Time limit: 0
Quiz-summary
0 of 188 questions completed
Questions:
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
- 97
- 98
- 99
- 100
- 101
- 102
- 103
- 104
- 105
- 106
- 107
- 108
- 109
- 110
- 111
- 112
- 113
- 114
- 115
- 116
- 117
- 118
- 119
- 120
- 121
- 122
- 123
- 124
- 125
- 126
- 127
- 128
- 129
- 130
- 131
- 132
- 133
- 134
- 135
- 136
- 137
- 138
- 139
- 140
- 141
- 142
- 143
- 144
- 145
- 146
- 147
- 148
- 149
- 150
- 151
- 152
- 153
- 154
- 155
- 156
- 157
- 158
- 159
- 160
- 161
- 162
- 163
- 164
- 165
- 166
- 167
- 168
- 169
- 170
- 171
- 172
- 173
- 174
- 175
- 176
- 177
- 178
- 179
- 180
- 181
- 182
- 183
- 184
- 185
- 186
- 187
- 188
Information
Section II: LAN Switching Technologies - Test Online
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading...
You must sign in or sign up to start the quiz.
You have to finish following quiz, to start this quiz:
Results
0 of 188 questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 points, (0)
| Average score |
|
| Your score |
|
Categories
- Not categorized 0%
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
- 97
- 98
- 99
- 100
- 101
- 102
- 103
- 104
- 105
- 106
- 107
- 108
- 109
- 110
- 111
- 112
- 113
- 114
- 115
- 116
- 117
- 118
- 119
- 120
- 121
- 122
- 123
- 124
- 125
- 126
- 127
- 128
- 129
- 130
- 131
- 132
- 133
- 134
- 135
- 136
- 137
- 138
- 139
- 140
- 141
- 142
- 143
- 144
- 145
- 146
- 147
- 148
- 149
- 150
- 151
- 152
- 153
- 154
- 155
- 156
- 157
- 158
- 159
- 160
- 161
- 162
- 163
- 164
- 165
- 166
- 167
- 168
- 169
- 170
- 171
- 172
- 173
- 174
- 175
- 176
- 177
- 178
- 179
- 180
- 181
- 182
- 183
- 184
- 185
- 186
- 187
- 188
- Answered
- Review
-
Question 1 of 188
1. Question
1 pointsWhich statement about Cisco Discovery Protocol is true?Correct
Incorrect
-
Question 2 of 188
2. Question
1 pointsA network administrator needs to configure port security on a switch. Which two statements are true? (Choose two.)Correct
Incorrect
Hint
Follow these guidelines when configuring port security: + Port security can only be configured on static access ports, trunk ports, or 802.1Q tunnel ports. -> A is not correct. + A secure port cannot be a dynamic access port. + A secure port cannot be a destination port for Switched Port Analyzer (SPAN). + A secure port cannot belong to a Fast EtherChannel or Gigabit EtherChannel port group. -> D is not correct + You cannot configure static secure or sticky secure MAC addresses on a voice VLAN. -> B is not correct. + When you enable port security on an interface that is also configured with a voice VLAN, you must set the maximum allowed secure addresses on the port to at least two. + If any type of port security is enabled on the access VLAN, dynamic port security is automatically enabled on the voice VLAN. + When a voice VLAN is configured on a secure port that is also configured as a sticky secure port, all addresses seen on the voice VLAN are learned as dynamic secure addresses, and all addresses seen on the access VLAN (to which the port belongs) are learned as sticky secure addresses. + The switch does not support port security aging of sticky secure MAC addresses. + The protect and restrict options cannot be simultaneously enabled on an interface. (Reference: http://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst3550/software/release/12-1_19_ea1/configuration/guide/3550scg/swtrafc.html#wp1038546) Note: Dynamic access port or Dynamic port VLAN membership must be connected to an end station. This type of port can be configured with the “switchport access vlan dynamic” command in the interface configuration mode. Please read more about Dynamic access port here: http://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst3550/software/release/12-1_19_ea1/configuration/guide/3550scg/swvlan.html#wp1103064 -
Question 3 of 188
3. Question
1 pointsWhich interface counter can you use to diagnose a duplex mismatch problem?Correct
Incorrect
Hint
A late collision is defined as any collision that occurs after the first 512 bits of the frame have been transmitted. The usual possible causes are full-duplex/half-duplex mismatch, exceeded Ethernet cable length limits, or defective hardware such as incorrect cabling, non-compliant number of hubs in the network, or a bad NIC. We can check the interface counter with the “show interface” command on a Cisco device. For example: 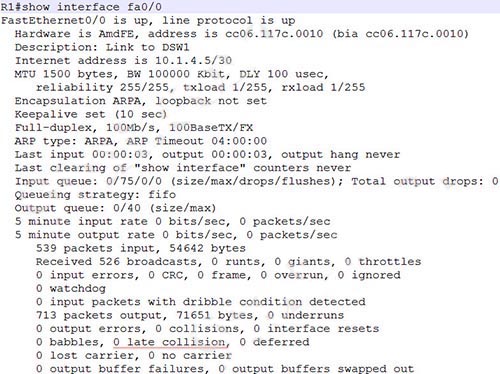 On an Ethernet connection, a duplex mismatch is a condition where two connected devices operate in different duplex modes, that is, one operates in half duplex while the other one operates in full duplex.
Note:
+ Runts are frames which do not meet the minimum frame size of 64 bytes. Runts are usually created by collisions.
+ Giants: frames that are larger than 1,518 bytes
On an Ethernet connection, a duplex mismatch is a condition where two connected devices operate in different duplex modes, that is, one operates in half duplex while the other one operates in full duplex.
Note:
+ Runts are frames which do not meet the minimum frame size of 64 bytes. Runts are usually created by collisions.
+ Giants: frames that are larger than 1,518 bytes -
Question 4 of 188
4. Question
1 pointsWhich switching method duplicates the first six bytes of a frame before making a switching decision?Correct
Incorrect
Hint
In cut-through switching, the switch copies into its memory only the destination MAC address (first six bytes of the frame) of the frame. After processing these first six bytes, the switch had enough information to make a forwarding decision and move the frame to the appropriate switchport. This switching method is faster than store-and-forward switching method. In store-and-forward switching, the switch copies each complete Ethernet frame into the switch memory and computes a Cyclic Redundancy Check (CRC) for errors. If a CRC error is found, the Ethernet frame is dropped. If no CRC error is found then that frame is forwarded. -
Question 5 of 188
5. Question
1 pointsWhich command can you enter to determine whether a switch is operating in trunking mode?Correct
Incorrect
Hint
Below is an example of the output of this command. Interface Ethernet1/0 is operating in trunking mode.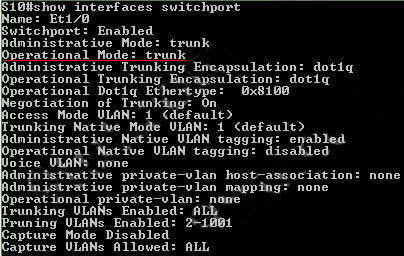
-
Question 6 of 188
6. Question
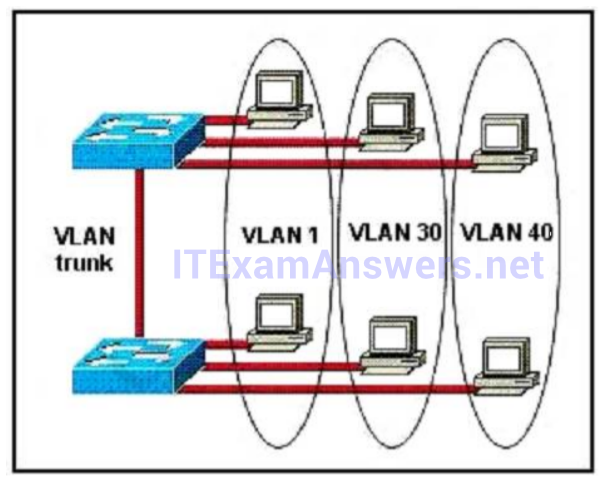
1 pointsWhat are three benefits of implementing VLANs? (Choose three.)Correct
Incorrect
-
Question 7 of 188
7. Question
1 pointsWhich command can you enter to view the ports that are assigned to VLAN 20?Correct
Incorrect
-
Question 8 of 188
8. Question
1 pointsWhen an interface is configured with PortFast BPDU guard, how does the interface respond when it receives a BPDU?Correct
Incorrect
Hint
PortFast BPDU guard prevents loops by moving a nontrunking port into an errdisable state when a BPDU is received on that port. When you enable BPDU guard on the switch, spanning tree shuts down PortFast-configured interfaces that receive BPDUs instead of putting them into the spanning tree blocking state. In a valid configuration, PortFast-configured interfaces do not receive BPDUs (because PortFast should only be configured on interfaces which are connected to hosts). If a PortFast-configured interface receives a BPDU, an invalid configuration exists. BPDU guard provides a secure response to invalid configurations because the administrator must manually put the interface back in service. Reference: http://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst4000/8-2glx/configuration/guide/stp_enha.html -
Question 9 of 188
9. Question
1 pointsWhat are three advantages of VLANs? (Choose three.)Correct
Incorrect
-
Question 10 of 188
10. Question
1 pointsRefer to the exhibit.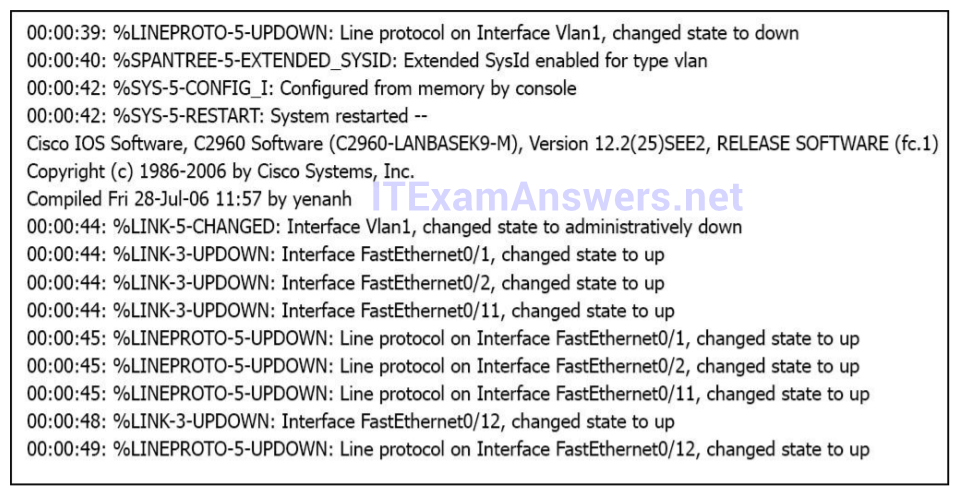 Which of these statements correctly describes the state of the switch once the boot process has been completed? Correct
Which of these statements correctly describes the state of the switch once the boot process has been completed? Correct
Incorrect
Hint
From the output we notice that the administrator has just shut down Interface Vlan1, which is the default VLAN so no one can access it remotely (like telnet) -> B is correct. Answer A is not correct as STP calculation does not depend on which port comes up first or last. STP recalculates when there is a change in the network. A normal switch can operate without VLAN -> C is not correct. This IOS does support VLAN because it has VLAN 1 on it -> D is not correct. -
Question 11 of 188
11. Question
1 pointsWhich condition does the err-disabled status indicate on an Ethernet interface?Correct
Incorrect
Hint
There are various reasons for the interface to go into errdisable. The reason can be: + Duplex mismatch + Port channel misconfiguration + BPDU guard violation + UniDirectional Link Detection (UDLD) condition + Late-collision detection + Link-flap detection + Security violation + Port Aggregation Protocol (PAgP) flap + Layer 2 Tunneling Protocol (L2TP) guard + DHCP snooping rate-limit + Incorrect GBIC / Small Form-Factor Pluggable (SFP) module or cable + Address Resolution Protocol (ARP) inspection + Inline power Reference: http://www.cisco.com/c/en/us/support/docs/lan-switching/spanning-tree-protocol/69980-errdisable-recovery.html Therefore in fact there are two correct answers in this question, which are “There is a duplex mismatch” and “Port security has disabled the interface” but maybe you should choose the port security answer as it is the most popular reason. -
Question 12 of 188
12. Question
1 pointsWhich statement about LLDP is true?Correct
Incorrect
Hint
Link Layer Discovery Protocol (LLDP) is a industry standard protocol that allows devices to advertise, and discover connected devices, and there capabilities (same as CDP of Cisco). To enable it on Cisco devices, we have to use this command under global configuration mode: Sw(config)# lldp run -
Question 13 of 188
13. Question
1 pointsIf the primary root bridge experiences a power loss, which switch takes over?Correct
Incorrect
Hint
The switches compare their Bridge ID with each other to find out who will be the root bridge. The root bridge is the bridge with the lowest bridge ID. Bridge ID = Bridge Priority + MAC Address In this question the bridge priority was not mentioned so we suppose they are the same. Therefore the switch with lowest MAC address will become the new root bridge. -
Question 14 of 188
14. Question
1 pointsRefer to the exhibit.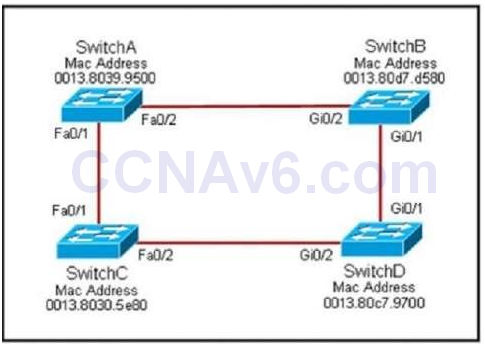 Each of these four switches has been configured with a hostname, as well as being configured to run RSTP.No other configuration changes have been made. Which three of these show the correct RSTP port roles for the indicated switches and interfaces? (Choose three.) Correct
Each of these four switches has been configured with a hostname, as well as being configured to run RSTP.No other configuration changes have been made. Which three of these show the correct RSTP port roles for the indicated switches and interfaces? (Choose three.) Correct
Incorrect
Hint
The question says “no other configuration changes have been made” so we can understand these switches have the same bridge priority. Switch C has lowest MAC address so it will become root bridge and 2 of its ports (Fa0/1 & Fa0/2) will be designated ports -> E is incorrect. Because SwitchC is the root bridge so the 2 ports nearest SwitchC on SwitchA (Fa0/1) and SwitchD (Gi0/2) will be root ports -> B and F are correct. Now we come to the most difficult part of this question: SwitchB must have a root port so which port will it choose? To answer this question we need to know about STP cost and port cost. In general, “cost” is calculated based on bandwidth of the link. The higher the bandwidth on a link, the lower the value of its cost. Below are the cost values you should memorize: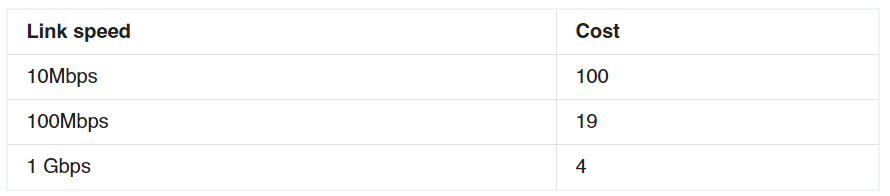 SwitchB will choose the interface with lower cost to the root bridge as the root port so we must calculate the cost on interface Gi0/1 & Gi0/2 of SwitchB to the root bridge. This can be calculated from the “cost to the root bridge” of each switch because a switch always advertises its cost to the root bridge in its BPDU. The receiving switch will add its local port cost value to the cost in the BPDU.
In the exhibit you also we FastEthernet port is connecting to GigabitEthernet port. In this case GigabitEthernet port will operate as a FastEthernet port so the link can be considered as FastEthernet to FastEthernet connection.
One more thing to notice is that a root bridge always advertises the cost to the root bridge (itself) with an initial value of 0.
Now let’s have a look at the topology again
SwitchB will choose the interface with lower cost to the root bridge as the root port so we must calculate the cost on interface Gi0/1 & Gi0/2 of SwitchB to the root bridge. This can be calculated from the “cost to the root bridge” of each switch because a switch always advertises its cost to the root bridge in its BPDU. The receiving switch will add its local port cost value to the cost in the BPDU.
In the exhibit you also we FastEthernet port is connecting to GigabitEthernet port. In this case GigabitEthernet port will operate as a FastEthernet port so the link can be considered as FastEthernet to FastEthernet connection.
One more thing to notice is that a root bridge always advertises the cost to the root bridge (itself) with an initial value of 0.
Now let’s have a look at the topology again
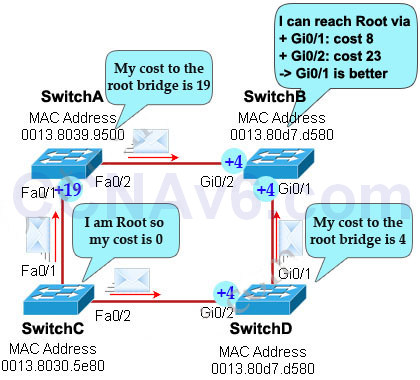 SwitchC advertises its cost to the root bridge with a value of 0. Switch D adds 19 (the cost value of 100Mbps link although the port on Switch D is GigabitEthernet port) and advertises this value (19) to SwitchB. SwitchB adds 4 (the cost value of 1Gbps link) and learns that it can reach SwitchC via Gi0/1 port with a total cost of 23. The same process happens for SwitchA and SwitchB learns that it can reach SwitchC via Gi0/2 with a total cost of 38 -> Switch B chooses Gi0/1 as its root port -> D is not correct.
Now our last task is to identify the port roles of the ports between SwitchA & SwitchB. It is rather easy as the MAC address of SwitchA is lower than that of SwitchB so Fa0/2 of SwitchA will be designated port while Gi0/2 of SwitchB will be alternative port -> A is correct but C is not correct.
