CCNA Security Chapter 3 Exam Answers (CCNAS v1.2 and v1.1)
1. Why is local database authentication preferred over a password-only login?
- It specifies a different password for each line or port.
- It provides for authentication and accountability.
- It requires a login and password combination on console, vty lines, and aux ports.
- It is more efficient for users who only need to enter a password to gain entry to a device.
2. What is a characteristic of AAA?
- Authorization can only be implemented after a user is authenticated.
- Accounting services are implemented prior to authenticating a user.
- Accounting services determine which resources the user can access and which operations the user is allowed to perform.
- Authorization records what the user does, including what is accessed, the amount of time the resource is accessed, and any changes that were made.
3. Due to implemented security controls, a user can only access a server with FTP. Which AAA component accomplishes this?
- accessibility
- accounting
- auditing
- authentication
- authorization
4. Which two AAA access method statements are true? (Choose two.)
- Character mode provides remote users with access to network resources and requires use of the console, vty, or tty ports.
- Character mode provides remote users with access to network resources and requires use of dialup or VPN.
- Character mode provides users with administrative privilege EXEC access and requires use of the console, vty, or tty ports.
- Packet mode provides users with administrative privilege EXEC access and requires use of dialup or VPN.
- Packet mode provides remote users with access to network resources and requires use of dialup or VPN.
- Packet mode provides users with administrative privilege EXEC access and requires use of the console, vty, or tty ports.
5. Which two statements describe AAA authentication? (Choose two.)
- Server-based AAA authentication is more scalable than local AAA authentication.
- Local AAA is ideal for large complex networks because it uses the local database of the router for authentication.
- Server-based AAA authentication can use the RADIUS or TACACS+ protocols to communicate between the router and a AAA server.
- Server-based AAA authentication is ideal for large complex networks because it uses the local database of the router for authentication.
- Local AAA authentication requires the services of an external server, such as the Cisco Secure ACS for Windows Server.
6. What is a difference between using the login local command and using local AAA authentication for authenticating administrator access?
- Local AAA authentication supports encrypted passwords; login local does not.
- Local AAA provides a way to configure backup methods of authentication; login local does not.
- A method list must be configured when using the login local command, but is optional when using local AAA authentication.
- The login local command supports the keyword none, which ensures that authentication succeeds, even if all methods return an error.
7. Refer to the exhibit. Router R1 has been configured as shown, with the resulting log message. On the basis of the information presented, which two AAA authentication statements are true? (Choose two.)
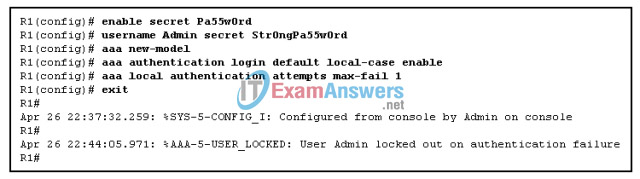
- The locked-out user failed authentication.
- The locked-out user is locked out for 10 minutes by default.
- The locked-out user should have used the username Admin and password Pa55w0rd.
- The locked-out user should have used the username admin and password Str0ngPa55w0rd.
- The locked-out user stays locked out until the clear aaa local user lockout username Admin command is issued.
8. Refer to the exhibit. Router R1 is configured as shown. An administrative user attempts to use Telnet from router R2 to router R1 using the interface IP address 10.10.10.1. However, Telnet access is denied. Which option corrects this problem?
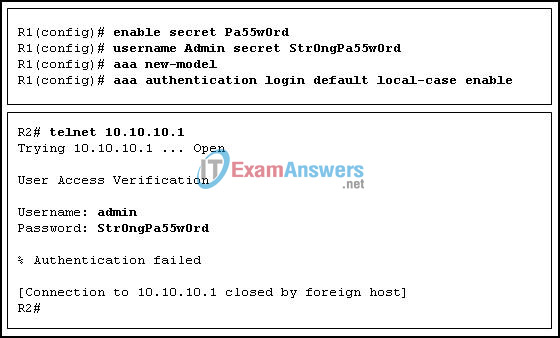
- The R1 10.10.10.1 router interface must be enabled.
- The vty lines must be configured with the login authentication default command.
- The aaa local authentication attempts max-fail command must be set to 2 or higher.
- The administrative user should use the username Admin and password Str0ngPa55w0rd.
9. When configuring a method list for AAA authentication, what is the effect of the keyword local?
- It accepts a locally configured username, regardless of case.
- It defaults to the vty line password for authentication.
- The login succeeds, even if all methods return an error.
- It uses the enable password for authentication.
10. What is a characteristic of TACACS+?
- TACACS+ is an open IETF standard.
- TACACS+ is backward compatible with TACACS and XTACACS.
