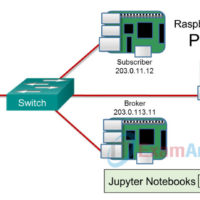
5.1.3.7 Lab – Hacking MQTT (Instructor Version) Topology Required Resources 3 Raspberry Pi 3 devices, Model B or later 8GB Micro SD card (minimum required) PC with IoTSec Kali VM Network connectivity between PC and Raspberry Pi Devices A Network Switch Objectives Part 1: Setting up a Publishing/Subscriber …
5.1.2.9 Lab – Web Application Vulnerability (Instructor Version) Topology Required Resources Raspberry Pi 3 Model B or later (with PL-App) 8GB Micro SD card (minimum required) PC with IoTSec Kali VM Network connectivity between PC and Raspberry Pi Objectives In this lab, you will discover vulnerabilities in a …
5.1.2.8 Lab – Challenge Passwords with Kali Tools (Instructor Version) Objectives In this lab, you will explore tools that are available in the Kali VM to challenge passwords. Part 1: Using Hashcat to Challenge Passwords Part 2: Investigating Other Password Challenging Tools on Kali Linux Background / Scenario …
5.1.2.7 Lab – Use OpenVAS for Vulnerability Assessment (Instructor Version) Addressing Table Device IP Address Subnet Mask Kali 203.0.113.1 255.255.255.0 Metasploitable 203.0.113.5 255.255.255.0 Objectives Part 1: Exploring OpenVAS Part 2: Configuring a Vulnerability Scan Part 3: Reviewing the Results Background / Scenario Open Vulnerability Assessment System (OpenVAS) is …
4.2.2.6 Lab – Packet Crafting to Exploit Unsecured Ports (Instructor Version) Topology Objectives Part 1: Using hping3 for Port Scanning Part 2: Crafting Different Types of ICMP Messages Part 3: Launching DoS Attacks Background / Scenario hping3 is a tool used to send custom-crafted TCP/IP packets to a …
4.2.2.5 Lab – Port Scanning an IoT Device (Instructor Version) Topology Objectives Part 1: Perform a Nmap network discovery scan Part 2: Compare a Nmap TCP default port scan and full scan Part 3: Perform a Nmap UDP Scan Part 4: Perform Nmap OS and Service Foot Printing …
4.1.2.3 Lab – Sniffing Bluetooth with the Raspberry Pi (Instructor Version) Topology Objectives In this lab, students will become familiar with varying levels of security on different common devices that use Bluetooth/BLE (Bluetooth Low Energy). Students will configure a Raspberry Pi to detect and display information about the …
3.2.2.7 Lab – Compromise IoT Device Firmware (Instructor Version) Objectives Part 1: Performing Threat Modeling Activities to Evaluate IoT Device Firmware Part 2: Reflection and Discussion of Threats to IoT Device Firmware Background / Scenario IoT devices are susceptible to attacks like many other Internet connected devices running …
3.2.1.5 Lab – Compromise IoT Device Hardware (Instructor Version) Topology Raspberry Pi Pinout Diagram Objectives Perform threat modeling activities to evaluate IoT device hardware and firmware. Part 1: Accessing the Raspberry Pi with Serial Interface Part 2: Disabling Serial Login Access to Raspberry Pi Background / Scenario This …
3.2.1.4 Lab – Investigate the FCC Database (Instructor Version) Objectives Use the Federal Communications Commission (FCC) database to view information about various IoT devices that utilize radio frequencies for data transmission. The database has information that could benefit both the user and a potential attacker. Part 1: Search …