Below summaries all the port roles of these switches:
SwitchC advertises its cost to the root bridge with a value of 0. Switch D adds 19 (the cost value of 100Mbps link although the port on Switch D is GigabitEthernet port) and advertises this value (19) to SwitchB. SwitchB adds 4 (the cost value of 1Gbps link) and learns that it can reach SwitchC via Gi0/1 port with a total cost of 23. The same process happens for SwitchA and SwitchB learns that it can reach SwitchC via Gi0/2 with a total cost of 38 -> Switch B chooses Gi0/1 as its root port -> D is not correct.
Now our last task is to identify the port roles of the ports between SwitchA & SwitchB. It is rather easy as the MAC address of SwitchA is lower than that of SwitchB so Fa0/2 of SwitchA will be designated port while Gi0/2 of SwitchB will be alternative port -> A is correct but C is not correct.
Below summaries all the port roles of these switches:
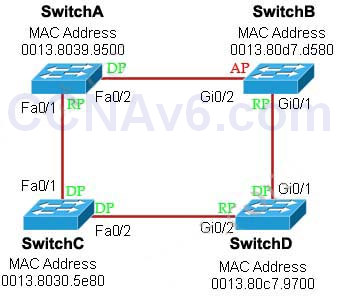 + DP: Designated Port (forwarding state)
+ RP: Root Port (forwarding state)
+ AP: Alternative Port (blocking state)
+ DP: Designated Port (forwarding state)
+ RP: Root Port (forwarding state)
+ AP: Alternative Port (blocking state) -
Question 15 of 188
15. Question
1 pointsWhich feature builds a FIB and an adjacency table to expedite packet forwarding?Correct
Incorrect
Hint
Cisco Express Forwarding (CEF) provides the ability to switch packets through a device in a very quick and efficient way while also keeping the load on the router’s processor low. CEF is made up of two different main components: the Forwarding Information Base (FIB) and the Adjacency Table. These are automatically updated at the same time as the routing table. The Forwarding Information Base (FIB) contains destination reachability information as well as next hop information. This information is then used by the router to make forwarding decisions. The FIB allows for very efficient and easy lookups. The adjacency table is tasked with maintaining the layer 2 next-hop information for the FIB. -
Question 16 of 188
16. Question
1 pointsWhat are two reasons that duplex mismatches can be difficult to diagnose? (Choose two.)Correct
Incorrect
-
Question 17 of 188
17. Question
1 pointsWhich command would you configure globally on a Cisco router that would allow you to view directly connected Cisco devices?Correct
Incorrect
Hint
CDP is enabled by default on all Cisco routers. If it is turned off by any reason, we can turn it on again with the following command on global configuration mode: Router(config)#cdp run Note: CDP can be turned on or turned off on each interface. For example to turn off CDP on an interface we use this command: Router(config-if)#no cdp enable -
Question 18 of 188
18. Question
1 pointsIf all switches are configured with default values, which switch will take over when the primary root bridge experiences a power loss?Correct
Incorrect
-
Question 19 of 188
19. Question
1 pointsWhich two protocols can detect native VLAN mismatch errors? (Choose two.)Correct
Incorrect
-
Question 20 of 188
20. Question
1 pointsWhich DTP switch port mode allows the port to create a trunk link if the neighboring port is in trunk mode, dynamic desirable mode, or desirable auto mode?Correct
Incorrect
Hint
The Dynamic Trunking Protocol (DTP) is a proprietary networking protocol developed by Cisco for the purpose of negotiating trunking on a link between two switches, and for negotiating the type of trunking encapsulation to be used. In dynamic auto mode, the interface is able to convert the link to a trunk link. The interface becomes a trunk interface if the neighboring interface is set to trunk or desirable mode. The default switchport mode for newer Cisco switch Ethernet interfaces is dynamic auto. Note that if two Cisco switches are left to the common default setting of auto, a trunk will never form. In dynamic desirable mode, the interface actively attempt to convert the link to a trunk link. The interface becomes a trunk interface if the neighboring interface is set to trunk, desirable, or auto mode. This is the default switchport mode on older switches, such as the Catalyst 2950 and 3550 Series switches -> This is the best answer in this question. Reference: http://www.ciscopress.com/articles/article.asp?p=2181837&seqNum=8 -
Question 21 of 188
21. Question
1 pointsWhich DTP switch port mode allows the port to create a trunk link if the neighboring port is in trunk mode, dynamic desirable mode, or desirable or auto mode?Correct
Incorrect
-
Question 22 of 188
22. Question
1 pointsWhich three statements about DWDM are true? (Choose three)Correct
Incorrect
Hint
A newer fiber-optic media development for long-range communications is called dense wavelength-division multiplexing (DWDM). DWDM multiplies the amount of bandwidth that a single strand of fiber can support. DWDM circuits are used in all modern submarine communications cable systems and other long-haul circuits. Specifically, DWDM: + Enables bidirectional communications over one strand of fiber -> Answer A is correct + Assigns incoming optical signals to specific wavelengths of light (i.e., frequencies) + Each channel is capable of carrying a 10-Gbps multiplexed signal -> Answer E is not correct + Can multiplex more than 80 different channels of data (i.e., wavelengths) onto a single fiber -> Answer C is not correct + Can amplify these wavelengths to boost the signal strength + Supports SONET and SDH standards Reference: http://www.ciscopress.com/articles/article.asp?p=2202411&seqNum=6 -
Question 23 of 188
23. Question
1 pointsWhich three statements about DTP are true? (Choose three.)Correct
Incorrect
-
Question 24 of 188
24. Question
1 pointsWhich three commands must you enter to create a trunk that allows VLAN 20? (Choose three.)Correct
Incorrect
-
Question 25 of 188
25. Question
1 pointsWhich feature facilitates the tagging of frames on a specific VLAN?Correct
Incorrect
-
Question 26 of 188
26. Question
1 pointsWhich statement about spanning-tree root-bridge election is true?Correct
Incorrect
Hint
Answer A is not correct as we can choose which switch to become root bridge by configuring bridge priority. The switch with lowest bridge priority (value) would become the root bridge. For answer B, this paragraph from Cisco confirms it is the correct answer: “When you implement a root bridge in a switching network, you usually refer to the root bridge as the root switch. Each VLAN must have its own root bridge because each VLAN is a separate broadcast domain. The roots for the different VLANs can all reside in a single switch or in various switches.” Reference: https://www.cisco.com/c/en/us/support/docs/lan-switching/spanning-tree-protocol/5234-5.html The meaning of answer C is not clear but maybe it means “every VLAN must use the same root bridge” which is not correct as Sw1 can be the root bridge for VLANs 1, 3, 5 but Sw2 can be the root bridge for VLAN 2, 4, 6… From the quote above we can say answer D is not correct. -
Question 27 of 188
27. Question
1 pointsWhich two statements about data VLANs on access ports are true? ( Choose two)Correct
Incorrect
-
Question 28 of 188
28. Question
1 pointsWhich three options are switchport configurations that can always avoid duplex mismatch errors between two switches? (Choose three.)Correct
Incorrect
Hint
http://www.pathsolutions.com/network-enemy-1-duplex-mismatch/ -
Question 29 of 188
29. Question
1 pointsUnder normal operations, cisco recommends that you configure switch ports on which vlan?Correct
Incorrect
Hint
http://www.cisco.com/c/en/us/support/docs/switches/catalyst-6500-series-switches/24330-185.html Note: There is a potential security consideration with dot1q that the implicit tagging of the native VLAN causes. The transmission of frames from one VLAN to another without a router can be possible. Refer to the Intrusion Detection FAQ leavingcisco.com for further details. The workaround is to use a VLAN ID for the native VLAN of the trunk that is not used for end-user access. In order to achieve this, the majority of Cisco customers simply leave VLAN 1 as the native VLAN on a trunk and assign access ports to VLANs other than VLAN 1. -
Question 30 of 188
30. Question
1 pointsWhich statement about VLAN operation on Cisco Catalyst switches is true?Correct
Incorrect
Hint
Each VLAN resides in its own broadcast domain, so incoming frames with unknown destinations are only transmitted to ports that reside in the same VLAN as the incoming frame. -
Question 31 of 188
31. Question
1 pointsWhich two options describe benefits of aggregated chassis technology (choose two)?Correct
Incorrect
Hint
Chassis aggregation is a Cisco technology to make multiple switches operate as a single switch. It is similar to stacking but meant for powerful switches (like the 6500 and 6800 series switches). Chassis aggregation is often used in the core layer and distribution layer (while switching stacking is used for access layer). The books do not mention about the benefits of chassis aggregation but they are the same as switch stacking. + The stack would have a single management IP address. + The engineer would connect with Telnet or SSH to one switch (with that one management IP address), not multiple switches. + One configuration file would include all interfaces in all physical switches. + STP, CDP, VTP would run on one switch, not multiple switches. + The switch ports would appear as if all are on the same switch. + There would be one MAC address table, and it would reference all ports on all physical switches. Reference: CCNA Routing and Switching ICND2 200-105 Official Cert Guide VSS is a chassis aggregation technology but it is dedicated for Cisco Catalyst 6500 Series Switches. VSS increases operational efficiency by simplifying the network, reducing switch management overhead by at least 50 percent -> A is correct Single point of management, IP address, and routing instance for the Cisco Catalyst 6500 virtual switch + Single configuration file and node to manage. Removes the need to configure redundant switches twice with identical policies. + Only one gateway IP address is required per VLAN, instead of the three IP addresses per VLAN used today -> C is correct while D is not correct. + Removes the need for Hot Standby Router Protocol (HSRP), Virtual Router Redundancy Protocol (VRRP), and Gateway Load Balancing Protocol (GLBP)-> so maybe E is not correct. Reference: http://www.cisco.com/c/en/us/products/collateral/switches/catalyst-6500-virtual-switching-system-1440/prod_qas0900aecd806ed74b.html -
Question 32 of 188
32. Question
1 pointsRefer to the exhibit. Which switch provides the spanning-tree designated port role for the network segment that services the printers?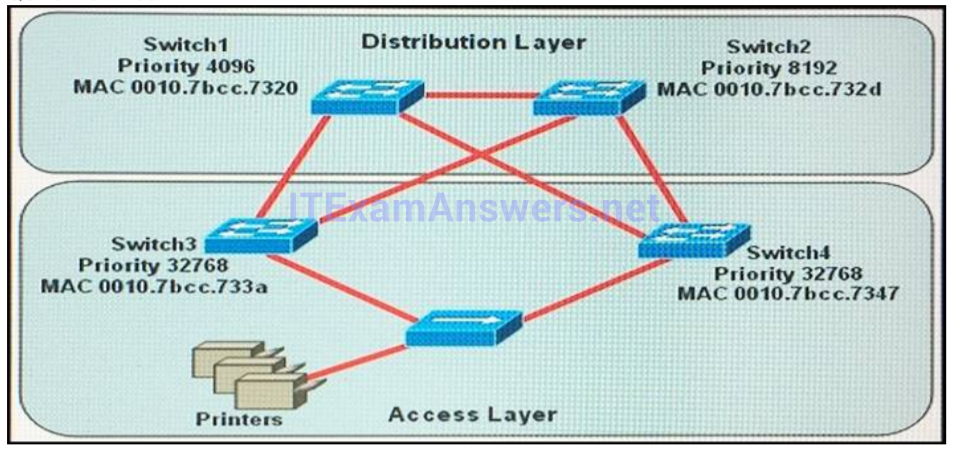 Correct
Correct
Incorrect
Hint
First, the question asks what switch services the printers, so it can be Switch 3 or Switch 4 which is connected directly to the Printers. Next, by comparing the MAC address of Switch 3 and Switch 4 we found that the MAC of Switch 3 is smaller. Therefore the interface connected to the Printers of Switch 3 will become designated interface and the interface of Switch 4 will be blocked. The picture below shows the roles of all ports: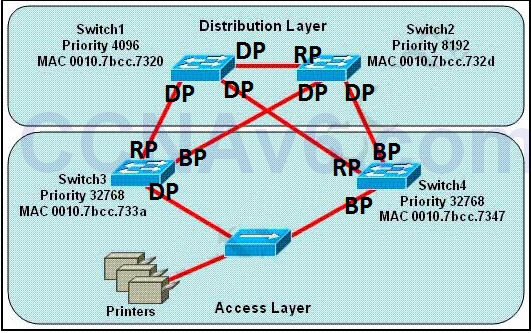 DP: Designated Port
RP: Root Port
BP: Blocked Port
(Please notice that Switch 1 will become the root bridge because of its lowest priority, not Switch 3)
DP: Designated Port
RP: Root Port
BP: Blocked Port
(Please notice that Switch 1 will become the root bridge because of its lowest priority, not Switch 3) -
Question 33 of 188
33. Question
1 pointsWhich type of MAC address is aged automatically by the switch?Correct
Incorrect
-
Question 34 of 188
34. Question
1 pointsFor what two purposes does the Ethernet protocol use physical addresses? (Choose two.)Correct
Incorrect
Hint
Physical addresses or MAC addresses are used to identify devices at layer 2 -> A is correct. MAC addresses are only used to communicate on the same network. To communicate on different network we have to use Layer 3 addresses (IP addresses) -> B is not correct; E is correct. Layer 2 frame and Layer 3 packet can be recognized via headers. Layer 3 packet also contains physical address -> C is not correct. On Ethernet, each frame has the same priority to transmit by default -> D is not correct. All devices need a physical address to identify itself. If not, they can not communicate -> F is not correct. -
Question 35 of 188
35. Question
1 pointsWhen you enable PortFast on a switch port, the port immediately transitions to which state?Correct
Incorrect
Hint
PortFast causes a switch or trunk port to enter the spanning tree forwarding state immediately, bypassing the listening and learning states. You can use PortFast on switch or trunk ports that are connected to a single workstation, switch, or server to allow those devices to connect to the network immediately, instead of waiting for the port to transition from the listening and learning states to the forwarding state. -
Question 36 of 188
36. Question
1 pointsWhich two EtherChannel PAgP modes can you configure? (Choose two.)Correct
Incorrect
-
Question 37 of 188
37. Question
1 pointsWhich command sequence can you enter to create VLAN 20 and assign it to an interface on a switch?Correct
Incorrect
-
Question 38 of 188
38. Question
1 pointsWhich two statements about late collisions are true? (Choose two.)Correct
Incorrect
Hint
