Time limit: 0
Quiz-summary
0 of 89 questions completed
Questions:
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
Information
Section VI: Infrastructure Security - Test Online
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading...
You must sign in or sign up to start the quiz.
You have to finish following quiz, to start this quiz:
Results
0 of 89 questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 points, (0)
| Average score |
|
| Your score |
|
Categories
- Not categorized 0%
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- Answered
- Review
-
Question 1 of 89
1. Question
1 pointsWhich statement about RADIUS security is true?Correct
Incorrect
-
Question 2 of 89
2. Question
1 pointsWhich command can you enter to block HTTPS traffic from the whole class A private network range to a host?Correct
Incorrect
-
Question 3 of 89
3. Question
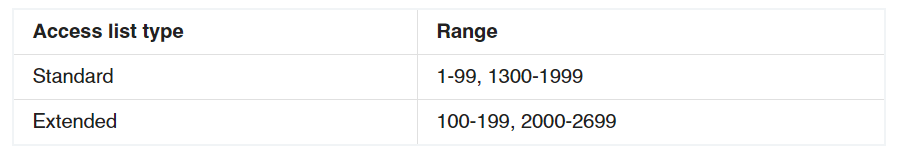
1 pointsWhich two options are valid numbers for a standard access list? (Choose two.)Correct
Incorrect
-
Question 4 of 89
4. Question
1 pointsWhich utility can you use to identify the cause of a traffic-flow blockage between the two devices in a network?Correct
Incorrect
Hint
APIC-EM automation scheduler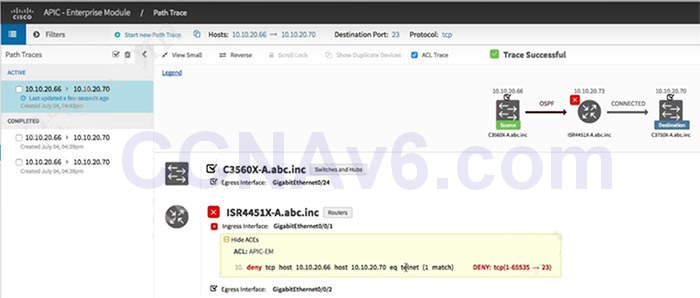 Icon
Icon
 means “there are ACLs that permit the traffic applied on the interface”.
Icon
means “there are ACLs that permit the traffic applied on the interface”.
Icon
 port when defining a path trace”.
Icon
port when defining a path trace”.
Icon
 means “there is an ACL on the device or interface that is blocking the traffic on the path”.
Icon
means “there is an ACL on the device or interface that is blocking the traffic on the path”.
Icon
 means “there are no ACLs applied on the interface”.
Reference: https://www.cisco.com/c/en/us/td/docs/cloud-systems-management/application-policy-infrastructure-controller-enterprise-module/1-5-x/path_trace/user-guide/b_Cisco_Path_Trace_User_Guide_1_5_0_x/b_Cisco_Path_Trace_User_Guide_1_5_0_x_chapter_0111
means “there are no ACLs applied on the interface”.
Reference: https://www.cisco.com/c/en/us/td/docs/cloud-systems-management/application-policy-infrastructure-controller-enterprise-module/1-5-x/path_trace/user-guide/b_Cisco_Path_Trace_User_Guide_1_5_0_x/b_Cisco_Path_Trace_User_Guide_1_5_0_x_chapter_0111 -
Question 5 of 89
5. Question
1 pointsWhich set of commands is recommended to prevent the use of a hub in the access layer?Correct
Incorrect
Hint
Port security is only used on access port (Which connects to hosts) so we need to set that port to “access” mode, then we need to specify the maximum number of hosts Which are allowed to connect to this port -> C is correct. Note: If we want to allow a fixed MAC address to connect, use the “switchport port-security mac-address ” command. -
Question 6 of 89
6. Question
1 pointsWhich two options are primary responsibilities of the APlC-EM controller? (Choose two.)Correct
Incorrect
Hint
http://www.cisco.com/c/en/us/products/cloud-systems-management/application-policy-infrastructure-controller-enterprise-module/index.html Automate network configuration and setup Deploy network devices faster Automate device deployment and provisioning across the enterprise. Provide a programmable network Enable developers to create new applications that use the network to fuel business growth. -
Question 7 of 89
7. Question
1 pointsWhich utility can you use to identify redundant or shadow rules?Correct
Incorrect
Hint
Cisco APIC-EM supports the following policy analysis features: + Inspection, interrogation, and analysis of network access control policies. + Ability to trace application specific paths between end devices to quickly identify ACLs in use and problem areas. + Enables ACL change management with easy identification of conflicts and shadows -> Maybe B is the most suitable answer. Reference: http://www.cisco.com/c/en/us/td/docs/cloud-systems-management/application-policy-infrastructure-controller-enterprise-module/1-2-x/config-guide/b_apic-em_config_guide_v_1-2-x/b_apic-em_config_guide_v_1-2-x_chapter_01000.pdf The ACL trace tool can only help us to identify Which ACL on Which router is blocking or allowing traffic. It cannot help identify redundant/shadow rules. Note: Cisco Application Policy Infrastructure Controller Enterprise Module (APIC-EM) is a Cisco Software Defined Networking (SDN) controller, Which uses open APIs for policy-based management and security through a single controller, abstracting the network and making network services simpler. APIC-EM provides centralized automation of policy-based application profiles. Reference: CCNA Routing and Switching Complete Study Guide Cisco Intelligent WAN (IWAN) application simplifies the provisioning of IWAN network profiles with simple business policies. The IWAN application defines business-level preferences by application or groups of applications in terms of the preferred path for hybrid WAN links. Doing so improves the application experience over any connection and saves telecom costs by leveraging cheaper WAN links. Shadow rules are the rules that are never matched (usually because of the first rules). For example two access-list statements: access-list 100 permit ip any any access-list 100 deny tcp host A host B Then the second access-list statement would never be matched because all traffic have been already allowed by the first statement. In this case we call statement 1 shadows statement 2. -
Question 8 of 89
8. Question
1 pointsWhat will be the result if the following configuration commands are implemented on a Cisco switch? Switch(config-if)# switchport port-security Switch(config-if)# switchport port-security mac-address stickyCorrect
Incorrect
-
Question 9 of 89
9. Question
1 pointsRefer to the exhibit. The following commands are executed on interface fa0/1 of 2950Switch. 2950Switch(config-if)# switchport port-security 2950Switch(config-if)# switchport port-security mac-address sticky 2950Switch(config-if)# switchport port-security maximum 1 The Ethernet frame that is shown arrives on interface fa0/1. What two functions will occur when this frame is received by 2950Switch? (Choose two.)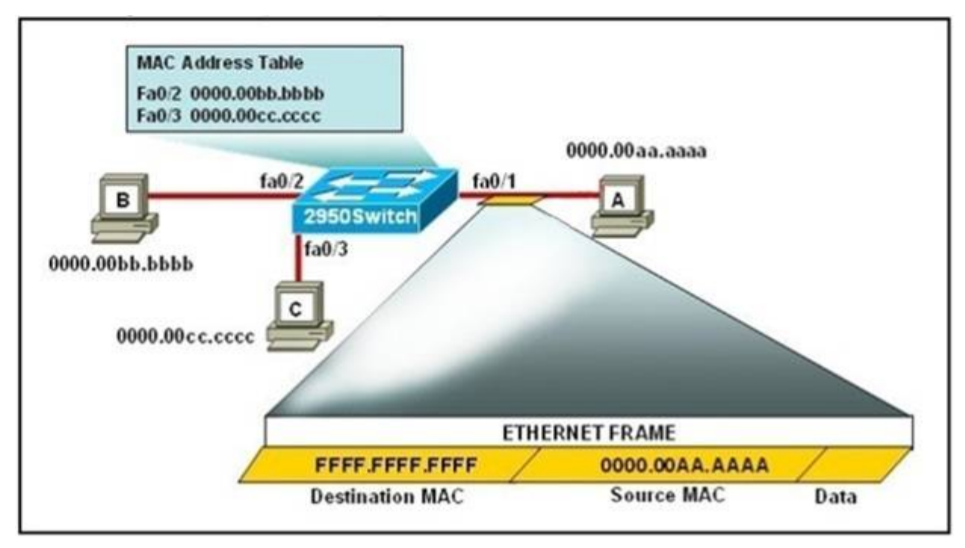 Correct
