping a public website IP address.
- Ping the DNS server.
- Determine whether the hardware address is correct.
- Determine whether a DHCP address has been assigned.
- Determine whether the name servers have been configured.
179. Which commands can you can enter to verify that a router is synced with a configured time source?
- Show ntp associations
- Show clock details
- Show clock
- Show time
- Show ntp status
180. Which three statements about the features of SNMPv2 and SNMPv3 are true? (Choose three.)
- SNMPv3 enhanced SNMPv2 security features
- SNMPv3 added the Inform protocol message to SNMP.
- SNMPv2 added the Inform protocol message to SNMP
- SNMPv3 added the GetBulk protocol messages to SNMP
- SNMPv2 added the GetBulk protocol message to SNMP.
- SNMPv2 added the GetNext protocol message to SNMP.
181. Which two cable specifications can support 1-Gbps Ethernet? (choose two)
- Category 5e
- RG11
- RG-6
- Category 6
- Category 3
182. Which Cisco Catalyst feature automatically disables the port in an operational PortFast upon receipt of a BPDU?
- BackboneFast
- UplinkFast
- Root Guard
- BPDU Guard
- BPDU Filter
183. Which two statements about EUI-64 addressing are true? (Choose two.)
- The address includes the hex digits FFFE after the last 24 bits of the interface MAC address.
- The address includes the hex digits FFFE after the first 24 bits of the interface MAC address
- A 64-bit interface identifier is derived from the interface MAC address.
- A locally administrated address has the universal/local bit set to 0.
- A 96-bit interface identifier is derived from the interface MAC address.
- The address includes the hex digits FFFE after the first 14 bits of the interface MAC address.
184. Which two pieces of information about a Cisco device can Cisco Discovery Protocol communicate? (Choose two.)
- The spanning-tree priority
- The spanning-tree protocol
- The native VLAN
- The VTP domain
- The trunking protocol
185. Which two statements about UTP cables are true? (Choose two.)
- Category 6a Ethernet cable can transmit up to 10 Gbps
- Category 6 Ethernet cables are appropriate for installations of up to 200m
- Category 5 Ethernet cables support speeds up to 1000 Mbps beyond 100m
- All Ethernet cable types from Category 1 through Category 6 are suitable for transmitting data in the appropriate environments
- Category 5e Ethernet cables support speeds up 1000 Mbps
186. Cisco IOS supports Which QoS models?
- best-effort and integrated services
- integrated services and differentiated services
- best-effort and differentiated services
- best-effort, integrated services, and differentiated services
187. Which command disable DTP?
- Switchport mode passive
- Switchport mode active
- Switchport nonegotiate
- Switchport negotiate
188. Which enterprise device provides centralized control of authentication and roaming?
- A lightweight access point
- A firewall
- A Lan Switch
- A wireless LAN controller
189. How many bits can be used to identify unique hosts in the address range for network 10.0.0.0/8
- 8
- 16
- 24
- 32
190. Which command must be present in a Cisco Device configuration to enable the device to resolve an FQDN?
- Ip host
- Ip name-server
- Ip domain-lookup
- Ip domain-name
191. Which command must you enter to configure a DHCP relay?
- ip dhcp relay
- ip address dhcp
- ip helper-address
- ip dhcp pool
192. You are implementing WAN access for an enterprise network while running applications that require a fully meshed network, Which two design standards are appropriate for such an environment? (Choose two.)
- a dedicated WAN distribution layer, to consolidate connectivity to remote sites
- a centralized DMVPN solution, to simplify connectivity for the enterprise
- multiple MPLS VPN connections with static routing
- a collapsed core and distribution layer, to minimize costs
- multiple MPLS VPN connections with dynamic routing
193. Which two commands can you enter to configure an interface to actively negotiate an EtherChannel? (Choose two.)
- channel-group 10 mode auto
- channel-group 10 mode active
- channel-group 10 mode on
- channel-group 10 mode desirable
- channel-group 10 mode passive
194. When troubleshooting a user complaint, you notice that two routers failed to establish an OSPF neighbor adjacency. Which two issues are root causes for the problem? (Choose two.)
- The two routers are configured with the same area ID
- The two router are using the same router ID
- The passive-interface command is configured on the connected interfaces
- The two routers are configured with different process Ids
- OSPF is configured on the primary network of the neighbor, but not on the secondary network
195. Which two statements about how a router makes forwarding decisions are true? (Choose two.)
- The control plane forwards traffic based on information that it receives from the data plane
- The data plane gathers information from routing protocols
- The management plane forwards traffic based on information that it receives from the data plane
- The control plane gathers information from routing protocols
- The data plane forwards traffic through the router
- The management plane gathers information from routing protocols
196. Which action do you take to reset the VTP configuration revision number on a switch in VTP server made?
- Change the VTP domain name to any new value, and then change the name back to the original name
- Change the VTP mode to transparent, and then change it back to server mode
- Change the VTP mode to off, and then change it back to server mode.
- Change the VTP mode to transparent, and then change it to cent mode.
197. Which two statements about southbound APIS are true? (Choose two.)
- OpenFlow is a southbound API standard.
- They communicate with the management plane.
- They use HTTP messages to communicate.
- They enable communication between the controller and the network device.
- They enable communication between the controller and SDN applications.
198. When you configure and boot a new device, when does the running configuration become active?
- Immediately after the power-on self-test
- When IOS is loaded into RAM.
- When the devices boots to ROMMON.
- When the startup configuration is copied into RAM.
199. Which command should you enter on an interface in a vendor-neutral EtherChannel so that it will be selected first to transmit packets?
- lacp system-priority 1024
- pagp system-priority 1024
- pagp port-priority 1024
- lacp port-priority 1024
200. After you deploy a new WLAN controller on your network, Which two additional tasks should you consider? (Choose two.)
- Configure multiple VRRP groups.
- Configure additional VLANs.
- Configure additional security policies.
- Deploy load balancers.
- Deplay POE switches.
201. Which two commands can you use to configure a PAgP EtherChannel? (Choose two.)
- channel-group 10 mode auto
- channel-group 10 mode active
- channel-group 10 mode desirable
- channel-group 10 mode on
- channel-group 10 mode passive
202. Which command should you enter to configure a single port to enter an err-disabled state when it receives an infenior BPDU?
- spanning-tree portfast bpduguard
- spanning-tree guard root
- spanning-tree portfast default
- spanning-tree portfast bpdufilter
203. Which two statements about single and dual-homed links are true? ( choose two.)
- Single-homed connections to a service provider require OSPF or EIGRP.
- Dual-homed connections to multiple service providers can use OSPF or EIGRP for load balancing.
- Single-homed connections to a service provider can use either static routing or BGP
- Dual-homed connection to multiple service providers typically use BGP.
- Dual-homed connections to a service provider most frequently use static routing.
204. After you configure the ip dns spoofing command globally on a device, under which two conditions is DNS spoofing enabled on the device? (Choose two.)
- The DNS server queue limit id disabled
- The ip host command is disabled
- All configured IP name server addresses are removed
- The ip dns spoofing command is disabled on the local interface
- The no ip domain lookup command is configured
205. Which command should you enter to verify the priority of a router in an HSRP group?
- show standby
- show interfaces
- show sessions
- show hsrp
206. Which feature or method can you use to isolate physical layer problems on a serial link?
- autonegotiation
- protocol analyzer
- loopback tests
- UDLD
207. Which algorithm is used for the frame check sequence in an Ethernet frame?
- MD5
- AES-256
- CRC
- SHA-1
208. Which two features can you enable on a switch to capture network traffic and measure performance?(choose two)
- ACL
- SPAN
- IP SLA
- STP
- SNMP
209. Which layer of the TCP/IP model manages the transmission of binary digits across an Ethernet cable?
- network
- data link
- transport
- physical
210. Which statement about recovering a password on a Cisco router is true?
- The default reset password is cisco
- It requires a secure SSl/VPN connection
- A factory resset is required if you forget the password
- It requires physical access to the router
211. What are two advantages of static routing? (Choose two.)
- It can be implemented easily even in large environments
- It allows the administrator to control the path of traffic
- It produces minimal CPU load
- It allows the network to respond immediately to changes
- It cannot be used to load-balance traffic over multiple links
212. Which two steps must you perform on each device that is configured for IPv4 routing before you implement OSPFv3?(Choose two)
- configure an autonomous system number
- configure a loopback interface
- configure a router ID
- Enable IPv6 on an interface
- Enable IPv6 unicast routing
213. What is the effect of PortFast on the MAC aging process?
- It prevents fast aging of MAC addresses when IEEE 802.1D is in use
- It prevents fast aging of MAC addresses when RSTP is in use
- It ignores the MAC aging timer when RSTP is in use
- It ignores the MAC aging timer when IEEE 802.1D is in use
214. Which two TLVs does LLDP support ? (Choose two.)
- system description
- port duplex
- management address
- native VLAN
- spanning tree
215. Which two circumstances can prevent two routers from establishing an EIGRP neighbor adjacency? (Choose two.)
- An ACL is blocking traffic from multicast address 224.0.05
- Both routers have the same router ID
- The routers are on different subnets
- The two routers have the same autonomous system number
- The routers have mismatched K values
216. Which two features can dynamically assign IPv6 addresses? (Choose two.)
- IPv6 stateless autoconfiguration
- DHCP
- NHRP
- IPv6 stateful autoconfiguration
- ISATAP tunneling
217. Which type of routing protocol operates by using first information from each device peers?
- link-state protocols
- distance-vector protocols
- path-vector protocols
- exterior gateway protocols
218. According to industry best practices, which length is the recommended maximum for a Category 6 cable in a 10GBASE-T environment?
- 37 meters
- 300 meters
- 100 meters
- 55 meters
219. Which two statements about floating static routes are true? (Choose two)
- They are routes to the exact /32 destination address
- They are used when a route to the destination network is missing
- They have a higher administrative distance than the default static route administrative distance
- They are used as back-up routes when the primary route goes down
- They are dynamic routes that are learned from a server
220. Which two IP SLA operations can you use to measure the end-to-end response time for all IP traffic between a Cisco router and an end device ?(choose two)
- ICMP path echo
- UDP echo
- ICMP path jitter
- UDP jitter
- TCP connect
- ICMP echo
221. Which type of port supports voice VLAN configuration?
- Access switch port
- Trunk switch port
- Private VLAN switch port
- Layer 3 Switch port
222. Which two advantages do dynamic routing protocols provide over static routing? (Choose two.)
- Dynamic routing requires fewer resources than static routing
- Only dynamic routing is supported on all topologies that require multiple routers
- Dynamic routing protocols are easier to manage on very large networks
- Dynamic routing protocols automatically adapt to reroute traffic if possible
- Dynamic routing is more secure than static routing
223. Which two statements about northbound and southbound APIs are true? (Choose two.)
- Only southbound APIs allow program control of the network.
- Only northbound APIs allow program control of the network.
- Only southbound API interfaces use a Service Abstraction Layer.
- Only northbound API interfaces use a Service Abstraction Layer.
- Both northbound and southbound API interfaces use a Service Abstraction Layer.
- Both northbound and southbound APIs allow program control of the network.
224. Which step in the router boot process searches for an IOS image to load into the router?
- bootstrap
- POST
- mini-IOS
- ROMMON mode
225. What is the danger of the permit any entry in a NAT access list?
- It can lead to overloaded resources on the router.
- It can cause too many addresses to be assigned to the same interface.
- It can disable the overload command.
- It prevents the correct translation of IP addresses on the inside network.
226. Which command can you enter on a switch to determine the current SNMP security model?
- show snmp group
- show snmp pending
- snmp-server contact
- show snmp engineID
227. Which value is included in the initial TCP SYN message?
- a session ID
- a TTL number
- an acknowledgment number
- a sequence number
228. Which circumstances is a common cause of late collisions?
- overload hardware queues
- native VLAN mismatch
- duplex mismatch
- software misconfiguration
229. Which two approaches are common when troubleshooting network issues? (Choose two.)
- top-down
- policing
- layer-by-layer
- round-robin
- divide and conquer
230. Which two descriptions of TACACS+ are true? (Choose two.)
- It encrypts only the password.
- It can authorize specific router commands.
- It separates authentication, authorization, and accounting functions.
- It uses UDP as its transport protocol.
- It combines authentication and authorization.
231. What is a valid HSRP virtual MAC address?
- 007.3313.9734
- 0000.0C07.AC15
- 0007.B400.AE01
- 0000.5E00.01A3
232. Which two statements about Ethernet standards are true?(choose two)
- Ethernet is defined by IEEE standard 802.2
- Ethernet is defined by IEEE standard 802.3
- Ethernet 10BASE-T dose not support full-duplex.
- When an Ethernet network uses CSMA/CD ,it terminates transmission as soon as collision occurs
- When an Ethernet network uses CSMA/CA ,it terminates transmission as soon as collision occurs
233. Which two options are features of the extended ping command? (Choose two.)
- It can send a specific number of packets
- It can send packet from specified interface of IP address
- It can resolve the destination host name
- It can ping multiple host at the same time
- It can count the number of hops to the remote host.
234. Which frame type allows STP to compute the spanning-tree topology?
- LSP
- LSA
- RSTP
- BPDU
235. Which utility can you use to identify redundant or shadow rules?
- The ACL trace tool in Cisco APIC-EM.
- The ACL analysis tool in Cisco APIC-EM.
- The Cisco APIC-EM automation scheduler.
- The Cisco IWAN application.
236. Which two statements about IPv6 multicast addresses are true? (Choose two.)
- They use the prefix FC80::/8
- If the lifetime parameter is set to 1, the route is permanent
- They identify a group of interfaces on different devices
- They use the prefix FF00::/8
- If the scope parameter is set to 5, the route is local to the node
237. What is the simplest IP SLA operation that can measure end-to-end response time between devices?
- ICMP path jitter
- ICMP path echo
- ICMP echo
- ICMP jitter
238. Which tunneling mechanism embeds an IPv4 address within an IPv6 address?
- Teredo
- 6to4
- 4to6
- GRE
- ISATAP
239. Which command should you enter to configure a single port to prevent alternate ports from becoming designated ports?
- spanning-tree guard root
- spanning-tree guard loop
- spanning-tree loopguard default
- spanning-tree etherchannel misconfig
240. What is the most efficient subnet mask for a point to point ipv6 connection?
- /127
- /128
- /64
- /48
- /32
241. Which two goals are reasons to implement private IPv4 addressing on your network? (Choose two.)
- Conserve IPv4 address
- Reduce the size of the forwarding table on network routers
- Reduce the risk of a network security breach
- Comply with PCI regulations
- Comply with local law
242. Which circumstance matches the description of an excessive collision?
- The same frame is sent sixteen times.