A late collision is defined as any collision that occurs after the first 512 bits of the frame have been transmitted. The usual possible causes are full-duplex/half-duplex mismatch, exceeded Ethernet cable length limits, or defective hardware such as incorrect cabling, non-compliant number of hubs in the network, or a bad NIC. Note: On an Ethernet connection, a duplex mismatch is a condition where two connected devices operate in different duplex modes, that is, one operates in half duplex while the other one operates in full duplex. -
Question 39 of 188
39. Question
1 pointsWhich command can you enter to re-enable Cisco Discovery Protocol on a local router after it has been disabled?Correct
Incorrect
-
Question 40 of 188
40. Question
1 pointsRefer to the exhibit. The output that is shown is generated at a switch. Which three of these statements are true? (Choose three.)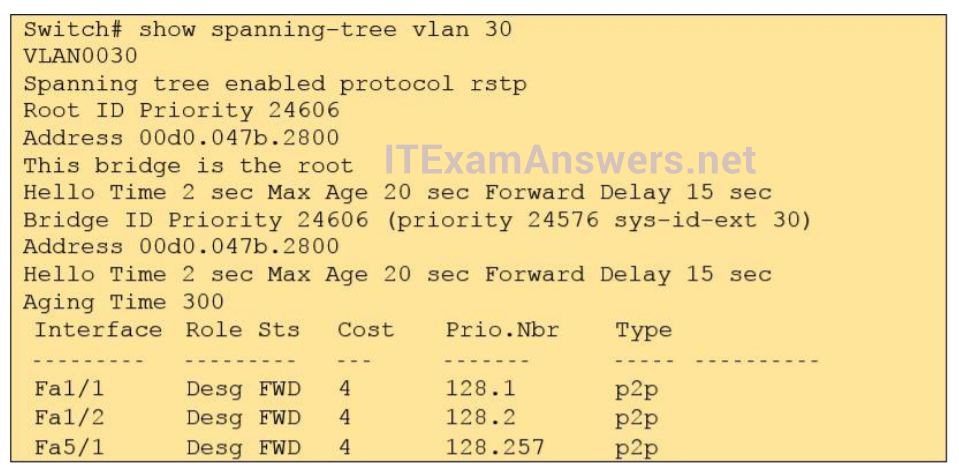 Correct
Correct
Incorrect
Hint
From the output, we see that all ports are in Designated role (forwarding state) -> A and E are correct. The command “show spanning-tree vlan 30″ only shows us information about VLAN 30. We don’t know how many VLAN exists in this switch -> B is not correct. The bridge priority of this switch is 24606 which is lower than the default value bridge priority 32768 -> C is correct. All three interfaces on this switch have the connection type “p2p”, which means Point-to-point environment – not a shared media -> D is not correct. The only thing we can specify is this switch is the root bridge for VLAN 30 but we can not guarantee it is also the root bridge for other VLANs -> F is not correct. -
Question 41 of 188
41. Question
1 pointsWhich two commands can be used to verify a trunk link configuration status on a given Cisco switch interface? (Choose two.)Correct
Incorrect
Hint
The “show interfaces trunk” command and “show interfaces switchport” command can be used to verify the status of an interface (trunking or not). The outputs of these commands are shown below (port Ethernet 1/0 has been configured as trunk):
 The “show ip interface brief” command only gives us information about the IP address, the status (up/down) of an interface:
The “show ip interface brief” command only gives us information about the IP address, the status (up/down) of an interface:
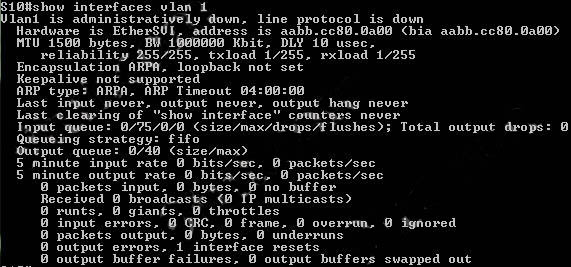
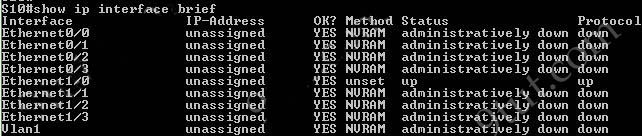 The “show interfaces vlan” command only gives us information about that VLAN, not about which ports are the trunk links:
The “show interfaces vlan” command only gives us information about that VLAN, not about which ports are the trunk links:
-
Question 42 of 188
42. Question
1 pointsWhich two states are the port states when RSTP has converged? (Choose two.)Correct
Incorrect
Hint
RSTP only has 3 port states that are discarding, learning and forwarding. When RSTP has converged there are only 2 port states left: discarding and forwarding. -
Question 43 of 188
43. Question
1 pointsRefer to the exhibit. A technician has installed SwithchB and needs to configure it for remote access from the management workstation connected SwitchA. Which set of commands is required to accomplish this task?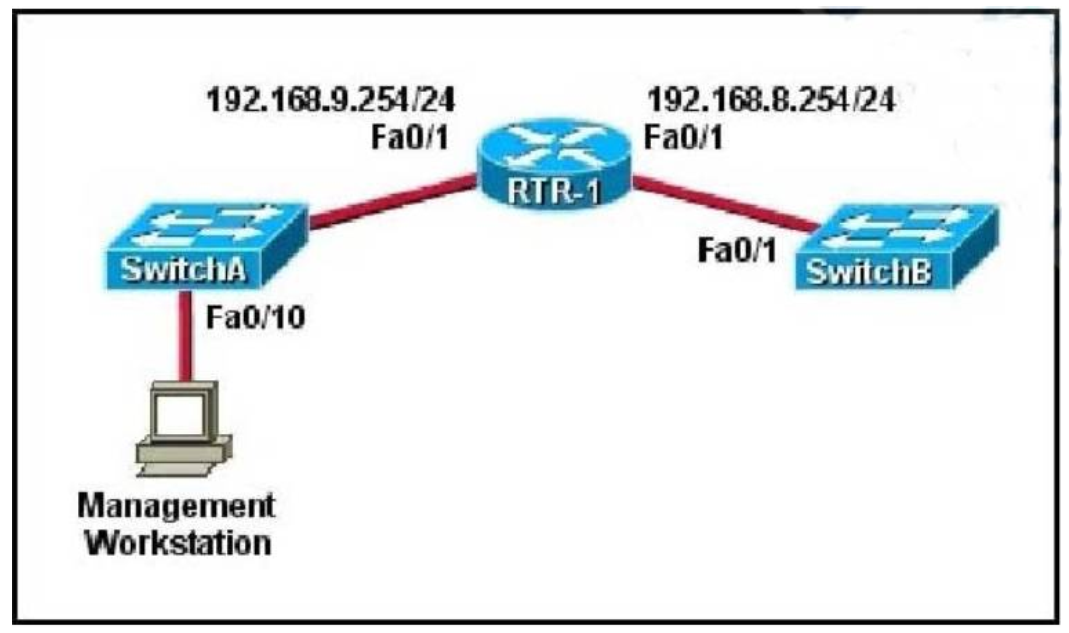 Correct
Correct
Incorrect
-
Question 44 of 188
44. Question
1 pointsA technician has installed SwitchB and needs to configure it for remote access from the management workstation connected SwitchA. Which set of commands is required to accomplish this task?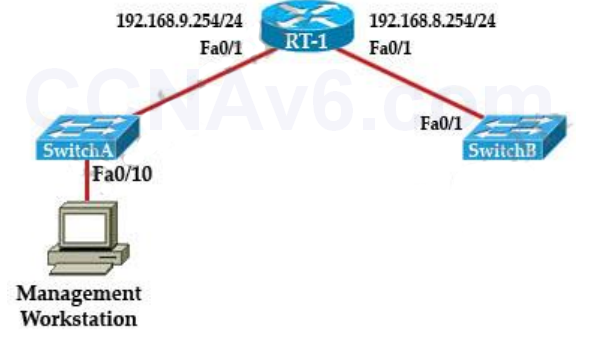 Correct
Correct
Incorrect
Hint
To remote access to SwitchB, it must have a management IP address on a VLAN on that switch. Traditionally, we often use VLAN 1 as the management VLAN (but in fact it is not secure). In the exhibit, we can recognize that the Management Workstation is in a different subnet from the SwitchB. For intersubnetwork communication to occur, you must configure at least one default gateway. This default gateway is used to forward traffic originating from the switch only, not to forward traffic sent by devices connected to the switch. -
Question 45 of 188
45. Question
1 pointsWhich of the following are benefits of VLANs? (Choose three.)Correct
Incorrect
Hint
When using VLAN the number and size of collision domains remain the same -> A is not correct. VLANs allow to group users by function, not by location or geography -> B is correct. VLANs help minimize the incorrect configuration of VLANs so it enhances the security of the network -> C is correct. VLAN increases the size of broadcast domains but does not decrease the number of collision domains -> D is not correct. VLANs increase the number of broadcast domains while decreasing the size of the broadcast domains which increase the utilization of the links. It is also a big advantage of VLAN -> E is correct. VLANs are useful but they are more complex and need more administration -> F is not correct. -
Question 46 of 188
46. Question
1 pointsWhich three statements accurately describe Layer 2 Ethernet switches? (Choose three.)Correct
Incorrect
Hint
Microsegmentation is a network design (functionality) where each workstation or device on a network gets its own dedicated segment (collision domain) to the switch. Each network device gets the full bandwidth of the segment and does not have to share the segment with other devices. Microsegmentation reduces and can even eliminate collisions because each segment is its own collision domain Note: Microsegmentation decreases the number of collisions but it increases the number of collision domains. -
Question 47 of 188
47. Question
1 pointsWhat is the status of port-channel if LACP is misconfigured?Correct
Incorrect
Hint
EtherChannel misconfiguration occurs when the channel parameters do not match on both sides of the EtherChannel, resulting in the following message: %PM-SP-4-ERR_DISABLE: channel-misconfig error detected on Po3, putting E1/3 in err-disable state Therefore from the output above we can see that when miconfigured, the physical (member) interface is put into err-disable state. But this question asks above “the status of port-channel” (not the physical member interface) so answer “Disabled” is a better choice. -
Question 48 of 188
48. Question
1 pointsHow to create a trunk port and allow VLAN 20? (Choose Three.)Correct
Incorrect
Hint
In switches that support both InterSwitch Link (ISL) and 802.1Q trunking encapsulations, we need to specify an trunking protocol so we must use the command “switchport trunk encapsulation dot1q” command first to set the trunk mode to 802.1Q. Then we configure trunking interface with the “switchport mode trunk” command. Then we explicitly allow vlan 20 with the command “switchport trunk allowed vlan 20” command. By default all VLANs are allowed to pass but after entering this command, only VLAN 20 is allowed. -
Question 49 of 188
49. Question
1 pointsWhich mode is compatible with Trunk, Access, and desirable ports?Correct
Incorrect
Hint
Explanation from http://www.9tut.com/trunking-questions Maybe this question wanted to ask “if the other end is configured with trunk/access/desirable mode” then which mode is compatible so that the link can work. In that case both “dynamic auto” and “dynamic desirable” mode are correct. The difference between these two modes is “dynamic auto” is passively waiting for the other end to request to form a trunk while “dynamic desirable” will actively attempt to negotiate to convert the link into a trunk. -
Question 50 of 188
50. Question
1 pointsWhat parameter can be different on ports within an EtherChannel?Correct
Incorrect
Hint
All interfaces in an EtherChannel must be configured identically to form an EtherChannel. Specific settings that must be identical include: + Speed settings + Duplex settings + STP settings + VLAN membership (for access ports) + Native VLAN (for trunk ports) + Allowed VLANs (for trunk ports) + Trunking Encapsulation (ISL or 802.1Q, for trunk ports) -
Question 51 of 188
51. Question
1 pointsWhich spanning-tree protocol rides on top of another spanning-tree protocol?Correct
Incorrect
Hint
Multiple Spanning Tree (MST) rides on top of RSTP so it converges very fast. The idea behind MST is that some VLANs can be mapped to a single spanning tree instance because most networks do not need more than a few logical topologies. -
Question 52 of 188
52. Question
1 pointsWhich three statements about RSTP are true? (Choose three.)Correct
Incorrect
-
Question 53 of 188
53. Question
1 pointsWhich two commands correctly verify whether port security has been configured on port FastEthernet 0/12 on a switch? (Choose two.)Correct
Incorrect
Hint
We can verify whether port security has been configured by using the “show running-config” or “show port-security interface ” for more detail. An example of the output of “show port-security interface ” command is shown below:
-
Question 54 of 188
54. Question
1 pointsRefer to the exhibit. Switch port FastEthernet 0/24 on ALSwitch1 will be used to create an IEEE 802.1Q-compliant trunk to another switch. Based on the output shown, what is the reason the trunk does not form, even though the proper cabling has been attached?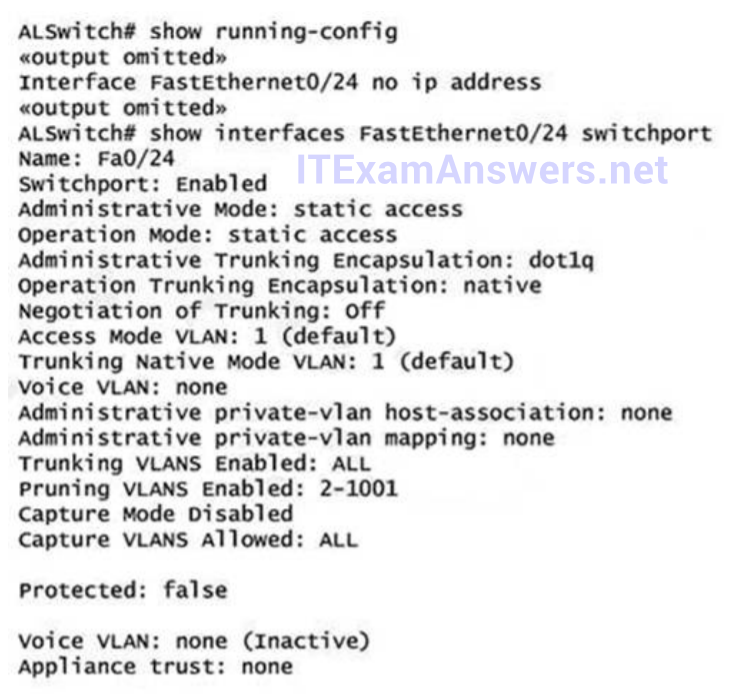 Correct
Correct
Incorrect
Hint
According to the output shown the switchport (layer 2 Switching) is enabled and the port is in access mode. To make a trunk link the port should configured as a trunk port, not an access port, by using the following command: (Config-if)#switchport mode trunk -
Question 55 of 188
55. Question
1 pointsRefer to the exhibit. Switch-1 needs to send data to a host with a MAC address of 00b0.d056.efa4. What will Switch-1 do with this data?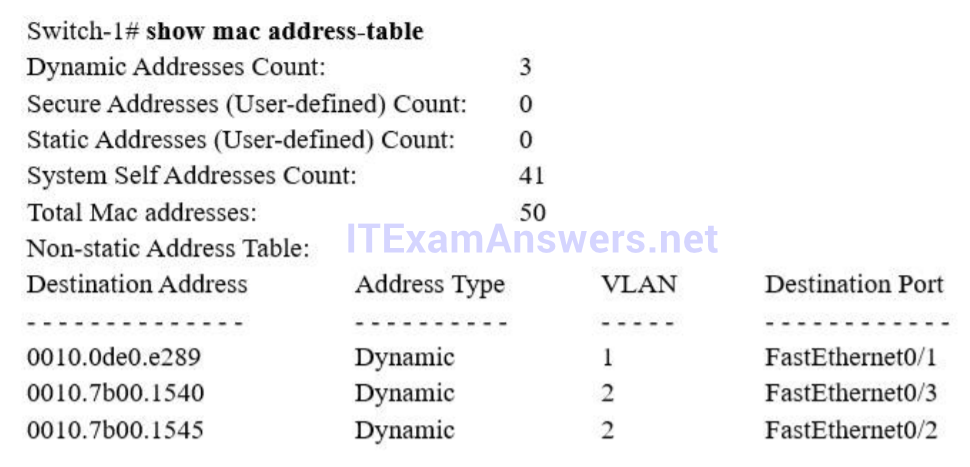 Correct
Correct
Incorrect
Hint
The MAC address of 00b0.d056.efa4 has not been learned in its MAC address table so Switch-1 will broadcast the frame out all of its ports except the port from which the data originated. -
Question 56 of 188
56. Question
1 pointsStandard industrialized protocol of etherchannel?Correct
Incorrect
-
Question 57 of 188
57. Question
1 pointsHow to enable vlans automatically across multiple switches?Correct
Incorrect
-
Question 58 of 188
58. Question
1 pointsWhat are contained in layer 2 ethernet frame? (Choose Three.)Correct
Incorrect
Hint
At the end of each frame there is a Frame Check Sequence (FCS) field. FCS can be analyzed to determine if errors have occurred. FCS uses cyclic redundancy check (CRC) algorithm to detect errors in the transmitted frames. Before sending data, the sending host generates a CRC based on the header and data of that frame. When this frame arrives, the receiving host uses the same algorithm to generate its own CRC and compare them. If they do not match then a CRC error will occur.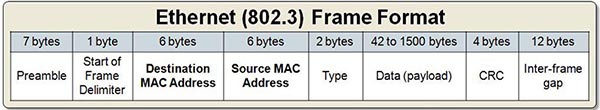 Preamble is used to indicate the start of the frame by arranging the first 62 bits as alternating “1/0s” and the last two bits as “1”s. Like so, 010101010101010………………………10101011. Therefore when the receiving end sees the “11” it knows where the actual Ethernet header starts. The alternating 1s and 0s will also allow the two endpoints to sync their internal clocks. In summary, preamble is used for synchronization.
The “Type/Length” field is used to indicate the “Type”of the payload (Layer 3 protocol) which is indicated as a Hexadecimal value.
Note: Ethernet II uses “Type” while the old Ethernet version use “Length”
Preamble is used to indicate the start of the frame by arranging the first 62 bits as alternating “1/0s” and the last two bits as “1”s. Like so, 010101010101010………………………10101011. Therefore when the receiving end sees the “11” it knows where the actual Ethernet header starts. The alternating 1s and 0s will also allow the two endpoints to sync their internal clocks. In summary, preamble is used for synchronization.
The “Type/Length” field is used to indicate the “Type”of the payload (Layer 3 protocol) which is indicated as a Hexadecimal value.
Note: Ethernet II uses “Type” while the old Ethernet version use “Length” -
Question 59 of 188
59. Question
1 pointsWhich two of these are characteristics of the 802.1Q protocol? (Choose two.)Correct
Incorrect
Hint
IEEE 802.1Q is the networking standard that supports Virtual LANs (VLANs) on an Ethernet network. It is a protocol that allows VLANs to communicate with one another using a router. 802.1Q trunks support tagged and untagged frames. If a switch receives untagged frames on a trunk port, it believes that frame is a part of the native VLAN. Also, frames from a native VLAN are not tagged when exiting the switch via a trunk port. The 802.1q frame format is same as 802.3. The only change is the addition of 4 bytes fields. That additional header includes a field with which to identify the VLAN number. Because inserting this header changes the frame, 802.1Q encapsulation forces a recalculation of the original FCS field in the Ethernet trailer. Note: Frame Check Sequence (FCS) is a four-octet field used to verify that the frame was received without loss or error. FCS is based on the contents of the entire frame. -
Question 60 of 188
60. Question
1 pointsWhich command is used to know the duplex speed of serial link?Correct
Incorrect
Hint
Nowadays all serial links are full-duplex (as serial interfaces have separate Rx & Tx pins) so maybe this question wants to ask about how to check the speed of the serial link. The “show interface” command gives us information about this. An example of this command is shown below: In this output the speed of S0/0 interface is 1544 Kbits.
