Time limit: 0
Quiz-summary
0 of 40 questions completed
Questions:
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
Information
Networking Devices and Initial Configuration Course Final Test Online
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading...
You must sign in or sign up to start the quiz.
You have to finish following quiz, to start this quiz:
Results
0 of 40 questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 points, (0)
| Average score |
|
| Your score |
|
Categories
- Not categorized 0%
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- Answered
- Review
-
Question 1 of 40
1. Question
1 pointsMatch the definition to the type of cloud.Correct
Incorrect
Hint
Place the options in the following order:intended for exclusive use by multiple organizations with shared functional needs community services made available to the general population public cloud made up of two or more distinct cloud infrastructures bound together by technology hybrid cloud intended for a specific organization or entity, such as the government private cloud -
Question 2 of 40
2. Question
1 pointsA data center has recently updated a physical server to host multiple operating systems on a single CPU. The data center can now provide each customer with a separate web server without having to allocate an actual discrete server for each customer. What is the networking trend that is being implemented by the data center in this situation?Correct
Incorrect
Hint
Virtualization technology can run several different operating systems in parallel on a single CPU. -
Question 3 of 40
3. Question
1 pointsWhat is an example of cloud computing?Correct
Incorrect
Hint
Cloud computing provides on-demand access to shared resources. With minimal management effort, resources can be deployed quickly at data centers. -
Question 4 of 40
4. Question
1 pointsWhich two scenarios would benefit the user the most by adding quality of service (QoS) to the network? (Choose two.)Correct
Incorrect
Hint
Voice and video data need to be transmitted in a continuous stream. If packets are delayed, the audio and video quality will be poor, sometimes even not usable. QoS can give voice and video data high priority during the data transmission so that they would be sent first before other types of traffic, such as email, web surfing, and web page update. -
Question 5 of 40
5. Question
1 pointsAn employee of a large corporation remotely logs into the company using the appropriate username and password. The employee is attending an important video conference with a customer concerning a large sale. It is important for the video quality to be excellent during the meeting. The employee is unaware that after a successful login, the connection to the company ISP failed. The secondary connection, however, activated within seconds. The disruption was not noticed by the employee or other employees. What three network characteristics are described in this scenario? (Choose three.)Correct
Incorrect
Hint
Usernames and passwords relate to network security. Good quality video, to support video conferencing, relates to prioritizing the video traffic with quality of service (QoS). The fact that a connection to an ISP failed and was then restored but went unnoticed by employees relates to the fault tolerant design of the network. -
Question 6 of 40
6. Question
1 pointsWhich three statements describe the functions of the Cisco hierarchical network design model? (Choose three.)Correct
Incorrect
Hint
There are three layers of the hierarchical network design model. – Access: Provides a connection point to end users. – Distribution: Controls traffic flows between access and core layers. – Core: Maximizes throughput moving traffic as quickly as possible. -
Question 7 of 40
7. Question
1 pointsWhat is the key difference between a type 1 hypervisor and a type 2 hypervisor?Correct
Incorrect
Hint
There are two types of hypervisors: – Type 1 – This type of hypervisor runs directly on the system hardware. – Type 2 – This type of hypervisor requires a host OS to run. Both types of hypervisors can run on regular computer systems and support multiple OS virtualizations. -
Question 8 of 40
8. Question
1 pointsRefer to the exhibit. Host A has sent a packet to host B. What will be the source MAC and IP addresses on the packet when it arrives at host B?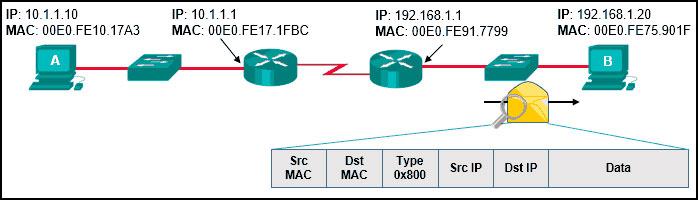 Correct
