2.2.2.5 Lab – Basic Data Analysis (Instructor Version) Objectives Use very simple methods to describe existing data, fill-in missing data values and to make simple predictions. Part 1: Learn how to Use Data as Information Part 2: Plot data and predict values Background/Scenario Data is meaningless in and …
1.3.2.9 Lab – Take the Python Challenge (Instructor Version) This is an optional exercise to test your understanding of Python basics. However, we strongly suggest the student to complete these exercises to prepare yourself for the rest of this course. If you don’t know how to solve them, …
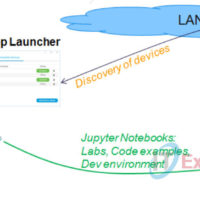
1.3.2.8 Lab – Setting up PL-app with the Raspberry Pi (Instructor Version) Lab Topology Objectives Set up a Raspberry Pi board as a PL-App device Use PL-App Launcher to provision and discover PL-App devices Background Cisco Prototyping Lab is a set of hardware and software components that enable …
1.3.2.6 Lab – Demonstrate Spreadsheet Limitations in Data Analysis (Instructor Version) Objectives Observe the limitations of a spreadsheet when it is used for data analysis. Part 1: Explore and Download the Data Part 2: Determine the Root Bridge Background / Scenario There are massive amounts of open data …
1.2.2.4 Lab – Where is My Data? (Instructor Version) Objectives Explore the ownership of your data when that data is not stored in a local system. Part 1: Explore the Terms of Service Policy Part 2: Do You Know What You Signed Up For? Background / Scenario Social …
1.2.2.3 Lab – Explore Sources of Open Data (Instructor Version) Objectives Explore the different websites that provide openly available data. Part 1: Open Government Partnership Part 2: Open Data Websites Part 3: Data Visualization Background/Scenario Immeasurable amounts of data have been generated and stored. Data is useful only …
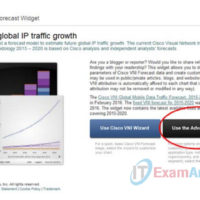
1.1.2.3 Lab – Demonstrate the Growth of Data with VNI (Instructor Version) Objective Demonstrate the growth of data using Cisco’s Visual Networking Index (VNI) web site. Part 1: Cisco VNI Forecast Widget Background/Scenario In this lab, you will access the Cisco VNI Forecast Widget to view network traffic …
IoT Fundamentals Big Data and Analytics QUIZ/Exam Answers Chapter 1: Data and the Internet of Things (Quiz Answers) Chapter 2: Fundamentals of Data Analysis (Quiz Answers) Chapter 3: Data Analysis (Quiz Answers) Chapter 4: Advanced Data Analytics and Machine Learning (Quiz Answers) Chapter 5: Storytelling with Data (Quiz …
Big Data & Analytics (Version 2) – IoT Fundamentals: Big Data and Analytics End of Course Assessment Final Exam Answers Full Questions 1. A patient who lives in Northern Canada has an MRI taken. The results of the medical procedure are immediately transmitted to a specialist in Toronto …
ENSA Bridging Exam Answers Enterprise Networking, Security, and Automation (Version 7.00) – Network Security and Automation Exam 1. Which protocol is attacked when a cybercriminal provides an invalid gateway in order to create a man-in-the-middle attack? HTTP or HTTPS DHCP DNS ICMP 2. In which TCP attack is …