In this output the speed of S0/0 interface is 1544 Kbits. -
Question 61 of 188
61. Question
1 pointsA BPDU guard is configured on an interface that has PortFast enabled. Which state does the interface enter when it receives a BPDU?Correct
Incorrect
Hint
PortFast BPDU guard prevents loops by moving a nontrunking port into an errdisable state when a BPDU is received on that port.In a valid configuration, PortFast-configured interfaces do not receive BPDUs (because PortFast should only be configured on interfaces which are connected to hosts). If a PortFast-configured interface receives a BPDU, an invalid configuration exists. BPDU guard provides a secure response to invalid configurations because the administrator must manually put the interface back in service.Reference: http://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst4000/8-2glx/configuration/guide/stp_enha.html -
Question 62 of 188
62. Question
1 pointsWhich mode are in PAgP? (choose two)Correct
Incorrect
-
Question 63 of 188
63. Question
1 pointsIn an Ethernet network, under what two scenarios can devices transmit? (Choose two.)Correct
Incorrect
-
Question 64 of 188
64. Question
1 pointsAt the end of an RSTP election process, which access layer switch port will assume the discarding role?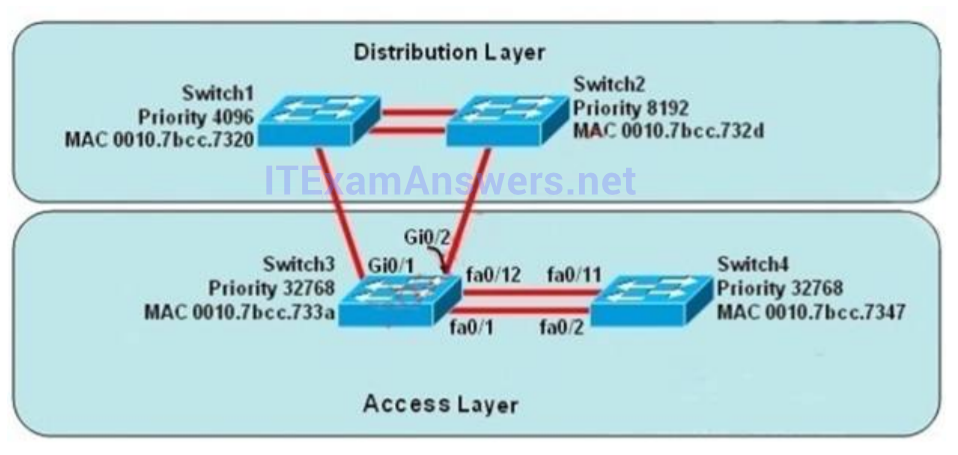 Correct
Correct
Incorrect
Hint
In this question, we only care about the Access Layer switches (Switch3 & 4). Switch 3 has a lower bridge ID than Switch 4 (because the MAC of Switch3 is smaller than that of Switch4) so both ports of Switch3 will be in forwarding state. The alternative port will surely belong to Switch4. Switch4 will need to block one of its ports to avoid a bridging loop between the two switches. But how does Switch4 select its blocked port? Well, the answer is based on the BPDUs it receives from Switch3. A BPDU is superior to another if it has: 1. A lower Root Bridge ID 2. A lower path cost to the Root 3. A lower Sending Bridge ID 4. A lower Sending Port ID These four parameters are examined in order. In this specific case, all the BPDUs sent by Switch3 have the same Root Bridge ID, the same path cost to the Root and the same Sending Bridge ID. The only parameter left to select the best one is the Sending Port ID (Port ID = port priority + port index). In this case the port priorities are equal because they use the default value, so Switch4 will compare port index values, which are unique to each port on the switch, and because Fa0/12 is inferior to Fa0/1, Switch4 will select the port connected with Fa0/1 (of Switch3) as its root port and block the other port -> Port fa0/11 of Switch4 will be blocked (discarding role). -
Question 65 of 188
65. Question
1 pointsWhich switch would STP choose to become the root bridge in the selection process?Correct
Incorrect
-
Question 66 of 188
66. Question
1 pointsRefer to the exhibit. What two results would occur if the hub were to be replaced with a switch that is configured with one Ethernet VLAN? (Choose two.)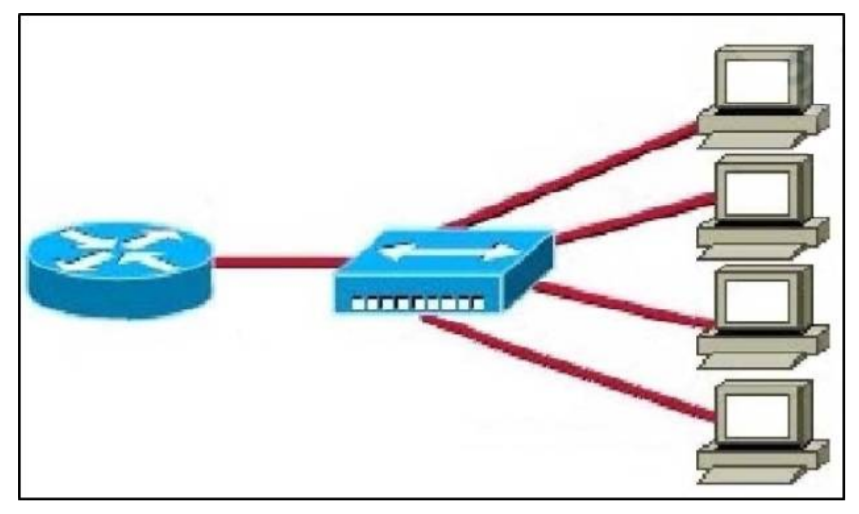 Correct
Correct
Incorrect
-
Question 67 of 188
67. Question
1 pointsFor which two protocols can PortFast alleviate potential host startup is-sues? (Choose two.)Correct
Incorrect
-
Question 68 of 188
68. Question
1 pointsWhich method does a connected trunk port use to tag VLAN traffic?Correct
Incorrect
Hint
IEEE 802.1Q is the networking standard that supports virtual LANs (VLANs) on an Ethernet network. When a frame enters the VLAN-aware portion of the network (a trunk link, for example), a VLAN ID tag is added to represent the VLAN membership of that frame. The picture below shows how VLAN tag is added and removed while going through the network.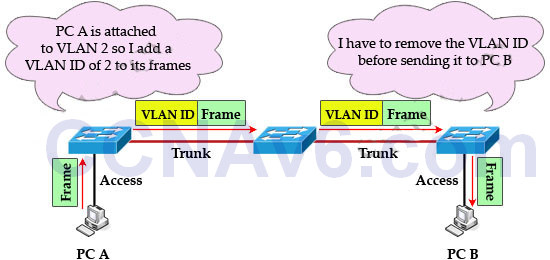
-
Question 69 of 188
69. Question
1 pointsConfiguration of which option is required on a Cisco switch for the Cisco IP phone to work?Correct
Incorrect
Hint
When you connect an IP phone to a switch using a trunk link, it can cause high CPU utilization in the switches. As all the VLANs for a particular interface are trunked to the phone, it increases the number of STP instances the switch has to manage. This increases the CPU utilization. Trunking also causes unnecessary broadcast / multicast / unknown unicast traffic to hit the phone link. In order to avoid this, remove the trunk configuration and keep the voice and access VLAN configured along with Quality of Service (QoS). Technically, it is still a trunk, but it is called a Multi-VLAN Access Port (MVAP). Because voice and data traffic can travel through the same port, you should specify a different VLAN for each type of traffic. You can configure a switch port to forward voice and data traffic on different VLANs. Configure IP phone ports with a voice VLAN configuration. This configuration creates a pseudo trunk, but does not require you to manually prune the unnecessary VLANs. The voice VLAN feature enables access ports to carry IP voice traffic from an IP phone. You can configure a voice VLAN with the “switchport voice vlan …” command under interface mode. The full configuration is shown below:Switch(config)#interface fastethernet0/1 Switch(config-if)#switchport mode access Switch(config-if)#switchport access vlan 10 Switch(config-if)#switchport voice vlan 20
Reference: http://www.cisco.com/c/en/us/support/docs/switches/catalyst-4500-series-switches/69632-configuring-cat-ip-phone.html -
Question 70 of 188
70. Question
1 pointsRefer to the exhibit. Which statement describes the effect of this configuration?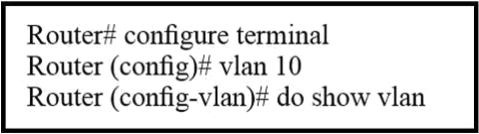 Correct
Correct
Incorrect
Hint
With the configuration above, when we type “do show vlan” we would not see VLAN 10 in the VLAN database because it has not been created yet. VLAN 10 is only created when we exits VLAN configuration mode (with “exit” command). -
Question 71 of 188
71. Question
1 pointsWhich statement about native VLAN traffic is true?Correct
Incorrect
-
Question 72 of 188
72. Question
1 pointsWhich statement about unicast frame forwarding on a switch is true?Correct
Incorrect
-
Question 73 of 188
73. Question
1 pointsWhich type does a port become when it receives the best BPDU on a bridge?Correct
Incorrect
Hint
Root port is the port on non-root bridge which is closest to the root bridge (in term of cost). Therefore when a port receives the best BPDU on a non-root bridge it will become the root port. -
Question 74 of 188
74. Question
1 pointsWhich value can you modify to configure a specific interface as the preferred forwarding interface?Correct
Incorrect
Hint
We can configure the port priority to change the preferred forwarding interface as we wish. For example we can change the port priority of an interface for VLAN 20 to 64 as follows:Switch(config-if)#spanning-tree vlan 20 port-priority 64
-
Question 75 of 188
75. Question
1 pointsWhich statement about VLAN configuration is true?Correct
Incorrect
-
Question 76 of 188
76. Question
1 pointsWhich two protocols are used by bridges and/or switches to prevent loops in a layer 2 network? (Choose two.)Correct
Incorrect
-
Question 77 of 188
77. Question
1 pointsHow can you disable DTP on a switch port?Correct
Incorrect
Hint
Although some books and websites said DTP is disabled if the switch port is configured as trunk or access mode (via the command “switchport mode trunk” or “switchport mode access”) but in fact DTP is still running in these modes. Please read at http://packetlife.net/blog/2008/sep/30/disabling-dynamic-trunking-protocol-dtp/. The only way to disable DTP on a switch port is to use the “switchport nonegotiate” command. But notice this command can only be used after configuring that switch port in “trunk” or “access” mode. Therefore this is a question with no correct answer but if we have to choose an answer, we will choose answer A. At least it is correct in theory. -
Question 78 of 188
78. Question
1 pointsWhich command can you enter on a switch to display the IP addresses associated with connected devices?Correct
Incorrect
Hint
Only the “show cdp neighbor detail” gives us information about the IP address of the connected device. Below is an example of this command.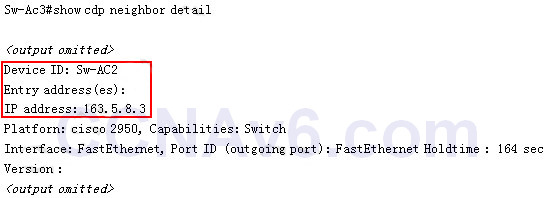
-
Question 79 of 188
79. Question
1 pointsWhich protocol is a Cisco proprietary implementation of STP?Correct
Incorrect
-
Question 80 of 188
80. Question
1 pointsVLAN 3 is not yet configured on your switch. What happens if you set the switchport access vlan 3 command in interface configuration mode?Correct
Incorrect
Hint
The “switchport access vlan 3″will put that interface as belonging to VLAN 3 while also updated the VLAN database automatically to include VLAN 3. -
Question 81 of 188
81. Question
1 pointsThree switches are connected to one another via trunk ports. Assuming the default switch configuration, which switch is elected as the root bridge for the spanning-tree instance of VLAN 1?Correct
Incorrect
Hint
Each switch in your network will have a Bridge ID Priority value, more commonly referred to as a BID. This BID is a combination of a default priority value and the switch’s MAC address, with the priority value listed first. The lowest BID will win the election process. For example, if a Cisco switch has the default priority value of 32,768 and a MAC address of 11-22-33- 44-55-66, the BID would be 32768:11-22-33-44-55-66. Therefore, if the switch priority is left at the default, the MAC address is the deciding factor in the root bridge election. -
Question 82 of 188
82. Question
1 pointsWhich command enables RSTP on a switch?Correct
Incorrect
Hint
Rapid Spanning Tree Protocol (RSTP) is an enhancement of the original STP 802.1D protocol. The RSTP 802.1w protocol is an IEEE open implementation. Cisco has its own proprietary implementation of RSTP, that includes the benefits of its Per-VLAN spanning tree protocols, called Rapid-PVST+. To activate the Rapid-PVST+ protocol: switch(config)#spanning-tree mode rapid-pvst -
Question 83 of 188
83. Question
1 pointsCisco Catalyst switches CAT1 and CAT2 have a connection between them using ports FA0/13. An 802.1Q trunk is configured between the two switches. On CAT1, VLAN 10 is chosen as native, but on CAT2 the native VLAN is not specified. What will happen in this scenario?Correct
Incorrect
Hint
A “native VLAN mismatch” error will appear by CDP if there is a native VLAN mismatch on an 802.1Q link. “VLAN mismatch” can cause traffic from one vlan to leak into another vlan. -
Question 84 of 188
84. Question
1 pointsRefer to the exhibit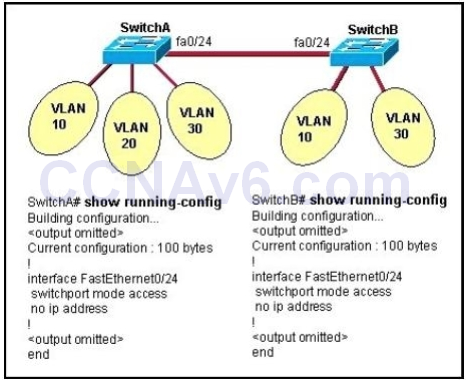 All switch ports are assigned to the correct VLANs, but none of the hosts connected to SwitchA can communicate with hosts in the same VLAN connected to SwitchB. Based on the output shown, what is the most likely problem?
Correct
All switch ports are assigned to the correct VLANs, but none of the hosts connected to SwitchA can communicate with hosts in the same VLAN connected to SwitchB. Based on the output shown, what is the most likely problem?
Correct
Incorrect
Hint
In order to pass traffic from VLANs on different switches, the connections between the switches must be configured as trunk ports. -
Question 85 of 188
85. Question
1 pointsWhat is the function of the command switchport trunk native vlan 999 on a Cisco Catalyst switch?Correct
Incorrect
Hint
Configuring the Native VLAN for Untagged Traffic A trunk port configured with 802.1Q tagging can receive both tagged and untagged traffic. By default, the switch forwards untagged traffic in the native VLAN configured for the port. The native VLAN is VLAN 1 by default. -
Question 86 of 188
86. Question
1 pointsRefer to the exhibit. A frame on VLAN 1 on switch S1 is sent to switch S2 where the frame is received on VLAN 2. What causes this behavior?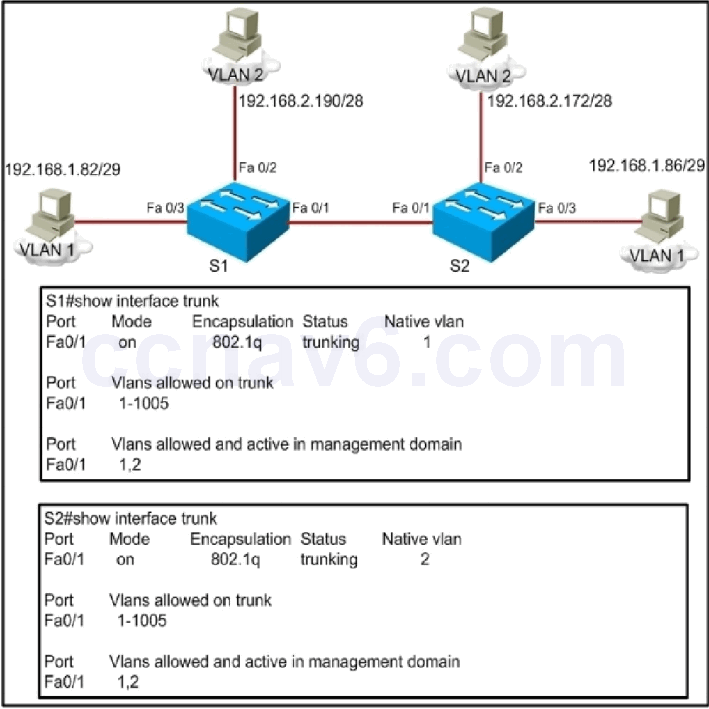 Correct
Correct
Incorrect
-
Question 87 of 188
87. Question
1 pointsWhy will a switch never learn a broadcast address?Correct
Incorrect
-
Question 88 of 188
88. Question
1 pointsWhat can you change to select switch as root bridge?Correct
Incorrect
-
Question 89 of 188
89. Question
1 pointsWhich two types of information are held in the MAC address table? (Choose two)Correct
Incorrect
Hint
We can check the MAC address table with the command “show mac address-table”: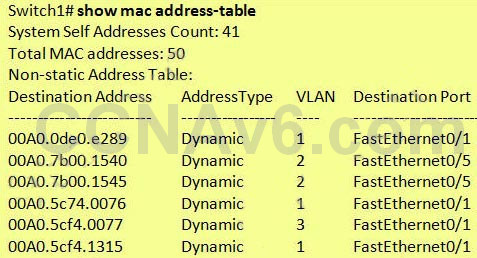 As we can see here, the “MAC address” field is the source MAC address and the “Ports” field are the ports of the switch from which the frames (with corresponding source MAC address) were received.
As we can see here, the “MAC address” field is the source MAC address and the “Ports” field are the ports of the switch from which the frames (with corresponding source MAC address) were received. -
Question 90 of 188
90. Question
1 pointsWhich three are valid modes for a switch port used as a VLAN trunk? (choose three)Correct
Incorrect
-
Question 91 of 188
91. Question
1 pointsWhich type of attack can be mitigated by configuring the default native VLAN to be unused?Correct
Incorrect
-
Question 92 of 188
92. Question
1 pointsWhich process is associated with spanning-tree convergence?Correct
Incorrect
Hint
SPT must performs three steps to provide a loop-free network topology: 1. Elects one root bridge 2. Select one root port per nonroot bridge 3. Select one designated port on each network segment -> Answer B is correct. -
Question 93 of 188
93. Question
1 pointsWhich option is a benefit of switch stacking?Correct
Incorrect
Hint
Switch stacking technology allows the network engineer to make that stack of physical switches act like one switch. The stacking cables together make a ring between the switches. That is, the switches connect in series, with the last switch connecting again to the first.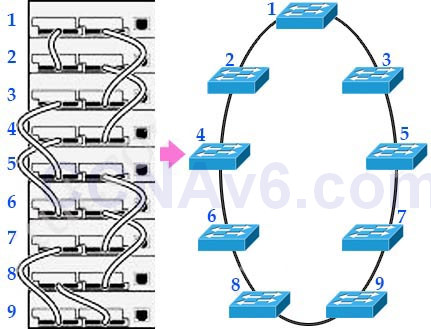 Answer B is not correct as switch stacking is about connecting switches together so that they act as one switch, not about adding and removing hosts.