Correct
Incorrect
Hint
As a packet traverses the network, the Layer 2 addresses will change at every hop as the packet is de-encapsulated and re-encapsulated, but the Layer 3 addresses will remain the same. -
Question 9 of 40
9. Question
1 pointsWhich two statements are correct in a comparison of IPv4 and IPv6 packet headers? (Choose two.)Correct
Incorrect
Hint
The IPv6 packet header fields are as follows: Version, Traffic Class, Flow Label, Payload Length, Next Header, Hop Limit, Source Address, and Destination Address. The IPv4 packet header fields include the following: Version, Differentiated Services, Time-to-Live, Protocol, Source IP Address, and Destination IP Address. Both versions have a 4-bit Version field. Both versions have a Source (IP) Address field. IPv4 addresses are 32 bits; IPv6 addresses are 128 bits. The Time-to-Live or TTL field in IPv4 is now called Hop Limit in IPv6, but this field serves the same purpose in both versions. The value in this 8-bit field decrements each time a packet passes through any router. When this value is 0, the packet is discarded and is not forwarded to any other router. -
Question 10 of 40
10. Question
1 pointsMatch the IPv6 packet header field with the description.Correct
Incorrect
Hint
Place the options in the following order:Traffic Class 8 bit field that is equivalent to the IPv4 Differenciated Services (DS) field. Next Header 8 bit field that indicates the data payload type. Flow Label 20 bit field that maintains the same packet flows through routers and switches to ensure that the packets arrive in the same order. Payload Length 16 bit field that stipulates the length of the data portion of the IPv6 packet. Hop Limit 8 bit field that is decremented by one for each router that fowards the packet. -
Question 11 of 40
11. Question
1 pointsWhich three IPv4 header fields have no equivalent in an IPv6 header? (Choose three.)Correct
Incorrect
Hint
Unlike IPv4, IPv6 routers do not perform fragmentation. Therefore, all three fields supporting fragmentation in the IPv4 header are removed and have no equivalent in the IPv6 header. These three fields are fragment offset, flag, and identification. IPv6 does support host packet fragmentation through the use of extension headers, which are not part of the IPv6 header. -
Question 12 of 40
12. Question
1 pointsRefer to the exhibit. A ping to PC2 is issued from PC0, PC1, and PC3 in this exact order. Which MAC addresses will be contained in the S1 MAC address table that is associated with the Fa0/1 port?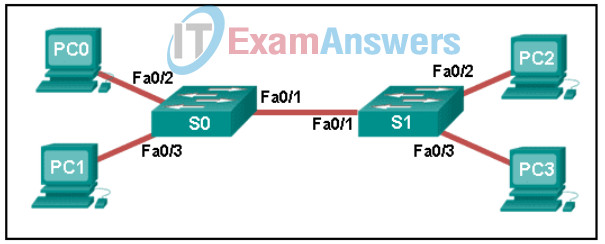 Correct
Correct
Incorrect
Hint
Switch S1 builds a MAC address table based on the source MAC address in the frame and the port upon which the frame enters the switch. The PC2 MAC address will be associated with port FA0/2. Because port FA0/1 of switch S1 connects with another switch, port FA0/1 will receive frames from multiple different devices. The MAC address table on switch S1 will therefore contain MAC addresses associated with each of the sending PCs. -
Question 13 of 40
13. Question
1 pointsMatch field names to the IP header where they would be found.Correct
Incorrect
Hint
Options matched to the correct selection.IP v4 header IP v6 header Flags Traffic Class Total Length Flow Label -
Question 14 of 40
14. Question
1 pointsWhat is the dotted decimal representation of the IPv4 address 11001011.00000000.01110001.11010011?Correct
Incorrect
Hint
Each section (octet) contains eight binary digits. Each digit represents a specific value (128, 64, 32, 16, 8, 4, 2, and 1). Everywhere there is a 1, the specific value is relevant. Add all relevant values in a particular octet to obtain the decimal value. For example binary 11001011 equals 203 in decimal. -
Question 15 of 40
15. Question
1 pointsWhich two items are used by a host device when performing an ANDing operation to determine if a destination address is on the same local network? (Choose two.)Correct
Incorrect
Hint
The result of ANDing any IP address with a subnet mask is a network number. If the source network number is the same as the destination network number, the data stays on the local network. If the destination network number is different, the packet is sent to the default gateway (the router that will send the packet onward toward the destination network). -
Question 16 of 40
16. Question