- The deferred counter value is greater than 1024.
- Bit 512 of the frame is sent.
- An interface receives fifteen or more alignment errors.
243. Which two statements about GRE tunnels are true? (Choose two.)
- They provide privacy, integrity, and authenticity.
- They can operate in tunnel mode and transport mode.
- They add 8 bytes to the IP header of each packet.
- They allow multicast traffic to traverse WAN circuits.
- They encapsulate the payload
244. When you deploy multilink PPP on your network, where must you configure the group IP Address on each device?
- In the global config
- Under serial interface
- Under the routing protocol
- Under the multilink interface
245. Which two commands should you enter to view the PID and serial number of a router? (Choose two.)
- show license udi
- show license feature
- show license
- show license status
- show version
246. Which file-system management command is used frequently when IOS backups, upgrades, and restores are performed?
- delete
- copy
- show file
- show dir
247. Which specification supports full-duplex traffic only?
- 100BASE-TX
- 1000BASE-SX
- 1000BASE-TX
- 10BASE-T
248. Which two statements about PDU encapsulation are true? (Choose two.)
- During encapsulation, each layer adds a header and trailer to the PDU from the layer below
- During encapsulation, each layer adds a header and sometimes adds a trailer to the PDU from the layer above
- In the TCP/IP reference model, PDU encapsulation occurs on the network layer
- PDU encapsulation takes place only at the transport layer
- In the TCP/IP reference model, PDU encapsulation starts on the Internet layer with the data from the application layer
249. Which statement about switch ports is true?
- The default VLAN and native VLAN must be different on al ports
- VLAN 1 is preconfigured as the native VLAN on trunk ports only.
- VLAN 1 is preconfigured as the default VLAN on all switch ports.
- VLAN 100 is preconfigured as the native VLAN on al switch ports
250. Which protocol enables a Cisco IP phone to provide QoS instructions to a switch?
- VTP
- CDP
- 802.1Q
- DTP
251. Which two statements about MPLS are true? (Choose two.)
- It uses point-to-point physical circuits to provide logical full-mesh connections to the service provider.
- It requires a hub in a large data center with a fast connection to the service provider.
- All connections are full mesh with full redundancy.
- It provides easily scalable bandwidth to support newer connectivity options for numerous remote sites.
- Because it is a mature technology, it requires less skill to administer.
252. Which two statements about the routing table are true? (Choose two.)
- It displays information about the successor and the feasible successor.
- It displays the administrative distance and metric of the routes that it learns
- It displays the metric and the reported distance of the routes that it learns.
- It uses letters such as O, I,and D to identify how a route is learned.
- It uses the > symbol to indicate the best route.
253. Which chassis-aggregation technology combines two physical switches into one virtual switch?
- VSS
- LACP
- VRRP
- StackWise
254. Which chassis-aggregation technology binds two individual Cisco switches at control and data planes to act as one logical switch?
- LACP
- vPC
- VRRP
- VSS
255. Which function can be centralized in software-defined networking?
- data plane
- application plane
- control plane
- services plane
256. How many bits in length is a VLAN identifier?
- 32
- 48
- 16
- 64
257. Which two features can mitigate spanning tree issues that are caused by broken fiber cables on interswitch links? (Choose two)
- UDLD
- root guard
- loop guard
- BPDU guard
- DTP
258. Which command must you use to verify hostname-to-IP-address mapping information?
- Show sessions
- Show arp
- Show mac-address-table
- Show hosts
259. Which two are advantages of static routing when compared to dynamic routing? (Choose two.)
- Configuration complexity decreases as network size increases.
- Security increases because only the network administrator may change the routing table.
- Route summarization is computed automatically by the router.
- Routing tables adapt automatically to topology changes.
- An efficient algorithm is used to build routing tables, using automatic updates.
- Routing updates are automatically sent to neighbors.
- Routing traffic load is reduced when used in stub network links.
260. Which two statements about the ip subnet-zero command are true? (Choose two.)
- It specifies the broadcast IP addresses in the subnet.
- It enables the network to make full use of the available IP address space.
- It is enabled by default on Cisco routers.
- It must be configured each time you reboot a router.
- It must be configured before you activate NAT on a router.
261. Refer to the exhibit. Which BGP configuration do you need to apply to router R4 to allow traffic to flow normally on this network?

- Router bgp 1
No synchronization
Neighbor 192.168.1.1 remote-as 1
Neighbor 192.168.1.1 ebgp-multihop 4
Neighbor 192.168.2.1 remote-as 1
Neighbor 192.168.2.1 ebgp-multihop 4
Neighbor 192.168.3.1 remote-as 5
No auto-summary - Router bgp 1
No synchronization
Neighbor 192.168.1.1 remote-as 1
Neighbor 192.168.2.1 remote-as 1
Neighbor 192.168.3.1 remote-as 5
No auto-summary - Router bgp1
No synchronization
Neighbor 192.168.1.1 remote-as 1
Neighbor 192.168.2.1 remote-as 1
Neighbor 192.168.2.1 ebgp-multihop 4
Neighbor 192.168.3.1 remote-as 5
No auto-summary - Router bgp1
No synchronization
Neighbor 192.168.1.1 remote-as 1
Neighbor 192.168.1.1 ebgp-multihop 4
Neighbor 192.168.2.1 remote-as 1
Neighbor 192.168.2.1 ebgp-multihop 4
Neighbor 192.168.3.1 remote-as 5
Neighbor 192.168.3.1 ebgp-multihop 4
No auto-summary
262. Refer to the diagram. All hosts have connectivity with one another. Which statements describe the addressing scheme that is in use in the network? (Choose three.) 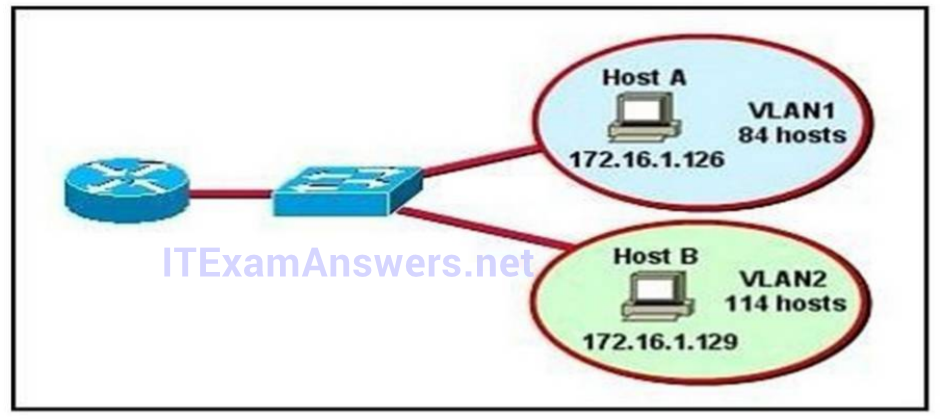
- The subnet mask in use is 255.255.255.192
- The subnet mask in use is 255.255.255.128
- The IP address 172.16.1.25 can be assigned to hosts in VLAN 1
- The IP address 172.16.1.205 can be assigned to hosts in VLAN1
- The LAN interface of the router is configured with one IP address.
- The LAN interface of the router is configured with multiple IP addresses.
263. Refer to the exhibit. Which port security violation mode is configured on interface FA0/1? 
- protect
- shutdown VLAN
- shutdown
- restrict
264. Refer to the exhibit. HostA cannot ping HostB. Assuming routing is properly configured, what is the cause of this problem? 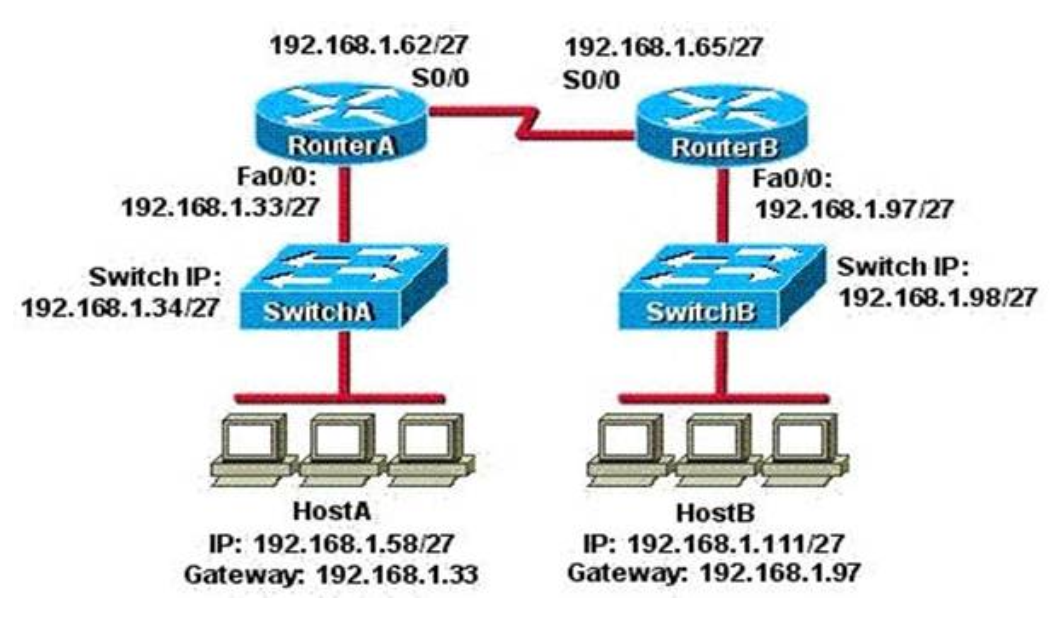
- HostA is not on the same subnet as its default gateway.
- The address of SwitchA is a subnet address.
- The Fa0/0 interface on RouterA is on a subnet that can’t be used.
- The serial interfaces of the routers are not on the same subnet.
- The Fa0/0 interface on RouterB is using a broadcast address.
265. Refer to the exhibit. Host 1 is trying to communicate with Host 2. The e0 interface on Router C is down. Which of the following are true? (Choose two.)
- Router C will use ICMP to inform Host 1 that Host 2 cannot be reached.
- Router C will use ICMP to inform Router B that Host 2 cannot be reached.
- Router C will use ICMP to inform Host 1, Router A, and Router B that Host 2 cannot be reached.
- Router C will send a Destination Unreachable message type.
- Router C will send a Router Selection message type.
- Router C will send a Source Quench message type.
266. When you troubleshoot an IPv4 connectivity issue on a router, which three router configuration checks you
must perform?
- Verify that the router interface IP address is correct.
- Verify that the DNS is configured correctly.
- Verify that the router and the host use the same subnet mask.
- Verify that the router firmware is up-to-date.
- Verify that a default route is configured.
- Verify that the route appears in the Routing table
267. Which 2 optns are requirements for configuring ripv2 for ipv4 (choose 2 )?
- enabling RIP authentication.
- connecting RIP to a WAN Interface.
- enabling auto route sumamrization.
- allowing unicast updates for RIP.
- enabling RIP on the router.
268. Based on the output below, which two statements are true of the interfaces on Switch1? (Choose two.) 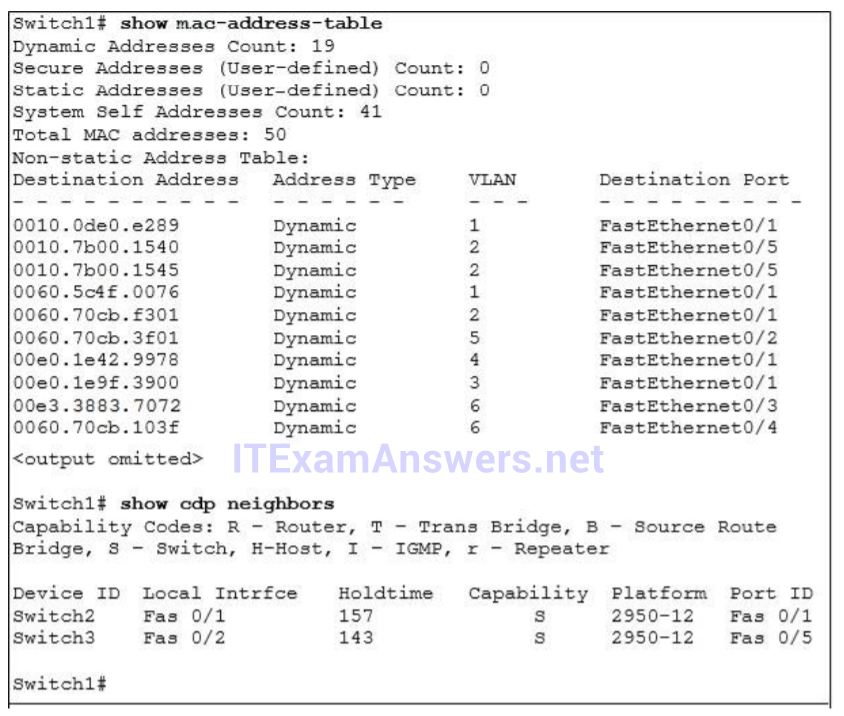
- A hub is connected directly to FastEthernet0/5
- FastEthernet0/1 is configured as a trunk link.
- FastEthernet0/5 has statically assigned mac address
- Interface FastEthernet0/2 has been disable.
- Multiple devices are connected directly to FastEthernet0/1.
- FastEthernet0/1 is connected to a host with multiple network interface cards.
269. If computer A is sending traffic to computer B, which option is the source IP address when a packet leaves R1 on interface F0/1? 
- IP address of the R2 interface F0/1
- Ip address of computer B
- Ip address of R1 interface F0/1
- Ip address of Computer A
270. Refer to the exhibit. Which two facts can you determine from the EIGRP topology table? (Choose two.) 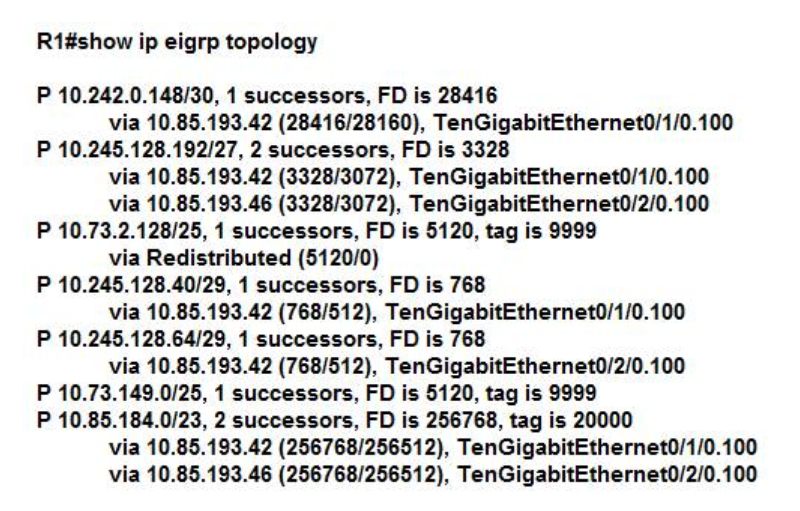
- All successors are injecting into the routing table.