Answer C is not correct because switch stacking has nothing to do with performance of high-needs applications.
Surely switch stacking provides redundancy as stacking creates a ring of connection with two opposite paths. Whenever a frame is ready for transmission onto the path, a calculation is made to see which path has the most available bandwidth. The entire frame is then copied onto this half of the path.
With switch stacking, STP, CDP and VTP would run on one switch, not multiple switches. Also there would be one MAC address table, and it would reference all ports on all physical switches so we may say switch stacking has better resource usage. Also if we consider all stacking switches as one logical switch then surely the port density is increase very much. Therefore answer D is the most suitable one.
Reference: http://www.cisco.com/c/en/us/products/collateral/switches/catalyst-3750-series-switches/prod_white_paper09186a00801b096a.html
Answer B is not correct as switch stacking is about connecting switches together so that they act as one switch, not about adding and removing hosts.
Answer C is not correct because switch stacking has nothing to do with performance of high-needs applications.
Surely switch stacking provides redundancy as stacking creates a ring of connection with two opposite paths. Whenever a frame is ready for transmission onto the path, a calculation is made to see which path has the most available bandwidth. The entire frame is then copied onto this half of the path.
With switch stacking, STP, CDP and VTP would run on one switch, not multiple switches. Also there would be one MAC address table, and it would reference all ports on all physical switches so we may say switch stacking has better resource usage. Also if we consider all stacking switches as one logical switch then surely the port density is increase very much. Therefore answer D is the most suitable one.
Reference: http://www.cisco.com/c/en/us/products/collateral/switches/catalyst-3750-series-switches/prod_white_paper09186a00801b096a.html -
Question 94 of 188
94. Question
1 pointsWhich port state is introduced by Rapid-PVST?Correct
Incorrect
Hint
PVST+ is based on IEEE802.1D Spanning Tree Protocol (STP). But PVST+ has only 3 port states (discarding, learning and forwarding) while STP has 5 port states (blocking, listening, learning, forwarding and disabled). So discarding is a new port state in PVST+. -
Question 95 of 188
95. Question
1 pointsWhat are the possible trunking modes for a switch port? (Choose three.)Correct
Incorrect
-
Question 96 of 188
96. Question
1 pointsRefer to the exhibit. What set of commands was configured on interface Fa0/3 to produce the given the output? Correct
Correct
Incorrect
-
Question 97 of 188
97. Question
1 pointsWhich type of secure MAC address must be configured manually?Correct
Incorrect
-
Question 98 of 188
98. Question
1 pointsWhich two elements are fields in an Ethernet frame? (Choose two.)Correct
Incorrect
-
Question 99 of 188
99. Question
1 pointsWhat is one benefit of PVST+?Correct
Incorrect
Hint
The PVST+ provides Layer 2 load-balancing for the VLAN on which it runs. You can create different logical topologies by using the VLANs on your network to ensure that all of your links are used but that no one link is oversubscribed. Each instance of PVST+ on a VLAN has a single root switch. This root switch propagates the spanning-tree information associated with that VLAN to all other switches in the network. Because each switch has the same information about the network, this process ensures that the network topology is maintained and optimized per VLAN. -
Question 100 of 188
100. Question
1 pointsWhich three of these statements regarding 802.1Q trunking are correct? (Choose three.)Correct
Incorrect
-
Question 101 of 188
101. Question
1 pointsWhich IEEE standard protocol is initiated as a result of successful DTP completion in a switch over FastEthernet?Correct
Incorrect
Hint
Dynamic Trunking Protocol (DTP) is a Cisco proprietary protocol for negotiating trunking on a link between two devices and for negotiating the type of trunking encapsulation (802.1Q) to be used. -
Question 102 of 188
102. Question
1 pointsWhich of the port is not part of STP protocol.Correct
Incorrect
-
Question 103 of 188
103. Question
1 pointsAssuming the default switch configuration which vlan range can be added modified and removed on a cisco switch?Correct
Incorrect
-
Question 104 of 188
104. Question
1 pointsBased on the output below, which two statements are true of the interfaces on Switch1? (Choose two.)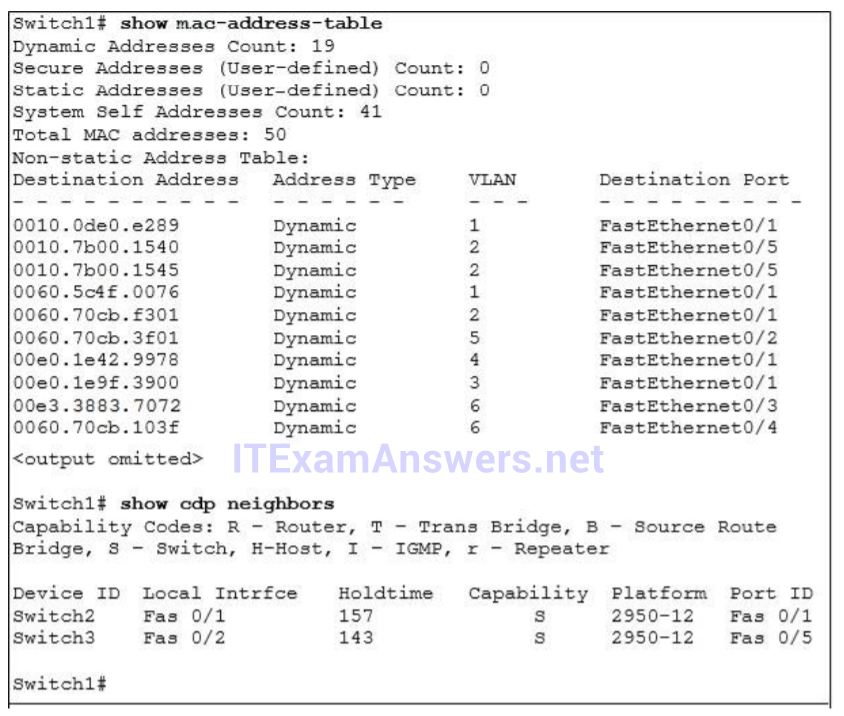 Correct
Correct
Incorrect
Hint
From the “show mac address-table” output, we see FastEthernet0/1 can receive traffic from multiple VLANs -> it is configured as a trunk. Also from the “show cdp neighbors” output, we see Fa0/1 of this switch is connecting to Switch2 so it is configured as a trunk. There are two MAC addresses learned from FastEthernet0/5 while FastEthernet0/5 is not configured as trunk (only Fa0/2 & Fa0/3 are configured as trunk links) -> a hub is used on this port. -
Question 105 of 188
105. Question
1 pointsRefer to the exhibit. How should the FastEthernet0/1 port on the 2950 model switches that are shown in the exhibit be configured to allow connectivity between all devices?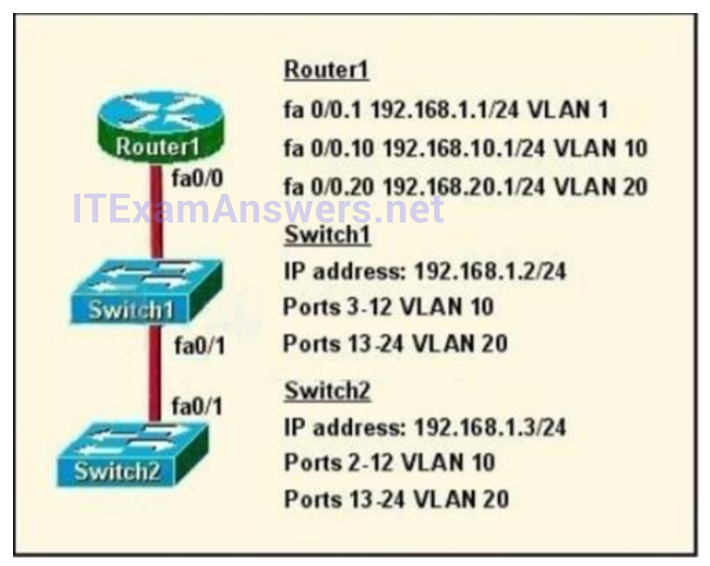 Correct
Correct
Incorrect
-
Question 106 of 188
106. Question
1 pointsWhich RPVST+ port state is excluded from all STP operations?Correct
Incorrect
-
Question 107 of 188
107. Question
1 pointsWhich option is the industry-standard protocol for EtherChannel?Correct
Incorrect
Hint
LACP is the IEEE Standard (IEEE 802.3ad) and is the most common dynamic Etherchannel protocol, whereas PAgP is a Cisco proprietary protocol and works only between supported vendors and Cisco devices. -
Question 108 of 188
108. Question
1 pointsWhich two pieces of information can be shared with LLDP TLVs? (Choose two)Correct
Incorrect
-
Question 109 of 188
109. Question
1 pointsWhich two statements about stacking Cisco switches are true ?(choose two)Correct
Incorrect
-
Question 110 of 188
110. Question
1 pointsRefer to the exhibit.If the devices produced the given output, what is the cause of the EtherChannel problem?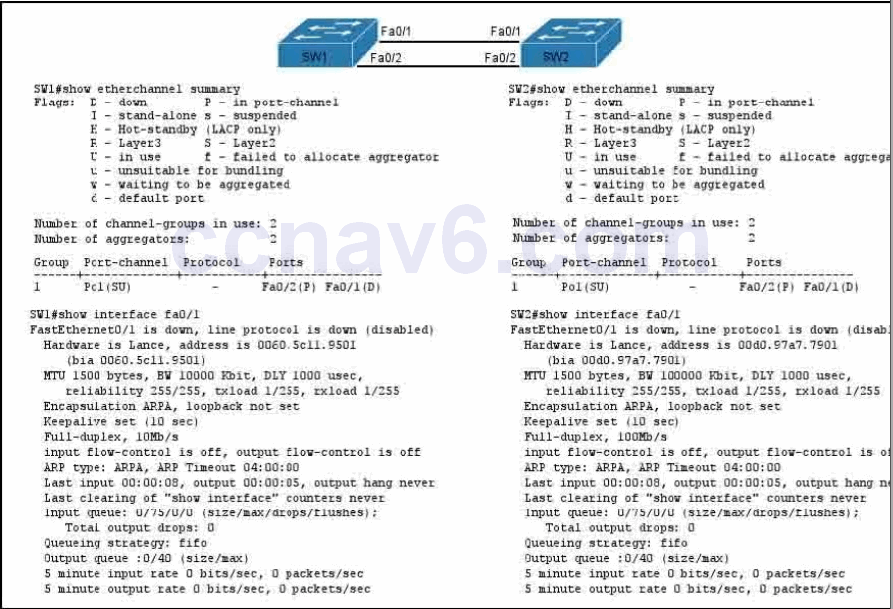 Correct
Correct
Incorrect
-
Question 111 of 188
111. Question
1 pointsFor which two reasons might be you choose chassis aggregation instead of stacking switches? (Choose two.)Correct
Incorrect
-
Question 112 of 188
112. Question
1 pointsRefer to the exhibit. The two exhibited devices are the only Cisco devices on the network. The serial network between the two devices has a mask of 255.255.255.252. Given the output that is shown, what three statements are true of these devices? (Choose three.)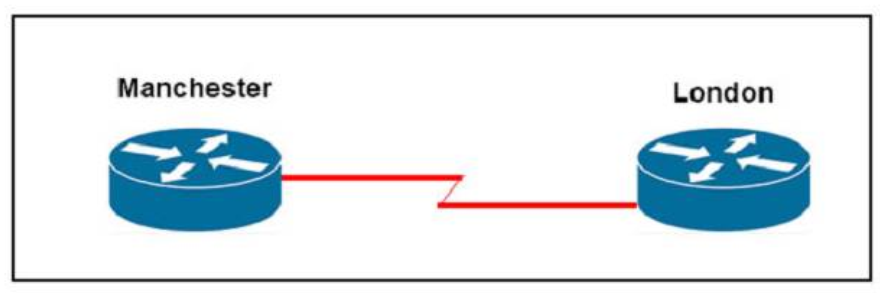
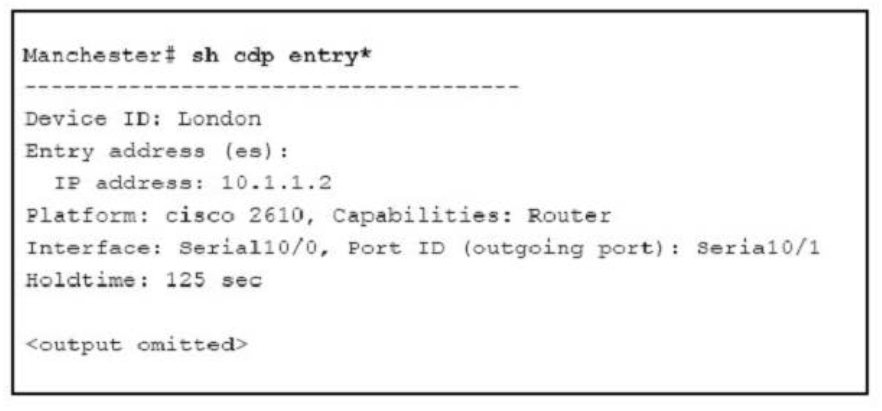 Correct
Correct
Incorrect
-
Question 113 of 188
113. Question
1 pointsRefer to the exhibit. Based on the information given, which switch will be elected root bridge and why?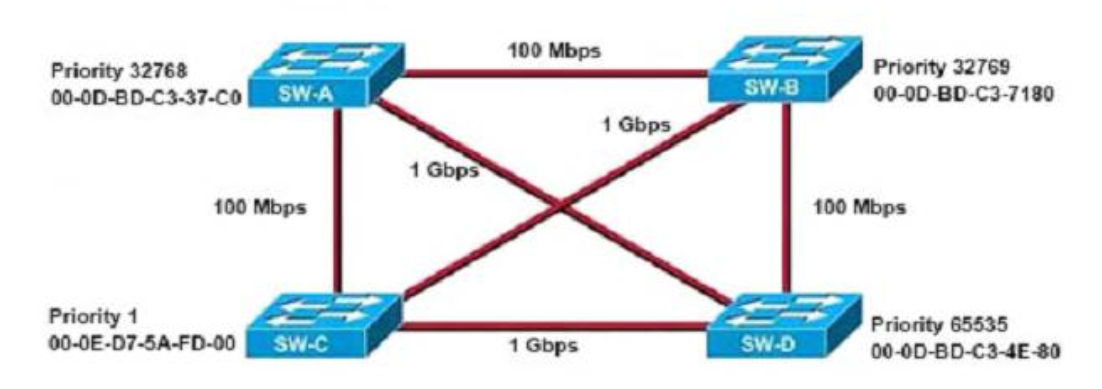 Correct
Correct
Incorrect
-
Question 114 of 188
114. Question
1 pointsA network interface port has collision detection and carrier sensing enabled on a shared twisted pair network. From this statement, what is known about the network interface port?Correct
Incorrect
Hint
Modern Ethernet networks built with switches and full-duplex connections no longer utilize CSMA/CD. CSMA/CD is only used in obsolete shared media Ethernet (which uses repeater or hub). -
Question 115 of 188
115. Question
1 pointsRefer to the exhibit. Given the output shown from this Cisco Catalyst 2950, what is the reason that interface FastEthernet 0/10 is not the root port for VLAN 2?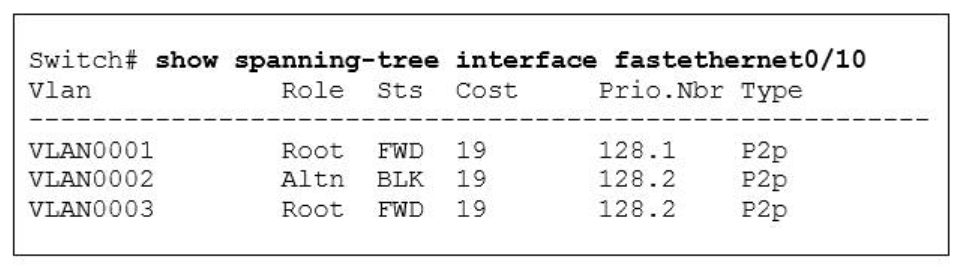 Correct
Correct
Incorrect
Hint
Since the port is in the blocked status, we must assume that there is a shorter path to the root bridge elsewhere. -
Question 116 of 188
116. Question
1 pointsRefer to the exhibit. Why has this switch not been elected the root bridge for VLAN1?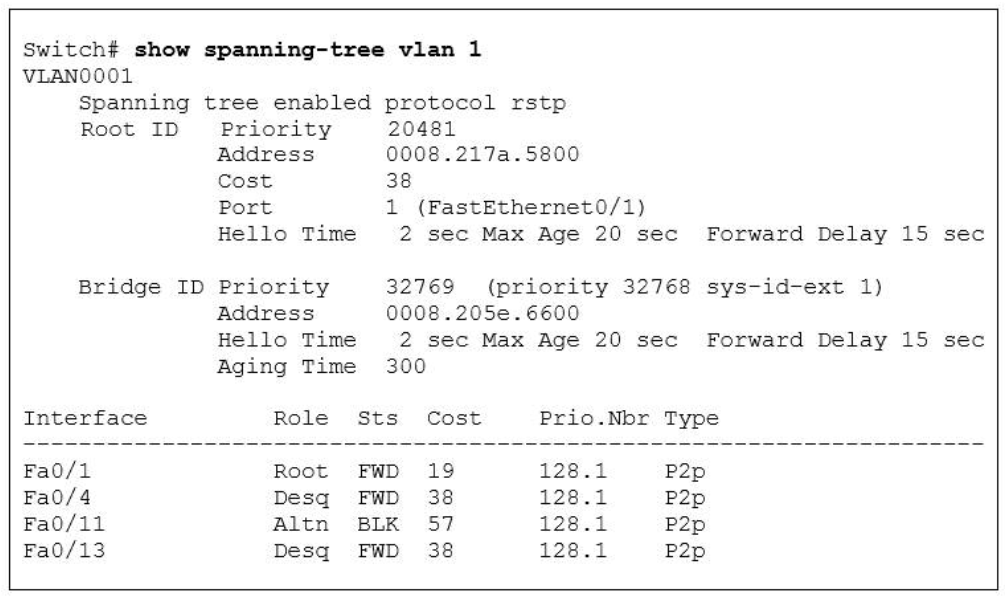 Correct
Correct
Incorrect
Hint
The root bridge is determined by the lowest bridge ID, and this switch has a bridge ID priority of 32768, which is higher than the roots priority of 20481. -
Question 117 of 188
117. Question
1 pointsWhich two link protocols are used to carry multiple VLANs over a single link? (Choose two.)Correct
Incorrect
Hint
Cisco switches can use two different encapsulation types for trunks, the industry standard 802.1q or the Cisco proprietary ISL. Generally, most network engineers prefer to use 802.1q since it is standards based and will interoperate with other vendors. -
Question 118 of 188
118. Question
1 pointsAssuming the default switch configuration, which VLAN range can be added, modified, and removed on a Cisco switch?Correct
Incorrect
Hint
VLAN 1 is the default VLAN on Cisco switch. It always exists and cannot be added, modified or removed. VLANs 1002-1005 are default VLANs for FDDI & Token Ring and they can’t be deleted or used for Ethernet. -
Question 119 of 188
119. Question
1 pointsRefer to the topology shown in the exhibit. Which ports will be STP designated ports if all the links are operating at the same bandwidth? (Choose three.)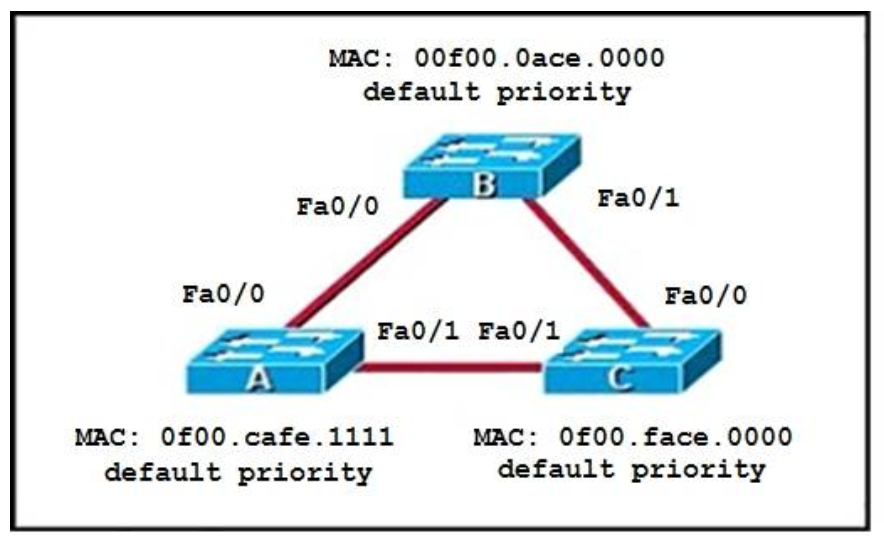 Correct
Correct
Incorrect
Hint
This question is to check the spanning tree election problem. 1. First, select the root bridge, which can be accomplished by comparing the bridge ID, the smallest will be selected. Bridge-id= bridge priority + MAC address. The three switches in the figure all have the default priority, so we should compare the MAC address, it is easy to find that SwitchB is the root bridge. 2. Select the root port on the non-root bridge, which can be completed through comparing root path cost. The smallest will be selected as the root port. 3. Next, select the Designated Port. First, compare the path cost, if the costs happen to be the same, then compare the BID, still the smallest will be selected. Each link has a DP. Based on the exhibit above, we can find DP on each link. The DP on the link between SwitchA and SwitchC is SwitchA’Fa0/1, because it has the smallest MAC address. -
