Time limit: 0
Quiz-summary
0 of 92 questions completed
Questions:
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
Information
Section VII: Infrastructure Management - Test online
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading...
You must sign in or sign up to start the quiz.
You have to finish following quiz, to start this quiz:
Results
0 of 92 questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 points, (0)
| Average score |
|
| Your score |
|
Categories
- Not categorized 0%
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- Answered
- Review
-
Question 1 of 92
1. Question
1 pointsWhich command is used to show the interface status of a router?Correct
Incorrect
Hint
The “show ip interface brief” command can be used to view a summary of the router interfaces. This command displays the IP address, interface status, and additional information. An example of the “show ip interface brief” command is shown below. We can see the interface status of E0/0 is “up/up”.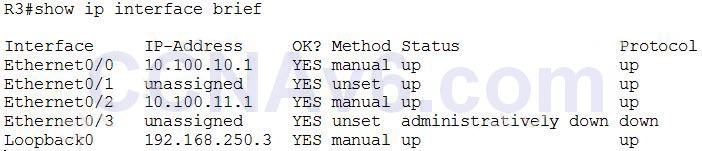
-
Question 2 of 92
2. Question
1 pointsAfter you configure the Loopback0 interface, Which command can you enter to verify the status of the interface and determine whether fast switching is enabled?Correct
Incorrect
Hint
Output from real device Router2901#sh int g0/0 GigabitEthernet0/0 is up, line protocol is up Hardware is CN Gigabit Ethernet, address is c471.fe99.9999 (bia c471.fe99.9999) Description: Lan Internet address is 10.1.1.1/25 MTU 1500 bytes, BW 1000000 Kbit/sec, DLY 10 usec, reliability 255/255, txload 1/255, rxload 1/255 Encapsulation ARPA, loopback not set Keepalive set (10 sec) Full Duplex, 1Gbps, media type is RJ45 output flow-control is unsupported, input flow-control is unsupported ARP type: ARPA, ARP Timeout 04:00:00 Last input 00:00:00, output 00:00:00, output hang never Last clearing of “show interface” counters never Input queue: 0/75/61/0 (size/max/drops/flushes); Total output drops: 0 Queueing strategy: fifo Output queue: 0/40 (size/max) 5 minute input rate 39000 bits/sec, 30 packets/sec 5 minute output rate 73000 bits/sec, 37 packets/sec 41068530 packets input, 3905407112 bytes, 0 no buffer Received 8678853 broadcasts (0 IP multicasts) 0 runts, 0 giants, 45 throttles 0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored 0 watchdog, 79853 multicast, 0 pause input 39267208 packets output, 2262399504 bytes, 0 underruns 0 output errors, 0 collisions, 0 interface resets 79926 unknown protocol drops 0 babbles, 0 late collision, 0 deferred 0 lost carrier, 0 no carrier, 0 pause output 0 output buffer failures, 0 output buffers swapped out Router2901# Router2901 ip int g0/0 GigabitEthernet0/0 is up, line protocol is up Internet address is 10.1.1.1/25 Broadcast address is 255.255.255.255 Address determined by non-volatile memory MTU is 1500 bytes Helper address is not set Directed broadcast forwarding is disabled Secondary address 192.168.1.7/24 Multicast reserved groups joined: 224.0.0.10 Outgoing access list is not set Inbound access list is not set Proxy ARP is enabled Local Proxy ARP is disabled Security level is default Split horizon is enabled ICMP redirects are always sent ICMP unreachables are always sent ICMP mask replies are never sent IP fast switching is enabled IP fast switching on the same interface is disabled IP Flow switching is disabled IP CEF switching is enabled IP CEF switching turbo vector IP multicast fast switching is enabled IP multicast distributed fast switching is disabled IP route-cache flags are Fast, CEF Router Discovery is disabled IP output packet accounting is disabled IP access violation accounting is disabled TCP/IP header compression is disabled RTP/IP header compression is disabled Policy routing is disabled Network address translation is enabled, interface in domain inside BGP Policy Mapping is disabled Input features: Common Flow Table, Stateful Inspection, Virtual Fragment Reassembly, Virtual Fragment Reassembly After IPSec Decryption, CAR, MCI Check Output features: NAT Inside, Common Flow Table, Stateful Inspection, NAT ALG proxy, CAR Post encapsulation features: CAR IPv4 WCCP Redirect outbound is disabled IPv4 WCCP Redirect inbound is disabled IPv4 WCCP Redirect exclude is disabled Router2901# -
Question 3 of 92
3. Question
1 pointsIn Which CLI configuration mode can you configure the hostname of a device?Correct
Incorrect
-
Question 4 of 92
4. Question
1 pointsWhich command can you use to set the hostname on a switch?Correct
Incorrect
-
Question 5 of 92
5. Question
1 pointsWhich logging command can enable administrators to correlate syslog messages with millisecond precision?Correct
Incorrect
Hint
The “service timestamps log” command configures the system to apply a time stamp to logging messages. The time-stamp format for datetime is MMM DD HH:MM:SS, where MMM is the month, DD is the date, HH is the hour (in 24-hour notation), MM is the minute, and SS is the second. With the additional keyword msec, the system includes milliseconds in the time stamp, in the format HH:DD:MM:SS.mmm, where .mmm is milliseconds. -
Question 6 of 92
6. Question
1 pointsWhich function of the IP SLAs ICMP jitter operation can you use to determine whether a VoIP issue is caused by excessive end-to-end time?Correct
Incorrect
-
Question 7 of 92
7. Question
1 pointsWhich two statements about northbound and southbound APIs are true? (Choose two.)Correct
Incorrect
Hint
A northbound interface is an interface that allows a particular component of a network to communicate with a higher-level component. Conversely, a southbound interface allows a particular network component to communicate with a lower-level component.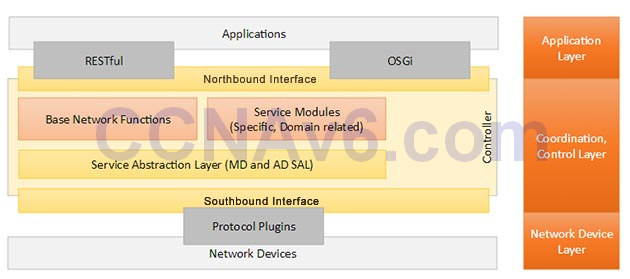 The northbound APIs on an SDN controller enable applications and orchestration systems to program the network and request services from it.
Southbound interfaces are implemented with a Service Abstraction Layer (SAL) Which speak to network devices using SNMP and CLI (Command Line Interface) of the elements that make up the network. The main functions of SAL are:
+ Expose device services and capabilities to apps
+ Determine how to fulfill requested service irrespective of the underlying protocol
Note:
+ An API is a method for one application (program) to exchange data with another application.
+ Interface here refers to the “software interface”, not the physical interfaces.
The northbound APIs on an SDN controller enable applications and orchestration systems to program the network and request services from it.
Southbound interfaces are implemented with a Service Abstraction Layer (SAL) Which speak to network devices using SNMP and CLI (Command Line Interface) of the elements that make up the network. The main functions of SAL are:
+ Expose device services and capabilities to apps
+ Determine how to fulfill requested service irrespective of the underlying protocol
Note:
+ An API is a method for one application (program) to exchange data with another application.