- If a route has more than one successor, only one route is injected into the routing table.
- The reported distance value is greater than the feasible distance.
- The FD 28416 for route 10.242.0.148 is also the metric for the routing table.
- The variance command must have been issued to allow route 10.85.184.0 to have two successors.
271. Refer to the exhibit. Given the output shown from this Cisco Catalyst 2950, what is the reason that interface FastEthernet 0/10 is not the root port for VLAN 2? 
- This switch has more than one interface connected to the root network segment in VLAN 2.
- This switch is running RSTP while the elected designated switch is running 802.1d Spanning Tree.
- This switch interface has a higher path cost to the root bridge than another in the topology.
- This switch has a lower bridge ID for VLAN 2 than the elected designated switch.
272. Refer to the exhibit. A new subnet with 60 hosts has been added to the network. Which subnet address should this network use to provide enough usable addresses while wasting the fewest addresses? 
- 192.168.1.56/27
- 192.168.1.64/26
- 192.168.1.64/27
- 192.168.1.56/26
273. Which two statements about the tunnel mode ipv6ip command are true? (Choose two.)
- It enables the transmission of IPv6 packets within the configured tunnel.
- It specifies IPv4 as the encapsulation protocol.
- It specifies IPv6 as the encapsulation protocol.
- It specifies IPv6 as the transport protocol.
- It specifies that the tunnel is a Teredo tunnel.
274. Which two statements about LLDP are true ?(choose two)
- It uses mandatory TLVs to discover the neighboring devices
- It functions at Layer 2 and Layer 3
- It is a Cisco-proprietary technology
- It is implemented in accordance with the 802.11a specification
- It enables systems to learn about one another over the data-link layer
275. Which two commands can you use to verify an IP SLA? (Choose two.)
- show ip sla application
- show ip sla history
- show ip sla configuration
- show ip sla reaction-configuration
- show ip sla statistics
276. Which technology supports multiple dynamic secure connections over an unsecure transport network?
- Point-to-point
- DMVPN
- VPN
- site-to-site VPN
277. After an FTP session to ftp.cisco.com fails, you attempt to ping the server. A ping to ftp.cisco.com also fails, but a ping to the IP address of the server is successful. What is a reason for the failed FTP session?
- The assigned DNS server is down
- A firewall is blocking traffic from the FTP site
- An ACL is blocking the FTP request
- The Internet connection is down
278. Which command can you enter to display the operational status of the network ports on a router?
- show interface switchport
- show ip interface brief
- show running-config interface fastethernet 0/1
- show interface status
279. Which three commands are required to enable NTP authentication on a Cisco router? (Choose three)
- ntp peer
- ntp max-associations
- ntp authenticate
- ntp trusted-key
- ntp authentication-key
- ntp refclock
280. Which two operational modes are supported on the members of a StackWise switch stack? (Choose two.)
- power-sharing
- passive
- active
- redundant
- standby
281. In which STP state does MAC address learning take place on a PortFast-enabled port?
- listening
- forwarding
- discarding
- learning
282. Which option describes a benefit of a point-to-point leased line ?
- Low cost
- Full-mesh capability
- Flexibillity of design
- Simply of configuration
283. Which option is the industry-standard industrialized protocol for EtherChannel?
- LACP
- PAGP
- PRP
- REP
284. Refer to the exhibit. Which two statements about the interface that generated the output are true? (Choose two.) 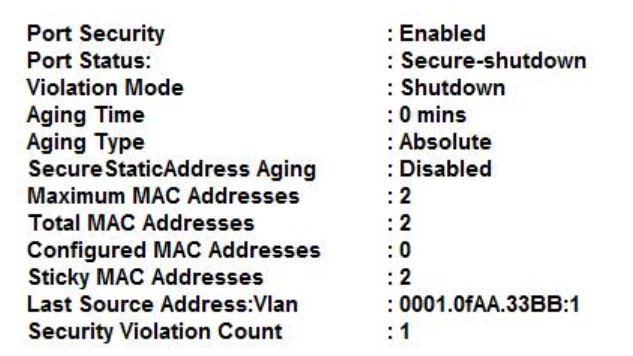
- The interface dynamically learned two secure MAC addresses.
- A syslog message is generated when the maximum number of secure MAC addresses is reached on the interface.
- Two secure MAC address are manually configured on the interface.
- The interface is error-disabled.
- An SNMP trap is generated when the maximum number of secure MAC addresses is reached on the interface.
285. While troubleshooting a GRE tunnel interface issue, show interface command output displays tunnel status up, but line protocol is down. Which reason for this problem is the most likely?
- The next hop server is misconfigured.
- The route to the tunnel destination address is through the tunnel itself.
- The tunnel was just reset.
- The interface has been administratively shut down.
286. Which two statements about IPv6 and routing protocols are true? (Choose two.)
- Link-local addresses are used to form routing adjacencies.
- OSPFv3 was developed to support IPv6 routing.
- EIGRP, OSPF, and BGP are the only routing protocols that support IPv6.
- Loopback addresses are used to form routing adjacencies.
- EIGRPv3 was developed to support IPv6 routing.
287. Which type of routing protocol operates by exchanging the entire routing information ?
- distance vector protocols
- link state protocols
- path vector protocols
- exterior gateway protocols
288. At the end of an RSTP election process, which access layer switch port will assume the discarding role? 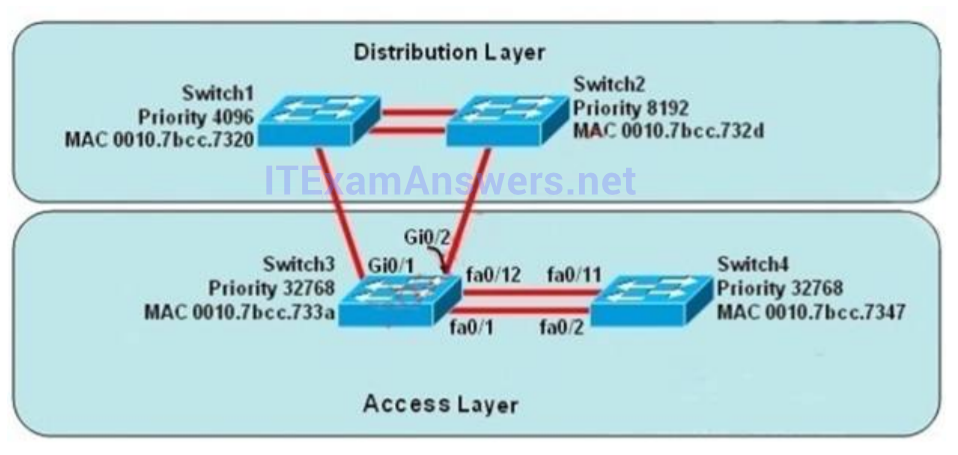
- Switch3, port fa0/1
- Switch3, port fa0/12
- Switch4, port fa0/11
- Switch4, port fa0/2
- Switch3, port Gi0/1
- Switch3, port Gi0/2
289. What are types of IPv6 static routes? (Choose Three )
- Recursive Static routes
- Directly connected Static routes
- Fully specified Static routes
- Advertised routes
- Virtual links
- Redistributed routes
290. Which two functions can be performed by a local DNS server? (Choose two.)
- assigning IP addresses to local clients
- copying updated IOS images to Cisco switches
- resolving names locally
- forwarding name resolution requests to an external DNS server
- transferring split horizon traffic between zones
291. Which two benefits of implementing a full-mesh WAN topology are true?(Choose two)
- increased latency
- redundancy
- improved scalability
- reliability
- reduced itter
292. Which two statements about IPv6 anycast addresses are true?( Choose two)
- They receive packets on the closest interface that is discovered by the routing protocol
- They are allocated from the IPv6 broadcast address space
- They are used in conjunction with source-specific multicast for IPv6
- They use the prefix FC00::/8
- They are allocated from the IPv6 unicast address space
293. What is one benefit of PVST+?
- PVST+ supports Layer 3 load balancing without loops.
- PVST+ reduces the CPU cycles for all the switches in the network.
- PVST+ allows the root switch location to be optimized per VLAN.
- PVST+ automatically selects the root bridge location, to provide optimized bandwidth usage.
294. Which keyword enables an HSRP router to take the active role immediately what it comes online?
- preempt
- priority
- version
- IP address
295. The network shown in the diagram is experiencing connectivity problems. Which of the following will correct the problems? (Choose two.) 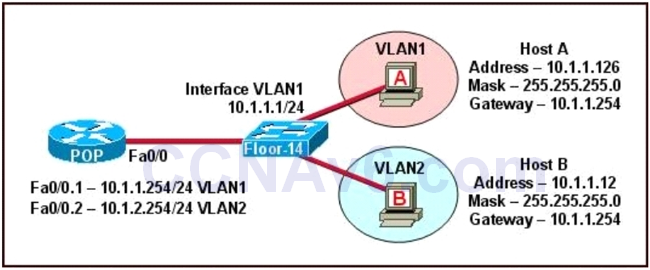
- Configure the gateway on Host A as 10.1.1.1
- Configure the gateway on Host B as 10.1.2.254
- Configure the IP address of Host A as 10.1.2.2
- Configure the IP address of Host B as 10.1.2.2
- Configure the masks on both hosts to be 255.255.255.224
- Configure the masks on both hosts to be 255.255.255.240
296. Which technology provides chassis redundancy in a VSS environment?
- BFD
- multichassis EtherChannels
- VRRP
- StackWise
297. During which phase of PPPoE is PPP authentication performed?
- the PPP Session phase
- Phase 2
- the Active Discovery phase
- the Authentication phase
- Phase 1
298. Which switching method helps mitigate late collissions?
- Layer 3
- Store-and-forward
- fragment-free
- cut-through
299. Which two QoS tools can provide congestion management? (Choose two.)
- CBWFQ
- FRTS
- CAR
- PQ
- PBR
300. Which command is configured on a switch to enable neighbor discovery in a multivendor environment?
- lldp run
- lldp transmit
- lldp receive
- cdp run
301. What parameter can be different on ports within an EtherChannel?
- speed
- DTP negotiation settings
- trunk encapsulation
- duplex
302. At Which severity level can syslog logging begin to affect router performance?
- debugging
- emergency
- notification
- critical
303. What are two benefits that the UDP protocol provide for application traffic? (Choose two.)
- UDP traffic has lower overhead than TCP traffic
- UDP provides a built-in recovery mechanism to retransmit lost packets
- The TTL field in the UDP packet header enables a three-way handshake to establish the connection
- The application can use checksums to verify the integrity of application data
- UDP maintains the connection state to provide more stable connections than TCP
304. Which two facts about configuring EIGRPv6 are true? (Choose two.)
- The variance command for EIGRPv6 is independent of EIGRPv4.
- If you change the interface delay, the EIGRPv4 delay remains unchanged.
- You must configure neighboring devices with the same ipv6 hello-interval eigrp value.
- If you change the interface bandwidth, the EIGRPv4 metric is affected.
- The router ID must be an IPv6 address.
305. Which command can you enter to set the default route for all traffic to an interface?
- router(config)#ip route 0.0.0.0 0.0.0.0 GigabitEthernet0/1
- router(config)#ip route 0.0.0.0 255.255.255.255 GigabitEthernet0/1
- router(config-router)#default-information originate
- router(config-router)#default-information originate always
306. Which two statements about an Ethernet frame source address are true? (Choose two.)
- The leftmost bit is always 0
- The leftmost bit is always 1
- The address is 4 bits long
- The address is 4 bytes long
- The address is 6 bytes long
307. Which command should you enter to configure a DHCP Client?
- ip dhcp pool
- ip dhcp client
- ip helper-address
- ip address dhcp
308. Refer to the exhibit. Which VLAN ID is associated with PC B?

- VLAN 5
- VLAN 20
- VLAN 10
- VLAN 1
309. Refer to the exhibit. Which two configuration lines must you add to the Dialer1 interface configuration to enable the two interfaces to establish a PPPoE connection (Choose two)

- ppp enable group
- no cdp enable
- ppp chap hostname cisco
- ppp authentication pap chap callin
- ip unnumbered GigabitEthernet0/0
310. Which characteristics are representative of a link-state routing protocol? (Choose two.)
- calculates shortest path
- exchanges routing tables with neighbors
- provides common view of entire topology
- utilizes frequent periodic updates
- utilizes event-triggered updates
311. Refer to the exhibit. Users on the 10.120.26.x subnet can reach server 10.10.20.10, but they cannot reach server 10.10.10.10. The network is using dynamic routing, and routers R1 and R2 are connected via EIGRP. Which two actions must you take to begin troubleshooting the connectivity issue to server 10.10.10.10? (Choose two.)

- Verify the status of the interfaces between routers and switches
- Verify that routers R1 and R2 have established an EIGRP neighbor relationship.
- Verity that the route to the server is present in the topology table and routing table.
- Verify that the inbound and outbound ACLs on each device permit traffic to and from the server.
- Verify that the route to the server is present in the database table
312. You are configuring port security on a Cisco switch. Which command must you enter so that only a certain number of dynamically learned MAC addresses are permanently assigned to the interface?
-
-
- switchport port-security maximum
- switchport nonegotiate
- switchport port-security
- switchport port-security mac-address sticky
-
313. When you configure DHCP on a router, Which command must you enter so that the default gateway is automatically distributed?