Question 120 of 188
120. Question
1 pointsRefer to the exhibit. Which statement is true?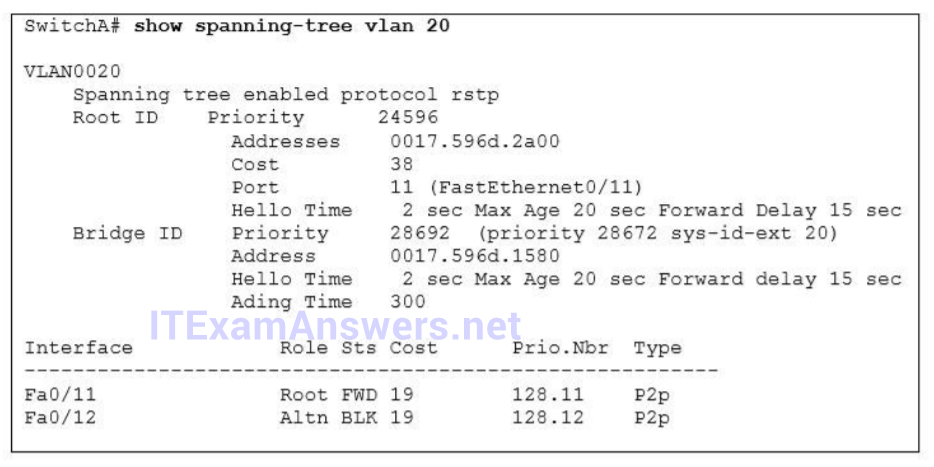 Correct
Correct
Incorrect
Hint
Only non-root bridge can have root port. Fa0/11 is the root port so we can confirm this switch is not the root bridge -> A is not correct. From the output we learn this switch is running Rapid STP, not PVST -> B is not correct. 0017.596d.1580 is the MAC address of this switch, not of the root bridge. The MAC address of the root bridge is 0017.596d.2a00 -> C is not correct. All of the interface roles of the root bridge are designated. SwitchA has one Root port and 1 Alternative port so it is not the root bridge -> D is correct. -
Question 121 of 188
121. Question
1 pointsWhich two benefits are provided by creating VLANs? (Choose two.)Correct
Incorrect
Hint
A VLAN is a switched network that is logically segmented on an organizational basis, by functions, project teams, or applications rather than on a physical or geographical basis. Security: VLANs also improve security by isolating groups. High-security users can be grouped into a VLAN, possible on the same physical segment, and no users outside that VLAN can communicate with them LAN Segmentation VLANs allow logical network topologies to overlay the physical switched infrastructure such that any arbitrary collection of LAN ports can be combined into an autonomous user group or community of interest. The technology logically segments the network into separate Layer 2 broadcast domains whereby packets are switched between ports designated to be within the same VLAN. By containing traffic originating on a particular LAN only to other LANs in the same VLAN, switched virtual networks avoid wasting bandwidth. -
Question 122 of 188
122. Question
1 pointsHow many broadcast domains are shown in the graphic assuming only the default VLAN is confgured on the switches?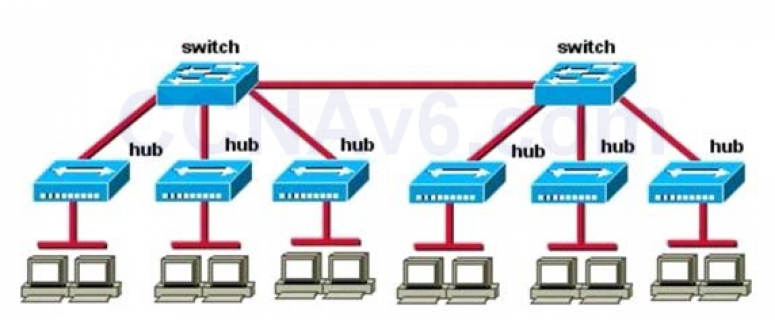 Correct
Correct
Incorrect
Hint
Only router can break up broadcast domains but in this exhibit no router is used so there is only 1 broadcast domain. For your information, there are 7 collision domains in this exhibit (6 collision domains between hubs & switches + 1 collision between the two switches). -
Question 123 of 188
123. Question
1 pointsWhich term describes a spanning-tree network that has all switch ports in either the blocking or forwarding state?Correct
Incorrect
Hint
Spanning Tree Protocol convergence (Layer 2 convergence) happens when bridges and switches have transitioned to either the forwarding or blocking state. When layer 2 is converged, root bridge is elected and all port roles (Root, Designated and Non-Designated) in all switches are selected. -
Question 124 of 188
124. Question
1 pointsA network administrator creates a layer 3 EtherChannel, bundling four interfaces into channel group 1. On what interface is the IP address configured?Correct
Incorrect
-
Question 125 of 188
125. Question
1 pointsWhich Cisco Catalyst feature automatically disables the port in an operational PortFast upon receipt of a BPDU?Correct
Incorrect
Hint
We only enable PortFast feature on access ports (ports connected to end stations). But if someone does not know he can accidentally plug that port to another switch and a loop may occur when BPDUs are being transmitted and received on these ports. With BPDU Guard, when a PortFast receives a BPDU, it will be shut down to prevent a loop. -
Question 126 of 188
126. Question
1 pointsRefer to the exhibit. Given this output for SwitchC, what should the network administrator’s next action be?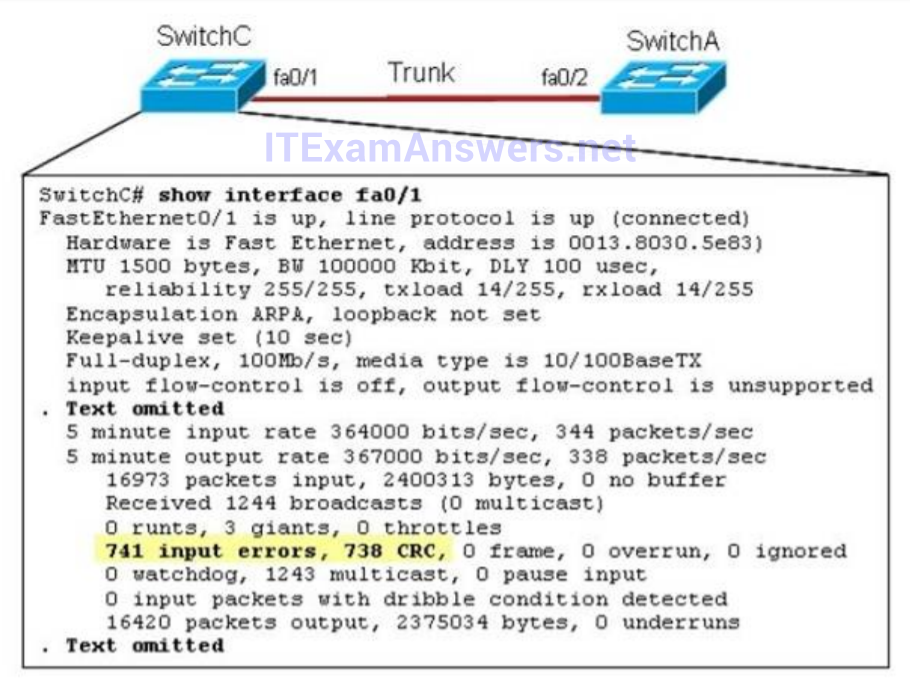 Correct
Correct
Incorrect
Hint
Here we can see that this port is configured for full duplex, so the next step would be to check the duple setting of the port on the other switch. A mismatched trunk encapsulation would not result in input errors and CRC errors. -
Question 127 of 188
127. Question
1 pointsIn a switched environment, what does the IEEE 802.1Q standard describe?Correct
Incorrect
Hint
A broadcast domain must sometimes exist on more than one switch in the network. To accomplish this, one switch must send frames to another switch and indicate which VLAN a particular frame belongs to. On Cisco switches, a trunk link is created to accomplish this VLAN identification. ISL and IEEE 802.1Q are different methods of putting a VLAN identifier in a Layer 2 frame. The IEEE 802.1Q protocol interconnects VLANs between multiple switches, routers, and servers. With 802.1Q, a network administrator can define a VLAN topology to span multiple physical devices. Cisco switches support IEEE 802.1Q for FastEthernet and Gigabit Ethernet interfaces. An 802.1Q trunk link provides VLAN identification by adding a 4-byte tag to an Ethernet Frame as it leaves a trunk port. -
Question 128 of 188
128. Question
1 pointsRefer to the exhibit. A technician is troubleshooting host connectivity issues on the switches. The hosts inVLANs 10 and 15 on Sw11 are unable to communicate with hosts in the same VLANs on Sw12. Hosts in the Admin VLAN are able to communicate. The port-to-VLAN assignments are identical on the two switches. What could be the problem?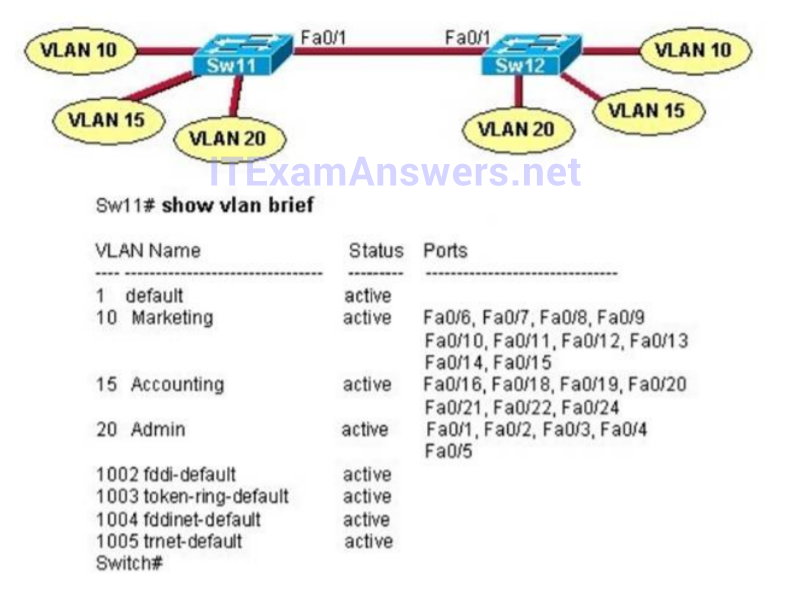 Correct
Correct
Incorrect
-
Question 129 of 188
129. Question
1 pointsAn administrator is unsuccessful in adding VLAN 50 to a switch. While troubleshooting the problem, the administrator views the output of the show vtp status command, which is displayed in the graphic. What commands must be issued on this switch to add VLAN 50 to the database? (Choose two.)Correct
Incorrect
-
Question 130 of 188
130. Question
1 pointsCorrect
Incorrect
-
Question 131 of 188
131. Question
1 pointsRefer to the exhibit. The network administrator has created a new VLAN on Switch1 and added host C and host D. The administrator has properly configured switch interfaces FastEthernet0/13 through FastEthernet0/14 to be members of the new VLAN. However, after the network administrator completed the configuration, host A could communicate with host B, but host A could not communicate with host C or host D. Which commands are required to resolve this problem?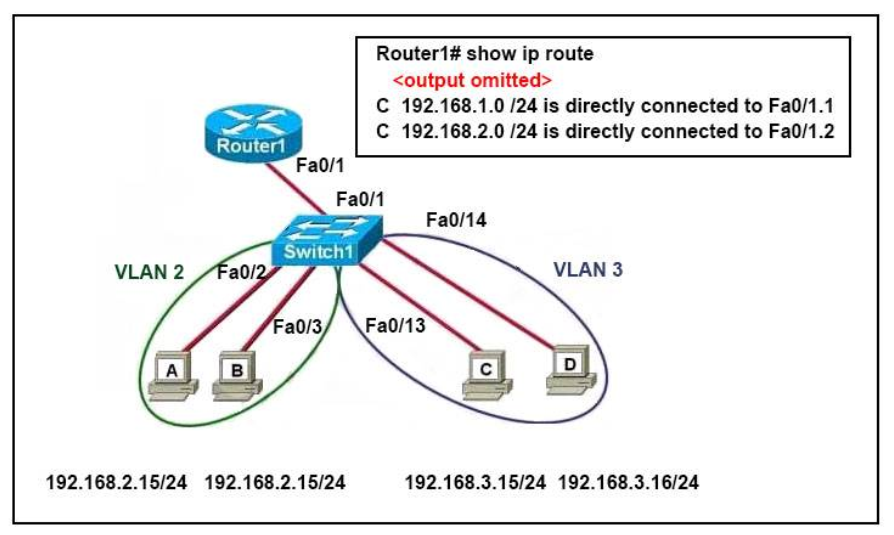 Correct
Correct
Incorrect
-
Question 132 of 188
132. Question
1 pointsOn a network of one department, there are four PCs connected to a switch, as shown in the following figure: After the Switch1 restarts. Host A (the host on the left) sends the first frame to Host C (the host on the right). What the first thing should the switch do?Correct
Incorrect
-
Question 133 of 188
133. Question
1 pointsA network administrator is explaining VTP configuration to a new technician. What should the network administrator tell the new technician about VTP configuration? (Choose three.)Correct
Incorrect
-
Question 134 of 188
134. Question
1 pointsA company is installing IP phones. The phones and office computers connect to the same device. To ensure maximum throughput for the phone data, the company needs to make sure that the phone traffic is on a different network from that of the office computer data traffic. What is the best network device to which to directly connect the phones and computers, and what technology should be implemented on this device? (Choose two.)Correct
Incorrect
-
Question 135 of 188
135. Question
1 pointsWhat are two benefits of using VTP in a switching environment? (Choose two.)Correct
Incorrect
-
Question 136 of 188
136. Question
1 pointsWhich two values are used by Spanning Tree Protocol to elect a root bridge? (Choose two.)Correct
Incorrect
-
Question 137 of 188
137. Question
1 pointsWhich three statements are typical characteristics of VLAN arrangements? (Choose three.)Correct
Incorrect
-
Question 138 of 188
138. Question
1 pointsSwitch ports operating in which two roles will forward traffic according to the IEEE 802.1w standard? (Choose two.)Correct
Incorrect
-
Question 139 of 188
139. Question
1 pointsRefer to the exhibit. This command is executed on 2960Switch: Which two of these statements correctly identify results of executing the command? (Choose two.) Correct
Correct
Incorrect
-
Question 140 of 188
140. Question
1 pointsRefer to the exhibit. The switches on a campus network have been interconnected as shown. All of the switches are running Spanning Tree Protocol with its default settings. Unusual traffic patterns are observed and it is discovered that Switch9 is the root bridge. Which change will ensure that Switch1 will be selected as the root bridge instead of Switch9?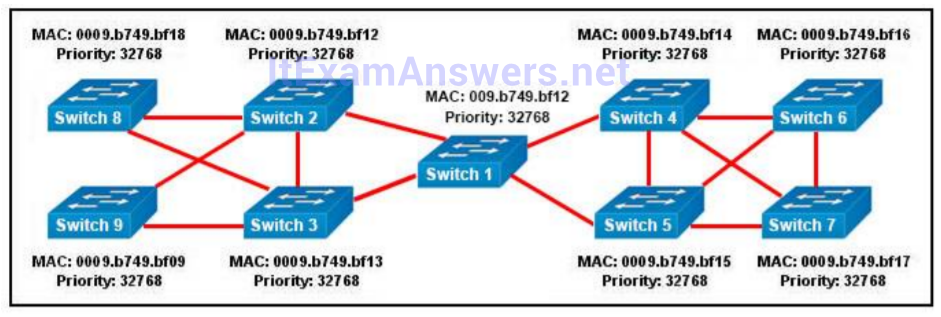 Correct
Correct
Incorrect
-
Question 141 of 188
141. Question
1 pointsWhich statement about DTP is true?Correct
Incorrect
Hint
Disabling Dynamic Trunking Protocol (DTP) Cisco’s Dynamic Trunking Protocol can facilitate the automatic creation of trunks between two switches. When two connected ports are configured in dynamic mode, and at least one of the ports is configured as desirable, the two switches will negotiate the formation of a trunk across the link. DTP isn’t to be confused with VLAN Trunking Protocol (VTP), although the VTP domain does come into play.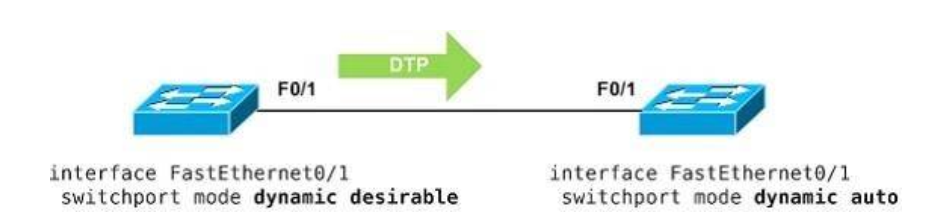 DTP on the wire is pretty simple, essentially only advertising the VTP domain, the status of the interface, and its DTP type. These packets are transmitted in the native (or access) VLAN every 60 seconds both natively and with ISL encapsulation (tagged as VLAN 1) when DTP is enabled.