- TACACS+ provides authorization of router commands on a per-user or per-group basis.
- TACACS+ uses UDP port 1645 or 1812 for authentication, and UDP port 1646 or 1813 for accounting
11. Which statement identifies an important difference between TACACS+ and RADIUS?
- TACACS+ provides extensive accounting capabilities when compared to RADIUS.
- The RADIUS protocol encrypts the entire packet transmission.
- The TACACS+ protocol allows for separation of authentication from authorization.
- RADIUS can cause delays by establishing a new TCP session for each authorization request.
12. In regards to Cisco Secure ACS, what is a client device?
- a web server, email server, or FTP server
- the computer used by a network administrator
- network users who must access privileged EXEC commands
- a router, switch, firewall, or VPN concentrator
13. What is the result if an administrator configures the aaa authorization command prior to creating a user with full access rights?
- The administrator is immediately locked out of the system.
- The administrator is denied all access except to aaa authorization commands.
- The administrator is allowed full access using the enable secret password.
- The administrator is allowed full access until a router reboot, which is required to apply changes.
14. When configuring a Cisco Secure ACS, how is the configuration interface accessed?
- A Web browser is used to configure a Cisco Secure ACS.
- The Cisco Secure ACS can be accessed from the router console.
- Telnet can be used to configure a Cisco Secure ACS server after an initial configuration is complete.
- The Cisco Secure ACS can be accessed remotely after installing ACS client software on the administrator workstation.
15. Which AAA protocol and feature best support a large ISP that needs to implement detailed accounting for customer invoicing?
- TACACS+ because it combines authentication and authorization, but separates accounting
- RADIUS because it supports detailed accounting that is required for billing users
- TACACS+ because it requires select authorization policies to be applied on a per-user or per-group basis
- RADIUS because it requires select authorization policies to be applied on a per-user or per-group basis
16. After accounting is enabled on an IOS device, how is a default accounting method list applied?
- Accounting method lists are applied only to the VTY interfaces.
- A named accounting method list must be explicitly defined and applied to desired interfaces.
- Accounting method lists are not applied to any interfaces until an interface is added to the server group.
- REJECT response. The default accounting method list is automatically applied to all interfaces, except those with named accounting method lists.
17. Refer to the exhibit. In the network shown, which AAA command logs the use of EXEC session commands?
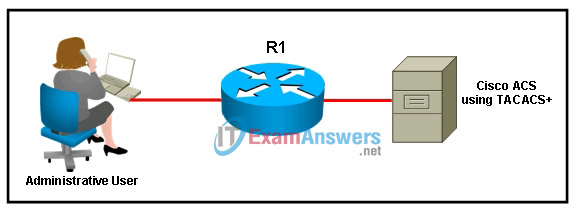
- aaa accounting connection start-stop group radius
- aaa accounting connection start-stop group tacacs+
- aaa accounting exec start-stop group radius
- aaa accounting exec start-stop group tacacs+
- aaa accounting network start-stop group radius
- aaa accounting network start-stop group tacacs+
18. How does a Cisco Secure ACS improve performance of the TACACS+ authorization process?
- reduces overhead by using UDP for authorization queries
- reduces delays in the authorization queries by using persistent TCP sessions
- reduces bandwidth utilization of the authorization queries by allowing cached credentials
- reduces number of authorization queries by combining the authorization process with authentication
19. Refer to the exhibit. Which Cisco Secure ACS menu is required to configure the IP address and secure password of an AAA client?
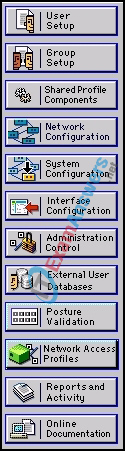
- User Setup
- Group Setup
- Network Configuration
- System Configuration
- Interface Configuration
- Administration Control
20. What is an effect if AAA authorization on a device is not configured?
- Authenticated users are granted full access rights.
- User access to specific services is determined by the authentication process.
- Character mode authorization is limited, and packet mode denies all requests.
- All authorization requests to the TACACS server receive a
21. Which authentication method stores usernames and passwords in the router and is ideal for small networks?
- local AAA
- local AAA over RADIUS
- local AAA over TACACS+
- server-based AAA
- server-based AAA over RADIUS
- server-based AAA over TACACS+
22. Which two statements describe Cisco Secure ACS? (Choose two.)
- Cisco Secure ACS supports LDAP.
- Cisco Secure ACS is only supported on wired LAN connections.
- Cisco Secure ACS only supports the TACACS+ protocol.
- Cisco Secure ACS supports both TACACS+ and RADIUS protocols.
- Cisco Secure ACS Express is a rack-mountable unit intended for more than 350 users.