-
-
- dns-server
- default-gateway
- ip helper-address
- default-router
-
314. Which statement about loopback testing on a router serial interface is true?
-
-
- Traffic passes through the interface with both software loopbacks and hardware loopbacks
- Traffic is dropped with a hardware loopback, but traffic passes through the interface with a software loopback
- Traffic is dropped with a software loopback, but traffic passes through the interface with a hardware loopback
- Traffic is dropped with both software loopbacks and hardware loopbacks
-
Drag & Drop questions
18. DRAG DROP. Drag and drop the STP features from the left onto the correct descriptions on the right.
Select and Place:
Correct Answer:
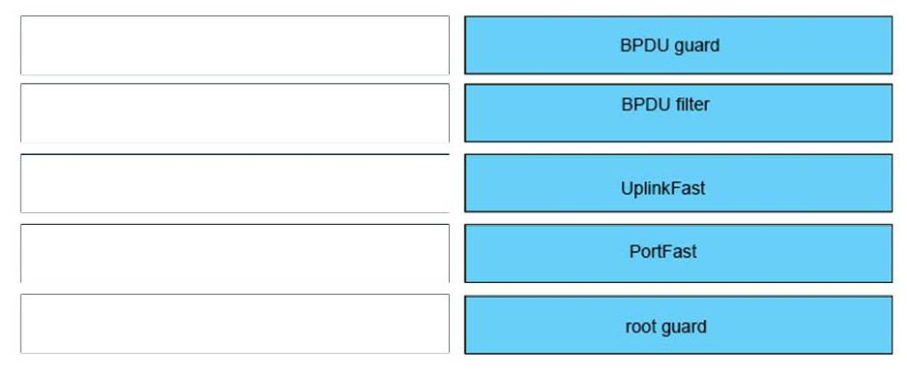
Answer:
+ BPDU Filter: drops all BPDU received on the switch port
+ BPDU guard: disables the switch port when it receives a BPDU
+ PortFast: forces the switch to transition directly from the blocking state to the forwarding state
+ Root guard: prevents the port from becoming a locked port
+ UplinkFast: enables quick convergence when a direct link to a non-end device fails
41. DRAG DROP. Drag and drop each WAN design option on the left onto the correct description on the right.
Select and Place:
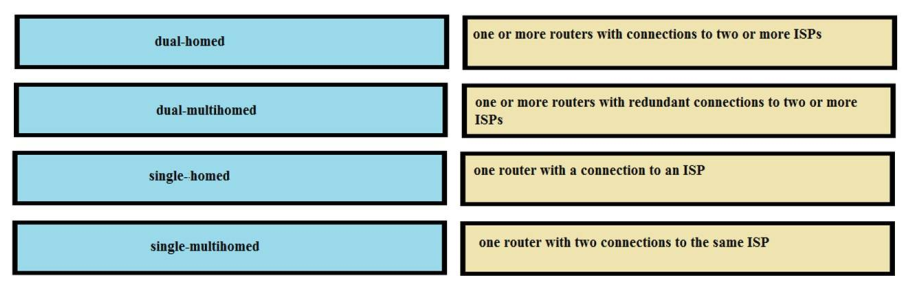
Correct Answer:
Answer:
one or more routers with connections to two or more ISPs <-> dual-homed
one or more routers with redundant connections to two or more ISPs <-> dual-multihomed
one router with a connection to an ISP <-> single-homed
one router with two connections to the same ISP <-> single-multihomed
41. DRAG DROP. Drag and drop each WAN design option on the left onto the correct description on the right.
Select and Place:

Correct Answer:
Answer:
one or more routers with connections to two or more ISPs <-> single-multihomed
one or more routers with redundant connections to two or more ISPs <-> dual-multihomed
one router with a connection to an ISP <-> single-homed
one router with two connections to the same ISP <-> dual-homed
8. DRAG DROP. A user is unable to connect to the Internet. Based on the layered approach to troubleshooting and beginning with the lowest layer, drag each procedure on the left to its proper category on the right.
Select and Place:
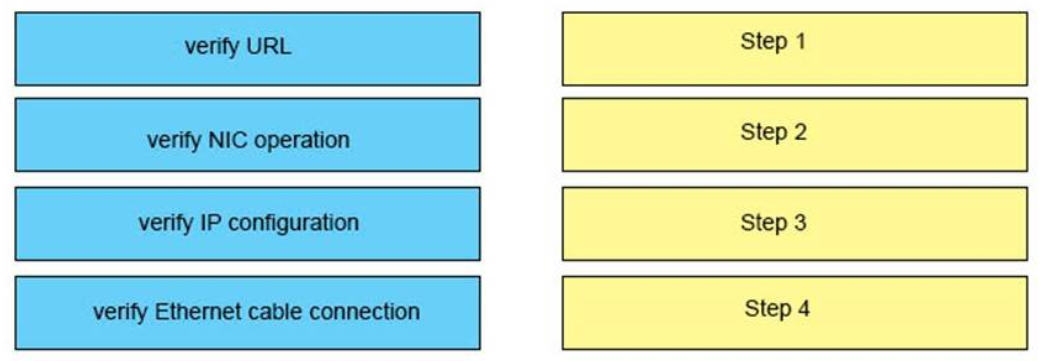
Correct Answer:
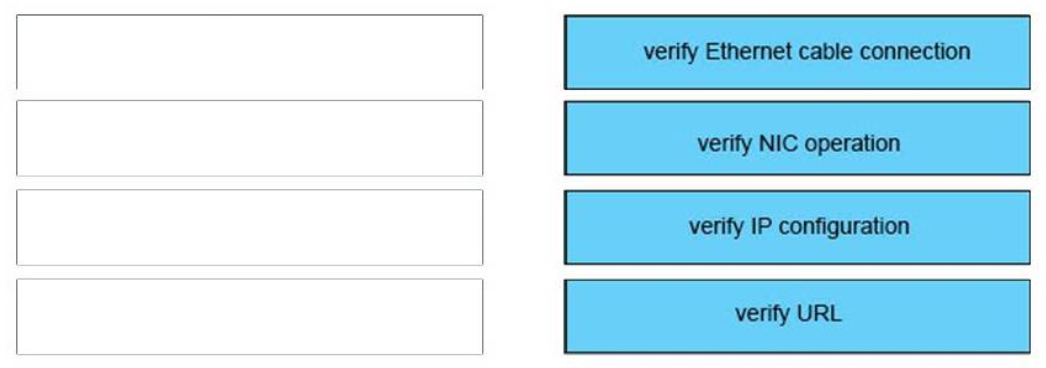
Answer:
1) Verify Ethernet cable connection: Step 1
2) Verify NIC operation: Step 2
3) Verify IP configuration: Step 3
4) Verify URL: Step 4
25. DRAG DROP. Drag and drop the BGP terms from the left onto the correct descriptions on the right.Select and Place:
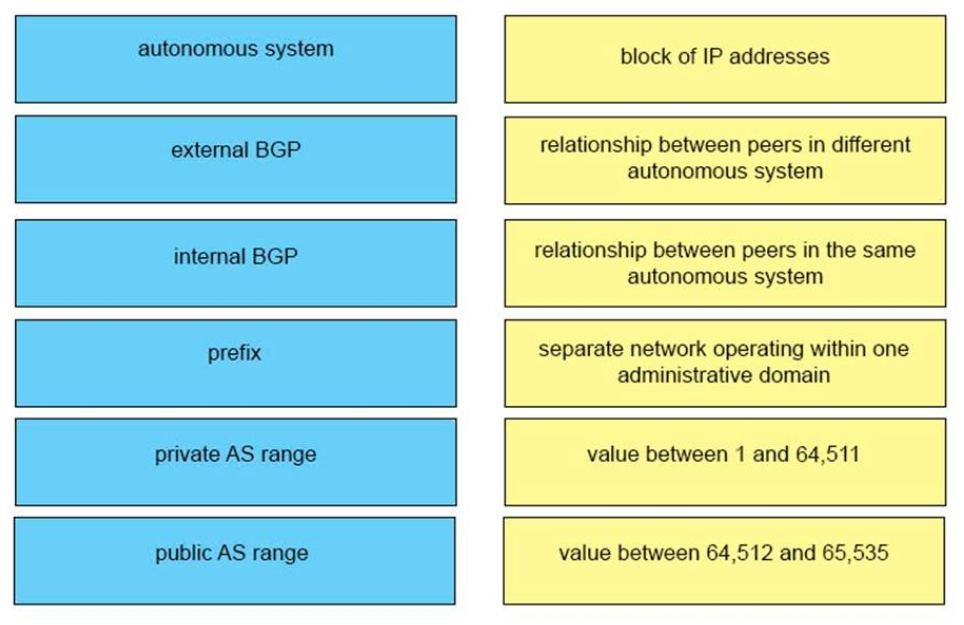 Correct Answer:
Correct Answer:
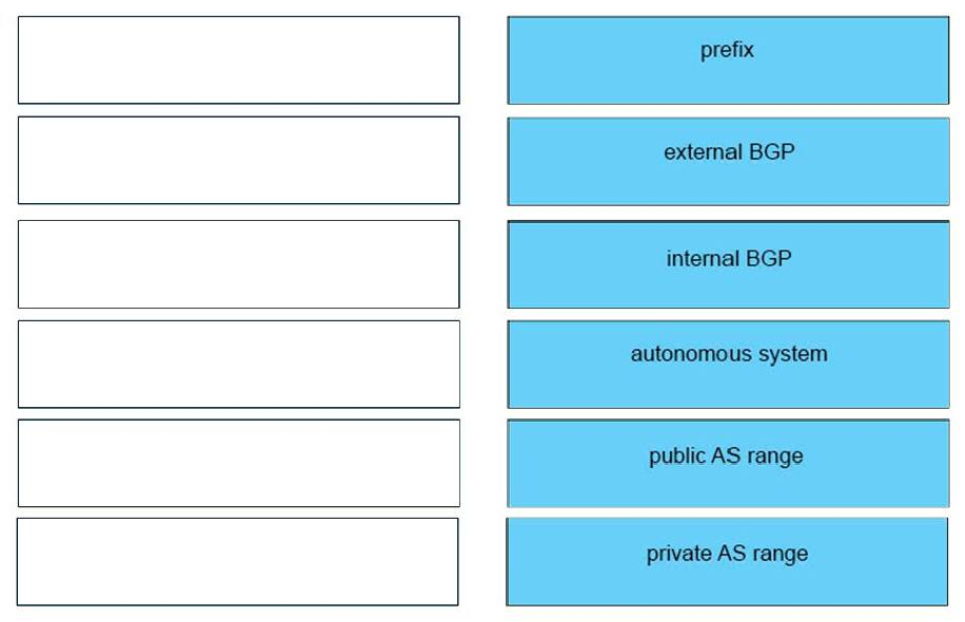
Answer:
iBGP <-> relationship between peers in same autonomous system
eBGP <-> relationship between peers in different autonomous system
Prefix <-> block of IP addresses
Private AS range <-> Value between 64,512 and 65,535
Public AS range <-> Value between 1 and 64,511
Autonomous System <-> separate network operating within one administrative domain
42. DRAG DROP.
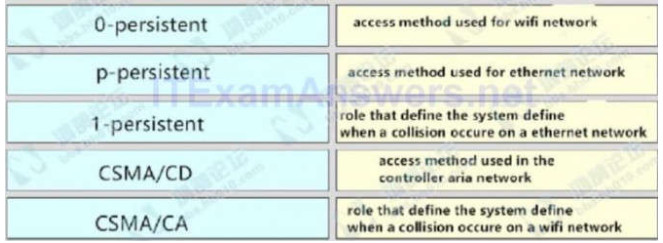
Correct Answer:
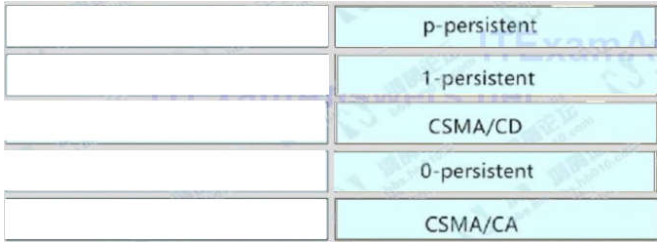
access method used for wifi network <-> p-persistent
access method used for ethernet network <-> 1-persistent
role that define the system define when a collision occure on a ethernet network <-> CSMA/CD
access method used in the controller aria network <-> 0-persistent
role that define the system define when a collision occure on a wifi network <-> CSMA/CA
28. DRAG DROP. Drag and drop the QoS features from the left onto the correct descriptions on the right.Select and Place:
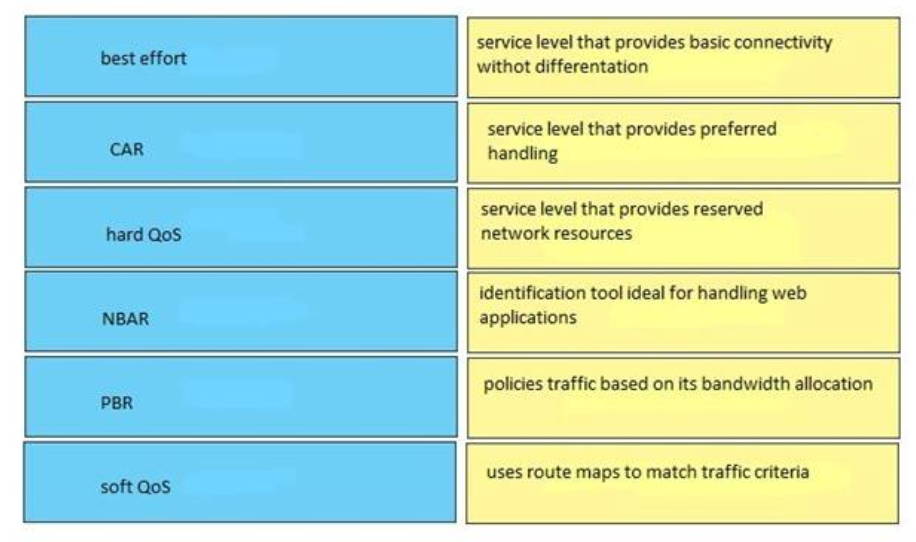 Correct Answer:
Correct Answer:
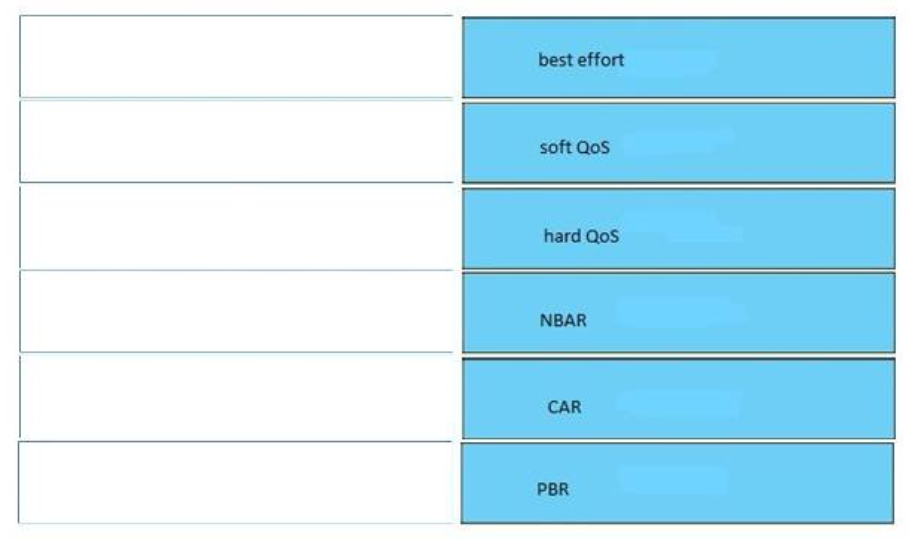
53. Refer to the exhibit
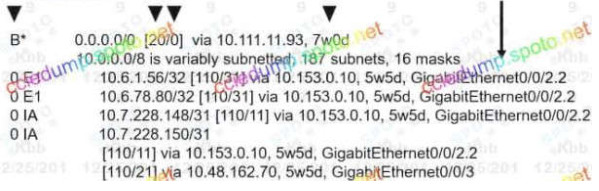
Drag and drop the routing table components on the left onto the corresponding letter from the exhibit on the right. Not all options are used.