DTP on the wire is pretty simple, essentially only advertising the VTP domain, the status of the interface, and its DTP type. These packets are transmitted in the native (or access) VLAN every 60 seconds both natively and with ISL encapsulation (tagged as VLAN 1) when DTP is enabled. -
Question 142 of 188
142. Question
1 pointsWhich feature can you use to monitor traffic on a switch by replicating it to another port or ports on the same switch?Correct
Incorrect
Hint
Switched Port Analyzer (SPAN) is used to analyze network traffic passing through ports on a switch. For example we can configure the Switch to monitor its interface Fa0/0, which connects to the Core, by sending all traffic to/from Fa0/0 to its Fa0/1 interface. At Fa0/1 interface we connect to a computer and use such a software like Wireshark to capture the packets.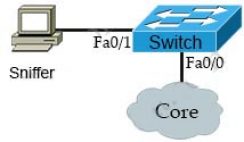
-
Question 143 of 188
143. Question
1 pointsRefer to the exhibit. While troubleshooting a switch, you executed the show interface port-channel 1 etherchannel command and it returned this output. Which information is provided by the Load value?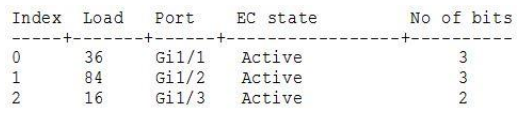 Correct
Correct
Incorrect
Hint
The way EtherChannel load balancing works is that the switch assigns a hash result from 0-7 based on the configured hash method ( load balancing algorithm ) for the type of traffic. This hash result is commonly called as Result Bundle Hash (RBH). Now we need to convert Load value from Hexadecimal to Binary numbers. Therefore: + Gi1/1: 36 (Hex) = 00110110 (Bin) -> Bits 3, 4, 6, 7 are chosen + Gi1/2: 84 (Hex) = 10000100 (Bin) -> Bits 1, 6 are chosen + Gi1/3: 16 (Hex) = 00010110 (Bin) -> Bits 4, 6, 7 are chosen Therefore if the RBH is 3, it will choose Gi1/1. If RBH is 4, it will choose Gi1/1 and Gi1/3 interfaces. If RBH is 6 it will choose all three above interfaces. And the bit sharing ratio is 3:3:2 (from “No of bits” column) hence two links has higher probability of getting utilized as compared to the third link. -
Question 144 of 188
144. Question
1 pointsWhich statement about slow inter VLAN forwarding is true?Correct
Incorrect
Hint
Common Causes of Slow IntraVLAN and InterVLAN Connectivity The symptoms of slow connectivity on a VLAN can be caused by multiple factors on different network layers. Commonly the network speed issue may be occurring on a lower level, but symptoms can be observed on a higher level as the problem masks itself under the term “slow VLAN”. To clarify, this document defines the following new terms: “slow collision domain”, “slow broadcast domain” (in other words, slow VLAN), and “slow interVLAN forwarding”. These are defined in the section Three Categories of Causes, below. In the following scenario (illustrated in the network diagram below), there is a Layer 3 (L3) switch performing interVLAN routing between the server and client VLANs. In this failure scenario, one server is connected to a switch, and the port duplex mode is configured half- duplex on the server side and full-duplex on the switch side. This misconfiguration results in a packet loss and slowness, with increased packet loss when higher traffic rates occur on the link where the server is connected. For the clients who communicate with this server, the problem looks like slow interVLAN forwarding because they do not have a problem communicating to other devices or clients on the same VLAN. The problem occurs only when communicating to the server on a different VLAN. Thus, the problem occurred on a single collision domain, but is seen as slow interVLAN forwarding.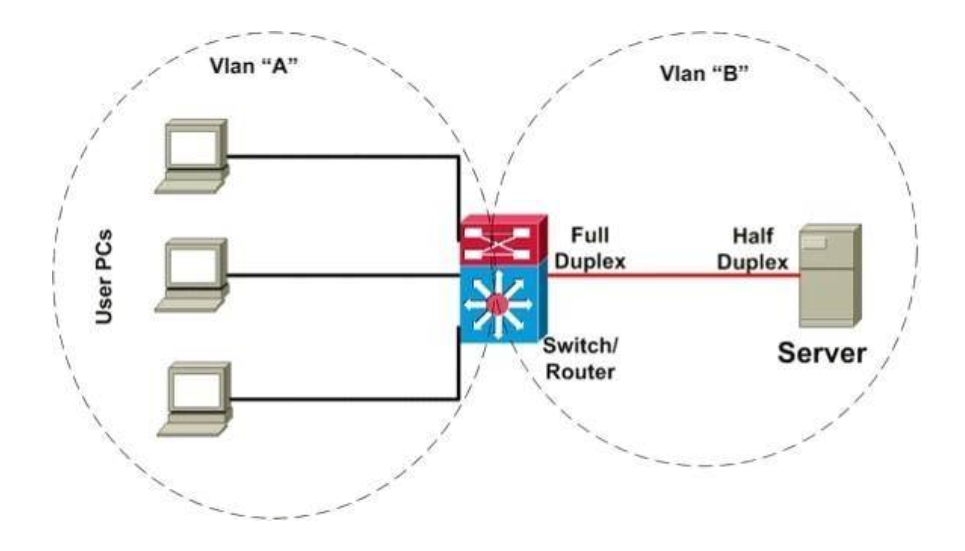 Three Categories of Causes
The causes of slowness can be divided into three categories, as follows:
Slow Collision Domain Connectivity
Collision domain is defined as connected devices configured in a half-duplex port configuration, connected to each other or a hub. If a device is connected to a switch port and full-duplex mode is configured, such a pointto-point connection is collisionless. Slowness on such a segment still can occur for different reasons.
Slow Broadcast Domain Connectivity (Slow VLAN)
Slow broadcast domain connectivity occurs when the whole VLAN (that is, all devices on the same VLAN)
experiences slowness.
Slow InterVLAN Connectivity (Slow Forwarding Between VLANs) Slow interVLAN connectivity (slow forwarding between VLANs) occurs when there is no slowness on the local VLAN, but traffic needs to be forwarded to an alternate VLAN, and it is not forwarded at the expected rate.
Causes for Network Slowness
Packet Loss
In most cases, a network is considered slow when higher-layer protocols (applications) require extended time to complete an operation that typically runs faster. That slowness is caused by the loss of some packets on the network, which causes higher-level protocols like TCP or applications to time out and initiate retransmission.
Hardware Forwarding Issues
With another type of slowness, caused by network equipment, forwarding (whether Layer 2 [L2] or L3) is performed slowly. This is due to a deviation from normal (designed) operation and switching to slow path forwarding. An example of this is when Multilayer Switching (MLS) on the switch forwards L3 packets between
VLANs in the hardware, but due to misconfiguration, MLS is not functioning properly and forwarding is done by the router in the software (which drops the interVLAN forwarding rate significantly).
Three Categories of Causes
The causes of slowness can be divided into three categories, as follows:
Slow Collision Domain Connectivity
Collision domain is defined as connected devices configured in a half-duplex port configuration, connected to each other or a hub. If a device is connected to a switch port and full-duplex mode is configured, such a pointto-point connection is collisionless. Slowness on such a segment still can occur for different reasons.
Slow Broadcast Domain Connectivity (Slow VLAN)
Slow broadcast domain connectivity occurs when the whole VLAN (that is, all devices on the same VLAN)
experiences slowness.
Slow InterVLAN Connectivity (Slow Forwarding Between VLANs) Slow interVLAN connectivity (slow forwarding between VLANs) occurs when there is no slowness on the local VLAN, but traffic needs to be forwarded to an alternate VLAN, and it is not forwarded at the expected rate.
Causes for Network Slowness
Packet Loss
In most cases, a network is considered slow when higher-layer protocols (applications) require extended time to complete an operation that typically runs faster. That slowness is caused by the loss of some packets on the network, which causes higher-level protocols like TCP or applications to time out and initiate retransmission.
Hardware Forwarding Issues
With another type of slowness, caused by network equipment, forwarding (whether Layer 2 [L2] or L3) is performed slowly. This is due to a deviation from normal (designed) operation and switching to slow path forwarding. An example of this is when Multilayer Switching (MLS) on the switch forwards L3 packets between
VLANs in the hardware, but due to misconfiguration, MLS is not functioning properly and forwarding is done by the router in the software (which drops the interVLAN forwarding rate significantly). -
Question 145 of 188
145. Question
1 pointsWhich option describes how a switch in rapid PVST+ mode responds to a topology change?Correct
Incorrect
Hint
Rapid PVST+This spanning-tree mode is the same as PVST+ except that is uses a rapid convergence based on the IEEE 802.1w standard. To provide rapid convergence, the rapid PVST+ immediately deletes dynamically learned MAC address entries on a per-port basis upon receiving a topology change. By contrast, PVST+ uses a short aging time for dynamically learned MAC address entries. The rapid PVST+ uses the same configuration as PVST+ (except where noted), and the switch needs only minimal extra configuration. The benefit of rapid PVST+ is that you can migrate a large PVST+ install base to rapid PVST+ without having to learn the complexities of the MSTP configuration and without having to reprovision your network. In rapid-PVST+ mode, each VLAN runs its own spanning-tree instance up to the maximum supported. -
Question 146 of 188
146. Question
1 pointsWhich statement about switch access ports is true?Correct
Incorrect
Hint
A VLAN does not need to be assigned to any port -> B is not correct. An access port can only receive traffic from one VLAN -> C is not correct. If not assigned to a specific VLAN, an access port carries traffic for VLAN 1 by default -> D is not correct. An access port will drop packets with 802.1Q tags -> A is correct. Notice that 802.1Q tags are used to packets moving on trunk links. -
Question 147 of 188
147. Question
1 pointsWhich two switch states are valid for 802.1w? (Choose two.)Correct
Incorrect
Hint
IEEE 802.1w is Rapid Spanning Tree Protocol (RSTP). There are only three port states left in RSTP that correspond to the three possible operational states. The 802.1D disabled, blocking, and listening states are merged into the 802.1w discarding state. * Discarding – the port does not forward frames, process received frames, or learn MAC addresses – but it does listen for BPDUs (like the STP blocking state) * Learning – receives and transmits BPDUs and learns MAC addresses but does not yet forward frames (same as STP). * Forwarding – receives and sends data, normal operation, learns MAC address, receives and transmits BPDUs (same as STP). -
Question 148 of 188
148. Question
1 pointsWhich feature allows a device to use a switch port that is configured for half-duplex to access the network?Correct
Incorrect
Hint
Ethernet began as a local area network technology that provided a half-duplex shared channel for stations connected to coaxial cable segments linked with signal repeaters. In this appendix, we take a detailed look at the half-duplex shared-channel mode of operation, and at the CSMA/CD mechanism that makes it work. In the original half-duplex mode, the CSMA/CD protocol allows a set of stations to compete for access to a shared Ethernet channel in a fair and equitable manner. The protocol’s rules determine the behavior of Ethernet stations, including when they are allowed to transmit a frame onto a shared Ethernet channel, and what to do when a collision occurs. Today, virtually all devices are connected to Ethernet switch ports over full-duplex media, such as twisted-pair cables. On this type of connection, assuming that both devices can support the full-duplex mode of operation and that Auto-Negotiation (AN) is enabled, the AN protocol will automatically select the highest-performance mode of operation supported by the devices at each end of the link. That will result in full-duplex mode for the vast majority of Ethernet connections with modern interfaces that support full duplex and AN. -
Question 149 of 188
149. Question
1 pointsWhich two statements about switch stacking are true? (Choose two)Correct
Incorrect
-
Question 150 of 188
150. Question
1 pointsWhich symptom most commonly indicates that two connecting interfaces are configured with a duplex mismatch?Correct
Incorrect
Hint
A late collision is defined as any collision that occurs after the first 512 bits of the frame have been transmitted. The usual possible causes are full-duplex/half-duplex mismatch, exceeded Ethernet cable length limits, or defective hardware such as incorrect cabling, non-compliant number of hubs in the network, or a bad NIC. Note: On an Ethernet connection, a duplex mismatch is a condition where two connected devices operate in different duplex modes, that is, one operates in half duplex while the other one operates in full duplex. Duplex mismatch would not cause the link to be down/down, but would only result in poor performance like increase late collisions on the interface. -
Question 151 of 188
151. Question
1 pointsWhich option is the main function of congestion management?Correct
Incorrect
-
Question 152 of 188
152. Question
1 pointsWhich feature must you enable to distribute vlans automatically across multiple switch?Correct
Incorrect
-
Question 153 of 188
153. Question
1 pointsWhich three statements about VTP features are true? (Choose three.)Correct
Incorrect
-
Question 154 of 188
154. Question
1 pointsWhich two statements about LLDP are true ?(choose two)Correct
Incorrect
-
Question 155 of 188
155. Question
1 pointsWhich two benefits can you get by stacking Cisco switches?(choose two)Correct
Incorrect
Hint
Each stack has only one configuration file, which is distributed to each member in the stack. This allows each switch in the stack to share the same network topology, MAC address, and routing information. In addition, it allows for any member to become the master, if the master ever fails -> Answer D is correct while answer A is not correct. Switches can be added and deleted to a working stack without affecting stack performance. When a new switch is added, the master switch automatically configures the unit with the currently running Cisco IOS Software image and configuration of the stack. The stack will gather information such as switching table information and update the MAC tables as new addresses are learned. The network manager does not have to do anything to bring up the switch before it is ready to operate. Similarly, switches can be removed from a working stack without any operational effect on the remaining switches. When the stack discovers that a series of ports is no longer present, it will update this information without affecting forwarding or routing. A working stack can accept new members or delete old ones without service interruption -> Answer B is correct. Reference: https://www.cisco.com/c/en/us/products/collateral/switches/catalyst-3750-series-switches/prod_white_paper09186a00801b096a.html -