+ Interface here refers to the “software interface”, not the physical interfaces. -
Question 8 of 92
8. Question
1 pointsWhile viewing the running configuration of a router, you observe the command logging trap warning. Which syslog messages will the router send?Correct
Incorrect
-
Question 9 of 92
9. Question
1 pointsWhich statement about SNMPv2 is true?Correct
Incorrect
Hint
Default values do not exist for authentication or privacy algorithms when you configure the SNMP commands. Also, no default passwords exist. The minimum length for a password is one character, although we recommend that you use at least eight characters for security. If you forget a password, you cannot recover it and must reconfigure the user. You can specify either a plain text password or a localized Message Digest 5 (MD5) digest. Reference: https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/snmp/configuration/xe-3se/3850/snmp-xe-3se-3850-book/nm-snmp-snmpv2c.pdf -
Question 10 of 92
10. Question
1 pointsWhich two statements about the extended traceroute command are true? (Choose two.)Correct
Incorrect
-
Question 11 of 92
11. Question
1 pointsRefer to the exhibit. You have determined that computer A cannot ping computer B. Which reason for the problem is most likely true?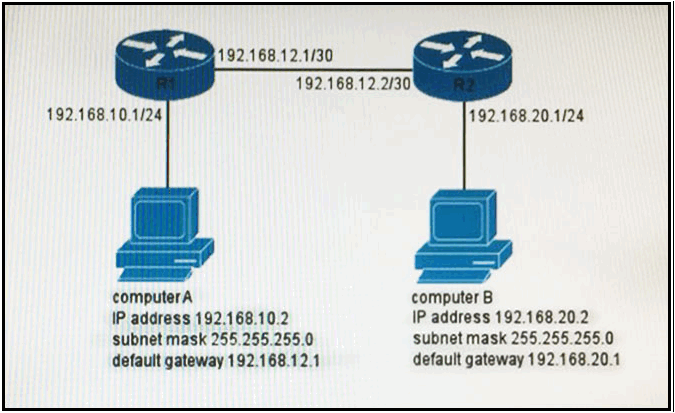 Correct
Correct
Incorrect
-
Question 12 of 92
12. Question
1 pointsIf you configure syslog messages without specifying the logging trap level, Which log messages will the router send?Correct
Incorrect
-
Question 13 of 92
13. Question
1 pointsWhich two statements about syslog logging are true?Correct
Incorrect
Hint
By default if we type “show logging” command we will see the Syslog logging has been enabled -> A is not correct.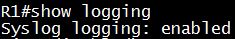 The syslog messages are stored in the internal buffer of the device. The buffer size is limited to few kilobytes. However, when the device reboots, these syslog messages are lost -> B is correct; C is correct; D is not correct.
The syslog messages are stored in the internal buffer of the device. The buffer size is limited to few kilobytes. However, when the device reboots, these syslog messages are lost -> B is correct; C is correct; D is not correct. -
Question 14 of 92
14. Question
1 pointsWhat is the purpose of the POST operation on a router?Correct
Incorrect
Hint
In short, when powered on the router needs to do: 1. Run POST to check hardware 2. Search for a valid IOS (the Operating System of the router) 3. Search for a configuration file (all the configurations applied to this router) -
Question 15 of 92
15. Question
1 pointsWhich function does the IP SLAs ICMP Echo operation perform to assist with troubleshooting?Correct
Incorrect
-
Question 16 of 92
16. Question
1 pointsWhich three commands can you use to set a router boot image? (Choose three.)Correct
Incorrect
Hint
The correct syntax of the “boot” command is “boot system” path. In Which the popular for path can be: + flash + rom + tftp + ftp + IP address (IP address of the server containing the system image file) Therefore answers A, B, C are correct. -
Question 17 of 92
17. Question
1 pointsA Cisco router is booting and has just completed the POST process. It is now ready to find and load an IOS image. What function does the router perform next?Correct
Incorrect
Hint
When you turn the router on, it runs through the following boot process. The Power-On Self Test (POST) checks the router’s hardware. When the POST completes successfully, the System OK LED indicator comes on. The router checks the configuration register to identify where to load the IOS image from. A setting of 0×2102 means that the router will use information in the startup-config file to locate the IOS image. If the startup-config file is missing or does not specify a location, it will check the following locations for the IOS image: 1. Flash (the default location) 2. TFTP server 3. ROM (used if no other source is found) The router loads the configuration file into RAM (Which configures the router). The router can load a configuration file from: + NVRAM (startup-configuration file) + TFTP server If a configuration file is not found, the router starts in setup mode. -
Question 18 of 92
18. Question
1 pointsIf you are configuring syslog messages specifying `logging trap warning’, Which log messages will the router send?Correct
Incorrect
Hint
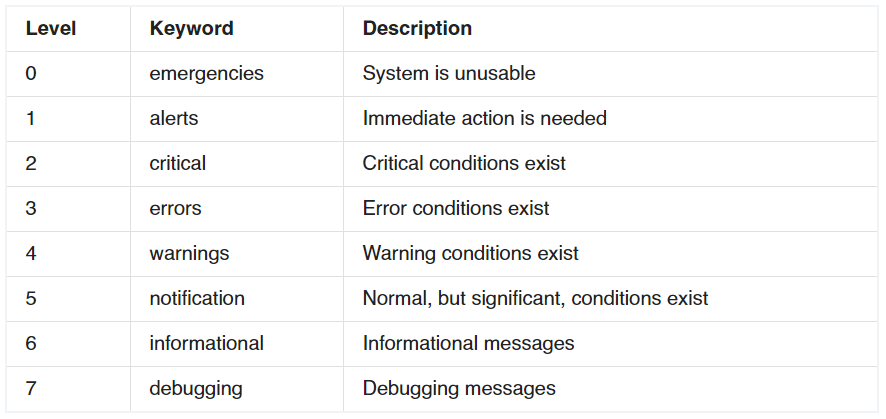
0 emergencies System is unusable 1 alerts Immediate action is needed 2 critical Critical conditions exist 3 errors Error conditions exist 4 warnings Warning conditions exist 5 notification Normal, but significant, conditions exist 6 informational Informational messages 7 debugging Debugging messages -
Question 19 of 92
19. Question
1 pointsWhich function does the IP SLA ICMP ECHO operation perform to assist with troubleshooting?Correct
Incorrect
-
Question 20 of 92
20. Question
1 pointsIf you configure syslog messages without specifying the logging trap level, Which log messages will the router send?Correct
Incorrect
Hint
Router(config)# logging trap level – Specifies the kind of messages, by severity level, to be sent to the syslog server. The default is informational (6) and lower ( 0 6). The possible values for level are as follows: Emergency: 0 Alert: 1 Critical: 2 Error: 3 Warning: 4 Notice: 5 Informational: 6 Debug: 7 -
Question 21 of 92
21. Question
1 pointsWhich command can you execute to set the user inactivity timer to 10 seconds?Correct
Incorrect
Hint
The “exec-timeout” command is used to configure the inactive session timeout on the console port or the virtual terminal. The syntax of this command is: exec-timeout minutes [seconds] Therefore we need to use the “exec-timeout 0 10” command to set the user inactivity timer to 10 seconds. -
Question 22 of 92
22. Question
1 pointsHow do you configure a hostname?Correct
Incorrect
-
Question 23 of 92
23. Question
1 pointsWhich command is necessary to permit SSH or Telnet access to a cisco switch that is otherwise configured for these vty line protocols?Correct
Incorrect
Hint
The “transport input” command is used to define Which protocols to use to connect to a specific line (vty, console, aux…) of the router. The “transport input all” command will allow all protocols (including SSH and Telnet) to do this. -
Question 24 of 92
24. Question
1 pointsWhich two Cisco IOS commands, used in troubleshooting, can enable debug output to a remote location? (Choose two)Correct
Incorrect
Hint
The “no logging console” turns off logging to the console connection (it is turned on by default) and it is often used if the console received large amount of logging output. But this command is not recommended in normal configuration -> A is not correct. The command “logging host ip-address” instructs the device to send syslog messages to an external syslog server -> B is correct. The “show logging | redirect flashioutput.txt” command will put the text file in the router flash memory because we did not specify a remote location (like tftp) -> D is not correct. The command “snmp-server enable traps syslog” instructs the device to send syslog messages to your network management server as SNMP traps instead of syslog packets. This command itself does not enable debug output to a remote location -> E is not correct. By default, Cisco IOS does not send log messages to a terminal session over IP, that is, telnet or SSH connections don’t get log messages. But notice that console connections on a serial cable do have logging enabled by default. The command “terminal monitor” helps logging messages appear on the your terminal. First we don’t think this is a correct answer but after reading the question again, we believe it is a suitable one as a Telnet/SSH session may be considered a “remote location” -> C is correct. -
Question 25 of 92
25. Question
1 pointsWhich two options are features of the extended ping command? (Choose two.)Correct
Incorrect
Hint
There are many options to choose when using extended ping. Below shows the options that we can choose: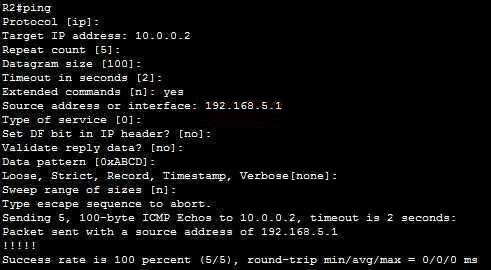 In which:
+ Repeat count [5]: Number of ping packets that are sent to the destination address. The default is 5 -> A is correct.