Select and Place – Your Response
Correct Answer:
A: route source
B: administrative distance
C: metric
D: timestamp
E: outbound interlace ho
30. DRAG DROP. Drag and drop the DHCP client states from the left into the standard order in which the client passes through
them on the right.
Select and Place:
Correct Answer:

Answer:
initializing – first
selecting – second
requesting – third
bound – fourth
renewing – fifth
rebinding – sixth
29. DRAG DROP. Drag and drop the PPPoE message types from the left into the sequence in which PPPoE messages are sent on the right.Select and Place:
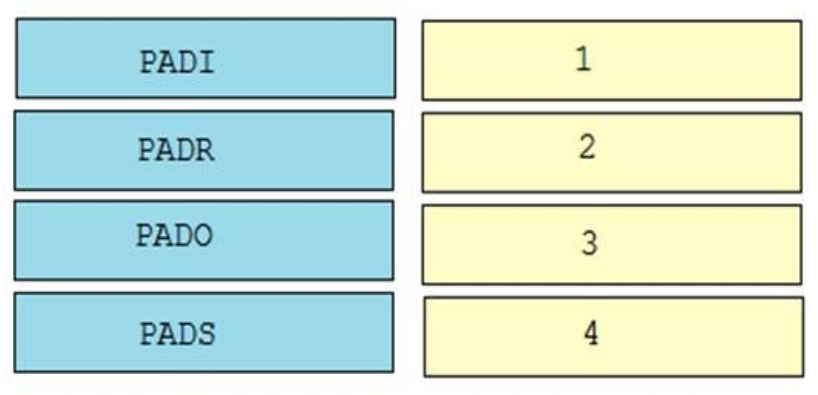 Correct Answer:
Correct Answer:
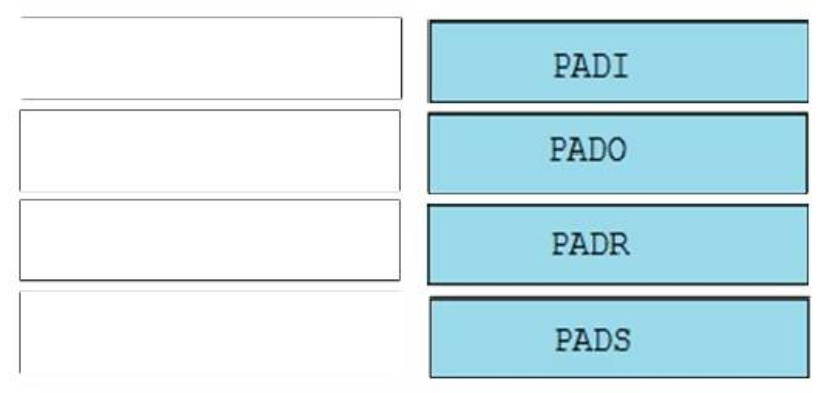
Answer:
1. PADI
2. PADO
3. PADR
4. PADS
49.

– Local database of address mappings that improves name-resolution performance : cache
– Service that maps hostnames to IP addresses : DNS
– Disables DNS services on a cisco device : no ip domain-lookup
– In response to client requests, queries a name server for IP address information : name resolver
– Component of e URL that indicates the location or organization type, such as .com or. edu : domain
3. DRAG DROP. Drag the cable type on the left to the purpose for which is the best suited on the right. Not all options are used.
Select and Place:
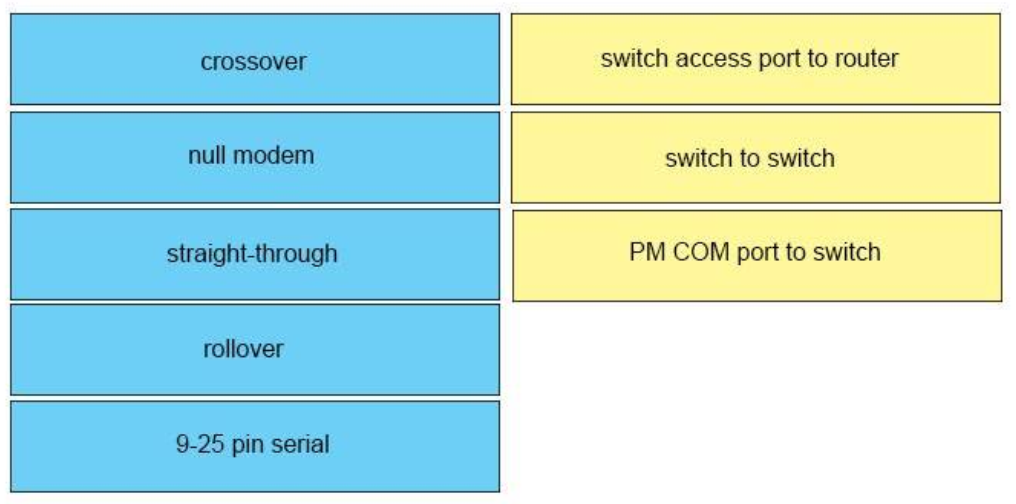
Correct Answer:
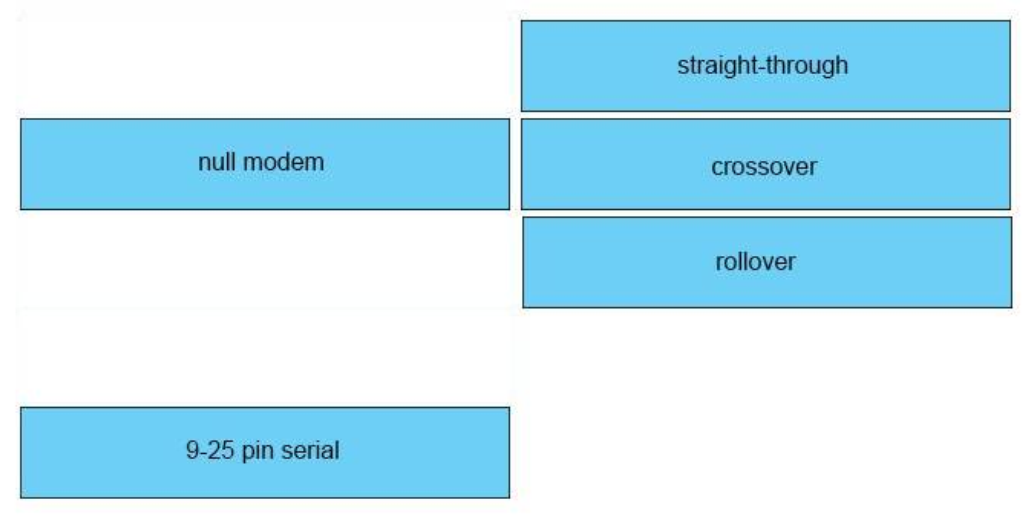
Answer:
+ switch access port to router: straight-through
+ switch to switch: crossover
+ PC COM to switch Console port: rollover
5. DRAG DROP. Drag and drop the IPv6 IP addresses from the left onto the correct IPv6 address types on the right.
Select and Place:
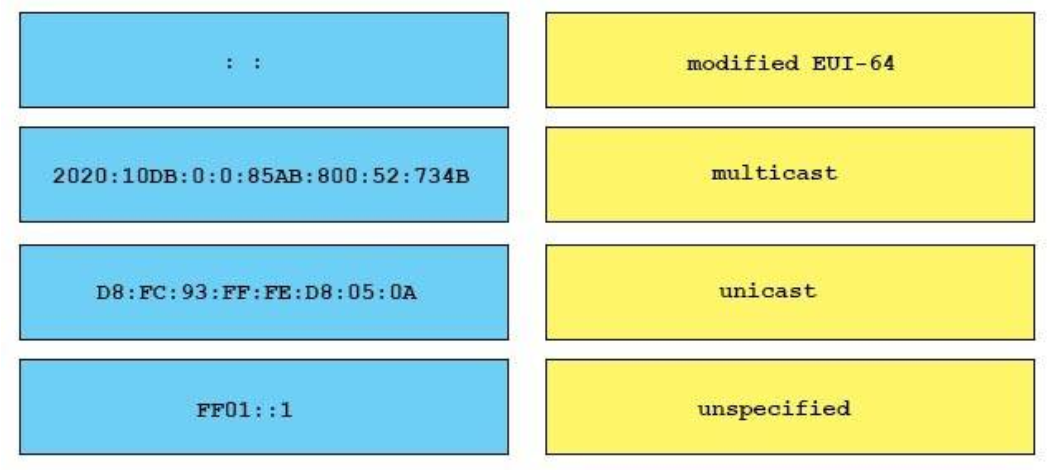
Correct Answer:
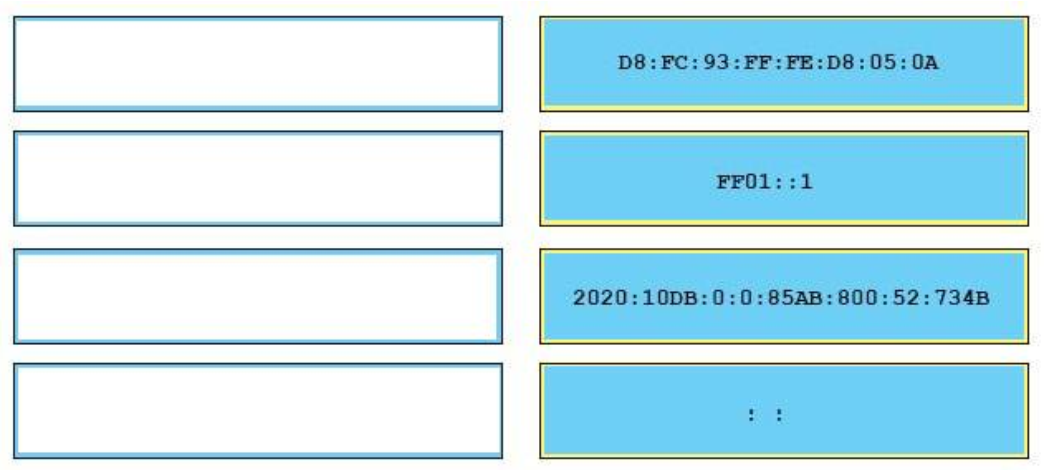
+ Modified EUI-64: DB:FC:93:FF:FE:D8:05:0A
+ multicast: FF01::1
+ unicast: 2020:10D8:0:0:85:800:52:7348
+ unspecified: ::
31. DRAG DROP. Drag and drop the DNS lookup commands from the left onto the correct effects on the right.
Select and Place:
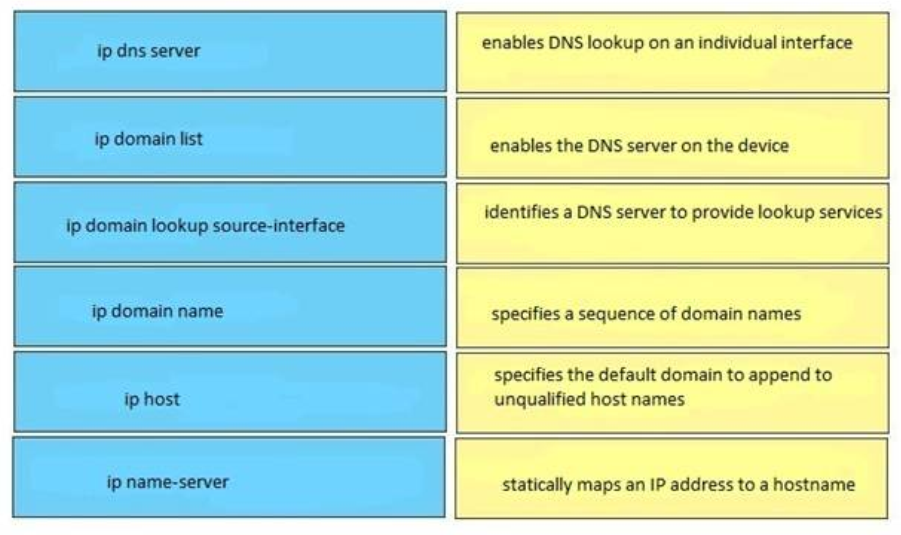
Correct Answer:
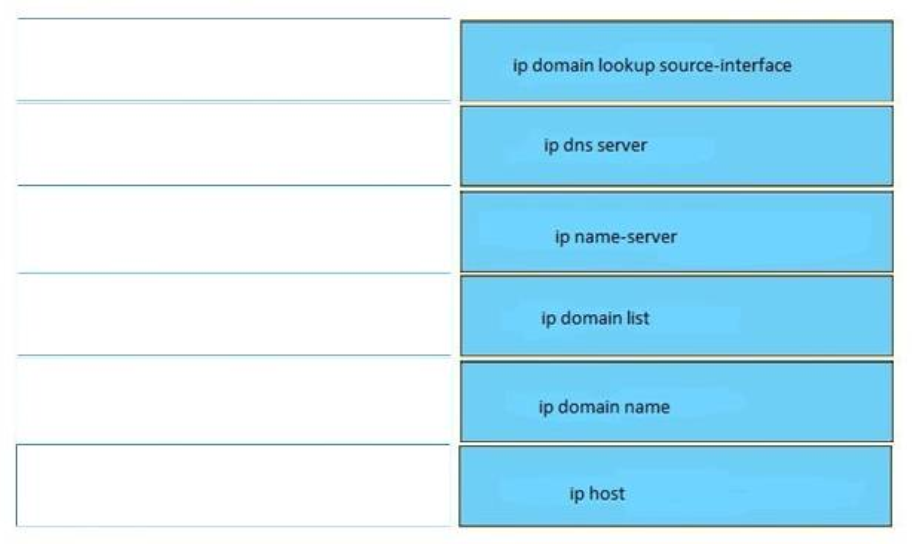
Answer:
enables DNS lookup on an individual interface <-> ip domain lookup source-interface
enables the DNS server on the device <-> ip dns server
identifies a DNS server to provide lookup services <-> ip name-server
specifies a sequence of domain names <-> ip domain list
specifies the default domain to append to unqualified host names <-> ip domain name