Correct
Incorrect
Hint
The first command 2950Switch(config-if)#switchport port-security is to enable the port-security in a switch port. In the second command 2950Switch(config-if)#switchport port-security mac-address sticky, we need to know the full syntax of this command is switchport port-security mac-address sticky [MAC]. The STICKY keyword is used to make the MAC address appear in the running configuration and you can save it for later use. If you do not specify any MAC addresses after the STICKY keyword, the switch will dynamically learn the attached MAC Address and place it into your running-configuration. In this case, the switch will dynamically learn the MAC address 0000.00aa.aaaa of host A and add this MAC address to the running configuration. In the last command 2950Switch(config-if)#switchport port-security maximum 1 you limited the number of secure MAC addresses to one and dynamically assigned it (because no MAC address is mentioned, the switch will get the MAC address of the attached MAC address to interface fa0/1), the workstation attached to that port is assured the full bandwidth of the port.Therefore only host A will be allowed to transmit frames on fa0/1 -> B is correct. After you have set the maximum number of secure MAC addresses for interface fa0/1, the secure addresses are included in the “Secure MAC Address” table (this table is similar to the Mac Address Table but you can only view it with the show port-security address command). So in this question, although you don’t see the MAC address of host A listed in the MAC Address Table but frames with a destination of 0000.00aa.aaaa will be forwarded out of fa0/1 interface -> D is correct. -
Question 10 of 89
10. Question
1 pointsRefer to the exhibit. A junior network administrator was given the task of configuring port security on SwitchA to allow only PC_A to access the switched network through port fa0/1. If any other device is detected, the port is to drop frames from this device. The administrator configured the interface and tested it with successful pings from PC_A to RouterA, and then observes the output from these two show commands. Which two of these changes are necessary for SwitchA to meet the requirements? (Choose two.)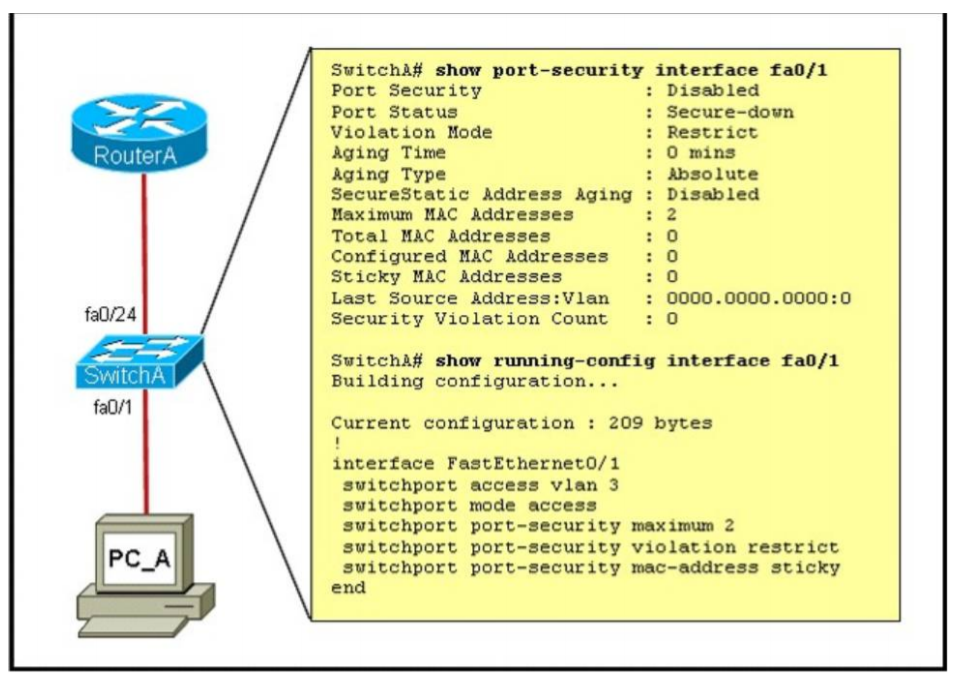 Correct
Correct
Incorrect
Hint
As we see in the output, the “Port Security” is in “Disabled” state (line 2 in the output). To enable Port security feature, we must enable it on that interface first with the command: SwitchA(config-if)#switchport port-security -> B is correct. Also from the output, we learn that the switch is allowing 2 devices to connect to it (switchport port-security maximum 2) but the question requires allowing only PC_A to access the network so we need to reduce the maximum number to 1 -> D is correct. -
Question 11 of 89
11. Question
1 pointsWhat to do when the router password was forgotten?Correct
Incorrect
Hint
To reset the password we can type “confreg 0x2142” under rommon mode to set the configuration register to 2142 in hexadecimal (the prefix 0x means hexadecimal (base 16)). With this setting when that router reboots, it bypasses the startup-config. -
Question 12 of 89
12. Question
1 pointsA network engineer wants to allow a temporary entry for a remote user with a specific username and password so that the user can access the entire network over the internet. Which ACL can be used?Correct
Incorrect
Hint
We can use a dynamic access list to authenticate a remote user with a specific username and password. The authentication process is done by the router or a central access server such as a TACACS+ or RADIUS server. The configuration of dynamic ACL can be read here: http://www.cisco.com/en/US/tech/tk583/tk822/technologies_tech_note09186a0080094524.shtml -
Question 13 of 89
13. Question
1 pointsWhat should be part of a comprehensive network security plan?Correct
Incorrect
Hint
All other answers are not recommended for a network security plan so only B is the correct answer. -
Question 14 of 89
14. Question
1 pointsWhich password types are encrypted?Correct
Incorrect
Hint
The “enable secret” password is always encrypted (independent of the “service password-encryption” command) using MD5 hash algorithm. Note: The “enable password” does not encrypt the password and can be view in clear text in the running-config. In order to encrypt the “enable password”, use the “service password-encryption” command. In general, don’t use enable password, use enable secret instead. -
Question 15 of 89
15. Question
1 pointsWhich statement about ACLs is true?Correct
Incorrect
-
Question 16 of 89
16. Question
1 pointsWhich three options are benefits of using TACACS+ on a device? (Choose three)Correct
Incorrect
Hint
TACACS+ (and RADIUS) allow users to be authenticated against a remote server -> E is correct. TACACS+ encrypts the entire body of the packet but leaves a standard TACACS+ header -> C is correct. TACACS+ supports access-level authorization for commands. That means you can use commands to assign privilege levels on the router -> F is correct. Note: By default, there are three privilege levels on the router. + privilege level 1 = non-privileged (prompt is router>), the default level for logging in + privilege level 15 = privileged (prompt is router#), the level after going into enable mode + privilege level 0 = seldom used, but includes 5 commands: disable, enable, exit, help, and logout -
Question 17 of 89
17. Question
1 pointsHow to verify SSH connections was secured?Correct
Incorrect
-
Question 18 of 89
18. Question
1 pointsWhich cisco platform can verify ACLs?Correct
Incorrect
Hint
The APIC-EM Path Trace ACL Analysis Tool can display the ACLs that are using (by downloading the configurations after a specific period of time and shows them when we do a path trace). Therefore it helps verify the ACLs more easily.