+ Source address or interface: The interface or IP address of the router to use as a source address for the probes -> B is correct.
For more information about extended ping, please read: http://www.cisco.com/c/en/us/support/docs/ip/routing-information-protocol-rip/13730-ext-ping-trace.html
In which:
+ Repeat count [5]: Number of ping packets that are sent to the destination address. The default is 5 -> A is correct.
+ Source address or interface: The interface or IP address of the router to use as a source address for the probes -> B is correct.
For more information about extended ping, please read: http://www.cisco.com/c/en/us/support/docs/ip/routing-information-protocol-rip/13730-ext-ping-trace.html -
Question 26 of 92
26. Question
1 pointsWhat is the cause of the Syslog output messages?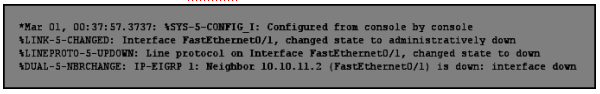 Correct
Correct
Incorrect
Hint
From the second line of the output, we learned that Fa0/1 interface was shut down so we see the “changed state to administratively down”. The third and fourth line is the result of this action, Which cause Fa0/1 interface “changed state to down” and the EIGRP neighbor relationship with 10.10.11.2 was down. -
Question 27 of 92
27. Question
1 pointsWhy is flash memory erased prior to upgrading the IOS image from the TFTP server?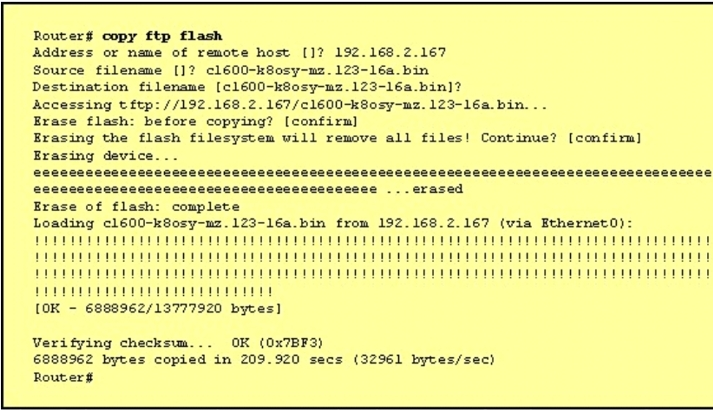 Correct
Correct
Incorrect
Hint
During the copy process, the router asked “Erasing flash before copying? [confirm]” and the administrator confirmed (by pressing Enter) so the flash was deleted. Note: In this case, the flash has enough space to copy a new IOS without deleting the current one. The current IOS is deleted just because the administrator wants to do so. If the flash does not have enough space you will see an error message like this: %Error copying tftp://192.168.2.167/ c1600-k8sy-mz.l23-16a.bin (Not enough space on device) -
Question 28 of 92
28. Question
1 pointsIn Which two situations should you use out-of-band management?Correct
Incorrect
-
Question 29 of 92
29. Question
1 pointsWhich command can you enter to configure a local username with an encrypted password and EXEC mode user privileges?Correct
Incorrect
Hint
Usually we enter a command like this: username bill password westward And the system display this command as follows: username bill password 7 21398211 The encrypted version of the password is 21398211. The password was encrypted by the Cisco-defined encryption algorithm, as indicated by the “7”. However, if you enter the following command: “username bill password 7 21398211”, the system determines that the password is already encrypted and performs no encryption. Instead, it displays the command exactly as you entered it. Reference: http://www.cisco.com/c/en/us/td/docs/ios/12_2/security/configuration/guide/fsecur_c/scfpass.html#wp1001412 -
Question 30 of 92
30. Question
1 pointsWhich statement about the IP SLAs ICMP Echo operation is true?Correct
Incorrect
Hint
The ICMP Echo operation measures end-to-end response time between a Cisco router and any devices using IP. Response time is computed by measuring the time taken between sending an ICMP Echo request message to the destination and receiving an ICMP Echo reply. Many customers use IP SLAs ICMP-based operations, in-house ping testing, or ping-based dedicated probes for response time measurements. Reference: http://www.cisco.com/c/en/us/td/docs/ios-xml/ios/ipsla/configuration/15-mt/sla-15-mt-book/sla_icmp_echo.html -
Question 31 of 92
31. Question
1 pointsWhat are three components that comprise the SNMP framework? (Choose three)Correct
Incorrect
-
Question 32 of 92
32. Question
1 pointsWhich command can be used from a PC to verify the connectivity between hosts that connect through a switch in the same LAN?Correct
Incorrect
Hint
To check the connectivity between a host and a destination (through some networks) we can use both “tracert” and “ping” commands. But the difference between these two commands is the “tracert” command can display a list of near-side router interfaces in the path between the source and the destination. In this question the PC and the host are in the same VLAN so “tracert” command is not useful as there is no router to go through. Therefore the best answer in this case is “ping address”. Note: “traceroute” command has the same function of the “tracert” command but it is used on Cisco routers only, not on a PC. -
Question 33 of 92
33. Question
1 pointsWhat command instructs the device to timestamp Syslog debug messages in milliseconds?Correct
Incorrect
Hint
The “service timestamps debug” command configures the system to apply a time stamp to debugging messages. The time-stamp format for datetime is MMM DD HH:MM:SS, where MMM is the month, DD is the date, HH is the hour (in 24-hour notation), MM is the minute, and SS is the second. With the additional keyword msec, the system includes milliseconds in the time stamp, in the format HH:DD:MM:SS.mmm, where .mmm is milliseconds (Reference: http://www.cisco.com/c/en/us/td/docs/ios/fundamentals/command/reference/cf_book/cf_r1.html#wp1030116) -
Question 34 of 92
34. Question
1 pointsWhich command can you enter on a switch to determine the current SNMP security model?Correct
Incorrect
Hint