statically maps an IP address to a hostname <-> ip host
7. DRAG DROP. Drag and drop the IEEE standard cable names from the left onto the correct cable types on the right.
Select and Place:
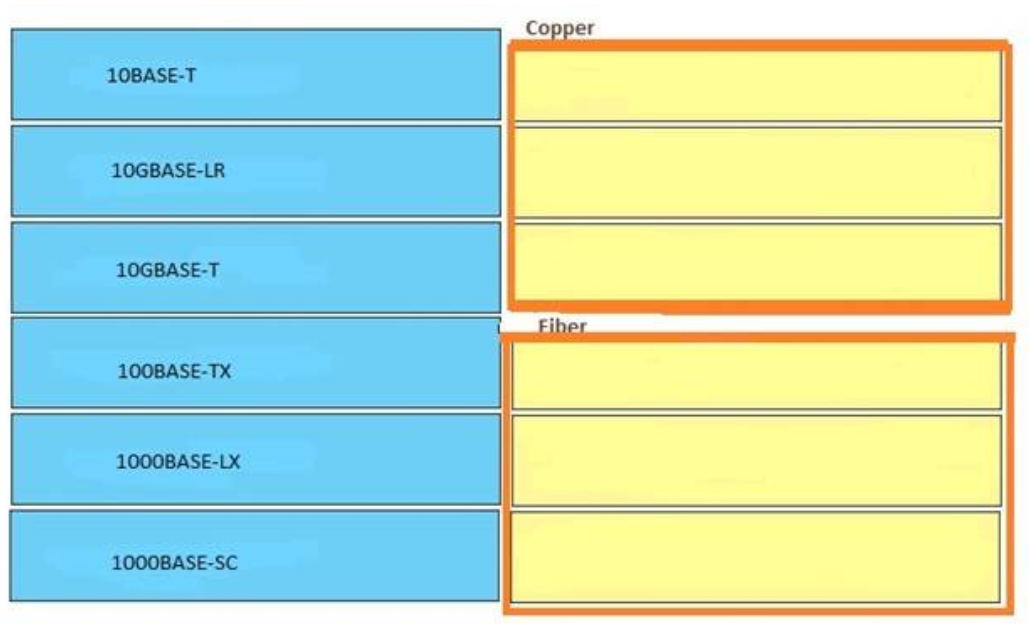
Correct Answer:

Answer:
Copper:
+ 10BASE-T
+ 100BASE-TX
+ 10GBASE-T
Fiber:
+ 10GBASE-LR
+ 1000BASE-LX
+ 1000BASE-SC
20. DRAG DROP. Drag and drop the BGP components from the left onto the correct descriptions on the right.
Select and Place:
Correct Answer:
Answer:
+ Device that running BGP: BGP speakers
+ Neighbor that share the same AS number as a local device: iBGP peer
+ Neighbor that located outside of AD domain of the local device: eBGP peer
+ Value that identify an AD: Autonomous system number
+ Value that is advertise with network keyword: Prefix
26. DRAG DROP. Drag and drop the values in a routing table from the left onto the correct meanings on the right.Select and Place:
Correct Answer:
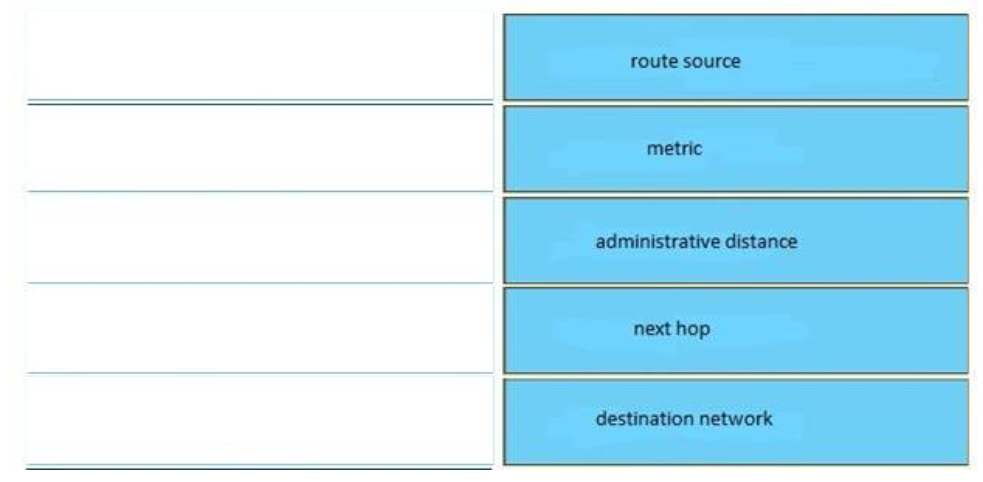
Answer:
+ Administrative distance: indicator of the trustworthiness of the route
+ Destination network: remote network address
+ Metric: value used by the router to determine the preferred route
+ Next hop: network to which the router forwards packets on the associated route
+ Route source: code that indicates the method by which the router learned the route
36. DRAG DROP. Drag and drop the extended traceroute options from the left onto the correct descriptions on the right.
Select and Place:
Correct Answer:
Answer:
+ Maximum time to live: value that, when reached, terminates the traceroute command
+ Minimum time to live: suppresses the display of known hops
+ Numeric display: suppresses the display of hostnames
+ Source address: overrides the router selection of an outbound interface
+ Timeout: sets the interval for which the probe waits for a response
+ Timestamp, verbose: IP header options
6. DRAG DROP. Drag and drop the application protocols from the left onto the transport protocols that is uses on the right.
Select and Place:
Correct Answer:
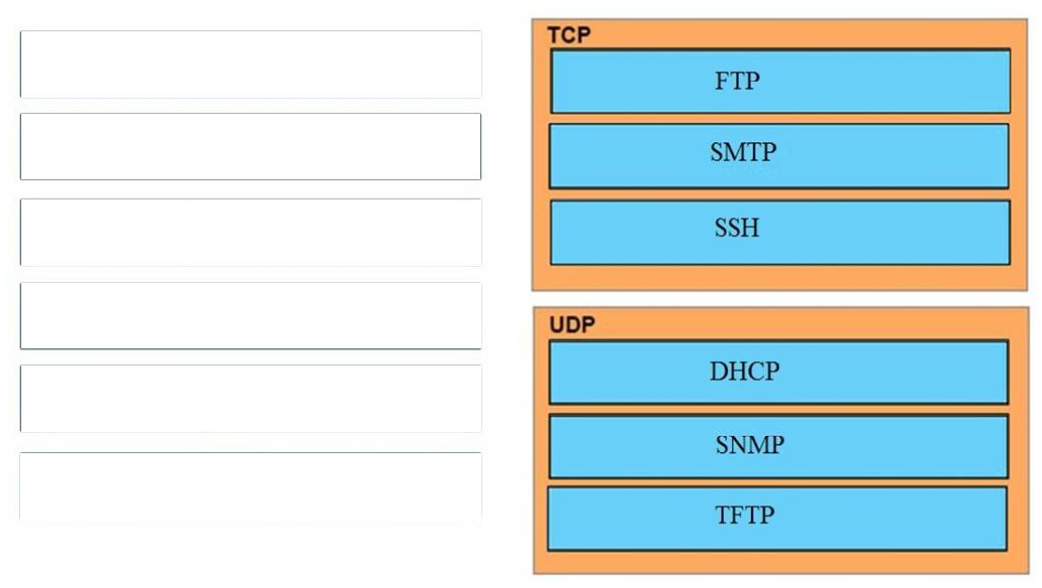
TCP:
+ SMTP
+ SSH
+ FTP
UDP:
+ SNMP
+ DHCP
+ TFTP
46.
mac that is learned by the switch through normal traffic : Dynamic mac address
associates a learned mac address with its connected interface : Mac address table
removing an inactive mac after a specified time : Mac aging
feature that determines whether incoming traffic will be allowed : Mac ACL
adding a previously unknown mac into the address table : Mac learning
mac address that remains in the mac address table after reboot : Static mac
14. DRAG DROP. Drag and Drop the descriptions of IP protocol transmissions from the left onto the correct IP traffic types on the right.
Select and Place:
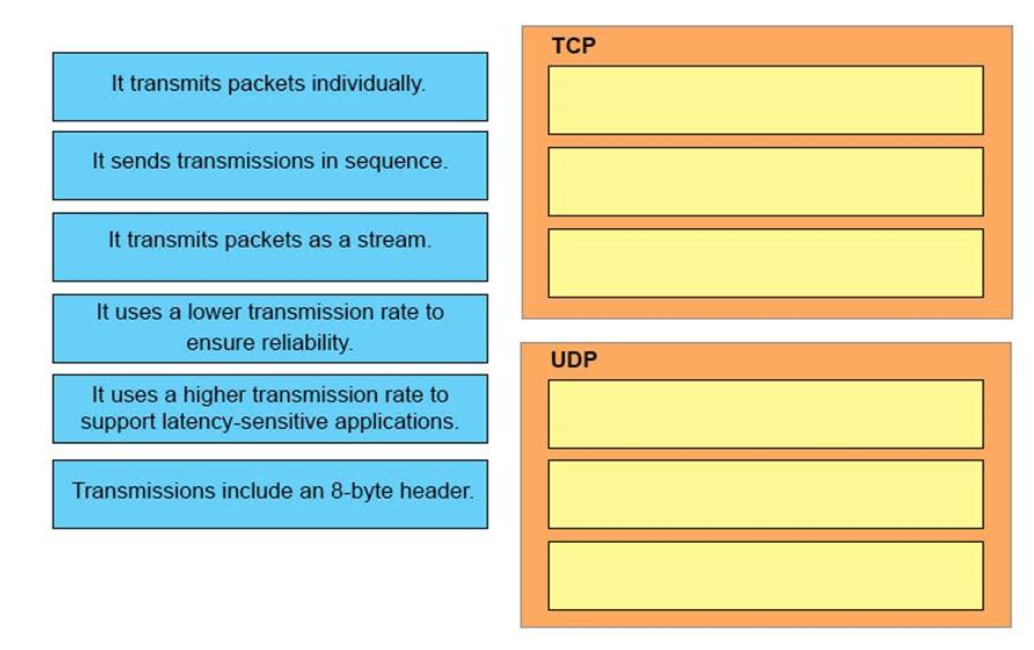
Correct Answer:
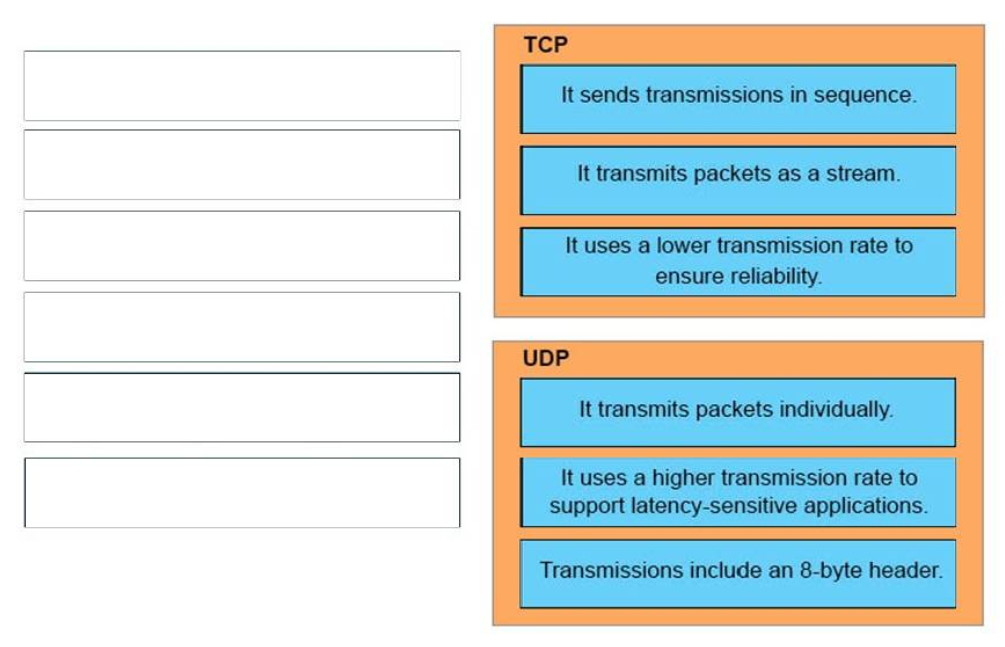
Answer:
TCP:
+ It sends transmissions in sequence.
+ It transmits packets as a stream.
+ It uses a lower transmission rate to ensure reliability.
UDP:
+ It transmits packets individually.
+ It uses a higher transmission rate to support latency-sensitive applications.
+ Transmissions include an 8-byte header.
45.
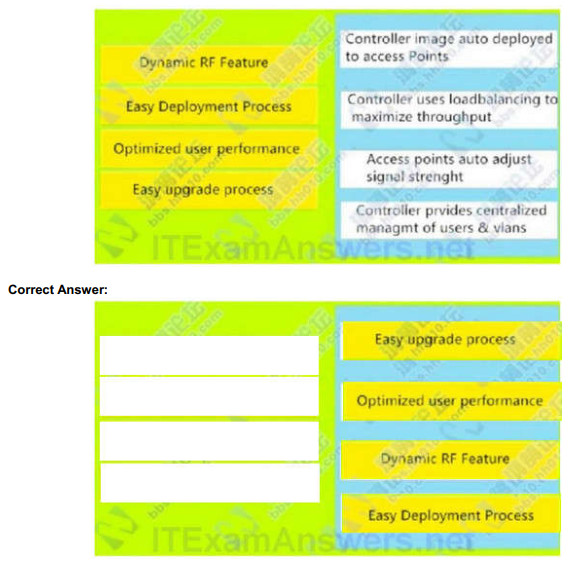
Controller image auto deployed to access Points : Easy upgrade process
Controller uses loadbalancing to maximize throughput : Optimized user performance
Access points auto adjust signal strenght : Dynamic RF Feature
Controller prvides centralized managmt of users & vlans : Easy Deployment Process
9. DRAG DROP. Drag the terms on the left onto the appropriate OSI layer on the right. (Not all options are used.)
Select and Place:
Correct Answer:
Answer:
Network Layer:
+ packets
+ IP address
+ routing
Transport Layer:
+ udp
+ segments
+ windowing
34. DRAG DROP. Drag the security features on the left to the specific security risks they help protect against on the right. (Not all options are used.)