23. Which technology provides the framework to enable scalable access security?
- role-based CLI access
- Simple Network Management Protocol
- AutoSecure
- Cisco Configuration Professional communities
- authentication, authorization, and accounting
24. Which two modes are supported by AAA to authenticate users for accessing the network and devices? (Choose two.)
- verbose mode
- character mode
- quiet mode
- packet mode
- ancillary mode
25. Which two features are included by both TACACS+ and RADIUS protocols? (Choose two.)
- separate authentication and authorization processes
- password encryption
- utilization of transport layer protocols
- SIP support
- 802.1X support
26. A company is deploying user device access control through a NAC appliance as part of the Cisco TrustSec solution. Which device is needed to serve as the central management for the access control?
- Cisco Secure ACS
- Cisco NAC Profiler
- Cisco NAC Manager
- Cisco NAC Guest Server
27. A global company is deploying Cisco Secure ACS to manage user access to its headquarters campus. The network administrator configures the ACS to use multiple external databases for users from different geographical regions. The administrator creates user groups to match these databases. What is a purpose of creating different groups of users to authenticate through the Cisco Secure ACS?
- to better manage the user database.
- to improve the performance of the authentication process.
- to accommodate any difference in the authorization process between the ACS and an external database.
- to accommodate any difference in the authentication requirements between the ACS and an external database.
28. Refer to the exhibit. A network administrator configures AAA authentication on R1. When the administrator tests the configuration by telneting to R1 and no ACS servers can be contacted, which password should the administrator use in order to login successfully?
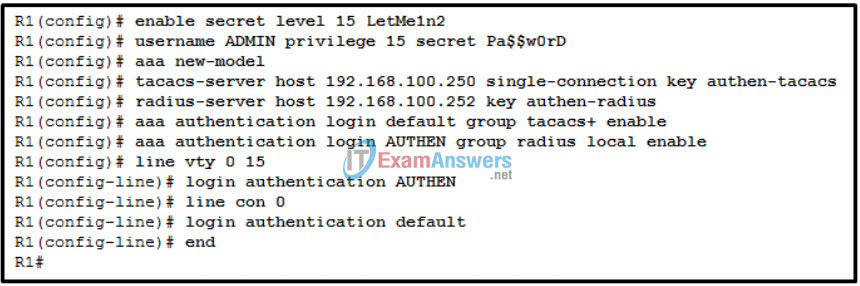
- LetMe1n2
- Pa$$w0rD
- authen-radius
- authen-tacacs
29. Which component of AAA is used to determine which resources a user can access and which operations the user is allowed to perform?
- authentication
- authorization
- accounting
- auditing
30. Refer to the exhibit. A network administrator configures AAA authentication on R1. Which statement describes the effect of the keyword single-connection in the configuration?
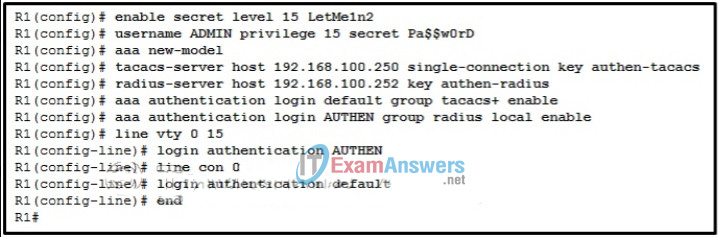
- The TACACS+ server only accepts one successful try for a user to authenticate with it.
- The authentication performance is enhanced by keeping the connection to the TACACS+ server open.
- R1 will open a separate connection to the TACACS+ server for each user authentication session.
- R1 will open a separate connection to the TACACS server on a per source IP address basis for each authentication session.
31. Refer to the exhibit. What is represented by the area marked as “A”?
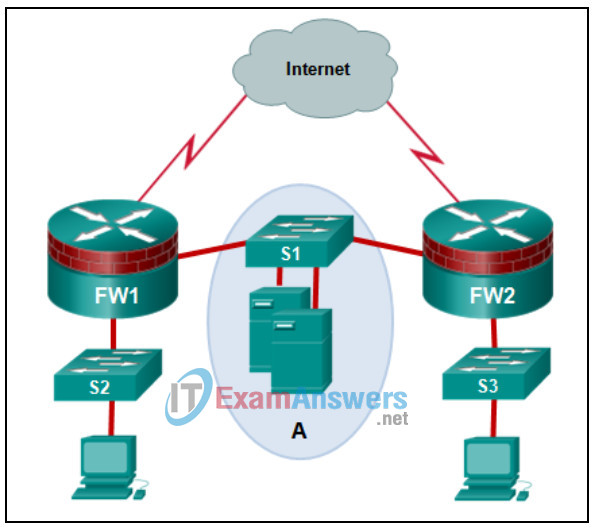
- Internal network
- Untrusted network
- DMZ
- Perimeter security boundary