-
Question 19 of 89
19. Question
1 pointsWhich major component of the network virtualization architecture isolate users according to policy?Correct
Incorrect
Hint
Network virtualization architecture has three main components: + Network access control and segmentation of classes of users: Users are authenticated and either allowed or denied into a logical partition. Users are segmented into employees, contractors and consultants, and guests, with respective access to IT assets. This component identifies users who are authorized to access the network and then places them into the appropriate logical partition. + Path isolation: Network isolation is preserved across the entire enterprise: from the edge to the campus to the WAN and back again. This component maintains traffic partitioned over a routed infrastructure and transports traffic over and between isolated partitions. The function of mapping isolated paths to VLANs and to virtual services is also performed in component. + Network Services virtualization: This component provides access to shared or dedicated network services such as security, quality of service (QoS), and address management (Dynamic Host Configuration Protocol [DHCP] and Domain Name System [DNS]). It also applies policy per partition and isolates application environments, if required. Reference: http://www.cisco.com/c/en/us/products/collateral/switches/catalyst-6500-series-switches/white_paper_c11-531522.pdf -
Question 20 of 89
20. Question
1 pointsWhich two statements about firewalls are true?Correct
Incorrect
-
Question 21 of 89
21. Question
1 pointsWhich three options are types of Layer 2 network attack? (Choose three)Correct
Incorrect
Hint
 (DHCP) Spoofing attack is a type of attack in that the attacker listens for DHCP Requests from clients and answers them with fake DHCP Response before the authorized DHCP Response comes to the clients. The fake DHCP Response often gives its IP address as the client default gateway -> all the traffic sent from the client will go through the attacker computer, the attacker becomes a “man-in-the-middle”.
The attacker can have some ways to make sure its fake DHCP Response arrives first. In fact, if the attacker is “closer” than the DHCP Server then he doesn’t need to do anything. Or he can DoS the DHCP Server so that it can’t send the DHCP Response.
VLAN Hopping: By altering the VLAN ID on packets encapsulated for trunking, an attacking device can send or receive packets on various VLANs, bypassing Layer 3 security measures. VLAN hopping can be accomplished by switch spoofing or double tagging.
1) Switch spoofing:
(DHCP) Spoofing attack is a type of attack in that the attacker listens for DHCP Requests from clients and answers them with fake DHCP Response before the authorized DHCP Response comes to the clients. The fake DHCP Response often gives its IP address as the client default gateway -> all the traffic sent from the client will go through the attacker computer, the attacker becomes a “man-in-the-middle”.
The attacker can have some ways to make sure its fake DHCP Response arrives first. In fact, if the attacker is “closer” than the DHCP Server then he doesn’t need to do anything. Or he can DoS the DHCP Server so that it can’t send the DHCP Response.
VLAN Hopping: By altering the VLAN ID on packets encapsulated for trunking, an attacking device can send or receive packets on various VLANs, bypassing Layer 3 security measures. VLAN hopping can be accomplished by switch spoofing or double tagging.
1) Switch spoofing:
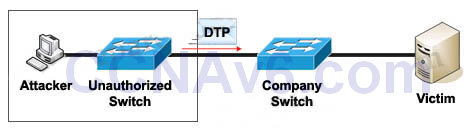 The attacker can connect an unauthorized Cisco switch to a Company switch port. The unauthorized switch can send DTP frames and form a trunk with the Company Switch. If the attacker can establish a trunk link to the Company switch, it receives traffic to all VLANs through the trunk because all VLANs are allowed on a trunk by default.
(Instead of using a Cisco Switch, the attacker can use a software to create and send DTP frames).
2) Double-Tagging:
The attacker can connect an unauthorized Cisco switch to a Company switch port. The unauthorized switch can send DTP frames and form a trunk with the Company Switch. If the attacker can establish a trunk link to the Company switch, it receives traffic to all VLANs through the trunk because all VLANs are allowed on a trunk by default.
(Instead of using a Cisco Switch, the attacker can use a software to create and send DTP frames).
2) Double-Tagging:
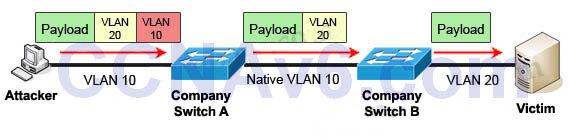 In this attack, the attacking computer generates frames with two 802.1Q tags. The first tag matches the native VLAN of the trunk port (VLAN 10 in this case), and the second matches the VLAN of a host it wants to attack (VLAN 20).
When the packet from the attacker reaches Switch A, Switch A only sees the first VLAN 10 and it matches with its native VLAN 10 so this VLAN tag is removed. Switch A forwards the frame out all links with the same native VLAN 10. Switch B receives the frame with an tag of VLAN 20 so it removes this tag and forwards out to the Victim computer.
Note: This attack only works if the trunk (between two switches) has the same native VLAN as the attacker.
ARP attack (like ARP poisoning/spoofing) is a type of attack in Which a malicious actor sends falsified ARP (Address Resolution Protocol) messages over a local area network. This results in the linking of an attacker’s MAC address with the IP address of a legitimate computer or server on the network. This is an attack based on ARP Which is at Layer 2.
In this attack, the attacking computer generates frames with two 802.1Q tags. The first tag matches the native VLAN of the trunk port (VLAN 10 in this case), and the second matches the VLAN of a host it wants to attack (VLAN 20).
When the packet from the attacker reaches Switch A, Switch A only sees the first VLAN 10 and it matches with its native VLAN 10 so this VLAN tag is removed. Switch A forwards the frame out all links with the same native VLAN 10. Switch B receives the frame with an tag of VLAN 20 so it removes this tag and forwards out to the Victim computer.
Note: This attack only works if the trunk (between two switches) has the same native VLAN as the attacker.