Select and Place:
Correct Answer:
Answer:
1) VTY password: remote access to device console
2) console password: access to the console 0 line
3) access-group: access to connected networks or resources
4) service password-encryption: viewing of passwords
5) enable secret: access to privileged mode
16. DRAG DROP. Drag and drop the networking features of functions from the left onto the planes on which they operate on the
right.
Select and Place:
Correct Answer:
Answer:
Control Plane:
Filtering
Routing state exchange
Device access
Data Plane:
QoS
Establishes telnet session
Data Encapsulation
11. DRAG DROP. Drag and drop each cable type from the left onto the type of connection for which it is best suited on the right.
Select and Place:
Correct Answer:
Answer:
crossover: switch to switch
DTE/DCE: Serial to Serial
straight-through: PC to router
rollover: PC to Console
1. DRAG DROP. Drag and drop the Ethernet terms from the left onto the correct descriptions on the right.
Select and Place:
Correct Answer:
– collision detection: use of CSMA to ensure that devices on a shared link can communicate without interfering with one another
– collision rate: calculated value that can increase when a new station is added to a network
– carrier sense: ability of an end device to determine that another device is communicating on a shared link
– medium: link used to transport data between a source and a destination
– collision: potential conflict when than one end device attempts to send traffic over the same link
55. Drag each WAN accesses connectivity option on a the left to the matching design goal on the right.
Correct Answer:

- Enable mobile devices to connect to an enterprise network : client VPN
- Use the logical full mesh network of a service provider across an enterprise headquarters and remote sites : MPLS
- Securely connect two networks over an untrusted network : site-to-site VPN
- Use GRE tunnels and IPsec to create a full mesh network through a central location. : DMVPN
54. Drag and drop the source from the left to the numbers on the right. Beginning with the lowest and ending with highest administrative distance.
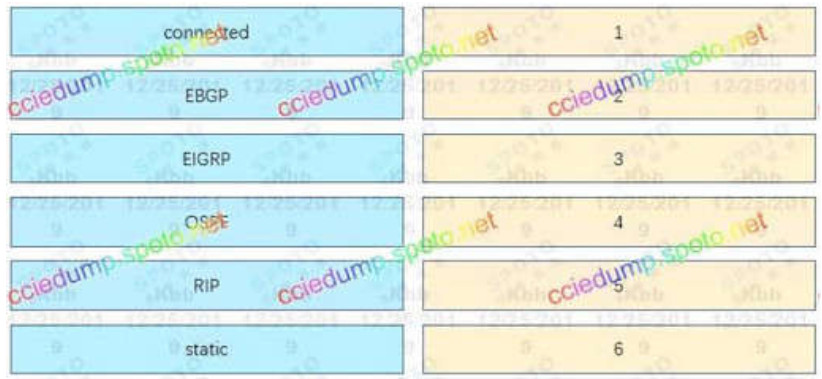
Correct Answer:
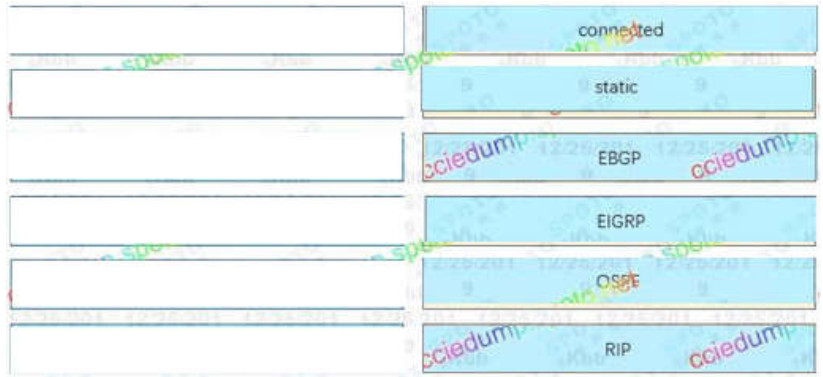
1: connected
2: static
3: EBGP
4: EIGRP
5: OSPF
6: RIP
56. You are configuring a switch so that it accepts traffic from a maximum of two dynamic MAC address. Drag and drop the required configuration commands on the left into the correct sequence on the right. (Not all commands are used.)
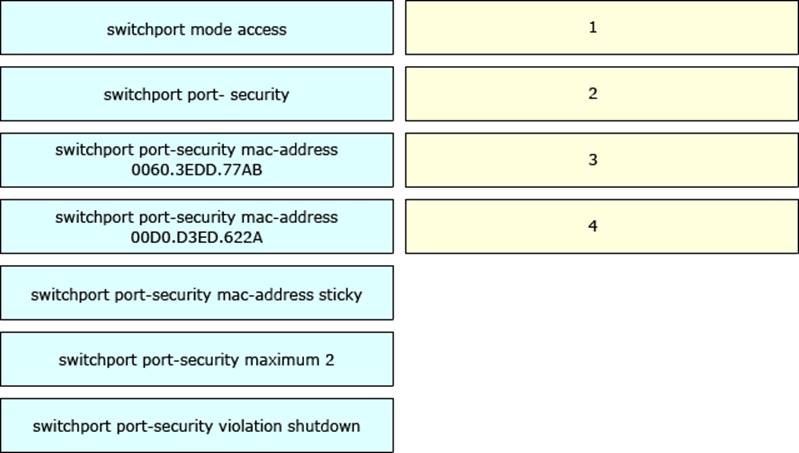
Correct Answer:
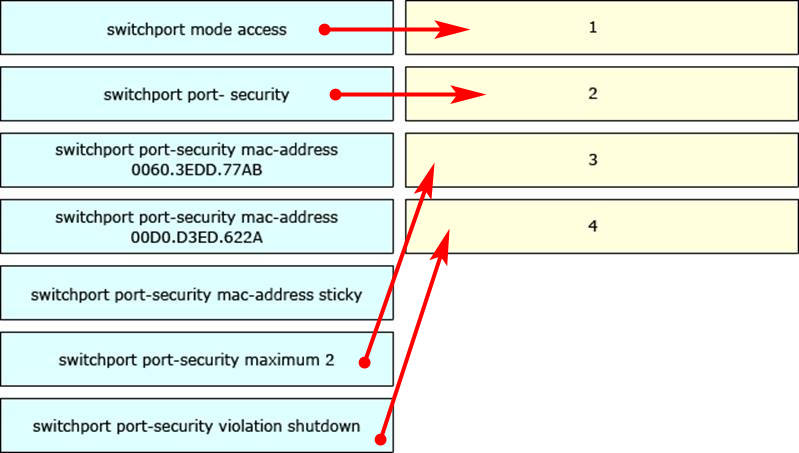
1: Switchport mode access
2: Switchport port-security
3: Switchport port-security maximum 2
4: Switchport port-security violation shutdown
Labs simulation
OSPF Neighbor Sim
EIGRP Troubleshooting Sim
ACL 2 Sim
ACL Sim
DHCP Troubleshooting Sim
RIPv2 Troubleshooting Sim
GRE Troubleshooting Sim
EIGRP GRE Troubleshooting
IPv6 OSPF Sim

 An example of configuring using this command is shown below:
An example of configuring using this command is shown below:
As the old CCNA and CCNP exams are wrapping up today, does anyone know of any good resources for the new ENCOR or ENARSI exams? I hear cbtnugget videos are being created for ENCOR which will be out in a few weeks.
Thanks,
Ethan
I’ve been reading through the official Cisco Press ENCOR kindle book, with the book you can get access to practice exam questions, flash cards, memory tables etc and each chaper of the book tests you on the bits discussed within the chapter.
Best wishes,
Robin
I have passed.
thx admin
thx Travis
thx Ethan(Mr. Perfect)
I would like to express my deep appreciation.
Congratulations!
I take my test in 9 hours. I hope everyone was genuine up here as I will be using it exclusively until I take my test. I took it last week and made a 770. I will say that all of the questions I got on that test I believe are in this dump. I am gonna focus on this dump for 2 hours prior to going to take the test. I have been on this dump for the past few hours and I wish I had it last week. Congrats to those who took it and passed.
I passed. Thanks a bunch to this site as it gave me the extra I needed to get over the hump. Now I take a break and then I will start on the CCNP.
Passed today with 9xx/1000.
Every single question and lab I got was within the lite 300 question version with just a couple of variations.
The labs I got were:
EIGRP GRE Troubleshooting
ACL-2 – Mod 3
Drag and drops:
3
6
20
30
55
As far as I remember, these questions from the lite version were used:
1
4
7
10
13
15
17
18
20
21
22
23
26
28
30
33
35
36
37
38
40
41
44
47
48
59
60
62
63
64
65
69
variation on 70 where it asks you to choose how many different subnets are listed etc
variation on 73 – this one had I think 5 sticky addresses which was asked about in the question
76
77
78
79
80
81
83
84
85
86
95
103
104
105
114
117
118
132
All the best,
Ethan
Passed my exam with 9xx/1000. I want to especially thank the ADMIN for providing us with the necessary study materials, I know it takes a lot of work to do so. I also want to the thank everyone else for collaborating and helping each other out with issues. Good teamwork on this site! 3 labs ACL1/ACL2 MOD4/EIGRP GRE. I had 2 DD. Q36 DD & 53 DD. Again, I appreciate everyone’s help with helping me pass.
Congrats my friend. questions were from Q300? you passed with 9xx
Buddy,
Yes my dude! there were a few new questions 3-4 I believe, they are from the 1000q. Labs are pretty much exact, with minor ip changes on acl2. Honestly if you know the 300 and labs as they are, it is really no problem. I was more nervous then anything. And don’t 2nd guess your answers, as i usually have an issue with that.
I passed the CCNA back in 2014 straight out of college. And had to re-take due to expiration and laziness. After re-learning almost everything and studying my a$$ off, do not let this certification expire.
wow.. you did a good job. This will be my first CCNA
how long it took you to do this exam?
Congratulations Travis,
I have mine in 9 hours.
All the best,
Robin
Travis, in ACL2 mod 4 last part – did you use any any or IP of Public Web Server?
access-list 100 permit ip any any??
Congratulations Travis
Cleared CCNA 200-125. Thanks Guys. Used 300Q
Posting a note of thanks for the administrator. Cleared 200-125.Pl ensure you go through all the questions listed along with the labs and Drag and drop. Best of luck!!
Hi guys, just wanted to say that the questions helped a lot, study them and the Labs you will pass. Make sure you study the Lab not only Q300. Best of luck.
I just finished my exam and I passed. Without fear of contradiction, I can recommend this site to my family, friends and colleagues 😊
Thanks it helps to pass 870 points
So i’ve ready a comment in another section on this site, with someone saying the exam has really nothing to do with the questions on this site……..is this for real? I’m just confused how this is possible if multiple people are passing. i really hope this isn’t true as my test is tomorrow :(
Not trying to discourage anyone, just want to make sure the information is legit, which it seems legit to myself.
Yea, I know. I am confused too :(
I work full time job, then after work I study 3-4 hours. I know its not enough and I still answer incorrect when I do practice VCE exam. Hopefully, nothing changed.
@buddy,
I work a full 40 hr week IT job already as well, and as soon as i get home i do 6 hours a night. I just hope my 100’s of hours i put into the labs and questions wasn’t for a waste of time. I still have confidence in this site, so it’s kind of late to change study habits now. I’ll give feed back once I am done with my test to help others
@Buddy,
In the ACL lab2. Did you notice if you need to alter / add an IP address and subnet mask to the serial 0/0/0 interface that connects to the core?
who ever is posting after the exam saying 9xx/1000… how come everyone is scoring in 900s, I heard CCNA is not an easy exam……….
Two more on the page said they scored 9xx… really!!! :-|
I just finished my exam and I passed. The questions are exactly as they are here. I got 3 labs: ACL2, EIGRP GRE and ACL
Hello All,
Can someone please help clarify the answer to Question 11? It says the traffic will be send to VLAN 100 which is the native VLAN, however the trunk does allow VLAN 10, so why would it drop onto the native VLAN?
Thanks,
Robin
Robin,
I have asked this question a few times. I also don’t understand how it would be passed to vlan 100.
for me what’s odd is that there’s vlan5 allowed on the trunk so why the need to use native vlan?
disregard my last comment.. read the Q wrong..
I hope this explains
Explanation:
The native VLAN of Fa0/1 interface on SW1 is VLAN 10 so traffic originated from this VLAN on Fa0/1 will be untagged. While the native VLAN of Fa0/1 on SW2 is VLAN 100 so when SW2 receives an untagged frame it will forward this frame to VLAN 100.
Hi Buddy,
Thanks for taking the time to clarify. I suddenly realised this last night when I came across the question again. Of course if VLAN 10 is native of SW1 then it will be untagged traffic by the time it gets to SW2 and then any untagged traffic will drop onto its own native VLAN 100.
Really appreciate all of the help and advice on this site, its great.
Best wishes,
Robin
i have passed my ccna with 920. Thx admin. I advise you to read the 300 questions. and labs.
I have ACLs and gre lab. drag and drop DHCP
Took the exam yesterday (Feb 19th, 2020) – and pass the exam with 889 score. I can say that 98% question here is up to date. Good for reference. Thank you admin and everyone participating for the discussion. Moving forward to CCNP
Question 310. Which characteristics are representative of a link-state routing protocol? (choose two) I have read in many articles online that they “exchange routing tables with their direct neighbors” to conserve bandwidth. So i’m not sure why the answer is “provides common view of entire topology”. Which answer should it be?
Which task should you perform before you use the APIC-EM Path Trace tool to perform ACL analysis?
A. Verify that DNS is configured on the controller
B. Execute a standard traceroute to the destination
C. Verify that the devices of interest are included in the device inventory
D. Configure the IP address from which to generate the trace
Answer should be B ?
question 23
Which task should you perform before you use the APIC-EM Path Trace tool to perform ACL analysis?
Before you begin
Make sure that you have devices in your inventory. If not, discover devices using the Discovery function.
Correct answer is C
source https://www.cisco.com/c/en/us/td/docs/cloud-systems-management/application-policy-infrastructure-controller-enterprise-module/1-6-x/path_trace/user-guide/b_Cisco_Path_Trace_User_Guide_1_6_0_x/b_Cisco_Path_Trace_User_Guide_1_6_0_x_chapter_0111.html
Confirmed, many thanks!
I just passed with high score. Thank you Admin. You are the best. Just read 300Q + Section 8
Acl1/Acl2/ Ripv2
Drag and drop just read from 300Q ( mine was first to Sixth initialization, selecting, request,renewing, bound, rebinding)
Which is section 8?, please could you help me?
This dump is valid. I passed 900+ . Many Thanks
Did the drag drops selection go from 50 or so to 30 now?