1 pointsA home network has both wired and wireless connectivity. From a laptop computer, the user issues a ping to the wireless printer located in another room. The first two echo requests fail, but the last two succeed. Additional pings are all successful. Why do the first two echo requests fail?Correct
Incorrect
Hint
In order to successfully send a packet on an Ethernet network, the computer sending the ping needs four key pieces of information: (1) source MAC address, (2) destination MAC address, (3) source IP address, and (4) destination IP address. The computer sending the ping knows its own source IP address and source MAC address. The computer also knows from the ping command the destination IP address. The only information not known is the destination MAC address. The destination MAC address is discovered by using ARP. -
Question 17 of 40
17. Question
1 pointsWhich statement is true regarding the UDP client process during a session with a server?Correct
Incorrect
Hint
Because there are no sequence numbers in UDP segments, there is no possibility to arrange the datagrams in the correct order. Sessions and three-way handshake are related to TCP communications. UDP servers can use registered or nonregistered port numbers to listen to clients. -
Question 18 of 40
18. Question
1 pointsMatch each DHCP message type with its description.Correct
Incorrect
Hint
Place the options in the following order:DHCPDISCOVER a client initiating a message to find a DHCP server DHCPOFFER a DHCP server responding to the initial request by a client DHCPREQUEST the client accepting the IP address provided by the DHCP server DHCPACK the DHCP server confirming that the address lease has been accepted -
Question 19 of 40
19. Question
1 pointsRefer to the exhibit. Which protocol was responsible for building the table that is shown?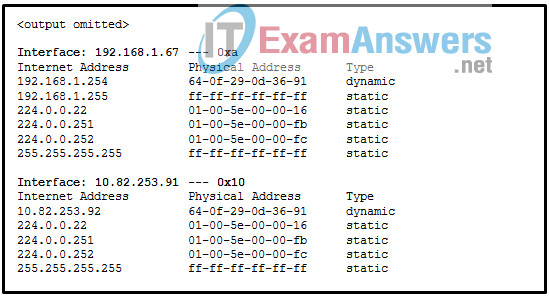 Correct
Correct
Incorrect
Hint
The table that is shown corresponds to the output of the arp -a command, a command that is used on a Windows PC to display the ARP table. -
Question 20 of 40
20. Question
1 pointsRefer to the exhibit. A web designer calls to report that the web server web-s1.cisco.com is not reachable through a web browser. The technician uses command line utilities to verify the problem and to begin the troubleshooting process. Which two things can be determined about the problem? (Choose two.)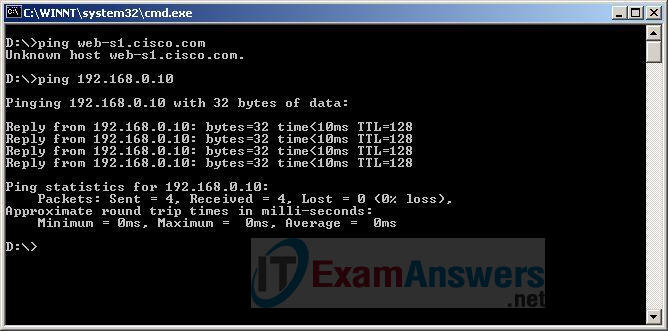 Correct
Correct
Incorrect
Hint
The successful result of the ping to the IP address indicates that the network is operational and the web server is online. However, the fact that the ping to the domain name of the server fails indicates there is a DNS issue, namely that the host cannot resolve the domain name to its associated IP address. -
Question 21 of 40
21. Question
1 pointsWhat are two potential network problems that can result from ARP operation? (Choose two.)Correct
Incorrect
Hint
Large numbers of ARP broadcast messages could cause momentary data communications delays. Network attackers could manipulate MAC address and IP address mappings in ARP messages with the intent to intercept network traffic. ARP requests and replies cause entries to be made into the ARP table, not the MAC address table. ARP table overflows are very unlikely. Manually configuring static ARP associations is a way to prevent, not facilitate, ARP poisoning and MAC address spoofing. Multiple ARP replies resulting in the switch MAC address table containing entries that match the MAC addresses of connected nodes and are associated with the relevant switch port are required for normal switch frame forwarding operations. It is not an ARP caused network problem. -
Question 22 of 40
22. Question
1 pointsMatch the TCP flag to the correct step in the session establishment sequence.Correct
Incorrect
Hint
Place the options in the following order:step 3 ACK step 1 SYN step 2 SYN + ACK -
Question 23 of 40
23. Question
1 pointsWhat is the difference between the terms keyword and argument in the IOS command structure?Correct
Incorrect
Hint
Keywords are specific parameters that are defined in IOS. Arguments are not predefined; they are the variables defined by the user when completing a command. Although most keywords appear directly after commands, they can appear in other locations, depending on a command structure. A keyword can be entered in its whole length or in a shortened format. -