ARP attack (like ARP poisoning/spoofing) is a type of attack in Which a malicious actor sends falsified ARP (Address Resolution Protocol) messages over a local area network. This results in the linking of an attacker’s MAC address with the IP address of a legitimate computer or server on the network. This is an attack based on ARP Which is at Layer 2. -
Question 22 of 89
22. Question
1 pointsBy default, how many MAC addresses are permitted to be learned on a switch port with port security enabled?Correct
Incorrect
Hint
By default, port security limits the MAC address that can connect to a switch port to one. If the maximum number of MAC addresses is reached, when another MAC address attempting to access the port a security violation occurs. -
Question 23 of 89
23. Question
1 pointsWhich option is the default switch port port-security violation mode?Correct
Incorrect
Hint
Shutdown is the default switch port port-security violation mode. When in this mode, the switch will automatically force the switchport into an error disabled (err-disable) state when a violation occurs. While in this state, the switchport forwards no traffic. The switchport can be brought out of this error disabled state by issuing the errdisable recovery cause CLI command or by disabling and re-enabling the switchport. -
Question 24 of 89
24. Question
1 pointsWhich three features are represented by the letter A in AAA authentication? (Choose three)Correct
Incorrect
-
Question 25 of 89
25. Question
1 pointsWhat is a possible reason why a host is able to ping a web server but it is not able to do an HTTP request?Correct
Incorrect
-
Question 26 of 89
26. Question
1 pointsWhich item represents the standard IP ACL?Correct
Incorrect
Hint
The range of standard ACL is 1-99, 1300-1999 so 50 is a valid number for standard ACL. -
Question 27 of 89
27. Question
1 pointsWhich statement about recovering a password on a Cisco router is true?Correct
Incorrect
Hint
Other choices are surely incorrect so only “physical access” answer is the correct one. In order to recover a password on a Cisco router, the first thing you have to do is either switch off or shut down the router. For more information about this process, please read http://www.cisco.com/c/en/us/support/docs/routers/2800-series-integrated-services-routers/112033-c2900-password-recovery-00.html -
Question 28 of 89
28. Question
1 pointsWhere information about untrusted hosts are stored?Correct
Incorrect
Hint
The DHCP snooping binding database is also referred to as the DHCP snooping binding table. The DHCP snooping feature dynamically builds and maintains the database using information extracted from intercepted DHCP messages. The database contains an entry for each untrusted host with a leased IP address if the host is associated with a VLAN that has DHCP snooping enabled. The database does not contain entries for hosts connected through trusted interfaces. Reference: http://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst6500/ios/12-2SX/configuration/guide/book/snoodhcp.html -
Question 29 of 89
29. Question
1 pointsWhich two statements about TACACS+ are true? (Choose two.)Correct
Incorrect
Hint
http://tacacs.net/docs/TACACS_Advantages.pdf Many IT departments choose to use AAA (Authentication, Authorization and Accounting) protocols RADIUS or TACACS+ to address these issues. http://www.cisco.com/c/en/us/support/docs/security-vpn/terminal-access-controller-access-control-system-tacacs-/13865-tacplus.pdf This document describes how to configure a Cisco router for authentication with the TACACS+ that runs on UNIX. TACACS+ does not offer as many features as the commercially available Cisco Secure ACS for Windows or Cisco Secure ACS UNIX. TACACS+ software previously provided by Cisco Systems has been discontinued and is no longer supported by Cisco Systems. -
Question 30 of 89
30. Question
1 pointsWhich two passwords must be supplied in order to connect by Telnet to a properly secured Cisco switch and make changes to the device configuration? (Choose two.)Correct
Incorrect
-
Question 31 of 89
31. Question
1 pointsIn order to comply with new auditing standards, a security administrator must be able to correlate system security alert logs directly with the employee who triggers the alert. Which of the following should the security administrator implement in order to meet this requirement?Correct
Incorrect
-
Question 32 of 89
32. Question
1 pointsWhich action can change the order of entries in a named access-list?Correct
Incorrect
Hint
You can check the named access-list with the “show ip access-list” (or “show access-list”) command:R1#show ip access-list Standard IP access list nat_traffic 10 permit 10.1.0.0, wildcard bits 0.0.255.255 15 permit 10.2.0.0, wildcard bits 0.0.255.255 20 permit 10.3.0.0, wildcard bits 0.0.255.255We can resequence a named access-list with the command: “ip access-list resequence access-list-name starting-sequence-number increment“. For example: R1(config)#ip access-list nat_traffic 100 10 Then we can check this access-list again:R1#show ip access-list Standard IP access list nat_traffic 100 permit 10.1.0.0, wildcard bits 0.0.255.255 110 permit 10.2.0.0, wildcard bits 0.0.255.255 120 permit 10.3.0.0, wildcard bits 0.0.255.255We can see the starting sequence number is now 100 and the increment is 10. But notice that resequencing an access-list cannot change the order of entries inside it but it is the best choice in this question. Adding or removing a n entry does not change the order of entries. Maybe we should understand this question “how to renumber the entries in a named access-list”. -
Question 33 of 89
33. Question
1 pointsWhat is the effect of using the service password-encryption command?Correct