Three security models are available: SNMPv1, SNMPv2c, and SNMPv3. The security model combined with the security level determine the security mechanism applied when the SNMP message is processed. The command “show snmp group” displays the names of groups on the router and the security model, the status of the different views, and the storage type of each group. Below is an example of this command.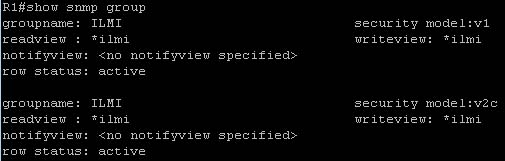 Reference: https://www.cisco.com/c/en/us/td/docs/switches/datacenter/sw/5_x/nx-os/system_management/configuration/guide/sm_nx_os_cg/sm_9snmp.html
Reference: https://www.cisco.com/c/en/us/td/docs/switches/datacenter/sw/5_x/nx-os/system_management/configuration/guide/sm_nx_os_cg/sm_9snmp.html -
Question 35 of 92
35. Question
1 pointsWhich statement about upgrading a cisco IOS device with TFTP server ?Correct
Incorrect
Hint
Verify that the TFTP or RCP server has IP connectivity to the router. If you cannot successfully ping between the TFTP or RCP server and the router, do one of the following: – Configure a default gateway on the router. – Make sure that the server and the router each have an IP address in the same network or subnet. Reference: https://www.cisco.com/c/en/us/td/docs/routers/access/1900/software/configuration/guide/Software_Configuration/upgrade.html The first option implies the router can be in a different subnet from the TFTP server -> D is not correct. TFTP has no encryption process so answer B is correct. -
Question 36 of 92
36. Question
1 pointsWhich three statements about the features of SNMPv2 and SNMPv3 are true? (Choose three.)Correct
Incorrect
Hint
SNMPv1/v2 can neither authenticate the source of a management message nor provide encryption. Without authentication, it is possible for nonauthorized users to exercise SNMP network management functions. It is also possible for nonauthorized users to eavesdrop on management information as it passes from managed systems to the management system. Because of these deficiencies, many SNMPv1/v2 implementations are limited to simply a read-only capability, reducing their utility to that of a network monitor; no network control applications can be supported. To correct the security deficiencies of SNMPv1/v2, SNMPv3 was issued as a set of Proposed Standards in January 1998. -> A is correct. (Reference: http://www.cisco.com/web/about/ac123/ac147/archived_issues/ipj_1-3/snmpv3.html) The two additional messages are added in SNMP2 (compared to SNMPv1) GetBulkRequest The GetBulkRequest message enables an SNMP manager to access large chunks of data. GetBulkRequest allows an agent to respond with as much information as will fit in the response PDU. Agents that cannot provide values for all variables in a list will send partial information. -> E is correct. InformRequest The InformRequest message allows NMS stations to share trap information. (Traps are issued by SNMP agents when a device change occurs.) InformRequest messages are generally used between NMS stations, not between NMS stations and agents. -> C is correct. Note: These two messages are carried over SNMPv3. -
Question 37 of 92
37. Question
1 pointsWhich command do use we to see SNMP versionCorrect
Incorrect
Hint
The “show snmp pending” command displays the current set of pending SNMP requests. It also displays the SNMP version used. Router# show snmp pendingreq id: 47, dest: 171.69.58.33.161, V2C community: public, Expires in 5 secs req id: 49, dest: 171.69.58.33.161, V2C community: public, Expires in 6 secs req id: 51, dest: 171.69.58.33.161, V2C community: public, Expires in 6 secs req id: 53, dest: 171.69.58.33.161, V2C community: public, Expires in 8 secs
Note: The “show snmp engineID” displays the identification of the local SNMP engine and all remote engines that have been configured on the router. The following example specifies 00000009020000000C025808 as the local engineID and 123456789ABCDEF000000000 as the remote engine ID, 171.69.37.61 as the IP address of the remote engine (copy of SNMP) and 162 as the port from Which the remote device is connected to the local device:Router# show snmp engineID Local SNMP engineID: 00000009020000000C025808 Remote Engine ID IP-addr Port 123456789ABCDEF000000000 171.69.37.61 162
-
Question 38 of 92
38. Question
1 pointsWhich feature can you use to restrict SNMP queries to a specific OID tree?Correct
Incorrect
Hint
You can assign views to community strings to limit Which MIB objects an SNMP manager can access. The syntax to create a view record is shown below: Router(config)# snmp-server view view-name oid-tree {included | excluded} Reference: https://www.cisco.com/c/en/us/td/docs/ios/12_2/configfun/configuration/guide/ffun_c/fcf014.html -
Question 39 of 92
39. Question
1 pointsWhat authentication type is used by SNMPv2 ?Correct
Incorrect
-
Question 40 of 92
40. Question
1 pointsWhich two IP SLA operations can you use to measure the end-to-end response time for all IP traffic between a Cisco router and an end device ?(choose two)Correct
Incorrect
Hint
To measure end-to-end reponse time we have to use ICMP echo to continuously ping to a remote device. The difference between ICMP path echo and ICMP echo is the former can measure hop-by-hop response time on its whole path while the latter can only measure to a specific destination. -
Question 41 of 92
41. Question
1 pointsRefer to the exhibit. The technician wants to upload a new IOS in the router while keeping the existing IOS. What is the maximum size of an IOS file that could be loaded if the original IOS is also kept in flash? Correct
Correct
Incorrect
Hint