Question 24 of 40
24. Question
1 pointsWhich three commands are used to set up secure access to a router through a connection to the console interface? (Choose three.)Correct
Incorrect
Hint
The three commands needed to password protect the console port are as follows: – line console 0 – password cisco – login The interface fastethernet 0/0 command is commonly used to access the configuration mode used to apply specific parameters such as the IP address to the Fa0/0 port. The line vty 0 4 command is used to access the configuration mode for Telnet. The0and 4 parameters specify ports 0 through 4, or a maximum of five simultaneous Telnet connections. The enable secret command is used to apply a password used on the router to access the privileged mode. -
Question 25 of 40
25. Question
1 pointsWhat three configuration steps must be performed to implement SSH access to a router? (Choose three.)Correct
Incorrect
Hint
To implement SSH on a router the following steps need to be performed: – Configure a unique hostname. – Configure the domain name of the network. – Configure a user account to use AAA or local database for authentication. – Generate RSA keys. – Enable VTY SSH sessions. -
Question 26 of 40
26. Question
1 pointsRefer to the exhibit. What is the maximum TTL value that is used to reach the destination www.cisco.com?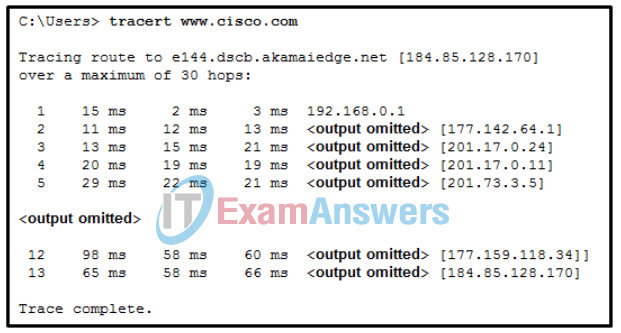 Correct
Correct
Incorrect
Hint
Traceroute (in this case the command tracert) sets the TTL field to a value of 1 and sends the packet. At each router hop, this value is decreased by one and a “TTL expired” message is sent back to the source host. This message has a source address which is used by the host to build the trace. The host then progressively increments the TTL field (2, 3, 4…) for each sequence of messages until the destination is reached or it is incremented to a predefined maximum. Because the executed command reached the destination in the 13th line, the TTL was increased up to the value of 13. -
Question 27 of 40
27. Question
1 pointsWhich protocol is used by IPv4 and IPv6 to provide error messaging?Correct
Incorrect
Hint
ICMP is used by IPv4 and IPv6 to provide for messages to be sent in the event of certain errors and for informational purposes. -
Question 28 of 40
28. Question
1 pointsThe global configuration command ip default-gateway 172.16.100.1 is applied to a switch. What is the effect of this command?Correct
Incorrect
Hint
A default gateway address is typically configured on all devices to allow them to communicate beyond just their local network.In a switch this is achieved using the command ip default-gateway <ip address>. -
Question 29 of 40
29. Question
1 pointsMatch the router prompt to the configuration task.Correct
Incorrect
Hint
Place the options in the following order:RouterA(config-line)# configure vty lines RouterA(config-if)# configure a WAN interface RouterA# enter configuration mode RouterA(config)# add a password required to access the privileged EXEC mode -
Question 30 of 40
30. Question
1 pointsWhile troubleshooting a network problem, a network administrator issues the show version command on a router. What information can be found by using this command?Correct
Incorrect
Hint
The show version command displays much information about the device, including the amount of memory (flash, NVRAM, and DRAM) that is installed on the device. -
Question 31 of 40
31. Question
1 pointsRefer to the exhibit. PC1 sends a frame with the destination MAC address 3c97.0e07.a1b2. Switch S1 looks up the destination MAC address in its CAM table but the address is not there. What will the switch do?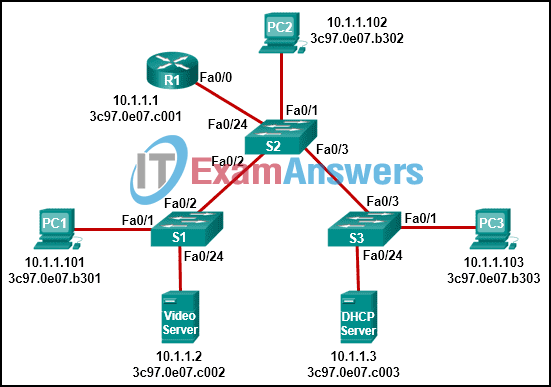 Correct
Correct
Incorrect
Hint
When a switch receives a frame with a destination that it does not already have in its CAM table, it will forward the frame out all ports except the one on which the frame was received. This is called unknown unicast flooding. -
Question 32 of 40
32. Question
1 pointsWhich forwarding action does a switch take when the destination MAC address of an Ethernet frame is an unknown unicast?Correct
Incorrect
Hint
If the destination MAC address is a unicast address, the switch will look for a match between the destination MAC address of the frame and an entry in its MAC address table:- If the destination MAC address is in the table, it will forward the frame out of the specified port.