Incorrect
-
Question 34 of 89
34. Question
1 pointsRefer to the exhibit. Which user-mode password has just been set?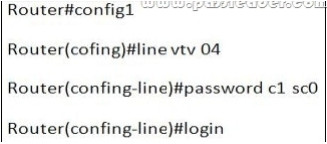 Correct
Correct
Incorrect
Hint
When you connect to a switch/router via Telnet, you first need to provide Telnet password first. Then to access Privileged mode (Switch#) you need to provide secret password after typing “enable” before making any changes. -
Question 35 of 89
35. Question
1 pointsWhat is a difference between TACACS+ and RADIUS in AAA?Correct
Incorrect
Hint
TACACS+ is an AAA protocol developed by Cisco. TACACS+ separates the authentication, authorization, and accounting steps. This architecture allows for separate authentication solutions while still using TACACS+ for authorization and accounting. For example, it is possible to use the Kerberos Protocol for authentication and TACACS+ for authorization and accounting. After an AAA client passes authentication through a Kerberos server, the AAA client requests authorization information from a TACACS+ server without the necessity to re-authenticate the AAA client by using the TACACS+ authentication mechanism. Authentication and authorization are not separated in a RADIUS transaction. When the authentication request is sent to a AAA server, the AAA client expects to have the authorization result sent back in reply. Reference: http://www.cisco.com/c/dam/en/us/products/collateral/security/secure-access-control-server-windows/prod_white_paper0900aecd80737943.pdf -
Question 36 of 89
36. Question
1 pointsWhich port security violation mode allows traffic from valid mac address to pass but block traffic from invalid mac address?Correct
Incorrect
Hint
In fact both “protect” and “restrict” mode allows traffic from passing with a valid MAC address so this question is not good. This is a quote from Cisco for these two modes: protect: drops packets with unknown source addresses until you remove a sufficient number of secure MAC addresses to drop below the maximum value. restrict: drops packets with unknown source addresses until you remove a sufficient number of secure MAC addresses to drop below the maximum value and causes the SecurityViolation counter to increment. Reference: https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst6500/ios/12-2SX/configuration/guide/book/port_sec.pdf Therefore the only difference between these two modes is “restrict” mode causes the SecurityViolation counter to increment (only useful for statistics). -
Question 37 of 89
37. Question
1 pointsWhich command can you enter in a network switch configuration so that learned mac addresses are saved in configuration as they connect?Correct
Incorrect
Hint
The full command should be “switchport port-security mac-address sticky” but we can abbreviate in Cisco command. -
Question 38 of 89
38. Question
1 pointsWhich major component of the Cisco network virtualization architecture isolates users according to policy?Correct
Incorrect
-
Question 39 of 89
39. Question
1 pointsOn Which combinations are standard access lists based?Correct
Incorrect
Hint
Standard ACL’s only examine the source IP address/mask to determine if a match is made. Extended ACL’s examine the source and destination address, as well as port information. -
Question 40 of 89
40. Question
1 pointsWhich statement about access lists that are applied to an interface is true?Correct
Incorrect
Hint
We can have only 1 access list per protocol, per direction and per interface. It means: + We cannot have 2 inbound access lists on an interface + We can have 1 inbound and 1 outbound access list on an interface -
Question 41 of 89
41. Question
1 pointsA network administrator is configuring ACLs on a Cisco router, to allow traffic from hosts on networks 192.168.146.0, 192.168.147.0, 192.168.148.0, and 192.168.149.0 only. Which two ACL statements, when combined, would you use to accomplish this task? (Choose two.)Correct
Incorrect
Hint
access-list 10 permit ip 192.168.146.0 0.0.1.255 will include the 192.168.146.0 and 192.168.147.0 subnets, while access-list 10 permit ip 192.168.148.0 0.0.1.255 will include -
Question 42 of 89
42. Question
1 pointsWhat can be done to secure the virtual terminal interfaces on a router? (Choose two.)Correct
Incorrect
Hint
It is a waste to administratively shut down the interface. Moreover, someone can still access the virtual terminal interfaces via other interfaces -> We cannot physically secure a virtual interface because it is “virtual” -> To apply an access list to a virtual terminal interface we must use the “access-class” command. The “access-group” command is only used to apply an access list to a physical interface -> C is not correct. The simplest way to secure the virtual terminal interface is to configure a username & password to prevent unauthorized login. -
Question 43 of 89
43. Question
1 pointsHow does using the service password-encryption command on a router provide additional security?Correct
Incorrect
Hint
By using this command, all the (current and future) passwords are encrypted. This command is primarily useful for keeping unauthorized individuals from viewing your password in your configuration file. -
Question 44 of 89
44. Question
1 pointsA network administrator needs to allow only one Telnet connection to a router. For anyone viewing the configuration and issuing the show run command, the password for Telnet access should be encrypted. Which set of commands will accomplish this task?Correct
Incorrect
Hint
Only one VTY connection is allowed Which is exactly what’s requested. Incorrect answer: command. line vty0 4 would enable all 5 vty connections. -
Question 45 of 89
45. Question
1 pointsRefer to the exhibit. What is the effect of the configuration that is shown?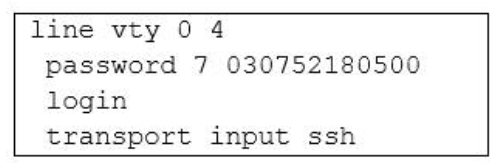 Correct