In this example, there are a total of 8 MB, but 3.8 are being used already, so another file as large as 4MB can be loaded in addition to the original file. -
Question 42 of 92
42. Question
1 pointsBefore installing a new, upgraded version of the IOS, what should be checked on the router, and Which command should be used to gather this information? (Choose two.)Correct
Incorrect
Hint
When upgrading new version of the IOS we need to copy the IOS to the Flash so first we have to check if the Flash has enough memory or not. Also running the new IOS may require more RAM than the older one so we should check the available RAM too. We can check both with the “show version” command. -
Question 43 of 92
43. Question
1 pointsWhich command reveals the last method used to powercycle a router?Correct
Incorrect
Hint
The “show version” command can be used to show the last method to powercycle (reset) a router.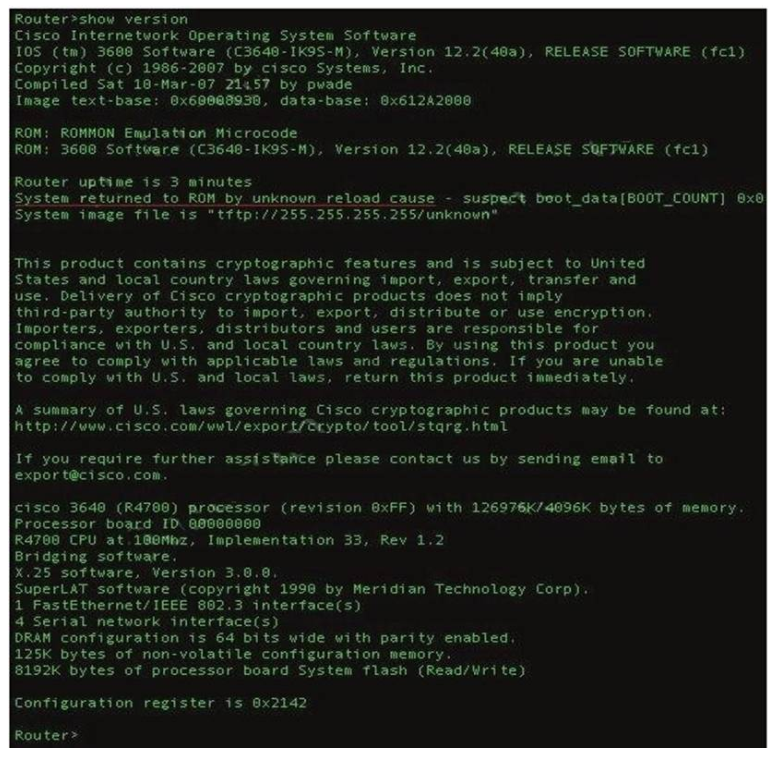
-
Question 44 of 92
44. Question
1 pointsWhich command would you use on a Cisco router to verify the Layer 3 path to a host?Correct
Incorrect
Hint
In computing, traceroute is a computer network diagnostic tool for displaying the route (path) and measuring transit delays of packets across an Internet Protocol (IP) network. The history of the route is recorded as the round-trip times of the packets received from each successive host (remote node) in the route (path); the sum of the mean times in each hop indicates the total time spent to establish the connection. Traceroute proceedsunless all (three) sent packets are lost more than twice, then the connection is lost and the route cannot be evaluated. Ping, on the other hand, only computes the final round-trip times from the destination point. -
Question 45 of 92
45. Question
1 pointsRefer to the exhibit. A network administrator configures a new router and enters the copy startup- config running-config command on the router. The network administrator powers down the router and sets it up at a remote location. When the router starts, it enters the system configuration dialog as shown. What is the cause of the problem? Correct
Correct
Incorrect
Hint
The “System Configuration Dialog” appears only when no startup configuration file is found. The network administrator has made a mistake because the command “copy startup-config running- config” will copy the startup config (Which is empty) over the running config (Which is configured by the administrator). So everything configured was deleted. Note: We can tell the router to ignore the start-up configuration on the next reload by setting the register to 0?142. This will make the “System Configuration Dialog” appear at the next reload. -
Question 46 of 92
46. Question
1 pointsWhich two locations can be configured as a source for the IOS image in the boot system command? (Choose two.)Correct
Incorrect
Hint
The following locations can be configured as a source for the IOS image: 1. + Flash (the default location) 2. + TFTP server3. + ROM (used if no other source is found) -
Question 47 of 92
47. Question
1 pointsRefer to the exhibit. For what two reasons has the router loaded its IOS image from the location that is shown? (Choose two.)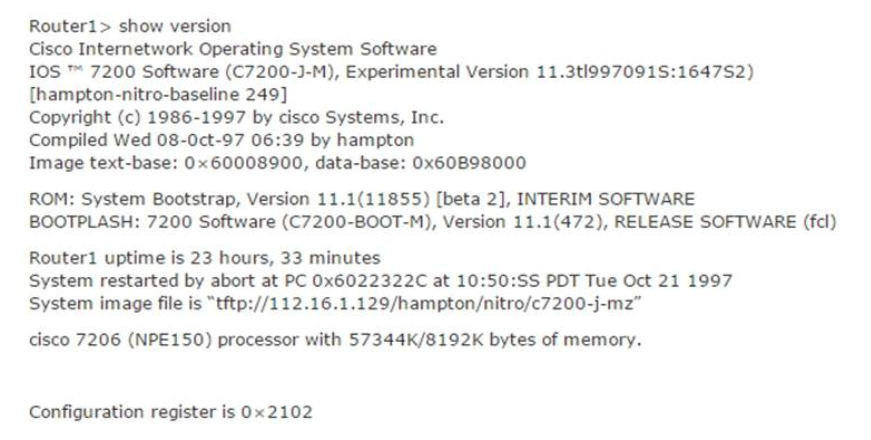 Correct
Correct
Incorrect
Hint
The loading sequence of CISCO IOS is as follows: Booting up the router and locating the Cisco IOS 1. POST (power on self test) 2. Bootstrap code executed 3. Check Configuration Register value (NVRAM) Which can be modified using the config-register command 0 = ROM Monitor mode 1 = ROM IOS 2 – 15 = startup-config in NVRAM 4. Startup-config filE. Check for boot system commands (NVRAM) If boot system commands in startup-config a. Run boot system commands in order they appear in startup-config to locate the IOS b. [If boot system commands fail, use default fallback sequence to locate the IOS (Flash, TFTP, ROM)?] If no boot system commands in startup-config use the default fallback sequence in locating the IOS: a. Flash (sequential) b. TFTP server (netboot) c. ROM (partial IOS) or keep retrying TFTP depending upon router model 5. If IOS is loaded, but there is no startup-config file, the router will use the default fallback sequence for locating the IOS and then it will enter setup mode or the setup dialogue. -
Question 48 of 92
48. Question
1 pointsRefer to the exhibit. What can be determined about the router from the console output?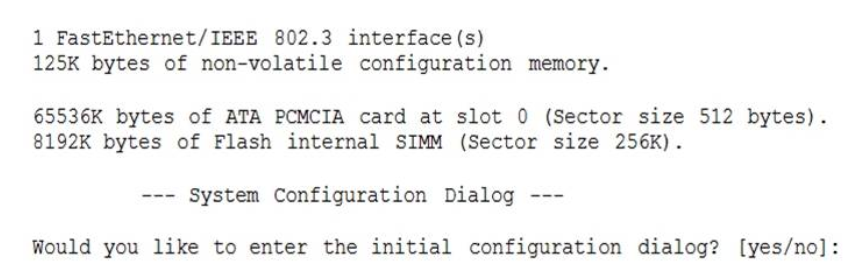 Correct
Correct
Incorrect
Hint
When no startup configuration file is found in NVRAM, the System Configuration Dialog will appear to ask if we want to enter the initial configuration dialog or not. -
Question 49 of 92
49. Question
1 pointsWhat is a global command?Correct
Incorrect
Hint
When you enter global configuration mode and enter a command, it is applied to the running configuration file that is currently running in ram. The configuration of a global command affects the entire router. An example of a global command is one used for the hostname of the router. -
Question 50 of 92
50. Question
1 pointsWhat are three factors a network administrator must consider before implementing Netflow in the network?Correct
Incorrect
-
Question 51 of 92
51. Question
1 pointsWhat SNMP message alerts the manager to a condition on the network?Correct
Incorrect
-
Question 52 of 92
52. Question
1 pointsWhat are three reasons to collect Netflow data on a company network? (Choose three.)Correct
Incorrect
-