- If the destination MAC address is not in the table (unknown unicast), the switch will forward the frame out all ports except the incoming port. If the destination MAC address is a broadcast or a multicast, the frame is also flooded out all ports except the incoming port.
-
Question 33 of 40
33. Question
1 pointsRefer to the exhibit. An administrator is troubleshooting connectivity on the office network. PC1 is able to send print jobs to Printer1, but is unable to access File Server1. Which action would correct the problem?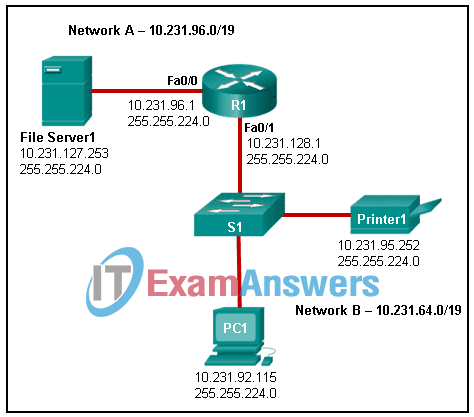 Correct
Correct
Incorrect
Hint
To correct the problem the Fa0/1 interface must be put into the 10.231.64.0 /19 network, so that it is in the same logical network as PC1. Currently the interface is in the 10.231.128.0 network. -
Question 34 of 40
34. Question
1 pointsMatch the characteristic to the protocol category.Correct
Incorrect
Hint
Options matched to the correct selection.TCP UDP Both UDP and TCP window size connectionless checksum 3-way handshake best for VoIP port number -
Question 35 of 40
35. Question
1 pointsThe ARP table in a switch maps which two types of address together?Correct
Incorrect
Hint
The switch ARP table keeps a mapping of Layer 2 MAC addresses to Layer 3 IP addresses. These mappings can be learned by the switch dynamically through ARP or statically through manual configuration. -
Question 36 of 40
36. Question
1 pointsA network administrator issues the Switch# show running-config command on a Cisco switch. Which term is used to describe the part “running-config” in the command?Correct
Incorrect
Hint
The running-config is a keyword of the show command. -
Question 37 of 40
37. Question
1 pointsThe global configuration command ip default-gateway 172.16.100.1 is applied to a switch. What is the effect of this command?Correct
Incorrect
Hint
A default gateway address is typically configured on all devices to allow them to communicate beyond just their local network.In a switch this is achieved using the command ip default-gateway <ip address>. -
Question 38 of 40
38. Question
1 pointsWhat is the purpose of the MAC address which is added to an e-mail message that is sent from a teacher to a student?Correct
Incorrect
Hint
A Media Access Control (MAC) address is unique on every device. An Internet Protocol (IP) address is used to communicate with devices on another LAN or on the Internet. -
Question 39 of 40
39. Question
1 pointsWhat is the purpose of assigning an IP address to the VLAN1 interface on a Cisco Layer 2 switch?Correct
Incorrect
Hint
The VLAN 1 on a Cisco Layer 2 switch is a virtual interface. By default, VLAN 1 is assigned as the management interface for remote access (Telnet or SSH) to the device for management tasks. In order to allow remote access through the network, a valid IP address configuration is needed on VLAN 1. -
Question 40 of 40
40. Question
1 pointsWhich command should be used to test connectivity to the loopback interface?Correct
Incorrect
Hint
The ping 127.0.0.1 command tests the TCP/IP stack through the loopback interface.