Correct
Incorrect
Hint
Secure Shell (SSH) is a protocol Which provides a secure remote access connection to network devices. Communication between the client and server is encrypted in both SSH version 1 and SSH version 2. If you want to prevent non-SSH connections, add the “transport input ssh” command under the lines to limit the router to SSH connections only. Straight (non-SSH) Telnets are refused. Reference: www.cisco.com/warp/public/707/ssh.shtml -
Question 46 of 89
46. Question
1 pointsWhich command encrypts all plaintext passwords?Correct
Incorrect
Hint
The “service password-encryption” command allows you to encrypt all passwords on your router so they cannot be easily guessed from your running-config. This command uses a very weak encryption because the router has to be very quickly decode the passwords for its operation. It is meant to prevent someone from looking over your shoulder and seeing the password, that is all. This is configured in global configuration mode. -
Question 47 of 89
47. Question
1 pointsWhat will be the result if the following configuration commands are implemented on a Cisco switch?Correct
Incorrect
Hint
In the interface configuration mode, the command switchport port-security mac-address sticky enables sticky learning. When entering this command, the interface converts all the dynamic secure MAC addresses to sticky secure MAC addresses. -
Question 48 of 89
48. Question
1 pointsRefer to exhibit. A network administrator cannot establish a Telnet session with the indicated router. What is the cause of this failure?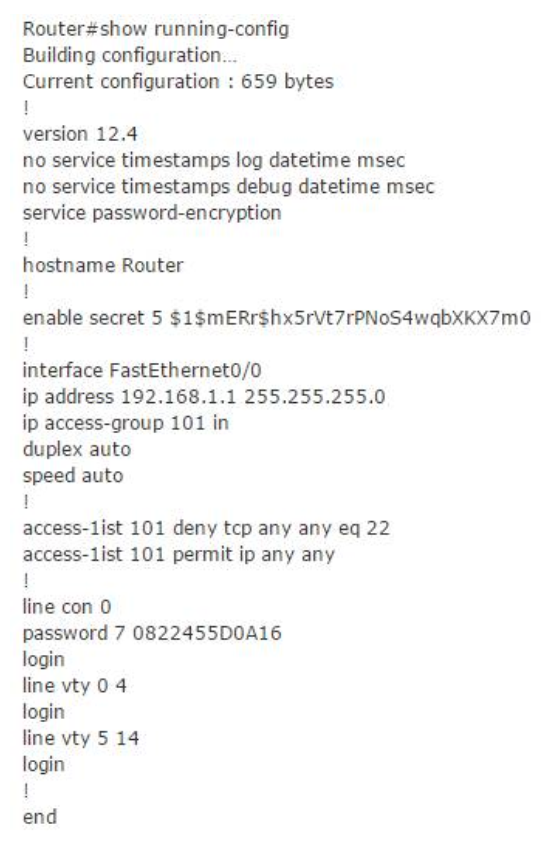 Correct
Correct
Incorrect
Hint
The login keyword has been set, but not password. This will result in the “password required, but none set” message to users trying to telnet to this router. -
Question 49 of 89
49. Question
1 pointsWhen you are troubleshooting an ACL issue on a router, Which command would you use to verify Which interfaces are affected by the ACL?Correct
Incorrect
Hint
show ip access-lists does not show interfaces affected by an ACL. -
Question 50 of 89
50. Question
1 pointsRefer to the exhibit. An attempt to deny web access to a subnet blocks all traffic from the subnet. Which interface command immediately removes the effect of ACL 102?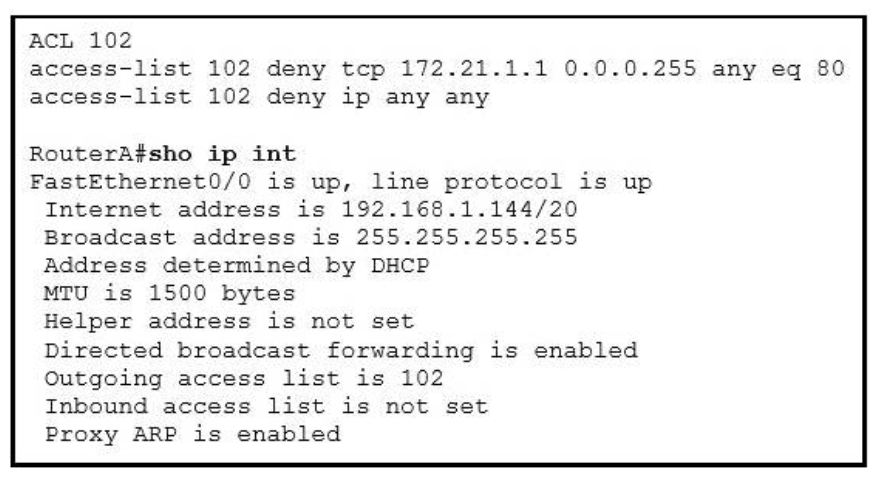 Correct
Correct
Incorrect
Hint
Now let’s find out the range of the networks on serial link: For the network 192.168.1.62/27: Increment: 32 Network address: 192.168.1.32 Broadcast address: 192.168.1.63 For the network 192.168.1.65/27:Increment: 32 Network address: 192.168.1.64 Broadcast address: 192.168.1.95 -> These two IP addresses don’t belong to the same network and they can’t see each other -
Question 51 of 89
51. Question
1 pointsRefer to the exhibit. Statements A, B, C, and D of ACL 10 have been entered in the shown order and applied to interface E0 inbound, to prevent all hosts (except those whose addresses are the first and last IP of subnet 172.21.1.128/28) from accessing the network. But as is, the ACL does not restrict anyone from the network. How can the ACL statements be re-arranged so that the system works as intended?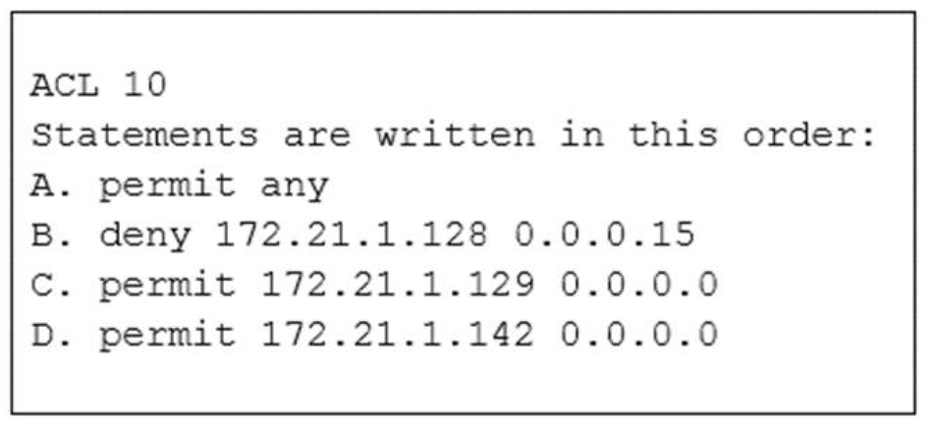 Correct
Correct
Incorrect
Hint
Routers go line by line through an access list until a match is found and then will not look any further, even if a more specific of better match is found later on in the access list. So, it it best to begin with the most specific entries first, in this cast the two hosts in line C and D. Then, include the subnet (B) and then finally the rest of the traffic (A). -
Question 52 of 89
52. Question
1 pointsWhat are two characteristics of SSH? (Choose two.)Correct
Incorrect
-
Question 53 of 89
53. Question
1 pointsRefer to the exhibit. The access list has been configured on the S0/0 interface of router RTB in the outbound direction. Which two packets, if routed to the interface, will be denied? (Choose two.)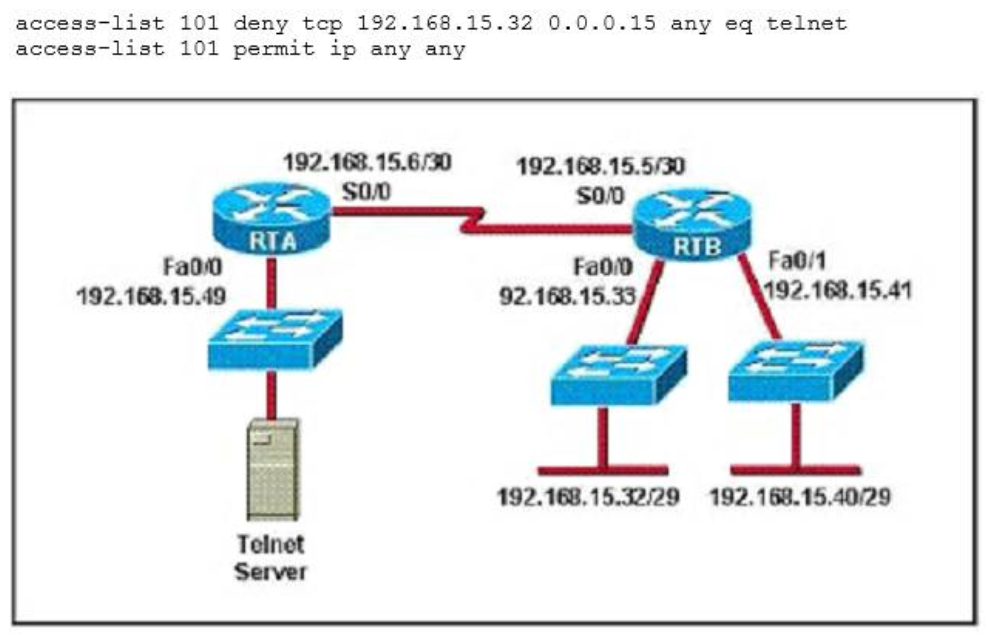 Correct
Correct
Incorrect
-
Question 54 of 89
54. Question
1 pointsRefer to the graphic. It has been decided that Workstation 1 should be denied access to Server1. Which of the following commands are required to prevent only Workstation 1 from accessing Server1 while allowing all other traffic to flow normally? (Choose two.)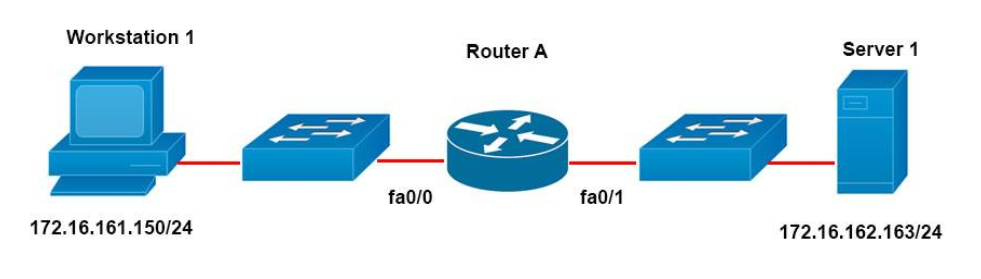 Correct
Correct
Incorrect
-
Question 55 of 89
55. Question
1 pointsAn access list was written with the four statements shown in the graphic. Which single access list statement will combine all four of these statements into a single statement that will have exactly the same effect?Correct
Incorrect
-
Question 56 of 89
56. Question
1 pointsA network administrator wants to add a line to an access list that will block only Telnet access by the hosts on subnet 192.168.1.128/28 to the server at 192.168.1.5. What command should be issued to accomplish this task?Correct
Incorrect
-
Question 57 of 89
57. Question
1 pointsAs a network administrator, you have been instructed to prevent all traffic originating on the LAN from entering the R2 router. Which the following command would implement the access list on the interface of the R2 router?Correct
Incorrect
-
Question 58 of 89
58. Question
1 pointsThe access control list shown in the graphic has been applied to the Ethernet interface of router R1 using the ip access-group 101 in command. Which of the following Telnet sessions will be blocked by this ACL? (Choose two.)Correct
Incorrect
-
Question 59 of 89
59. Question
1 pointsThe following access list below was applied outbound on the E0 interface connected to the 192.169.1.8/29 LAN: access-list 135 deny tcp 192.169.1.8 0.0.0.7 eq 20 any access-list 135 deny tcp 192.169.1.8 0.0.0.7 eq 21 any How will the above access lists affect traffic?Correct