Any second thoughts on following questions:
Q 70 A and E ( See D EX and number 170 in brackets)
Q 183 B and C ( It is a 64 bit address derived from MAC address and NOT D because the universal/local bit is flipped, i. e if its 0 it becomes one and if it’s 1 it becomes 0)
Q 195 I am not sure but i have seen many alternative answers….Can someone help in this one please? ??
199 is so confusing. The B answer makes no logical sense, a new device (if they mean a brand new device) does not have a running config.
Q 204 Can someone give some more insight in this one ?
Q 233 -i have seen so many variations of answers. can someone help please?
Q198 the correct answer B or D
Some of the websites say the correct answer is D.
I see that they updated the dumps ?1
Here is a new set of questions,all from yesterday. are these from here still valid ?
https://www.dumpsbase.com/freedumps/the-current-ccna-certification-200-125-exam-dumps-updated.html
Question 307, which command should you enter to configure a DHCP Client?
I checked on cisco page (https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/ipaddr_dhcp/configuration/12-4/dhcp-12-4-book/config-dhcp-client.html#GUID-75502973-D32F-4438-A79D-7569BA87534A)
and it is
“Before You Begin
You must configure the ip dhcp client commands before entering the ip address dhcp command on an interface to ensure that the DHCPDISCOVER messages that are generated contain the correct option values. The ip dhcp client commands are checked only when an IP address is acquired from DHCP. If any of the ip dhcp client commands are entered after an IP address has been acquired from DHCP, it will not take effect until the next time the router acquires an IP address from DHCP. This means that the new configuration will take effect only after either the ip address dhcp command or the release dhcp and renew dhcpEXECcommandshave been configured.”
SUMMARY STEPS
1. enable
2. configure terminal
3. interface type number
4. ip dhcp client client-id {interface-name| ascii string| hex string}
5. ip dhcp client class-id {string| hex string}
6. ip dhcp client lease days [hours][minutes]
7. ip dhcp client hostname host-name
8. [no] ip dhcp client request option-name
9. ip address dhcp
So I dont know if should it be answer ip dhcp client (answer B) which looks like is not fully completed as an option or stays ip address dhcp (answer D) which is completed as an option.
Hello guys, are the answers are corrected please ?
I think answer for Q.209 is “network”
Explanation
In the TCP/IP model, the “Network Access Layer” is equivalent to “Physical” and “Data Link” layers in the OSI model.
Someone please verify… its little tricky answer doesn’t say Network Access Layer, instead just network and in TCP/IP model there is no network layer as its in OSI model
yub that is correct
Yes, network access
Keep it in mind that there are the Original and Modern TCP/IP Models, and the modern model is used more often today.
So, the answer D. physical is correct.
References:
1. WENDELL ODOM, CCNA 200-125 Guide, page# 84
2. http://www.ciscopress.com/articles/article.asp?p=1757634&seqNum=2
Q8 – answer should be “show ip bgp neighbors”
Explanation
The “show ip bgp neighbors” shows detailed information about EBGP peers. Below is an example of the output of this command:
BGP neighbor is 172.16.254.3, remote AS 150, internal link
1. BGP version 4, remote router ID 172.16.254.3
2. BGP state = Established, up for 19:24:07
3. Last read 00:00:06, hold time is 180, keepalive interval is 60 seconds
4. Neighbor capabilities:
5. Route refresh:advertised and received(new)
6. Address family IPv4 Unicast:advertised and received
7. Graceful Restart Capability:advertised and received
8. Remote Restart timer is 120 seconds
9. Address families preserved by peer
10. IPv4 Unicast
11. Received 4231 messages, 0 notifications, 0 in queue
12. Sent 4167 messages, 0 notifications, 0 in queue
13. Default minimum time between advertisement runs is 5 seconds
14. For address family:IPv4 Unicast
15. BGP table version 159559, neighbor version 159559
16. Index 90, Offset 11, Mask 0x4
17. Route refresh request:received 0, sent 0
18. 10031 accepted prefixes consume 441364 bytes
19. Prefix advertised 29403, suppressed 0, withdrawn 9801
20. Number of NLRIs in the update sent:max 242, min 0
21. Connections established 2; dropped 1
22. Last reset 19:26:54, due to NSF peer closed the session
23. Connection state is ESTAB, I/O status:1, unread inout bytes:0
24. Local host:150.254.254.2, Local port:11005
25. Foreign host:172.16.254.3, Foreign port:179
question 136 is not correct the correct one is A
Yes ‘A’ is correct answer
ip name-server 192.168.10.14 192.168.10.15
I think answer for 102 should be
The reported distance of 10.0.0.0/8 is 0.
Each route has only one best path.
I am confused now, answer on this site are correct??? Admin please validate your answers, we have one week when this exam will expire. I still have to write my exam, will not get second chance as it will pass exam expiry date.
Shouldn’t Question 50 be “Late Collisions” not “deferred”?
Answer is “deferred”
The deferred counter counts the number of times the interface has tried to send a frame, but found the carrier busy at the first attempt (Carrier Sense). This does not constitute a problem, and is part of normal Ethernet operation.
Note:
+ The collisions counter counts the number of frames for which one or more collisions occurred when the frames were sent.
+ When a collision is detected by a station after it has sent the 512th bit of its frame, it is counted as a late collision (and the late collision counter will increase). Possible causes are usually incorrect cabling or a non-compliant number of hubs in the network. Bad network interface cards (NICs) can also cause late collisions
Reference: https://www.cisco.com/c/en/us/support/docs/interfaces-modules/port-adapters/12768-eth-collisions.html
Answer for Q.44 is incorrect up here, please correct. There should be two correct answers for this question
44. Refer to the exhibit. If all routers on this network run RIPv2, Which configurations should you apply to router R3 to produce this routing table?
ANSWER: (two answers are correct for this question)
router rip
version 2
network 192.168.3.0
network 192.168.4.0
network 192.168.23.0
passive-interface default
router rip
version 2
network 192.168.3.0
network 192.168.4.0
network 192.168.23.0
Explanation:
From the output, we just need to notice that there are two RIP routes which are:
+ R 192.168.5.0/24 [1/0] via 192.168.4.1
and
+ R 192.168.1.0/24 [120/1] via 192.168.23.1, 00:00:09, Ethernet1/1
—(white space)—- [120/1] via 192.168.3.1, 00:00:11, Ethernet1/0
The first RIP-learned network 192.168.5.0/24 was learned via 192.168.4.1 so surely the right-side interface of R3 must run RIP -> R3 must have the command “network 192.168.4.0” under RIP process.
The second RIP-learned network 192.168.1.0/24 was learned via both R1 and R2 so surely the two interfaces of R3 that are connected to R1 and R2 must run RIP -> R3 must have the command “network 192.168.3.0” and “network 192.168.23.0” under RIP process.
Note: The command “passive-interface default” is not important here as RIP can still learn RIP-advertised routes from its neighbors.
Options are different in VCE and here, but same question and image
No, because 192.168.5.0 has a static route (is S there, not R), the answer is correct
167. You are configuring a 100-Mb fast Ethernet connection between a PC and Switch. Which action must you take to configure the speed one each of the two interfaces?
Answer for Q.167 is marked incorrect it should be “Set both interfaces to auto-negotiate”
Explanation:
We don’t know if PC or the switch support 100 Mbps connection or not so we should let them negotiate to find out the matching speed. If either of them does not support 100 Mbps, they can try to negotiate slower speed (like 10 Mbps).
Admin please check/confirm.
In 300Qs VCE this questions appear twice.
Which command should you enter to configure a single port to enter an err-disabled state when it receives an infenior BPDU?
Both with different correct answers. One is correct with “spanning-tree portfast bpduguard” and other one is with “spanning-tree guard root”
Please correct the VCE file, correct answer for this question should be “spanning-tree portfast bpduguard”
There is another very similar question:
Which command should you enter to configure a single port to disabled infenior BPDU?
Correct answer for this question is: “spanning-tree guard root”
spanning-tree portfast bpduguard err-disabled state when it receives an.
spanning-tree guard root disabled.
2. Refer to the exhibit. Which two statements about router R1 are true?
At least three IGP routing protocols are running on the router
At least two IGP routing protocols are running on the router
The router has two EIGRP neighbors and one OSPF neighbor
The router has an OSPF Area 0 adjacency with the device at 10.82.4.42
The router is learning external OSPF and EIGRP routes
The Answear should be A and E
Are you sure about this from the experience or you are just referring to some other source?
Are:
At least two IGP routing protocols are running on the router
The router is learning external OSPF and EIGRP routes
Tomorrow I have ccna test please tell me how to do vlan labs and some guide. Thank you so much
can somebody help with question 280. the answear seems to be wrong.
Which two operational modes are supported on the members of a StackWise switch stack? (Choose
two)
A. power-sharing
B. passive
C. active
D. redundant
E. standby
Correct Answer: C, E
That one through me off as well. I found that A and D are correct.
https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst3850/software/release/3se/int_hw_components/configuration_guide/b_int_3se_3850_cg/b_int_3se_3850_cg_chapter_01000.html#con_1014593
StackPower Modes
You can configure the power stack to run in one of two modes:
In power-sharing mode (the default), all input power is available to be used for power loads. The total available power in all switches in the power stack (up to four) is treated as a single large power supply, with power available to all switches and to all powered devices connected to PoE ports. In this mode, the total available power is used for power budgeting decisions and no power is reserved to accommodate power-supply failures. If a power supply fails, powered devices and switches could be shut down (load shedding).
In redundant mode, the power from the largest power supply in the system is subtracted from the power budget, which reduces the total available power, but provides backup power in case of a power-supply failure. Although there is less available power in the pool for switches and powered devices to draw from, the possibility of having to shut down switches or powered devices in case of a power failure or extreme power load is reduced.
Please tell me how to get vlans lab?
question 72 wold be Network 172.16.1.33 mask 255.255.255.224??
will take my CCNA today hope to pass
Let us know how it went
R u pass exam
20. Which feature or protocol must you enable so that the output of the show interface trunk command include information about native VLAN mismatch?
why “CDP” ?
Cisco Discovery Protocol (CDP) version 2 passes native VLAN information between Cisco switches. If you have a native VLAN mismatch, you will see CDP error messages on the console output like this:
Dec 9 14:10:21: %CDP-4-NATIVE_VLAN_MISMATCH: Native VLAN mismatch discovered on FastEthernet0/1 (1), with FastEthernet0/2 (301)
Therefore CDP can also detect native VLAN mismatch.
Reference: http://www.ciscopress.com/articles/article.asp?p=29803&seqNum=3
CDP infroms the mismatch.
” %CDP-4-NATIVE_VLAN_MISMATCH: Native VLAN mismatch discovered on ”
You can see it’s CDP messages.
Which two address spaces are valid Class B IPv4 ranges that are non-routable to the Internet? (Choose two.)
172.16.0.0 through 172.31.255.255
192.168.0.0 through 192.168.255.255
192.168.0.0/16 – C class
256. How many bits in length is a VLAN identifier?
The answer here says 16, but Cisco docs and whole internet says 12.
What are your thoughts?
https://www.cisco.com/c/en/us/support/docs/lan-switching/8021q/17056-741-4.html
In the document that you provided, it says ‘ The VLAN identifier is a tag that is encapsulated with the data. ISL and 802.1Q are two types of encapsulation that are used to carry data from multiple VLANs over trunk links’. So it refers to the whole tag, and that is 32 bits. It is an annoying trick question I think.
Has anyone had this question in the exam and was it asked this way?
Unless the question in this site is wrongly worded it is a tricky question.
TPID – Tag Protocol Identifier: 16-bit field
VID – VLAN Identifier: 12-bit field
Frame Size: The 802.1Q tag is 4 bytes (32-bit field)
I haven’t had this question as I only did ICND1 so far but I think it is a typical Cisco question. The questions often confuse people and can be interpreted in many ways. So I wouldn’t be surprised if it was asked this way.
Hi! in lab side, is possible to use help (?) and tab (autocomplete) to work with devices?
What is the correct answer of Q60? A:standby 10 priority 150 or B:standby 10 preempt… 😰
Router will be active, Preempt: before charged hsrp, priority: after charged hsrp
answer 44 is B
router rip
version 2
network 192.168.3.0
network 192.168.4.0
network 192.168.23.0
distance 50
Which two TCP messages use a 32-bit number as part of the initial TCP handshake? (Choose two.)
correct answer is ACk and SYN
thx to check that
He is right. The question is about 32 bits. ACk and SYN are 32 bits. Ack-syn is for 64 bits.
Which command should you use to display detailed information about EBGP peers?
the correct answer is show ip bgp summary
Thx to fix that
Use the show ip bgp summary command to the status of all BGP connections.
Use the show ip bgp neighbors command to display information about a peers
and all the routes received from that peer.
The question is to display information about many EBGP peers so we need to use show ip bgp summay
show ip bgp neighbors display for one peers
Confirmed!
Description: Use the show ip bgp neighbors command to display information about a peer and all the routes received from that peer.
Use the optional ip-address argument to display information about the specified neighbor. Use no ip-address argument to display information about all neighbors.
http://www.powerfast.net/bgp/BGP_Nd55.html
Hello m8s. In Question 44 (q300) is something wrong?
Thank you for your time.
There are two similar questions bouncing about. One of them has a configured distance which is easy to spot, the other one (in the 300q vce file) doesn’t make any sense to me, hope it doesn’t come up!
There is also a third variation on the web with the same topology but different answears.
A. router rip
version 2
network 192.168.3.0
network 192.168.4.0
network 192.168.23.0
passive-interface default
B. router rip
version 2
network 192.168.3.0
network 192.168.23.0
passive-interface default
C. router rip
version 2
network 192.168.3.0
network 192.168.4.0
network 192.168.23.0
D. router rip
version 2
network 192.168.3.0
network 192.168.4.0
Answer: A C
Hello
I passed the exam with 944 points all question came from Dumpsbase v 32.02 and v 33.02
And labs (my friend sent to me)
Alot of mistakes in Dumpsbase answer so I corrected it with Admin’s answer and vice versa
For configuration Labs focus on ACL, vlans and ipv6 ospf
If Admin wants dumpsbase version send my an email
OK. Congratulation! :)
Hi KingA, congratulations on your results! could you please share the dumps and labs :D !
excellent admi let us know when you update the questions, thanks KingA
What are the wrong questions? Could you tell us pls?
On question 179. “Which commands can you can enter to verify that a router is synced with a configured time source?” I would say the correct answer is E. show ntp status. The “show ntp associations” command only shows your ntp neighbors, and does not show if you are synced or not. On the other hand, show ntp status tells you if you are synchronized, which is what the question asks.