Question 156 of 188
156. Question
1 pointsWhich VTP mode cannot make a change to vlan?Correct
Incorrect
Hint
VTP Client · VTP clients function the same way as VTP servers, but you cannot create, change, or delete VLANs on a VTP client. · A VTP client only stores the VLAN information for the entire domain while the switch is on. · A switch reset deletes the VLAN information. · You must configure VTP client mode on a switch. -
Question 157 of 188
157. Question
1 pointsWhich two circumstances can cause collision domain issues on VLAN domain? (Choose two)Correct
Incorrect
Hint
On an Ethernet connection, a duplex mismatch is a condition where two connected devices operate in different duplex modes, that is, one operates in half duplex while the other one operates in full duplex. Duplex mismatch can easily cause collision domain issue as the device that operates in full duplex mode turns off CSMA/CD. So it is eager to send data immediately without checking if the link is free to use -> A is correct. An “inband path” is the path which provides path for management traffic (like CDP, VTP, PAgP…) but we are not sure why congestion on the switch inband path can cause collision domain issues. Maybe congestion on inband path prevents the JAM signal (sent when a collision occurs on the link) to be sent correctly on the link. -
Question 158 of 188
158. Question
1 pointsWhich protocol supports sharing the VLAN configuration between two or more switches?Correct
Incorrect
Hint
VTP allows a network manager to configure a switch so that it will propagate VLAN configurations to other switches in the network” VTP minimizes misconfigurations and configuration inconsistencies that can cause problems, such as duplicate VLAN names or incorrect VLAN-type specifications. VTP helps you simplify management of the VLAN database across multiple switches. VTP is a Cisco-proprietary protocol and is available on most of the Cisco switches -
Question 159 of 188
159. Question
1 pointsWhich spanning-tree feature places a port immediately into a forwarding stated?Correct
Incorrect
Hint
PortFast causes a switch or trunk port to enter the spanning tree forwarding state immediately, bypassing the listening and learning states. You can use PortFast on switch or trunk ports that are connected to a single workstation, switch, or server to allow those devices to connect to the network immediately, instead of waiting for the port to transition from the listening and learning states to the forwarding state. -
Question 160 of 188
160. Question
1 pointsIn which STP state does MAC address learning take place on a PortFast-enabled port?Correct
Incorrect
-
Question 161 of 188
161. Question
1 pointsRefer to the exhibit. A network associate needs to configure the switches and router in the graphic so that the hosts in VLAN3 and VLAN4 can communicate with the enterprise server in VLAN2. Which two Ethernet segments would need to be configured as trunk links? (Choose two.)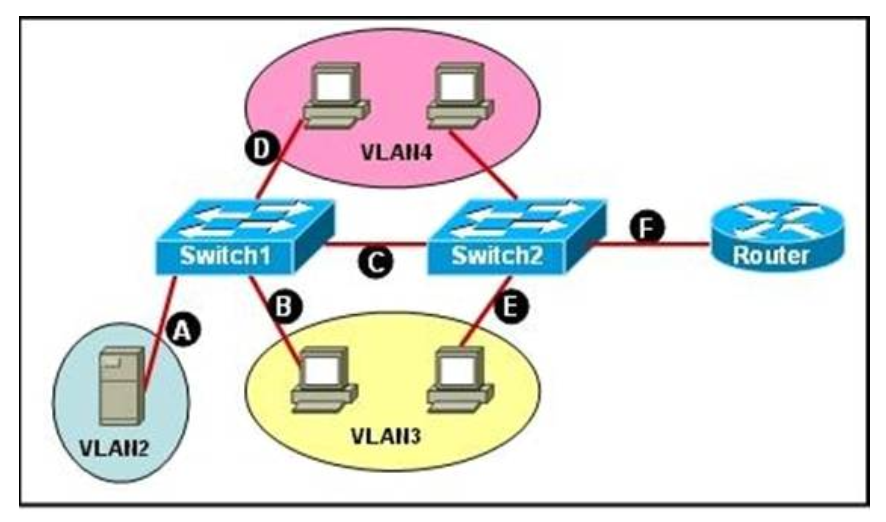 Correct
Correct
Incorrect
-
Question 162 of 188
162. Question
1 pointsWhich IEEE standard does PVST+ use to tunnel information?Correct
Incorrect
Hint
Cisco developed PVST+ to allow strolling numerous STP instances, even over an 802.1Q network via the use of a tunneling mechanism. PVST+ utilizes Cisco gadgets to hook up with a Mono Spanning Tree area to a PVST+ region. No particular configuration is needed to attain this. PVST+ affords assist for 802.1Q trunks and the mapping of a couple of spanning trees to the single spanning tree of popular 802.1Q switches strolling Mono Spanning Tree. -
Question 163 of 188
163. Question
1 pointsWhat is the default VLAN on an access port?Correct
Incorrect
Hint
If we configure an access port as follows:Switch(config)#interface fa0/1 Switch(config-if)#switchport mode access
Then this interface, by default, will belong to VLAN 1. Of course we can assign another VLAN to this port via the “switchport access vlan {vlan-number}” command. -
Question 164 of 188
164. Question
1 pointsWhich VTP mode prevents you from making changes to VLANs?Correct
Incorrect
-
Question 165 of 188
165. Question
1 pointsOn which type of port can switches interconnect for multi-VLAN communication?Correct
Incorrect
-
Question 166 of 188
166. Question
1 pointsWhich two of these statements regarding RSTP are correct? (Choose two)Correct
Incorrect
-
Question 167 of 188
167. Question
1 pointsIf primary and secondary root switches with priority 16384 both experience catastrophic losses, which tertiary switch can take over?Correct
Incorrect
Hint
This is a tricky question. We know the switch with lowest value of priority is elected the root switch. Therefore in this question the switches with priority of 4096, 8192, 12288 (which are lower than the current value of the root bridge 16384) are not joining the root bridge election by somehow. The only suitable answer is the switch with priority 20480 will become the root bridge. -
Question 168 of 188
168. Question
1 pointsWhat is true about Ethernet? (Choose Two.)Correct
Incorrect
Hint
Carrier sense multiple access with collision detection (CSMA/CD) is a media access control method used most notably in early Ethernet (IEEE 802.3) technology for local area networking. When collision detection (CD) observes a collision (excess current above what it is generating, i.e. > 24 mA for coaxial Ethernet), it stops transmission immediately and instead transmits a 32-bit jam sequence. Note: CSMA/CA (Carrier Sense Multiple Access/Collision Avoidance) is a protocol for carrier transmission used in wireless networks. Unlike CSMA/CD (Carrier Sense Multiple Access/Collision Detect) which deals with transmissions after a collision has occurred, CSMA/CA acts to prevent collisions before they happen. -
Question 169 of 188
169. Question
1 pointsWhat field is consisted of 6 bytes in the field identification frame in IEEE 802.1Q?Correct
Incorrect
-
Question 170 of 188
170. Question
1 pointsWhich three options are switchport configurations that can always avoid duplex mismatch errors between theswitches? (Choose three.)Correct
Incorrect
-
Question 171 of 188
171. Question
1 pointsWhich technology can enable multiple VLANs to communicate with one another?Correct
Incorrect
-
Question 172 of 188
172. Question
1 pointsRefer to the exhibit. Which two statements are true about interVLAN routing in the topology that is shown in the exhibit? (Choose two.)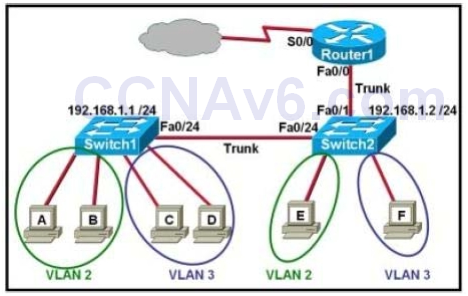 Correct
Correct
Incorrect
Hint
In order for multiple VLANs to connect to a single physical interface on a Cisco router, subinterfaces must be used, one for each VLAN. This is known as the router on a stick configuration. Also, for any trunk to be formed, both ends of the trunk must agree on the encapsulation type, so each one must be configured for 802.1q or ISL. -
Question 173 of 188
173. Question
1 pointsWhat value is primarily used to determine which port becomes the root port on each non-root switch in a spanning-tree topology?Correct
Incorrect
Hint
The path cost to the root bridge is the most important value to determine which port will become the root port on each non-root switch. In particular, the port with lowest cost to the root bridge will become root port (on non-root switch). -
Question 174 of 188
174. Question
1 pointsHow is provided master redundancy on a stacked switches?Correct
Incorrect
Hint
1:N master redundancy: Every switch in the stack can act as the master. If the current master fails, another master is elected from the stack. 1:N master redundancy allows each stack member to serve as a master, providing the highest reliability for forwarding. Each switch in the stack can serve as a master, creating a 1:N availability scheme for network control. In the unlikely event of a single unit failure, all other units continue to forward traffic and maintain operation. Reference: http://www.cisco.com/c/en/us/products/collateral/switches/catalyst-3750-series-switches/prod_white_paper09186a00801b096a.html Note: N+1 simply means that there is a power backup in place should any single system component fail. The ‘N’ in this equation stands for the number of components necessary to run your system. The ‘+1’ means there is one independent backup should a component of that system fail. An example of “N+1” is your family has 5 members, so you need 5 cups to drink. But you have one extra cup for redundancy (6 cups in total) so that if any cup breaks, you still have enough cups for the family. -
Question 175 of 188
175. Question
1 pointsWhich three elements must be used when you configure a router interface for VLAN trunking? (Choose three.)Correct
Incorrect
Hint
This scenario is commonly called a router on a stick. A short, well written article on this operation can be found here: http://www.thebryantadvantage.com/RouterOnAStickCCNACertificationExamTutorial.htm -
Question 176 of 188
176. Question
1 pointsRefer to the exhibit. A network administrator is configuring an EtherChannel between SW1 and SW2. The SW1 configuration is shown. What is the correct configuration for SW2?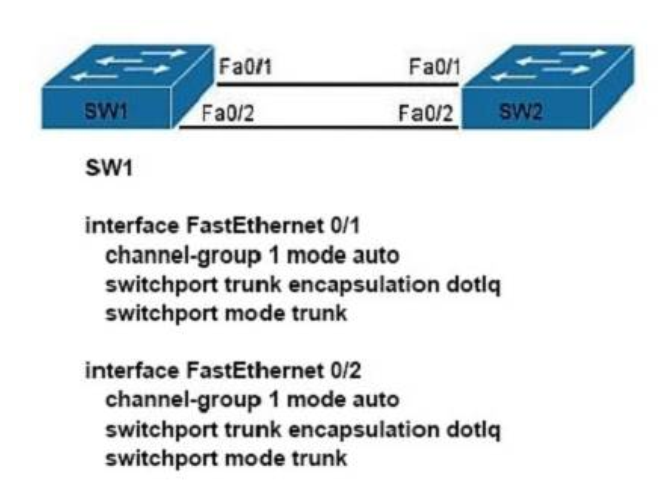 Correct
Correct
Incorrect
-
Question 177 of 188
177. Question
1 pointsRefer to the exhibit. After HostA pings HostB, which entry will be in the ARP cache of HostA to support this transmission?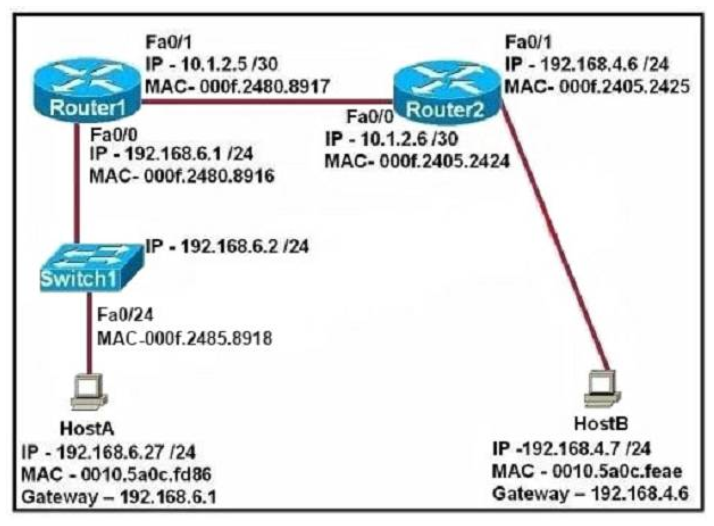 Correct
Correct
Incorrect
Hint
When a host needs to reach a device on another subnet, the ARP cache entry will be that of the Ethernet address of the local router (default gateway) for the physical MAC address. The destination IP address will not change, and will be that of the remote host (HostB). -
Question 178 of 188
178. Question
1 pointsBased on the output below from SwitchB, which statement is true?Correct
Incorrect
-
Question 179 of 188
179. Question
1 pointsA router has two Fast Ethernet interfaces and needs to connect to four VLANs in the local network. How can you accomplish this task, using the fewest physical interfaces and without decreasing network performance?Correct
Incorrect
Hint
A router on a stick allows you to use sub-interfaces to create multiple logical networks on a single physical interface. -
Question 180 of 188
180. Question
1 pointsRefer to the exhibit, The VLAN configuration of S1 is not being in this VTP enabled environment. The VTP and uplink port configurations for each switch are displayed. Which two command sets, if issued, resolve this failure and allow VTP to operate as expected? (Choose two.)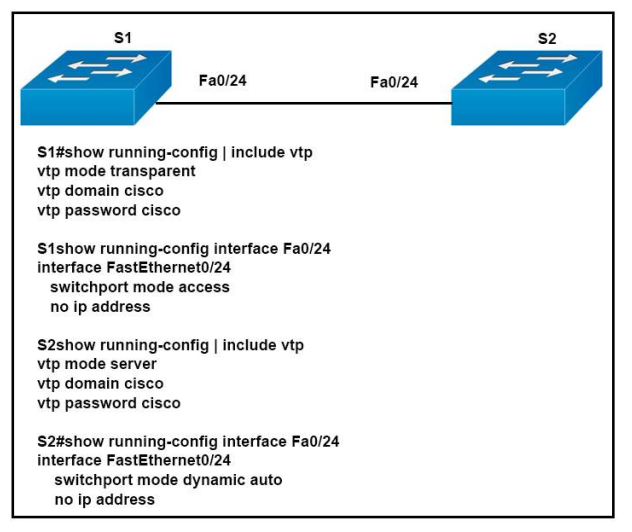 Correct
Correct
Incorrect
-
Question 181 of 188
181. Question
1 pointsHow are VTP advertisements delivered to switches across the network?Correct
Incorrect
-
Question 182 of 188
182. Question
1 pointsWhat are two reasons a network administrator would use CDP? (Choose two.)Correct
Incorrect
-
Question 183 of 188
183. Question
1 pointsHow can you manually configure a switch so that it is selected as the root Switch?Correct
Incorrect
-
Question 184 of 188
184. Question
1 pointsWhich three options are switch port config that can always avoid duplex mismatch error between the switches? (Choose three.)Correct
Incorrect
-
Question 185 of 188
185. Question
1 pointsWhich option is the master redundancy scheme for stacked switches?Correct
Incorrect
-
Question 186 of 188
186. Question
1 pointsUnder which two circumstances is a switch port that is configured with PortFast BPDU guard error-disabled? (Choose two.)Correct
Incorrect
-
Question 187 of 188
187. Question
1 pointsDRAG DROP. Drag and drop the STP features from the left onto the correct descriptions on the right. Select and Place: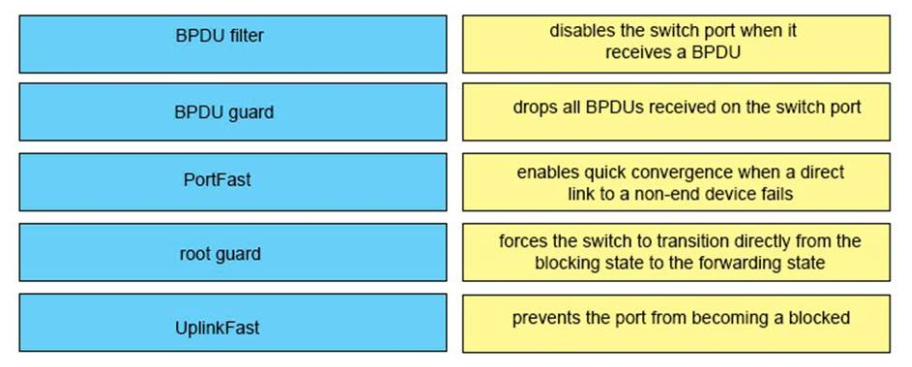
Sort elements
- BPDU guard
- BPDU filter
- UplinkFast
- PortFast
- root guard
-
disables the switch port when it receives a BPDU
-
drops all BPDUs received on the switch port
-
enables quick convergence when a direct link to a non-end devices fails
-
forces the switch to transition directly from the blocking state to the forwarding state
-
prevents the port from becoming a blocked
Correct
Incorrect
-
Question 188 of 188
188. Question
1 pointsDRAG DROP. Drag and drop the MAC address types from the left onto the correct descriptions on the right? Select and Place: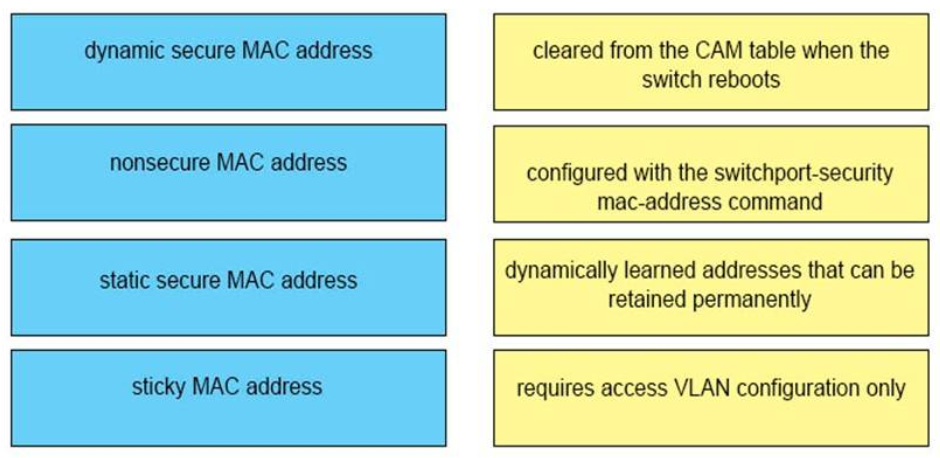
Sort elements
- nonsecure MAC address
- sticky MAC address
- dynamic secure MAC address
- static secure MAC address
-
cleared from the CAM table when the switch reboots
-
configured with the switchport-security mac-address command
-
dynamically learned address that can be retained permanently
-
requires access VLAN configuration only
Correct
Incorrect