CCNA Security Chapter 4 Exam Answers (CCNAS v1.2 and v1.1) 1. Which statement accurately describes Cisco IOS zone-based policy firewall operation? The pass action works in only one direction. A router interface can belong to multiple zones. Service policies are applied in interface configuration mode. Router management interfaces …
CCNA Security Chapter 3 Exam Answers (CCNAS v1.2 and v1.1) 1. Why is local database authentication preferred over a password-only login? It specifies a different password for each line or port. It provides for authentication and accountability. It requires a login and password combination on console, vty lines, …
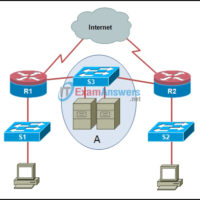
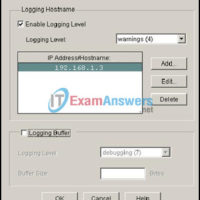
CCNA Security Chapter 2 Exam Answers (CCNAS v1.2 and v1.1) 1. Refer to the exhibit. What two pieces of information can be gathered from the generated message? (Choose two.) This message is a level five notification message. This message appeared because a minor error occurred requiring further investigation. …
CCNA Security Chapter 1 Exam Answers (CCNAS v1.2 and v1.1) 1. What are the basic phases of attack that can be used by a virus or worm in sequential order? paralyze, probe, penetrate, persist, and propagate probe, penetrate, persist, propagate, and paralyze penetrate, persist, propagate, paralyze, and probe …
6.6.2 Digital Forensics and Incident Analysis and Response Quiz Answers 6.6.2 Digital Forensics and Incident Analysis and Response Quiz. Cyber Threat Management Module 6 Quiz Answers 1. Which term is used in the Diamond Model of intrusion to describe a tool that a threat actor uses toward a …
5.4.2 Risk Management and Security Controls Quiz Answers 5.4.2 Risk Management and Security Controls Quiz. Cyber Threat Management Module 5 Quiz Answers 1. The CEO of a company is concerned that if a data breach should occur and customer data is exposed, the company could be sued. The …
4.4.2 Endpoint Vulnerability Quiz Answers 4.4.2 Endpoint Vulnerability Quiz. Cyber Threat Management Module 4 Quiz Answers 1. In profiling a server, what defines what an application is allowed to do or run on a server? user accounts listening ports service accounts software environment 2. In network security assessments, …
3.3.2 Threat Intelligence Quiz Answers 3.3.2 Threat Intelligence Quiz. Cyber Threat Management Module 3 Quiz Answers 1. What is the primary function of (ISC2)? to provide a weekly digest of news articles about computer security to maintain a detailed list of all zero-day attacks to maintain a list …
2.5.2 Network Security Testing Quiz Answers 2.5.2 Network Security Testing Quiz. Cyber Threat Management Module 2 Quiz Answers 1. What is the purpose of the Tripwire network testing tool? to perform vulnerability scanning to provide password auditing and recovery to detect unauthorized wired network access to provide information …
1.4.2 Governance and Compliance Quiz Answers 1.4.2 Governance and Compliance Quiz. Cyber Threat Management Module 1 Quiz Answers 1. Which of the following principles is used by the U.S. government in its access control models? Job rotation Separation of duties Need to know Mandatory vacations 2. An organization …