Question 53 of 92
53. Question
1 pointsWhat Netflow component can be applied to an interface to track IPv4 traffic?Correct
Incorrect
Hint
Flow monitors are the Flexible NetFlow component that is applied to interfaces to perform network traffic monitoring. Flow monitors consist of a record and a cache. You add the record to the flow monitor after you create the flow monitor. The flow monitor cache is automatically created at the time the flow monitor is applied to the first interface. Flow data is collected from the network traffic during the monitoring process based on the key and nonkey fields in the record, Which is configured for the flow monitor and stored in the flow monitor cache. For example, the following example creates a flow monitor named FLOW-MONITOR-1 and enters Flexible NetFlow flow monitor configuration mode: Router(config)# flow monitor FLOW-MONITOR-1 Router(config-flow-monitor)# -
Question 54 of 92
54. Question
1 pointsWhich command displays CPU utilization?Correct
Incorrect
Hint
The “show process” (in fact, the full command is “show processes”) command gives us lots of information about each process but in fact it is not easy to read. Below shows the output of this command (some next pages are omitted)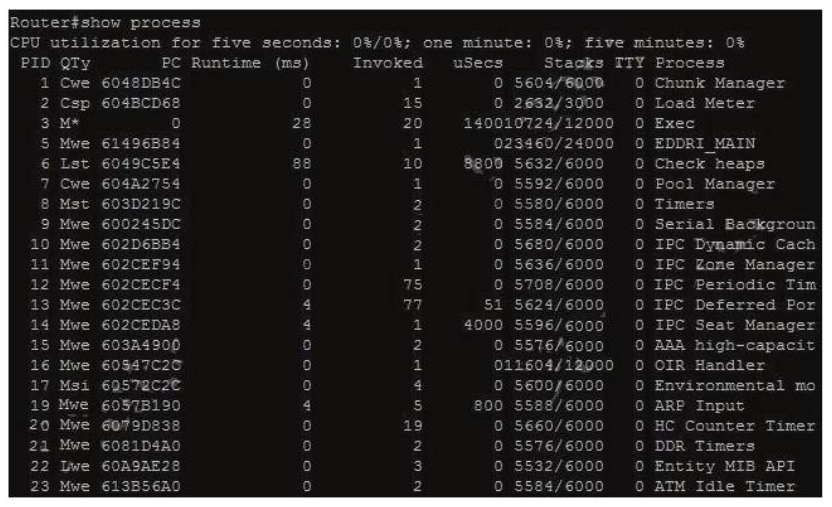
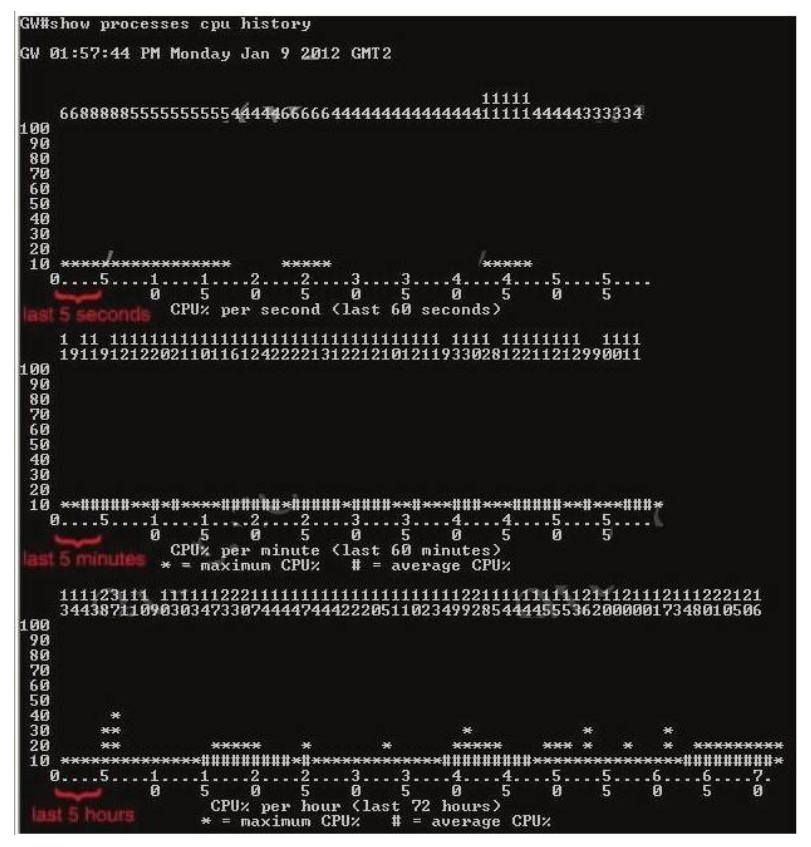 + The Y-axis of the graph is the CPU utilization.+ The X-axis of the graph is the increment within the period displayed in the graph For example, from the last graph (last 72 hours) we learn that the highest CPU utilization within 72 hours is 37% about six hours ago.
+ The Y-axis of the graph is the CPU utilization.+ The X-axis of the graph is the increment within the period displayed in the graph For example, from the last graph (last 72 hours) we learn that the highest CPU utilization within 72 hours is 37% about six hours ago. -
Question 55 of 92
55. Question
1 pointsWhich router IOS commands can be used to troubleshoot LAN connectivity problems? (Choose three.)Correct
Incorrect
Hint
Ping, show ip route, and show interfaces are all valid troubleshooting IOS commands. Tracert, ipconfig, and winipcfg are PC commands, not IOS. -
Question 56 of 92
56. Question
1 pointsSyslog was configured with a level 3 trap. Which 4 types of logs would be generated (Choose four.)Correct
Incorrect
Hint
The Message Logging is divided into 8 levels as listed below: Level Keyword Description 0 emergencies System is unusable 1 alerts Immediate action is needed 2 critical Critical conditions exist 3 errors Error conditions exist 4 warnings Warning conditions exist 5 notification Normal, but significant, conditions exist 6 informational Informational messages 7 debugging Debugging messages The highest level is level 0 (emergencies). The lowest level is level 7. If you specify a level with the “logging console level” command, that level and all the higher levels will be displayed. For example, by using the “logging console warnings” command, all the logging of emergencies, alerts, critical, errors, warnings will be displayed. -
Question 57 of 92
57. Question
1 pointsWhat are the benefit of using Netflow? (Choose three.)Correct
Incorrect
-
Question 58 of 92
58. Question
1 pointsWhich protocol can cause overload on a CPU of a managed device?Correct
Incorrect
Hint
Sometimes, messages like this might appear in the router console: %SNMP-3-CPUHOG: Processing [chars] of [chars] They mean that the SNMP agent on the device has taken too much time to process a request. You can determine the cause of high CPU use in a router by using the output of the show process cpu command. Note: A managed device is a part of the network that requires some form of monitoring and management (routers, switches, servers, workstations, printers…). -
Question 59 of 92
59. Question
1 pointsWhat are the three things that the Netflow uses to consider the traffic to be in a same flow? (Choose three.)Correct
Incorrect
Hint
What is an IP Flow? Each packet that is forwarded within a router or switch is examined for a set of IP packet attributes. These attributes are the IP packet identity or fingerprint of the packet and determine if the packet is unique or similar to other packets. Traditionally, an IP Flow is based on a set of 5 and up to 7 IP packet attributes. IP Packet attributes used by NetFlow: + IP source address + IP destination address + Source port + Destination port + Layer 3 protocol type + Class of Service + Router or switch interface -
Question 60 of 92
60. Question
1 pointsWhat is the alert message generated by SNMP agents called?Correct
Incorrect
Hint
A TRAP is a SNMP message sent from one application to another (Which is typically on a remote host). Their purpose is merely to notify the other application that something has happened, has been noticed, etc. The big problem with TRAPs is that they’re unacknowledged so you don’t actually know if the remote application received your oh-so-important message to it. SNMPv2 PDUs fixed this by introducing the notion of an INFORM, Which is nothing more than an acknowledged TRAP. -
Question 61 of 92
61. Question
1 pointsWhich three features are added in SNMPv3 over SNMPv2? (Choose three.)Correct
Incorrect
-
Question 62 of 92
62. Question
1 pointsWhich three statements about Syslog utilization are true? (Choose three.)Correct
Incorrect
-
Question 63 of 92
63. Question
