Networking Devices and Initial Configuration Module 11.5.3 Build a Small Cisco Network Quiz Answers
1. A user can print to a printer that is on the same network, but the traffic of the user cannot reach the internet. What is a possible cause of the problem?
- The PC default gateway address is missing or incorrect.
- The PC has an incorrect IP address.
- The network cable connected to the user PC is faulty.
- The NIC on the PC is faulty.
2. Which connection provides a secure CLI session with encryption to a Cisco switch?
- a console connection
- an AUX connection
- a Telnet connection
- an SSH connection
3. On which switch interface would an administrator configure an IP address so that the switch can be managed remotely?
- FastEthernet0/1
- VLAN 1
- vty 0
- console 0
4. An administrator defined a local user account with a secret password on router R1 for use with SSH. Which three additional steps are required to configure R1 to accept only encrypted SSH connections? (Choose three.)
- Configure the IP domain name on the router.
- Enable inbound vty Telnet sessions.
- Generate the SSH keys.
- Configure DNS on the router.
- Enable inbound vty SSH sessions.
- Generate two-way pre-shared keys.
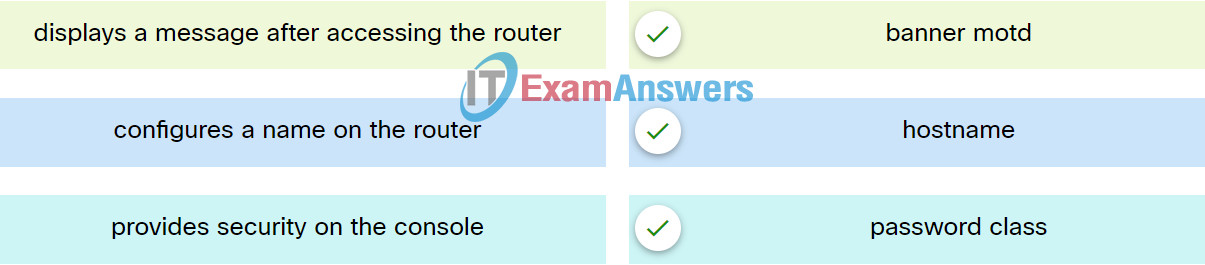
5. Match the commands to the correct actions.
6. A technician is configuring a router to allow for all forms of management access. As part of each different type of access, the technician is trying to type the command login. Which configuration mode should be entered to do this task?
- user executive mode
- global configuration mode
- any line configuration mode
- privileged EXEC mode
7. Which statement describes SVIs?
- An SVI is created automatically for each VLAN on a multilayer switch.
- Creating an SVI automatically creates an associated VLAN.
- A default SVI is created for VLAN 1 for switch administration.
- An SVI can only be created for the management purposes.
8. What is one difference between using Telnet or SSH to connect to a network device for management purposes?
- Telnet uses UDP as the transport protocol whereas SSH uses TCP.
- Telnet does not provide authentication whereas SSH provides authentication.
- Telnet supports a host GUI whereas SSH only supports a host CLI.
- Telnet sends a username and password in plain text, whereas SSH encrypts the username and password.
9. Which type of access is secured on a Cisco router or switch with the enable secret command?
- virtual terminal
- privileged EXEC
- AUX port
- console line
10. Which statement regarding the service password-encryption command is true?
- It is configured in privileged EXEC mode.
- It encrypts only line mode passwords.
- As soon as the service password-encryption command is entered, all currently set passwords formerly displayed in plain text are encrypted.
- To see the passwords encrypted by the service password-encryption command in plain text, issue the no service password-encryption command.
11. What happens when the transport input ssh command is entered on the switch vty lines?
- The SSH client on the switch is enabled.
- Communication between the switch and remote users is encrypted.
- The switch requires a username/password combination for remote access.
- The switch requires remote connections via a proprietary client software.