Incorrect
-
Question 60 of 89
60. Question
1 pointsThe following configuration line was added to router R1 Access-list 101 permit ip 10.25.30.0 0.0.0.255 any. What is the effect of this access list configuration?Correct
Incorrect
-
Question 61 of 89
61. Question
1 pointsThis graphic shows the results of an attempt to open a Telnet connection to router ACCESS1 from router Remote27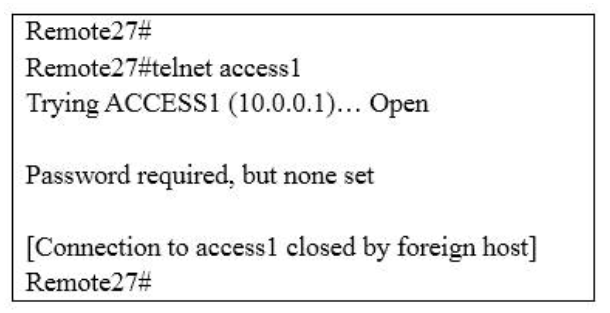 Which of the following command sequences will correct this problem? Correct
Which of the following command sequences will correct this problem? Correct
Incorrect
-
Question 62 of 89
62. Question
1 pointsWhat are two recommended ways of protecting network device configuration files from outside network security threats? (Choose two.)Correct
Incorrect
-
Question 63 of 89
63. Question
1 pointsRefer to the exhibit. What is the result of setting the no login command?Router#config t Router(config)#line vty 0 4 Router(config-line)#password c1sc0 Router(config-line)#no login
Correct
Incorrect
Hint
This configuration will let someone telnet to that router without the password (so the line “password c1sco” is not necessary). -
Question 64 of 89
64. Question
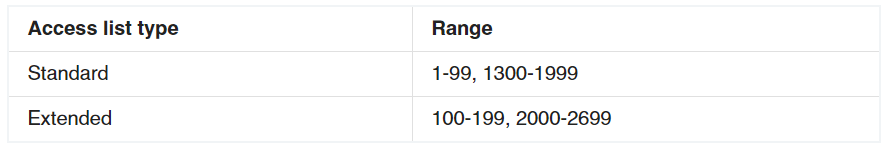
1 pointsWhich identification number is valid for an extended ACL?Correct
Incorrect
-
Question 65 of 89
65. Question
1 pointsWhich statement about named ACLs is true?Correct
Incorrect
Hint
Named Access Control Lists (ACLs) allows standard and extended ACLs to be given names instead of numbers. Unlike in numbered Access Control Lists (ACLs), we can edit Named Access Control Lists. Another benefit of using named access configuration mode is that you can add new statements to the access list, and insert them wherever you like. With the legacy syntax, you must delete the entire access list before reapplying it using the updated rules -
Question 66 of 89
66. Question
1 pointsWhich two values are needed to run the APIC-EM ACL Analysis tool ?(choose two)Correct
Incorrect
-
Question 67 of 89
67. Question
1 pointsWhich command sets and automatically encrypts the privileged enable mode password?Correct
Incorrect
-
Question 68 of 89
68. Question
1 pointsThe enable secret command is used to secure access to Which CLI mode?Correct
Incorrect
-
Question 69 of 89
69. Question
1 pointsWhich two statements about stateful firewalls in an enterprise network are true?Correct
Incorrect
-
Question 70 of 89
70. Question
1 pointsWhich type of access list compares source and destination IP addresses?Correct
Incorrect
-
Question 71 of 89
71. Question
1 pointsWhich two descriptions of TACACS+ are true? (Choose two.)Correct
Incorrect
-
Question 72 of 89
72. Question
1 pointsWhich condition indicates that service password-encryption is enabled?Correct
Incorrect
Hint
The service password-encryption command will encrypt all current and future passwords so any password existed in the configuration will be encrypted. -
Question 73 of 89
73. Question
1 pointsWhich command can you use to test whether a switch supports secure connections and strong authentication?Correct
Incorrect
-
Question 74 of 89
74. Question
1 pointsWhich port security mode can assist with troubleshooting by keeping count of violations?Correct
Incorrect
-
Question 75 of 89
75. Question
1 pointsWhich range represents the standard access list?Correct
Incorrect
-
Question 76 of 89
76. Question
1 pointsWhich of the following encrypts the traffic on a leased line?Correct
Incorrect
Hint
SSH, or secure shell, is a secure protocol that provides a built-in encryption mechanism for establishing a secured connection between two parties, authenticating each side to the other, and passing commands and output back and forth. Note: Virtual Private Networks (VPNs) are only secure if encrypted. The word “private” only means a given user’s virtual network is not shared with others. In reality a VPN still runs on a shared infrastructure and is not secured if not encrypted. VPNs are used over a connection you already have. That might be a leased line. It might be an ADSL connection. It could be a mobile network connection. Therefore answer “SSH” is still better than the answer “VPN”. -
Question 77 of 89
77. Question
1 pointsA security administrator wants to profile endpoints and gain visibility into attempted authentications. Which 802.1x mode allows these actions?Correct
Incorrect
Hint
There are three authentication and authorization modes for 802.1x: + Monitor mode + Low impact mode + High security mode Monitor mode allows for the deployment of the authentication methods IEEE 802.1X without any effect to user or endpoint access to the network. Monitor mode is basically like placing a security camera at the door to monitor and record port access behavior. With AAA RADIUS accounting enabled, you can log authentication attempts and gain visibility into who and what is connecting to your network with an audit trail. You can discover the following: + Which endpoints such as PCs, printers, cameras, and so on, are connecting to your network + Where these endpoints connected + Whether they are 802.1X capable or not + Whether they have valid credentials + In the event of failed MAB attempts, whether the endpoints have known, valid MAC addresses Monitor mode is enabled using 802.1X with the open access and multiauth mode Cisco IOS Software features enabled, as follows: sw(config-if)#authentication open sw(config-if)#authentication host-mode multi-auth For more information about each mode, please read this article: http://www.cisco.com/c/en/us/td/docs/solutions/Enterprise/Security/TrustSec_1-99/Phased_Deploy/Phased_Dep_Guide.html -