1 pointsA network administrator enters the following command on a router:logging trap 3 . What are three message types that will be sent to the Syslog server? (choose three)Correct
Incorrect
-
Question 64 of 92
64. Question
1 pointsWhat is the default Syslog facility level?Correct
Incorrect
-
Question 65 of 92
65. Question
1 pointsWhat is the cause of the Syslog output messages? Correct
Correct
Incorrect
Hint
From the second line of the output, we learned that Fa0/1 interface was shut down so we see the “changed state to administratively down”. The third and fourth line is the result of this action, Which cause Fa0/1 interface “changed state to down” and the EIGRP neighbor relationship with 10.10.11.2 was down. -
Question 66 of 92
66. Question
1 pointsWhat Cisco IOS feature can be enabled to pinpoint an application that is causing slow network performance?Correct
Incorrect
-
Question 67 of 92
67. Question
1 pointsWhat command visualizes the general NetFlow data on the command line?Correct
Incorrect
Hint
The “show ip cache flow” command displays a summary of the NetFlow -
Question 68 of 92
68. Question
1 pointsWhat are three values that must be the same within a sequence of packets for Netflow to consider them a network flow? (Choose three.)Correct
Incorrect
-
Question 69 of 92
69. Question
1 pointsWhich three are the components of SNMP? (Choose three)Correct
Incorrect
Hint
SNMP is an application-layer protocol that provides a message format for communication between SNMP managers and agents. SNMP provides a standardized framework and a common language used for the monitoring and management of devices in a network. The SNMP framework has three parts: + An SNMP manager + An SNMP agent + A Management Information Base (MIB) The SNMP manager is the system used to control and monitor the activities of network hosts using SNMP. The most common managing system is called a Network Management System (NMS). The term NMS can be applied to either a dedicated device used for network management, or the applications used on such a device. A variety of network management applications are available for use with SNMP. These features range from simple command-line applications to feature-rich graphical user interfaces (such as the CiscoWorks2000 line of products). The SNMP agent is the software component within the managed device that maintains the data for the device and reports these data, as needed, to managing systems. The agent and MIB reside on the routing device (router, access server, or switch). To enable the SNMP agent on a Cisco routing device, you must define the relationship between the manager and the agent. The Management Information Base (MIB) is a virtual information storage area for network management information, Which consists of collections of managed objects. -
Question 70 of 92
70. Question
1 pointsWhat are the Popular destinations for syslog messages to be saved?Correct
Incorrect
Hint
By default, switches send the output from system messages and debug privileged EXEC commands to a logging process. The logging process controls the distribution of logging messages to various destinations, such as the logging buffer (on RAM), terminal lines (console terminal), or a UNIX syslog server, depending on your configuration. The process also sends messages to the console. Note: Syslog messages can be written to a file in Flash memory although it is not a popular place to use. We can configure this feature with the command logging file flash:filename. -
Question 71 of 92
71. Question
1 pointsWhat levels will be trapped if the administrator executes the command router(config)# logging trap 4? (Choose four.)Correct
Incorrect
Hint
The Message Logging is divided into 8 levels as listed below: Level Keyword Description 0 emergencies System is unusable 1 alerts Immediate action is needed 2 critical Critical conditions exist 3 errors Error conditions exist 4 warnings Warning conditions exist 5 notification Normal, but significant, conditions exist 6 informational Informational messages 7 debugging Debugging messages If you specify a level with the “logging trap level” command, that level and all the higher levels will be logged. For example, by using the “logging trap 4 command, all the logging of emergencies, alerts, critical, errors, warnings will be logged. -
Question 72 of 92
72. Question
1 pointsWhen upgrading the IOS image, the network administrator receives the exhibited error message. What could be the cause of this error?Correct
Incorrect
-
Question 73 of 92
73. Question
1 pointsRefer to the exhibit. What could be possible causes for the “Serial0/0 is down” interface status? (Choose two.)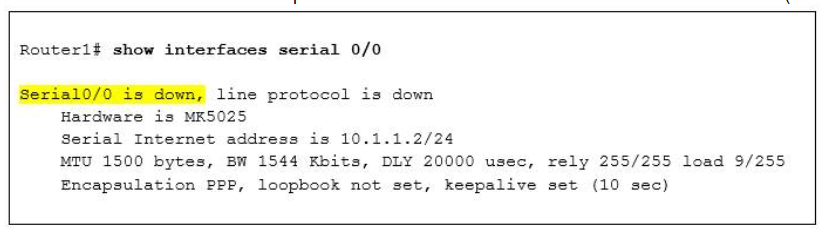 Correct
Correct
Incorrect
-
Question 74 of 92
74. Question
1 pointsRefer to the exhibit. What does the address 192.168.2.167 represent?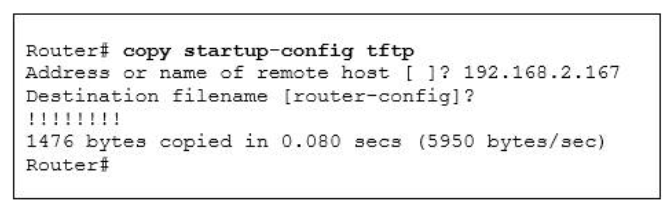 Correct
Correct
Incorrect
-
Question 75 of 92
75. Question
1 pointsHow can an administrator determine if a router has been configured when it is first powered up?Correct
Incorrect
-
Question 76 of 92
76. Question
1 pointsWhich two commands can you enter to verify that a configured NetFlow data export is operational? (Choose two.)Correct
Incorrect
-
Question 77 of 92
77. Question
1 pointsWhat is the first step you perform to configure an SNMPv3 user?Correct
Incorrect
Hint
The first step we need to do when configuring an SNMPv3 user is to configure the server group to enable authentication for members of a specified named access list via the “snmp-server group” command. For example:Router(config)# snmp-server group MyGroup v3 auth access snmp_ac
In this example, the SNMP server group MyGroup is configured to enable user authentication for members of the named access list snmp_acl. Reference: http://www.cisco.com/c/en/us/td/docs/ios-xml/ios/snmp/configuration/xe-3se/3850/snmp-xe-3se-3850-book/nm-snmp-snmpv3.html -
Question 78 of 92
78. Question
1 pointsA network administrator has configured access list 173 to prevent Telnet and ICMP traffic from reaching a server with the address of 192.168.13.26. Which commands can the administrator issue to verify that the access list is working properly? (Choose three.)Correct
Incorrect
-
Question 79 of 92
79. Question
1 pointsWhich configuration register value can you set on a Cisco device so that it ignores the NVRAM when it boots?Correct
Incorrect
Hint
To reset the password we can type “confreg 0x2142” under rommon mode to set the configuration register to 2142 in hexadecimal (the prefix 0x means hexadecimal (base 16)). With this setting when that router reboots, it bypasses the startup-config. -
Question 80 of 92
80. Question
1 pointsWhich version of SNMP first allowed user-based access?Correct
Incorrect
Hint
The user-based access control implemented by SNMPv3 is based on contexts and user names, rather than on IP addresses and community strings. It is a partial implementation of the view-based access control model (VACM). -
Question 81 of 92
81. Question
1 pointsWhich two criteria must be met to support the ICMP echo IP SLA? (Choose two)Correct
Incorrect
-
Question 82 of 92
82. Question
1 pointsWhich two characteristics of an ICMP echo-based IP SLA are true? (Choose two)Correct
Incorrect
-
Question 83 of 92
83. Question
1 pointsWhich two commands can you use to verify an IP SLA? (Choose two.)Correct
Incorrect
-
Question 84 of 92
84. Question
1 pointsWhich effect of the terminal monitor command is true?Correct
Incorrect
-
Question 85 of 92
85. Question
1 pointsWhich command is configured on a switch to enable neighbor discovery in a multivendor environment?Correct
Incorrect
-
Question 86 of 92
86. Question
1 pointsWhich API uses HTTP messages to transfer data to applications residing on different hosts?Correct
Incorrect
-
Question 87 of 92
87. Question
1 pointsYou are configuring an IP SLA ICMP Echo operation to troubleshoot a network connectivity issue. When do you enter an IP address to test the IP SLA?Correct
Incorrect
-
Question 88 of 92
88. Question
1 pointsDRAG DROP. Drag and drop the extended traceroute options from the left onto the correct descriptions on the right. Select and Place: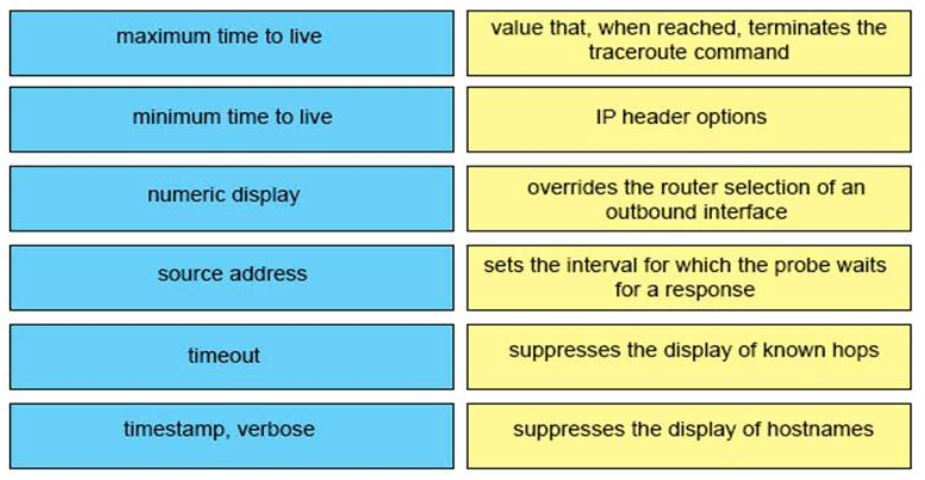
Sort elements
- maximum time to live
- timestamp, verbose
- source address
- timeout
- minimum time to live
- numeric display
-
value that, when reached, terminates the traceroute commnad
-
IP header options
-
overrides the router selection of an outbound interface
-
sets the interval for which the probe waits for a response
-
suppresses the display of known hops
-
suppresses the display of hostnames
Correct
Incorrect
-
Question 89 of 92
89. Question
1 pointsDRAG DROP. Drag and drop the descriptions of performing an initial device configuration from the left onto the correct features or components on the right. Select and Place: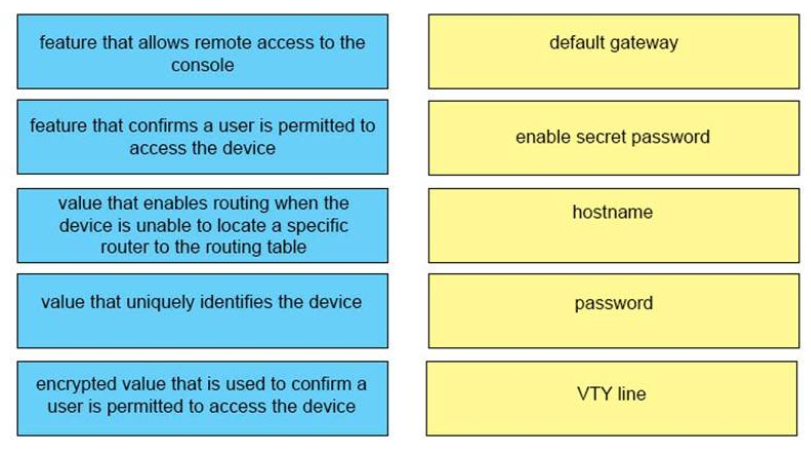
Sort elements
- value that enables routing when the device is unable to locate to specific router to the routing table
- encrypted value that is used to confirm a user is permitted to access the device
- value that uniquely identifies the device
- feature that confirm a user is permitted to access the device
- feature that allows remote access to the console
-
default gateway
-
enable secret password
-
hostname
-
password
-
VTY line
Correct
Incorrect
-
Question 90 of 92
90. Question
1 pointsDRAG DROP. Drag and drop the descriptions of logging from the left onto the correct logging features or components on the right. Select and Place: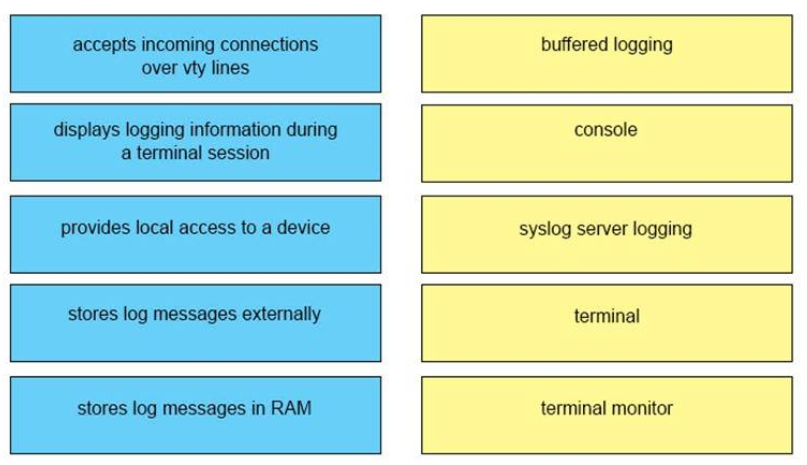
Sort elements
- stores log messages externally
- provides local access to a device
- stores log messages in RAM
- accepts incoming connections over vty lines
- displays logging information during a terminal session
-
buffered logging
-
console
-
syslog server logging
-
terminal
-
terminal monitor
Correct
Incorrect
-
Question 91 of 92
91. Question
1 pointsDRAG DROP. You are performing the initial configuration on a new Cisco device. Drag the task from the left onto the required or optional category on the right. Select and Place: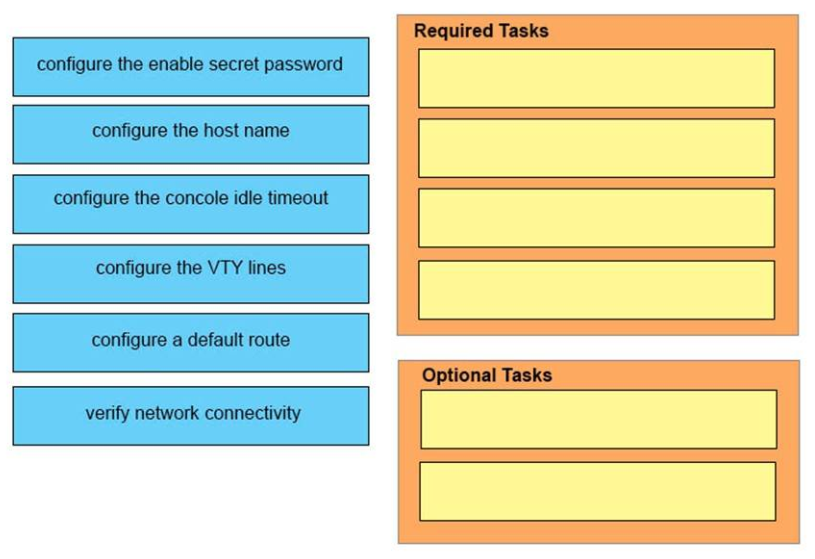
Sort elements
- configure the enable secret password
- verify network connectivity
- configure the VTY lines
- configure the default route
- configure the console idle timeout
- configure the host name
-
Required Tasks (1)
-
Required Tasks (2)
-
Required Tasks (3)
-
Required Tasks (4)
-
Optinal Tasks (1)
-
Optinal Tasks (2)
Correct
Incorrect
-
Question 92 of 92
92. Question
1 pointsDRAG DROP. Drag and drop the network programmability features from the left onto the correct description on the right. Select and Place: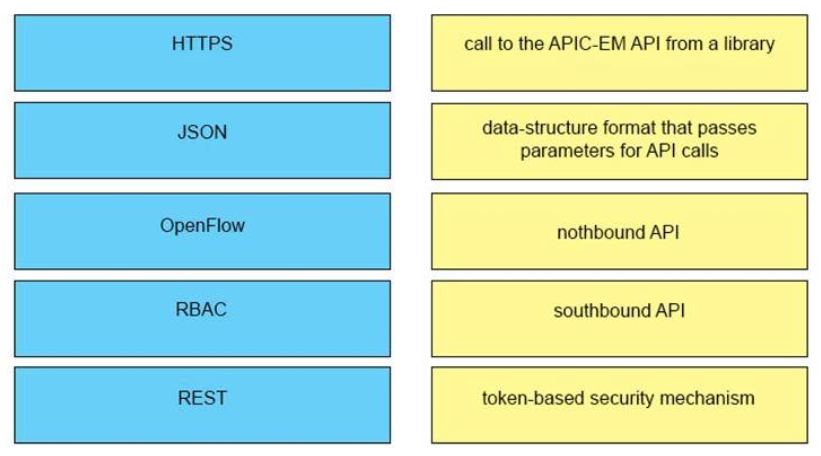
Sort elements
- RBAC
- JSON
- REST
- OpenFlow
- HTTPS
-
call tho the APIC-EM API from the library
-
data-structure format that passes parameters for API callls
-
nothbound API
-
southbound API
-
token-based security mechanism
Correct
Incorrect