Question 78 of 89
78. Question
1 pointsWhat are two statements for SSH? (Choose two.)Correct
Incorrect
-
Question 79 of 89
79. Question
1 pointsWhich command shows your active Telnet connections?Correct
Incorrect
Hint
The “show users” shows telnet/ssh connections to your router while “show sessions” shows telnet/ssh connections from your router (to other devices). The question asks about “your active Telnet connections”, meaning connections from your router -
Question 80 of 89
80. Question
1 pointsWhich IPsec security protocol should be used when confidentiality is required?Correct
Incorrect
Hint
IPsec is a pair of protocols, Encapsulating Security Payload (ESP) and Authentication Header (AH), Which provide security services for IP datagrams. ESP can provide the properties authentication, integrity, replay protection, and confidentiality of the data (it secures everything in the packet that follows the IP header). AH provides authentication, integrity, and replay protection (but not confidentiality) of the sender. -
Question 81 of 89
81. Question
1 pointsWhat are two characteristics of Telnet? (Choose two.)Correct
Incorrect
-
Question 82 of 89
82. Question
1 pointsWhich protocol authenticates connected devices before allowing them to access the LAN?Correct
Incorrect
Hint
802.1X authentication involves three parties: a supplicant, an authenticator, and an authentication server. The supplicant is a client device (such as a laptop) that wishes to attach to the LAN/WLAN. The term ‘supplicant’ is also used interchangeably to refer to the software running on the client that provides credentials to the authenticator. The authenticator is a network device, such as an Ethernet switch or wireless access point; and the authentication server is typically a host running software supporting the RADIUS and EAP protocols. The authenticator acts like a security guard to a protected network. The supplicant (i.e., client device) is not allowed access through the authenticator to the protected side of the network until the supplicant’s identity hasbeen validated and authorized. An analogy to this is providing a valid visa at the airport’s arrival immigration before being allowed to enter the country. With 802.1X port-based authentication, the supplicant provides credentials, such as user name/password or digital certificate, to the authenticator, and the authenticator forwards the credentials to the authentication server for verification. If the authentication server determines the credentials are valid, the supplicant (client device) is allowed to access resources located on the protected side of the network. -
Question 83 of 89
83. Question
1 pointsRefer to the exhibit. You have determined that computer A cannot ping computer B. Which reason for the problem is most likely true?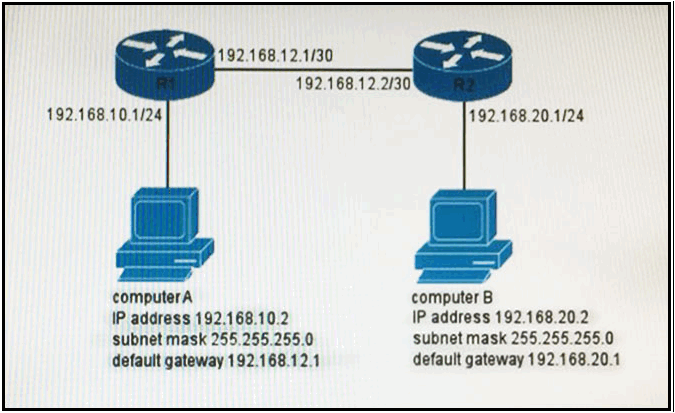 Correct
Correct
Incorrect
-
Question 84 of 89
84. Question
1 pointsWhich IEEE mechanism is responsible for the authentication of devices when they attempt to connect to a local network?Correct
Incorrect
Hint
IEEE 802.1X is an IEEE Standard for port-based Network Access Control (PNAC). It is part of the IEEE 802.1 group of networking protocols. It provides an authentication mechanism to devices wishing to attach to a LAN or WLAN -
Question 85 of 89
85. Question
1 pointsWhich two values must you specify to perform an ACL-based Path Trace using APIC-EM? (Choose two.)Correct
Incorrect
-
Question 86 of 89
86. Question
1 pointsWhich two services can be provided by a wireless controller? (Choose two.)Correct
Incorrect
-
Question 87 of 89
87. Question
1 pointsWhich of the following privilege level is the most secured?Correct
Incorrect
Hint
By default, the Cisco IOS CLI has two privilege levels enabled, level 1 and level 15. + User EXEC mode (privilege level 1): provides the lowest EXEC mode user privileges and allows only user-level commands available at the Router> prompt. + Privileged EXEC mode (privilege level 15): includes all enable-level commands at the Router# prompt. Level 15 users can execute all commands and this is the most secured and powerful privilege level. However, there are actually 16 privilege levels available on the CLI, from 0 to 15 and you can assign users to any of those levels. Zero-level access allows only five commands -logout, enable, disable, help, and exit. User level (level 1) provides very limited read-only access to the router, and privileged level (level 15) provides complete control over the router. -
Question 88 of 89
88. Question
1 pointsDRAG DROP. Drag the security features on the left to the specific security risks they help protect against on the right. (Not all options are used.) Select and Place: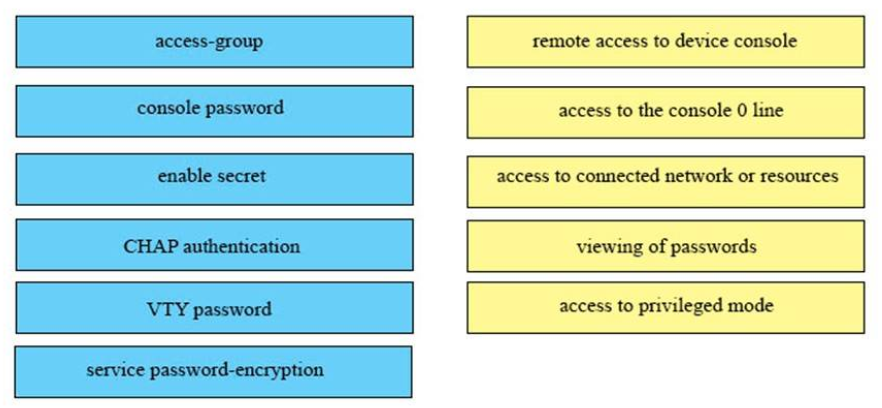
Sort elements
- VTY password
- console password
- access-group
- service password-encryption
- enable secret
- CHAP authentication
-
remote access to device console
-
access to the console 0 line
-
access to connected network or resources
-
viewing of passwords
-
access to privileged mode
Correct
Incorrect
-
Question 89 of 89
89. Question
1 pointsDRAG DROP. An interface has been configured with the access list that is shown below. On the basis of that access list,drag each information packet on the left to the appropriate category on the right. Select and Place:
Select and Place:
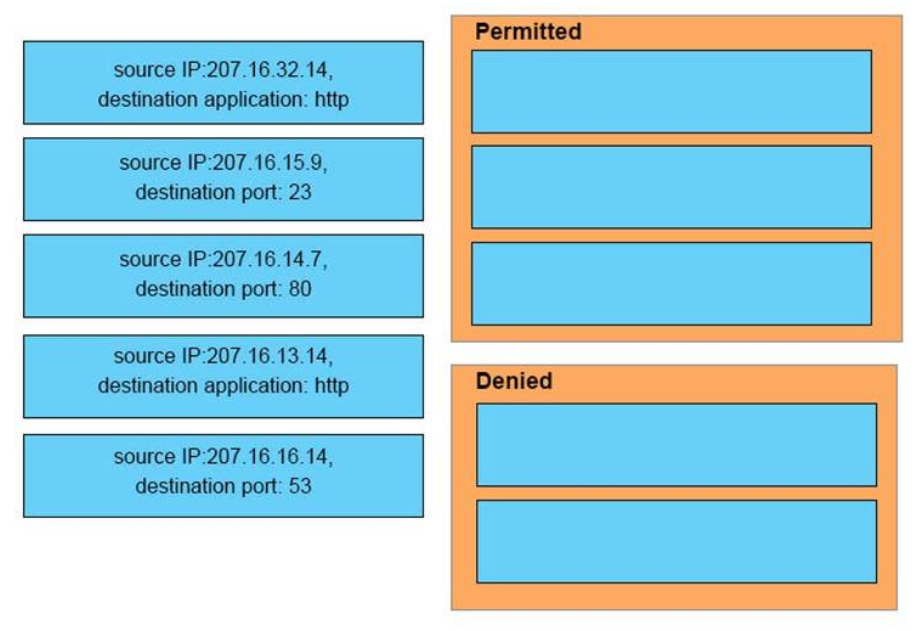
Sort elements
- source IP: 207.16.32.14 destination application: http
- source IP: 207.16.15.9 destination port: 23
- source IP: 207.16.16.14 destination port: 53
- source IP: 207.16.14.7 destination port: 80
- source IP: 207.16.13.14 destination application: http
-
Permitted (1)
-
Permitted (2)
-
Permitted (3)
-
Denied (1)
-
Denied (2)
Correct
Incorrect